- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
Behaviours that Challenge
By Prima Cura Training
Challenging behaviour is causing increasing concern today as many individuals have increasing levels of stress and uncertainty in their lives. Understanding the causes of challenging behaviour is the first step towards finding ways to support individuals and manage their behaviour.

Fire Safety Awareness
By Prima Cura Training
A fire, or similar emergency can happen at any time in your workplace. Fire safety awareness refers to the knowledge and understanding of the precautions and measures that individuals can take to prevent fires from occurring and to minimize the damage caused by fires. This course will ensure that your staff and their managers all know what to do to maximize safety in the event of a fire or a gas leak.

Crisis communications
By Rough House Media
Are you confident your organisation could cope if a bad news story went viral and you were besieged by the media? Would you be able to fend off a determined and aggressive journalist, take control and deliver your key messages? Our crisis communications courses show you how to cope when your organisation is under fire, and protect your good name. We can: Train your spokespeople to handle challenging interviews, pitting their wits against a hostile reporter Train your PR team to manage communications during an unfolding crisis Deliver a fast-paced crisis simulation where your team have to decide how to handle the press during an unfolding emergency Facilitate a crisis strategy workshop, where we work together to develop your crisis communications strategy All of our crisis communications courses are bespoke, so we will design each one to meet your specific needs. Areas we can cover include: How a crisis can escalate in seconds How journalists respond to bad news stories How to develop effective key messages & write holding statements How to manage your social media How to take control of an interview and get your message across How to handle press conferences and doorsteps Venue We deliver courses in the most appropriate format for your circumstances – whether face to face or online. Face to face courses are portable: they can be held in purpose-built studios, at your own offices or at an external venue. In the latter two cases, we create a mock studio for the practical exercises. Online courses give you flexibility and enable you to offer training to delegates from all over the world. We have run virtual courses for people from the Far East, South Asia, North America and Europe, as well as the UK.

Women in Construction Management Course
By The Power Within Training & Development Ltd
Supporting Women in Leadership Throughout The UK Our women in leadership course is specifically designed to target challenges and support women in developing their leadership and management careers. AWARD WINNING LEADERSHIP DEVELOPMENT PROGRAMME Discover Our Women in Construction Management Course The Power Within is dedicated to helping women in construction across England and Scotland achieve business success through our Motivational Intelligence framework. Motivational Intelligence is the third level of intelligence, and the science behind it has won a Nobel Prize. Our women leadership in construction course supports women by improving their motivation, self-belief, decision-making, and leadership skills. This programme is designed to help female business leaders adapt more quickly to their environment, handle adversity more effectively, take productive action, and thrive during times of change. Each is a vital skill needed in today’s ever-changing business environment. When completed, you’ll have the skills needed to make decisions more effectively that help your business grow, become more resilient, and take opportunities when others are stuck. "This course has completely changed my outlook on my responsibilities as a manager/leader. In 26 years with Pfizer, I have never participated in a programme that has as profoundly changed my perspective on my role, my responsibilities and my ability to positively impact my team." FEMALE DIRECTOR OF BUSINESS SERVICES, PFIZER LEADING WITH MOTIVATIONAL INTELLIGENCE What is our Women in Construction Course? In the past five years, we’ve supported thousands of business leaders and managers in nurturing the skills and mindset needed to achieve and exceed their business goals. The Power Within knows women are incredibly effective and consistent at applying our Motivational Intelligence techniques to their lives and business. Our women in construction management course is designed to give you the skills you need to take charge of your business and ensure constant growth while future-proofing your business. The training is perfect for women in construction who are managers or leaders looking to: Quickly Adapt Their Team to Change Effectively Mentor Every Team Member Improve Communication and Collaboration Gain More Buy-In to New Goals or Strategies Transform Their Team Culture Increase Initiative and Self-Motivation Across Their Team How We Help Women in the Construction Industry Our course focuses on imparting fundamental skills, tactical best practices, and powerful insights into the human side of the business. You’ll be provided with valuable knowledge needed to be successful leaders and managers of all levels. We’ll focus on addressing the challenges new businesses around the world face, like leading teams and developing businesses in turbulent and transitional times as well as overcoming the challenges of being women in the construction industry. Throughout the course, particular emphasis is given to helping leaders raise motivational intelligence and foster a growth mindset within their team. LEADING WITH MOTIVATIONAL INTELLIGENCE Our Leading with Motivational Intelligence (MQ) Executive Diploma Programme is specifically designed to help participants create the “complete game” of leadership and management. Leveraged by more than 40% of the largest Fortune 500 companies and implemented around the world, the Leading with Motivational Intelligence (MQ) consistently receives a participant buy-in rate in excess of 97%. However, the most important statistic is: 12 months after completing the course more than 93% of participants continue to use the skills and techniques taught on a daily basis. SQA APPROVED EXECUTIVE DIPLOMA What Skills Do We Help Women in Construction Develop? The skills we teach through our women in construction management courses are delivered through seven modularised sessions, each between three and three-and-a-half hours per session, with all sessions starting at 9:30 am via Zoom. An additional two hours per week is spent working on the online training assignments and leadership development plan. Each session will provide the education and information needed to establish yourself in your business. Here is more information regarding each session and the skills taught: