- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
915 GRE courses in Coventry delivered Live Online
Legal Aid - Family Controlled Work Billing Course
By DG Legal
The LAA operates a strict compliance regime when it comes to auditing family controlled work matters, and mistakes can often result in a Contract Notice, corrective action, and further follow-up activity within 6 months. This course will discuss the various aspects of family controlled work billing, with discussions on topics such as how to bill private law, public law, and help with mediation matters; how to evidence whether substantive negotiations and a settlement have taken place in private law matters; how do the LAA audit travel and other disbursement claims; what evidence must be present on files to avoid any issues on audit – including scope, gateway evidence, and forms/evidence of means (rules on evidence of means will be included in brief, however, a separate, more in-depth course will be announced in due course); and the rules on claiming separate matters and escape fees. Key aspects of the Civil Contract and associated LAA Guidance (including the Codes Guidance) will be included, along with a discussion of common errors that are made. Target Audience This online course is aimed at anyone involved in billing Family Controlled Work matters or managing an LAA Family Contract. Resources Course notes will be provided to all delegates which may be useful for ongoing reference or cascade training. Please note a recording of the course will not be made available. Speaker Steve Keeling, Consultant, DG Legal Steve joined DG Legal after leaving the Legal Aid Agency in August 2016. In his 17 years at the LAA, he worked in the audit team as both auditor and manager and was a Contract Manager for several years. Steve is also a certified SQM auditor and undertakes audits on behalf of Recognising Excellence as well as running training sessions for the SQM Audit Team periodically.

LOOKING FOR: ADULT FICTION, NON-FICTION Diana joined the prestigious DHH Literary Agency in June 2024. She started agenting with Rupert Heath Literary Agency in 2011 before moving to UTA and Marjacq in 2017. Before that she was senior commissioning editor at Transworld. Diana was chosen as one of The Bookseller’s Rising Stars of 2012, was a nominee for RNA Agent of the Year 2019, and was shortlisted for Literary Agent of the Year 2022 at the British Book Awards. Her list includes a wide range of bestselling and prize-winning authors in the UK and internationally. Diana represents adult fiction and non-fiction. For fiction, she is looking for upmarket women's commercial, with depth and heart, including reading group, historical, saga, uplit and contemporary stories that are irreverent and make her laugh; accessible literary fiction, high-concept crime fiction and thrillers. She has a thing for spy novels and would love to find a great vampire story. On the non-fiction side: memoir, smart, funny feminists, lifestyle, cookery and social justice, and open to anything with a strong, original voice. She also encourages submissions from writers who have been traditionally under-represented. Diana would like you to submit a covering letter, 1 - 2 page synopsis and the first three chapters (a maximum of 5,000 words) of your manuscript in a single word document. (In addition to the paid sessions, Diana is kindly offering one free session for low income/underrepresented writers. Please email agent121@iaminprint.co.uk to apply, outlining your case for this option which is offered at the discretion of I Am In Print). By booking you understand you need to conduct an internet connection test with I Am In Print prior to the event. You also agree to email your material in one document to reach I Am In Print by the stated submission deadline and note that I Am In Print take no responsibility for the advice received during your agent meeting. The submission deadline is: Wednesday 13th August 2025

