- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
2974 Design courses in Salisbury delivered Live Online
Certified Data Centre Professional (CDCP)
By Nexus Human
Duration 2 Days 12 CPD hours This course is intended for The primary audience for this course is any IT, facilities or data centre professional who works in and around the data centre and who has the responsibility to achieve and improve the availability and manageability of the data centre. Overview After completion of the course the participant will be able to:? Choose an optimum site for mission-critical data centre based on current and future needs? Describe all components that are important for high availability in a data centre and how to effectively setup the data centre? Name and apply the various industry standards? Describe the various technologies for UPS, fire suppression, cooling, monitoring systems, cabling standards, etc, and to select and apply them effectively to cost-efficiently enhance the high-availability of the data centre.? Review the electrical distribution system to avoid costly downtime? Enhance cooling capabilities and efficiency in the data centre by using existing and new techniques and technologies for the increased cooling requirements of the future? Design a highly reliable and scalable network architecture and learn how to ensure installers apply proper testing techniques? Create effective maintenance contracts with equipment suppliers ensuring the best return on investment? Setup effective data centre monitoring ensuring the right people get the right message? Ensure proper security measures, both procedural and technical, are established to safeguard your company's valuable information in the data centre The course will address how to setup and improve key aspects such as power, cooling, security, cabling, safety, etc., to ensure a high available data centre. It will also address key operations and maintenance aspects. The Data Centre, it?s Importance and Causes for DowntimeData Centre Standards and Best PracticesData Centre Location, Building and Construction Selecting appropriate sites and buildings and how to avoid pitfalls Various components of an effective data centre and supporting facilities setup Raised Floor/Suspended Ceiling Uniform, concentrated and rolling load definitions Applicable standards Raised Floor guidelines Signal Reference Grid, grounding of racks Disability act and regulations Suspended ceiling usage and requirements Light Standards Light fixture types and placement Emergency lighting, Emergency Power Supply (EPS) Power Infrastructure Power infrastructure layout from generation to rack level ATS and STS systems Redundancy levels and techniques Three-phase and single-phase usage Power distribution options within the computer room Power cabling versus bus bar trunking Bonding versus grounding Common Mode Noise and isolation transformers Distribution boards, form factors and IP-protection grades Power quality guidelines Real power versus apparent power How to size and calculate load in the data centre Generators Static and dynamic UPS systems, selection criteria, how they operate and energy efficiency option Battery types, correct selection and testing Thermo-graphics Electro Magnetic Fields Electrical fields and magnetic fields definitions and units of measurements Sources of EMF Effects of EMF on human health and equipment (H)EMP Standards EMF shielding solutions Equipment Racks Rack standards, properties and selection criteria Security considerations Power rail/strip options Cooling Infrastructure Temperature and humidity recommendations Cooling measurement units and conversion rates Sensible and latent heat definitions Differences between comfort and precision cooling Overview of different air conditioner technologies Raised floor versus non-raised floor cooling Placement of air conditioner units and limitations to be observed Supplemental cooling options Cold aisle/hot aisle containment Water Supply Importance of water supply and application areas Backup water supply techniques Designing a Scalable Network Infrastructure The importance of a Structured Cabling System Planning considerations Copper and Fiber cable technology and standards ANSI/TIA-942 Cabling hierarchy and recommendations Testing and verification SAN storage cabling Network redundancy Building-to-building connectivity Network monitoring system requirements Fire Suppression Standards for fire suppression Detection systems Various total flooding fire suppression techniques and systems, their benefits and disadvantages Handheld extinguishers Signage and safety Regulatory requirements and best practices Data Centre Monitoring Data centre monitoring requirements EMS versus BMS Water leak detection systems Notification options and considerations Operational Security and Safety Practices Data centre security layers Physical, infrastructure and organisational security Safety measures and essential signage Labelling Choosing a labelling scheme Recommended labelling practices Network labelling Documentation How to setup proper documentation Document management policies and procedures Cleaning Cleaning practices for the data centre MTBF/MTTR Standards and definitions Calculation models The ?real? value Maintenance Contracts/SLA/OLAEXAM: Certified Data Centre Professional Additional course details: Nexus Humans Certified Data Centre Professional (CDCP) training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Certified Data Centre Professional (CDCP) course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Professional Management Programme
By Mpi Learning - Professional Learning And Development Provider
Professional Management is crucial to your company's success. In fact, managers can have the single largest impact on your organisation's productivity and overall profitability, with more influence over employee morale and performance than anyone else.