SESSION 1: SELF-LEADERSHIP & THE SECRET TO PERSONAL SUCCESS Our first module is focused on setting course expectations and creating the right environment for learning. We’ll introduce the format and logistics, then discuss leading through turbulent times and how we can take control of ourselves, our thoughts, and our actions to lead growth. There is also a discussion on adult learning techniques and how leaders can leverage them to improve the effectiveness of their teams. We’ll also explore how turbulence and transition have changed how we manage and lead our teams. SESSION 2: THE ROLE OF INTELLIGENCE WHEN LEADING In this session, we’ll discuss the three levels of human intelligence and show how they each play in an individual’s performance and behaviors. Through two distinct mindsets, you’ll be shown how an individual’s motivational intelligence ultimately influences their emotional intelligence and intelligence quotient (IQ). Depending on which mindset a person operates under ultimately dictates their view of themselves, opportunities, and the work at which they will allow themselves to succeed. Finally, we’ll discuss switching your team to a growth mindset. SESSION 3: THE PILLARS OF HUMAN PERFORMANCE Completing this session will allow you to deconstruct the components that create a motivational intelligence growth mindset. Through discussion, you’ll see how most organizational challenges can be directly tied back to lapses in these components. We’ll review the leaders who’ve had the most significant influence on the meeting participants and shows the commonalities that make these leaders stand out. Lastly, we’ll introduce terminology, tools, and techniques that leaders can leverage to better coach and mentor their team. SESSION 4: MANAGEMENT VERSUS LEADERSHIP: THE TWO CRITICAL AND CO-DEPENDENT SKILLSETS FOR CREATING TEAM SUCCESS We’ll discuss the difference between a manager’s and a leader’s focus. The discussion focuses on the two most common management mistakes and how they undermine team culture and individual performance. The final debate focuses on the five critical best practices of excellent management, including clearly defining and communicating goals, creating alignment and buy-in, setting proper expectations, monitoring performance, and recognizing and rewarding performance. Our final portion will work to define what management is. Session 5: Exploring and Defining Leadership: Dispelling the Myths that Surround It Session 5 strives to define leadership. Building on this definition is a follow-up discussion regarding how people develop their leadership abilities. We’ll explore the underpinnings of what creates a successful leader. It also includes the importance of asking questions and active listening. We’ll review the five behavioral characteristics associated with motivational intelligence and how leaders can assess the relative strengths or weaknesses of the characteristics within their team. Lastly, we’ll explore great leaders’ five critical best practices, including communicating a compelling vision, modeling the correct behaviors, establishing a team culture anchored in responsibility, consistently building team confidence and self-esteem, and proactively coaching and mentoring. SESSION 6: BUILDING A LEADERSHIP TOOLBOX FOSTERING ADAPTABILITY, RESILIENCE, AND COURAGE We’ll provide information regarding tools and techniques that leaders can utilize to foster greater accountability and ownership win their teams. The Power Within will explore self-esteem’s critical role in the relative strength or weakness of a person’s motivational intelligence and adaptability in life. We’ll discuss how self-esteem has formed and how it will influence how a person interprets feedback in life. Lastly, we’ll explore levels of self-esteem and the associated behaviors of each. SESSION 7: HELPING EMPLOYEES DEVELOP A HEALTHY PERSPECTIVE AND RESILIENT ATTITUDE During the final session, we’ll explore self-esteem’s critical role in the relative strength or weakness of a person’s motivational intelligence and adaptability in life. We’ll talk about how self-esteem is formed and how it influences how a person interprets feedback. Finally, we’ll explore levels of self-esteem and the behaviors of each and the influence of comfort zones, and the tools that leaders can use to help people escape the fear of change. Our Course Leaders The Power Within was founded by husband and wife team James and Enas Fleming, to inspire people worldwide to think bigger, be better, and achieve more. They both work on a personal level with individuals, businesses, and organisations to help them create leaders and build environments where they can thrive. James and Enas challenge the limits with the Motivational Intelligence formula to help you broaden your perspective and create a future on your terms. Here is more about your course instructors: James Fleming James Fleming – James Fleming, the co-creator of The Power Within. He wanted to inspire people around the world to think better, be better, and achieve more. James believes everyone can do whatever they set their minds to. Founding The Power Within allowed James to turn that deep knowledge into a business that helps others think bigger, better, and achieve more daily. He strives to give leaders the tools and knowledge to achieve their full potential while increasing their self-confidence and self-belief through the Motivational Intelligence Revolution. James wants to support today’s businesses to become tomorrow’s leaders. Mari Steyn Mari is the go-to person for building self-esteem, offering new perspectives and stepping up in Life. With an endless abundance of excitement and love for all people, combined with degrees in Psychology, Knowledge and Information Management and is a Master NLP and Transformation Coach and International NLP and Coaching Trainer and Executive Coach, Mari offers an attractive, fresh, expert approach to Emotional Freedom, Motivational Intelligence, Leadership Development and ReWriting your Story. We undoubtedly have the power within to alchemize ourselves and any situation! Seeing the light go on in someone’s eyes is my ultimate joy. Take Charge with Our Women in Construction Course The Power Within is a Motivational Intelligence company dedicated to helping businesses and leaders become more accountable, resilient, adaptable, and capable of handling all challenges, regardless of the complexity. Our women in construction management course build upon best practices, strategic insights, and lessons learned over three decades of building leadership universities for Fortune 500 companies. Throughout the course, emphasis is given to helping leaders raise their motivational intelligence and foster a growth mindset within their team. You’ll gain the skills you need to successfully lead your team and overcome adversity while ensuring your company is profitable. To learn more about our course or to register, reach out today.

