- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
Staff Retention Workshop - Part 1 & 2
By The Development People
This 2 x 2.5 hour workshop is for healthcare managers & leaders that want to explore staff retention, how it is effecting their organisation, and consider what they can do to improve.

Staff Retention Techniques
By OnlineCoursesLearning.com
Introduction: Staff retention is a growing concern, but by having a proper staff retention strategy in place you'll be able to keep your top employees. Recruiting and training a new employee is time-consuming and costs a great deal of revenue - it's much more beneficial to the business to keep current employees satisfied in their job. Understanding your employees and having proper retention strategies in place is key to retaining employees long-term. This course on staff retention will look at the four main trends that contribute to employees leaving their jobs, including compensation and benefits, career growth, flexible working schedules, and training and development, and how you can create a strategy to improve these areas and retain your employees. You Will Learn: What the main factors are that lead to employees leaving their jobs and what you can do to prevent this. How to come up with a competitive compensations and benefits plan. How to encourage career advancement and growth opportunities in your company. The benefits of flexible working, both to the employer and employee. How to implement various training and development techniques and the benefits of encouraging training in the workplace. Benefits of Taking This Course: You will learn what drives employees to leave and with this knowledge be able to implement preventative measures. You will learn how implementing employee retention programmes can help reduce unnecessary turnover costs. You will gain insight into retaining a positive and motivated body of staff. You will learn the benefits that retaining your staff can bring to your business. Your knowledge will allow you to formulate an effective retention plan that works for your employees and business. Course Modules/Lessons Module 1: Staff Retention Techniques Introduction Module 2: Compensation and Benefits Module 3: Career Advancement and Opportunities for Growth Module 4: Flexible Work Schedules Module 5: Training and Development
Overview Uplift Your Career & Skill Up to Your Dream Job - Learning Simplified From Home! Kickstart your career & boost your employability by helping you discover your skills, talents and interests with our special Talent Management & Employee Retention Techniques Course. You'll create a pathway to your ideal job as this course is designed to uplift your career in the relevant industry. It provides professional training that employers are looking for in today's workplaces. The Talent Management & Employee Retention Techniques Course is one of the most prestigious training offered at StudyHub and is highly valued by employers for good reason. This Talent Management & Employee Retention Techniques Course has been designed by industry experts to provide our learners with the best learning experience possible to increase their understanding of their chosen field. This Talent Management & Employee Retention Techniques Course, like every one of Study Hub's courses, is meticulously developed and well researched. Every one of the topics is divided into elementary modules, allowing our students to grasp each lesson quickly. At StudyHub, we don't just offer courses; we also provide a valuable teaching process. When you buy a course from StudyHub, you get unlimited Lifetime access with 24/7 dedicated tutor support. Why buy this Talent Management & Employee Retention Techniques? Unlimited access to the course for forever Digital Certificate, Transcript, student ID all included in the price Absolutely no hidden fees Directly receive CPD accredited qualifications after course completion Receive one to one assistance on every weekday from professionals Immediately receive the PDF certificate after passing Receive the original copies of your certificate and transcript on the next working day Easily learn the skills and knowledge from the comfort of your home Certification After studying the course materials of the Talent Management & Employee Retention Techniques there will be a written assignment test which you can take either during or at the end of the course. After successfully passing the test you will be able to claim the pdf certificate for £5.99. Original Hard Copy certificates need to be ordered at an additional cost of £9.60. Who is this course for? This Talent Management & Employee Retention Techniques course is ideal for Students Recent graduates Job Seekers Anyone interested in this topic People already working in the relevant fields and want to polish their knowledge and skill. Prerequisites This Talent Management & Employee Retention Techniques does not require you to have any prior