- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
3437 Design courses in Scunthorpe delivered Live Online
VMware Cloud Director: Install, Configure, Manage [V10.4]
By Nexus Human
Duration 5 Days 30 CPD hours Overview By the end of the course, you should be able to meet the following objectives: Deploy VMware Cloud Director Manage VMware Cloud Director to meet the service provider needs Create and manage VMware Cloud Director organizations and vApps to fulfill business needs Create and manage VMware Cloud Director catalogs Configure networking for organizations and vApps with the help of NSX-T Data Center Manage resources from the VMWare Cloud Director console Enable VM and Named Disk Create VM sizing and placement policies Create vApps and perform VM operations and actions Manage vGPU resources with VMware Cloud Director Discuss how VMware Cloud Director can be integrated with other solutions In this five-day course, you focus on installing, configuring, and managing on-premises VMware Cloud Director? 10.4. You will learn about workload provisioning, the creation of organizations, virtual data centers (VDCs), catalog services that include predefined virtual machines, and on-demand VMware NSX-T? Data Center networks. You will learn about different networks that a system administrator and an organization administrator can configure and use with virtual machines (VMs).This course also covers the UI enhancements of VMware Cloud Director, the new licensing model and UI enhancements with NSX Advanced Load Balancer?, and the L2 and L3 VPN enhancements in VMware Cloud Director. You will learn about defining segment profile templates to organization VDC networks and vApp networks and configuring DHCP, static routes, and no distributed routing in VMware Cloud Director. This course explains how to integrate and implement vGPU in VMware Cloud Director as well as how to use API access tokens and service accounts for programmatic access to VMware Cloud Director. Course Introduction Introductions and course logistics Course objectives Software-Defined Data Center and VMware Validated Solution Define software-defined data center (SDDC) Discuss VMware offerings for cloud-based services Discuss the deployment options for VMware Cloud Director Discuss VMware Validated Solution Recognize the design considerations when creating a cloud environment on the SDDC using VMware Cloud Foundation? VMware Cloud Director Deployment and Configuration Discuss the deployment options for VMware Cloud Director Explain the two-stage deployment of VMware Cloud Director cells Discuss failover mechanisms (automatic and manual) with VMware Cloud Director cells Define the switchover, promote, and fencing options of the VMware Cloud Director appliance Understand the VMware Cloud Director appliance enhancements VMware Cloud Director Provider Configuration Describe how the compute resources are provided to VMware Cloud Director Describe how storage is provided to VMware Cloud Director Configure and manage storage for Virtual Data Centers (VDCs) Discuss network pools, external networks, and Tier-0 gateways Showcase VMware Cloud Director integration with VMware vCenter Server© and NSX-T Data Center Describe VMware Cloud Director organizations Understand organization policies Explain how to access an organization using various portals Understand organization VDC Discuss Linked Clone and Fast Provisioning Understand the use cases of Allocation Models VMware Cloud Director User, Roles, and Quota Management Discuss user bundle Describe role-based access Explain custom roles and rights Describe and configure LDAP integration with Active Directory Discuss OIDC authentication methods Describe SAML identity provider Discuss API Access Token and Service Accounts Explain Quota Management and its use cases VMware Cloud Director Virtual Machines