European Data Protection & Privacy Programme Management - DPO Ready
By Training Centre
European Data Protection Principles of Data Protection in Europe covers the essential pan-European and national data protection laws, as well as industry-standard best practices for corporate compliance with these laws. Those taking this course will gain an understanding of the European model for privacy enforcement, key privacy terminology and practical concepts concerning the protection of personal data and trans-border data flows. The training is based on the body of knowledge for the IAPP's ANSI-accredited Certified Information Privacy Professional/Europe (CIPP/E) certification program. Privacy Programme Management Principles of Privacy Management is the how-to training on implementing a privacy program framework, managing the privacy program operational lifecycle and structuring a knowledgeable, high-performing privacy team. Those taking this course will learn the skills to manage privacy in an organisation through process and technology-regardless of jurisdiction or industry. The Principles of Privacy Program Management training is based on the body of knowledge for the IAPP's ANSI-accredited Certified Information Privacy Manager (CIPM) certification programme. Make a difference in your organization and in your career. The CIPM designation says that you're a leader in privacy program administration and that you've got the goods to establish, maintain and manage a privacy program across all stages of its lifecycle. About This Course Delivered in a modular format, this four day course covers Days 1 & 2 Module 1: Data Protection Laws Introduces key European data protection laws and regulatory bodies, describing the evolution toward a Harmonised European Legislative Framework. Module 2: Personal Data Defines and differentiates between types of data-including personal, anonymous, pseudo-anonymous and special categories. Module 3: Controllers and Processors Describes the roles and relationships of controllers and processors. Module 4: Processing Personal Data Defines data processing and GDPR processing principles, Explains the application of the GDPR and outlines the legitimate bases for processing personal data. Module 5: Information provision Explains controller obligations for providing information about data processing activities to data subjects and Supervisory Authorities. Module 6: Data Subjects 'Rights Describes data subjects' rights, applications of rights and obligations controller and processor. Module 7: Security or Processing Discusses considerations and duties of controllers and processors for Ensuring security of personal data and providing notification of data breaches. Module 8: Accountability Investigates accountability requirements, data protection management systems, data protection impact assessments, privacy policies and the role of the data protection officer. Module 9: International Data Transfers Outlines options and obligations for transferring data outside the European Economic Area, Decisions adequacy and appropriateness safeguards and derogations. Module 10: Supervision and Enforcement Describes the role, powers and procedures or Supervisory Authorities; the composition and tasks of the European Data Protection Board; the role of the European Data Protection Supervisor; and remedies, liabilities and penalties for non-compliance. Module 11: Compliance Discusses the applications of European data protection law, legal bases and compliance requirements for processing personal data in practice, employers-including processing employee data, surveillance, direct marketing, Internet technology and communications and outsourcing. Days 3 & 4 Module 1: Introduction to privacy program management Identifies privacy program management responsibilities, and describes the role of accountability in privacy program management. Module 2: Privacy governance Examines considerations for developing and implementing a privacy program, including the position of the privacy function within the organization, role of the DPO, program scope and charter, privacy strategy, support and ongoing involvement of key functions and privacy frameworks. Module 3: Applicable laws and regulations Discusses the regulatory environment, common elements across jurisdictions and strategies for aligning compliance with