- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
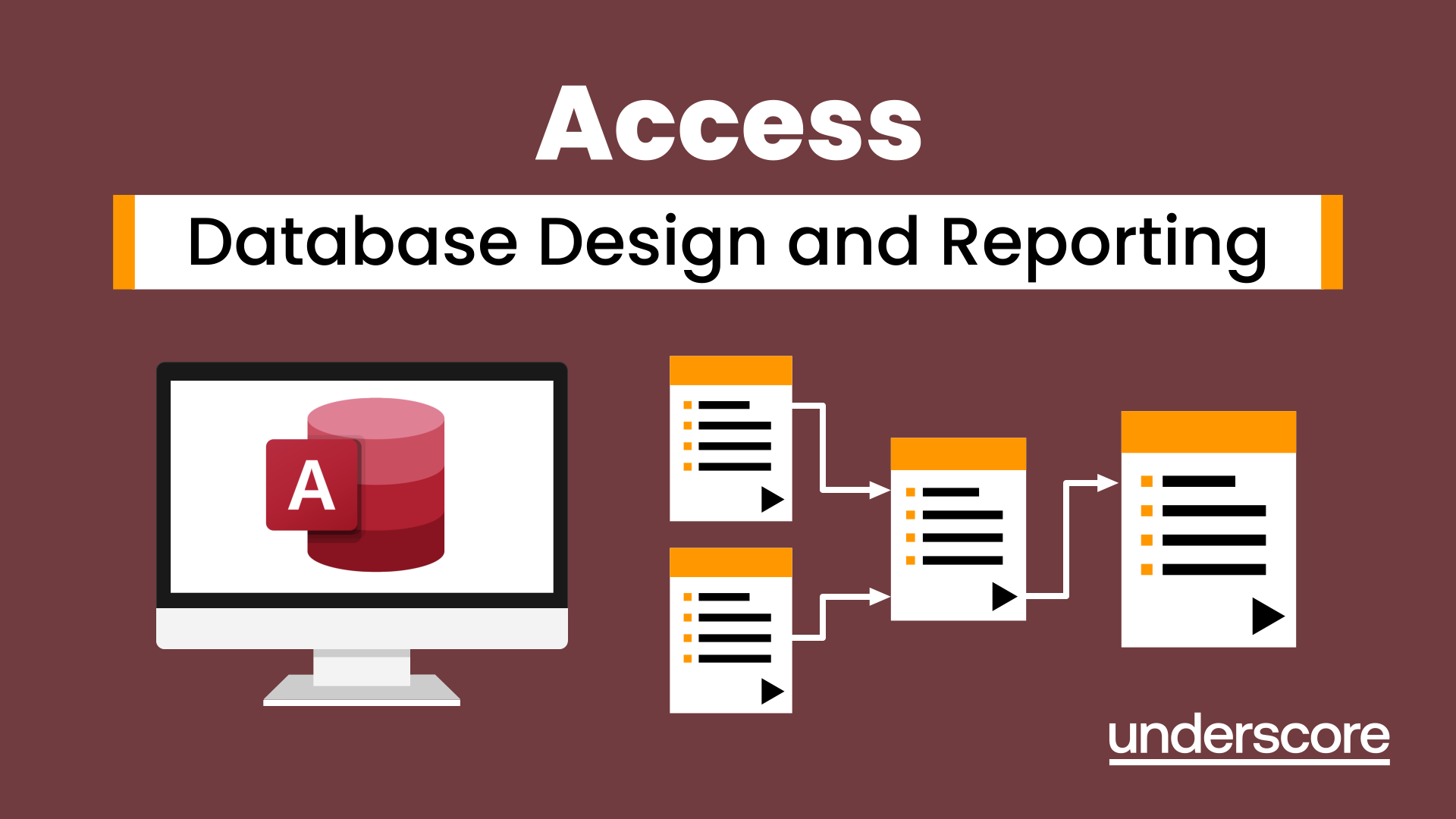
Access - Database Design and Reporting
By Underscore Group
Learn how to create fully relational databases and how to input, extract and report on data. Course overview Duration: 2 days (13 hours) Our Access Database Design and reporting course looks at the key elements to building fully relational databases and entering and extracting information from them. This course is designed for new users who need to build relational database systems. Objectives By the end of the course you will be able to: Create a new database Create data tables Set field validation and properties Enter data and manage data Create forms Use queries to extract data Create parameter queries Create calculations in queries Build relational databases Use sub datasheets Build multi table queries Use advanced form and report design techniques Content Creating a database Creating a new database Database elements Creating a data table Setting field properties Using input masks Using input masks Validation rules Default values Setting a primary key Creating lookup fields Data entry Adding data Deleting data Quick keys for data entry Working with data Sorting data Filtering data Finding information Navigation Creating data form Creating quick forms The form wizard Amending forms Formatting Setting the tab order Entering data using forms Creating queries Creating a query Setting criteria Using the expression builder Creating parameter queries Using wildcards Using more than one parameter Using calculations in queries Adding a totals row Formatting results Adding calculations Printing and reporting Printing tables and queries Creating reports Building and amending reports Adding headers and footers Working with relational databases Relational database principles Importing data from other sources Linking information between tables One-to-one and one-to-many links Defining referential integrity Amending links Deleting links Sub datasheets Viewing a subdatasheet Removing a subdatasheet Connecting a subdatasheet Multiple table queries Deciding which tables to use Adding tables to the query Creating links between tables Setting join properties Advanced form design Field properties Creating lookup fields Adding calculated fields Applying conditional formatting Advanced report design Field properties Report properties Alternate colour bandings Concatenating fields Adding calculated fields Sorting and grouping Grouping settings Adding headers and footers Adding dates, times, page numbers
AWS Technical Essentials
By Nexus Human
Duration 1 Days 6 CPD hours This course is intended for Individuals responsible for articulating the technical benefits of AWS services Individuals interested in learning how to get started with using AWS SysOps Administrators, Solution Architects and Developers interested in using AWS services Overview Recognize terminology and concepts as they relate to the AWS platform and navigate the AWS Management Console. Understand the foundational services, including Amazon Elastic Compute Cloud (EC2), Amazon Virtual Private Cloud (VPC), Amazon Simple Storage Service (S3), and Amazon Elastic Block Store (EBS). Understand the security measures AWS provides and key concepts of AWS Identity and Access Management (IAM). Understand AWS database services, including Amazon DynamoDB and Amazon Relational Database Service (RDS). Understand AWS management tools, including Auto Scaling, Amazon CloudWatch, Elastic Load Balancing (ELB), and AWS Trusted Advisor. AWS Technical Essentials introduces you to AWS services, and common solutions. It provides you with fundamental knowledge to become more proficient in identifying AWS services. It helps you make informed decisions about IT solutions based on your business requirements and get started working on AWS. Prerequisites Working knowledge of distributed systems Familiarity with general networking concepts Working knowledge of multi-tier architectures Familiarity with cloud computing concepts 1 - AWS introduction and history AWS Global Infrastructure Demonstration: AWS Management Console 2 - AWS Storage Identify key AWS storage options