- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
An Old Boat & boat shed in Morocco in watercolour
By Marilyn Allis
Capture the textures and Moroccan feel of this scene in Essaouira easily with lots of tips to create texture & drama.

Circle of Friends
By Inclusive Solutions
Circle of Friends is an approach to enhancing the inclusion, in a mainstream setting, of any child or young person who is experiencing difficulties in school because of disability, personal crisis or because of their challenging behaviour towards others. The ‘circle of friends’ approach works by mobilising the young person’s peers to provide support and engage in problem solving with the person in difficulty. Online Course now available via Teachable Platform – Creating Circles ofFriends Learn at your own pace… lots of text and video support Course Category Inclusion Peer Support Behaviour and Relationships Autism and Communication Description Circle of Friends is an approach to enhancing the inclusion, in a mainstream setting, of any child or young person who is experiencing difficulties in school because of disability, personal crisis or because of their challenging behaviour towards others. The ‘circle of friends’ approach works by mobilising the young person’s peers to provide support and engage in problem solving with the person in difficulty. ‘Circle of friends’ is not the same as ‘circle time’ but many of the skills and techniques used by teachers in ‘circle time’ can be used to support the ‘circle of friends’ process. Over the past 12 years Colin Newton and Derek Wilson have been encouraging the use of ‘circle of friends’ in a wide variety of primary and secondary schools, often with very successful outcomes. Some of these are described in their books ‘Circles of Friends’, (Folens, 1999) and ‘Creating Circles of Friends’ (Inclusive Solutions, 2005). This is an excellent opportunity to learn from Colin Newton and Derek Wilson the educational psychologists who brought this Department of Education endorsed approach to the UK. Learn how to build teams around challenging pupils by drawing on a resource which is always there…. other children. Enjoy participating in a multi media workshop that will challenge, entertain and reach for your emotions. Circles of support are for us all, for life…. and they work! Testimonials ‘Absolutely fantastic session – so thought provoking and positive.’ ‘Well presented excellent course’ ‘Wonderful, mind blowing day. Lots of children and young people there we need to really see – not treat’ ‘Excellent presentation, lively, modern, current – definitely got the attention. Course gave great food for thought and I feel confident that this way of working will have a place in the future of our school. Learning Objectives To be able to understand the values and wider context of inclusion To be able to set up and run a ‘circle of friends’ to reduce likelihood of a pupil being excluded or segregated To understand and be able to maximise the power of the peer group in supporting relationships, achievement and behaviour Who Is It For ? Primary and secondary teachers Heads and Deputies SENCOs Learning Support and Guidance staff Advanced Skills Teachers Parents Local Authority Support Services Community Development workers Early Years and School based Practitioners Course Content The course answers the questions: What do you do with the child who is isolated by their aggression and anger, through being different, disabled or new to the school or community? Practically how do we go about including high profile children or young people? How can we help some children be friends? We will cover: The importance of Welcome Inclusion values underpinning this work The Intentional Building of Relationships – ‘Circle of Friends’ work as an example Not doing it alone – The Importance of Teams in developing inclusive practice Practical setting up of circles of friends Lessons learned Stories of circles in primary and secondary mainstream schools ^ Circles of Friends Training in Kiev, Ukraine

Writing Clear Business Communication: In-House Training
By IIL Europe Ltd
