- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
3232 Engineering courses delivered Online
Overview This comprehensive course on Quick Data Science Approach from Scratch will deepen your understanding on this topic. After successful completion of this course you can acquire the required skills in this sector. This Quick Data Science Approach from Scratch comes with accredited certification from CPD, which will enhance your CV and make you worthy in the job market. So enrol in this course today to fast track your career ladder. How will I get my certificate? You may have to take a quiz or a written test online during or after the course. After successfully completing the course, you will be eligible for the certificate. Who is This course for? There is no experience or previous qualifications required for enrolment on this Quick Data Science Approach from Scratch. It is available to all students, of all academic backgrounds. Requirements Our Quick Data Science Approach from Scratch is fully compatible with PC's, Mac's, Laptop, Tablet and Smartphone devices. This course has been designed to be fully compatible with tablets and smartphones so you can access your course on Wi-Fi, 3G or 4G. There is no time limit for completing this course, it can be studied in your own time at your own pace. Career Path Learning this new skill will help you to advance in your career. It will diversify your job options and help you develop new techniques to keep up with the fast-changing world. This skillset will help you to- Open doors of opportunities Increase your adaptability Keep you relevant Boost confidence And much more! Course Curriculum 4 sections • 15 lectures • 01:00:00 total length •Introduction: 00:02:00 •Data Science Explanation: 00:05:00 •Need of Data Science: 00:02:00 •8 Common mistakes by Aspiring Data Scientists/Data Science Enthusiasts: 00:08:00 •Myths about Data Science: 00:03:00 •Data Types and Variables: 00:04:00 •Descriptive Analysis: 00:02:00 •Data Cleaning: 00:02:00 •Feature Engineering: 00:02:00 •Data Thinking Development: 00:03:00 •Problem Definition: 00:05:00 •Algorithms: 00:14:00 •Prediction: 00:03:00 •Learning Methods: 00:05:00 •Assignment - Quick Data Science Approach from Scratch: 00:00:00

Learn DOM Manipulation with Easy Modern JavaScript
By Packt
This course primarily focuses on explaining the concepts of the Document Object Model through a project-based approach. It will help you enhance your coding skills using JavaScript along with a deeper understanding of the DOM fundamentals.

Our Aim Is Your Satisfaction! Offer Ends Soon; Hurry Up!! Are you looking to improve your current abilities or make a career move? Our unique Renewables Energy Consultant course might help you get there! Expand your expertise with high-quality training - study the Renewables Energy Consultant and get an expertly designed, great-value training experience. The Renewables Energy Consultant course is broken down into several in-depth modules to provide you with the most convenient and rich learning experience possible. Upon successful completion of the Renewables Energy Consultant course, an instant e-certificate will be exhibited in your profile that you can order as proof of your skills and knowledge. Add these amazing new skills to your resume and boost your employability by simply enrolling in this course. This Renewables Energy Consultant training can help you to accomplish your ambitions and prepare you for a meaningful career. So, join us today and gear up for excellence! Why Prefer Us? Opportunity to earn a certificate accredited by CPD . Get a free student ID card! (£10 postal charges will be applicable for international delivery) Innovative and engaging content. Free assessments. 24/7 tutor support. **** Course Curriculum **** Here is the curriculum breakdown of the Renewables Energy Consultant Course: Module 01: History of Energy Consumption Module 02: Non-Renewable Energy Module 03: Basics of Sustainable Energy Module 04: Fuel Cell Module 05: Solar Energy Module 06: Wind Energy Module 07: Ocean Energy Module 08: Geothermal Energy Module 09: Application of Renewable Energy Module 10: Being Environment-Friendly Assessment Process Your skills and knowledge will be tested with an automated multiple-choice assessment. You will then receive instant results to let you know if you have successfully passed the Renewables Energy Consultant course. CPD 10 CPD hours / points Accredited by CPD Quality Standards Who is this course for? Anyone interested in learning more about the topic is advised to take this Renewables Energy Consultant course. This course is open to everybody. Requirements You will not need any prior background or expertise to enrol in this Renewables Energy Consultant course. Career path The Energy Engineer Course Consultant is designed for anyone looking to kickstart a career in the energy sector, specifically within the field of engineering. The average annual salary for an Energy Engineer in the UK is £40,838. Professions in this field include: Energy Engineer Wind Energy Consultant Energy Analyst Energy & Sustainability Manager Certificates CPD Accredited Certificate Digital certificate - £10 CPD Accredited Certificate Hard copy certificate - £29 If you are an international student, then you have to pay an additional 10 GBP as an international delivery charge.

