- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
Certified Diploma in Email Marketing
By iStudy UK
Marketing these days is not an easy feat. If you are looking to sell a product, you will have hundreds of competitors each looking to undercut you and steal your customers. Well in that case you also need to up your game, and one way to do that is through opt-in lists. This Certified Diploma in Email Marketing course is just the place for you to get started. Many opt-in marketing ploys fail because sellers try to jump right into the program. The first thing you need to do though is gain the trust of your customers. Through this diploma level course you will not only learn to make your subscribers trust you quickly but also get tips to build your subscriber list. The course then divulges into making certain that you are able grab your reader's attention and make them beg for more. You will also discover things to consider when publishing a newsletter and things to avoid when emailing your list. Finally you will learn about seven ways to make money using nothing more than your list. So what are you waiting for, get started on this course immediately if you want to learn more about email marketing. Course Highlights Certified Diploma in Email Marketing is an award winning and the best selling course that has been given the CPD Certification & IAO accreditation. It is the most suitable course anyone looking to work in this or relevant sector. It is considered one of the perfect courses in the UK that can help students/learners to get familiar with the topic and gain necessary skills to perform well in this field. We have packed Certified Diploma in Email Marketing into 15 modules for teaching you everything you need to become successful in this profession. To provide you ease of access, this course is designed for both part-time and full-time students. You can become accredited in just 13 hours, 10 minutes and it is also possible to study at your own pace. We have experienced tutors who will help you throughout the comprehensive syllabus of this course and answer all your queries through email. For further clarification, you will be able to recognize your qualification by checking the validity from our dedicated website. Why You Should Choose Certified Diploma in Email Marketing Lifetime access to the course No hidden fees or exam charges CPD Accredited certification on successful completion Full Tutor support on weekdays (Monday - Friday) Efficient exam system, assessment and instant results Download Printable PDF certificate immediately after completion Obtain the original print copy of your certificate, dispatch the next working day for as little as £9. Improve your chance of gaining professional skills and better earning potential. Who is this Course for? Certified Diploma in Email Marketing is CPD certified and IAO accredited. This makes it perfect for anyone trying to learn potential professional skills. As there is no experience and qualification required for this course, it is available for all students from any academic backgrounds. Requirements Our Certified Diploma in Email Marketing is fully compatible with any kind of device. Whether you are using Windows computer, Mac, smartphones or tablets, you will get the same experience while learning. Besides that, you will be able to access the course with any kind of internet connection from anywhere at any time without