- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
Cisco Introduction to SD-Access and DNA Center (SDAINT)
By Nexus Human
Duration 2 Days 12 CPD hours This course is intended for The primary audience for this course is as follows:Anyone interested in knowing about DNA Center and SD-AccessPersonnel involved in SD-Access Design and ImplementationNetwork Operations team with SD-Access solutionNetwork admin staff that deal with User AccessChannel Partner SEs and other sales supportNetwork Access Control administrationNetwork AdministratorsNetwork ArchitectsNetwork Engineers Overview Upon completing this course, the learner will be able to meet these overall objectives:Know and understand Cisco?s SD-Access concepts, features, benefits, terminology and the way this approach innovates common administrative tasks on today?s networks.Differentiate and explain each of the building blocks of SD-Access SolutionExplain the concept of ?Fabric? and the different node types that conform it (Fabric Edge Nodes, Control Plane Nodes, Border Nodes)Describe the role of LISP in Control Plane and VXLAN in Data Plane for SD-Access SolutionUnderstand the role of DNA Center as solution orchestrator and Intelligent GUIBe familiar with workflow approach in DNA Center and its 4 Steps: Design, Policy, Provision and Assurance DNA Center and SD-Access offer Cisco?s next-generation programmable digital network to help automate common network access security features and streamline the redundant, complex configuration required to allow different groups of users access to the network infrastructure. This network security training course allows network administrators to quickly allow differentiated access for end users on the network while allowing the network to react automatically to day zero and other types of attacks. Introduction to Cisco?s Software Defined Access (SD-Access) SD-Access Overview SD-Access Benefits SD-Access Key Concepts