- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
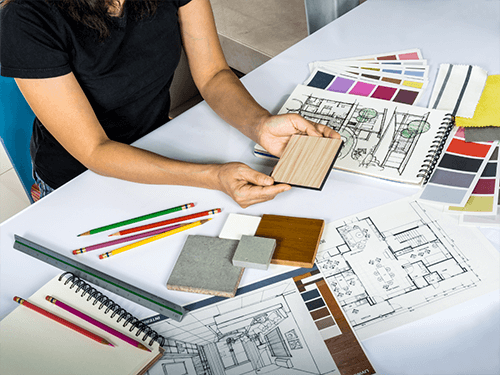
Furniture Restoration & Interior Decorating Skills Training
By iStudy UK
Interior decorating is the art of decoration of the interior of a building, house, or a room. Decorations will depend on the preference of the owner while considering its functionality. Interior decorating includes furniture restoration since it will help in creating a new look in a place. Provided in this course are both the skills in furniture restoration and interior decorating. Interior decorating is important as it provides an essence of the space that makes it livable and pleasing. Course Highlights Furniture Restoration & Interior Decorating Skills Training is an award winning and the best selling course that has been given the CPD Certification & IAO accreditation. It is the most suitable course anyone looking to work in this or relevant sector. It is considered one of the perfect courses in the UK that can help students/learners to get familiar with the topic and gain necessary skills to perform well in this field. We have packed Furniture Restoration & Interior Decorating Skills Training into 72 modules for teaching you everything you need to become successful in this profession. To provide you ease of access, this course is designed for both part-time and full-time students. You can become accredited in just 2 days, 12 hours hours and it is also possible to study at your own pace. We have experienced tutors who will help you throughout the comprehensive syllabus of this course and answer all your queries through email. For further clarification, you will be able to recognize your qualification by checking the validity from our dedicated website. Why You Should Choose Furniture Restoration & Interior Decorating Skills Training Lifetime access to the course No hidden fees or exam charges CPD Accredited certification on successful completion Full Tutor support on weekdays (Monday - Friday) Efficient exam system, assessment and instant results Download Printable PDF certificate immediately after completion Obtain the original print copy of your certificate, dispatch the next working day for as little as £9. Improve your chance of gaining professional skills and better earning potential. Who is this Course for? Furniture Restoration & Interior Decorating Skills Training is CPD certified and IAO accredited. This makes it perfect for anyone trying to learn potential professional skills. As there is no experience and qualification required for this course, it is available for all students from any academic backgrounds. Requirements Our Furniture Restoration & Interior Decorating Skills Training is fully compatible with any kind of device. Whether you are using Windows computer, Mac, smartphones or tablets, you will get the same experience while learning. Besides that, you will be able to access the course with any kind of internet connection from anywhere at any time without any kind of limitation. Career Path You will be ready to enter the relevant job market after completing this course. You will be able to gain necessary knowledge and skills required to succeed in this sector. All our Diplomas' are CPD and IAO accredited so you will be able to stand out in the crowd by adding our qualifications to your CV and Resume. Restoring Your Furniture WOOD FINISHING IN GENERAL FREE 01:00:00 PREPARATION OF NEW AND OLD SURFACES FREE 01:00:00 STAINS IN GENERAL 00:30:00 FACTORY PREPARED STAINS 00:30:00 WATER STAINS 01:00:00 STAIN BRUSHING AND PROCEDURE 01:00:00 PREPARING WOOD TO TAKE STAIN WITH EVEN COLOR EFFECT 01:00:00 THE USE OF WOOD FILLERS 01:00:00 VARNISH AND SHELLAC 01:00:00 VARNISHING, RUBBING, POLISHING 01:00:00 VARNISH DEFECTS AND THEIR CAUSES 01:00:00 LACQUERS 01:00:00 Interior Design Fundamentals Define a Theme: Contemporary, Cottage, Eclectic, Southwest FREE 01:00:00 Budget Design for Your Living Room, Den or Family Room 01:00:00 Budget Ideas for Kitchen Design 01:00:00 Budget Bedroom Makeover 01:00:00 Closet Cleanups 01:00:00 Need a Home Office? 00:30:00 Camouflage with Paint! 01:00:00 Faux Finishes Are Hot - Bare Walls Are Not! 00:30:00 Window Treatments 01:00:00 Making the Most of Molding 00:30:00 Fabulous Furniture Finds 00:30:00 Decorate With Wallpaper 01:00:00 Freehand or Stencil A Mural Makes the Wall! 01:00:00 Accessorize - Funky Can Be Fun! 01:00:00 Have Some Fun with Fabric! 01:00:00 Decorating House Interior HOW TO REARRANGE A ROOM FREE 02:00:00 HOW TO ANALYZE A ROOM AS PROFESSIONALS DO BEFORE YOU FREE 01:00:00 HOW TO CREATE A ROOM 02:00:00 HOW TO DETERMINE CHARACTERS OF HANGINGS AND FURNITURES-COVERING FOR A GIVEN ROOM 01:00:00 CANDLESTICKS, LAMPS, FIXTURES FOR GAS AND ELECTRICITY, AND SHADES 01:00:00 WINDOW SHADES AND AWNINGS 00:30:00 TREATMENT OF PICTURES AND PICTURE FRAMES 01:00:00 TREATMENT OF PIANO CASES 00:15:00 TREATMENT OF DINING-ROOM BUFFETS AND DRESSING-TABLES 00:15:00 TREATMENT OF WORK TABLES, BIRD CAGES, DOG BASKETS AND FISH GLOBES 00:30:00 TREATMENT OF FIREPLACES 00:30:00 TREATMENT OF BATHROOMS 01:00:00 PERIOD ROOMS 01:00:00 PERIODS IN FURNITURE 01:00:00 CONTINUATION OF PERIODS IN FURNITURE 01:00:00 THE GOTHIC PERIOD 00:30:00 THE RENAISSANCE 01:00:00 FRENCH FURNITURE 01:00:00 THE PERIODS OF THE THREE LOUIS 01:00:00 THE MAHOGANY PERIOD 02:00:00 THE COLONIAL PERIOD 00:30:00 THE REVIVAL OF DIRECTOIRE AND EMPIRE FURNITURE 00:30:00 THE VICTORIAN PERIOD 00:30:00 PAINTED FURNITURE 00:30:00 TREATMENT OF AN INEXPENSIVE BEDROOM 01:00:00 TREATMENT OF A GUEST ROOM (Where economy is not an item of importance) 01:00:00 A MODERN HOUSE IN WHICH GENUINE JACOBEAN FURNITURE IS APPROPRIATELY SET 00:30:00 UNCONVENTIONAL BREAKFAST-ROOMS AND SPORTS BALCONIES 01:00:00 SUN-ROOMS 01:00:00 TREATMENT OF A WOMAN'S DRESSING-ROOM 00:30:00 THE TREATMENT OF CLOSETS 00:30:00 TREATMENT OF A NARROW HALL 00:15:00 TREATMENT OF A VERY SHADED LIVING-ROOM 00:15:00 SERVANTS' ROOMS 00:15:00 THE BABY'S ROOMS: THE DAY ROOM, THE NIGHT ROOM 01:00:00 ROOMS FOR THE ELDERLY 01:00:00 A YOUNG GIRL'S ROOM 01:00:00 THE YOUNG BOY'S ROOM 00:30:00 TABLE DECORATION 01:00:00 WHAT TO AVOID IN INTERIOR DECORATION: RULES FOR BEGINNERS 01:00:00 FADS IN COLLECTING 01:00:00 WEDGWOOD POTTERY; OLD AND MODERN 01:00:00 ITALIAN POTTERY 00:15:00 VENETIAN GLASS, OLD AND MODERN 00:30:00 CONCLUSION 00:15:00 Mock Exam Final Exam

Diploma in Adobe After Effects CC 2017
By iStudy UK
Learn to create incredible motion graphics and visual effects with the Diploma in Adobe After Effects CC 2017 course. Adobe After Effects CC, developed by Adobe Systems, is used in the post-production process of film making and television production. It is a digital visual effect, motion graphics, and compositing application that Is designed to help you to improve your videos with professional motion graphics and helps you to create excellent film, TV, video, and web. The course is devoted to the motion graphics software and makes you as a pro user of the software. Throughout the course, you will be introduced with the various tools and techniques that you need to know for using the software. You will learn about creating a circle, applying animation effect, using graph editor, adding backgrounds, colour creation and more. You will explore how to create a video project from start to finish in After Effects. Upon completion, you will be able to create professional motion graphics that improve your videos. What Will I Learn? You will know how to use After Effects to make your videos better than ever You will be comfortable using After Effects - even if you're a beginner Know how to create a video project from start to finish in After Effects Create professional motion graphics that improve your videos Add creative visual effects to your video projects Export high quality videos from After Effects and know how to use it with Premiere Pro efficiently You will have the full support of an instructor who loves teaching Requirements You should have Adobe After Effects installed so you can follow along with the course lessons. We'll be using the Creative Cloud version of After Effects, but you can do many of the lessons in a previous version if you don't have After Effects CC. You DO NOT need any experience with After Effects. This course is for beginners and assumes you don't have any experience with the program. Module: 01 1.1 Intro Video FREE 00:03:00 1.2 Project Files - Diploma in Adobe After Effects CC 2017 00:00:00 1.3 Animate Your Name FREE 00:07:00 Module: 02 2.1 Understand the After Effects Workspace 00:06:00 2.2 Starting a New Composition 00:08:00 2.3 Adding Media to Your Project and Timeline 00:05:00 2.4 Using the Basic After Effects Tools 00:10:00 2.5 Create a Perfect Circle, Alignment, and Shape Colors 00:03:00 2.6 Working in the Timeline 00:11:00 2.7 Layer Properties 00:09:00 Module: 03 3.1 Animating in After Effects 00:08:00 3.2 Position, Scale, and Rotation Animations 00:05:00 3.3 Tips to Make Your Animations Look More Nautral 00:04:00 3.4 Using the Graph Editor 00:06:00 3.5 Challenge - Bouncing Ball 00:01:00 3.6 Solution - Bouncing Ball 00:20:00 Module: 04 4.1 Working With Solid Layers and the ken Burns Effects 00:07:00 4.2 Working With Shape Layers, Strokes, and Paths 00:06:00 4.3 Adding Layer Styles Like Drop Shadow, Bevel, and Gradients 00:04:00 4.4 Shape Effects - Trim Path Animation, Wiggle, and Zig Zag 00:06:00 Module: 05 5.1 Track Matte Animation - Make Layers Appear And Disappear 00:09:00 