and vApps Understand standalone VMs Discuss the VM managing operations Explain VM properties Discuss deployment methods of vApps Discuss the vApp managing operations Discuss the vApp lease policies Understand the vApps and VM actions Explain vApp and VM badges VMware Cloud Director Content Libraries Explain the purpose of catalogs and how to create a catalog organization Define catalog management and sharing catalogs inside and between organizations Explain media in VMware Cloud Director and its usage Discuss vApp templates Understand vApp template operations Describe the purpose and usage of Open Virtualization Format (OVF) Discuss organization VDC templates Discuss Fast Cross vCenter Server vApp Instantiation Utilizing Shared Storage VMware Cloud Director Networking Discuss organization VDC networks List the types of organization VDC networks Describe the edge gateway services Explore the services offered by the edge gateway Discuss the sub-allocation IP pool and its use cases Discuss DHCP, NAT, load balancer, and firewall services on the edge gateway Discuss SNAT, DNAT, NO SNAT, and NO DNAT use cases Explain routing and distributed firewall services Discuss vApp networks List the various types of vApp networks VMware Cloud Director Storage and Compute Describe named disks and shared named disks Demonstrate how to attach and detach a named disk and a shared named disk Describe methods of sharing the named disk Discuss the implications of deleting VMs that have an attached named disk Discuss how VMware Cloud Director VMs and disks are encrypted Explain the storage policy capabilities Demonstrate how VM sizing and placement policies are published Discuss vCenter Server and VMware Cloud Director IOPS storage policies usage Discuss how to enable and use the storage IOPS limitation in VMware Cloud Director Describe the storage policy-supported entities Discuss vGPU in VMware Cloud Director Additional UI Features and Integrated Solutions Explain custom advisories, global search, guided tours, keyboard shortcuts, and quick search Demonstrate the new branding and theming experience Briefly discuss how VMware Cloud Director can be integrated with other solutions
![VMware Cloud Director: Install, Configure, Manage [V10.4]](https://cademy-images-io.b-cdn.net/9dd9d42b-e7b9-4598-8d01-a30d0144ae51/4c81f130-71bf-4635-b7c6-375aff235529/original.png?width=3840)
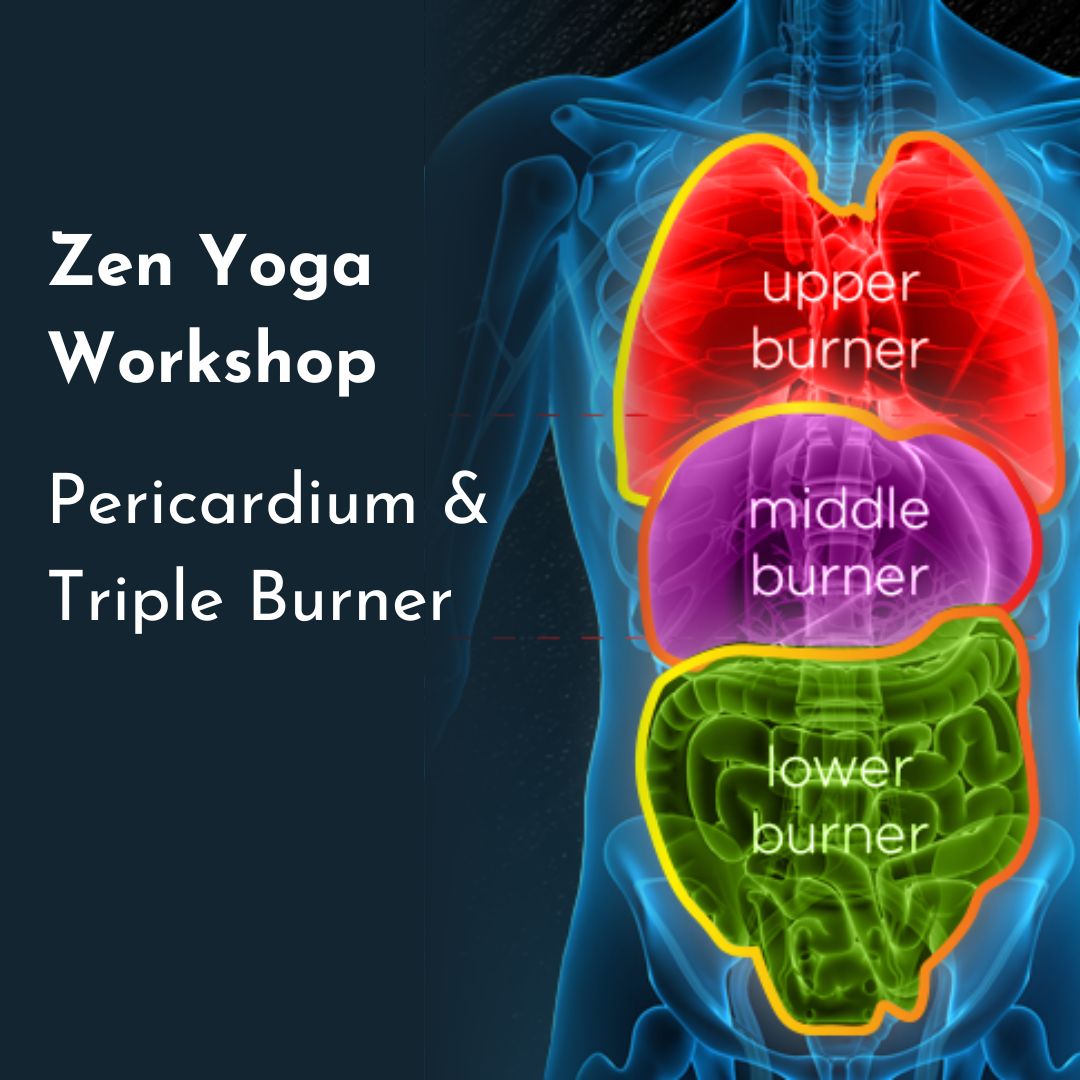
Zen Yoga Workshop - The Pericardium and Triple Heater
By Mark Westmoquette
Zen Yoga workshop exploring the paired energy systems of the Pericardium and Triple Heater. Learn about these organs from both a Western and Eastern perspective, and practice a sequence designed to enliven both systems.
Juniper - Introduction to the Junos Operating System (IJOS)
By Nexus Human
Duration 3 Days 18 CPD hours This course is intended for This course benefits individuals responsible for configuring and monitoring devices running the Junos OS. Overview After successfully completing this course, you should be able to: Describe the basic design architecture of the Junos OS. Identify and provide a brief overview of Junos devices. Navigate within the Junos CLI. Perform tasks within the CLI operational and configuration modes. Restore a Junos device to its factory-default state. Perform initial configuration tasks. Configure and monitor network interfaces. Describe user configuration and authentication options. Perform secondary configuration tasks for features and services such as system logging (syslog) and tracing, Network Time Protocol (NTP), configuration archival, and SNMP. Monitor basic operation for the Junos OS and devices. Identify and use network utilities. Upgrade the Junos OS. Perform file system maintenance and password recovery on a Junos device. Navigate within the Junos J-Web interface. Explain basic routing operations