Writing Clear Business Communication: In-House Training This program is about learning about the writing process and covers the full spectrum of documents used when corresponding in the workplace. The ability to write effectively comes naturally to some people, but for the vast majority, it is a task often approached with a mixture of trepidation and dread. Effective writing seldom, if ever, 'magically materializes' on the spot. In reality, it is most often the product of planning, writing, and rewriting. This is why writing is called a process; it must go through a series of steps before it is clear and complete. This program is about learning about the writing process and covers the full spectrum of documents used when corresponding in the workplace. The ability to write effectively comes naturally to some people, but for the vast majority, it is a task often approached with a mixture of trepidation and dread. However, the ability to communicate in the written word, for whatever purpose, is an important part of our working and personal lives and can have a direct impact on our ability to persuade, gain commitment or agreement and enhance understanding. Good writing sounds like talking on paper, which is why this program is focused on getting the message across and achieving the desired results using the 'keep it simple and direct' approach. What you Will Learn At the end of this program, you will be able to: Write effective e-mails, letters, memos, and reports Clearly articulate the message Achieve desired results from correspondence Organize content for maximum impact Format for enhanced understanding Choose the appropriate communication medium for each document Revise documents to increase clarity and impact Foundations Concepts Business writing as a form of professional communication How business writing compares to other forms of writing Characteristics of good business writing Challenges with business writing The Project Environment Business writing in the project environment The concept of art, science, and optics of business writing Art Economy Precision Action Music Personality Science Purpose, simple, compound, and complex sentence structures Techniques to engage the reader Point of view: tone, attitude, and humor Organization: opening, body, and closing Support and coherence Optics Visual optics Sound optics Feel optics Effective optics Efficient optics Email Formal vs. informal emails Suggestions for improving email communication Instant and text messaging Reports Common types of reports created Formatting of reports Guidelines for meeting minutes Contracts Types of contracts Common agreements Procurement documents Templates, Forms, and Checklists Templates Forms Checklists Other Formatting Good Documentation Practices Good documentation practices Data integrity in business communication

Making Your Sales Pitch
By OnlineCoursesLearning.com
MAKING YOUR SALES PITCH To persuade a prospective client to make a purchase, you need to make a convincing sales pitch. Your success will depend on your ability to understand your customer's needs, communicate your message and appear confident at all times. This course will teach you how to put together a compelling pitch that will help you build a strong rapport with a prospect and close the deal. It takes you step-by-step through the planning process so you can feel confident when making a pitch. You Will Learn: Why it's normal to feel anxious prior to making a sales pitch and the five steps you should take to ensure you are well-prepared How to speak and stand in a way that conveys quiet confidence and authority What to do if you make a mistake during your sales pitch The five most common mistakes people make when giving a sales pitch and how to overcome them Why it is important to get feedback on your pitch and why it's a good idea to watch other people make sales pitches Benefits of Taking This Course: This course will help you make convincing sales pitches that will give you a better chance of closing a deal This course will teach you what makes for a weak and strong sales pitch, and will therefore enable you to give meaningful feedback to colleagues who ask for your opinion on their selling skills This course will improve your public speaking abilities, which in turn will improve your confidence and make you a more persuasive sales person This course will teach you a number of transferable communication skills, which will be useful in both your professional and personal life

Advanced Well Engineering
By EnergyEdge - Training for a Sustainable Energy Future