SD-Access Main Components SD-Access Campus Fabric The concept of Fabric Node types Fabric Edge Nodes Control Plane Nodes Border Nodes LISP as protocol for Control Plane VXLAN as protocol for Data Plane Concept of Virtual Network Fabric-enabled WLAN DNA Center and Workflow for SD-Access Introduction to DNA Center Workflow for SD-Access in DNA Center Integration with Cisco ISE for Policy Enforcement Integration with Cisco NDP for Analytics and Assurance Relationship with APIC-EM controller DNA Center Workflow First Step - Design Creating Enterprise and Sites Hierarchy Discuss and Demonstrate General Network Settings Loading maps into the GUI IP Address Administration Administering Software Images Network Device Profiles DNA Center Workflow Second Step - Policy 2-level Hierarchy Policy Types ISE Integration with DNA Center Cross Domain Policies DNA Center Workflow Third Step - Provision Devices Onboarding Fabric Domains Adding Nodes DNA Center Workflow Fourth Step ? Assurance Introduction to Analytics NDP Fundamentals Overview of DNA Assurance Components of DNA Assurance DNA Center Assurance Dashboard Implementing WLAN in SD-Access Solution WLAN Integration Strategies in SD-Access Fabric SD-Access Wireless Architecture Sample Design for SD-Access Wireless Campus Fabric External Connectivity for SD-Access Enterprise Sample Topology for SD-Access Role of Border Nodes Types of Border Nodes Single Border vs. Multiple Border Designs Collocated Border and Control Plane Nodes Distributed (separated) Border and Control Plane Nodes

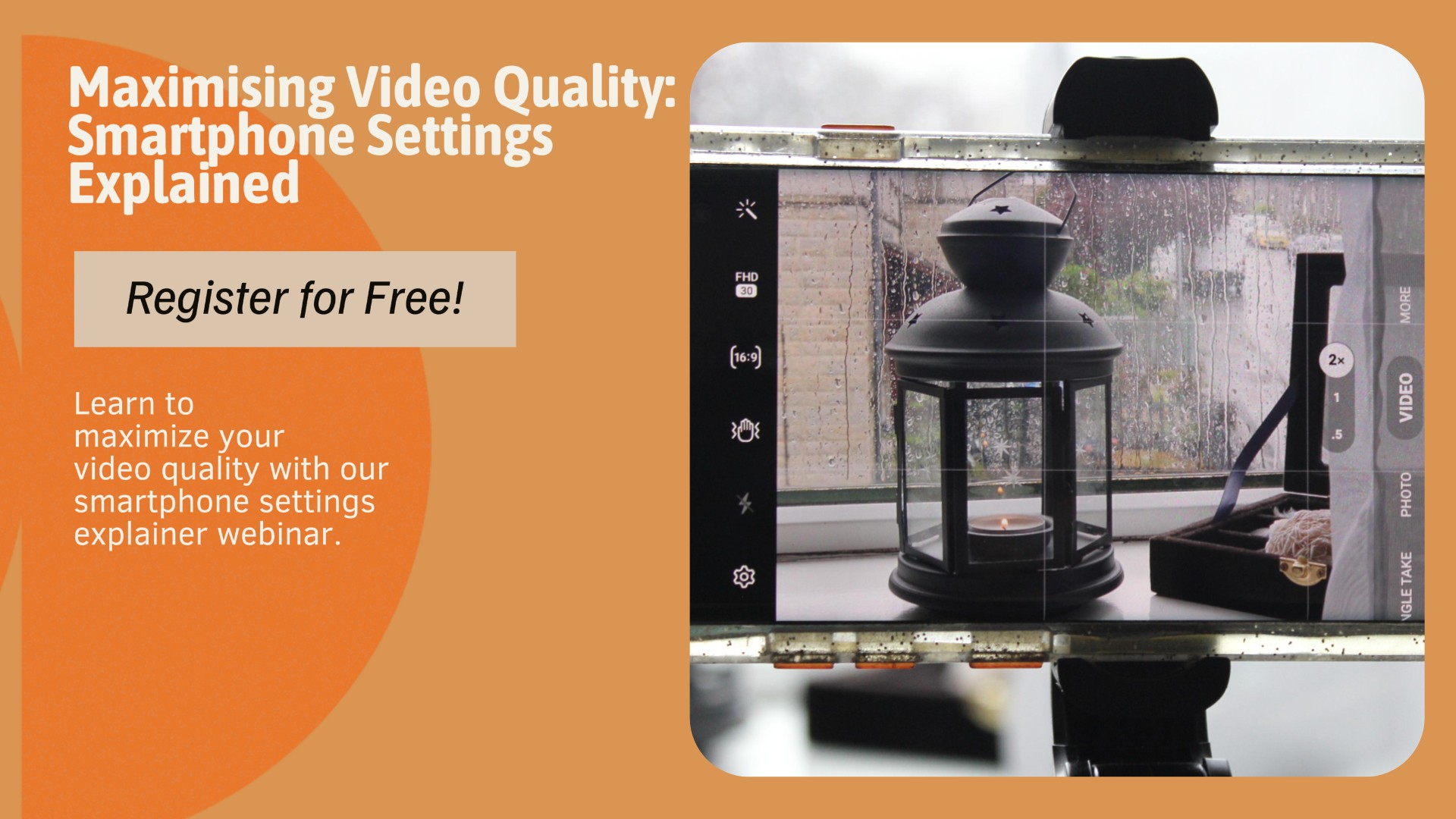
Maximise Video Quality: Smartphone Settings Explained (Free Webinar)
5.0(1)By Clockwork Eye Video Training
Join our free webinar to learn how to optimize the generic settings on any smartphone for creating high-quality videos. Perfect for small business owners and entrepreneurs looking to boost their online presence with professional video content.