5.2 Using Pre-Compositions to Group Layers 00:06:00 5.3 Easily Reverse Complicated Animations 00:02:00 5.4 Playing with Time 00:06:00 5.5 Blend Modes 00:06:00 5.6 Stabilize Shaky Footage 00:04:00 Module: 06 6.1 Intro to Motion Graphics Projects 00:01:00 6.2 Clean Lower Third 00:09:00 6.3 Logo Reveal Animation Bumper 00:13:00 6.4 Colorful Transition 00:17:00 6.5 Text with Mask Path Animation 00:10:00 6.6 Text Bubble Animation 00:14:00 6.7 Weather App 1 00:16:00 6.8 Weather App 2 00:08:00 6.9 Weather App 3 00:07:00 Module: 07 7.1 Flat Animation Challenge 00:03:00 7.2 Phil Designs his Flat Animation Scene 00:13:00 7.3 Animating Fireworks with the Repeater Effect 00:15:00 Module: 08 8.1 Removing Green Screen Background 00:07:00 8.2 Adding a Background that Matches the Foreground 00:08:00 8.3 Adding Motion to a Still Image with the Puppet Tool 00:06:00 8.4 Adding Movement with the Ripple Effect 00:06:00 Module: 09 9.1 Intro to 3D 00:10:00 9.2 Swinging 3D Text Animation 00:12:00 9.3 Build Out Your 3D Composition 00:06:00 9.4 Animating Our 3D Scene 00:08:00 9.5 Create Stars in After Effects 00:05:00 Module: 10 10.1 Using the Rotoscope Tool 00:07:00 10.2 Cleaning Up Your Edges 00:07:00 10.3 Finishing Our Rotobrush Animation 00:08:00 Module: 11 11.1 Easy Screen Replacement with Masks 00:10:00 11.2 Replacing a Screen Version 2 00:14:00 11.3 Screen Replacement with Mocha 00:08:00 Module: 12 12.1 Using the Puppet Pin Tool 00:05:00 12.2 Animating Your Puppet Pins 00:03:00 12.3 Animated Blinking Eyes 00:08:00 12.4 Adding Perspective with Animated Clouds 00:07:00 Module: 13 13.1 Applying Text Animation Presets 00:06:00 13.2 Create a page Turn Effect with CC page Turn 00:10:00 13.3 Radial and Linear wipes 00:03:00 13.4 Color Correction in After Effects 00:04:00 Module: 14 14.1 Motion Tracking Basics 00:10:00 14.2 Tracking Text and Visual Effects to Video Clip 00:06:00 14.3 Tracking Rotation and Scale 00:12:00 14.4 Adding Details to Our Text 00:04:00 Module: 15 15.1 Intro to Character Animation 00:02:00 15.2 Design Your Character 00:15:00 15.3 Rigging Your Character 00:03:00 15.4 animation Our Character 00:10:00 15.5 Adding the Animated Background 00:09:00 15.6 Adding Details to Character Movement 00:07:00 15.7 Adding the Paper Cut Out Look 00:06:00 Module: 16 16.1 Exporting an H264 File From After Effects 00:07:00 16.2 Exporting from After Effects with a Transparent Background 00:04:00 16.3 Exporting from After Effects through Adobe Media Encoder 00:05:00 16.4 Create an Animated GIF from After Effects 00:07:00 Module: 17 17.1 Audio Tips for After Effects 00:03:00 17.2 Working with Premiere Pro 00:06:00 Module: 18 18.1 Expressions Basics 00:07:00 18.2 Animate a Flickering with Expressions 00:18:00 Module: 19 19.1 Conclusion 00:01:00

Home Decoration, Home Improvement and Gardening Course
By iStudy UK
Innovative ways to Decorate your Home and surroundings Do you want to make your house and garden look the best they possibly can? Do you feel like your home is in need of a revamp? Then you are in luck! This course will show you how you can improve your daily surrounding by giving it touch of the artist inside of you. Your garden is just lying there without being fully utilized but it is upto to you to bring out its beauty. Work as a professional horticulturist at any professional level. It takes you step by step through common vegetables and fruits for backyard gardeners. As for your home, you will learn new ways to make your house stand out. Get with the modern decorating trend and make people gasp. With this course you can even kickstart your career as an interior decorator. During this course you will have to complete multiple units all designed to improve your knowledge on house decoration and how to improve your surroundings as well as ways to bring out the beauty of your garden. Course Highlights Home Decoration, Home Improvement and Gardening Course is an award winning and the best selling course that has been given the CPD Certification & IAO accreditation. It is the most suitable course anyone looking to work in this or relevant sector. It is considered one of the perfect courses in the UK that can help students/learners to get familiar with the topic and gain necessary skills to perform well in this field. We have packed Home Decoration, Home Improvement and Gardening Course into 85 modules for teaching you everything you need to become successful in this profession. To provide you ease of access, this course is designed for both part-time and full-time students. You can become accredited in just 2 days, 14 hours hours and it is also possible to study at your own pace. We have experienced tutors who will help you throughout the comprehensive syllabus of this course and answer all your queries through email. For further clarification, you will be able to recognize your qualification by checking the validity from our dedicated website. Why You Should Choose Home Decoration, Home Improvement and Gardening Course Lifetime access to the course No hidden fees or exam charges CPD Accredited certification on successful completion Full Tutor support on weekdays (Monday - Friday) Efficient exam system, assessment and instant results Download Printable PDF certificate immediately after completion Obtain the original print copy of your certificate, dispatch the next working day for as little as £9. Improve your chance of gaining professional skills and better earning potential. Who is this Course for? Home Decoration, Home Improvement and Gardening Course is CPD certified and IAO accredited. This makes it perfect for anyone trying to learn potential professional skills. As there is no experience and qualification required for this course, it is available for all students from any academic backgrounds. Requirements Our Home Decoration, Home Improvement and Gardening Course is fully compatible with any kind of device. Whether you are using Windows computer, Mac, smartphones or tablets, you will get the same experience while learning. Besides that, you will be able to access the course with any kind of internet connection from anywhere at any time without any kind of limitation. Career Path You will be ready to enter the relevant job market after completing this course. You will be able to gain necessary knowledge and skills required to succeed in this sector. All our Diplomas' are CPD and IAO accredited so you will be able to stand out in the crowd by adding our qualifications to your CV and Resume. Module 1: Home Decorating HOW TO REARRANGE A ROOM FREE 02:00:00 HOW TO ANALYZE A ROOM AS PROFESSIONALS DO BEFORE YOU FREE 01:00:00 HOW TO CREATE A ROOM 02:00:00 HOW TO DETERMINE CHARACTERS OF HANGINGS AND FURNITURES-COVERING FOR A GIVEN ROOM 01:00:00 CANDLESTICKS, LAMPS, FIXTURES FOR GAS AND ELECTRICITY, AND SHADES 01:00:00 WINDOW SHADES AND AWNINGS 00:30:00 TREATMENT OF PICTURES AND PICTURE FRAMES 01:00:00 TREATMENT OF PIANO CASES 00:15:00 TREATMENT OF DINING-ROOM BUFFETS AND DRESSING-TABLES 00:15:00 TREATMENT OF WORK TABLES, BIRD CAGES, DOG BASKETS AND FISH GLOBES 00:30:00 TREATMENT OF FIREPLACES 00:30:00 TREATMENT OF BATHROOMS 01:00:00 PERIOD ROOMS 01:00:00 PERIODS IN FURNITURE 01:00:00 CONTINUATION OF PERIODS IN FURNITURE 01:00:00 THE GOTHIC PERIOD 00:30:00 THE RENAISSANCE 01:00:00 FRENCH FURNITURE 01:00:00 THE PERIODS OF THE THREE LOUIS 01:00:00 THE MAHOGANY PERIOD 02:00:00 THE COLONIAL PERIOD 00:30:00 THE REVIVAL OF DIRECTOIRE AND EMPIRE FURNITURE 00:30:00 THE VICTORIAN PERIOD 00:30:00 PAINTED FURNITURE 00:30:00 TREATMENT OF AN INEXPENSIVE BEDROOM 01:00:00 TREATMENT OF A GUEST ROOM (Where economy is not an item of importance) 01:00:00 A MODERN HOUSE IN WHICH GENUINE JACOBEAN FURNITURE IS APPROPRIATELY SET 00:30:00 UNCONVENTIONAL BREAKFAST-ROOMS AND SPORTS BALCONIES 01:00:00 SUN-ROOMS 01:00:00 TREATMENT OF A WOMAN'S DRESSING-ROOM 00:30:00 THE TREATMENT OF CLOSETS 00:30:00 TREATMENT OF A NARROW HALL 00:15:00 TREATMENT OF A VERY SHADED LIVING-ROOM 00:15:00 SERVANTS' ROOMS 00:15:00 THE BABY'S ROOMS: THE DAY ROOM, THE NIGHT ROOM 01:00:00 ROOMS FOR THE ELDERLY 01:00:00 A YOUNG GIRL'S ROOM 01:00:00 THE YOUNG BOY'S ROOM 00:30:00 TABLE DECORATION 01:00:00 WHAT TO AVOID IN INTERIOR DECORATION: RULES FOR BEGINNERS 01:00:00 FADS IN COLLECTING 01:00:00 WEDGWOOD POTTERY; OLD AND MODERN 01:00:00 ITALIAN POTTERY 00:15:00 VENETIAN GLASS, OLD AND MODERN 00:30:00 CONCLUSION 00:15:00 Module 2: Home Improvement Choosing A Contractor FREE 01:00:00 Pollution and Remodeling FREE 00:30:00 Do It Yourself Bathroom Remodeling 00:30:00 Tips for Installing Leak-proof Showers 00:30:00 Do It Yourself Kitchen Remodeling 00:30:00 Installing Kitchen Cabinets 00:30:00 Choosing Countertops 00:30:00 Adding A Bedroom 00:30:00 Basement Problems Turned Around 00:30:00 Options for Lighting Your Home 00:30:00 How To Lay Indoor-Outdoor Carpet 00:30:00 Tips for Installing A Tile Floor 00:30:00 How To Prepare to Install Moulding 01:00:00 TV Stand Design Ideas 00:30:00 Home Air Conditioning Maintenance Made Easy 01:00:00 How To Diagnose Central Heating Systems 00:30:00 Insulation 00:30:00 Fixing Your Sink 00:30:00 Fixing Clogged Pipes and Drains 00:30:00 Replacing Screens 00:30:00 Replacing Doors 01:00:00 Six Tips For Decks Built to Last 00:30:00 Three Steps To Refinish Your Decks 00:30:00 Installing Your Hot Tub 00:30:00 Low Hassle Exterior Painting 00:30:00 Low Hassle Roof Repair 00:30:00 Gardens for Profit and Beauty 01:00:00 Judging Construction - Ground and Walls 00:30:00 Judging Construction - Ground and Walls 00:30:00 Choosing An Alarm System, Hardware AND People 00:30:00 Module 3: Gardening Organic Gardening Basics FREE 00:30:00 Having a Plan FREE 00:30:00 Having the Right Tools 01:00:00 Making your Own Mulch 01:00:00 Natural Pest Control 00:30:00 Organic Fertilizer 01:00:00 Planting 01:00:00 Harvesting 01:00:00 What to Avoid 01:00:00 Benefits of Organic Gardening 01:00:00 Mock Exam Final Exam

