- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
331 Fire courses in Cardiff delivered Live Online
Attack Prevention with Juniper Networks Firewalls
By Nexus Human
Duration 1 Days 6 CPD hours This course is intended for This course is intended for network engineers, support personnel, reseller support, and others responsible for implementing ScreenOS products. Overview After successfully completing this course, you should be able to: Configure attack prevention features, including: ?SCREEN options; Deep Inspection (DI); and Antivirus (AV) scanning. Configure URL filtering. Configure antispam filters. This course meets the business needs of customers who are deploying the attack prevention features of ScreenOS software. The course focuses specifically on the attack-related features and assumes familiarity with ScreenOS software. Upon completing this course, you should be able to return to work and successfully configure and verify the desired attack prevention features. Chapter 1: Course Introduction Chapter 2: ScreenOS Basics Review Concepts Review Configuration Review Lab: ScreenOS Basics Review Chapter 3: SCREEN Options Multilayer Network Protection Types of Attacks SCREEN Options Configuration SCREEN Best Practices Lab: SCREEN Options Configuration Chapter 4: Deep Inspection Deep Inspection Overview Attack Database Configuration Policy Configuration Logging and Monitoring Lab: Deep Inspection Configuration Chapter 5: Antivirus Antivirus Operations Antivirus Configuration?Kaspersky Antivirus Configuration?ICAP Verifying Operations Lab: Antivirus Configuration Chapter 6: Web Filtering Web-Filtering Options Web-Filtering Configuration Verifying Operations Lab: Configuring Web Filtering Chapter 7: Antispam Antispam Concepts Antispam Configuration Verifying Operations Lab: Antispam Configuration Additional course details: Nexus Humans Attack Prevention with Juniper Networks Firewalls training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Attack Prevention with Juniper Networks Firewalls course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

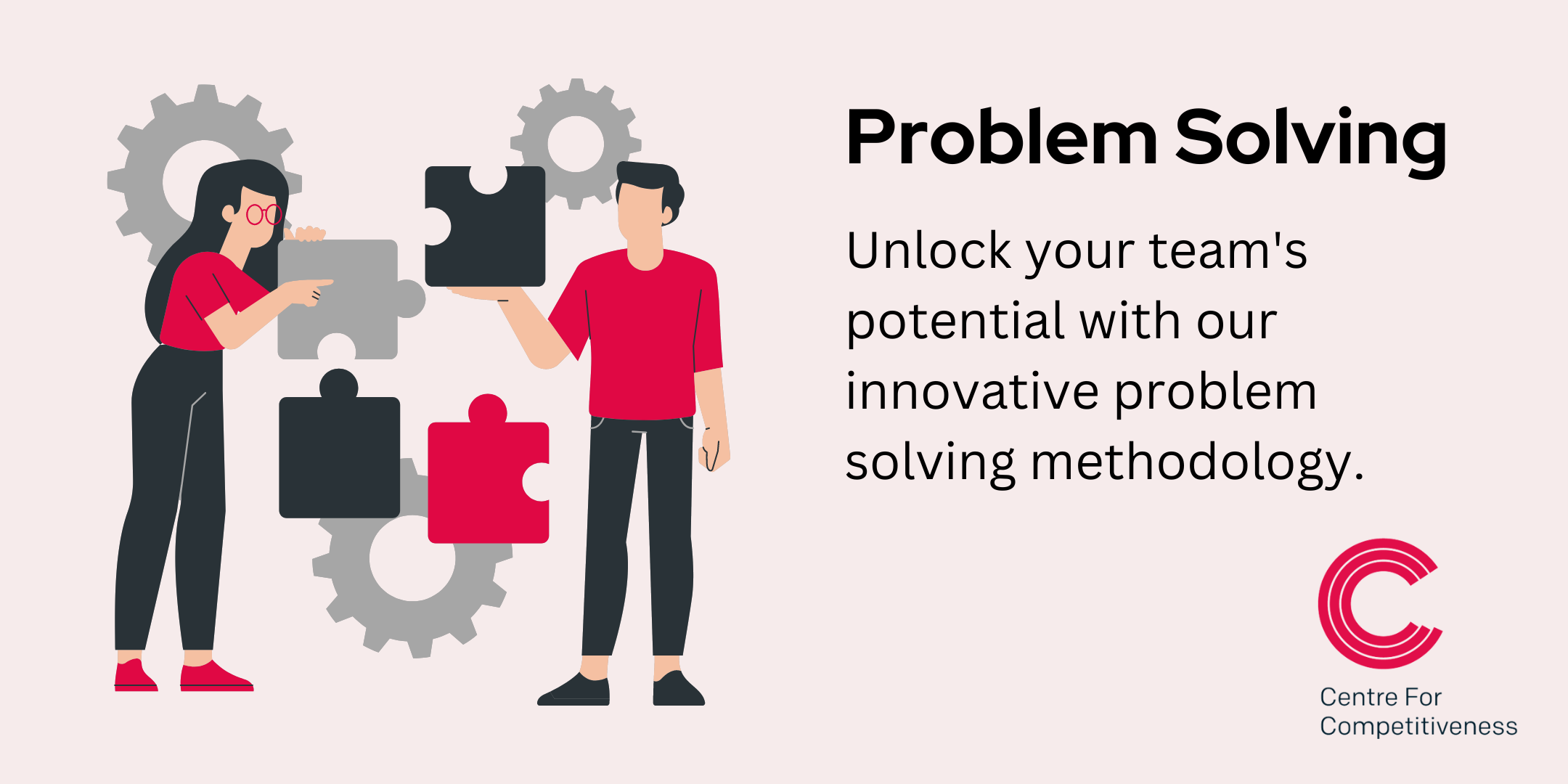
Creative Problem Solving
By Centre for Competitiveness
Firefighting or solving the same problems week after week? Create a problem-solving culture in your business with this proven methodology.