any kind of limitation. Career Path You will be ready to enter the relevant job market after completing this course. You will be able to gain necessary knowledge and skills required to succeed in this sector. All our Diplomas' are CPD and IAO accredited so you will be able to stand out in the crowd by adding our qualifications to your CV and Resume. Email Marketing Introduction to Email Marketing 00:30:00 Using Email Marketing Software 00:30:00 Building Email Lists by Quantity 00:30:00 Building Email Lists by Quality 00:30:00 Crafting an Email 01:00:00 Analyzing and Tracking Your Email Marketing Strategy 00:30:00 Email Marketing Secrets Introduction 01:00:00 4 Crucial Things You Need To Do To Build your List 01:00:00 Ways To Get Your Opt In Subscribers To Trust You Quickly 01:00:00 Tips To Build A List Of Eager Subscribers 01:00:00 Easy Ways To Grab Your Reader's Attention In Your Subject 01:00:00 Effective Techniques To Get Your Subscribers Begging For More 01:00:00 Can You Really Use Articles To Build Your List? 01:00:00 Things To Consider When Publishing A Newsletter 01:00:00 The 3 Things To Avoid When Emailing Your List 01:00:00 Mock Exam Mock Exam- Certified Diploma in Email Marketing 00:20:00 Final Exam Final Exam- Certified Diploma in Email Marketing 00:20:00

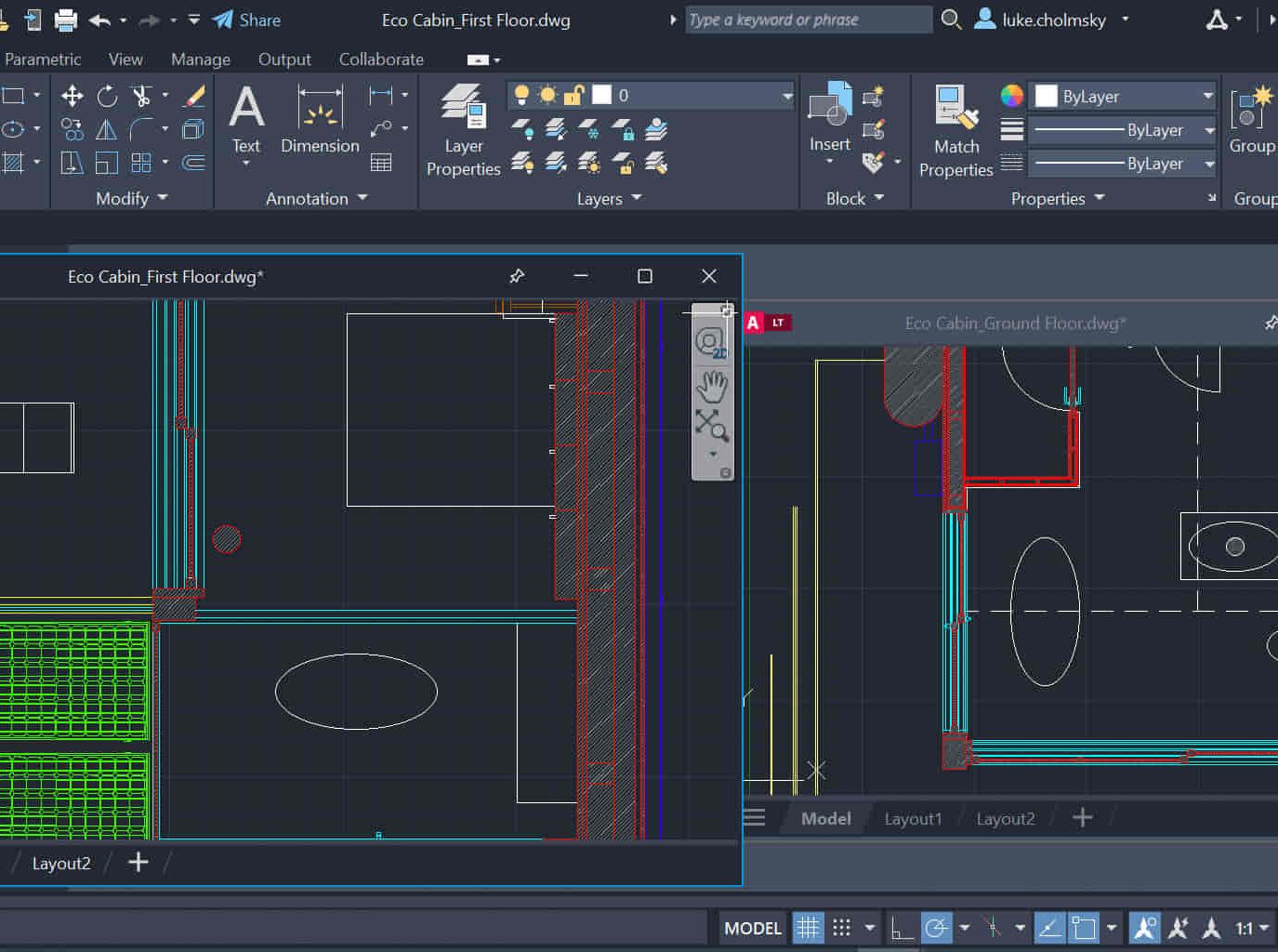
AutoCAD Night Training Course
By ATL Autocad Training London
Why AutoCAD Night Training Course? This Autodesk AutoCAD 2D Evening Course, 10 hours, is perfect for beginners aiming to create 2D plans, elevations, sections. It covers all tools in AutoCAD 2D, making it valuable for both newcomers and those aspiring to enhance their skills. Click here for more info: Website When: Personalized 1-on-1 sessions. Available from Mon to Sat 9 am to 7 pm. Book over the phone, call 02077202581 Duration: 10 hours (Split 10 hrs over as many as days you want) Method: In-person or live online training Course Content: Foundational Shape Construction Manipulating Lines, Arcs, and Polylines Optimizing Object Alignment with Grip Tools Data Management and Backup Protocols File Format Exploration and Understanding Disaster Recovery Strategies Advanced Object Creation Techniques Precision Measurement Unit Handling Dynamic Input Methods Utilizing Inquiry Commands and Measurement Tools Effective Object Visualization and Navigation Zoom, Pan, and Object Manipulation Swift Object Management Strategies Object Transformation and Alteration Techniques Functions for Trimming, Extending, and Offsetting Objects Creating Various Geometric Shapes Object Editing, Joining, and Filleting Stretching and Organizing Objects Layer Management and Customization Configuring Object Properties and Linetypes Designing Layouts and Efficient Page Configurations Scaling Drawing Views and Adding Annotations Text Creation, Styling, and Editing Dimensioning Principles and Customization Implementing Multileaders for Annotations Object Hatching and Editing Techniques Managing Reusable Content: Blocks and Symbols Utilizing Tool Palettes and Working with Groups Understanding Model Space and Paper Space Creating Layouts and Viewports Scaling Viewports and Plotting/PDF Output Managing Multiple Sheet Drawings Optimizing Plotstyles for Printing Creating Custom Drawing Templates To download AutoCAD, visit Autodesk's official website. Advantages: AutoCAD stands as the industry-leading computer-aided design (CAD) software, widely