Online Options
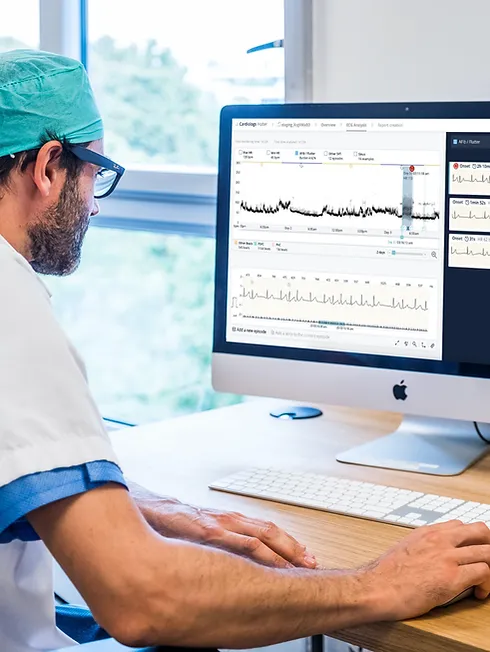
Show all 469Learn how to perform and read an ECG ... Nationally Recognised Qualification OCN Accredited - Level 3 (advanced level) CPD Accredited - The CPD Certification Service Introduces you to the fundamentals of setting up and operating an ECG machine Includes patient preparation Produce a valid (error free) ECG Learn and understand ECG traces Recognise recordings that require urgent attention Basic understanding of English language required OPEN TO ALL APPLICANTS VIRTUAL CLASSROOM OPTION INCLUDES COMPREHENSIVE PRACTISE@HOME ECG TRAINING KIT Final interpretation of all ECG recordings is the responsibility of a medical professional.
Cisco Network Services Orchestrator Advanced Design (NSO300)
By Nexus Human
Duration 4 Days 24 CPD hours This course is intended for The primary audience for this course is system installers, system integrators, system administrators, network administrators, and solutions designers. Overview At the end of this course, you will be able to: Describe the NSO's transactional application framework and mapping model options Describe the Reactive Fastmap design pattern and the NSO Configuration Database (CDB) subscriber in the NSO Transaction model Simplify packages to remove the need for subscriber applications, scale orchestration solutions, and integrate NSO with external systems (east-west integration)Describe the Cisco ESC architecture and integration with NSO, and how the NSO VNF Orchestration (VNFO) Release 2 bundle interacts with ESC for orchestration This course explores how to create advanced services using the NSO application framework and Python scripting with both new and existing Layer 3 Multiprotocol Label Switching (MPLS) VPN services. Students will also learn how to manage and scale these services, and how to use NSO Network Functions Virtualization (NFV) orchestration features and Cisco Elastic Services Controller (ESC) to manage Virtualized Network Functions (VNFs). Cisco NSO Programmability NSO Application Framework NSO Python Scripting NSO Python and Template-Based Services Resources Augmenting Cisco NSO Service Service Lifecycle and Integration Options Overview Greenfield Layer 3 MPLS VPN Service Brownfield Layer 3 MPLS VPN Service Managed Services Managed Services Overview Stacked Service Design Overview Design-Managed Network Services Scaling Service Orchestration Cisco NSO Network Functions Virtualization (NFV) Orchestration ETSI MANO Cisco ESC Cisco NSO Orchestration Additional course details: Nexus Humans Cisco Network Services Orchestrator Advanced Design (NSO300) training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Cisco Network Services Orchestrator Advanced Design (NSO300) course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Cisco Service Provider 5G Technologies Foundations v1.0 (SPMBL100)
By Nexus Human
Duration 4 Days 24 CPD hours This course is intended for This course is designed for network and software engineers and hold job roles such as: Network administrator Network engineer Network manager System engineer Project manager Network designer Overview After taking this course, you should be able to: Describe mobile network architecture basics List enabling technologies for 5G and describe 5G key use cases Perform basic operations on a Cisco 5G NSA mobile packet core Describe the Cisco 5G Converged SDN Transport Architecture Describe Cisco NFVI and perform basic operations using Cisco ESC and Cisco Virtualized Infrastructure Manager (VIM) Describe Cisco service provider automation and orchestration solutions to deploy and manage 5G network functions Describe the Cisco Ultra Cloud Core architecture and deploy the Cisco SMI Explain the 5G ready distributed Telco DC with Cisco ACI solution Describe the Cisco 5G security architecture The Cisco Service Provider 5G Technologies Foundations (SPMBL100) v1.0 course introduces mobile network components, basic 5G concepts, and features of 5G technology including faster data speeds, higher device capacity, and improved user experience. You will examine the mobile packet core solutions, 5G transport architecture, and Cisco© automation and orchestration tools used in 5G networks. You will also learn about the Cisco 5G Non-standalone (NSA) and the Cisco Ultra Cloud Core 5G standalone (SA) platform solutions, the Cisco 5G converged Software-Defined Networking (SDN) transport architecture, and Cisco edge computing solutions. You will study the Cisco Network Function Virtualization (NFVI) architecture, Cisco Network Services Orchestrator (NSO), and Cisco Elastic Services Controller (ESC). You will learn how 5G is distributed with Telco Data Center (DC) with Cisco Application Centric Infrastructure (Cisco ACI©). And finally, Zero-Touch Provisioning (ZTP), Cisco Crosswork?, and the Cisco 5G security architecture will also be presented. Mobile Network Fundamentals 5G Key Use Cases Examining Mobile Network Components Enabling Technologies for 5G Introduction to 5G NR Characteristics Cloud Radio Access network (RAN) Cisco 5G NSA Solution 5G NSA Basics 5G NSA StarOS Configurations Cisco 5G Converged SDN Transport Architecture Cisco 5G Transport Ready Devices Application Awareness and Network Slicing with Segment Routing Cisco NFV Infrastructure, Cisco Virtualized Network Functions (VNFs), Cisco VIM, and Cisco ESC NFVI and SDN Architecture Overview Cisco VIM Pod Configurations Cisco Service Provider Automation and Orchestration Telemetry Basics ZTP Fundamentals Cisco Ultra Cloud Core Cisco Ultra Cloud Core Basics Kubernetes and Docker Fundamentals 5G Ready Distributed DC with Cisco ACI Cisco ACI in Telco Data Centers 5GC Deployment Mitigating Threats in 5G Introduction to 5G Cybersecurity Risks Mitigating 5G Cybersecurity Risks