Cisco Implementing and Operating Cisco Security Core Technologies v1.0 (SCOR)
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for Security engineer Network engineer Network designer Network administrator Systems engineer Consulting systems engineer Technical solutions architect Network manager Cisco integrators and partners Overview After taking this course, you should be able to: Describe information security concepts and strategies within the network Describe common TCP/IP, network application, and endpoint attacks Describe how various network security technologies work together to guard against attacks Implement access control on Cisco ASA appliance and Cisco Firepower Next-Generation Firewall Describe and implement basic email content security features and functions provided by Cisco Email Security Appliance Describe and implement web content security features and functions provided by Cisco Web Security Appliance Describe Cisco Umbrella security capabilities, deployment models, policy management, and Investigate console Introduce VPNs and describe cryptography solutions and algorithms Describe Cisco secure site-to-site connectivity solutions and explain how to deploy Cisco Internetwork Operating System (Cisco IOS) Virtual Tunnel Interface (VTI)-based point-to-point IPsec VPNs, and point-to-point IPsec VPN on the Cisco ASA and Cisco Firepower Next-Generation Firewall (NGFW) Describe and deploy Cisco secure remote access connectivity solutions and describe how to configure 802.1X and Extensible Authentication Protocol (EAP) authentication Provide basic understanding of endpoint security and describe Advanced Malware Protection (AMP) for Endpoints architecture and basic features Examine various defenses on Cisco devices that protect the control and management plane Configure and verify Cisco IOS software Layer 2 and Layer 3 data plane controls Describe Cisco Stealthwatch Enterprise and Stealthwatch Cloud solutions Describe basics of cloud computing and common cloud attacks and how to secure cloud environment The Implementing and Operating Cisco Security Core Technologies (SCOR) v1.0 course helps you prepare for the Cisco© CCNP© Security and CCIE© Security certifications and for senior-level security roles. In this course, you will master the skills and technologies you need to implement core Cisco security solutions to provide advanced threat protection against cybersecurity attacks. You will learn security for networks, cloud and content, endpoint protection, secure network access, visibility, and enforcements. You will get extensive hands-on experience deploying Cisco Firepower© Next-Generation Firewall and Cisco Adaptive Security Appliance (ASA) Firewall; configuring access control policies, mail policies, and 802.1X Authentication; and more. You will get introductory practice on Cisco Stealthwatch© Enterprise and Cisco Stealthwatch Cloud threat detection features. This course, including the self-paced material, helps prepare you to take the exam, Implementing and Operating Cisco Security Core Technologies (350-701 SCOR), which leads to the new CCNP Security, CCIE Security, and the Cisco Certified Specialist - Security Core certifications. Describing Information Security Concepts* Information Security Overview Assets, Vulnerabilities, and Countermeasures Managing Risk Vulnerability Assessment Understanding Common Vulnerability Scoring System (CVSS) Describing Common TCP/IP Attacks* Legacy TCP/IP Vulnerabilities IP Vulnerabilities Internet Control Message Protocol (ICMP) Vulnerabilities TCP Vulnerabilities User Datagram Protocol (UDP) Vulnerabilities Attack Surface and Attack Vectors Reconnaissance Attacks Access Attacks Man-in-the-Middle Attacks Denial of Service and Distributed Denial of Service Attacks Reflection and Amplification Attacks Spoofing Attacks Dynamic Host Configuration Protocol (DHCP) Attacks Describing Common Network Application Attacks* Password Attacks Domain Name System (DNS)-Based Attacks DNS Tunneling Web-Based Attacks HTTP 302 Cushioning Command Injections SQL Injections Cross-Site Scripting and Request Forgery Email-Based Attacks Describing Common Endpoint Attacks* Buffer Overflow Malware Reconnaissance Attack Gaining Access and Control Gaining Access via Social Engineering Gaining Access via Web-Based Attacks Exploit Kits and Rootkits Privilege Escalation Post-Exploitation Phase Angler Exploit Kit Describing Network Security Technologies Defense-in-Depth Strategy Defending Across the Attack Continuum Network Segmentation and Virtualization Overview Stateful Firewall Overview Security Intelligence Overview Threat Information Standardization Network-Based Malware Protection Overview Intrusion Prevention System (IPS) Overview Next Generation Firewall Overview Email Content Security Overview Web Content Security Overview Threat Analytic Systems Overview DNS Security Overview Authentication, Authorization, and Accounting Overview Identity and Access Management