About this Training Course Well engineers who are responsible for technically evaluating and authorizing programs for drilling or working over wells must have the required skills and competencies to safely design wells of varying nature. They also need to be able to confirm that well delivery and intervention programs generate intrinsic well control assurance. Such work programs must establish, verify, monitor and maintain suitable and sufficient barriers for the entire well lifecycle - from spud to abandonment. Well engineers must also be able to select a suitable drilling or workover rig, capable of safely performing the work within its operational envelope. This 3 full-day course aims to further develop and assess the knowledge required to work on and eventually, authorize a well delivery program as deemed fit for purpose. It also addresses elements of well control that must be embedded into well design, well work programming and equipment selection. This course is intended for participants who already have a sound understanding of the principles of the design and/or delivery of wells and with more than 3 years of relevant industry experience. Training Objectives By the end of this course, participants will be able to: Feel confident to design and plan drilling and workover activities while considering geological risks, formation pressures/strengths, and any integrity or well control concerns. Monitor wells operations and ensure that they can and will remain within the accepted design envelope. Assess risks and then apply mitigation or recovery methods in cases where design envelopes are threatened. Participants should be capable of assessing a drilling or workover program and then be able to answer the following key questions: Does the program delivery have a sound design and work plan that allows the well(s) to be drilled or worked over safely? Have we determined the appropriate kick tolerance for each open hole section and is it realistic for all drilling hazards that may be encountered? Have all drilling hazards been suitably assessed, and the associated risk mitigated to a level as low as reasonably practicable? Are there adequate, verifiable barriers in place throughout the operation and does everybody know their role and responsibility? And, as applicable, is the selected rig capable of implementing the work program? Target Audience This course is intended for personnel directly or indirectly involved in the preparation, review or authorization of drilling and workover programs. This includes: Well engineers and drilling supervisors who are responsible for planning and executing drilling and workover operations. Contractor well engineers, rig managers and other senior drilling staff. Senior well engineers and rig superintendents who are responsible for managing the delivery of a project or well. Technical authority holders who are responsible for licensing drilling and workover operations from a regulatory perspective. Assessment: A satisfactory command of critical knowledge and skills is assured by a 1+ hour closed book assessment. This assessment has a mix of multiple-choice questions (MCQs), calculations and answers that must be written up. The exam is taken electronically. Participants are provided with a suitable formula sheet. The pass mark for issuing a certificate is 70% and participants who are not successful will be issued with a certificate of attendance instead. Trainer Your expert course leader has over 45 years of experience in the Oil & Gas industry. During that time, he has worked exclusively in the well engineering domain. After being employed in 1974 by Shell, one of the major oil & gas producing operators, he worked as an apprentice on drilling rigs in the Netherlands. After a year, he was sent for his first international assignment to the Sultanate of Oman where he climbed up the career ladder from Assistant Driller, to Driller, to wellsite Petroleum Engineer and eventually on-site Drilling Supervisor, actively engaged in the drilling of development and exploration wells in almost every corner of this vast desert area. At that time, drilling techniques were fairly basic and safety was just a buzz word, but such a situation propels learning and the fruits of 'doing-the-basics' are still reaped today when standing in front of a class. After some seven years in the Middle East, a series of other international assignments followed in places like the United Kingdom, Indonesia, Turkey, Denmark, China, Malaysia, and Russia. Apart from on-site drilling supervisory jobs on various types of drilling rigs (such as helicopter rigs) and working environments (such as jungle and artic), he was also assigned to research, to projects and to the company's learning centre. In research, he was responsible for promoting directional drilling and surveying and advised on the first horizontal wells