qualifications or experience. You can just enrol and start learning.This Talent Management & Employee Retention Techniques was made by professionals and it is compatible with all PC's, Mac's, tablets and smartphones. You will be able to access the course from anywhere at any time as long as you have a good enough internet connection. Career path As this course comes with multiple courses included as bonus, you will be able to pursue multiple occupations. This Talent Management & Employee Retention Techniques is a great way for you to gain multiple skills from the comfort of your home. Course Curriculum Section 1: Introduction Unit 1: Welcome to the Course 00:05:00 Unit 2: Course Highlights 00:03:00 Unit 3: Quick Activity 00:02:00 Section 2: Core Concepts Unit 1: What does Talent Management Mean 00:06:00 Unit 2: Steps for Talent Management Process 00:05:00 Unit 3: Meaning of Talent Acquisition 00:06:00 Unit 4: 4 Tips to Hire the Best Employees 00:06:00 Unit 5: Training & Developing Employees + Quick Tips 00:05:00 Unit 6: Why Companies Spend Million Dollars in Training & Development 00:04:00 Unit 7: Why Employee Retention is Important for a Company 00:03:00 Unit 8: Employee Retention Techniques 00:07:00 Section 3: Best Employee Retention Strategies That Actually Work Unit 1: Why These Strategies Are So Useful 00:01:00 Unit 2: 1st Retention Strategy 00:06:00 Unit 3: 2nd Retention Strategy 00:11:00 Unit 4: Quick Activity - Here's How to Use It 00:01:00 Section 4: Employee Benefits & Retention Strategies Used by World's Top Companies Unit 1: Section Introduction 00:01:00 Unit 2: How Google Takes Care of its Employees 00:12:00 Unit 3: How Microsoft Retains it's Employees 00:06:00 Unit 4: Key Takeaway 00:04:00 Section 5: Practical Tips to Retain Employees in Your Organisation Unit 1: Offer Quick Incentives 00:03:00 Unit 2: Show Career Growth 00:02:00 Unit 3: Praising & Rewarding 00:02:00 Unit 4: Make it Convenient 00:03:00 Unit 5: Sponsor Education 00:02:00 Section 6: Bonus Section: Building a Strong Relation with Employees Unit 1: 3 Words to Retain Your Best Employees 00:03:00 Section 7: Conclusion Unit 1: Conclusion 00:01:00 Resources Resources - Talent Management & Employee Retention Techniques 00:00:00 Assignment Assignment - Talent Management & Employee Retention Techniques 00:00:00

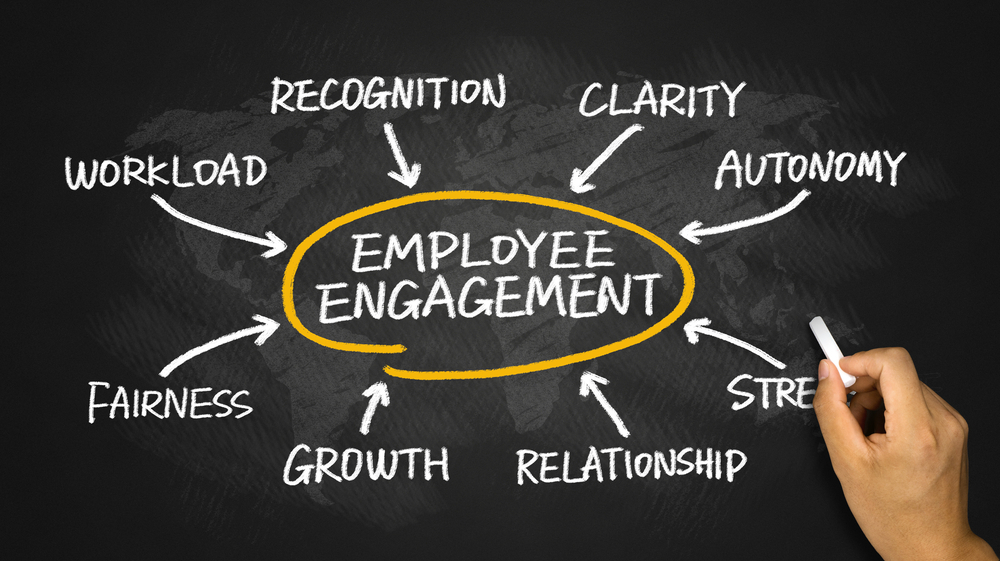
Imagine transforming your workplace into a thriving hub of motivated and engaged employees. 'Employee Engagement and Retention Strategies' offers a blueprint to achieving just that. This immersive course begins by laying the groundwork on the significance of employee engagement and its profound impact on organizational success. You will be guided through the nuances of fostering a motivating work environment, understanding that the heart of productivity and innovation lies in how valued and involved employees feel. As you progress, the course delves into the analytical aspect of engagement - understanding employee sentiment through surveys and data analysis. This insight is pivotal in crafting tailored engagement strategies. In the realms of leadership and team building, you will uncover techniques to inspire and manage teams for optimal engagement. The journey through this course further empowers you with the skills to support employee development and career growth, recognising that the growth of individuals fuels the advancement of the entire organisation. With a focus on recognition, rewards, and incentives, you will learn how to create a culture of appreciation and achievement, key elements in retaining top talent. Learning Outcomes Understand the essentials of employee engagement and its organisational impact. Create and maintain a motivating work environment. Effectively utilise employee engagement surveys for strategic insights. Apply leadership and management skills to boost employee engagement. Design and implement effective recognition and reward systems. Why choose this Employee Engagement and Retention Strategies course? Unlimited access to the course for a lifetime. Opportunity to earn a certificate accredited by the CPD Quality Standards and CIQ after completing this course. Structured lesson planning in line with industry standards. Immerse yourself in innovative and captivating course materials and activities. Assessments designed to evaluate advanced cognitive abilities and skill proficiency. Flexibility to complete the Course at your own pace, on your own schedule. Receive full tutor support throughout the week, from Monday to Friday, to enhance your learning experience. Unlock career resources for CV improvement, interview readiness, and job success. Who is this Employee Engagement and Retention Strategies course for? HR professionals aiming to enhance engagement strategies. Team leaders and managers seeking to boost team morale. Organisational development consultants. Business owners focused on employee retention. Professionals in employee