organizational strategy. Module 4: Data assessments Relates practical processes for creating and using data inventories/maps, gap analyses, privacy assessments, privacy impact assessments/data protection impact assessments and vendor assessments. Module 5: Policies Describes common types of privacy-related policies, outlines components and offers strategies for implementation. Module 6: Data subject rights Discusses operational considerations for communicating and ensuring data subject rights, including privacy notice, choice and consent, access and rectification, data portability, and erasure and the right to be forgotten. Module 7: Training and awareness Outlines strategies for developing and implementing privacy training and awareness programs. Module 8: Protecting personal information Examines a holistic approach to protecting personal information through privacy by design. Module 9: Data breach incident plans Provides guidance on planning for and responding to a data security incident or breach. Module 10: Measuring, monitoring and auditing program performance Relates common practices for monitoring, measuring, analyzing and auditing privacy program performance Prerequisites There are no prerequisites for this course but attendees would benefit from a review of the materials on the IAPP SITE What's Included? 1 years membership of the IAPP Breakfast, Lunch, mid-morning and afternoon snacks, teas, coffees Official Study Guides* Official Participant Guides* Official Exam Q&A's* Both exam fees * In electronic format for Live Online and hard copy for Classroom delegates Who Should Attend? This course is suitable for aspiring Data Protection Officers, as well as Information Security Managers, Lawyers, Data Managers, Analysts and Risk Teams. Provided by Our Guarantee We are an approved IAPP Training Partner. You can learn wherever and whenever you want with our robust classroom and interactive online training courses. Our courses are taught by qualified practitioners with a minimum of 25 years commercial experience. We strive to give our delegates the hands-on experience. Our courses are all-inclusive with no hidden extras. The one-off cost covers the training, all course materials, and exam voucher. Our aim: To achieve a 100% first time pass rate on all our instructor-led courses. Our Promise: Pass first time or 'train' again for FREE. *FREE training offered for retakes - come back within a year and only pay for the exam.

Values Based Recruitment
By Mpi Learning - Professional Learning And Development Provider
Recruiting great people to our organisations is the key to high performance and sustainable business success.

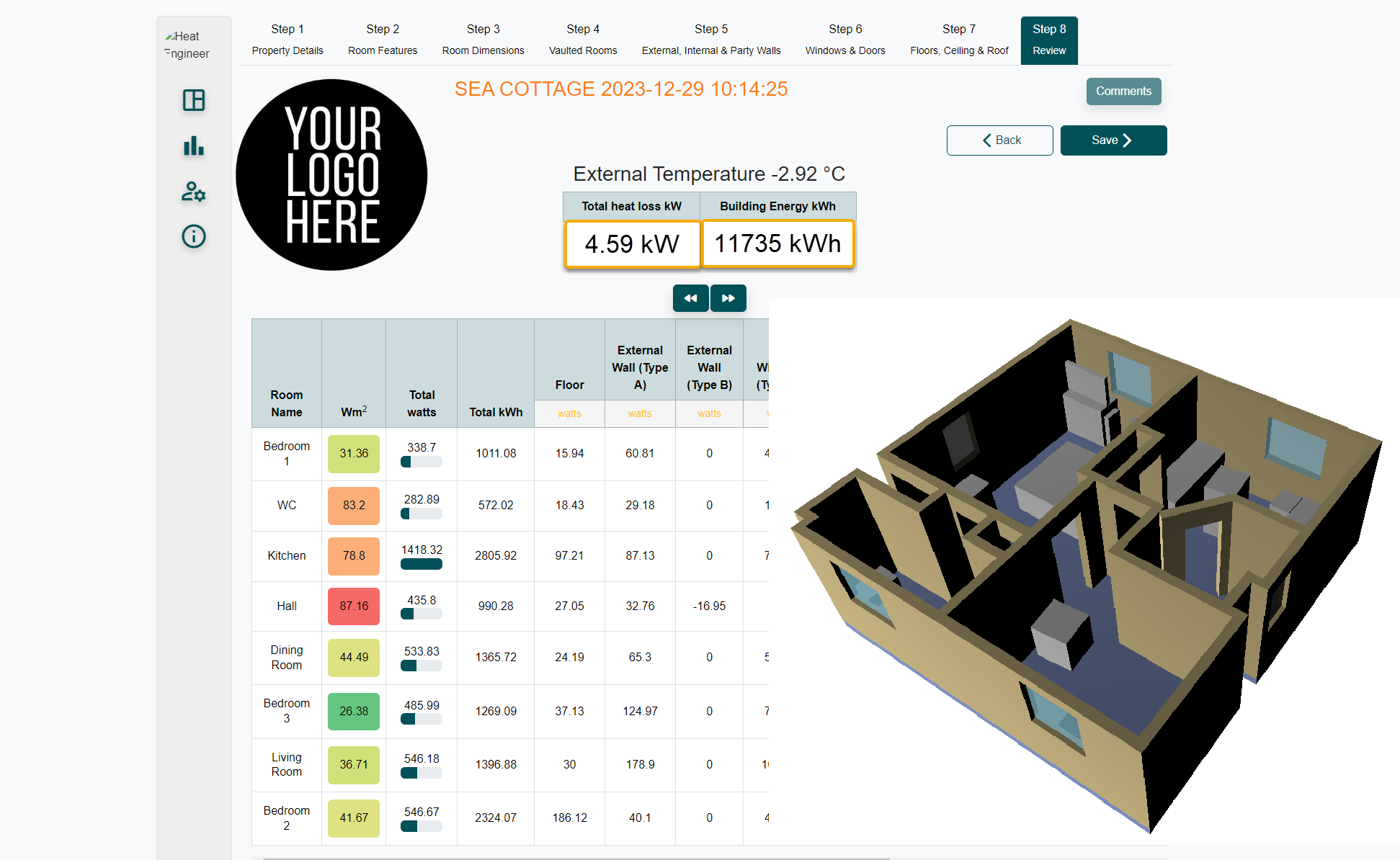
This is designed to be an introduction into how to start a room by room survey using the new CAD Heat Engineer feature, using the online dashboard. We will then go through the different steps to complete this heat loss report. Optional pages will also be worked through and shown. Examples of how to select the flow temperature and the heat source (heat pumps and boilers) will be presented once the heat loss result is completed.
Becoming a Professional Market Trader: A Workshop for Young Entrepreneurs
By North Essex Economic Board
Are you a young entrepreneur eager to start your journey as a market trader? Join us for an interactive and practical workshop designed to give you the skills, knowledge, and confidence to succeed in the competitive world of market trading!

Certified Information Privacy Manager (CIPM)
By Training Centre
Make a difference in your organization and in your career. The CIPM designation says that you're a leader in privacy program administration and that you've got the goods to establish, maintain and manage a privacy program across all stages of its lifecycle. The CIPM is the world's first and only certification in privacy program management. When you earn a CIPM, it shows that you don't just know privacy regulations-you know how to make it work for your organization. In other words, you're the go-to person for day-to-day operations when it comes to privacy. Developed in collaboration with the law firms, Bird and Bird, Field Fisher, Wilson/Sonsini and Covington and Burling, the CIPM encompasses pan-European and national data protection laws, key privacy terminology and practical concepts concerning the determination