Accredited Diploma in Wedding Photography
By iStudy UK
A wedding is a heavenly thing. Everyone wants to capture the divine moment nicely. The Accredited Diploma in Wedding Photography course is designed for the people who want to be a qualified Wedding Photographer. Wedding Photography is a very demanding job nowadays. If you want to be a wedding photographer or want to start a full-time wedding photography business, the course is designed for you. The course teaches the secrets of capturing excellent wedding photos. The course guides you to shoot at a wedding timely, confidently, and professionally. The course also helps you to plan and prepare for the big day. You will learn about camera and flash settings. The course shows you how to deal with low light and tricky situations, Upon completion, you will be able to start successful Wedding Photography business anywhere in the world. What Will I Learn? Managing the day What equipment to use and how to use it Posing large and small groups Photographing the bride Photographing the groom Lighting effects Requirements All Internet browsers, including Internet Explorer, Safari, Chrome, and Firefox Module: 01 01. Introduction ##01 What is this Course all about-sanj FREE 00:01:00 01. Introduction ##02 Who am I FREE 00:01:00 01. Introduction ##03 Top 5 Tips for Better Wedding Photos FREE 00:03:00 01. Introduction ##04 Why should you Become a Wedding photographer FREE 00:02:00 01. Introduction ##05 How to Succeed with this course FREE 00:01:00 01. Introduction ##06 Live Posing Session 00:13:00 01. Introduction ##07 What is this course all about 00:01:00 Module: 02 02. Setting Up Your Business ##01 Section Intro 00:01:00 02. Setting Up your Business ##02 What Type of Wedding Photographer are you 00:03:00 02. Setting Up Your Business ##03 Equipment You Need toGet Started 00:05:00 02. Setting Up Your Business ##04 What Camera Brand is Best 00:02:00 02. Setting Up Your Business ##05 Where Should you buy Camera equipment 00:01:00 02. Setting Up Your Business ##06 Picking a Name for Your Company 00:03:00 02 Setting Up Your Business ##07 Launching a Website - Top Tips for a Successful Site 00:04:00 02. Setting Up Your Business ##08 Action Item-Pick a Name & Build a Website 00:01:00 02. Setting Up Your Business ##09 Creating Wedding Photography Packages 00:05:00 02. Setting Up Your Busines ##10 Pricing for Success 00:09:00 02. Setting Up Your Busines ##11 How to Get Your First Client 00:04:00 02. Setting Up Your Busines ##12 The Importance of Contracts 00:03:00 02. Setting Up Your Busines ##13 The Wedding Photography 00:02:00 02. Setting Up Your Busines ##15 Recap - Setting up your business 00:02:00 Module: 03 03. Wedding Day Overview ##01 Section Intro 00:01:00 03. Wedding Day Overview ##02 Taking Care of Business on the Wedding Day 00:02:00 03. Wedding Day Overview ##03 Overview of What to Photograph 00:12:00 03. Wedding Day Overview ##04 Using Pinterest to find Inspirational Photos 00:02:00 03. Wedding Day Overview ##05 Recap of Wedding Overview 00:01:00 Module: 04 04. How to Shoot a Wedding ##01 Section Intro 00:03:00 04. How to Shoot a Wedding ##02 Wedding Day Equipment Check 00:05:00 04. How to Shoot a Wedding ##03 Wedding Day Consideration-Day-Night-Indoor-Outdoor 00:03:00 04. How to Shoot a Wedding ##04 Do You Need an Assistant or Second Shooter 00:04:00 04. How to Shoot a Wedding ##05 How Much to Pay a second Shooter 00:01:00 04. How to Shoot a Wedding ##06 Scheduling the Wedding Day (First, Looks, Candide, Posed Family Shits) 00:02:00 04. How to Shoot a Wedding ##07 Achieving Your Look 00:01:00 04. How to Shoot a Wedding ##08 Details 00:05:00 04. How to Shoot a Wedding ##09 Groom Preparation 00:09:00 04. How to Shoot a Wedding ##10 Bride Preparation 00:11:00 04. How to Shoot a Wedding ##11 Walking Down the Aisle 00:04:00 04. How to Shoot a Wedding ##12 Ceremony Coverage 00:12:00 04. How to Shoot a Wedding ##13 Readers 00:03:00 04. How to Shoot a Wedding ##14 Rings, Vows,Kiss 00:03:00 04. How to Shoot a Wedding ##15 Post-Ceremony 00:05:00 04. How to Shoot a Wedding ##16 How to Shoot Family Shots 00:08:00 04. How to Shoot a Wedding ##17 Posed Couple Shots 00:13:00 04. How to Shoot a Wedding ##18 Grand Entrance 00:01:00 04. How to Shoot a Wedding ##19 Reception Details 00:06:00 04. How to Shoot a Wedding ##20 Toast and Speeches 00:06:00 04. How to Shoot a Wedding ##21 Cake Cutting 00:03:00 04. How to Shoot a Wedding ##22 First Dance 00:06:00 04. How to Shoot a Wedding ##23 Bouquet Garter Toss 00:03:00 04. How to Shoot a Wedding ##24 Dance Party 00:06:00 04. How to Shoot a Wedding ##25 Recap - How to Shoot a Wedding 00:01:00 Module: 05 05. Editing Wedding Photos ##01 section Intro 00:01:00 05. Editing Wedding Photos ##02 Choosing an Editing App 00:02:00 05. Editing Wedding Photos ##03 Editing in Lightroom 00:10:00 05. Editing Wedding Photos ##04 Exporting from Lightroom 00:05:00 05. Editing Wedding Photos ##05 Editing in Photoshop 00:11:00 05. Editing Wedding Photos ##06 Creating Online Galleries 00:06:00 05. Editing Wedding Photos ##07 Recap of Editing Section 00:01:00 Module: 06 06. Succeeding Wedding Photography ##01 Section Intro 00:01:00 06. Succeeding Wedding Photography ##02 Being Happy - Tips from a Wedding Photographer 00:01:00 06. Succeeding Wedding Photography ##03 Making it a Business and Sticking to it 00:02:00 06. Succeeding Wedding Photography ##04 Building Out Your Portfolio 00:01:00 06. Succeeding Wedding Photography ##05 Dealing With Saturated Photography Markets 00:02:00 06. Succeeding Wedding Photography ##06 Competing With Family Photographers for Jobs 00:01:00 06. Succeeding Wedding Photography ##07 Working With Other Vendors for Success 00:01:00 06. Succeeding Wedding Photography ##08 Using Social Networks to Expand Your Business 00:02:00 06. Succeeding Wedding Photography ##09 Testimonials - Yelp, Wedding Wire, The Knot 00:02:00 06. Succeeding Wedding Photography ##10 Recap Succeeding With Wedding Photography 00:01:00 Module: 07 07. Wrap Up ##01 Thank You and What's Next 00:01:00 Module: 08 08. Bonus Engagement Photography ##01 Section Intro 00:01:00 08. Bonus Engagement Photography ##02 Equipment Check for the Engagement Photo Session 00:01:00 08. Bonus Engagement Photography ##03 How Much To Charge for an engagement Session 00:01:00 08. Bonus Engagement Photography ##04 Picking the Perfect Location for Engagement Photos 00:02:00 08. Bonus Engagement Photography ##05 Tips for Posing and Interacting with Clients for engagement Photos 00:01:00 08. Bonus Engagement Photography ##06 Engagement Photo Review 00:07:00 08. Bonus Engagement Photography ##07 Bonus Engagement Recap 00:01:00 How to Use Pinterest to Find Great Wedding Poses 00:02:00 How-to-Register-a-Domain-Name-with-Godaddy-with-a-Promo-Code 00:04:00 Course Certification

Complete Online Photography Course For Beginner: A to Z
By Lead Academy
Quality Guarantee: Promising training excellence, satisfaction gurantee Accredited by CPD UK & Quality License Scheme Tutor Support Unlimited support via email, till you complete the course Recognised Certification: Accepted by thousands of professional bodies Start Anytime With 1 year access to the course materials Online Learning Learn from anywhere, whenever you want This course provides complete guidelines for learning photography as beginners. From the fundamentals of photography to lighting techniques, and camera settings, this course covers it all. With expert guidance, you will be able to transform your images into stunning works of art. This course at a glance Accredited by CPD UK Endorsed by Quality Licence Scheme Master the photography materials, equipment, and processes of the discipline - use of cameras, film, lightning, and printing (wet, hybrid, and digital) Get to know about the photographic history and theory, the relationship of photography to the visual disciplines, and the cultural influence Develop skills to use digital photography tools and the internet, such as emailing and posting to a website Learn how to work in experimental and manipulative techniques and gain knowledge about candid imagery, documentary photography, and interpretive studies Understand the advanced digital and analogue camera operations such as formats, photographic exposure, depth of field, and shutter speed Ability to control both natural and studio lighting with emphasis on the quality, quantity, and direction of light Learn how to plan, organize, edit, and evaluate a professional quality portfolio of photographic work Why Complete Photography Course right for you? The comprehensive online course will give you an overview of camera settings to understand technical concepts such as the ISO setting and what it's used for, exposure compensation, and why there is a need to darken or lighten your images. You will also learn about lens apertures and basic camera settings. This online course will help you know how to use the exposure triangle and how to use the exposure feature and get out of the auto mode. You will develop a solid