- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
Digital, Text & Voice Communicators Course
By Hi-Tech Training
The Hi-Tech Training Digital Text & Voice Communicator Course is designed to provide participants with the skills required to connect Digital, Text & Voice Communicators to an Alarm Control Panel for transmission of Digital status signals via the telephone line, GSM Network or IP network to a central monitoring station. The Digital Communicator Course’s practical application and our highly experienced trainers ensure that this course is second to none. The course is technical and practical in nature and is suitable for participants who have successfully completed the Hi-Tech Training Intruder Alarm Installation Course or equivalent.

55321 SQL Server Integration Services
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for The primary audience for this course is database professionals who need to fulfil a Business Intelligence Developer role. They will need to focus on hands-on work creating BI solutions including Data Warehouse implementation, ETL, and data cleansing. Overview Create sophisticated SSIS packages for extracting, transforming, and loading data Use containers to efficiently control repetitive tasks and transactions Configure packages to dynamically adapt to environment changes Use Data Quality Services to cleanse data Successfully troubleshoot packages Create and Manage the SSIS Catalog Deploy, configure, and schedule packages Secure the SSIS Catalog SQL Server Integration Services is the Community Courseware version of 20767CC Implementing a SQL Data Warehouse. This five-day instructor-led course is intended for IT professionals who need to learn how to use SSIS to build, deploy, maintain, and secure Integration Services projects and packages, and to use SSIS to extract, transform, and load data to and from SQL Server. This course is similar to the retired Course 20767-C: Implementing a SQL Data Warehouse but focuses more on building packages, rather than the entire data warehouse design and implementation. Prerequisites Working knowledge of T-SQL and SQL Server Agent jobs is helpful, but not required. Basic knowledge of the Microsoft Windows operating system and its core functionality. Working knowledge of relational databases. Some experience with database design. 1 - SSIS Overview Import/Export Wizard Exporting Data with the Wizard Common Import Concerns Quality Checking Imported/Exported Data 2 - Working with Solutions and Projects Working with SQL Server Data Tools Understanding Solutions and Projects Working with the Visual Studio Interface 3 - Basic Control Flow Working with Tasks Understanding Precedence Constraints Annotating Packages Grouping Tasks Package and Task Properties Connection Managers Favorite Tasks 4 - Common Tasks Analysis Services Processing Data Profiling Task Execute Package Task Execute Process Task Expression Task File System Task FTP Task Hadoop Task Script Task Introduction Send Mail Task Web Service Task XML Task 5 - Data Flow Sources and Destinations The Data Flow Task The Data Flow SSIS Toolbox Working with Data Sources SSIS Data Sources Working with Data Destinations SSIS Data Destinations 6 - Data Flow Transformations Transformations Configuring Transformations 7 - Making Packages Dynamic Features for Making Packages Dynamic Package Parameters Project Parameters Variables SQL Parameters Expressions in Tasks Expressions in Connection Managers After Deployment How It All Fits Together 8 - Containers Sequence Containers For Loop Containers Foreach Loop Containers 9 - Troubleshooting and Package Reliability Understanding MaximumErrorCount Breakpoints Redirecting Error Rows Logging Event Handlers Using Checkpoints Transactions 10 - Deploying to the SSIS Catalog The SSIS Catalog Deploying Projects Working with Environments Executing Packages in SSMS Executing Packages from the Command Line Deployment Model Differences 11 - Installing and Administering SSIS Installing SSIS Upgrading SSIS Managing the SSIS Catalog Viewing Built-in SSIS Reports Managing SSIS Logging and Operation Histories Automating Package Execution 12 - Securing the SSIS Catalog Principals Securables Grantable Permissions Granting Permissions Configuring Proxy Accounts Additional course details: Nexus Humans 55321 SQL Server Integration Services training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the 55321 SQL Server Integration Services course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

In-Depth Wedding Planning Courses - Extensive, Intensive Training Program
By AP Wedding Consultancy & Academy
5* Wedding Planner Courses UK & Online. Certified, intensive training alongside est. London Consultants. Home-study & online wedding planning courses.