Describe Amazon EBS Create an Amazon S3 bucket and manage associated objects 3 - Compute, network and storage services Amazon Elastic Compute Cloud (EC2) Amazon Virtual Private Cloud (VPC) Amazon Simple Storage Service (S3) Amazon Elastic Block Store (EBS) Demonstration: Amazon Simple Storage Service (S3) Hands-on lab: Build your VPC and launch a web server 4 - AWS Security, AWS Identity and Access Management (IAM) AWS Identity and Access Management (IAM) Demonstration: AWS Identity and Access Management (IAM) 5 - Compute Services & Networking Identify the different AWS compute and networking options Describe an Amazon Virtual Private Cloud (VPC) Create an Amazon EC2 instance Use Amazon EBS with Amazon EC2 6 - Managed Services & Database Describe Amazon DynamoDB Understand key aspects of Amazon RDS Launch an Amazon RDS instance 7 - Databases (RDS, DynamoDB) SQL and NoSQL databases Data storage considerations Hands-on lab: Build your database server and connect to it 8 - AWS elasticity and management tools Auto scaling Load balancing Cloud Watch Trusted Advisor Hands-on lab: Scale and load balance your architecture 9 - Deployment and Management Identify what is CloudFormation Describe Amazon CloudWatch metrics and alarms Describe Amazon Identity and Access Management (IAM)

ICA Diploma in Financial Crime Prevention
By International Compliance Association
ICA International Diploma in Financial Crime Prevention This advanced level qualification will better equip you to meet the many challenges associated with identifying, understanding, and mitigating financial crime risks including fraud, cybercrime, corruption, money laundering and terrorist financing. It will deepen your understanding and enhance your professional credibility. Benefits of studying with ICA: Flexible learning solutions that are suited to you Our learner-centric approach means that you will gain relevant practical and academic skills and knowledge that can be used in your current role Improve your career options by undertaking a globally recognised qualification that hiring managers look for as part of their hiring criteria Many students have stated that they have received a promotion and/or pay rise as a direct result of gaining their qualification The qualifications ensure that you are enabled to develop strategies to help manage and prevent risk within your firm, thus making you an invaluable asset within the current climate. This course is awarded in association with Alliance Manchester Business School, the University of Manchester. how will you learn 9-month course assessed by 3 written assignments (3,000 - 3,500 words) A mixture of guided online study and participation in live sessions:2 x virtual classrooms1 x immersive learning scenario (putting you at the centre of a story)3 x tutorials (a chance to discuss elements of the course in more depth)3 x assessment preparation sessions Videos covering the latest industry developments and case studies Access to the ICA members' portal containing additional reading and resources Proactive support throughout the course to help you stay on track Completion of the ICA Diploma in Financial Crime Prevention training course will produce the following outcomes: Professional qualification: ICA Diploma in Financial Crime Prevention-participants will be able to use the designation 'Dip (Fin.Crime).' Eligibility to apply for Professional membership of the ICA Detailed knowledge on the nature of financial crime Practical understanding of best practice and how to prevent financial crime This course is awarded in association with Alliance Manchester Business School, the University of Manchester. This ICA Diploma in Financial Crime Prevention provides Participants with in-depth knowledge and skills in the following areas: Understanding and managing financial crime Practical application of the International Standards The prevention and detection of specific financial crime risks Data and information security Bribery and corruption Electronic crime Investigation, prosecution and recovery.

AWS Security Essentials
By Nexus Human