Overview Virtual Private Network Technology Overview Network Security Device Form Factors Overview Deploying Cisco ASA Firewall Cisco ASA Deployment Types Cisco ASA Interface Security Levels Cisco ASA Objects and Object Groups Network Address Translation Cisco ASA Interface Access Control Lists (ACLs) Cisco ASA Global ACLs Cisco ASA Advanced Access Policies Cisco ASA High Availability Overview Deploying Cisco Firepower Next-Generation Firewall Cisco Firepower NGFW Deployments Cisco Firepower NGFW Packet Processing and Policies Cisco Firepower NGFW Objects Cisco Firepower NGFW Network Address Translation (NAT) Cisco Firepower NGFW Prefilter Policies Cisco Firepower NGFW Access Control Policies Cisco Firepower NGFW Security Intelligence Cisco Firepower NGFW Discovery Policies Cisco Firepower NGFW IPS Policies Cisco Firepower NGFW Malware and File Policies Deploying Email Content Security Cisco Email Content Security Overview Simple Mail Transfer Protocol (SMTP) Overview Email Pipeline Overview Public and Private Listeners Host Access Table Overview Recipient Access Table Overview Mail Policies Overview Protection Against Spam and Graymail Anti-virus and Anti-malware Protection Outbreak Filters Content Filters Data Loss Prevention Email Encryption Deploying Web Content Security Cisco Web Security Appliance (WSA) Overview Deployment Options Network Users Authentication Secure HTTP (HTTPS) Traffic Decryption Access Policies and Identification Profiles Acceptable Use Controls Settings Anti-Malware Protection Deploying Cisco Umbrella* Cisco Umbrella Architecture Deploying Cisco Umbrella Cisco Umbrella Roaming Client Managing Cisco Umbrella Cisco Umbrella Investigate Overview and Concepts Explaining VPN Technologies and Cryptography VPN Definition VPN Types Secure Communication and Cryptographic Services Keys in Cryptography Public Key Infrastructure Introducing Cisco Secure Site-to-Site VPN Solutions Site-to-Site VPN Topologies IPsec VPN Overview IPsec Static Crypto Maps IPsec Static Virtual Tunnel Interface Dynamic Multipoint VPN Cisco IOS FlexVPN Deploying Cisco IOS VTI-Based Point-to-Point IPsec VPNs Cisco IOS VTIs Static VTI Point-to-Point IPsec Internet Key Exchange (IKE) v2 VPN Configuration Deploying Point-to-Point IPsec VPNs on the Cisco ASA and Cisco Firepower NGFW Point-to-Point VPNs on the Cisco ASA and Cisco Firepower NGFW Cisco ASA Point-to-Point VPN Configuration Cisco Firepower NGFW Point-to-Point VPN Configuration Introducing Cisco Secure Remote Access VPN Solutions Remote Access VPN Components Remote Access VPN Technologies Secure Sockets Layer (SSL) Overview Deploying Remote Access SSL VPNs on the Cisco ASA and Cisco Firepower NGFW Remote Access Configuration Concepts Connection Profiles Group Policies Cisco ASA Remote Access VPN Configuration Cisco Firepower NGFW Remote Access VPN Configuration Explaining Cisco Secure Network Access Solutions Cisco Secure Network Access Cisco Secure Network Access Components AAA Role in Cisco Secure Network Access Solution Cisco Identity Services Engine Cisco TrustSec Describing 802.1X Authentication 802.1X and Extensible Authentication Protocol (EAP) EAP Methods Role of Remote Authentication Dial-in User Service (RADIUS) in 802.1X Communications RADIUS Change of Authorization Configuring 802.1X Authentication Cisco Catalyst© Switch 802.1X Configuration Cisco Wireless LAN Controller (WLC) 802.1X Configuration Cisco Identity Services Engine (ISE) 802.1X Configuration Supplicant 802.1x Configuration Cisco Central Web Authentication Describing Endpoint Security Technologies* Host-Based Personal Firewall Host-Based Anti-Virus Host-Based Intrusion Prevention System Application Whitelists and Blacklists Host-Based Malware Protection Sandboxing Overview File Integrity Checking Deploying Cisco Advanced Malware Protection (AMP) for Endpoints* Cisco AMP for Endpoints Architecture Cisco AMP for Endpoints Engines Retrospective Security with Cisco AMP Cisco AMP Device and File Trajectory Managing Cisco AMP for Endpoints Introducing Network Infrastructure Protection* Identifying Network Device Planes Control Plane Security Controls Management Plane Security Controls Network Telemetry Layer 2 Data Plane Security Controls Layer 3 Data Plane Security Controls Deploying Control Plane Security Controls* Infrastructure ACLs Control Plane Policing Control Plane Protection Routing Protocol Security Deploying Layer 2 Data Plane Security Controls* Overview of Layer 2 Data Plane Security Controls Virtual LAN (VLAN)-Based Attacks Mitigation Sp

VMware NSX for Intrinsic Security [V4.x]