CRISC Certified in Risk and Information Systems Control
By Nexus Human
Duration 3 Days 18 CPD hours This course is intended for This course is ideal for Professionals preparing to become CRISC certified. Risk practitioners Students or recent graduates Overview At course completions, students will understand the essential concepts in the 4 ISACA CRISC domains: Governance IT Risk Assessment Risk Response and Reporting Information Technology and Security This 3 Day CRISC course is geared towards preparing students to pass the ISACA Certified in Risk and Information Systems Control examination. The course covers all four of the CRISC domains, and each section corresponds directly to the CRISC job practice. CRISC validates your experience in building a well-defined, agile risk-management program, based on best practices to identify, analyze, evaluate, assess, prioritize and respond to risks. This enhances benefits realization and delivers optimal value to stakeholders. GOVERNANCE - a. Organizational Governance Organizational Strategy, Goals, and Objectives Organizational Structure, Roles, and Responsibilities Organizational Culture Policies and Standards Business Processes Organizational Assets GOVERNANCE - b. Risk Governance Enterprise Risk Management and Risk Management Framework Three Lines of Defense Risk Profile Risk Appetite and Risk Tolerance Legal, Regulatory, and Contractual Requirements Professional Ethics of Risk Management IT RISK ASSESSMENT - a. IT Risk Identification Risk Events (e.g., contributing conditions, loss result) Threat Modelling and Threat Landscape Vulnerability and Control Deficiency Analysis (e.g., root cause analysis) Risk Scenario Development IT RISK ASSESSMENT - b. IT Risk Analysis and Evaluation Risk Assessment Concepts, Standards, and Frameworks Risk Register Risk Analysis Methodologies Business Impact Analysis Inherent and Residual Risk RISK RESPONSE AND REPORTING - a. Risk Response Risk Treatment / Risk Response Options Risk and Control Ownership Third-Party Risk Management Issue, Finding, and Exception Management Management of Emerging Risk RISK RESPONSE AND REPORTING - b. Control Design and Implementation Control Types, Standards, and Frameworks Control Design, Selection, and Analysis Control Implementation Control Testing and Effectiveness Evaluation RISK RESPONSE AND REPORTING - c. Risk Monitoring and Reporting Risk Treatment Plans Data Collection, Aggregation, Analysis, and Validation Risk and Control Monitoring Techniques Risk and Control Reporting Techniques (heatmap, scorecards, dashboards) Key Performance Indicators Key Risk Indicators (KRIs) Key Control Indicators (KCIs) INFORMATION TECHNOLOGY AND SECURITY - a. Information Technology Principles Enterprise Architecture IT Operations Management (e.g., change management, IT assets, problems, incidents) Project Management Disaster Recovery Management (DRM) Data Lifecycle Management System Development Life Cycle (SDLC) Emerging Technologies INFORMATION TECHNOLOGY AND SECURITY - b. Information Security Principles Information Security Concepts, Frameworks, and Standards Information Security Awareness Training Business Continuity Management Data Privacy and Data Protection Principles

Overview This course is specially designed to increase the fundamental knowledge of business analysts and their roles and functions more efficiently. In this course, participants attain skills and knowledge of efficient ways to approach, the best methods to elaborate the supplies for business system projects.

AutoCAD Training at QLS Level 6
By Imperial Academy
Free Level 6 QLS Endorsed Certificate | CPD Accredited | Audio Visual Training | Lifetime Access
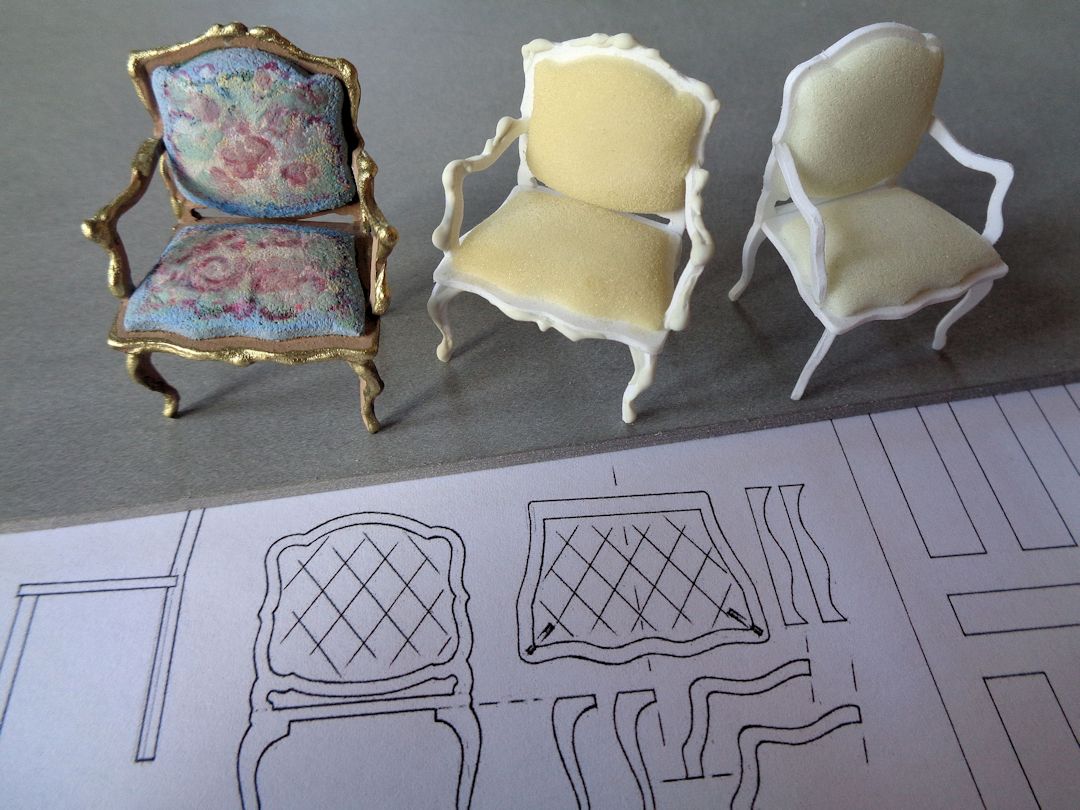
Model-making Techniques Course Online
By David Neat
A 5-day intensive, practical course covering model-making skills for theatre, film, animation or spatial design. Led by David Neat from his studio in Deptford.
WNAI41 SAP Information Design Tool Delta 4.1
By Nexus Human
Duration 1 Days 6 CPD hours This course is intended for Experienced universe designers upgrading from a previous version of SAP BusinessObjects Designer to SAP BusinessObjects Information Design Tool 4.1. NOTE: This workshop is not designed for users new to the tool. In this course, participants will gain an understanding of the Delta between Universe Design and the Information Design Tool. Course Outline New File extension Universe components -Projects -Connections -Data foundation -Business Layer Universe Testing Lists of Values Parameters @Execute function Calculated Columns Multisource universe Federated Tables Additional course details: Nexus Humans WNAI41 SAP Information Design Tool Delta 4.1 training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the WNAI41 SAP Information Design Tool Delta 4.1 course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