Duration 1 Days 6 CPD hours This course is intended for Security IT business-level professionals interested in cloud security practices Security professionals with minimal to no working knowledge of AWS Overview Assimilate Identify security benefits and responsibilities of using the AWS Cloud Describe the access control and management features of AWS Explain the available methods for providing encryption of data in transit and data at rest when storing your data in AWS. Describe how to secure network access to your AWS resources Determine which AWS services can be used for monitoring and incident response This course covers fundamental AWS cloud security concepts, including AWS access control, data encryption methods, and how network access to your AWS infrastructure can be secured. Based on the AWS Shared Security Model, you learn where you are responsible for implementing security in the AWS Cloud and what security-oriented services are available to you and why and how the security services can help meet the security needs of your organization. Prerequisites Working knowledge of IT security practices and infrastructure concepts, familiarity with cloud computing concepts 1 - Security on AWS Security design principles in the AWS Cloud AWS Shared Responsibility Model 2 - Security OF the Cloud AWS Global Infrastructure Data center security Compliance and governance 3 - Security IN the Cloud ? Part 1 Identity and access management Data protection essentials Lab 01 ? Introduction to security policies 4 - Security IN the Cloud ? Part 2 Securing your infrastructure Monitoring and detective controls Lab 02 ? Securing VPC resources with Security Groups 5 - Security IN the Cloud ? Part 3 DDoS mitigation Incident response essentials Lab 03 ? Remediating issues with AWS Config Conformance Packs 6 - Course Wrap Up AWS Well-Architected tool overview Next Steps Additional course details: Nexus Humans AWS Security Essentials training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the AWS Security Essentials course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

24th September Diana Beaumont #Agent121. Looking for: ADULT FICTION, NON-FICTION
5.0(3)By I Am In Print
LOOKING FOR: ADULT FICTION, NON-FICTION Diana joined the prestigious DHH Literary Agency in June 2024. She started agenting with Rupert Heath Literary Agency in 2011 before moving to UTA and Marjacq in 2017. Before that she was senior commissioning editor at Transworld. Diana was chosen as one of The Bookseller’s Rising Stars of 2012, was a nominee for RNA Agent of the Year 2019, and was shortlisted for Literary Agent of the Year 2022 at the British Book Awards. Her list includes a wide range of bestselling and prize-winning authors in the UK and internationally. Diana represents adult fiction and non-fiction. For fiction, she is looking for upmarket women's commercial, with depth and heart, including reading group, historical, saga, uplit and contemporary stories that are irreverent and make her laugh; accessible literary fiction, high-concept crime fiction and thrillers. She has a thing for spy novels and would love to find a great vampire story. On the non-fiction side: memoir, smart, funny feminists, lifestyle, cookery and social justice, and open to anything with a strong, original voice. She also encourages submissions from writers who have been traditionally under-represented. Diana would like you to submit a covering letter, 1 - 2 page synopsis and the first three chapters (a maximum of 5,000 words) of your manuscript in a single word document. (In addition to the paid sessions, Diana is kindly offering one free session for low income/underrepresented writers. Please email agent121@iaminprint.co.uk to apply, outlining your case for this option which is offered at the discretion of I Am In Print). By booking you understand you need to conduct an internet connection test with I Am In Print prior to the event. You also agree to email your material in one document to reach I Am In Print by the stated submission deadline and note that I Am In Print take no responsibility for the advice received during your agent meeting. The submission deadline is: Wednesday 17th September 2025

ANXIETY – UNDERSTANDING AND INCLUDING CHILDREN AND YOUNG PEOPLE
By Inclusive Solutions