VMware vRealize Automation SaltStack SecOps: Deploy and Manage [V8.6]
By Nexus Human
Duration 2 Days 12 CPD hours This course is intended for Security administrators who are responsible for using SaltStack SecOps to manage the security operations in their enterprise Overview By the end of the course, you should be able to meet the following objectives: Describe the architecture of SaltStack Config and SaltStack SecOps Integrate SaltStack Config with directory services. Configure roles and permissions for users and groups to manage and use SaltStack SecOps Use targeting to ensure that the jobs run on the correct minion systems Use remote execution modules to install the packages, transfer files, manage services, and manage users on minion systems Manage configuration control on the minion systems with states, pillars, requisites, and declarations Use Jinja and YAML code to manage the minion systems with the state files Enforce the desired state across minion systems automatically Use SaltStack SecOps to update the compliance and vulnerability content libraries Use SaltStack SecOps to enforce compliance and remediation on the infrastructure with industry standards Use SaltStack SecOps to provide automated vulnerability scanning and remediation on your infrastructure This two-day, hands-on training course provides you with the advanced knowledge, skills, and tools to achieve competency in using VMware vRealize© Automation SaltStack© SecOps. SaltStack SecOps allows you to scan your system for compliance against security benchmarks, detect system vulnerabilities, and remediate your results. This course enables you to create the SaltStack SecOps custom compliance libraries and use SaltStack SecOps. In addition, this course provides you with the fundamentals of how to use VMware vRealize© Automation SaltStack© Config to install software and manage system configurations. Course Introduction Introductions and course logistics Course objectives SaltStack Config Architecture Identify the SaltStack Config deployment types Identify the components of SaltStack Config Describe the role of each SaltStack Config component SaltStack Config Security Describe local user authentication Describe LDAP and Active Directory authentication Describe the roles and permissions in vRealize Automation for SaltStack Config Describe the roles and permissions in SaltStack Config Describe the SecOps permissions in SaltStack Config Describe the advanced permissions available in SaltStack Config Targeting Minions Describe targeting and its importance Target minions by minion ID Target minions by glob Target minions by regular expressions Target minions by lists Target minions by compound matching Target minions by complex logical matching Remote Execution and Job Management Describe remote execution and its importance Describe functions and arguments Create and manage jobs Use the Activities dashboard Configuration Control Through States, Pillars, Requisites, and Declarations Define the SaltStack states Describe file management in SaltStack Config Create the SaltStack state files Identify the components of a SaltStack state Describe pillar data and the uses of pillar data Configure pillar data on the SaltStack Config master server Use pillar data in variables in the state files Describe the difference between IDs and names in the state files Use the correct execution order Use requisites in the state files Using Jinja and YAML Describe the SaltStack Config renderer system Use YAML in the state files Use Jinja in the state files Use Jinja conditionals, lists, and loops Using SaltStack SecOps Comply Describe the SaltStack SecOps Comply architecture Describe CIS and DISA STIG benchmarks Describe the SaltStack SecOps Comply security library Describe the remediation differences between SaltStack SecOps and VMware Carbon Black© Create and manage the policies Create and manage the custom checks Run assessments on the minion systems Use SaltStack SecOps to remediate the noncompliant systems Manage the SaltStack SecOps Comply configuration options Manage the benchmark content ingestion Using SaltStack SecOps Protect Describe Common Vulnerabilities and Exposures (CVEs) Use the Protect dashboard Create and manage the policies Update the vulnerability library Run the vulnerability scans Remediate the vulnerabilities Manage the vulnerability exemptions
![VMware vRealize Automation SaltStack SecOps: Deploy and Manage [V8.6]](https://cademy-images-io.b-cdn.net/9dd9d42b-e7b9-4598-8d01-a30d0144ae51/4c81f130-71bf-4635-b7c6-375aff235529/original.png?width=3840)
The Art of Self-Introduction: Structuring Your Speech for Maximum Impact
By Sophia Baker
Introduction Making a great first impression can be a game-changer, and your self-introduction plays a crucial role in this. It’s not just about stating who you are but presenting yourself in a way that captures attention and fosters connections. Whether you're stepping into a job interview or mingling at a party, a well-structured self-introduction can make all the difference. Understanding Your Audience Identifying Your Audience Before you craft your introduction, it's essential to understand who you're speaking to. Are you addressing colleagues in a corporate setting, potential clients, or new acquaintances at a social event? Knowing your audience helps tailor your message to their interests and expectations. Tailoring Your Message to the Audience Different audiences require different approaches. For a professional audience, focus on your career achievements and skills. For a social setting, you might emphasize hobbies or personal interests. Adapting your message ensures relevance and keeps your audience engaged. Crafting Your Introduction Key Elements of a Self-Introduction A solid introduction typically includes: Name and Current Role: Start with who you are and what you do. This sets the context for your audience. Relevant Background Information: Share a bit about your background that adds value to the conversation. Unique Selling Points: Highlight what makes you unique or what you bring to the table. Structuring Your Introduction for Clarity Organize your introduction in a logical flow. Start with your name, move on to your current role, share relevant