being drilled, in projects, he was responsible for a high pressure drilling campaign in Nigeria while in the learning centre, he looked after the development of new engineers joining the company after graduating from university. He was also involved in international well control certification and served as chairman for a period of three years. In the last years of his active career, he worked again in China as a staff development manager, a position he nurtured because he was able to pass on his knowledge to a vast number of new employees once again. After retiring in 2015, he has delivered well engineering related courses in Australia, Indonesia, Brunei, Malaysia, China, South Korea, Thailand, India, Dubai, Qatar, Kuwait, The Netherlands, and the United States. The training he provides includes well control to obtain certification in drilling and well intervention, extended reach drilling, high pressure-high temperature drilling, stuck pipe prevention and a number of other ad-hoc courses. He thoroughly enjoys training and is keen to continue taking classes as an instructor for some time to come. POST TRAINING COACHING SUPPORT (OPTIONAL) To further optimise your learning experience from our courses, we also offer individualized 'One to One' coaching support for 2 hours post training. We can help improve your competence in your chosen area of interest, based on your learning needs and available hours. This is a great opportunity to improve your capability and confidence in a particular area of expertise. It will be delivered over a secure video conference call by one of our senior trainers. They will work with you to create a tailor-made coaching program that will help you achieve your goals faster. Request for further information post training support and fees applicable Accreditions And Affliations

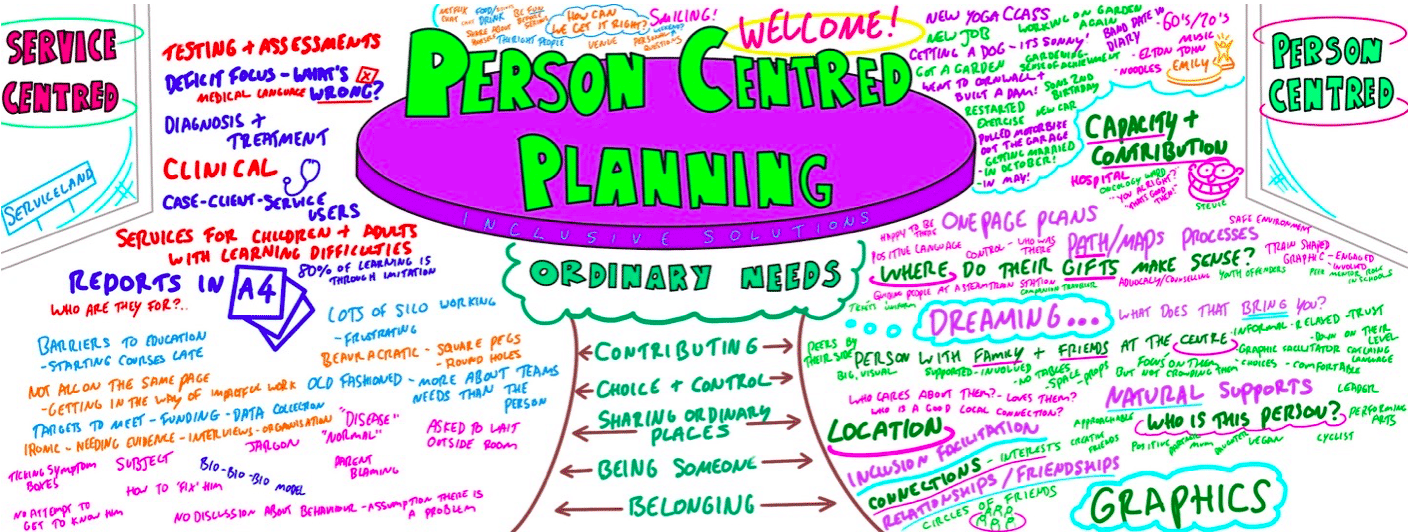
PERSON CENTRED PLANNING TRAINING
By Inclusive Solutions
Person Centred Planning (PCP) is a powerful tool for visioning, future planning and team building. It gets everyone on the same page and creates a progressive, constructive atmosphere so it is especially useful for people who are feeling ‘stuck’ or in a really desperate situation. The PCP processes we teach are called “PATH” and “MAPs”, and are both used for different situations. “To facilitate a group, family, team or organisation in thinking together around a given challenge or issue. Here is an opportunity to experience for real the person centred, futures planning tool – MAP/PATH” (Pearpoint, Forest, O’Brien. 1989). PCP can focus on an individual, with family and friends in the room supporting them, or focus on a group who want to set goals, and realise their potential as a team. PCP focuses on hopes and dreams, so is a very positive approach to planning, and utilises graphic facilitation, making it a very friendly way of working that is accessible to everyone. This unique, hands on PCP training course explores the difference between ‘person-centred thinking’ and ‘service-centred thinking’. Traditionally, we have not always listened deeply enough to the needs of those we are planning for. Often ‘medical model’ thinking dominates our planning for those with the most complex needs. Typically we plan ‘about’ rather than ‘with’ children and adults. We examine this ‘service centred’ approach that most professionals are used to, and question its limitations. This values based approach to inclusion will give participants the ‘theory’ behind why thinking and working in a person centred way is so important, and challenges people to strive for more for the people we are planning around. In addition to the knowledge and theory, this course empowers participants to facilitate their own Person Centred Plans using the PATH or MAPs process and provides the skills to do this effectively. Learning objectives Strengthen understanding of how to think in a person centred way Knowledge of the steps of PATH / MAPs process Ability to facilitate PATH/MAPs process Ability to graphically facilitate a PCP meeting Develop problem solving and planning skills Inclusive Solutions offer: We could provide training for a team of staff, or we could facilitate a PATH or MAP around a disabled person. We can also offer bespoke training packages, please enquire for more details. 1 day “Introduction to PCP” with up to 100 attendees focusing on ‘Person Centred Thinking’ – includes live demonstration of PATH or MAPs Process (for a member of the group / with a student and their family/friends). 