In this competitive job market, you need to have some specific skills and knowledge to start your career and establish your position. This Create A Character From The Post-Apocalypse will help you understand the current demands, trends and skills in the sector. The course will provide you with the essential skills you need to boost your career growth in no time. The Create A Character From The Post-Apocalypse will give you clear insight and understanding about your roles and responsibilities, job perspective and future opportunities in this field. You will be familiarised with various actionable techniques, career mindset, regulations and how to work efficiently. This course is designed to provide an introduction to Create A Character From The Post-Apocalypse and offers an excellent way to gain the vital skills and confidence to work toward a successful career. It also provides access to proven educational knowledge about the subject and will support those wanting to attain personal goals in this area. Learning Objectives Learn the fundamental skills you require to be an expert Explore different techniques used by professionals Find out the relevant job skills & knowledge to excel in this profession Get a clear understanding of the job market and current demand Update your skills and fill any knowledge gap to compete in the relevant industry CPD accreditation for proof of acquired skills and knowledge Who is this Course for? Whether you are a beginner or an existing practitioner, our CPD accredited Create A Character From The Post-Apocalypse is perfect for you to gain extensive knowledge about different aspects of the relevant industry to hone your skill further. It is also great for working professionals who have acquired practical experience but require theoretical knowledge with a credential to support their skill, as we offer CPD accredited certification to boost up your resume and promotion prospects. Entry Requirement Anyone interested in learning more about this subject should take this Create A Character From The Post-Apocalypse. This course will help you grasp the basic concepts as well as develop a thorough understanding of the subject. The course is open to students from any academic background, as there is no prerequisites to enrol on this course. The course materials are accessible from an internet enabled device at anytime of the day. CPD Certificate from Course Gate At the successful completion of the course, you can obtain your CPD certificate from us. You can order the PDF certificate for £9 and the hard copy for £15. Also, you can order both PDF and hardcopy certificates for £22. Career path The Create A Character From The Post-Apocalypse will help you to enhance your knowledge and skill in this sector. After accomplishing this course, you will enrich and improve yourself and brighten up your career in the relevant job market. Course Curriculum Create A Character From The Post-Apocalypse Lesson 01: Introduction to the Future! 00:01:00 Lesson 02: Finding Reference and Inspiration 00:01:00 Lesson 03: Start Sketching 00:08:00 Lesson 04: Find the Shadow 00:02:00 Lesson 05: Find the Design 00:04:00 Lesson 06: Explore the Design PT 1 00:04:00 Lesson 07: Explore the Design PT 2 00:04:00 Lesson 08: Last Looks and Final Thoughts 00:01:00 Certificate and Transcript Order Your Certificates or Transcripts 00:00:00