background information, and end with your unique selling points. This structure ensures your introduction is clear and impactful. The Power of a Strong Opening Creating a Memorable Hook Capture your audience's attention right from the start. Use a compelling hook, such as an intriguing fact about yourself, a brief anecdote, or a relevant quote. A strong opening piques curiosity and draws your audience in. Using Anecdotes or Quotes Incorporating a brief story or a quote can make your introduction more engaging and memorable. Choose anecdotes that reflect your personality or achievements, and quotes that resonate with your message. Building Your Narrative Crafting a Compelling Story People connect with stories. Weave a narrative around your experiences, challenges, and successes. This approach makes your introduction more relatable and interesting. Highlighting Achievements and Experiences Focus on significant achievements and experiences that align with the context of your introduction. This helps establish credibility and shows what you bring to the table. Keeping It Concise Importance of Brevity While it’s tempting to share every detail, brevity is key. Aim for a concise introduction that covers the essentials without overwhelming your audience. A brief, well-crafted introduction is often more effective than a lengthy one. Techniques for Staying on Point To stay on point, practice your introduction and focus on the most relevant information. Avoid tangents and ensure every part of your introduction adds value. Engaging with Your Audience Asking Questions Engage your audience by asking questions or inviting them to share their thoughts. This interaction not only makes your introduction more engaging but also fosters a two-way conversation. Inviting Interaction Encourage dialogue by showing interest in your audience’s responses or reactions. This approach helps build connections and makes your introduction more dynamic. Non-Verbal Communication Body Language Tips Non-verbal cues play a significant role in communication. Maintain good posture, use open gestures, and avoid crossing your arms. Your body language should complement your verbal introduction. The Role of Eye Contact Maintaining eye contact shows confidence and helps build trust with your audience. It demonstrates engagement and sincerity in your introduction. Tailoring Your Introduction for Different Settings Professional Settings In professional settings, focus on your career achievements, skills, and professional interests. Be formal and concise, and ensure your introduction aligns with the context of the meeting or event. Social Gatherings For social gatherings, highlight personal interests, hobbies, or interesting facts about yourself. This helps create a friendly atmosphere and fosters personal connections. Virtual Introductions In virtual settings, ensure your introduction is clear and engaging despite the lack of physical presence. Use visual aids if possible, and maintain a positive and professional tone. Practicing Your Delivery Rehearsing Your Introduction Practice your introduction to build confidence and ensure smooth delivery. Rehearse in front of a mirror or with friends to refine your approach and timing. Adapting to Feedback Be open to feedback and adjust your introduction based on what resonates best with your audience. Continuous improvement helps keep your introduction fresh and effective. Common Mistakes to Avoid Overloading with Information Avoid overwhelming your audience with too much information. Focus on key points and keep your introduction relevant to the context. Being Too Vague or Generic Generic introductions can be forgettable. Be specific and highlight unique aspects of your background or achievements to stand out. Using Visual Aids Enhancing Your Introduction with Slides or Props In some settings, visual aids can enhance your introduction. Use slides or props to highlight key points or add visual interest. Ensure they support your message without overshadowing it. When and How to Use Visual Aids Effectively Only use visual aids when they add value to your introduction. Keep them simple and relevant, and practice using them smoothly in your delivery. The Role of Confidence Building Self-Confidence Confidence can be built through practice and preparation. Know your material, rehearse regularly, and adopt a positive mindset to boost your confidence. Projecting Confidence Through Speech Your tone, pace, and clarity of speech reflect your confidence. Speak clearly, at a steady pace, and with enthusiasm to convey confidence effectively. Feedback and Improvement Seeking Constructive Feedback Request feedback from trusted friends or colleagues to gain insights into how your introduction is received. Use this feedback to make improvements. Continuously Refining Your Introduction Refine your introduction based on feedback and personal experiences. Regular updates ensure your introduction remains relevant and impactful. Conclusion Crafting a powerful self-introduction is both an art and a skill. By understanding your audience, structuring your message clearly, and practicing your delivery, you can make a memorable first impression. Remember to tailor your introduction for different settings, engage with your audience, and continually refine your approach. With these strategies, you'll be well-equipped to introduce yourself effectively in any situation. FAQs 1. What should be included in a professional self-introduction? Include your name, current role, key achievements, and relevant skills. Tailor it to the context of the professional setting. 2. How long should my self-introduction be? Aim for 30-60 seconds. It should be concise yet comprehensive enough to convey your key points. 3. How can I make my introduction more engaging? Use a memorable hook, incorporate personal anecdotes, and engage your audience with questions or interactive elements. 4. What are common mistakes to avoid in a self-introduction? Avoid being too vague, overloading with information, or appearing uninterested. Focus on relevance and clarity. 5. How can I improve my self-introduction over time? Seek feedback, practice regularly, and refine your introduction based on experiences and audience reactions.