EC-Council Certified Ethical Hacker (CEH) v12
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for The Certified Ethical Hacking v12 course will significantly benefit security officers, auditors, security professionals, site administrators, and anyone who is concerned about the integrity of the network infrastructure. Overview Information security controls, laws, and standards. Various types of footprinting, footprinting tools, and countermeasures. Network scanning techniques and scanning countermeasures Enumeration techniques and enumeration countermeasures Vulnerability analysis to identify security loopholes in the target organization?s network, communication infrastructure, and end systems. System hacking methodology, steganography, steganalysis attacks, and covering tracks to discover system and network vulnerabilities. Different types of malware (Trojan, Virus, worms, etc.), system auditing for malware attacks, malware analysis, and countermeasures. Packet sniffing techniques to discover network vulnerabilities and countermeasures to defend against sniffing. Social engineering techniques and how to identify theft attacks to audit human-level vulnerabilities and social engineering countermeasures. DoS/DDoS attack techniques and tools to audit a target and DoS/DDoS countermeasures. Session hijacking techniques to discover network-level session management, authentication/authorization, and cryptographic weaknesses and countermeasures. Webserver attacks and a comprehensive attack methodology to audit vulnerabilities in webserver infrastructure, and countermeasures. Web application attacks, comprehensive web application hacking methodology to audit vulnerabilities in web applications, and countermeasures. SQL injection attack techniques, injection detection tools to detect SQL injection attempts, and countermeasures. Wireless encryption, wireless hacking methodology, wireless hacking tools, and Wi-Fi security tools. Mobile platform attack vector, android vulnerability exploitations, and mobile security guidelines and tools. Firewall, IDS and honeypot evasion techniques, evasion tools and techniques to audit a network perimeter for weaknesses, and countermeasures. Cloud computing concepts (Container technology, serverless computing), the working of various threats and attacks, and security techniques and tools. Penetration testing, security audit, vulnerability assessment, and penetration testing roadmap. Threats to IoT and OT platforms and defending IoT and OT devices. Cryptography ciphers, Public Key Infrastructure (PKI), cryptography attacks, and cryptanalysis tools. CEH provides an in-depth understanding of ethical hacking phases, various attack vectors, and preventative countermeasures. It will teach you how hackers think and act maliciously so you will be better positioned to setup your security infrastructure and defend against future attacks. An understanding of system weaknesses and vulnerabilities helps organizations strengthen their system security controls to minimize the risk of an incident. CEH was built to incorporate a hands-on environment and systematic process across each ethical hacking domain and methodology, giving you the opportunity to work towards proving the required knowledge and skills needed to achieve the CEH credential. You will be exposed to an entirely different posture toward the responsibilities and measures required to be secure. Now in its 12th version, CEH continues to evolve with the latest operating systems, tools, tactics, exploits, and technologies. 1 - Introduction to Ethical Hacking Information Security Overview Cyber Kill Chain Concepts Hacking Concepts Ethical Hacking Concepts Information Security Controls Information Security Laws and Standards 2 - 2 - Foot-printing and Reconnaissance Footprinting Concepts Footprinting through Search Engines Footprinting through Web Services Footprinting through Social Networking Sites Website Footprinting Email Footprinting Who is Footprinting DNS Footprinting Network Footprinting Footprinting through Social Engineering Footprinting Tools Footprinting Countermeasures 3 - Scanning Networks Network Scanning Concepts Scanning Tools Host Discovery Port and Service Discovery OS Discovery (Banner Grabbing/OS Fingerprinting) Scanning Beyond IDS and Firewall Draw Network Diagrams 4 - Enumeration Enumeration Concepts NetBIOS Enumeration SNMP Enumeration LDAP Enumeration NTP and NFS Enumeration SMTP and DNS Enumeration Other Enumeration Techniques Enumeration Countermeasures 5 - Vulnerability Analysis Vulnerability Assessment Concepts Vulnerability Classification and Assessment Types Vulnerability Assessment Solutions and Tools Vulnerability Assessment Reports 6 - System Hacking System Hacking Concepts Gaining Access Escalating Privileges Maintaining Access Clearing Logs 7 - Malware Threats Malware Concepts APT Concepts Trojan Concepts Virus and Worm Concepts Fileless Malware Concepts Malware Analysis Countermeasures