In this practical workshop session we will explore ways of including young people of all ages who experience anxiety some of whom may well be on the autism spectrum. The session will be values based and practical and will aim to allow the sharing of experiences and good practice as well as promoting innovative approaches to inclusion through the design of best practice. Course Category Autism and Communication Inclusion Parents and Carers Behaviour and Relationships Meeting emotional needs Description In this practical workshop session we will explore ways of including anxious children in mainstream schools and settings. The session will be values based and practical and will aim to allow the sharing of experiences and good practice as well as promoting innovative approaches to inclusion through the design of best practice. Family perspectives and experiences will also be explored. This is not a ‘medical model’ day on anxiety. Testimonials ‘Really gave me an idea of how people feel and helped me think how to plan to meet their needs.’ ‘Really useful insights’ Learning Objectives Increased confidence and understanding regarding including anxious children Access to a wider range of practical strategies to impact on anxiety Deeper understanding of core values surrounding inclusion New skills and processes to strengthen the inclusion of anxious children Insights and understanding of sensory sensitivities Understanding increased in area of movement differences Who Is It For? Personal Assistants Teachers Heads and deputies Guidance staff Learning support teams SENCOs Primary and secondary teachers Parents Brothers and sisters Local authority support services Community workers and carers Course Content The course answers the questions : What is anxiety? How do we go about including anxious children? Can we understand more deeply what is going on underneath concerning behaviours? Key themes include: Movement differences Supports and Accommodations for Sensory Sensitivities Developing Friendships and Peer Support Learning to Listen

IP security training course description Connection to the Internet is becoming an essential business tool. This course looks at firewalls, digital certificates, encryption and other essential topics for e-commerce sites. A generic course that looks at firewalls and VPNs. Hands on sessions include using hacking tools and configuring firewalls. What will you learn Describe: Basic security attacks RADIUS SSL IPSec VPNs Implement digital certificates Deploy firewalls to protect Web servers and users. Secure Web servers and clients. IP security training course details Who will benefit: Network administrators. Network operators. Security auditors Prerequisites: TCP/IP foundation for engineers Duration 2 days IP security training course contents TCP/IP review Brief overview of the relevant headers. Hands on Download software for course, use analyser to capture passwords on the wire. Security review Policies, Types of security breach, denial of service, data manipulation, data theft, data destruction, security checklists, incident response. Security exploits The Internet worm, IP spoofing, SYN attack, hijacking, Ping o' Death⦠keeping up to date with new threats. Hands on Use a port scanning tool, use a 'hacking' tool. Firewalls Products, Packet filtering, DMZ, content filtering, stateful packet inspection, Proxies, firewall architectures, Intrusion Detection Systems, Viruses. Hands on Set up a firewall and prevent attacks. NAT NAT and PAT, Why use NAT, NAT-ALG, RSIP. Encryption Encryption keys, Encryption strengths, Secret key vs Public key, algorithms, systems, SSL, SSH, Public Key Infrastructures. Hands on Run a password-cracking program. Authentication Types of authentication, Securid, Biometrics, PGP, Digital certificates, X.509 v3, Certificate authorities, CRLs, PPP authentication, RADIUS. Hands on Using certificates. Web client and server security Cookies, browser certificates, censorship, PICS. Operating system security, Web server user authentication, Restricting access, Logging, Securing CGI scripts. Hands on Browser security. VPNs and IPSec What is a VPN, tunnelling, L2F, PPTP, L2TP, IPSec, AH, ESP, transport mode, tunnel mode.