Mastering Harvard Referencing: A Comprehensive Guide for UK Students
By Sophia Baker
Introduction When it comes to academic writing, referencing is crucial. It’s not just about giving credit where it’s due, but also about enhancing the credibility of your work. Among the various referencing styles, Harvard referencing for word essays is one of the most widely used, especially in the UK. But why is it so popular, and how can you master it? Let’s dive in! Understanding Harvard Referencing Harvard referencing is a system of citation that allows you to acknowledge the sources you’ve used in your academic writing. It’s an author-date system, which means you include the author’s surname and the year of publication within the text, and provide full details in a reference list at the end. Despite its name, Harvard references didn’t originate from Harvard University. The style was first used by a zoologist named Edward Laurens Mark in a paper published in 1881. Over time, it has evolved and become one of the most recognized citation styles worldwide. Harvard referencing consists of two main components: in-text citations and a reference list. In-text citations are brief and are placed within the body of your text, while the reference list provides full details of all the sources you’ve cited. The Basics of Harvard Referencing In-text citations in Harvard referencing include the author’s surname and the year of publication. If you’re quoting directly, you should also include the page number. For example: (Smith, 2020, p. 23). The reference list is where you provide full details of each source cited in your work. Each entry should include the author’s name, year of publication, title of the work, and other relevant information, depending on the type of source. A reference list includes only the sources you’ve directly cited in your text, while a bibliography may include all sources you’ve consulted, whether or not you’ve cited them. How to Cite Different Types of Sources When citing a book, you should include the author’s name, year of publication, title (in italics), edition (if applicable), place of publication, and publisher. For example: Smith, J. (2020). The Art of Referencing (2nd ed.). London: Academic Press. Journal articles should include the author’s name, year of publication, title of the article, title of the journal (in italics), volume number, issue number, and page numbers. For example: Brown, A. (2019). ‘Understanding Harvard Referencing’, Journal of Academic Writing, 12(3), pp. 45-67. For websites, include the author (or organization), year of publication (or last update), title of the webpage (in italics), and the URL. For example: University of Oxford. (2021). Harvard Referencing Guide. Available at: https://www.ox.ac.uk/harvard (Accessed: 10 September 2024). When citing a newspaper article, include the author’s name, year of publication, title of the article, title of the newspaper (in italics), date, and page number. For example: Doe, J. (2022). ‘The Future of Academic Writing’, The Times, 5 May, p. 12. For government documents, include the name of the government department, year of publication, title of the document (in italics), place of publication, and publisher. For example: UK Department for Education. (2020). Education Policy Report. London: HMSO. Cite conference papers by including the author’s name, year of publication, title of the paper, title of the conference (in italics), location, and date of the conference. For example: Jones, M. (2023). ‘Innovations in Academic Writing’, International Writing Conference, Manchester, 10-12 April. Harvard Referencing for Electronic Sources When citing e-books, the format is similar to print books, but you should include the format (e.g., Kindle) or the platform where it’s available. For example: Adams, R. (2018). Digital Referencing (Kindle ed.). Available at: Amazon.co.uk. For online journals, follow the same format as print journals, but include the DOI or the URL where the article can be accessed. For example: Taylor, S. (2021). ‘Harvard Referencing in the Digital Age’, Journal of Modern Research, 15(4), pp. 33-50. DOI: 10.1234/jmr.2021.0987. The format for websites remains the same as mentioned earlier, with the inclusion of the URL and the access date. For social media, include the author (or username), year, content of the post (in italics), platform, and the date of the post. For example: @AcademicWriterUK. (2023). The key to successful referencing is consistency. Twitter, 15 March. Advanced Harvard Referencing Techniques When you can’t access the original source and need to cite a secondary source, mention both the original and secondary source. For example: (Smith, 1989, cited in Brown, 2019). For works with multiple authors, list up to three authors in the in-text citation. For more than three, use “et al.” after the