understanding of improving images with natural lighting and using better compositions. By the end of the course, you will have a theoretical knowledge of basic and advanced camera settings, tips on posing for portraits, flash photography, and much more. Complete Photography Course Details Accredited by CPD certificates are accepted by thousands of professional bodies and government regulators here in the UK and around the world. Many organisations look for employees with CPD requirements, which means, that by doing this course, you would be a potential candidate in your respective field. The Quality Licence Scheme is a brand of the Skills and Education Group, a leading national awarding organisation for providing high-quality vocational qualifications across a wide range of industries. Course Curriculum Beginner Camera Setting (Important Info Used In Subsequent Lectures) Use The Exposure Triangle to Understand Exposure and Get Out of The Auto Mode The ISO setting, What is It and What's It for? Exposure Compensation, Why You Sometimes Need to Darken or Lighten Your Images Lens Apertures, Learn About One of The Most Important Camera Settings More Advanced Camera Setting 5 Tips for Tack Sharp Focussing Use Your Histogram to Nail the Exposure for Those Important Images. Aperture & Depth of Field - Start Getting Creative (DSLRs) Scene Modes & Depth of Field (Compact Cameras) Improve Your Image with Natural Lighting Direction of Light and The Effect It has on Your Photos Get Nice Blue Skies in Your Photos and Avoid White Skies Better Indoor Portraits Using Window Light - pt 1 of 2 Better Indoor Portraits Using Window Light - pt 2 of 2 Create a Great Look Using Backlighting How to Improve Your Natural Light Portraits Using a Reflector Improve Your Image Using Better Composition Use the Rule of Thirds for Improved Composition Better Composition Using Diagonal Lines Use 'Leading Lines' to Create More Dramatic Images Use Repeating Patterns for More Impact Improve Your Composition Using the 'Frame within a Frame' Trick Blur the Background for More Impact (DSLRs) Blur the Background to Isolate your Subject (Compact Cameras) Don't Let Cluttered Backgrounds Ruin Your Portraits Improve Your Portraits Using Nature's Own Abstract Backgrounds Tips on Posing for Portraits Flatter Your Individual Subject with These Full Length Posing Tips Family or Small Group Poses - Pt I Standing Poses Family or Small Group Poses - Pt II Seated Poses Individual Natural and Relaxed Female Poses Ideas for Photographing Children, 4-6 Months Old Ideas for Photographing Children, 9-12 Months Old Lanscapes and Scenery Landscape Photography Tips, a Walkthough with Barbara How to Take Better Photos in The Snow Flash Photography Better Results Using an External Flashgun, PT I - Bouncing The Flash Better Flash Portraits Using an External Flashgun, PT II - More Creative Portraits Better Results Using Your Cameras' Built-in Flash - Soften The Shadows Better Results Using on-Board Flash - Get a More Pleasing Background Information and Tips on Using Lenses General Tips on Camera Lenses, Variable/Fixed Apertures, Fast/Slow, What are Prime Lenses? Lens Focal Length, Pt I - Perspective Lens Focal Length, Pt II - 'Field of View' Lens Focal Length, Pt III - 'Depth of Field' Other General Techniques A Neat Idea for a Fun, Dramatic Portrait How the 'Half Press of The Shutter' Technique Can Improve Your Picture Taking How to Easily Create a Stunning Online Slide Show in Minutes How to Take Photos of Fireworks How to Take a Really Flattering Profile or PR Photo Take a More Flattering PR or Profile Photo - Basic Technique Using Using 'Top Shade' Take a More Flattering Profile or PR Photo - Refining The Basic Profile or PR Image Which Digital Camera to Buy Next, Megapixels is Not The Answer. The Myth of Megapixels - Image Resolution and Quality Which Camera Should I Buy Next - There's So Many to Choose from! Who should take this course? This online photography course for beginners: A to Z is suitable for those who want to gain skills and knowledge in becoming a digital photographer, anyone who wants to update their technical expertise on digital photography. This course is ideal for those who want to take their photography skills to an advanced level. Entry Requirements There are no academic entry requirements for this professional photography online course, and it is open to students of all academic backgrounds. However, you are required to have a laptop/desktop/tablet or smartphone and a good internet connection. Assessment Method This online photography course for beginners: a to z assesses learners through multiple-choice questions (MCQs). Upon successful completion of the modules, learners must answer MCQs to complete the assessment procedure. Through the MCQs, it is measured how much a learner could grasp from each section. In the assessment pass mark is 60%. Certification Endorsed Certificate from Quality Licence Scheme After successfully passing the MCQ exam you will be eligible to order the Endorsed Certificate by Quality Licence Scheme. The Quality Licence Scheme is a brand of the Skills and Education Group, a leading national awarding organisation for providing high-quality vocational qualifications across a wide range of industries. It will give you a competitive advantage in your career, making you stand out from all other applicants and employees. There is a Quality Licence Scheme endorsement fee to obtain an endorsed certificate which is £65. Certificate of Achievement from Lead Academy After successfully passing the MCQ exam you will be eligible to order your certificate of achievement as proof of your new skill. The certificate of achievement is an official credential that confirms that you successfully finished a course with Lead Academy. Certificate can be obtained in PDF version at a cost of £12, and there is an additional fee to obtain a printed copy certificate which is £35. FAQs Is CPD a recognised qualification in the UK? CPD is globally recognised by employers, professional organisations and academic intuitions, thus a certificate from CPD Certification Service creates value towards your professional goal and achievement. CPD-certified certificates are accepted by thousands of professional bodies and government regulators here in the UK and around the world. Are QLS courses recognised? Although QLS courses are not subject to Ofqual regulation, they must adhere to an extremely high level that is set and regulated independently across the globe. A course that has been approved by the Quality Licence Scheme simply indicates that it has been examined and evaluated in terms of quality and fulfils the predetermined quality standards. When will I receive my certificate? For CPD accredited PDF certificate it will take 24 hours, however for the hardcopy CPD certificate takes 5-7 business days and for the Quality License Scheme certificate it will take 7-9 business days. Can I pay by invoice? Yes, you can pay via Invoice or Purchase Order, please contact us at info@lead-academy.org for invoice payment. Can I pay via instalment? Yes, you can pay via instalments at checkout. How to take online classes from home? Our platform provides easy and comfortable access for all learners; all you need is a stable internet connection and a device such as a laptop, desktop PC, tablet, or mobile phone. The learning site is accessible 24/7, allowing you to take the course at your own pace while relaxing in the privacy of your home or workplace. Does age matter in online learning? No, there is no age limit for online learning. Online learning is accessible to people of all ages and requires no age-specific criteria to pursue a course of interest. As opposed to degrees pursued at university, online courses are designed to break the barriers of age limitation that aim to limit the learner's ability to learn new things, diversify their skills, and expand their horizons. When I will get the login details for my course? After successfully purchasing the course, you will receive an email within 24 hours with the login details of your course. Kindly check your inbox, junk or spam folder, or you can contact our client success team via info@lead-academy.org

Extended Diploma in Interior Design
By iStudy UK