Anti-Malware Software 8 - Sniffing Sniffing Concepts Sniffing Technique: MAC Attacks Sniffing Technique: DHCP Attacks Sniffing Technique: ARP Poisoning Sniffing Technique: Spoofing Attacks Sniffing Technique: DNS Poisoning Sniffing Tools Countermeasures Sniffing Detection Techniques 9 - Social Engineering Social Engineering Concepts Social Engineering Techniques Insider Threats Impersonation on Social Networking Sites Identity Theft Countermeasures 10 - Denial-of-Service DoS/DDoS Concepts DoS/DDoS Attack Techniques BotnetsDDoS Case Study DoS/DDoS Attack Tools Countermeasures DoS/DDoS Protection Tools 11 - Session Hijacking Session Hijacking Concepts Application Level Session Hijacking Network Level Session Hijacking Session Hijacking Tools Countermeasures 12 - Evading IDS, Firewalls, and Honeypots IDS, IPS, Firewall, and Honeypot Concepts IDS, IPS, Firewall, and Honeypot Solutions Evading IDS Evading Firewalls IDS/Firewall Evading Tools Detecting Honeypots IDS/Firewall Evasion Countermeasures 13 - Hacking Web Servers Web Server Concepts Web Server Attacks Web Server Attack Methodology Web Server Attack Tools Countermeasures Patch Management Web Server Security Tools 14 - Hacking Web Applications Web Application Concepts Web Application Threats Web Application Hacking Methodology Web API, Webhooks, and Web Shell Web Application Security 15 - SQL Injection SQL Injection Concepts Types of SQL Injection SQL Injection Methodology SQL Injection Tools Evasion Techniques Countermeasures 16 - Hacking Wireless Networks Wireless Concepts Wireless Encryption Wireless Threats Wireless Hacking Methodology Wireless Hacking Tools Bluetooth Hacking Countermeasures Wireless Security Tools 17 - Hacking Mobile Platforms Mobile Platform Attack Vectors Hacking Android OS Hacking iOS Mobile Device Management Mobile Security Guidelines and Tools 18 - IoT and OT Hacking IoT Hacking IoT Concepts IoT Attacks IoT Hacking Methodology IoT Hacking Tools Countermeasures OT Hacking OT Concepts OT Attacks OT Hacking Methodology OT Hacking Tools Countermeasures 19 - Cloud Computing Cloud Computing Concepts Container Technology Serverless Computing Cloud Computing Threats Cloud Hacking Cloud Security 20 - Cryptography Cryptography Concepts Encryption Algorithms Cryptography Tools Public Key Infrastructure (PKI) Email Encryption Disk Encryption Cryptanalysis Countermeasures Additional course details: Nexus Humans EC-Council Certified Ethical Hacker (CEH) v.12 training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the EC-Council Certified Ethical Hacker (CEH) v.12 course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Cisco Implementing Automation for Cisco Service Provider Solutions v1.0 (SPAUI)
By Nexus Human
Duration 3 Days 18 CPD hours This course is intended for This course is designed for Service Provider networking professionals in job roles such as: Network administrators Network architects Network designers Network engineers Network managers Network Operations Center (NOC) personnel Network supervisors Overview After taking this course, you should be able to: Use NETCONF and RESTCONF programmability protocols on Cisco devices Describe and use tools to validate YANG data models on Cisco devices Describe and configure model-driven telemetry on Cisco devices Describe and configure network traffic automation with Cisco XTC Describe and use network automation tools that utilize SSH Automate service provider network configuration with Cisco NSO Describe how to automate virtualized resources with Cisco ESC Describe how to automate service provider WAN with Cisco WAE This course prepares you to implement and support automation solutions in a Service Provider network infrastructure, using network programmability principles, protocols, tools, and mechanisms. Through a combination of lessons and hands-on labs, you will learn to deploy, configure, monitor, and operate Service Provider network environments using modern data models. These models allow you to represent operational data and new network management protocols in order to administer hundreds or thousands of devices in a single operation, replacing traditional, time-consuming, error prone, device-by-device Command Line Interface (CLI) management. The course also introduces powerful automation solutions that can streamline network operations. This course also prepares you for the CCNP-Service Provider concentration exam 300-535. Implementing Network Device Programmability Interfaces with NETCONF and RESTCONF Implement NETCONF Protocol Implement RESTCONF Protocol Implementing Model-Driven Programmability with YANG YANG Data Models YANG Tools YANG Development Kit Implementing Model-Driven Telemetry Implementing Model-Driven Telemetry with gRPC Implementing Model-Driven Telemetry with gNMI Automating Service Provider Network Traffic with Cisco XTC Cisco XTC Fundamentals Configure Cisco XTC Automating Networks with Tools That Utilize SSH Implement Device Configurations with Python Netmiko Library Implement Device Configurations with Ansible Playbooks Orchestrating Network Services with Cisco NSO Cisco NSO Fundamentals Cisco NSO Device Manager Cisco NSO Services Implement Device Configurations with Python Automating Virtualized Resources with Cisco Elastic Services Controller Cisco ESC Architecture Cisco ESC Resource Management Automating the WAN with Cisco WAE Describe the Cisco WAE Components Additional course details: Nexus Humans Cisco Implementing Automation for Cisco Service Provider Solutions v1.0 (SPAUI) training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Cisco Implementing Automation for Cisco Service Provider Solutions v1.0 (SPAUI) course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