Becoming a Cloud Expert - Microsoft Azure IaaS - Level 3
By Packt
Learn to design a resilient and scalable cloud solution using traffic load balancers, availability sets, and scale sets

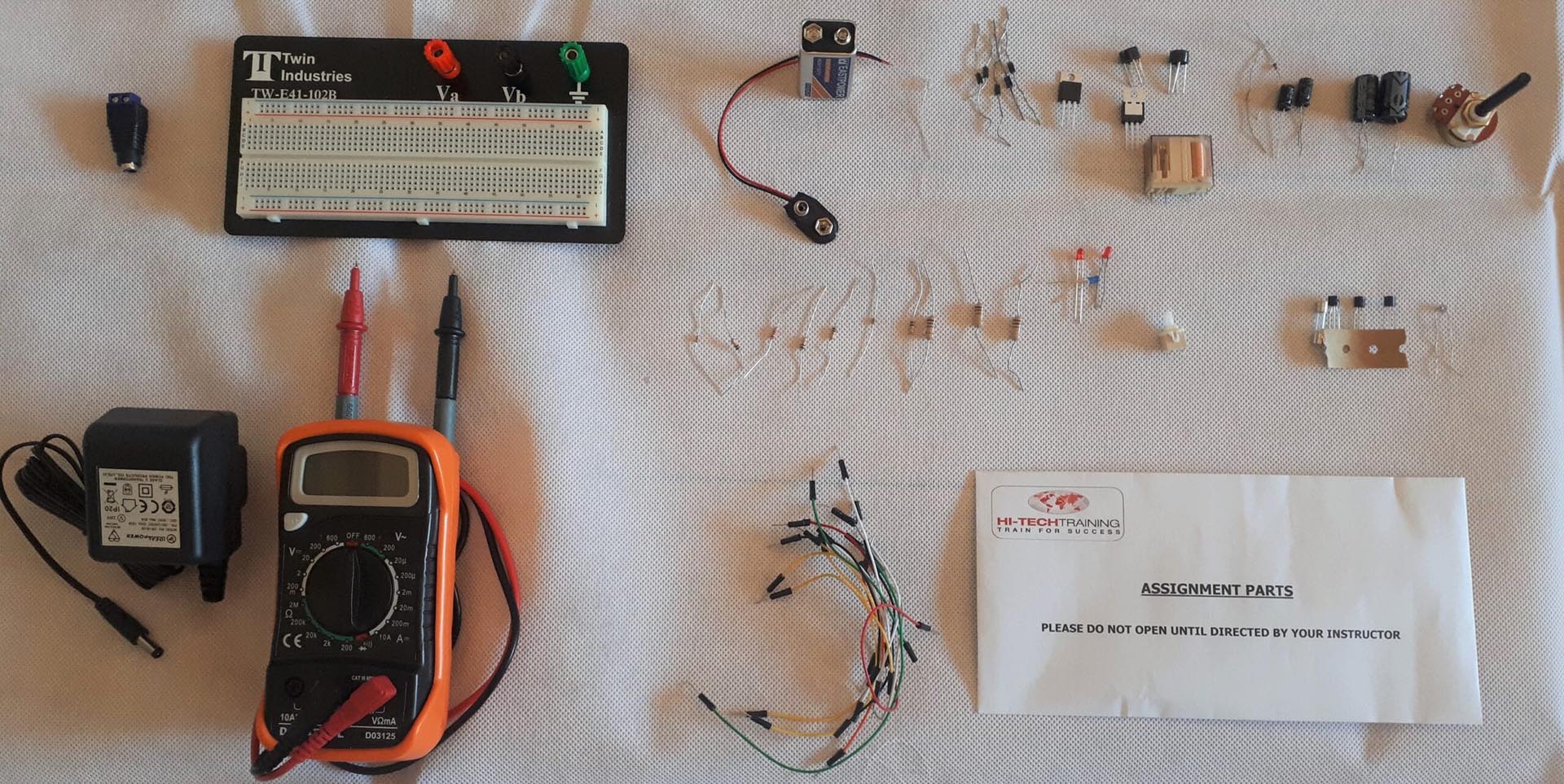
Electronics Repair 1 Course
By Hi-Tech Training
The Electronics Equipment Repair 1 equips participants with practical “Hands-On” skills relevant to the workplace and the theory required for certification. Participants on successful completion of the course will have the skills and knowledge to: Demonstrate the operation of a wide range of electronic components and circuits and their applications in modern electronic-based equipment such as amplifiers, Hi-Fi systems, stereos, and control systems Construct, test and fault-find the following popular basic circuits: Power supplies, amplifiers, timers, etc. Become competent in the correct use of electronic test and measurement equipment such as Analogue and Digital Multimeter and Oscilloscopes.
Technical Writing for Developers Course
By Cherryleaf
An affordable way for developers to develop skills in technical writing Cherryleaf's Technical Writing for Developers e-learning course teaches the basics of technical writing to developers who are writing documentation. It teaches you how to write clearer technical documentation, plus topics such as creating sample code, tutorials, images and diagrams. The course will improve your technical writing skills. You’ll gain confidence you’re approaching each writing project in the right way, and creating content that follows best practice. Who are these courses for? The courses have been designed for: Software engineers Software engineering students In addition, other people involved in software development (such as product managers) can benefit from these courses, especially if they: Want to communicate more clearly and effectively Want to know how little, or how much, they should write Struggle with planning their writing Want people to answer their own support questions Prerequisites Delegates need to have basic writing proficiency in English. What will I learn? You’ll learn: How to communicate clearly, even if writing doesn’t come naturally How to save time and write in an efficient way Confidence in the work you produce You’ll have access to a framework and templates to help you with your writing. You can also get feedback on your completed exercises. Course duration The course typically takes 1 to 1.5 days to complete, but you can go at the pace that suits you. Your Instructor Cherryleaf Cherryleaf is a technical writing services company formed in 2002 by people with a passion for technical communication and learning development. Cherryleaf is recognised as a leader within the technical communication profession. Our staff have written articles for the Society for Technical Communication's (STC) Intercom magazine, the Institute of Scientific and Technical Communicator's Communicator journal and tekom's TCWorld magazine. They've also written books on technical communication. We've presented webinars for Adobe, Madcap Software or the STC, and we've spoken at various conferences around the world. Today, organisations throughout Europe use Cherryleaf’s services so they can provide clear information that enables users and staff to complete tasks productively. Course Curriculum First Section Introduction (0:52) Writing clearly (24:47) Writing headings, lists, and links (7:00) Structuring the information (13:12) Planning and outlining your writing (7:43) Using Information Types (15:34) Using images and videos (7:58) Writing in Markdown Writing clear code samples (8:22) Reviewing and editing your content (8:40) Summary (1:29) Frequently Asked Questions When does the course start and finish? The course starts now and never ends! It is a completely self-paced online course - you decide when you start and when you finish.How long do I have access to the course?How does lifetime access sound? After enrolling, you have unlimited access to this course for as long as you like - across any and all devices you own.What if I am unhappy with the course?We would never want you to be unhappy! If you are unsatisfied with your purchase, contact us in the first 30 days and we will give you a full refund.