2 day “PCP Skills training” – More skills focused, lots of practice. Includes Graphics academy, Process academy and Coaching (Best with under 30 attendees). 2 day “Introduction to PCP with Skills training” – includes live demonstration of PATH or MAPs process, Graphics academy, Process academy and Coaching (Best with under 30 attendees). Half day PATH or MAP for a disabled person, led by two experienced Inclusive Solutions facilitators. Full day PATH or MAP for a team, organisation or group such as a full school staff led by two experienced Inclusive Solutions facilitators. Typical Structure of 2-Day “Introduction to PCP with Skills” Training This course is most useful when delivered over 2 days so we have time to cover the ‘skills’ behind facilitating a PATH or a MAP. Here is an example of what usually happens. If you need us to, we can tailor any of our courses to suit your specific needs. Day 1 AM What makes a good welcome?Service centred thinking and working – what does it involve, how does it make people feel?Reflections on current practices – what is useful and what is harmful?Introduction to underpinning values of person centred thinking and working In depth exploration of the fundamentals of inclusion – encouraging identity, focusing on gifts and capacities Sharing success stories, and personal insight from experienced psychologistsShowcasing a number of practical PCP process in actionIntroduction to the “5 service accomplishments”, or “5 ordinary needs” PM Full PATH process demonstration, led by 2 experienced facilitators – one process facilitator and one graphic facilitatorVolunteers will make notes on what they see the facilitators doing and feedback at the end of the dayFeedback, Q&A Day 2 AM Graphics Academy – we will ease you into the world of graphic facilitation and show you how simple it really is – includes live coaching and graphics tutorial, then participants will practice on each other by facilitating the first 1 or 2 sections of the PATH Process Academy – we will give you some pointers about holding the group, and facilitating in an inclusive way, this is another chance to practice your new graphics skills PM The group is divided up, and volunteers are selected to facilitate PATH meetings The group then run the PATH’s simultaneously with an experienced coaches in the room to guide and to be available for questionsWe reconvene to feedback about the process and digest all we have learntBrief Q&A session and then final reflections
AutoCAD 3D modeling course
By Real Animation Works
Autocad face to face training customised and bespoke.
EC-Council Certified Ethical Hacker (CEH) v12
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for The Certified Ethical Hacking v12 course will significantly benefit security officers, auditors, security professionals, site administrators, and anyone who is concerned about the integrity of the network infrastructure. Overview Information security controls, laws, and standards. Various types of footprinting, footprinting tools, and countermeasures. Network scanning techniques and scanning countermeasures Enumeration techniques and enumeration countermeasures Vulnerability analysis to identify security loopholes in the target organization?s network, communication infrastructure, and end systems. System hacking methodology, steganography, steganalysis attacks, and covering tracks to discover system and network vulnerabilities. Different types of malware (Trojan, Virus, worms, etc.), system auditing for malware attacks, malware analysis, and countermeasures. Packet sniffing techniques to discover network vulnerabilities and countermeasures to defend against sniffing. Social engineering techniques and how to identify theft attacks to audit human-level vulnerabilities and social engineering countermeasures. DoS/DDoS attack techniques and tools to audit a target and DoS/DDoS countermeasures. Session hijacking techniques to discover network-level session management, authentication/authorization, and cryptographic weaknesses and countermeasures. Webserver attacks and a comprehensive attack methodology to audit vulnerabilities in webserver infrastructure, and countermeasures. Web application attacks, comprehensive web application hacking methodology to audit vulnerabilities in web applications, and countermeasures. SQL injection attack techniques, injection detection tools to detect SQL injection attempts, and countermeasures. Wireless encryption, wireless hacking methodology, wireless hacking tools, and Wi-Fi security