LOOKING FOR: ADULT FICTION, NON-FICTION Daisy Chandley joined PFD in 2019 after graduating from the University of Oxford with a BA in Politics, Philosophy and Economics. She is an Associate Agent and assistant to Senior Agent Annabel Merullo and Head of Books Tim Bates as the UK sub-agent for New Directions Publishing in the US. Daisy is actively building a list of both fiction and non-fiction authors across a range of genres. With fiction, Daisy's wishlist roughly falls into three categories – if something feels like it overlaps between them, even better! 1) Sharp, original novels on the literary to upmarket spectrum, all the way from deeply dark and boundary-pushing books like Hurricane Season, Under The Skin or In The Cut to those balancing edge, heart and humour, like Detransition, Baby or A Visit From The Goon Squad. She loves irreverent wit, daring approaches in narrative or form, and seriously unsettling stories in equal measure, and if you can bring a few of those elements into one, it’ll go straight to the top of her. 2) Com-heavy rom-coms, whether in the dry but ultimately sob-inducing vein of Greta and Valdin or a Nora Ephron film, the escapist screwball delight of a Cary Grant classic, or the more unusual, genre-bending style of something like Palm Springs. Daisy is a sucker for Emily Henry and will always be happy to see an innovative take on tropey love stories, but is equally very keen to see to things a bit outside of the box, whether that’s integrating speculative elements, dark humour, or topical issues. In any case, humour and originality are my priority, and affectionately snarky bickering is the best way to make her fall head over heels with a couple. 3) Sleuths! Daisy is not the right person for police procedurals, but loves classic detectives and amateur sleuths. Whether it’s a delightful Knives Out or Nancy Drew homage or an intricate, unputdownable mystery on the darker side, the minute someone finds a good old fashioned clue, count her in! Overall, whether it’s a delightfully fun and scandalous page-turner or something really bold and experimental, if it’s stylish and smart – and maybe even a bit sexy – Daisy would love to see it. Daisy is definitely interested in literary speculative fiction, though not generally looking for hard SFF. Across the board, she is always looking for stories that explore sexuality, race, gender, and disability, and would particularly love to hear from writers whose voices and experiences aren’t given enough space in publishing. On the non-fiction side, Daisy is looking for bold new insights and underrepresented voices on popular science, nature writing, relationships, social issues and politics, and am always especially interested in fresh, playful and exciting writing on pop culture, love and the internet. She’d also love to see illuminating narrative non-fiction, whether a beautiful and lyrical exploration, or an enthralling and explosive deep-dive. A (large) handful of authors past and present whose work Daisy loves include Patricia Lockwood, Toni Morrison, Elif Batuman, Gillian Flynn, Shirley Jackson, Raven Leilani, Max Porter, Carmen Maria Machado, Virginia Woolf, Sayaka Murata, Kiley Reid, Sally Rooney, George Saunders, Joan Didion, Amy Liptrot, Ottessa Moshfegh, J.D. Salinger, Donna Tartt, Bret Easton Ellis, and Fernanda Melchor. Daisy is not the right fit for Children’s or YA authors. Daisy would like you to submit a covering letter, 1 page synopsis and the first 2,500 words of your manuscript in a single word document. (In addition to the paid sessions, Daisy is kindly offering one free session for low income/under-represented writers. Please email agent121@iaminprint.co.uk to apply, outlining your case for this option which is offered at the discretion of I Am In Print). By booking you understand you need to conduct an internet connection test with I Am In Print prior to the event. You also agree to email your material in one document to reach I Am In Print by the stated submission deadline and note that I Am In Print take no responsibility for the advice received during your agent meeting. The submission deadline is: Thursday 14th August 2025

TWO SPACES LEFT! 20th August Marilia Savvides #Agent121. Looking for: ADULT FICTION
5.0(3)By I Am In Print