of control measures designed to protect personal data and trans-border data flows. About This Course Delivered in a modular format, the course covers; Module 1: Introduction to privacy program management Identifies privacy program management responsibilities, and describes the role of accountability in privacy program management. Module 2: Privacy governance Examines considerations for developing and implementing a privacy program, including the position of the privacy function within the organization, role of the DPO, program scope and charter, privacy strategy, support and ongoing involvement of key functions and privacy frameworks. Module 3: Applicable laws and regulations Discusses the regulatory environment, common elements across jurisdictions and strategies for aligning compliance with organizational strategy. Module 4: Data assessments Relates practical processes for creating and using data inventories/maps, gap analyses, privacy assessments, privacy impact assessments/data protection impact assessments and vendor assessments. Module 5: Policies Describes common types of privacy-related policies, outlines components and offers strategies for implementation. Module 6: Data subject rights Discusses operational considerations for communicating and ensuring data subject rights, including privacy notice, choice and consent, access and rectification, data portability, and erasure and the right to be forgotten. Module 7: Training and awareness Outlines strategies for developing and implementing privacy training and awareness programs. Module 8: Protecting personal information Examines a holistic approach to protecting personal information through privacy by design. Module 9: Data breach incident plans Provides guidance on planning for and responding to a data security incident or breach. Module 10: Measuring, monitoring and auditing program performance Relates common practices for monitoring, measuring, analyzing and auditing privacy program performance The CIPM body of knowledge outlines all the concepts and topics that you need to know to become certified. The exam blueprint gives you an idea of how many questions from each topic area you can expect on the exam. Prerequisites There are no prerequisites for this course but attendees would benefit from a review of the materials on the IAPP site What's Included? Breakfast, Lunch and refreshments (Classroom based courses only) The Official Study Guide (Privacy Programme Management - Third Edition)* Official Exam Q&A's* Official Practice Exam Participant Guide* 1 years membership of the IAPP The Exam Fees * In electronic format for Live Online and hard copy for Classroom delegates Who Should Attend? The CIPM is ideal for IT and information security leaders responsible for developing Data Protection frameworks and applying best practice, including those in the following positions: Data Analysts Cyber Security Analysts and Managers Aspiring Data Protection Officers IT Managers Accreditation Our Guarantee We are an approved IAPP Training Partner. You can learn wherever and whenever you want with our robust classroom and interactive online training courses. Our courses are taught by qualified practitioners with a minimum of 25 years commercial experience. We strive to give our delegates the hands-on experience. Our courses are all-inclusive with no hidden extras. The one-off cost covers the training, all course materials, and exam voucher. Our aim: To achieve a 100% first time pass rate on all our instructor-led courses. Our Promise: Pass first time or 'train' again for FREE. *FREE training offered for retakes - come back within a year and only pay for the exam.

Certified Information Privacy Professional (CIPP/E)
By Training Centre