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for Experienced security administrators Overview By the end of the course, you should be able to meet the following objectives: Define the concepts related to information security Explain the different types of firewalls and their use cases Describe the operation of intrusion detection and intrusion prevention systems Differentiate between Malware Prevention approaches Describe the VMware intrinsic security portfolio Use NSX segmentation to implement Zero-Trust Security Configure user and role management Configure and troubleshoot Distributed Firewall, Identity Firewall, and time-based policies Configure and troubleshoot Gateway Security Use VMware Aria Operations⢠for Logs and VMware Aria Operations⢠for Networks to operate NSX firewalls Explain the security best practices related to grouping, tagging, and rule configuration Describe north-south and east-west service insertion Describe endpoint protection Configure and troubleshoot IDS/IPS Deploy NSX Application Platform Configure and troubleshoot NSX Malware Prevention Describe the capabilities of NSX Intelligence and NSX NDR This five-day, hands-on training course provides you with the knowledge, skills, and tools to achieve competency in configuring, operating, and troubleshooting VMware NSX© for intrinsic security. This course introduces all the security features in NSX, including Distributed Firewall and Gateway Firewall, Intrusion Detection and Prevention (IDS/IPS), NSX Application Platform, NSX Malware Prevention, VMware NSX© Intelligence?, and VMware NSX© NDR?. In addition, this course presents common configuration issues and gives a methodology to resolve them. Course Introduction Introduction and course logistics Course objectives Security Basics Define the concepts related to information security Explain the different types of firewalls and their use cases Describe the operation of IDS/IPS Differentiate between Malware Prevention approaches VMware Intrinsic Security Define the VMware intrinsic security strategy Describe the VMware intrinsic security portfolio Explain how NSX aligns with the intrinsic security strategy Implementing Zero-Trust Security Define Zero-Trust Security Describe the five pillars of a Zero-Trust architecture Define NSX segmentation and its use cases Describe the steps needed to enforce Zero-Trust with NSX segmentation User and Role Management Integrate NSX and VMware Identity Manager? Integrate NSX and LDAP Describe the native users and roles in NSX Create and assign custom user roles Explain object-based RBAC in a multitenancy environment Distributed Firewall Configure Distributed Firewall rules and policies Describe the NSX Distributed Firewall architecture Troubleshoot common problems related to NSX Distributed Firewall Configure time-based policies Configure Identity Firewall rules Configure the distributed firewall to block malicious IPs Gateway Security Configure Gateway Firewall rules and policies Describe the architecture of the Gateway Firewall Identify and troubleshoot common Gateway Firewall issues Configure TLS Inspection to decrypt traffic for both internal and external services Configure URL filtering and identify common configuration issues Operating Internal Firewalls Use VMware Aria Operations for Logs and VMware Aria Operations for Networks to operate NSX firewalls Explain security best practices related to grouping, tagging, and rule configuration Network Introspection Explain network introspection Describe the architecture and workflows of north-south and east-west service insertion Troubleshoot north-south and east-west service insertion Endpoint Protection Explain endpoint protection Describe the architecture and workflows of endpoint protection Troubleshoot endpoint protection Intrusion Detection and Prevention Describe the MITRE ATT&CK framework Explain the different phases of a cyber attack Describe how NSX security solutions can be used to protect against cyber attacks Configure and troubleshoot Distributed IDS/IPS Configure and troubleshoot North-South IDS/IPS NSX Application Platform Describe NSX Application Platform and its use cases Identify the topologies supported for the deployment of NSX Application Platform Deploy NSX Application Platform Explain the NSX Application Platform architecture and services Validate the NSX Application Platform deployment and troubleshoot common issues NSX Malware Prevention Identify use cases for NSX Malware Prevention Identify the components in the NSX Malware Prevention architecture Describe the NSX Malware Prevention packet flows for known and unknown files Configure NSX Malware Prevention for east-west and north-south traffic NSX Intelligence and NSX NDR Describe NSX Intelligence and its use cases Explain NSX Intelligence visualization, recommendation, and network traffic analysis capabilities Describe NSX NDR and its use cases Explain the architecture of NSX NDR in NSX Describe the visualization capabilities of NSX NDR Additional course details:Notes Delivery by TDSynex, Exit Certified and New Horizons an VMware Authorised Training Centre (VATC) Nexus Humans VMware NSX for Intrinsic Security [V4.x] training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the VMware NSX for Intrinsic Security [V4.x] course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.