relations and personnel management. Career path Human Resources Manager - £30,000 to £50,000 Employee Engagement Specialist - £28,000 to £45,000 Organisational Development Consultant - £35,000 to £60,000 Team Leader/Manager - £32,000 to £48,000 Compensation and Benefits Manager - £33,000 to £55,000 Talent Acquisition Specialist - £27,000 to £42,000 Prerequisites This Employee Engagement and Retention Strategies does not require you to have any prior qualifications or experience. You can just enrol and start learning.This Employee Engagement and Retention Strategies was made by professionals and it is compatible with all PC's, Mac's, tablets and smartphones. You will be able to access the course from anywhere at any time as long as you have a good enough internet connection. Certification After studying the course materials, there will be a written assignment test which you can take at the end of the course. After successfully passing the test you will be able to claim the pdf certificate for £4.99 Original Hard Copy certificates need to be ordered at an additional cost of £8. Course Curriculum Module 01: Introduction to Employee Engagement and Its Impact Introduction to Employee Engagement and Its Impact 00:15:00 Module 02: Understanding Motivation and Creating a Motivating Work Environment Understanding Motivation and Creating a Motivating Work Environment 00:19:00 Module 03: Employee Engagement Surveys and Data Analysis Employee Engagement Surveys and Data Analysis 00:18:00 Module 04: Leadership and Management for Employee Engagement Leadership and Management for Employee Engagement 00:19:00 Module 05: Building Effective Teams for High Engagement Building Effective Teams for High Engagement 00:20:00 Module 06: Employee Development and Career Growth Employee Development and Career Growth 00:17:00 Module 07: Recognition, Rewards, and Incentives Recognition, Rewards, and Incentives 00:21:00

Customer Service: Customer Retention Specialist Training
By Compliance Central
The demand for Customer Retention Specialists is on the rise, driven by the need to improve customer loyalty and reduce churn. Recent statistics indicate a 20% increase in job postings for Customer Retention Specialists in the past year. These professionals can expect to earn an average salary ranging from £25,000 to £35,000 per year, with the potential for higher earnings based on experience and industry. Their role in preserving valuable customer relationships makes them valuable assets to businesses seeking long-term success. Are you looking to enhance your Customer Service skills? If yes, then you have come to the right place. Our comprehensive course on Customer Service will assist you in producing the best possible outcome by mastering the Customer Service skills. The Customer Service course is for those who want to be successful. In the Customer Service course, you will learn the essential knowledge needed to become well versed in Customer Service. Our Customer Service course starts with the basics of Customer Service and gradually progresses towards advanced topics. Therefore, each lesson of this Customer Service course is intuitive and easy to understand. Why would you choose the Customer Service course from Compliance Central: Lifetime access to Customer Service course materials Full tutor support is available from Monday to Friday with the Customer Service course Learn Customer Service skills at your own pace from the comfort of your home Gain a complete understanding of Customer Service course Accessible, informative Customer Service learning modules designed by expert instructors Get 24/7 help or advice from our email and live chat teams with the Customer Service Study Customer Service in your own time through your computer, tablet or mobile device A 100% learning satisfaction guarantee with your Customer Service Course Customer Service: Customer Retention Specialist Training Curriculum Breakdown of the Customer Service Course Transform your career with the Customer Retention Specialist Bundle! Perfect your skills and stand out in the employment market with our comprehensive training program. Impress potential employers and add valuable expertise to your resume. Don't wait-enrol in the Customer Retention Specialist Bundle now and take the first step towards a successful and fulfilling career! Course Outline: WHY Customer Service Is CRITICAL To Your Business! Good Isn't Good Enough! We Are ALL in the 'Helping Field' Providing 'Concierge' Level Of Service The 5 Tenets Of TQM How To Boost Customer Satisfaction How To Avoid The 10 Deadly Sins Of Customer Service! More Money $$$ - Through Customer Retention How Much Is A Customer Worth? Do You Understand Your Customer? Dealing With Difficult Customers 'LEAP' Into Customer Service! Exceptional Phone Service WHY Customers Buy From YOU! BONUS LECTURE!!! FINAL TIPS!!! CPD 10 CPD hours / points Accredited by CPD Quality Standards Who is this course for? The