The IAPP offers the most encompassing, up-to-date and sought-after global training and certification program for privacy and data protection. The Certified Information Privacy Professional (CIPP) helps organizations around the world bolster compliance and risk mitigation practices, and arms practitioners with the insight needed to add more value to their businesses. Skilled privacy pros are in high demand and IAPP certification is what employers want. When you earn an IAPP credential, you earn the right to be recognized as part of an elite group of knowledgeable, capable and dedicated privacy professionals. With the GDPR effective as of May 2018, among its mandates was the requirement to appoint knowledgeable DPOs (data protection officers) tasked with monitoring compliance, managing internal data protection activities, training data processing staff, conducting internal audits and more. There's a lot to know, there's a lot at stake and there's a lot of opportunity for privacy professionals with the right training and education. Achieving a CIPP/E credential shows you have the comprehensive GDPR knowledge, perspective and understanding to ensure compliance and data protection success in Europe-and to take advantage of the career opportunity this sweeping legislation represents. About This Course Delivered in a Modular format, the course includes; Module 1: Data Protection Laws Introduces key European data protection laws and regulatory bodies, describing the evolution toward a Harmonised European Legislative Framework. Module 2: Personal Data Defines and differentiates between types of data-including personal, anonymous, pseudo-anonymous and special categories. Module 3: Controllers and Processors Describes the roles and relationships of controllers and processors. Module 4: Processing Personal Data Defines data processing and GDPR processing principles, Explains the application of the GDPR and outlines the legitimate bases for processing personal data. Module 5: Information provision Explains controller obligations for providing information about data processing activities to data subjects and Supervisory Authorities. Module 6: Data Subjects 'Rights Describes data subjects' rights, applications of rights and obligations controller and processor. Module 7: Security or Processing Discusses considerations and duties of controllers and processors for Ensuring security of personal data and providing notification of data breaches. Module 8: Accountability Investigates accountability requirements, data protection management systems, data protection impact assessments, privacy policies and the role of the data protection officer. Module 9: International Data Transfers Outlines options and obligations for transferring data outside the European Economic Area, Decisions adequacy and appropriateness safeguards and derogations. Module 10: Supervision and Enforcement Describes the role, powers and procedures or Supervisory Authorities; the composition and tasks of the European Data Protection Board; the role of the European Data Protection Supervisor; and remedies, liabilities and penalties for non-compliance. Module 11: Compliance Discusses the applications of European data protection law, legal bases and compliance requirements for processing personal data in practice, employers-including processing employee data, surveillance, direct marketing, Internet technology and communications and outsourcing. Prerequisites There are no prerequisites for this course but candidates would benefit from reading the freely available materials found on the IAPP website. What's Included? 1 years membership of the IAPP Breakfast, Lunch and refreshments (Classroom courses only) Official Study Guide (European Data Protection, Law & Practice)* Participant Guide* Official Exam Q&A* Official Practice Exam Official Practice Exam* The Exam Fees * In electronic format for Live Online and hard copy for Classroom delegates Who Should Attend? The CIPP/E is ideal for IT and information security leaders responsible for applying best practices to cloud security architecture, design, operations and service orchestration, including those in the following positions: Cybersecurity Analysts Data Analysts Security Administrators Aspiring Data Protection Officers Accreditation Our Guarantee We are an approved IAPP Training Partner. You can learn wherever and whenever you want with our robust classroom and interactive online training courses. Our courses are taught by qualified practitioners with a minimum of 25 years commercial experience. We strive to give our delegates the hands-on experience. Our courses are all-inclusive with no hidden extras. The one-off cost covers the training, all course materials, and exam voucher. Our aim: To achieve a 100% first time pass rate on all our instructor-led courses. Our Promise: Pass first time or 'train' again for FREE. *FREE training offered for retakes - come back within a year and only pay for the exam.