![VMware NSX for Intrinsic Security [V4.x]](https://cademy-images-io.b-cdn.net/9dd9d42b-e7b9-4598-8d01-a30d0144ae51/4c81f130-71bf-4635-b7c6-375aff235529/original.png?width=3840)
VMware NSX-T Data Center for Intrinsic Security [V3.2]
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for Experienced security administrators Overview By the end of the course, you should be able to meet the following objectives: Define information-security-related concepts Explain the different types of firewalls and their use cases Describe the operation of intrusion detection and intrusion prevention systems Differentiate between Malware Prevention approaches Describe the VMware intrinsic security portfolio Implement Zero-Trust Security using VMware NSX segmentation Configure user and role management Configure and troubleshoot Distributed Firewall, Identity Firewall, and time-based policies Configure and troubleshoot Gateway Security Use VMware vRealize Log Insight⢠for NSX⢠and VMware vRealize Network Insight⢠to operate NSX firewalls Explain the security best practices related to grouping, tagging, and rule configuration Describe north-south and east-west service insertion Describe endpoint protection Configure and troubleshoot IDS/IPS Deploy NSX Application Platform Configure and troubleshoot NSX Malware Prevention Describe the capabilities of NSX Intelligence and NSX Network Detection and Response This five-day, hands-on training course provides you with the knowledge, skills, and tools to achieve competency in configuring, operating, and troubleshooting VMware NSX-T? Data Center for intrinsic security. In this course, you are introduced to all the security features in NSX-T Data Center, including Distributed Firewall and Gateway Firewall, Intrusion Detection and Prevention (IDS/IPS), NSX Application Platform, NSX Malware Prevention, VMware NSX© Intelligence?, and VMware NSX© Network Detection and Response?.In addition, you are presented with common configuration issues and given a methodology to resolve them. Course Introduction Introductions and course logistics Course objectives Security Basics Define information-security-related concepts Explain the different types of firewalls and their use cases Describe the operation of IDS/IPS Differentiate between Malware Prevention approaches VMware Intrinsic Security Define the VMware intrinsic security strategy Describe the VMware intrinsic security portfolio Explain how NSX-T Data Center aligns with the intrinsic security strategy Implementing Zero-Trust Security Define Zero-Trust Security Describe the five pillars of a Zero-Trust Architecture Define NSX segmentation and its use cases Describe the steps needed to enforce Zero-Trust with NSX segmentation User and Role Management Integrate NSX-T Data Center and VMware Identity Manager? Integrate NSX-T Data Center and LDAP Describe the native users and roles in NSX-T Data Center Create and assign custom user roles Distributed Firewall Configure Distributed Firewall rules and policies Describe the NSX Distributed Firewall architecture Troubleshoot common problems related to NSX Distributed Firewall Configure time-based policies Configure Identity Firewall rules Gateway Security Configure Gateway Firewall rules and policies Describe the architecture of the Gateway Firewall Identify and troubleshoot common Gateway Firewall issues Configure TLS Inspection to decrypt traffic for both internal and external services Configure URL filtering and identify common configuration issues Operating Internal Firewalls Use vRealize Log Insight for NSX and vRealize Network Insight to operate NSX firewalls Explain security best practices related to grouping, tagging, and rule configuration Network Introspection Explain network introspection Describe the architecture and workflows of north-south and east-west service insertion Troubleshoot north-south and east-west service insertion Endpoint Protection Explain endpoint protection Describe the architecture and workflows of endpoint protection Troubleshoot endpoint protection Intrusion Detection and Prevention Describe the MITRE ATT&CK framework Explain the different phases of a cyber attack Describe how NSX security solutions can be used to protect against cyber attacks Configure and troubleshoot Distributed IDS/IPS Configure and troubleshoot North-South IDS/IPS NSX Application Platform Describe NSX Application Platform and its use cases Identify the topologies supported for the deployment of NSX Application Platform Deploy NSX Application Platform Explain the NSX Application Platform architecture and services Validate the NSX Application Platform deployment and troubleshoot common issues NSX Malware Prevention Identify use cases for NSX Malware Prevention Identify the components in the NSX Malware Prevention architecture Describe the NSX Malware Prevention packet flows for known and unknown files Configure NSX Malware Prevention for east-west and north-south traffic NSX Intelligence and NSX Network Detection and Response Describe NSX Intelligence and its use cases Explain NSX Intelligence visualization, recommendation, and network traffic analysis capabilities Describe NSX Network Detection and Response and its use cases Explain the architecture of NSX Network Detection and Response in NSX-T Data Center Describe the visualization capabilities of NSX Network Detection and Response
![VMware NSX-T Data Center for Intrinsic Security [V3.2]](https://cademy-images-io.b-cdn.net/9dd9d42b-e7b9-4598-8d01-a30d0144ae51/4c81f130-71bf-4635-b7c6-375aff235529/original.png?width=3840)
Certified Professional Ethical Hacker