LOOKING FOR: ADULT FICTION Marilia Savvides founded The Plot Agency in 2024. She began her career in publishing at Peters Fraser and Dunlop, where she spent eight years, first as International Rights Agent, and later as Literary Agent, building her own list of authors. In 2019, she joined 42MP, where she worked as Literary Agent for four years, helping to launch and set up the Book Division. She is particularly interested in fiction that is beautifully written and cleverly constructed, but still accessible to a wide readership. She is often drawn to darker tales that weave together excellent characters and an impossible-to-put-down story, from immersive book club novels with a splash of suspense, crime and thrillers, accessible horror, and speculative, genre-bending or dystopian stories. She also adores smart, witty contemporary rom-com in the style of Emily Henry. In the thriller, crime and mystery space she is interested in most areas, except military thrillers and organised crime/ mafia / mob stories. Big hooks and clever set ups are a big bonus! She adores Karin Slaughter (especially her standalone novels) and Gillian Flynn. In the book club / reading group space, she’s particularly drawn to fiction in the vein of Jodi Picoult, Liane Moriarty and Celeste Ng, and absolutely fell in love with Bright Young Women by Jessica Knoll, both for the incredible voice, and the exquisite use of structure and time. Complicated family dynamics, empathetic and smart approaches to controversial issues, stand out protagonists (like Elizabeth Zott in Lessons in Chemistry or Bernadette in Where D’You Go Bernadette), long buried secrets, complicity, the road to justice, and impossible decisions, are all themes she finds herself drawn to. In the horror space, she’s a sucker for amazing female-centric stories in the vein of Yellowjackets, and the kind of contemporary, accessible horror that Stephen King always nails. She wants to get lost in a world that feels within reach of ours. In the speculative and dystopian spaces, she’s interested in genius ideas that set up big questions or reflect the most broken (and sometimes hidden) parts of society. She loves Octavia Butler, Margaret Atwood, George Orwell, and also adored The Leftovers, Station Eleven, Wanderers, and The Power. The what-ifs of life and fiction fascinate her. In the grounded sci-fi space, she’d love to find a smart, immersive, and accessible story like The Martian. She doesn’t represent fantasy or romantasy. In regards to sci-fi, unless it’s very grounded and has crossover potential to a mainstream audience, it’s not for her. In the romance space, she’s particularly drawn to smart, complex and witty characters, where the chemistry is jumping off the page. She loves contemporary settings and all the tropes, though the voice and characters must come first to make the reading experience fully immersive. She wants to be cackling, and rooting for the characters with all her heart. She is very hands-on editorially, and loves working with her authors to shape their manuscripts, and brainstorm ideas. The best part of the job is discovering debut authors, and helping them find a home for their books. Marilia would like you to submit a covering letter, 1 - 2 page synopsis and the first 5,000 words of your manuscript in a single Word document. (In addition to the paid sessions, Marilia is kindly offering one free session for low income/underrepresented writers. Please email agent121@iaminprint.co.uk to apply, outlining your case for this option which is offered at the discretion of I Am In Print). By booking you understand you need to conduct an internet connection test with I Am In Print prior to the event. You also agree to email your material in one document to reach I Am In Print by the stated submission deadline and note that I Am In Print take no responsibility for the advice received during your agent meeting. The submission deadline is: Wednesday 13th August 2025

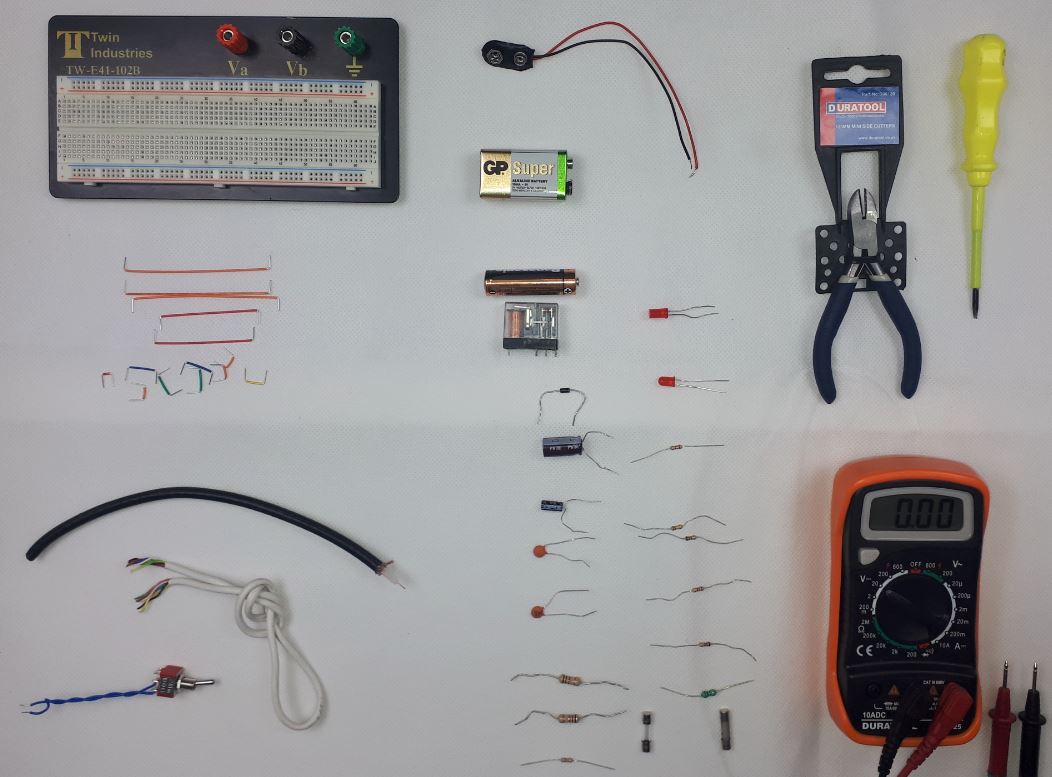
Digital Electronics Course Online
By Hi-Tech Training
This Digital Electronics Course is designed to give practical knowledge of the type of electronic circuitry used in a modern Computer System or in any type of Computer Controlled equipment such as Photocopiers, Cash Registers, Tablets, mobile phones and many other types of IT equipment. Digital Electronics involves the use of Silicon chips (Integrated Circuits). The internal structure of a computer is to a large extent comprised of Digital Electronic Circuits.