and concepts. View and describe routing and forwarding tables. Configure and monitor static routing. Configure and monitor OSPF. Describe the framework for routing policy and firewall filters. Explain the evaluation of routing policy and firewall filters. Identify instances where you might use routing policy. Write and apply a routing policy. Identify instances where you might use firewall filters. Write and apply a firewall filter. Describe the operation and configuration for unicast reverse path forwarding (RPF). This three-day course provides students with the foundational knowledge required to work with the Juniper Networks Junos operating system and to configure Junos devices. The course provides a brief overview of the Junos device families and discusses the key architectural components of the software. Key topics include user interface options with a heavy focus on the command-line interface (CLI), configuration tasks typically associated with the initial setup of devices, interface configuration basics with configuration examples, secondary system configuration, and the basics of operational monitoring and maintenance of Junos devices. The course then delves into foundational routing knowledge and configuration examples including general routing concepts, routing policy, and firewall filters. Course Outline COURSE INTRODUCTION Junos Operating System Fundamentals The Junos OS Traffic Processing Overview of Junos Devices User Interface Options: The Junos CLI User Interface Options The Junos CLI: CLI Basics The Junos CLI: Operational Mode The Junos CLI: Configuration Mode User Interface Options: The J-Web Interface User Interface Options The Junos CLI: CLI Basics The Junos CLI: Operational Mode The Junos CLI: Configuration Mode Initial Configuration Factory-Default Configuration Initial Configuration Interface Configuration Secondary System Configuration User Configuration and Authentication System Logging and Tracing Network Time Protocol Archiving Configurations SNMP Operational Monitoring and Maintenance Monitoring Platform and Interface Operation Network Utilities Maintaining the Junos OS Password Recovery System Clean-Up Interface Configuration Examples Review of the Interface Configuration Hierarchy Interface Configuration Examples Using Configuration Groups Routing Fundamentals Routing Concepts: Overview of Routing Routing Concepts: The Routing Table Routing Concepts: Routing Instances Static Routing Dynamic Routing Routing Policy Routing Policy Overview Case Study: Routing Policy Firewall Filters Firewall Filters Overview Case Study: Firewall Filters Unicast Reverse-Path-Forwarding Checks Class of Service CoS Overview Traffic Classification Traffic Queueing Traffic Scheduling Case Study: CoS JTAC Procedures Opening a Support Case Customer Support Tools Transferring Files to JTAC Juniper Security Concepts Security Challenges Juniper Networks? Security Focus A IPv6 Fundamentals IPv6 Addressing Protocols and Services Configuration Additional course details: Nexus Humans Juniper - Introduction to the Junos Operating System (IJOS) training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Juniper - Introduction to the Junos Operating System (IJOS) course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Cisco Securing Cloud Deployments with Cisco Technologies v1.0 (SECCLD)
By Nexus Human