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for This course is targeted towards the information technology (IT) professional that has a minimum 1 year IT Security and Networking experience. This course would be ideal for Information System Owners, Security Officers, Ethical Hackers, Information Owners, Penetration Testers, System Owner and Managers as well as Cyber Security Engineers. Overview Upon completion, the Certified Professional Ethical Hacker candidate will be able to competently take the CPEH exam. The CPEH certification training enables students to understand the importance of vulnerability assessments and how to implement counter response along with preventative measures when it comes to a network hack. Security Fundamentals Overview The Growth of Environments and Security Our Motivation? The Goal: Protecting Information! CIA Triad in Detail Approach Security Holistically Security Definitions Definitions Relationships Method: Ping The TCP/IP Stack Which Services Use Which Ports? TCP 3-Way Handshake TCP Flags Malware Types of Malware Types of Malware Cont... Types of Viruses More Malware: Spyware Trojan Horses Back Doors DoS DDoS Packet Sniffers Passive Sniffing Active Sniffing Firewalls, IDS and IPS Firewall ? First Line of Defense IDS ? Second Line of Defense IPS ? Last Line of Defense? Firewalls Firewall Types: (1) Packet Filtering Firewall Types: (2) Proxy Firewalls Firewall Types ? Circuit-Level Proxy Firewall Type of Circuit- Level Proxy ? SOCKS Firewall Types ? Application-Layer Proxy Firewall Types: (3) Stateful Firewall Types: (4) Dynamic Packet-Filtering Firewall Types: (5) Kernel Proxies Firewall Placement Firewall Architecture Types ? Screened Host Multi- or Dual-Homed Screened Subnet Wi-Fi Network Types Wi-Fi Network Types Widely Deployed Standards Standards Comparison 802.11n - MIMO Overview of Database Server Review Access Controls Overview Role of Access Control Definitions More Definitions Categories of Access Controls Physical Controls Logical Controls ?Soft? Controls Security Roles Steps to Granting Access Access Criteria Physical Access Control Mechanisms Biometric System Types Synchronous Token Asynchronous Token Device Memory Cards Smart Card Cryptographic Keys Logical Access Controls OS Access Controls Linux Access Controls Accounts and Groups Password & Shadow File Formats Accounts and Groups Linux and UNIX Permissions Set UID Programs Trust Relationships Review Protocols Protocols Overview OSI ? Application Layer OSI ? Presentation Layer OSI ? Session Layer Transport Layer OSI ? Network Layer OSI ? Data Link OSI ? Physical Layer Protocols at Each OSI Model Layer TCP/IP Suite Port and Protocol Relationship Conceptual Use of Ports UDP versus TCP Protocols ? ARP Protocols ? ICMP Network Service ? DNS SSH Security Protocol SSH Protocols ? SNMP Protocols ? SMTP Packet Sniffers Example Packet Sniffers Review Cryptography Overview Introduction Encryption Cryptographic Definitions Encryption Algorithm Implementation Symmetric Encryption Symmetric Downfalls Symmetric Algorithms Crack Times Asymmetric Encryption Public Key Cryptography Advantages Asymmetric Algorithm Disadvantages Asymmetric Algorithm Examples Key Exchange Symmetric versus Asymmetric Using the Algorithm Types Together Instructor Demonstration Hashing Common Hash Algorithms Birthday Attack Example of a Birthday Attack Generic Hash Demo Instructor Demonstration Security Issues in Hashing Hash Collisions MD5 Collision Creates Rogue Certificate Authority Hybrid Encryption Digital Signatures SSL/TLS SSL Connection Setup SSL Hybrid Encryption SSH IPSec - Network Layer Protection IPSec IPSec Public Key Infrastructure Quantum Cryptography Attack Vectors Network Attacks More Attacks (Cryptanalysis) Review Why Vulnerability Assessments? Overview What is a Vulnerability Assessment? Vulnerability Assessment Benefits of a Vulnerability Assessment What are Vulnerabilities? Security Vulnerability Life Cycle Compliance and Project Scoping The Project Overview Statement Project Overview Statement Assessing Current Network Concerns Vulnerabilities in Networks More Concerns Network Vulnerability Assessment Methodology Network Vulnerability Assessment Methodology Phase I: Data Collection Phase II: Interviews, Information Reviews, and Hands-On Investigation Phase III: Analysis Analysis cont. Risk Management Why Is Risk Management Difficult? Risk Analysis Objectives Putting Together the Team and Components What Is the Value of an Asset? Examples of Some Vulnerabilities that Are Not Always Obvious Categorizing Risks Some Examples of Types of Losses Different Approaches to Analysis Who Uses What? Qualitative Analysis Steps Quantitative Analysis ALE Values Uses ALE Example ARO Values and Their Meaning ALE Calculation Can a Purely Quantitative Analysis Be Accomplished? Comparing Cost and Benefit Countermeasure Criteria Calculating Cost/Benefit Cost of a Countermeasure Can You Get Rid of All Risk? Management?s Response to Identified Risks Liability of Actions Policy Review (Top-Down) Methodology Definitions Policy Types Policies with Different Goals Industry Best Practice Standards Components that Support the Security Policy Policy Contents When Critiquing a Policy Technical (Bottom-Up) Methodology Review Vulnerability Tools of the Trade Vulnerability Scanners Nessus SAINT ? Sample Report Tool: Retina Qualys Guard http://www.qualys.com/products/overview/ Tool: LANguard Microsoft Baseline Analyzer MBSA Scan Report Dealing with Assessment Results Patch Management Options Review Output Analysis and Reports Overview Staying Abreast: Security Alerts Vulnerability Research Sites Nessus SAINT SAINT Reports GFI Languard GFI Reports MBSA MBSA Reports Review Reconnaissance, Enumeration & Scanning Reconnaissance Overview Step One in the Hacking ?Life-Cycle? What Information is Gathered by the Hacker? Passive vs. Active Reconnaissance Footprinting Defined Social Access Social Engineering Techniques Social Networking Sites People Search Engines Internet Archive: The WayBack Machine Footprinting Tools Overview Maltego GUI Johnny.Ihackstuff.com Google (cont.) Domain Name Registration WHOIS Output DNS Databases Using Nslookup Traceroute Operation Web Server Info Tool: Netcraft Introduction to Port Scanning Which Services use Which Ports? Port Scan Tips Port Scans Shou

Cisco Implementing Automation for Cisco Security Solutions v1.0 (SAUI)
By Nexus Human