SOLD OUT! 12th December Maddy Belton #Agent121. Looking for: MG, YA, CHILDREN'S NON-FICTION, ADULT FICTION
5.0(1)By I Am In Print
LOOKING FOR: MG, YA AND ADULT SCI-FI / FANTASY, CHILDREN'S NON-FICTION After graduating from St Andrews University with a degree in English Literature and Art History, Maddy followed her love of literature to an internship at non-fiction literary agency Graham Maw Christie. At GMC, Maddy worked her way up to Agent and built a list of authors who wrote for both for adults and children, spanning history, tarot, and nature writing. An avid reader of anything magical, Maddy joined Madeleine Milburn in 2022 to build a list specialising in SFF. Maddy would like to see SFF across all genres for all ages, including: grim dark, thriller, historical, romance, cosy fantasy, sci-fi, epic, YA fantasy, dark academia, contemporary fantasy, fantasy middle-grade, mythology, fairy tale and queer fantasy. Inspiring children’s non-fiction. She loves worlds to get lost in, adventures that transform what it means to be a hero, and unique magic that offers as many problems as solutions. She likes books that make her cry and books that change her mind. Above all, when she finishes a story about another world, she wants it to have taught her a lesson which helps her live in this one. She loves all fantasy, but favours richly imagined, complex worlds with a history to discover and a future to protect. Worldbuilding is one of her favourite aspects of this genre and she is always looking for a new, dense world with series potential. Think Brandon Sanderson’s Cosmere or the Marvel Cinematic Universe – the bigger the better! She also likes character-driven fantasy with a diverse cast to root for (or root against) and she wants to see a range of different relationships depicted authentically. She particularly like epics that dip into big, universal themes such as grief, climate change, or war and which ask impossible questions in the vein of R.F. Kuang or N.K. Jemisin. She is also excited by authors that play with form and language in a fantasy setting. In YA, she is looking for much the same as in an adult fantasy, but with younger protagonists and a closer focus on relationships. She wants to see the tropes she knows and loves in new and exciting forms and her favourite YA books often centre around belonging and becoming. She likes a dash of romance in everything, because she is sentimental that way, but it’s particularly important in the YA space. Sci-fi is a big passion of hers, especially when it comes with a strong hook. She is a huge fan of Becky Chamber’s The Long Way to a Small Angry Planet and Michaiah Johnson’s The Space Between Worlds. She likes space as a metaphor, and would love something that explores different alien species. Please send her your space operas and sci-fi romances which combine space, magic and mayhem! In fantasy middle grade, she favours whimsy and animal companions; she would love to follow a group of kids through magic school. She tends to look for plenty of humour with a strong friendship at the centre, and she wants middle grade stories which engage with the concerns of children growing up as well as offering an all-important escape (preferably on a dragon/unicorn’s back). She is also looking for children’s non-fiction for all ages. In this space, she wants something as creative as it is informative, and thinks diverse voices are increasingly important. Maddy would like you to submit a covering letter, one page synopsis and the first three chapters (Max 5000 words) of your completed manuscript in a single word document. (In addition to the paid sessions, Maddy is kindly offering one free session for low income/under-represented writers. Please email agent121@iaminprint.co.uk to apply, outlining your case for this option which is offered at the discretion of I Am In Print). By booking you understand you need to conduct an internet connection test with I Am In Print prior to the event. You also agree to email your material in one document to reach I Am In Print by the stated submission deadline and note that I Am In Print take no responsibility for the advice received during your agent meeting. The submission deadline is: Thursday 28 November 2024

Certified Information Security Manager (CISM)
By Nexus Human