first author’s name. For example: (Jones, Smith, and Brown, 2020) or (Jones et al., 2020). If you’re citing different editions of a book, mention the edition in your reference. For example: Brown, A. (2018). Theories of Learning (3rd ed.). Oxford: Oxford University Press. If some information is missing, like the author or date, use “Anon.” for anonymous authors and “n.d.” for no date. Common Harvard Referencing Mistakes and How to Avoid Them Incorrect formatting can easily occur if you’re not careful. Make sure to follow the correct structure for each type of source, as this can significantly impact your grade. Leaving out essential details like the author’s name or the year of publication is a common mistake. Always double-check your references before submitting your work. Punctuation is crucial in Harvard referencing. Misplacing a comma or period can change the meaning of your citation. Pay attention to the details! Tools and Resources for Harvard Referencing Online citation generators can save you time, but be cautious—always double-check the generated citations for accuracy. Tools like EndNote or Zotero can help you manage your references and ensure consistency throughout your work. Many universities provide specific guidelines for Harvard referencing. Always refer to your institution’s guidelines to ensure you’re following the correct format. The Importance of Consistency in Harvard Referencing Consistency is key in Harvard referencing. Uniformity in your citations not only makes your work look professional but also enhances readability. Inconsistent referencing can confuse readers and may lead to a lower grade. Make sure your citations follow a consistent style throughout your work. Tips for Mastering Harvard Referencing Always double-check your references before submission. Small errors can add up and impact your overall grade. Keep a record of all the sources you consult. This will make it easier to create your reference list and avoid missing any citations. Using a Harvard style guide can help ensure that you’re following the correct format. It’s a handy tool for quick reference. Conclusion Mastering Harvard referencing may seem daunting at first, but with practice and attention to detail, it becomes second nature. Remember, proper referencing not only supports your arguments but also adds credibility to your work. So, take your time, be consistent, and use the resources available to you.

MyAssignment Help.Expert
By MyAssignmenthelp.Expert
Yes

Exam Readiness Intensive Workshop: AWS Certified Solutions Architect - Associate
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for This course is intended for: Solutions architects and cloud architects seeking their AWS Certified Solutions Architect - Associate certification Customers and APN Partners who have 6 to 12 months of experience with AWS including a strong architecture background and experience Individuals who prefer an instructor led course for training and exam readiness Individuals who have not taken the Architecting on AWS course in the last ~6 months Overview In this course, you will learn to: Make architectural decisions based on AWS architectural principles and best practices Leverage AWS services to make your infrastructure scalable, reliable, and highly available Leverage AWS Managed Services to enable greater flexibility and resiliency in an infrastructure Make an AWS-based infrastructure more efficient to increase performance and reduce costs Use the Well-Architected Framework to improve architectures with AWS solutions Navigate the logistics of the examination process, exam structure, and question types Identify how questions relate to AWS architectural concepts Interpret the concepts being tested by an exam question This five-day, instructor-led course helps busy architects get away from the day-to-day to get focused and ready for their AWS Certified Solutions Architect ? Associate exam. Attendees learn the fundamentals of building IT infrastructure on AWS, so they can build scalable and resilient solutions in the cloud, by spending the first 3 days on the Architecting on AWS course. They?ll start getting in the exam readiness mindset with bonus end of module quizzes. Next, they?ll learn strategies to answer exam questions and avoid common mistakes with the Exam Readiness: AWS Certified Solutions Architect ? Associate half-day course. The course broadens attendees? knowledge of AWS services with deep dives into Amazon Redshift, Amazon Kinesis, and AWS Key Management Service, and then concludes with two quizzes and an instructor guided review of the AWS Certified Solutions Architect ? Associate practice exam. Architecting on AWS Module 1: Introduction Module 2: The Simplest Architectures Hands-On Lab 1: Hosting a Static Website Module 3: Adding a Compute Layer Module 4: Adding a Database Layer Hands-On Lab 