Duration 3 Days 18 CPD hours This course is intended for Channel and Customer Engineers Network Engineer System Engineer Wireless Engineer Consulting Systems Engineer Technical Solutions Architect Network Admisnistrator Wireless Design Engineer Network Manager Channel SEs Sales Engineer Channel AMs Account Manager Overview Upon completing this course, students will be able to meet these objectives: Understand the overall architecture of the Cisco security solutions and how APIs help enable security Understand how to use Cisco Firepower APIs Understand how pxGrid APIs function and their benefits Understand what capabilities the Cisco Stealthwatch APIs offer and construct API requests to them for configuration changes and auditing purposes Understand the features and benefits of using Cisco Stealthwatch Cloud APIs Learn how to use the Cisco Umbrella Investigate API Understand the Functionality provided by Cisco AMP and its APIs Learn how to use Cisco Threat Grid APIs to analyze, search, and dispose of threats This course demonstrates the tools and the benefits of leveraging programmability and automation in Cisco Security Solutions, including Cisco Firepower Management Center, Cisco Firepower Threat Defense, Cisco ISE, Cisco pxGrid, Cisco Stealthwatch Enterprise, Cisco Stealthwatch Cloud, Cisco Umbrella, Cisco AMP, Cisco Threat grid, and Cisco Security Management Appliances. Students will learn how to use the API for each Cisco security solution and specific applications of when the API benefits IT security content. Introducing Cisco Security APIs Role of APIs in Cisco Security Solutions Cisco Firepower, Cisco ISE, Cisco pxGrid, and Cisco Stealthwatch APIs Use cases and security workflow Consuming Cisco Advanced Malware Protection APIs Cisco AMP overview Cisco AMP endpoint API Cisco AMP use cases and workflows Discovery 1: Query Cisco AMP endpoint APIs for verifying compliance Using Cisco ISE Introducing Cisco Identity services engine Cisco ISE use cases Cisco ISE APIs Using Cisco pxGrid APIs Cisco pxGrid overview WebSockets and STOMP messaging protocol Discovery 2: Use the REST API and Cisco pxGrid with Cisco Identity services engine Using Cisco Threat Grid APIs Cisco threat grid overview Cisco threat grid API Cisco threat grid use cases and workflows Discovery 3: Construct a Python script using the Cisco threat grid API Investigating Cisco Umbrella Security Data Programmatically Cisco Umbrella investigate API overview Cisco Umbrella investigate API: Details Discovery 4: Query security data with the Cisco Umbrella investigate API Exploring Cisco Umbrella Reporting and Enforcement APIs Cisco Umbrella reporting and enforcement APIs: Overview Cisco Umbrella reporting and enforcement APIs: Deep dive Discovery 5: Generate reports using the Cisco Umbrella reporting API Automating Security with Cisco Firepower APIs Review basic constructs of Firewall policy management Design policies for automation Cisco FMC APIs in depth Discovery 6: Explore the Cisco Firepower management center API Cisco FTD automation with ansible Discovery 7: Use ansible to automate Cisco Firepower threat defense configuration Cisco FDM API in depth Discovery 8: Automate Firewall policies using the Cisco Firepower device manager API Operationalizing Cisco Stealthwatch and Its API Capabilities Cisco Stealthwatch overview Cisco Stealthwatch APIs: Details Discovery 9: Automate alarm policies and create reports using the Cisco Stealthwatch APIs Using Cisco Stealthwatch Cloud APIs Cisco Stealthwatch Cloud overview Cisco Stealthwatch Cloud APIs: Deep dive Discovery 10: Construct a report using Cisco stealthwatch Cloud APIs Describing Cisco Security Management Appliance APIs Cisco SMA APIs overview Cisco SMA API Discovery 11: Construct reports using Cisco SMA APIs

Developing Applications with Google Cloud
By Nexus Human
Duration 3 Days 18 CPD hours This course is intended for Application developers who want to build cloud-native applications or redesign existing applications that will run on Google Cloud Platform Overview This course teaches participants the following skills: Use best practices for application development. Choose the appropriate data storage option for application data. Implement federated identity management. Develop loosely coupled application components or microservices. Integrate application components and data sources. Debug, trace, and monitor applications. Perform repeatable deployments with containers and deployment services. Choose the appropriate application runtime environment; use Google Container Engine as a runtime environment and later switch to a no-ops solution with Google App Engine flexible environment. Learn how to design, develop, and deploy applications that seamlessly integrate components from the Google Cloud ecosystem. This course uses lectures, demos, and hands-on labs to show you how to use Google Cloud services and pre-trained machine learning APIs to build secure, scalable, and intelligent cloud-native applications. Best Practices for Application Development Code and environment management. Design and development of secure, scalable, reliable, loosely coupled application components and microservices. Continuous integration and delivery. Re-architecting applications for the cloud. Google Cloud Client Libraries, Google Cloud SDK, and Google Firebase SDK How to set up and use Google Cloud Client Libraries, Google Cloud SDK, and Google Firebase SDK. Lab: Set up Google Client Libraries, Cloud SDK, and Firebase SDK on a Linux instance and set up application credentials. Overview of Data Storage Options Overview of options to store application data. Use cases for Google Cloud Storage, Cloud Firestore, Cloud Bigtable, Google Cloud SQL, and Cloud Spanner. Best Practices for Using Cloud Firestore Best practices related to using Cloud Firestore in Datastore mode for:Queries, Built-in and composite indexes, Inserting and deleting data (batch operations),Transactions,Error handling. Bulk-loading data into Cloud Firestore by using Google Cloud Dataflow. Lab: Store application data in Cloud Datastore. Performing Operations on Cloud Storage Operations that can be performed on buckets and objects. Consistency model. Error handling. Best Practices for Using Cloud Storage Naming buckets for static websites and other uses. Naming objects (from an access distribution perspective). Performance considerations. Setting up and debugging a CORS configuration on a bucket. Lab: Store files in Cloud Storage. Handling Authentication and Authorization Cloud Identity and Access Management (IAM) roles and service accounts. User authentication by using Firebase