Duration 3 Days 18 CPD hours This course is intended for The intended audience for this course is information security and IT professionals, such as network administrators and engineers, IT managers, and IT auditors, and other individuals who want to learn more about information security, who are interested in learning in-depth information about information security management, who are looking for career advancement in IT security, or who are interested in earning the CISM certification. Overview Establish and maintain a framework to provide assurance that information security strategies are aligned with business objectives and consistent with applicable laws and regulations. Identify and manage information security risks to achieve business objectives. Create a program to implement the information security strategy. Implement an information security program. Oversee and direct information security activities to execute the information security program. Plan, develop, and manage capabilities to detect, respond to, and recover from information security incidents. In this course, students will establish processes to ensure that information security measures align with established business needs. Prerequisites Information security governance Information risk management Information security program development Information security program management Incident management and response 1 - Information Security Governance Develop an Information Security Strategy Align Information Security Strategy with Corporate Governance Identify Legal and Regulatory Requirements Justify Investment in Information Security Identify Drivers Affecting the Organization Obtain Senior Management Commitment to Information Security Define Roles and Responsibilities for Information Security Establish Reporting and Communication Channels 2 - Information Risk Management Implement an Information Risk Assessment Process Determine Information Asset Classification and Ownership Conduct Ongoing Threat and Vulnerability Evaluations Conduct Periodic BIAs Identify and Evaluate Risk Mitigation Strategies Integrate Risk Management into Business Life Cycle Processes Report Changes in Information Risk 3 - Information Security Program Development Develop Plans to Implement an Information Security Strategy Security Technologies and Controls Specify Information Security Program Activities Coordinate Information Security Programs with Business Assurance Functions Identify Resources Needed for Information Security Program Implementation Develop Information Security Architectures Develop Information Security Policies Develop Information Security Awareness, Training, and Education Programs Develop Supporting Documentation for Information Security Policies 4 - Information Security Program Implementation Integrate Information Security Requirements into Organizational Processes Integrate Information Security Controls into Contracts Create Information Security Program Evaluation Metrics 5 - Information Security Program Management Manage Information Security Program Resources Enforce Policy and Standards Compliance Enforce Contractual Information Security Controls Enforce Information Security During Systems Development Maintain Information Security Within an Organization Provide Information Security Advice and Guidance Provide Information Security Awareness and Training Analyze the Effectiveness of Information Security Controls Resolve Noncompliance Issues 6 - Incident Management and Response Develop an Information Security Incident Response Plan Establish an Escalation Process Develop a Communication Process Integrate an IRP Develop IRTs Test an IRP Manage Responses to Information Security Incidents Perform an Information Security Incident Investigation Conduct Post-Incident Reviews

STGO Awareness/ Escort vehicles & Safe Loading of Vehicles - Online
By Total Compliance
STGO Abnormal Loads

24th January Maddy Belton #Agent121. Looking for: MG, YA, CHILDREN'S NON-FICTION, ADULT FICTION
5.0(1)By I Am In Print
LOOKING FOR: MG, YA AND ADULT SCI-FI / FANTASY, CHILDREN'S NON-FICTION After graduating from St Andrews University with a degree in English Literature and Art History, Maddy followed her love of literature to an internship at non-fiction literary agency Graham Maw Christie. At GMC, Maddy worked her way up to Agent and built a list of authors who wrote for both for adults and children, spanning history, tarot, and nature writing. An avid reader of anything magical, Maddy joined Madeleine Milburn in 2022 to build a list specialising in SFF. Maddy would like to see SFF across all genres for all ages, including: grim dark, thriller, historical, romance, cosy fantasy, sci-fi, epic, YA fantasy, dark academia, contemporary fantasy, fantasy middle-grade, mythology, fairy tale and queer fantasy. Inspiring children’s non-fiction. She loves worlds to get lost in, adventures that transform what it means to be a hero, and unique magic that offers as many problems as solutions. She likes books that make her cry and books that change her mind. Above all, when she finishes a story about another world, she wants it to have taught her a lesson which helps her live in this one. She loves all fantasy, but favours richly imagined, complex worlds with a history to discover and a future to protect. Worldbuilding is one of her favourite aspects of this genre and she is always looking for a new, dense world with series potential. Think Brandon Sanderson’s Cosmere or the Marvel Cinematic Universe – the bigger the better! She also likes character-driven fantasy with a diverse cast to root for (or root against) and she wants to see a range of different relationships depicted authentically. She particularly like epics that dip into big, universal themes such as grief, climate change, or war and which ask impossible questions in the vein of R.F. Kuang or N.K. Jemisin. She is also excited by authors that play with form and language in a fantasy setting. In YA, she is looking for much the same as in an adult fantasy, but with younger protagonists and a closer focus