FPSO Operations Management & Safety
By EnergyEdge - Training for a Sustainable Energy Future
About this Training Course This five-day training course will cover aspects of FPSO operations with an emphasis on management of safety. A background of the methodology used to generate the various safety plans and codes used in the operational safety case will be covered. The course will also review general operational guidelines in the offshore environment to ensure that the operations are completed as designed. This will include offtake operations and maintenance processes for the plant and vessel as well as a session on subsea. Training Objectives To enable participants to obtain an in-depth understanding of FPSO operations, safety and maintenance: Provide a broad overview of how an FPSO operation is set up and established in the field Grasp the various methods used to moor the production units Analyse information and methods required to establish the operation according to local and international regulations. Assess the methods used to calculate the safety parameters and requirements to construct an approved valid safety case Explore conditions to monitor during operations with regards to safety and structure Inspect various types of hazards associated with production and produced materials Review regular and emergency operational maintenance requirements Examine cyclones and weather events causing disconnection Comprehend manning, training requirements and operations including cargo Case studies and Exercises: The training course uses real life examples and case studies to explain the setup, preparation, implementation and operational activities required to successfully complete FPSO operations from a safety and maintenance perspective. This will allow the application of participants' newly-acquired knowledge. Case studies also stimulate independent thinking and discussion among the participants. Case Studies The case studies proposed for this course will include: A group exercise to consider what is the minimum requirement for the production of a safety case Generic plan for the development of a maintenance management system using computer software systems (e.g. Amos) Construction of a UWILD plan to include scope and potential tendering requirements Quizzes The various quizzes can be expanded or arranged to suit the group/interests and topics covered but will generally include the following topics: Mooring types and location where they are primarily used Safety cases Safety management systems Process hazards and mitigation UWILD components and regulations Operations management Offtake operations Target Audience The course is generally aimed at personnel who are involved in FPSO operations as either offshore crew or onshore support team members. This course will also greatly benefit the following groups but not limited to: Process engineers Surveyors Facility engineers Naval architects Operations engineer Health, Safety, Environment (HSE) specialists and managers Maintenance engineers Course Level Intermediate Training Methods The training course is presented in an interactive workshop format that allows for discussion. The course will be delivered through analysis of case studies and running examples of problems. Course Duration: 5 days in total (35 hours) The training instructor relies on a highly interactive training method to enhance the learning process. This method ensures that all participants gain a complete understanding of all the topics covered. The training comprises of information supplemented by visual activities including photographs from various operations and videos of operational and safety activities. Interaction verbally will be necessary to achieve the best learning outcome from the materials. Course timings and breaks 0830 - Registration 0900 - Start of training 1030 - Morning break 1045 - Training recommences 1230 - Lunch break 1330 - Training recommences 1515 - Afternoon break 1530 - Training recommences 1700 - End of training Trainer Your expert course leader has been involved in the Oil and Gas industry for over 28 years in several different roles commencing as a second deck officer on FPSO's and moving through the industry from deck officer to Master, OIM and Field Superintendent. He has also been in charge of semisubmersible and fixed production platforms as field superintendent before moving ashore into senior management roles. On completion of industry specific activities, he moved to teaching roles at South Tyneside Maritime College in the department of marine and simulation and presented live courses to maritime students from cadet to Master. Prior to returning to Perth in March 2019, he was training manager for a subsidiary of Gaz Transport and Technigaz of