2: Deploying a Web Application on AWS Module 5: Networking in AWS Part 1 Hands-On Lab 3: Creating a Virtual Private Cloud Architecting on AWS (continued) Module 6: Networking in AWS Part 2 Module 7: AWS Identity and Access Management (IAM) Module 8: Elasticity, High Availability, and Monitoring Hands-On Lab 4: Creating a Highly Available Environment Module 9: Automation Hands-On Lab 5: Automating Infrastructure Deployment with AWS CloudFormation Module 10: Caching Architecting on AWS (continued) Module 11: Building Decoupled Architectures Module 12: Microservices and Serverless Architectures Hands-On Lab 6: Implementing a Serverless Architecture with AWS Managed Services Module 13: RTP/RPO and Backup Recovery Setup Module 14: Optimizations and Review Exam Readiness: AWS Certified Solutions Architect -- Associate Module 0: The Exam Module 1: Design Resilient Architectures Module 2: Design Performant Architectures Module 3: Specify Secure Applications and Architectures Module 4: Design Cost-Optimized Architectures Module 5: Define Operationally Excellent Architectures Exam Readiness Additional deep dive of AWS services Quiz #1 Practice exam: AWS Certified Solutions Architect ? Associate Quiz #2 Wrap-up

Cisco Designing Cisco Data Center Infrastructure v7.0 (DCID)
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for IT professionals with five to eight years of experience in these roles: Data center engineers Network designers Network administrators Network engineers Systems engineers System administrator Consulting systems engineers Technical solutions architects Server administrators Network managers Cisco integrators or partners Overview After taking this course, you should be able to: Describe the Layer 2 and Layer 3 forwarding options and protocols used in a data center Describe the rack design options, traffic patterns, and data center switching layer access, aggregation, and core Describe the Cisco Overlay Transport Virtualization (OTV) technology that is used to interconnect data centers Describe Locator/ID separation protocol Design a solution that uses Virtual Extensible LAN (VXLAN) for traffic forwarding Describe hardware redundancy options; how to virtualize the network, compute, and storage functions; and virtual networking in the data center Describe solutions that use fabric extenders and compare Cisco Adapter Fabric Extender (FEX) with single root input/output virtualization (SR-IOV) Describe security threats and solutions in the data center Describe advanced data center security technologies and best practices Describe device management and orchestration in the data center Describe the storage options for compute function and different Redundant Array of Independent Disks (RAID) levels from a high-availability and performance perspective Describe Fibre Channel concepts, topologies, architecture, and industry terms Describe Fibre Channel over Ethernet (FCoE) Describe security options in the storage network Describe management and automation options for storage networking infrastructure Describe Cisco UCS servers and use cases for various Cisco UCS platforms Explain the connectivity options for fabric interconnects for southbound and northbound connections Describe the hyperconverged solution and integrated systems Describe the systemwide parameters for setting up a Cisco UCS domain Describe role-based access control (RBAC) and integration with directory servers to control access rights on Cisco UCS Manager Describe the pools that may be used in service profiles or service profile templates on Cisco UCS Manager Describe the different policies in the service profile Describe the Ethernet and Fibre Channel interface policies and additional network technologies Describe the advantages of templates and the difference between initial and updated templates Describe data center automation tools The Designing Cisco Data Center Infrastructure (DCID) v7.0 course helps you master design and deployment options focused on Cisco© data center solutions and technologies across network, compute, virtualization, storage area networks, automation, and security. You will learn design practices for the Cisco Unified Computing System? (Cisco UCS©) solution based on Cisco UCS B-Series and C-Series servers, Cisco UCS Manager, and Cisco Unified Fabric. You will also gain design experience with network management technologies including Cisco UCS Manager, Cisco Data Center Network Manager (DCNM), and Cisco UCS Director. This course helps you prepare to take the exam, Designing Cisco Data Center Infrastructure (300-610 DCID) Describing High Availability on Layer 2 Overview of Layer 2 High-Availability Mechanisms Virtual Port Channels Cisco Fabric Path Virtual Port Channel+ Designing Layer 3 Connectivity First Hop Redundancy Protocols Improve Routing Protocol Performance and Security Enhance Layer 3 