Customer Service course helps aspiring professionals who want to obtain the knowledge and familiarise themselves with the skillsets to pursue a career in Customer Service. It is also great for professionals who are already working in Customer Service and want to get promoted at work. Requirements To enrol in this Customer Service course, all you need is a basic understanding of the English Language and an internet connection. Career path Customer Service Representative: £18,000 to £25,000 per year Call Center Supervisor: £22,000 to £30,000 per year Customer Success Manager: £30,000 to £45,000 per year Customer Experience Specialist: £25,000 to £35,000 per year Client Relations Manager: £35,000 to £50,000 per year Customer Service Team Leader: £25,000 to £40,000 per year Certificates CPD Accredited PDF Certificate Digital certificate - Included CPD Accredited Hardcopy Certificate Hard copy certificate - £10.79 CPD Accredited Hardcopy Certificate Delivery Charge: Inside the UK: Free Outside of the UK: £9.99 each

People don't leave organizations, they leave people. We will show you a tool you can use to retain employees. Reward, empowerment, training, appreciation, involvement and care are all vital for employees. Learn how to motivate your staff and realize why the quality of leadership and management are important. Learning Objectives Identify two keys to employee retention, Summarize the R.E.T.A.I. N. system for improving employee retention, Explain strategies for nurturing employees Target Audience Managers, Team Leaders, Young Professionals, Sales Professionals, Customer Service Teams

Professional Certificate Course in Effective Talent Sourcing and Retention in London 2024
4.9(261)By Metropolitan School of Business & Management UK
The aim of this course is to provide participants with a comprehensive understanding of Talent Management, including the War for Talent and talent types, Competency-based Management, Four Stages of Competence, Competency Architecture, Recruitment and Retention practices, and Succession Planning and its Process. Participants will gain insight into effective Talent Management practices that are crucial to an organization's success in attracting, developing, and retaining top talent. After the successful completion of the course, you will be able to learn about the following, War for Talent and talent Types. Competency-based Management. Four Stages of Competence. Competency Architecture. Recruitment and Retention. Succession Planning and its Process. The aim of this course is to provide an overview of Talent Management, including the War for Talent and the different talent types, Competency-based Management, the Four Stages of Competence, Competency Architecture, Recruitment and Retention practices, and Succession Planning and its Process. By the end of this module, learners will have gained a fundamental understanding of Talent Management and the key practices involved in effectively managing talent. The aim of this course is to provide an overview of Talent Management, including the War for Talent and the different talent types, Competency-based Management, the Four Stages of Competence, Competency Architecture, Recruitment and Retention practices, and Succession Planning and its Process. By the end of this module, participants will have gained a fundamental understanding of Talent Management and the key practices involved in effectively managing talent. VIDEO - Course Structure and Assessment Guidelines Watch this video to gain further insight. Navigating the MSBM Study Portal Watch this video to gain further insight. Interacting with Lectures/Learning Components Watch this video to gain further insight. Effective Talent Sourcing and Retention Self-paced pre-recorded learning content on this topic. Effective Talent Sourcing and Retention Put your knowledge to the test with this quiz. Read each question carefully and choose the response that you feel is correct. All MSBM courses are accredited by the relevant partners and awarding bodies. Please refer to MSBM accreditation in about us for more details. There are no strict entry requirements for this course. Work experience will be added advantage to understanding the content of the course. The certificate is designed to enhance the learner's knowledge in the field. This certificate is for everyone eager to know more and get updated on current ideas in their respective field. We recommend this certificate for the following audience. Talent Acquisition Manager Recruiter HR Business Partner Recruitment Coordinator Employer Branding Specialist Employee Retention Specialist HR Generalist Staffing Manager Talent Development Manager HR Talent Acquisition Consultant Average Completion Time 2 Weeks Accreditation 3 CPD Hours Level Advanced Start Time Anytime 100% Online Study online with ease. Unlimited Access 24/7 unlimited access with pre-recorded lectures. Low Fees Our fees are low and easy to pay online.