CIRCLES OF ADULTS
By Inclusive Solutions
Circles of adults is a process that ‘listens deeper’ to generate reflective problem solving that can create lasting behaviour change and effective behaviour intervention plans. This is a particularly valuable process for those looking to enhance their leadership and facilitation skills or to build such processes into their school or team approach to complex pupils. ‘The question is not should they be here anymore. Now it’s how can we figure out how best to include them?’ In this practical workshop session we will explore ways of problem solving around complex situations. The session will be practical and will aim to allow the sharing of experiences and good practice as well promoting innovative approaches to problem solving around systemic, organisational as well as individual inclusion issues. Behaviour problems, relationship challenges and personnel dilemmas can all be worked on with these team oriented problem solving processes. We will introduce participants to a powerful and effective approach. The ‘Circles of Adults’ approach addresses the need for a problem solving process that is able to take an in-depth look at meeting the emotional needs that commonly underlie challenging behaviour in schools. The approach is co-facilitated and is designed to enable the participation of teacher teams to reach a deeper understanding of a young person and to evolve a set of hypotheses and emerging strategies that better accommodate to unmet emotional and learning needs. The approach takes at least 90 minutes and is intended for use with the most challenging young people, those at high risk of being permanently excluded from the regular school system. Learning Objectives Increased confidence regarding problem solving around inclusion in mainstream settings Access to a wider range of practical strategies and techniques to impact on communication, realtionship, learning and behaviour issues Learn new problem solving processes Course Content The course answers the questions : How to set up and run a Circle of Adults process How can we work out how to include this child best? How can we understand what lies beneath their behaviour? Is there a more structured way to run this meeting? Can we explore the emotional impact the person is having on us and still agree strategies? How can I get unstuck from this problem?
Transform 1:1 Programme
By Butterfly Minds
1:1 wellbeing programmes for parents and carergivers in neurodiverse families to help you feel less overwhelmed, more energised, and present. Are you exhausted from the constant demands of neurodivergent parenting? Do you find yourself caught in an endless cycle of stress, worrying about what tomorrow might bring? You deserve to prioritise yourself without feeling guilty. After all, taking care of yourself benefits your whole family. And what's even better is that you don't need to sacrifice your time or energy to do so! Who are these programmes for? This programme is designed especially for parents and caregivers, in neurodiverse families, who: Want to feel calmer in daily life Are ready to start prioritising their mental and emotional wellbeing with 1-to-1 support Desire a deeper connection with themselves and want to rediscover their sense of identify outside of their caring responsibilities. Because you deserve to be someone outside a parent/carer. By the end of the programme you'll: Feel less stressed Have new healthy habits that nurture your wellbeing Have more energy, because running on empty isn't good for anyone Feel grounded and present, even during challenging times Notice a calmer mind and feel more intentional with your time and energy. How it Works A mindful approach to escape the cycle of burnout. Based on my Burnout Prevention Method and 4-step ARIA Framework: Awareness Reflection Insight Action A 12-week journey to reset your energy and stop burnout before it happens Tailored guidance, support, and encouragement via voice notes & messaging x2 days a week (Tuesdays and Wednesdays) Monthly reflection to acknowledge your journey and celebrate yourself A personalised self-care plan, so you can continue taking care of yourself beyond our time working together. Plus you'll get… Lifetime access to: Online course ‘The Mindful Reconnect’ (worth £399), so you can continue your mindfulness journey and be supported beyond the programme. Self Care Bundle People pay £77 for this, but you get it for free! Have more tools to support you on your wellbeing journey. Next Steps Imagine the calm and joy you can create with ongoing support and encouragement. It's a investment in you and your family’s wellbeing. Due to the personalised support offered, spaces are very limited. Don’t let another day slip by feeling overwhelmed and exhausted. Please note: The booking will ask you to select a date after the payment page. Please select the date as the day you are booking. Take the first step today