ASP.NET Core MVC - Up and Running (.NET 5)
By Packt
This course will take you from the basic structure of ASP.Net Core 5 to building and enhancing a functional website. You will deep dive into the concepts by creating a product catalog, connecting your application to a database, sending emails from your application, integrating a secure payment system into your application, and a lot more.

Python for Data Analysis: Step-By-Step with Projects
By Packt
Step into the world of data analysis and gain practical experience analyzing real-world datasets with the help of this course. This course will not only guide you in analyzing data efficiently in Python from scratch but also help you in conducting your own analysis with Python and extracting valuable insights that can transform your business!

Overview Learn to become a qualified domestic Gas Installer and light up a whole new world of business opportunities. This Level 2 Domestic Gas Course course will deliver all the essential skills and information you'll need to start in Gas Engineering and assure a lucrative future career. Written with the help of industry experts, you will be given 'hands-on' tests and assessments to perform, as well as substantial theoretical training. As a result, you will quickly learn the fundamental principles and concepts of safely installing gas fittings, and become a sought after asset in organisations. Alternatively, you can be guided towards starting your own qualified business. How will I get my certificate? You may have to take a quiz or a written test online during or after the course. After successfully completing the course, you will be eligible for the certificate. Who is this course for? There is no experience or previous qualifications required for enrolment on this Level 2 Domestic Gas Course. It is available to all students, of all academic backgrounds. Requirements Our Level 2 Domestic Gas Course is fully compatible with PC's, Mac's, Laptop, Tablet and Smartphone devices. This course has been designed to be fully compatible on tablets and smartphones so you can access your course on wifi, 3G or 4G. There is no time limit for completing this course, it can be studied in your own time at your own pace. Career path Having these various qualifications will increase the value in your CV and open you up to multiple sectors such as Business & Management , Admin, Accountancy & Finance, Secretarial & PA, Teaching & Mentoring etc. Course Curriculum 2 sections • 18 lectures • 04:25:00 total length •Module 01: Gas Legislation: 00:05:00 •Module 02: Gas Safety Regulations: 00:05:00 •Module 03: The Gas Safety (Installation and Use) Regulations 1998: 00:50:00 •Module 04: Overview of Gas: 00:15:00 •Module 05: Combustion: 00:05:00 •Module 6: Flues: 00:30:00 •Module 07: Ventilation: 00:15:00 •Module 08: Testing and Purging: 00:20:00 •Module 09: Unsafe Situations: 00:10:00 •Module 10: Commissioning and Servicing Of Gas: 00:05:00 •Module 11: Gas Fires Space Heaters, Open Flud Gas Fires Fan Flued, Room Sealed Heaters and Space Heaters: 00:30:00 •Module 12: Domestic Gas Cookers: 00:15:00 •Module 13: Gas Water Heaters: 00:15:00 •Module 14: Domestic Gas Boilers: 00:15:00 •Module 15: Pipework Installation: 00:10:00 •Module 16: LPG Supply and Installation: 00:10:00 •Module 17: Electrical Work on Gas Appliances: 00:10:00 •Assignment - Level 2 Domestic Gas Course: 00:00:00