tools. Mobile platform attack vector, android vulnerability exploitations, and mobile security guidelines and tools. Firewall, IDS and honeypot evasion techniques, evasion tools and techniques to audit a network perimeter for weaknesses, and countermeasures. Cloud computing concepts (Container technology, serverless computing), the working of various threats and attacks, and security techniques and tools. Penetration testing, security audit, vulnerability assessment, and penetration testing roadmap. Threats to IoT and OT platforms and defending IoT and OT devices. Cryptography ciphers, Public Key Infrastructure (PKI), cryptography attacks, and cryptanalysis tools. CEH provides an in-depth understanding of ethical hacking phases, various attack vectors, and preventative countermeasures. It will teach you how hackers think and act maliciously so you will be better positioned to setup your security infrastructure and defend against future attacks. An understanding of system weaknesses and vulnerabilities helps organizations strengthen their system security controls to minimize the risk of an incident. CEH was built to incorporate a hands-on environment and systematic process across each ethical hacking domain and methodology, giving you the opportunity to work towards proving the required knowledge and skills needed to achieve the CEH credential. You will be exposed to an entirely different posture toward the responsibilities and measures required to be secure. Now in its 12th version, CEH continues to evolve with the latest operating systems, tools, tactics, exploits, and technologies. 1 - Introduction to Ethical Hacking Information Security Overview Cyber Kill Chain Concepts Hacking Concepts Ethical Hacking Concepts Information Security Controls Information Security Laws and Standards 2 - 2 - Foot-printing and Reconnaissance Footprinting Concepts Footprinting through Search Engines Footprinting through Web Services Footprinting through Social Networking Sites Website Footprinting Email Footprinting Who is Footprinting DNS Footprinting Network Footprinting Footprinting through Social Engineering Footprinting Tools Footprinting Countermeasures 3 - Scanning Networks Network Scanning Concepts Scanning Tools Host Discovery Port and Service Discovery OS Discovery (Banner Grabbing/OS Fingerprinting) Scanning Beyond IDS and Firewall Draw Network Diagrams 4 - Enumeration Enumeration Concepts NetBIOS Enumeration SNMP Enumeration LDAP Enumeration NTP and NFS Enumeration SMTP and DNS Enumeration Other Enumeration Techniques Enumeration Countermeasures 5 - Vulnerability Analysis Vulnerability Assessment Concepts Vulnerability Classification and Assessment Types Vulnerability Assessment Solutions and Tools Vulnerability Assessment Reports 6 - System Hacking System Hacking Concepts Gaining Access Escalating Privileges Maintaining Access Clearing Logs 7 - Malware Threats Malware Concepts APT Concepts Trojan Concepts Virus and Worm Concepts Fileless Malware Concepts Malware Analysis Countermeasures Anti-Malware Software 8 - Sniffing Sniffing Concepts Sniffing Technique: MAC Attacks Sniffing Technique: DHCP Attacks Sniffing Technique: ARP Poisoning Sniffing Technique: Spoofing Attacks Sniffing Technique: DNS Poisoning Sniffing Tools Countermeasures Sniffing Detection Techniques 9 - Social Engineering Social Engineering Concepts Social Engineering Techniques Insider Threats Impersonation on Social Networking Sites Identity Theft Countermeasures 10 - Denial-of-Service DoS/DDoS Concepts DoS/DDoS Attack Techniques BotnetsDDoS Case Study DoS/DDoS Attack Tools Countermeasures DoS/DDoS Protection Tools 11 - Session Hijacking Session Hijacking Concepts Application Level Session Hijacking Network Level Session Hijacking Session Hijacking Tools Countermeasures 12 - Evading IDS, Firewalls, and Honeypots IDS, IPS, Firewall, and Honeypot Concepts IDS, IPS, Firewall, and Honeypot Solutions Evading IDS Evading Firewalls IDS/Firewall Evading Tools Detecting Honeypots IDS/Firewall Evasion Countermeasures 13 - Hacking Web Servers Web Server Concepts Web Server Attacks Web Server Attack Methodology Web Server Attack Tools Countermeasures Patch Management Web Server Security Tools 14 - Hacking Web Applications Web Application Concepts Web Application Threats Web Application Hacking Methodology Web API, Webhooks, and Web Shell Web Application Security 15 - SQL Injection SQL Injection Concepts Types of SQL Injection SQL Injection Methodology SQL Injection Tools Evasion Techniques Countermeasures 