Interior design will help you showcase your artistic talents in arts and designing. If you are someone who wants to venture in the interior designing industry, then this course will be perfect for you. You will learn how to build your career as an interior designer. Explore how interior decorating is an enjoyable job that would give you opportunities. A lot of people want always to have a beautiful and presentable interior of their place. Enroll in this course and unleash your hidden talents in art. Course Highlights Extended Diploma in Interior Design is an award winning and the best selling course that has been given the CPD Certification & IAO accreditation. It is the most suitable course anyone looking to work in this or relevant sector. It is considered one of the perfect courses in the UK that can help students/learners to get familiar with the topic and gain necessary skills to perform well in this field. We have packed Extended Diploma in Interior Design into 89 modules for teaching you everything you need to become successful in this profession. To provide you ease of access, this course is designed for both part-time and full-time students. You can become accredited in just 2 days, 18 hours and it is also possible to study at your own pace. We have experienced tutors who will help you throughout the comprehensive syllabus of this course and answer all your queries through email. For further clarification, you will be able to recognize your qualification by checking the validity from our dedicated website. Why You Should Choose Extended Diploma in Interior Design Lifetime access to the course No hidden fees or exam charges CPD Accredited certification on successful completion Full Tutor support on weekdays (Monday - Friday) Efficient exam system, assessment and instant results Download Printable PDF certificate immediately after completion Obtain the original print copy of your certificate, dispatch the next working day for as little as £9. Improve your chance of gaining professional skills and better earning potential. Who is this Course for? Extended Diploma in Interior Design is CPD certified and IAO accredited. This makes it perfect for anyone trying to learn potential professional skills. As there is no experience and qualification required for this course, it is available for all students from any academic backgrounds. Requirements Our Extended Diploma in Interior Design is fully compatible with any kind of device. Whether you are using Windows computer, Mac, smartphones or tablets, you will get the same experience while learning. Besides that, you will be able to access the course with any kind of internet connection from anywhere at any time without any kind of limitation. Career Path You will be ready to enter the relevant job market after completing this course. You will be able to gain necessary knowledge and skills required to succeed in this sector. All our Diplomas' are CPD and IAO accredited so you will be able to stand out in the crowd by adding our qualifications to your CV and Resume. Extended Diploma in Interior Design - Updated Version Introduction to Interior Design 00:24:00 Design Principle 00:22:00 Design Elements 00:24:00 Design Elements Practical Components 00:29:00 Room by Room Design 00:22:00 Popular Interior Designs 00:20:00 Sustainable Design 00:15:00 Presenting Your Ideas 00:17:00 Managing Interior Design Business 00:22:00 Project Overview 00:30:00 Extended Diploma in Interior Design - Old Version Interior Design Fundamentals Define a Theme: Contemporary, Cottage, Eclectic, Southwest FREE 01:00:00 Budget Design for Your Living Room, Den or Family Room 01:00:00 Budget Ideas for Kitchen Design 01:00:00 Budget Bedroom Makeover 01:00:00 Closet Cleanups 01:00:00 Need a Home Office? 00:30:00 Camouflage with Paint! 01:00:00 Faux Finishes Are Hot - Bare Walls Are Not! 00:30:00 Window Treatments 01:00:00 Making the Most of Molding 00:30:00 Fabulous Furniture Finds 00:30:00 Decorate With Wallpaper 01:00:00 Freehand or Stencil A Mural Makes the Wall! 01:00:00 Accessorize - Funky Can Be Fun! 01:00:00 Have Some Fun with Fabric! 01:00:00 Interior Decorating Basics HOW TO REARRANGE A ROOM FREE 02:00:00 HOW TO ANALYZE A ROOM AS PROFESSIONALS DO BEFORE YOU FREE 01:00:00 HOW TO CREATE A ROOM 02:00:00 HOW TO DETERMINE CHARACTERS OF HANGINGS AND FURNITURES-COVERING FOR A GIVEN ROOM 01:00:00 CANDLESTICKS, LAMPS, FIXTURES FOR GAS AND ELECTRICITY, AND SHADES 01:00:00 WINDOW SHADES AND AWNINGS 00:30:00 TREATMENT OF PICTURES AND PICTURE FRAMES 01:00:00 TREATMENT OF PIANO CASES 00:15:00 TREATMENT OF DINING-ROOM BUFFETS AND DRESSING-TABLES 00:15:00 TREATMENT OF WORK TABLES, BIRD CAGES, DOG BASKETS AND FISH GLOBES 00:30:00 TREATMENT OF FIREPLACES 00:30:00 TREATMENT OF BATHROOMS 01:00:00 PERIOD ROOMS 01:00:00 PERIODS IN FURNITURE 01:00:00 CONTINUATION OF PERIODS IN FURNITURE 01:00:00 THE GOTHIC PERIOD 00:30:00 THE RENAISSANCE 01:00:00 FRENCH FURNITURE 01:00:00 THE PERIODS OF THE THREE LOUIS 01:00:00 THE MAHOGANY PERIOD 02:00:00 THE COLONIAL PERIOD 00:30:00 THE REVIVAL OF DIRECTOIRE AND EMPIRE FURNITURE 00:30:00 THE VICTORIAN PERIOD 00:30:00 PAINTED FURNITURE 00:30:00 TREATMENT OF AN INEXPENSIVE BEDROOM 01:00:00 TREATMENT OF A GUEST ROOM (Where economy is not an item of importance) 01:00:00 A MODERN HOUSE IN WHICH GENUINE JACOBEAN FURNITURE IS APPROPRIATELY SET 00:30:00 UNCONVENTIONAL BREAKFAST-ROOMS AND SPORTS BALCONIES 01:00:00 SUN-ROOMS 01:00:00 TREATMENT OF A WOMAN'S DRESSING-ROOM 00:30:00 THE TREATMENT OF CLOSETS 00:30:00 TREATMENT OF A NARROW HALL 00:15:00 TREATMENT OF A VERY SHADED LIVING-ROOM 00:15:00 SERVANTS' ROOMS 00:15:00 THE BABY'S ROOMS: THE DAY ROOM, THE NIGHT ROOM 01:00:00 ROOMS FOR THE ELDERLY 01:00:00 A YOUNG GIRL'S ROOM 01:00:00 THE YOUNG BOY'S ROOM 00:30:00 TABLE DECORATION 01:00:00 WHAT TO AVOID IN INTERIOR DECORATION: RULES FOR BEGINNERS 01:00:00 FADS IN COLLECTING 01:00:00 WEDGWOOD POTTERY; OLD AND MODERN 01:00:00 ITALIAN POTTERY 00:15:00 VENETIAN GLASS, OLD AND MODERN 00:30:00 CONCLUSION 00:15:00 Interior Design INTRODUCTION 00:30:00 DO'S AND DON'TS OF DECORATING 01:00:00 GETTING IDEAS 00:15:00 ELEMENTS OF DESIGN 01:00:00 ORGANIZE YOUR IDEAS 01:00:00 DECORATING ON A BUDGET 01:30:00 MINIMALIST STYLE 01:00:00 CASUAL STYLE 00:30:00 FORMAL STYLE 00:30:00 SHABBY CHIC STYLE 00:30:00 PARIS APARTMENT STYLE 00:30:00 FRENCH COUNTRY STYLE 00:30:00 TROPICAL CHIC STYLE 00:30:00 LODGE STYLE 00:30:00 USING WHAT YOU'VE GOT 00:30:00 DECORATING IN A DAY 00:30:00 CHOOSING ART 01:00:00 CONCLUSION 00:15:00 Illustrations Illustrations 00:00:00 Mock Exam Mock Exam- Extended Diploma in Interior Design 00:30:00 Final Exam Final Exam- Extended Diploma in Interior Design 00:30:00
Course Overview The demand for iOS apps is increasing every day. If you want to build your career as an app developer or programmer, learning iOS app development will be a smart choice for you. Learn how to create iOS apps using Swift 5 from this Build your first iOS 14 apps using swift 5 course and take your first step to be a pro developer. This course will help you understand Swift coding and solve your problems with app development. In this Build your first iOS 14 apps using swift 5 course, you will learn about the functions of Swift programming, variables and types, operations, collections, flow control, classes and inheritance. You will be able to create your first iOS app using swift 5 and enhance your skill to start your career as an iOS app developer. This course will help you understand the app development process step by step with easily understandable bite-sized lessons. Learning Outcomes Get a clear understanding of the fundamentals of iOS and Swift development Learn iOS development programming from scratch Be able to operate Swift 5 Learn the functions of Swift 5 Learn what you should consider before making an iOS app Gain the skills to be an efficient app developer Who is this course for? This course is designed for you to learn how to design iOS applications using swift 5. Anyone interested in app development can learn effective app development skills from this course Entry Requirement This course is available to all learners, of all academic backgrounds. Learners should be aged 16 or over to undertake the qualification. Good understanding of English language, numeracy and ICT are required to attend this course. Certification After you have successfully completed the course, you will be able to obtain an Accredited Certificate of Achievement. You can however also obtain a Course Completion Certificate following the course completion without sitting for the test. Certificates can be obtained either in hardcopy at the cost of £39 or in PDF format at the cost of £24. PDF certificate's turnaround time is 24 hours, and for the hardcopy certificate, it is 3-9 working days. Why choose us? Affordable, engaging & high-quality e-learning study materials; Tutorial videos/materials from the industry-leading experts; Study in a user-friendly, advanced online learning platform; Efficient exam systems for the assessment and instant result; The UK & internationally recognized accredited qualification; Access to course content on mobile, tablet or desktop from anywhere anytime; The benefit of career advancement opportunities; 24/7 student support via email. Career Path Build your first iOS 14 apps using swift 5 is a useful qualification to possess and would be beneficial for any related profession or industry such as: Ios Developers Programmers Designers Unit 01: Introduction Module 01: Setup 00:02:00 Module 01: A Quick Reminder 00:01:00 Unit 02: Variables and Types in Swift Programming Module 01: Variables Strings and Constants in Swift 00:08:00 Module 02: Solution - Variables Strings and Constants in Swift 00:01:00 Module 03: Variables and Numbers in Swift 00:07:00 Module 04: Solution - Variables and Numbers in Swift 00:01:00 Module 05: Type conversions in Swift - Danger Will Robinson 00:05:00 Module 06: Solution - Type conversions in Swift - Danger Will Robinson 00:02:00 Module 07: Tuple Types in Swift 00:05:00 Module 08: Solution - Tuple Types in Swift 00:02:00 Unit 03: Optionals in Swift and the Null Problem Module 01: Optionals Nulls and Variables in Swift 00:05:00 Module 02: Solution - Optionals Nulls and Variables in Swift 00:01:00 Unit 04: Operators in Swift Module 01: Operators in Swift - Assignment Arithmetic and Concatenation 00:04:00 Module 02: Solution - Operators in Swift - Assignment Arithmetic and Concatenation 00:01:00 Module 03: Operators in Swift - Unary Compound Logic and Comparison 00:04:00 Unit 05: Collections in Swift Module 01: Collections in Swift - Arrays 00:05:00 