Duration 4 Days 24 CPD hours This course is intended for This course is open to engineers, administrators, and security-minded users of public, private, and hybrid cloud infrastructures responsible for implementing security in cloud environments: Security architects Cloud architects Security engineers Cloud engineers System engineers Cisco integrators and partners Overview After taking this course, you should be able to: Contrast the various cloud service and deployment models. Implement the Cisco Security Solution for SaaS using Cisco Cloudlock Micro Services. Deploy cloud security solutions using Cisco AMP for Endpoints, Cisco Umbrella, and Cisco Cloud Email Security. Define Cisco cloud security solutions for protection and visibility using Cisco virtual appliances and Cisco Stealthwatch Cloud. Describe the network as a sensor and enforcer using Cisco Identity Services Engine (ISE), Cisco Stealthwatch Enterprise, and Cisco TrustSec. Implement Cisco Firepower NGFW Virtual (NGFWv) and Cisco Stealthwatch Cloud to provide protection and visibility in AWS environments. Explain how to protect the cloud management infrastructure by using specific examples, defined best practices, and AWS reporting capabilities. This course shows you how to implement Cisco© cloud security solutions to secure access to the cloud, workloads in the cloud, and software as a service (SaaS) user accounts, applications, and data. This course covers usage of Cisco Cloudlock, Cisco Umbrella?, Cisco Cloud Email Security, Cisco Advanced Malware Protection (AMP) for Endpoints, Cisco Stealthwatch© Cloud and Enterprise, Cisco Firepower© NGFW (next-generation firewall), and more. Introducing the Cloud and Cloud Security Describe the Evolution of Cloud Computing Explain the Cloud Service Models Explore the Security Responsibilities Within the Infrastructure as a Service (IaaS) Service Model Explore the Security Responsibilities Within the Platform as a Service (PaaS) Service Model Explore the Security Responsibilities Within the SaaS Service Model Describe Cloud Deployment Models Describe Cloud Security Basics Implementing the Cisco Security Solution for SaaS Access Control Explore Security Challenges for Customers Using SaaS Describe User and Entity Behavior Analytics, Data Loss Prevention (DLP), and Apps Firewall Describe Cloud Access Security Broker (CASB) Describe Cisco CloudLock as the CASB Describe OAuth and OAuth Attacks Deploying Cisco Cloud-Based Security Solutions for Endpoints and Content Security Describe Cisco Cloud Security Solutions for Endpoints Describe AMP for Endpoints Architecture Describe Cisco Umbrella Describe Cisco Cloud Email Security Design Comprehensive Endpoint Security Introducing Cisco Security Solutions for Cloud Protection and Visibility Describe Network Function Virtualization (NFV) Describe Cisco Secure Architectures for Enterprises (Cisco SAFE) Describe Cisco NGFWv/Cisco Firepower Management Center Virtual Describe Cisco ASAv Describe Cisco Services Router 1000V Describe Cisco Stealthwatch Cloud Describe Cisco Tetration Cloud Zero-Trust Model Describing the Network as the Sensor and Enforcer Describe Cisco Stealthwatch Enterprise Describe Cisco ISE Functions and Personas Describe Cisco TrustSec Describe Cisco Stealthwatch and Cisco ISE Integration Describe Cisco Encrypted Traffic Analytics (ETA) Implementing Cisco Security Solutions in AWS Explain AWS Security Offerings Describe AWS Elastic Compute Cloud (EC2) and Virtual Private Cloud (VPC) Discover Cisco Security Solutions in AWS Explain Cisco Stealthwatch Cloud in AWS Describing Cloud Security Management Describe Cloud Management and APIs Explain API Protection Illustrate an API Example: Integrate to ISE Using pxGrid Identify SecDevOps Best Practices Illustrate a Cisco Cloud Security Management Tool Example: Cisco Defense Orchestrator Illustrate a Cisco Cloud Security Management Tool Example: Cisco CloudCenter? Describe Cisco Application Centric Infrastructure (ACI) Describe AWS Reporting Tools Additional course details: Nexus Humans Cisco Securing Cloud Deployments with Cisco Technologies v1.0 (SECCLD) training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Cisco Securing Cloud Deployments with Cisco Technologies v1.0 (SECCLD) course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Introduction to Writing SQL Queries (TTSQL003)