22nd August Laura Williams #Agent121. Looking for: YA, ADULT FICTION, NON-FICTION
5.0(3)By I Am In Print
LOOKING FOR: YA, ADULT FICTION, NON-FICTION Laura Williams is literary agent at the Greene and Heaton Literary Agency. She is seeking literary fiction, commercial fiction, psychological thrillers and high concept Young Adult. Laura is actively building a fiction list and a small non-fiction list. She is currently looking for literary fiction, edgy commercial fiction, psychological thrillers and high-concept contemporary young adult, as well as narrative non-fiction of all types. Her taste is quite dark, and she loves gothic, ghost stories, horror and anything sinister. She also loves books that make her cry, from big love stories to intense family dramas. She is open to historical or horror YA, but not magical or fantasy. Meditative or moving novels about modern life, appeal to Laura, sad stories with love and the importance of caring for each other shining through. She also loves stories about female friendships or conversely groups of women who don't get on, such as the hugely fun BAD SUMMER PEOPLE by Emma Rosenblum. She is always on the lookout for a big tragic love story to make her cry happy or sad tears. At the more commercial end of fiction, think funny novels with warmth and romantic comedies with a bit of depth – think Marian Keyes. Most of all Laura is looking for novels she hasn’t read before – something unusual structurally or thematically, something that shines a light on a subject the author is passionate about, something that’ll break her heart or raise her blood in an entirely new way. Laura is always looking to promote diverse voices from across the globe, and is particularly keen on LGBTQI+ stories. Laura would like you to submit a covering letter, a 1-2 page synopsis and the first 5,000 words of your completed manuscript in a single word document. (In addition to the paid sessions, Laura is kindly offering one free session for low income/under-represented writers. Please email agent121@iaminprint.co.uk to apply, outlining your case for this option which is offered at the discretion of I Am In Print). By booking you understand you need to conduct an internet connection test with I Am In Print prior to the event. You also agree to email your material in one document to reach I Am In Print by the stated submission deadline and note that I Am In Print take no responsibility for the advice received during your agent meeting. The submission deadline is: Wednesday 13th August 2025

SOLD OUT! 21st August Camille Burns #Agent121. Looking for: MG, YA inc YA/CROSSOVER ROMANCE, and ADULT FICTION; NON-FICTION FOR ALL AGES.
5.0(3)By I Am In Print
LOOKING FOR: MIDDLE GRADE, YOUNG ADULT & ADULT FICTION AS WELL AS NON-FICTION FOR ALL AGES Prior to joining DKW in 2023, Camille worked at David Higham Associates as Agent’s Assistant to Jane Gregory and in the Children’s Translation Rights team. She has also worked in editorial for an academic publisher, in rights and marketing for an audiobook publisher and as an intern at Felicity Bryan Literary Agency. Camille loves engaging with narratives on a structural level in order to draw out their best qualities. Camille has an MSc in Publishing from Edinburgh Napier University and an MA in English Literature from the University of Edinburgh. She was Secretary of the Association of Authors’ Agents, as well as Co-Chair for the AAA’s Bridge Committee for early career agents and assistants, from late 2021 to early 2024. She also previously volunteered at the Story Museum in Oxford. Camille is looking to grow her list with a particular focus on middle grade, young