Authentication. User authentication and authorization by using Cloud Identity-Aware Proxy. Lab: Authenticate users by using Firebase Authentication. Using Pub/Sub to Integrate Components of Your Application Topics, publishers, and subscribers. Pull and push subscriptions. Use cases for Cloud Pub/Sub. Lab: Develop a backend service to process messages in a message queue. Adding Intelligence to Your Application Overview of pre-trained machine learning APIs such as Cloud Vision API and Cloud Natural Language Processing API. Using Cloud Functions for Event-Driven Processing Key concepts such as triggers, background functions, HTTP functions. Use cases. Developing and deploying functions. Logging, error reporting, and monitoring. Managing APIs with Cloud Endpoints Open API deployment configuration. Lab: Deploy an API for your application. Deploying Applications Creating and storing container images. Repeatable deployments with deployment configuration and templates. Lab: Use Deployment Manager to deploy a web application into Google App Engine flexible environment test and production environments. Execution Environments for Your Application Considerations for choosing an execution environment for your application or service:Google Compute Engine (GCE),Google Kubernetes Engine (GKE), App Engine flexible environment, Cloud Functions, Cloud Dataflow, Cloud Run. Lab: Deploying your application on App Engine flexible environment. Debugging, Monitoring, and Tuning Performance Application Performance Management Tools. Stackdriver Debugger. Stackdriver Error Reporting. Lab: Debugging an application error by using Stackdriver Debugger and Error Reporting. Stackdriver Logging. Key concepts related to Stackdriver Trace and Stackdriver Monitoring. Lab: Use Stackdriver Monitoring and Stackdriver Trace to trace a request across services, observe, and optimize performance.

Oracle Database Security - Detective Controls
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for This course is intended for Administrator, Database Administrator, Security Specialist, and Systems Administrator. Overview Upon successful completion of this course, students will be able to Enumerate Oracle auditing solutions to monitor database security requirements, Implement Oracle Audit Vault and Database Firewall, Configure Oracle Audit Vault and Database Firewall, Explain Oracle Compliance Framework, and Configure basic Compliance Framework rules. In the Oracle Database Security: Detective Controls course, students learn how they can use Oracle Database administration auditing features to meet the compliance requirements of their organization. IntroductionUsing Unified AuditUsing Fine-Grained AuditIntroduction to Oracle Audit Vault and Database Firewall (AVDF)Planning the Oracle Audit Vault and Database Firewall ImplementationInstalling the Audit Vault ServerConfiguring the Audit Vault ServerConfiguring Oracle AVDF and Deploying the Audit Vault AgentNetworking and Oracle AVDFInstalling a Database FirewallConfiguring Oracle AVDF and Deploying Database FirewallUsing Host MonitoringConfiguring High AvailabilityCreating Custom Collection Plug-insManaging the Audit Vault ServerManaging the Database FirewallsOverview of the Auditing and Reporting FeaturesPerforming Administrative TasksCreating Audit Policies for Oracle DatabasesCreating Database Firewall PoliciesOracle AVDF ReportsManaging Entitlements Additional course details: Nexus Humans Oracle Database Security - Detective Controls training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Oracle Database Security - Detective Controls course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Palo Alto Networks : Strata Foundations
By Nexus Human
Duration 1 Days 6 CPD hours This course is intended for Security Engineers Network Engineers Support staff Overview This course is intended to provide an understanding of Palo Alto Networks Next-Generation firewall technologies enable the student to perform a basic installation of Palo Alto Networks Next-Generation firewalls. Upon completion of this course, students will be able to: Explain the features and advantages of the Palo Alto Networks next-generation firewall architecture Understand the capabilities of App-ID, Content-ID, and User-ID Perform the basic configuration of the firewall including: Interfaces and virtual routers NAT Policies Security zones Objects Security policies Content security profiles View logs and basic reports This course was formerly named Palo Alto Networks Foundations of Next Generation Firewalls (EDU-150). ** Our foundation classes are just introductory trainings, NOT a full technical training. Your network has expanded beyond your organization\'s boundaries. Cloud locations and remote users (often using personal devices) have \'distributed\' the surface you need to both enable and protect.At the same time, the motivations of attackers and their sophistication have continued to evolve.Palo Alto Networks' next-generation firewalls are all based on a consistent Single-Pass Architecture, enabling security capability that is unique in the industry. This architecture is implemented in a portfolio of both physical and virtual appliances, designed to cover a range of performance and use case requirements.Features and management are consistent across the portfolio. Integration with GlobalProtect? mobile security service extends policy-based security to mobile devices (whether on-premises or remote). Integration with our threat intelligence services keeps information up to date for the firewall (e.g., URL categories, threat signatures). WildFire? cloud-based malware analysis environment integration supports a rapid \'feedback loop\' that enables the firewall to stop advanced threats throughout the attack lifecycle. Course Outline Module 0: Introduction Module 1: Platforms & Architecture Module 2: Getting Started Module 3: Basic Administration Module 4: Connectivity Module 5: Security Module 6: Logging & Reporting Additional course details: Nexus Humans Palo Alto Networks : Strata Foundations training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Palo Alto Networks : Strata Foundations course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.