on relationships. She wants to see the tropes she knows and loves in new and exciting forms and her favourite YA books often centre around belonging and becoming. She likes a dash of romance in everything, because she is sentimental that way, but it’s particularly important in the YA space. Sci-fi is a big passion of hers, especially when it comes with a strong hook. She is a huge fan of Becky Chamber’s The Long Way to a Small Angry Planet and Michaiah Johnson’s The Space Between Worlds. She likes space as a metaphor, and would love something that explores different alien species. Please send her your space operas and sci-fi romances which combine space, magic and mayhem! In fantasy middle grade, she favours whimsy and animal companions; she would love to follow a group of kids through magic school. She tends to look for plenty of humour with a strong friendship at the centre, and she wants middle grade stories which engage with the concerns of children growing up as well as offering an all-important escape (preferably on a dragon/unicorn’s back). She is also looking for children’s non-fiction for all ages. In this space, she wants something as creative as it is informative, and thinks diverse voices are increasingly important. Maddy would like you to submit a covering letter, one page synopsis and the first three chapters (Max 5000 words) of your completed manuscript in a single word document. (In addition to the paid sessions, Maddy is kindly offering one free session for low income/under-represented writers. Please email agent121@iaminprint.co.uk to apply, outlining your case for this option which is offered at the discretion of I Am In Print). By booking you understand you need to conduct an internet connection test with I Am In Print prior to the event. You also agree to email your material in one document to reach I Am In Print by the stated submission deadline and note that I Am In Print take no responsibility for the advice received during your agent meeting. The submission deadline is: Wednesday 15th January 2025

Security+ training course description A hands on course aimed at getting delegates successfully through the CompTia Security+ examination. What will you learn Explain general security concepts. Describe the security concepts in communications. Describe how to secure an infrastructure. Recognise the role of cryptography. Describe operational/organisational security. Security+ training course details Who will benefit: Those wishing to pass the Security+ exam. Prerequisites: TCP/IP foundation for engineers Duration 5 days Security+ training course contents General security concepts Non-essential services and protocols. Access control: MAC, DAC, RBAC. Security attacks: DOS, DDOS, back doors, spoofing, man in the middle, replay, hijacking, weak keys, social engineering, mathematical, password guessing, brute force, dictionary, software exploitation. Authentication: Kerberos, CHAP, certificates, usernames/ passwords, tokens, biometrics. Malicious code: Viruses, trojan horses, logic bombs, worms. Auditing, logging, scanning. Communication security Remote access: 802.1x, VPNs, L2TP, PPTP, IPsec, RADIUS, TACACS, SSH. Email: S/MIME, PGP, spam, hoaxes. Internet: SSL, TLS, HTTPS, IM, packet sniffing, privacy, Javascript, ActiveX, buffer overflows, cookies, signed applets, CGI, SMTP relay. LDAP. sftp, anon ftp, file sharing, sniffing, 8.3 names. Wireless: WTLS, 802.11, 802.11x, WEP/WAP. Infrastructure security Firewalls, routers, switches, wireless, modems, RAS, PBX, VPN, IDS, networking monitoring, workstations, servers, mobile devices. Media security: Coax, UTP, STP, fibre. Removable media. Topologies: Security zones, DMZ, Intranet, Extranet, VLANs, NAT, Tunnelling. IDS: Active/ passive, network/host based, honey pots, incident response. Security baselines: Hardening OS/NOS, networks and applications. Cryptography basics Integrity, confidentiality, access control, authentication, non-repudiation. Standards and protocols. Hashing, symmetric, asymmetric. PKI: Certificates, policies, practice statements, revocation, trust models. Key management and certificate lifecycles. Storage: h/w, s/w, private key protection. Escrow, expiration, revocation, suspension, recovery, destruction, key usage. Operational/Organisation security Physical security: Access control, social engineering, environment. Disaster recovery: Backups, secure disaster recovery plans. Business continuity: Utilities, high availability, backups. Security policies: AU, due care, privacy, separation of duties, need to know, password management, SLAs, disposal, destruction, HR policies. Incident response policy. Privilege management: Users, groups, roles, single sign on, centralised/decentralised. Auditing. Forensics: Chain of custody, preserving and collecting evidence. Identifying risks: Assets, risks, threats, vulnerabilities. Role of education/training. Security documentation.

Educators matching "ESC"
Show all 5Search By Location
- ESC Courses in London
- ESC Courses in Birmingham
- ESC Courses in Glasgow
- ESC Courses in Liverpool
- ESC Courses in Bristol
- ESC Courses in Manchester
- ESC Courses in Sheffield
- ESC Courses in Leeds
- ESC Courses in Edinburgh
- ESC Courses in Leicester
- ESC Courses in Coventry
- ESC Courses in Bradford
- ESC Courses in Cardiff
- ESC Courses in Belfast
- ESC Courses in Nottingham