adopted for creating architectural, engineering, and construction drawings. Acquire essential skills applicable across a diverse spectrum of industries. Assessment: Evaluation will occur informally during classes, which comprehensively cover specific topics, complemented by practical drawing exercises to reinforce skills and knowledge. Additionally, we offer longer, independent drawing tasks that encompass multiple acquired skills, evaluated against professional benchmarks. Requirements: Prospective participants should possess basic computer literacy and engagement in professions where CAD is utilized. English Proficiency: Applicants are expected to demonstrate proficiency in both written and spoken English. Why Opt for This Course? Our AutoCAD course is your gateway to mastering the essential skills for creating top-notch technical drawings. Designed with beginners in mind, this course is perfect for individuals who have little to no prior experience with AutoCAD. If your work or studies involve CAD drawings, gaining a solid grasp of the program is crucial for confidence and proficiency. Upon enrollment, students gain access to a free 30 days trial. While classes are conducted using AutoCAD on PC, it's worth noting that the course is compatible with AutoCAD on Mac, albeit with slight interface variations. Who Should Attend? This course caters to those eager to acquire the skills necessary for creating and interpreting drawings produced in AutoCAD. Our diverse system hails from various industries, including engineering, architecture, landscape architecture, construction, electronics, and product design. Why Opt for CAD Training? Practical Learning Experience: Immerse yourself in hands-on training. Personalized One-to-One AutoCAD Classes: Benefit from individualized attention. Expert and Knowledgeable Instructors: Learn from skilled and experienced teachers. Online Training Recordings: Access recorded AutoCAD training sessions online. Best Price Guarantee: Enjoy competitive pricing with a satisfaction guarantee. Pre and Post-Training Support: Receive lifetime free support before and after completing your training. Flexible Schedule: Choose your class timings and dates-weekdays, weekends, or evenings. Tailored Course Content: Customize the AutoCAD course to align with your specific needs. Access Anywhere: Access AutoCAD training and support from any location.
Platelet-rich Plasma (PRP) treatments Nationally Recognised Qualification No previous experience or qualifications needed Open College Network Accreditation Level 4 (as required for minimally invasive procedures) Covers standards set by HEE Employed (salon) or Self-Employed opportunities Basic understanding of English language required OPEN TO ALL APPLICANTS

Specializing in sports performance training with NASM will help enhance not only your clients’ performance but also your earning potential. With NASM’s Performance Enhancement Specialization (NASM-PES), you’ll learn how to provide cutting-edge strength and conditioning training for your clients. You’ll gain the advanced knowledge, insight, and skills needed to help clients of all levels reach their peak performance potential. The 16 modules in this program will also help you meet the demands necessary of a Sports Performance Professional at all levels of sport by providing you the tools you need to improve your clients’ speed, agility, quickness, lifting, and more.