Module 02: Solution - Collections in Swift - Arrays 00:02:00 Module 03: Collections in Swift - Sets 00:06:00 Module 04: Collections in Swift - Dictionaries 00:05:00 Module 05: Solution - Collections in Swift - Dictionaries 00:03:00 Unit 06: Flow Control in Swift Module 01: Controlling Flow in Swift - for in loops 00:08:00 Module 02: Solution - Controlling Flow in Swift - for in loops 00:03:00 Module 03: Controlling Flow in Swift - While loops 00:04:00 Module 04: Solution - Controlling Flow in Swift - While loops 00:02:00 Unit 07: Conditional Statements in Swift Module 01: Conditional Statements in Swift - If Else 00:04:00 Module 02: Solution - Conditional Statements in Swift - If Else 00:02:00 Module 03: Conditional Statements in Swift - Switch Case 00:04:00 Module 04: Solution - Conditional Statements in Swift - Switch Case 00:02:00 Unit 08: Control Transfer in Swift Module 01: Control Transfer in Swift - continue break fallthrough return throw 00:06:00 Unit 09: Functions in Swift Module 01: Functions in Swift 00:10:00 Module 02: Solution - Functions in Swift 00:03:00 Module 03: Nested Functions in Swift 00:04:00 Module 04: Solution - Nested Functions in Swift 00:03:00 Unit 10: Enumerations in Swift Module 01: Enumerations in Swift 00:05:00 Module 02: Solution - Enumerations in Swift 00:01:00 Unit 11: Classes and Inheritance in Swift Module 01: Classes in Swift 00:05:00 Module 02: Solution 1 - Classes in Swift 00:02:00 Module 03: Solution 2 - Classes in Swift 00:02:00 Module 04: Inheritance in Swift 00:07:00 Module 05: Solution - Inheritance in Swift 00:04:00 Unit 12: Your First iOS App Module 01: Your First iOS App and Familiarisation 00:05:00 Module 02: The Key iOS Project Files 00:06:00 Module 03: How to Implement a Button in the User Interface 00:05:00 Module 04: How to Connect a Button to Code in Xcode 00:05:00 Module 05: Writing Code to Change a Views Appearance and a TASK 00:02:00 Module 06: Solution to the Task and If Else View Colors 00:07:00 Unit 13: Temperature Conversion App - iOS Layouts Positioning and Buttons Module 01: A Preview of the App We Will Build 00:01:00 Module 02: Create the App and Its User Interface 00:02:00 Module 03: iOS Layouts and Positioning 00:10:00 Module 04: Connecting UI Elements to Code 00:05:00 Module 05: Converting Temperature via Button Click 00:06:00 Module 06: Adding a Bit of Excellence to the UI and a Task for You 00:06:00 Module 07: Task Solution - Adding a Conversions Counter Label 00:07:00 Unit 14: Gods App - Navigation Table Views and Data Passing Module 01: What we are Building 00:02:00 Module 02: Creating the GreekGod Data Model 00:06:00 Module 03: Navigation Controllers in iOS 00:06:00 Module 04: Creating Fake Gods 00:04:00 Module 05: How to Set Up a Table View and Its Controller 00:11:00 Module 06: Task Solution - How to Fix the Table View 00:04:00 Module 07: How to Navigate from Table View to New View in iOS 00:04:00 Module 08: Create a View Controller for the Detail View 00:03:00 Module 09: Passing Data from Table View to View Controller 00:04:00 Module 10: Setting up a Detail View Controller with Passed Data 00:11:00 Module 11: Using Images and ImageViews in Swift - And a Task 00:04:00 Module 12: Solution to the Task 00:04:00 Unit 15: Will I Burn App - Accessing APIs and Device Hardware - GPS Module 01: Preview of the App We Will Make 00:02:00 Module 02: Structures Instead of Classes 00:05:00 Module 03: How to Request Permissions and Capabilities in iOS 00:04:00 Module 04: Requesting User Permissions in iOS - Part 2 00:09:00 Module 05: Requesting User Permissions in iOS - Part 3 00:07:00 Module 06: Creating a SWEET User Interface 00:09:00 Module 07: Task - Connect the UI to Code 00:01:00 Module 08: Connecting User Interface to Code 00:02:00 Module 09: Action Sheet Alerts in iOS 00:05:00 Module 10: Update a Label and Thoughts on Storage 00:03:00 Module 11: User Defaults Storage in iOS 00:05:00 Module 12: Getting and Setting User Defaults in iOS 00:04:00 Module 13: Getting a Location in Latitude and Longitude in iOS Apps 00:04:00 Module 14: Selecting an API Provider for Your Apps 00:07:00 Module 15: Generating an API Key and Exploring the Docs 00:04:00 Module 16: Create an API Access Class in Swift 00:04:00 Module 17: Using Third Party Libraries in iOS - AlamoFire 00:06:00 Module 18: How to Use AlamoFire in iOS 00:08:00 Module 19: How to Extract JSON Data from an API Call 00:06:00 Module 20: Performing Background Calculations in iOS 00:06:00 Module 21: Performing Background Calculations in iOS - Part 2 00:07:00 Module 22: Activity Indicators in iOS and Swift 00:07:00 Module 23: Local Notifications in iOS 00:06:00 Module 24: Solution to the Task - UI Smoothing 00:05:00 Unit 16: Whatsapp Clone Using Google Firebase Module 01: Preview of What We're Building 00:03:00 Module 02: Should you Choose Firebase or Firestore 00:10:00 Module 03: Create a Firebase Application 00:03:00 Module 04: Installing Firebase in your iOS App 00:09:00 Module 05: Firebase Authentication Options 00:05:00 Module 06: Designing the Auth Screen 00:10:00 Module 07: Connecting UI to Code 00:04:00 Module 08: Showing the Auth Screen 00:11:00 Module 09: Validating User Input for Firebase Authentication 00:08:00 Module 10: Register a User in Firebase 00:05:00 Module 11: Logging in via Firebase 00:06:00 Module 12: Set Activity Indicator to Show Network Processing 00:07:00 Module 13: How to Reset a Firebase User Password 00:11:00 Module 14: How to Prevent Dismissal of a View Controller 00:02:00 Module 15: Setting up a Table View and Cell Manually 00:11:00 Module 16: Connecting a TableView and ViewController Manually 00:05:00 Module 17: Implementing TableView Functions in the ViewController 00:06:00 Module 18: Listening to Firebase Data Streams on iOS 00:09:00 Module 19: Demo with Dummy Data 00:03:00 Module 20: Using a TextField Delegate in iOS 00:03:00 Module 21: Sending Data from iOS to Firebase Database 00:05:00 Module 22: Well Done and a Couple HARD TASKS with NO SOLUTION 00:05:00 Certificate and Transcript Order Your Certificates and Transcripts 00:00:00

Certification in Windows 10 - Practical Hands-on Learning
By Study Plex
Highlights of the Course Course Type: Online Learning Duration: 1 to 2 hours Tutor Support: Tutor support is included Customer Support: 24/7 customer support is available Quality Training: The course is designed by an industry expert Recognised Credential: Recognised and Valuable Certification Completion Certificate: Free Course Completion Certificate Included Instalment: 3 Installment Plan on checkout What you will learn from this course? Gain comprehensive knowledge about Windows 10 Understand the core competencies and principles of Windows 10 Explore the various areas of Windows 10 Know how to apply the skills you acquired from this course in a real-life context Become a confident and expert Windows 10 user Certification in Windows 10 - Practical Hands-on Learning Course Master the skills you need to propel your career forward in Windows 10. This course will equip you with the essential knowledge and skillset that will make you a confident Windows 10 user and take your career to the next level. This comprehensive Windows 10 user course is designed to help you surpass your professional goals. The skills and knowledge that you will gain through studying this practical hands course will help you get one step closer to your professional aspirations and develop your skills for a rewarding career. This certification in windows 10 - practical hands-on learning course is endorsed by the Quality Licence Scheme for its high-quality, non-regulated provision and training programmes. The Quality Licence Scheme is a brand of the Skills and Education Group, a leading national awarding organisation for providing high-quality vocational qualifications across a wide range of industries. This comprehensive course will teach you the theory of effective Windows 10 practice and equip you with the essential skills, confidence and competence to assist you in the Windows 10 industry. You'll gain a solid understanding of the core competencies required to drive a successful career in Windows 10. This course is designed by industry experts, so you'll gain knowledge and skills based on the latest expertise and best practices. This extensive course is designed for Windows 10 user or for people who are aspiring to specialise in Windows 10.This certification in windows 10 - practical hands-on learning course has been endorsed by the Quality Licence Scheme for its high-quality, non-regulated provision and training programmes. This course is not regulated by Ofqual and is not an accredited qualification. Enrol in this practical hands course today and take the next step towards your personal and professional goals. Earn industry-recognised credentials to demonstrate your new skills and add extra value to your CV that will help you outshine other candidates. Who is this Course for? This comprehensive practical hands course is ideal for anyone wishing to boost their career profile or advance their career in this field by gaining a thorough understanding of the subject. Anyone willing to gain extensive knowledge on this Windows 10 can also take this course. Whether you are a complete beginner or an aspiring professional, this course will provide you with the necessary skills and professional competence, and open your doors to a wide number of professions within your chosen sector. Entry Requirements