The Diploma in HR and Marketing (Recruitment & Retention) Course offers a deep dive into two crucial business functions: human resources and marketing. This course is designed for those looking to sharpen their ability to recruit the best talent and keep them engaged for the long term. Learn how to blend HR strategies with marketing techniques to create effective recruitment campaigns and retention strategies. Understand the importance of aligning brand messaging with recruitment practices and how the two can work together to build a strong, sustainable workforce. In today’s competitive job market, it’s not enough to just fill positions – it’s about finding the right people and keeping them happy. This course will guide you through modern HR techniques for recruitment, retention, and employee satisfaction, while seamlessly integrating marketing principles to make your efforts even more successful. With the knowledge gained, you'll be well-equipped to manage the talent lifecycle, develop strong employer branding, and create a workplace where both employees and employers flourish. Whether you're new to the field or looking to enhance your expertise, this course provides valuable insights without needing to step outside your office. Learning Outcomes of Recruitment, HR and marketing - Recruitment & Retention Learn Strategic HR and Marketing Policies Know the Details of HR and Marketing Operations Understand How to Use Marketing Tools Use of Social Media Marketing for Branding Get Knowledge of Hiring, Safe Recruitment, and Talent Hunting Key Features of HR and marketing - Recruitment & Retention Accredited by CPD Instant PDF certificate Fully online, interactive HR and Marketing course with audio voiceover Enrol now in this HR and Marketing - Recruitment & Retention course to excel! The Curriculum of HR and Marketing- Recruitment & Retention Course Module 01: Human Resource Management Module 02: Introduction to Safer Recruitment Training Module 03: Recruitment Methods Module 04: The UK Recruitment Legislation Module 05: Key Skills and Issues in Recruitment Module 06: Virtual Interviewing Module 07: Business operations Module 08: Organisational Studies Module 09: HR and marketing & Advertising Module 10: Fundamentals of Digital Marketing Module 11: LinkedIn Marketing Module 12: Facebook Marketing Module 13: E-Mail Marketing Module 14: Use of Social Networks Module 15: Talent Management and The Role of Recruiting Module 16: Attract and Hire the Best Talents Module 17: Job Analysis and Design Module 18: Final Thoughts and On-boarding Accreditation All of our courses included in this HR and Marketing (Recruitment and Retention) are fully CPD accredited. Certification Once you've successfully completed your Recruitment, HR and Marketing course, you will immediately be sent digital certificates for the bundle courses. CPD 30 CPD hours / points Accredited by CPD Quality Standards Who is this course for? This Level 3 Diploma in HR and Marketing - Recruitment and Retention course is suitable for anyone also interested in: CIPD HR practice HR Management Level 3 Certificate in Principles of Human Resource (HR) Practice (RQF) Human resources management Level 7 Diploma in Human Resource Management CIPD Level 7 Advanced Diploma in Human Resource Management Level 3 Certificate in Principles of Human Resource (HR) Practice (RQF) NCFE Level 3 Diploma in Skills for Business: Human Resources Requirements There are no formal requirements for this HR and Marketing - Recruitment courses to be enrolled. Career path HR Administration Assistant HR Administrator HR and Marketing Assistant HR Manager Recruitment Officer Marketing Manager Certificates Certificate of completion (HARDCOPY) Hard copy certificate - Included You will get the hard copy certificates for Free! The delivery charge of the hard copy certificate inside the UK is £3.99 each. Certificate of completion (PDF) Digital certificate - Included

Customer Retention
By OnlineCoursesLearning.com
Client Retention Certification Each business should manage disappointed clients every once in a while. Seeing how to determine client complaints so they return later on is critical to growing a business' benefits and notoriety. In this course, you will realize how fruitful organizations deal with hold their clients and how they utilize the standards of incredible client assistance to rapidly resolve objections. You will figure out how to speak with troublesome clients, how to utilize grievances as a chance to improve and how your demeanor can have a significant effect in settling a difficult circumstance. You Will Learn: Why each client merits remarkable help and how to react if a client submits an outlandish question The most effective method to cause a client to feel esteemed and regarded The most effective method to tune in to a client, show sympathy and pose the correct inquiries when they submit a question Why staff need to have adequate foundation information on the items and administrations they are selling Why critical thinking is a key ability you should create to appease a disappointed client Advantages of Taking This Course: On the off chance that you work in client care or aftersales, this course will show you how to determine client complaints rapidly and productively In the event that you direct representatives who work in client assistance, this course will assist you with investigating issues and improve consumer loyalty The relational abilities you will learn on this course are appropriate to other business circumstances, for example, haggling in gatherings This course will help you rethink client objections as a chance to improve the business, which thus will expand income

Discover effective employee engagement and retention strategies in this comprehensive course. Learn key principles of motivation, leadership techniques, team building, and data analysis to foster a dynamic work environment. Explore methods for employee development, recognition, and career growth to enhance organizational performance and employee satisfaction. Enroll now to optimize your workforce and drive success.