France. He has a Master Class 1 certificate with endorsements for hazardous cargoes and a Graduate Certificate in Business Administration as well as multiple course certificates required to operate FPSO's, platforms and semisubmersible facilities. He has been involved in the preparation of national standards for Safety Cases (Australia); Designing and structural setup of competency-based training systems in South East Asia. He was also involved in the development of minimum standards, competency profiles position based and preparation and implementation of training plans to ensure competency in the local staff in Asian operations. He was part of the development team for minimum standards of offshore safety in Australian offshore operations including the implementation of the Common Safety Training Program (CSTP). He was also involved in implementing training plans for both simulator and classroom based courses in LNG operations and cargo tank design and construction. Highlighted work experience: Premier Petroleum Myanmar Ltd Petronas Carigali Newfield Australia (Cartier) Pty Ltd: FPSO Jabiru Venture FPSO Challis Venture Onshore OIM Australian FPSO Management Pty. Ltd. POST TRAINING COACHING SUPPORT (OPTIONAL) To further optimise your learning experience from our courses, we also offer individualized 'One to One' coaching support for 2 hours post training. We can help improve your competence in your chosen area of interest, based on your learning needs and available hours. This is a great opportunity to improve your capability and confidence in a particular area of expertise. It will be delivered over a secure video conference call by one of our senior trainers. They will work with you to create a tailor-made coaching program that will help you achieve your goals faster. Request for further information post training support and fees applicable Accreditions And Affliations

CNS-420 Citrix (NetScaler) Networking Assessment, Design, and Advanced Configuration
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for Built for IT Professionals with extensive networking and Citrix ADC experience. This course is built for IT Professionals who are responsible for defining the overall structure or architecture of a Citrix networking environment. This course encompasses advanced Citrix networking configurations and leading Citrix design principles. Overview How to identify and prioritize business drivers, constraints, and requirements using the Citrix Consulting methodology Assess environment requirements and learn to apply leading design principles to address them in a multi-site Citrix ADC deployment Apply advanced authentication and load balancing principles In this expert level 5-day training course you will be exposed to advanced networking and Citrix ADC concepts and configurations. Through lecture, lab exercises, and real-world case studies, you will learn to look critically at environment requirements, constraints, and business drivers to create a complex Citrix networking solution. Topics to be covered in this course include multi-site and multitenant deployments, advanced authentication and load balancing, and automation and orchestration and advanced troubleshooting. This training will also prepare you for the Citrix Certified Expert in Networking (CCE-N) exam. Module 1: Networking Methodology and Assessment Understanding the Citrix methodology Business Drivers and Requirementrs User Segmentation Application Assessment Capabilities Assessment Module 2: Citrix Networking Deployment Architecture and Topology Multi-Site Deployments Multi Tennant Infrastructure Cloud Deployments High Availability Citrix ADC Double-Hop Scenarios Secure Web Gateway Module 3: Advanced Authentication and Authorization Authorization Policies Access Policies Advanced Authentication Options Multi-Factor Authentication nFactor Authentication AAA Session Management Module 4: Citrix ADC Security Authorization Pre-authentication and Endpoint Analysis Scans Protection against Layer 4-7 Attacks Web App Firewall Module 5: Citrix Gateway Configuration Considerations ICA Proxy Configuration VPN Access Clientless Access Split Tunneling RDP Proxy Deployment and Configuration Module 6: Advanced Load Distribution and Link Load balancing Advanced Load Balancing Advanced Load Balancing Link Load Balancing Firewall Load Balancing Microsoft Exchange Load Balancing Advanced Global Server Load Balancing Global Server Load Balancing Persistence DNS, Policies, Expressions, Actions, and Views GSLB Monitoring and Considerations Module 7: Application Delivery Management Automation and Orchestration Application Delivery Management Outbound Traffic Dashboard Automation Orchestration Configuration Jobs Configuration Audit NITRO API StyleBooks (Net-new)