By Nexus Human
Duration 3 Days 18 CPD hours This course is intended for This is an introductory- level course appropriate for those who are developing applications using relational databases, or who are using SQL to extract and analyze data from databases and need to use the full power of SQL queries. Overview This course combines expert lecture, real-world demonstrations and group discussions with machine-based practical labs and exercises. Working in a hands-on learning environment led by our expert practitioner, attendees will learn to: Maximize the potential of SQL to build powerful, complex and robust SQL queries Query multiple tables with inner joins, outer joins and self joins Construct recursive common table expressions Summarize data using aggregation and grouping Execute analytic functions to calculate ranks Build simple and correlated subqueries Thoroughly test SQL queries to avoid common errors Select the most efficient solution to complex SQL problems A company?s success hinges on responsible, accurate database management. Organizations rely on highly available data to complete all sorts of tasks, from creating marketing reports and invoicing customers to setting financial goals. Data professionals like analysts, developers and architects are tasked with creating, optimizing, managing and analyzing data from databases ? with little room for error. When databases aren?t built or maintained correctly, it?s easy to mishandle or lose valuable data. Our SQL Programming and Database Training Series provides students with the skills they require to develop, analyze and maintain data and in correctly structured, modern and secure databases. SQL is the cornerstone of all relational database operations. In this hands-on course, you learn to exploit the full potential of the SELECT statement to write robust queries using the best query method for your application, test your queries, and avoid common errors and pitfalls. It also teaches alternative solutions to given problems, enabling you to choose the most efficient solution in each situation. Introduction: Quick Tools Review Introduction to SQL and its development environments Using SQL*PLUS Using SQL Developer Using the SQL SELECT Statement Capabilities of the SELECT statement Arithmetic expressions and NULL values in the SELECT statement Column aliases Use of concatenation operator, literal character strings, alternative quote operator, and the DISTINCT keyword Use of the DESCRIBE command Restricting and Sorting Data Limiting the Rows Rules of precedence for operators in an expression Substitution Variables Using the DEFINE and VERIFY command Single-Row Functions Describe the differences between single row and multiple row functions Manipulate strings with character function in the SELECT and WHERE clauses Manipulate numbers with the ROUND, TRUNC and MOD functions Perform arithmetic with date data Manipulate dates with the date functions Conversion Functions and Expressions Describe implicit and explicit data type conversion Use the TO_CHAR, TO_NUMBER, and TO_DATE conversion functions Nest multiple functions Apply the NVL, NULLIF, and COALESCE functions to data Decode/Case Statements Using the Group Functions and Aggregated Data Group Functions Creating Groups of Data Having Clause Cube/Rollup Clause SQL Joins and Join Types Introduction to JOINS Types of Joins Natural join Self-join Non equijoins OUTER join Using Subqueries Introduction to Subqueries Single Row Subqueries Multiple Row Subqueries Using the SET Operators Set Operators UNION and UNION ALL operator INTERSECT operator MINUS operator Matching the SELECT statements Using Data Manipulation Language (DML) statements Data Manipulation Language Database Transactions Insert Update Delete Merge Using Data Definition Language (DDL) Data Definition Language Create Alter Drop Data