16 - Hacking Wireless Networks Wireless Concepts Wireless Encryption Wireless Threats Wireless Hacking Methodology Wireless Hacking Tools Bluetooth Hacking Countermeasures Wireless Security Tools 17 - Hacking Mobile Platforms Mobile Platform Attack Vectors Hacking Android OS Hacking iOS Mobile Device Management Mobile Security Guidelines and Tools 18 - IoT and OT Hacking IoT Hacking IoT Concepts IoT Attacks IoT Hacking Methodology IoT Hacking Tools Countermeasures OT Hacking OT Concepts OT Attacks OT Hacking Methodology OT Hacking Tools Countermeasures 19 - Cloud Computing Cloud Computing Concepts Container Technology Serverless Computing Cloud Computing Threats Cloud Hacking Cloud Security 20 - Cryptography Cryptography Concepts Encryption Algorithms Cryptography Tools Public Key Infrastructure (PKI) Email Encryption Disk Encryption Cryptanalysis Countermeasures Additional course details: Nexus Humans EC-Council Certified Ethical Hacker (CEH) v.12 training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the EC-Council Certified Ethical Hacker (CEH) v.12 course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Effective Interpersonal Communication for Business Professionals
By Nexus Human
Duration 1 Days 6 CPD hours This course is intended for The typical students of this course will be business professionals who want to enhance their communication skills to interact more effectively with superiors, colleagues, team members, customers, and vendors, and ultimately improve their overall job performance. Overview Interact productively with others in the workplace on a day-to-day basis. Build positive relationships with diverse individuals. Consider organizational communication systems. Communicate with peers. Communicate with supervisors. Communicate with external people. Communicate during conflict and change. To be successful in the workplace, you must be able to effectively communicate and cooperate with coworkers and external people. Private classes on this topic are available. We can address your organization?s issues, time constraints, and save you money, too. Contact us to find out how. Prerequisites To ensure your success in this course, you should have some level of work experience in any of a variety of organizational settings. 1. Interacting with Others Topic A- Understand the Communication Process Topic B- Apply Core Communication Skills Topic C- Observe Nonverbal Communication 2. Building Positive Relationships Topic A- Create Connection Topic B- Adapt Appropriately to Different Communication Styles Topic C- Accommodate Diversity 3. Considering Organizational Communication Systems Topic A- Analyze Organizational Culture Topic B- Ensure Communication Flows Effectively 4. Communicating with Peers Topic A- Interact Effectively with Peers Topic B- Work Productively in a Group Topic C- Engage in Productive Meetings Topic D- Lead a Team 5. Communicating with Supervisors Topic A- Communicate with Different Supervisor Styles Topic B- Discuss Important Topics with Your Supervisor 6. Communicating with External People Topic A- Interact Effectively with Customers Topic B- Work Productively with Vendors 7. Communicating During Conflict and Change Topic A- Communicate Through Conflict Topic B- Communicate Through Change Additional course details: Nexus Humans Effective Interpersonal Communication for Business Professionals training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Effective Interpersonal Communication for Business Professionals course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Working Safely-IIRSM & CPD Approved
By BAB Business Group
Working safely is in the interest and concern of all staff, both employers and employees. Health and safety is one of the few areas where the law places specific duties specifically on employees so a knowledge of where this applies and how to ensure that it is adhered to is vital to protect individuals and businesses. Most workers feel that accidents are something that only happens to other people. The reality is that too many workers are coming to harm by not observing Health and Safety laws and not working to safe systems of work - the physical, mental and financial burden of these accidents can have a huge impact on themselves, their families and their colleagues. The course covers a wide range of topics including fire safety, asbestos awareness, working at height, COSHH, PPE and electricity. It also covers methods for improving safety performance and methods of protecting the environment.