Scalability and Robustness Designing Data Center Topologies Data Center Traffic Flows Cabling Challenges Access Layer Aggregation Layer Core Layer Spine-and-Leaf Topology Redundancy Options Designing Data Center Interconnects with Cisco OTV Cisco OTV Overview Cisco OTV Control and Data Planes Failure Isolation Cisco OTV Features Optimize Cisco OTV Evaluate Cisco OTV Describing Locator/ID Separation Protocol Locator/ID Separation Protocol Location Identifier Separation Protocol (LISP) Virtual Machine (VM) Mobility LISP Extended Subnet Mode (ESM) Multihop Mobility LISP VPN Virtualization Describing VXLAN Overlay Networks Describe VXLAN Benefits over VLAN Layer 2 and Layer 3 VXLAN Overlay Multiprotocol Border Gateway Protocol (MP-BGP) Ethernet VPN (EVPN) Control Plane Overview VXLAN Data Plane Describing Hardware and Device Virtualization Hardware-Based High Availability Device Virtualization Cisco UCS Hardware Virtualization Server Virtualization SAN Virtualization N-Port ID Virtualization Describing Cisco FEX Options Cisco Adapter FEX Access Layer with Cisco FEX Cisco FEX Topologies Virtualization-Aware Networking Single Root I/O Virtualization Cisco FEX Evaluation Describing Basic Data Center Security Threat Mitigation Attack and Countermeasure Examples Secure the Management Plane Protect the Control Plane RBAC and Authentication, Authorization, and Accounting (AAA) Describing Advanced Data Center Security Cisco TrustSec in Cisco Secure Enclaves Architecture Cisco TrustSec Operation Firewalling Positioning the Firewall Within Data Center Networks Cisco Firepower© Portfolio Firewall Virtualization Design for Threat Mitigation Describing Management and Orchestration Network and License Management Cisco UCS Manager Cisco UCS Director Cisco Intersight Cisco DCNM Overview Describing Storage and RAID Options Position DAS in Storage Technologies Network-Attached Storage Fibre Channel, FCoE, and Internet Small Computer System Interface (iSCSI) Evaluate Storage Technologies Describing Fibre Channel Concepts Fibre Channel Connections, Layers, and Addresses Fibre Channel Communication Virtualization in Fibre Channel SAN Describing Fibre Channel Topologies SAN Parameterization SAN Design Options Choosing a Fibre Channel Design Solution Describing FCoE FCoE Protocol Characteristics FCoE Communication Data Center Bridging FCoE Initialization Protocol FCoE Design Options Describing Storage Security Common SAN Security Features Zones SAN Security Enhancements Cryptography in SAN Describing SAN Management and Orchestration Cisco DCNM for SAN Cisco DCNM Analytics and Streaming Telemetry Cisco UCS Director in the SAN Cisco UCS Director Workflows Describing Cisco UCS Servers and Use Cases Cisco UCS C-Series Servers Fabric Interconnects and Blade Chassis Cisco UCS B-Series Server Adapter Cards Stateless Computing Cisco UCS Mini Describing Fabric Interconnect Connectivity Use of Fabric Interconnect Interfaces VLANs and VSANs in a Cisco UCS Domain Southbound Connections Northbound Connections Disjoint Layer 2 Networks Fabric Interconnect High Availability and Redundancy Describing Hyperconverged and Integrated Systems Hyperconverged and Integrated Systems Overview Cisco HyperFlex? Solution Cisco HyperFlex Scalability and Robustness Cisco HyperFlex Clusters Cluster Capacity and Multiple Clusters on One Cisco UCS Domain External Storage and Graphical Processing Units on Cisco HyperFlex Cisco HyperFlex Positioning Describing Cisco UCS Manager Systemwide Parameters Cisco UCS Setup and Management Cisco UCS Traffic Management Describing Cisco UCS RBAC Roles and Privileges Organizations in Cisco UCS Manager Locales and Effective Rights Authentication, Authorization, and Accounting Two-Factor Authentication Describing Pools for Service Profiles Global and Local Pools Universally Unique Identifier (UUID) Suffix and Media Access Control (MAC) Address Pools World Wide Name (WWN) Pools Server and iSCSI Initiator IP Pools Describing Policies for Service Profiles Global vs. Local Policies Storage and Basic Input/Output System (BIOS) Policies Boot and Scrub Policies Intelligent Platform Management Interface (IPMI) and Maintenance Policies Describing Network-Specific Adapters and Policies LAN Connectivity Controls SAN Connectivity Controls Virtual Access Layer Connectivity Enhancements Describing Templates in Cisco UCS Manager Cisco UCS Templates Service Profile Templates Network Templates Designing Data Center Automation Model-Driven Programmability Cisco NX-API Overview Programmability Using Python Cisco Ansible Module Use the Puppet Agent Additional course details: Nexus Humans Cisco Designing Cisco Data Center Infrastructure v7.0 (DCID) training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Cisco Designing Cisco Data Center Infrastructure v7.0 (DCID) course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.