Dictionary Views Introduction to Data Dictionary Describe the Data Dictionary Structure Using the Data Dictionary views Querying the Data Dictionary Views Dynamic Performance Views Creating Sequences, Synonyms, Indexes Creating sequences Creating synonyms Creating indexes Index Types Creating Views Creating Views Altering Views Replacing Views Managing Schema Objects Managing constraints Creating and using temporary tables Creating and using external tables Retrieving Data Using Subqueries Retrieving Data by Using a Subquery as Source Working with Multiple-Column subqueries Correlated Subqueries Non-Correlated Subqueries Using Subqueries to Manipulate Data Using the Check Option Subqueries in Updates and Deletes In-line Views Data Control Language (DCL) System privileges Creating a role Object privileges Revoking object privileges Manipulating Data Overview of the Explicit Default Feature Using multitable INSERTs Using the MERGE statement Tracking Changes in Data

Bespoke bass guitar and music theory & harmony lessons for young students and adults in a friendly environment by a professional bass player. Whether you're a Beginner, Intermediate or Advanced player, I can give you the proper tools to take your bass playing to the next level. I provide tailored lessons to the individual that are specifically designed to enhance the right skills and to help you achieve your goals as a player and a musician. Musical Subjects Being Taught: • Bass Technique and Fretboard Knowledge • Sight Reading • Music Theory & Harmony • Ear Training • Styles & Bassline Creation • Groove, Feel & Timing • Bass Gear & Tone Tips • Exam Preparation

Safeguarding Your Most Vulnerable Pupils & Students
By Brightcore Consultancy
Ensuring the safety and wellbeing of vulnerable pupils and students is more challenging than ever. This masterclass is designed to equip key safeguarding staff with the knowledge and strategies needed to navigate the complexities of protecting our most at risk young people. In an ever changing landscape, where safeguarding concerns are becoming increasingly complex, this session will explore the key vulnerabilities affecting students today and the practical changes that can lead to earlier identification and intervention. We will examine critical areas of concern, statutory safeguarding requirements, key statistics and the risk factors that place students at heightened risk. Additionally, we will review best practices for providing effective support, ensuring that every young person receives the protection and care they need.

HA Webinar: How can we ensure we have an ambitious and well-structured primary history curriculum?
5.0(1)By Historical Association
Historical Association webinar series: Draft Ofsted toolkits; implications for primary history Presenter: Dan Hartley This session will explore ways to enable pupils to develop secure, deep and fluent knowledge across the curriculum in primary history. It will consider how a curriculum can be designed, including the foundations laid at EYFS, to ensure pupils have a coherent and planned pathway to enable them to engage in future history learning. To use your corporate webinar offer for this webinar please complete this form: https://forms.office.com/e/qG8gK0CU8X

Historical Association webinar series: Building different types of historical knowledge Presenters: Claire Holliss This third session will focus on how a range of different teachers have dealt with student misconceptions about interpretations. It will first consider how teachers have helped their students to read the work of historians sensitively and will then discuss how teachers have designed teaching sequences to build students’ understanding of this aspect of the discipline. To use your corporate webinar offer on this webinar please fill in this form: https://forms.office.com/e/9JZCQ0RUkJ