This practical hands course has no academic prerequisites and is open to students from all academic disciplines. You will, however, need a laptop, desktop, tablet, or smartphone, as well as a reliable internet connection. Assessment This practical hands course assesses learners through multiple-choice questions (MCQs). Upon successful completion of the modules, learners must answer MCQs to complete the assessment procedure. Through the MCQs, it is measured how much a learner could grasp from each section. In the assessment pass mark is 60%. Recognised Accreditation This course is accredited by continuing professional development (CPD). CPD UK is globally recognised by employers, professional organisations, and academic institutions, thus a certificate from CPD Certification Service creates value towards your professional goal and achievement. The Quality Licence Scheme is a brand of the Skills and Education Group, a leading national awarding organisation for providing high-quality vocational qualifications across a wide range of industries. What is CPD? Employers, professional organisations, and academic institutions all recognise CPD, therefore a credential from CPD Certification Service adds value to your professional goals and achievements. Benefits of CPD Improve your employment prospects Boost your job satisfaction Promotes career advancement Enhances your CV Provides you with a competitive edge in the job market Demonstrate your dedication Showcases your professional capabilities What is IPHM? The IPHM is an Accreditation Board that provides Training Providers with international and global accreditation. The Practitioners of Holistic Medicine (IPHM) accreditation is a guarantee of quality and skill. Benefits of IPHM It will help you establish a positive reputation in your chosen field You can join a network and community of successful therapists that are dedicated to providing excellent care to their client You can flaunt this accreditation in your CV It is a worldwide recognised accreditation What is Quality Licence Scheme? This course is endorsed by the Quality Licence Scheme for its high-quality, non-regulated provision and training programmes. The Quality Licence Scheme is a brand of the Skills and Education Group, a leading national awarding organisation for providing high-quality vocational qualifications across a wide range of industries. Benefits of Quality License Scheme Certificate is valuable Provides a competitive edge in your career It will make your CV stand out Course Curriculum Course Overview Video - Course Overview 00:05:00 Building Your Virtual Lab Environment Video - Downloading ISO and OVA Fles for VirtualBox 00:08:00 Video and Lab - Create Virtual Install of Server 2016 Full GUI Using VirtualBox 00:12:00 Video and Lab - Creating a Virtual Install of Windows 10 Pro Using VirtualBox 00:16:00 Video - Taking A Snapshot Of Your Current Configuration 00:04:00 Upgrading Windows 7,8,Or 8.1 to Windows 10 Video - Perform a Windows 10 Upgrade for Free 00:09:00 Building a Microsoft Server 2016 Domain Video and Lab - Preparing Your Network for Active Directory 00:10:00 Video and Lab - Preparing Server 2016 for Promotion to a Domain Controller 00:10:00 Video and Lab - Promote Server 2016 to a Domain Controller 00:09:00 Video and Lab - Join a Windows 10 Workstation to a Microsoft Domain 00:15:00 Windows Deployment Service Video - Install WDS on a Windows Server 00:16:00 Video - Deploy a Windows 10 Client Using WDS 00:09:00 Video and Lab - Create an Unattended Install of Windows 10 00:15:00 Windows 10 firewall, Windows Defender and UAC video - Turn the Windows 10 Firewall Off or On 00:00:00 Video - Allow an app through the Windows 10 firewall 00:05:00 video - Add a rule or port to a Windows 10 firewall 00:05:00 Video - Allow PING between Windows Server and Windows 10 00:05:00 Video - Disable the UAC User Account Control in Windows 10 00:02:00 Video - Using Netsh To Manage the Windows Firewall 00:05:00 Video - Using Powershell to Gather Firewall Information 00:04:00 Networking Video - Change your IP address in Windows 10 00:05:00 Video - Add a second IP address in Windows 10 00:09:00 Troubleshooting Video - Enable System Restore on Windows 10 00:03:00 Video - Create a System Restore point in Windows 10 00:00:00 Video - Recover using System Restore on Windows 10 00:04:00 Video - Fix TCPIP Corruption in Windows 10 Using Netsh 00:02:00 Video - Repair Windows 10 with System File Checker (SFC) 00:03:00 Video - Repair Windows 10 System files offline Using SFC 00:04:00 Video - Use ReadyBoost to Speed up Windows 10 00:05:00 Video - Reset Your Network Adapter 00:06:00 Video and Lab - Troubleshooting Internet Connectivity 00:16:00 Video - NSLookup 00:05:00 Overview of Windows Sysinternal Tools 00:08:00 Video - Overview of Sysinternal's Process Explorer 00:15:00 Performance Video - Generate a Windows Experience Index 00:06:00 Video - Windows 10 Performance Hack For a Slow PC 00:05:00 Video - Windows Reliability Monitor 00:04:00 User Preference Video - Disable the Lock Screen on Windows 10 00:03:00 Video - Disable Superfetch via Windows Services 00:03:00 Video - Disable Screen Saver in Windows 10 Using REGEDIT 00:02:00 Video - Disable Windows 10 Automatic Logoff For Inactivity 00:02:00 Video - Overview of the Windows 10 Shutdown and Restart buttons 00:01:00 Maintanence Video - Rename your Windows 10 computer 00:01:00 Video - Change the date and time in Windows 10 00:03:00 Video - Create a new local user in Windows 10 00:04:00 Video - Rearm the 30-day evaluation Period for Windows 10 Pro 00:03:00 Disk Management Video - Adding a secondary hard drive in Windows 10 Using VirtualBox 00:05:00 Video - How to use Storage Spaces in Windows 10 00:04:00 Video - How to Change drive letters in Windows 10 00:02:00 Video - How to format a volume Using FAT32 in Windows 10 00:03:00 Video - How to Convert FAT32 to NTFS in Windows 10 00:04:00 Video - How to run Chkdsk (Check Disk) in Windows 10 00:04:00 Printing Video - TCPIP Printing Overview 00:08:00 Video and lab - Adding a Printer to the Network Using TCPIP 00:10:00 Video and lab - Quickly install a network printer in Windows 10 00:03:00 Video - Printer Pooling 00:06:00 Powershell Disable UAC on Windows 10 Using PowerShell 00:03:00 Video - Using Powershell to Gather Firewall Information 00:04:00 Windows 10 Features, Tips and Tricks Video - Windows 10 Sandbox Feature 00:07:00 Video - Accessing the Extended Right-Click Menu in Windows 10 00:03:00 Wideo - Windows 10 File History 00:07:00 Video and Lab - Dumping Windows 10 Wi-Fi Credentials Using netsh 00:04:00 Video and Lab - Windows 10 God Mode 00:04:00 Obtain Your Certificate Order Your Certificate of Achievement 00:00:00 Get Your Insurance Now Get Your Insurance Now 00:00:00 Feedback Feedback 00:00:00

Microsoft Windows Server 2016 - Hands-on Training Part I
By Study Plex
Recognised Accreditation This course is accredited by continuing professional development (CPD). CPD UK is globally recognised by employers, professional organisations, and academic institutions, thus a certificate from CPD Certification Service creates value towards your professional goal and achievement. The Quality Licence Scheme is a brand of the Skills and Education Group, a leading national awarding organisation for providing high-quality vocational qualifications across a wide range of industries. What is CPD? Employers, professional organisations, and academic institutions all recognise CPD, therefore a credential from CPD Certification Service adds value to your professional goals and achievements. Benefits of CPD Improve your employment prospects Boost your job satisfaction Promotes career advancement Enhances your CV Provides you with a competitive edge in the job market Demonstrate your dedication Showcases your professional capabilities What is IPHM? The IPHM is an Accreditation Board that provides Training Providers with international and global accreditation. The Practitioners of Holistic Medicine (IPHM) accreditation is a guarantee of quality and skill. Benefits of IPHM It will help you establish a positive reputation in your chosen field You can join a network and community of successful therapists that are dedicated to providing excellent care to their client You can flaunt this accreditation in your CV It is a worldwide recognised accreditation What is Quality Licence Scheme? This course is endorsed by the Quality Licence Scheme for its high-quality, non-regulated provision and training programmes. The Quality Licence Scheme is a brand of the Skills and Education Group, a leading national awarding organisation for providing high-quality vocational qualifications across a wide range of industries. Benefits of Quality License Scheme Certificate is valuable Provides a competitive edge in your career It will make your CV stand out Course Curriculum Course Overview Course Overview Video 00:05:00 Building Your Virtual Lab Environment Downloading ISO and OVA Fles for VirtualBox 00:08:00 Create Virtual Install of Server 2016 Full GUI Using VirtualBox 00:12:00 Video and Lab - Creating a Virtual Install of Server 2016 Core Using VirtualBox 00:11:00 Video and Lab - Creating a Virtual Install Of Windows 10 Pro Using Virtualbox 00:16:00 Take a Snapshot of Your Current Configuration 00:04:00 Building a Microsoft Server 2016 Domain Preparing Your Network for Active Directory 00:09:00 Prepare Server 2016 for Promotion to a Domain Controller 