SharePoint - Advanced Site Owner (Modern Experience)
By Nexus Human
Duration 1 Days 6 CPD hours This course is intended for This course is designed for students who already have experience creating Modern SharePoint sites and populating them with content, who want to learn advanced features to extend SharePoint's capabilities, make information easier to find and manage, use SharePoint features to improve governance and compliance, and improve the security of information and services within the SharePoint environment. Overview Create a custom site template to reduce the time spent creating similarly configured SharePoint sites. Configure managed metadata, including custom term sets, content types, and metadata-based navigation. Control access through permissions. Improve overall security of sites, lists, libraries, folders, list items, and documents. Microsoft© SharePoint©, in conjunction with the Microsoft 365? productivity and office automation suite, provides tools to create and manage a corporate intranet, facilitate content sharing and collaboration, and enable users to create, access, store, and track documents and data in a central location. Users who already have experience as SharePoint site members and owners may be ready to move on to more advanced site-building tasks such as using custom site templates, custom themes, applying advanced permissions settings, improving security, and preparing sites to support governance and compliance. Advanced site builders may be ready to undertake more advanced site management tasks, working in conjunction with their SharePoint Administrator to create and use custom site templates, term sets and metadata, manage information governance and compliance, and get deeper into SharePoint security configuration. This course focuses on these advanced site-building and administration tasks. Prerequisites To ensure your success in this course, you should have SharePoint site user skills such as the ability to view and enter data in SharePoint lists and libraries, and to navigate a typical SharePoint site. You should also have intermediate site builder skills such as the ability to create a SharePoint site, apply a site template, populate sites with pages, create lists and libraries, and connect a site to a hub site. NOTE: This course was developed using Microsoft 365 Business Standard edition. If you opt to use one of the Enterprise editions, be sure to key the course activities before you deliver the class so you will be able to anticipate any differences that students might see with the edition you use. Lesson 1: Creating Custom Site Templates Topic A: Prepare a Site Script Topic B: Generate and Use a Custom Site Template Lesson 2: Managing Content Services Topic A: Plan and Configure Managed Metadata Topic B: Create and Manage Content Types Topic C: Use Managed Metadata for Navigation and Filtering Lesson 3: Controlling Access Through Permissions Topic A: Assign Permissions Topic B: Manage Permissions Inheritance Lesson 4: Improving Security Topic A: Manage Access at the Site Level Topic B: Manage Access at the Tenant Level

The VTCT Level 3 Certificate in Assessing Vocational Achievement (Hairdressing)
4.8(16)By Kleek Academy
Obtain The Assessor's Qualification through our comprehensive teaching and assessing courses at Kleek Training. Develop the skills and knowledge needed to effectively assess learners. Enquire today!

Aweber Training Course
By iStudy UK
Learn to communicate with your audience regularly with appropriate email marketing. Enrol the Aweber Training Course and explore the strategies of finding massive subscribers and sales. Aweber is an email marketing and autoresponder tool. Email marketing is one of the best ways of gaining profit. The course shows you some of the surefire methods of email marketing with Aweber. The techniques of using the service and the ways of setting up an auto-responder will be discussed in the course. The course shows you the ways of making money through email. You will learn to create a double and a single opt-in subscriber process. Throughout the course, you will also know how to develop an opt-in form for your website. Additionally, the course shows you the systems of importing an existing list from an offline source. business cards, LinkedIn contacts, etc. Next, the course teaches you how to add people to your email list and how to send a broadcast email. Shortly, the course will focus on the various potential ways of using email marketing for gaining profit by using Aweber. What you'll learn You will know how to use Aweber You will know how to send a broadcast email You will know how to set up an autoresponder You will know how to add people to your email list You will know how to make money from your email list You will know how to communicate with your audience and increase conversions You will know how to 2X your business with the power of the SOAP + SEINFELD Email Sequence Requirements You should have a subscription for Aweber or will get one Introduction 1. Promo FREE 00:01:00 2. Introduction 00:01:00 4. The Blueprint Overview 00:11:00 5. Signup for Aweber 00:01:00 6. Sign Into Aweber 00:01:00 7. Create a New Email List 00:06:00 8. Create Your First Signup Form 00:04:00 9. Customizing Your Signup Form 00:03:00 10. Signup Form Widget & Footer 00:01:00 11. ClickFunnels Autoresponder Integration 00:01:00 12. Importing Your List 00:05:00 13. Sending Broadcast Messages & Autoresponders 00:13:00 14. Segmentation & Why We Do It 00:10:00 15. List Options 00:05:00 16. Reports 00:02:00 17. Apps 00:02:00 18. Getting Help in Aweber 00:01:00 19. Copy My ClickFunnels Sales Funnel 00:03:00 Email Marketing 20. Why Email Everyday 00:03:00 21. The Value Ladder Explained 00:12:00 22. Soap Opera Sequence 00:13:00 23. Walkthrough of My SOAP Sequence 00:29:00 24. Client SOAP Sequence Example 00:11:00 25. Seinfeld Email Sequence 00:11:00 26. The Attractive Character Overview 00:10:00 27. Attractive Character II 00:18:00 Assessment
The ability to change speed and direction of movement and appropriately react to all given stimuli is often the difference between injury and safety or success. Improving speed, change of direction and reaction time is possible through proper training strategies known as speed, agility and quickness or SAQ training. This comprehensive course provides students with a general understanding of SAQ training concepts and the knowledge to help clients increase performance while decreasing risk of injury through the Optimum Performance Training® (OPT™) Model.