adult and adult/crossover fiction, as well as non-fiction for all ages. Books that she has loved and that speak to her taste include Lockwood and Co by Jonathan Stroud (MG), I’ll Give You The Sun by Jandy Nelson (YA), Fourth Wing by Rebecca Yarros (crossover) and Every Summer After by Carley Fortune (adult). For more information, please visit Camille's page on the Diamond Kahn Woods Literary Agency website. Camille would like you to submit a covering letter, 1 page synopsis and the first three chapters or 5,000 words of your manuscript in a single word document. (In addition to the paid sessions, Camille is kindly offering one free session for low income/under-represented writers. Please email agent121@iaminprint.co.uk to apply, outlining your case for this option which is offered at the discretion of I Am In Print). By booking you understand you need to conduct an internet connection test with I Am In Print prior to the event. You also agree to email your material in one document to reach I Am In Print by the stated submission deadline and note that I Am In Print take no responsibility for the advice received during your agent meeting. The submission deadline is: Wednesday 13th August 2025

Catching the Wind
By SoulSpark Online
Training Trainers of Spiritual Directors Developing the abilities needed to facilitate Spiritual Direction formation programmes

Improving Communications UK offers an Advanced Presentation Skills course designed to enhance public speaking abilities and improve the use of presentation software. This course provides delegates with the opportunity to refine their skills in a supportive environment. As delegates deliver their presentations, they are coached on key areas such as body language, posture, word choice, confidence, eye contact, volume, and reducing verbal tics and filler words. This comprehensive approach ensures that delegates can effectively engage their audience and convey their message with clarity and confidence. The course also focuses on enhancing content and visual aids, typically using software like PowerPoint. Delegates learn how to: Clearly state their purpose Reduce text on slides Create user-friendly messages Select impactful graphics to support their message By the end of the course, delegates will be able to deliver organised and engaging presentations that motivate audiences, craft streamlined messages, enhance their stage presence, and convince listeners with compelling evidence in speech and visuals. This course is ideal for those seeking to improve their presentation skills and make a lasting impact. The Advanced Presentation Skills course is a 4-hour interactive virtual class for up to six delegates. Upon registration, delegates will receive online login instructions prior to the class date. This format allows for a personal and interactive learning experience from the comfort of one's own home.

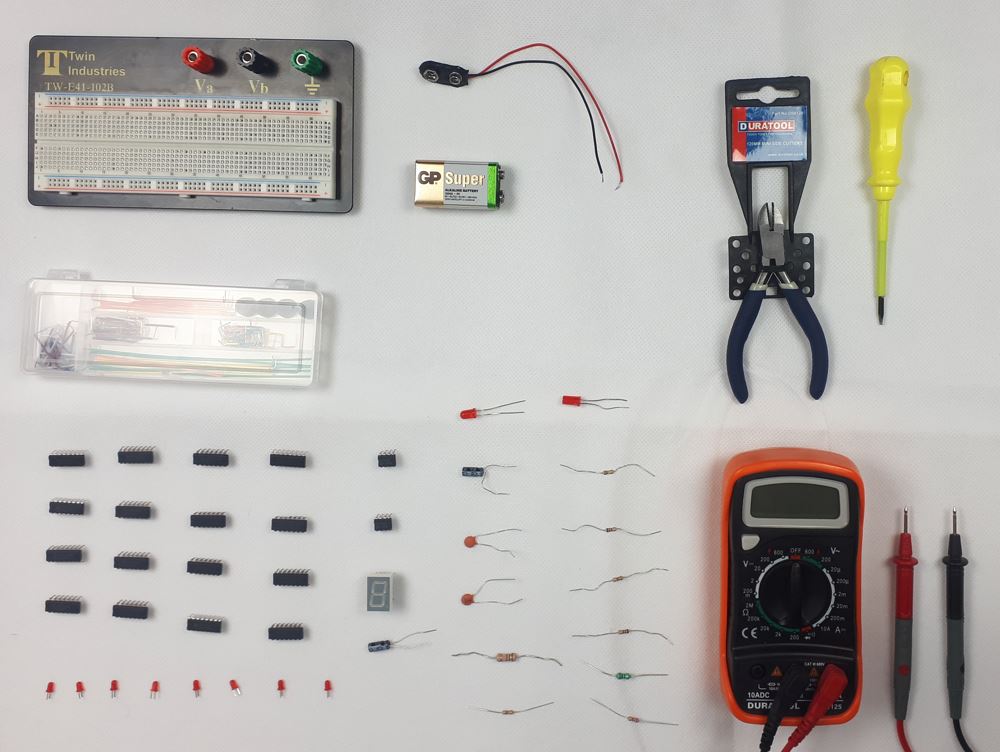
Preliminary Electronic Security Course
By Hi-Tech Training
The Preliminary Electronic Security Course is an introductory (or revision) course designed to provide participants who have no previous Electrical or Electronics experience with the background skills required to attend the CCTV Installation Course, Access Control Course or Fire Alarm Foundation Course. The course gives both an introduction to electronics and electronic security and shows how the two fields merge together. Ideal for a beginner wishing to learn more about this fascinating area. A large practical content is guaranteed. The day will be an excellent learning experience with a skilled instructor. It is a great introduction to the other courses we provide.