00:09:00 Video and Lab - Promote Server 2016 to a Domain Controller 00:09:00 Join Server 2016 Core to Windows 2016 Domain 00:08:00 Promote Server Core to a Domain Controller 00:14:00 Add a Windows 10 Workstation to a Microsoft Domain 00:15:00 Create a Server 2016 Replica Domain Controller 00:13:00 Domain Naming System (DNS) Installing the DNS Role Using Server Manager 00:05:00 Create a Secondary or Backup DNS Server 00:07:00 Create a Secondary or Backup DNS Server Using Server Core 00:08:00 Create a DNS Reverse lookup Zone in Server 2016 00:02:00 Create a New DNS Host Record 00:01:00 Create a New MX record in DNS 00:04:00 Dynamic Host Configuration Protocol (DHCP) Install and Configure DHCP Using PowerShell 00:08:00 Authorize a Windows 2016 DHCP Server 00:03:00 Server and Scope Options in Windows Server 2016 00:03:00 How to Edit the Default Gateway Settings in DHCP 00:02:00 How to Edit DNS Server List in DHCP 00:03:00 Use Filters in DHCP to Deny Clients DHCP Services 00:02:00 Use DHCP User Classes to assign alternate scope options 00:05:00 Edit a DHCP Scope 00:02:00 How to Backup and Restore the DHCP Database 00:03:00 Create Predefined Options in DHCP 00:06:00 Speed Learning Active Directory Administration Create a User in Active Directory 00:01:00 Create an Administrator User in Server 2016 00:04:00 Create a Distribution Group in Active Directory 00:02:00 Create and Use a Security Group 00:03:00 Create an Organizational Unit 00:02:00 Unlock a User account 00:01:00 Move an Object to a New Organizational Unit in Active Directory 00:02:00 Change the Domain Administrator Password 00:01:00 Fix Access Denied When deleting Active Directory objects 00:01:00 Speed Learning Group Policy Prevent Automatic Logoff Due to Inactivity 00:03:00 Create and Link a Group Policy Object to an OU 00:04:00 Edit Group Policy Objects to Affect a User 00:03:00 Edit a Group Policy Object to Affect a Computer 00:03:00 Backup and Restore Group Policy Objects 00:03:00 Force Screensaver and Timeouts Using Group Policy 00:06:00 Change Users Desktop Background Using Group Policy 00:09:00 Speed Learning Server 2016 Administration Overview of the New Start Menu for Server 2016 00:02:00 Working with Task View in Server 2016 00:02:00 Enable Remote Desktop Using PowerShell 00:10:00 Rearm the 180-day Evaluation Period for Wndows Server 00:02:00 Rearm the 30-day Evaluation Period for Windows 10 00:03:00 Create a Heads-up Display Using BgInfo 00:08:00 Change the Date, Time and Numbers Format in Server 2016. 00:02:00 Rename Windows Server 2016 Using PowerShell 00:02:00 Manage Files and Shares Setup Work Folders in a Windows Domain 00:15:00 Configure a Distributed File System Using Windows Server 00:16:00 Create a Shared Folder on a Windows Server 00:04:00 Create a Shared Folder Using Server Manager 00:06:00 Speed Learning Managing Printers Add a Network Printer in Windows Server 2016 00:04:00 Install and Use the Print Management role in Windows Server 2016 00:04:00 Deploy Printers Using Group Policy in Windows Server 2016 00:03:00 Speed Learning Server 2016 Firewall Turn the Firewall on or off in Windows 2016 Server 00:01:00 Allow an Inbound Port Through a Windows Firewall 00:02:00 Enable PING for Server 2016 and Windows 10 00:04:00 Using Netsh to Manage the Windows Firewall 00:04:00 Using Powershell to Gather Firewall Information 00:04:00 Disk Management Adding Additional Hard Disks Using VirtualBox 00:06:00 Shrink or Extend a Volume in Windows Server 00:04:00 Format a Volume with ReFS in Windows Server 00:03:00 Format a Volume With FAT32 in Windows Server 00:02:00 Troubleshooting NSLookup 00:05:00 Troubleshooting Internet Connectivity 00:16:00 Overview of Windows Sysinternal Tools 00:08:00 Overview of Sysinternal's Process Explorer 00:17:00 Obtain Your Certificate Order Your Certificate of Achievement 00:00:00 Get Your Insurance Now Get Your Insurance Now 00:00:00 Feedback Feedback 00:00:00

Course Overview Learn how you can install, upgrade and maintain your Microsoft Windows 10 like a pro from this Microsoft Windows 10 Pro Masterclass course and make your work smooth and fast. This course will help you to understand the functions of Windows 10, configuration, management, security and many other functions and help you get the best output from your device. The easily understandable and bite-sized lessons of this Microsoft Windows 10 Pro Masterclass course will help you to understand how Windows 10 functions. You will be able to familiarize yourself with the network configuration and server domain-based environment to utilize the functions of Internet and cloud services. Even if you don't know anything about Windows 10, this course will help you to grasp the ideas and functions and use them properly. Learning Outcomes Learn how to plan, install and upgrade to Windows 10 Be able to implement networking system and remote management Understand file management and resources for your Windows 10 Familiarize with maintenance and update options of Windows 10 Get a clear understanding of local storage Ensure network security for your device Be able to troubleshoot and recover Windows 10 Who is this course for? This course is ideal for anyone who wants to understand the functions of Windows 10 and how to maintain and update their browser. You will learn various security and networking options of Windows 10 from this course. Entry Requirement This course is available to all learners, of all academic backgrounds. Learners should be aged 16 or over to undertake the qualification. Good understanding of English language, numeracy and ICT are required to attend this course. Certification After you have successfully completed the course, you will be able to obtain an Accredited Certificate of Achievement. You can however also obtain a Course Completion Certificate following the course completion without sitting for the test. Certificates can be obtained either in hardcopy at the cost of £39 or in PDF format at the cost of £24. PDF certificate's turnaround time is 24 hours, and for the hardcopy certificate, it is 3-9 working days. Why choose us? Affordable, engaging & high-quality e-learning study materials; Tutorial videos/materials from the industry-leading experts; Study in a user-friendly, advanced online learning platform; Efficient exam systems for the assessment and instant result; The UK & internationally recognized accredited qualification; Access to course content on mobile, tablet or desktop from anywhere anytime; The benefit of career advancement opportunities; 24/7 student support via email. Career Path Microsoft Windows 10 Pro Masterclass is a useful qualification to possess and would be beneficial for any related profession or industry such as: Computer Operators Data Security Officers Troubleshooters Data Maintenance Officers IT Professionals Administrators Module 01: Course Overview Course Overview 00:05:00 Module 02: Building Your Virtual Lab Environment Easily download ISO Images 00:10:00 Lab - Creating a Virtual Install of Windows 10 Pro Using VirtualBox 00:16:00 Lab - Create Virtual Install of Server 2016 Full GUI Using VirtualBox 00:13:00 Taking a Snapshot of Your Current configuration 00:04:00 Module 03: Upgrading Windows 7, 8, or 8.1 to Windows 10 Perform a Windows 10 Upgrade for Free 00:09:00 Module 04: Building a Microsoft Server 2016 Domain Preparing Your Network for Active Directory 00:10:00 Lab - Prepare Server 2016 for Promotion to a Domain Controller 00:10:00 Lab - Promote Server 2016 to a Domain Controller 00:09:00 Lab - Join a Windows 10 Workstation to a Microsoft Domain 00:15:00 Module 05: Windows Deployment Services (WDS) Installing WDS on a Windows Server Using VirtualBox 00:18:00 Deploy a Windows 10 Client Using WDS 00:09:00 lab - Create an Unattended Install of Windows 10 Pro 00:17:00 Module 06: Windows 10 Firewall, Windows Defender and UAC Turn the Windows 10 Firewall Off or On 00:01:00 Allow an app through the Windows 10 firewall 00:05:00 Add a rule or port to a Windows 10 firewall 00:05:00 Allow PING for Windows 10 00:04:00 Disable the UAC User Account Control in Windows 10 00:02:00 Using netsh to Manage the Windows Firewall 00:05:00 Using Powershell to Gather Firewall Information 00:04:00 Module 07: Networking Change your IP address in Windows 10 00:05:00 Add a second IP address in Windows 10 00:09:00 Module 08: Troubleshooting Enable System Restore on Windows 10 00:03:00 Create a System Restore point on Windows 10 00:02:00 Recover using System Restore on Windows 10 00:04:00 Fix TCPIP Corruption in Windows 10 Using Netsh 00:02:00 Repair Windows 10 with System File Checker (SFC) 00:03:00 Repair Windows 10 System files offline Using SFC 00:04:00 Use ReadyBoost to Speed up Windows 10 00:05:00 Reset Your Network Adapter 00:06:00 Lab - Troubleshooting Internet Connectivity 00:16:00 NSLookup 00:05:00 Windows Reliability Monitor 00:04:00 Module 09: User Preferences Disable the Lock Screen on Windows 10 00:03:00 Disable Superfetch via Windows Services 00:03:00 Disable Screen Saver in Windows 10 using REGEDIT 00:02:00 Disable Windows 10 Automatic Logoff For Inactivity 00:02:00 Overview of the Windows 10 Shutdown and Restart buttons 00:01:00 Module 10: Maintenance Rename your Windows 10 computer 00:01:00 Change the date and time in Windows 10 00:03:00 Create a new local user in Windows 10 00:04:00 Rearm the 30-day evaluation Period for Windows 10 Pro 00:03:00 Certificate and Transcript Order Your Certificates and Transcripts 00:00:00
