- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
The 'MATLAB Simulink for Electrical Power Engineering' course focuses on practical applications and simulations using MATLAB and Simulink for power electronics, solar energy, DC motors, synchronous generators, and induction motors. It aims to provide participants with hands-on experience in electrical power engineering simulations and analysis using MATLAB and Simulink. Learning Outcomes: Understand the applications of matrices in MATLAB and solve non-linear equations using appropriate functions. Simulate power electronics circuits, including rectifiers, choppers, regulators, and inverters, using Simulink in MATLAB. Analyze and simulate solar energy systems and separately excited DC machines in MATLAB. Model and simulate synchronous generators connected to a small power system using MATLAB and Simulink. Simulate induction motors and study their equivalent circuits and torque-speed characteristics using Simulink. Implement PID controllers in Simulink and tune them for effective control in power systems simulations. Acquire hands-on skills in using MATLAB and Simulink to perform various electrical power engineering simulations. Apply MATLAB and Simulink tools to solve practical electrical power engineering problems. Develop an in-depth understanding of power electronics, motor simulations, and solar energy systems. Successfully complete the course with the ability to perform advanced electrical power engineering simulations using MATLAB and Simulink. Why buy this MATLAB Simulink for Electrical Power Engineering? Unlimited access to the course for forever Digital Certificate, Transcript, student ID all included in the price Absolutely no hidden fees Directly receive CPD accredited qualifications after course completion Receive one to one assistance on every weekday from professionals Immediately receive the PDF certificate after passing Receive the original copies of your certificate and transcript on the next working day Easily learn the skills and knowledge from the comfort of your home Certification After studying the course materials of the MATLAB Simulink for Electrical Power Engineering there will be a written assignment test which you can take either during or at the end of the course. After successfully passing the test you will be able to claim the pdf certificate for £5.99. Original Hard Copy certificates need to be ordered at an additional cost of £9.60. Who is this course for? This MATLAB Simulink for Electrical Power Engineering course is ideal for Students Recent graduates Job Seekers Anyone interested in this topic People already working in the relevant fields and want to polish their knowledge and skill. Prerequisites This MATLAB Simulink for Electrical Power Engineering does not require you to have any prior qualifications or experience. You can just enrol and start learning.This MATLAB Simulink for Electrical Power Engineering was made by professionals and it is compatible with all PC's, Mac's, tablets and smartphones. You will be able to access the course from anywhere at any time as long as you have a good enough internet connection. Career path As this course comes with multiple courses included as bonus, you will be able to pursue multiple occupations. This MATLAB Simulink for Electrical Power Engineering is a great way for you to gain multiple skills from the comfort of your home. Course Curriculum Unit 1- Applications on Matrices in MATLAB Module 1- Solving One Non Linear Equation in MATLAB Using Fzero Function 00:15:00 Module 2-Example 1 on Solving Multiple Non Linear Equations in MATLAB Using Fsolve Function 00:15:00 Module 3- Example 2 on Solving Multiple Non Linear Equations in Matlab Using Fsolve 00:13:00 Module 4-Application Multi Level Inverter Part 1 00:25:00 Module 5- Application Multi Level Inverter Part 2 00:05:00 Unit 2-Power Electronics Simulations Using Simulink in MATLAB Module 1-Introduction to MATLAB Simulations Using Simulink 00:04:00 Module 2-Half Wave Uncontrolled Rectifier with R Load Principle of Operation 00:21:00 Module 3- Half Wave Controlled Rectifier R Load Principle of Operation 00:05:00 Module 4-Simulation of Half Wave Controlled Rectifier Using Simulink In Matlab 00:26:00 Module 5- Principle of Operation of Fully Controlled Bridge Rectifier Part 1 00:06:00 Module 6- Principle of Operation of Fully Controlled Bridge Rectifier Part 2 00:06:00 Module 7-Simulation of Bridge Controlled Rectifier 00:16:00 Module 8-AC Chopper with R Load Principle of Operation 00:14:00 Module 9- Simulation of AC Chopper with R and RL Loads in MATLAB 00:11:00 Module 10- Buck Regulator Principle of Operation Part 1 00:16:00 Module 11-Buck Regulator Principle of Operation Part 2 00:17:00 Module 12-Simulation of Buck Regulator in MATLAB 00:14:00 Module 13-Boost Regulator Principle of Operation 00:23:00 Module 14- Simulation of Boost Regulator in MATLAB 00:12:00 Module 15-Buck-Boost Regulator Principle of Operation 00:17:00 Module 16- Simulation of Buck-Boost Regulator 00:09:00 Module 17- Single Phase Half Bridge R-Load 00:15:00 Module 18- Single Phase Half Bridge RL-Load 00:08:00 Module 19-Simulation of Single Phase Half Bridge Inverter 00:18:00 Module 20-Single Phase Bridge Inverter R-Load 00:06:00 Module 21-Single Phase Bridge Inverter RL-Load 00:07:00 Module 22-Simulation of Single Phase Bridge Inverter 00:10:00 Module 23-Three Phase Inverters and Obtaining The Line Voltages 00:15:00 Module 24-Three Phase Inverters and Obtaining The Phase Voltages 00:17:00 Module 25-Simulation of Three Phase Inverter 00:17:00 Module 26-Simulation of Charging and Discharging Capacitor Using Matlab 00:10:00 Unit 3- Solar Energy Simulation Using Simulink in MATLAB Module 1-Separately Excited DC Machine 00:21:00 Module 2-DC Motor Modelling without Load Using Simulink in MATLAB 00:25:00 Module 3-DC Motor Modelling with Load Using Simulink in MALTAB 00:23:00 Module 4-DC Motor Block Simulation Using Power Library in MATLAB 00:16:00 Unit 4- DC Motor Simulation Using Simulink in MATLAB Module 1-Construction and Principle of Operation of Synchronous Generator 00:29:00 Module 2-Equivalent Circuit and Phasor Diagram of Non Salient Synchronous Machine 00:29:00 Module 3-Equivalent Circuit and Phasor Diagram of Salient Synchronous Machine 00:39:00 Module 4-Simulation of Synchronous Machine Connected to Small Power System 00:38:00 Unit 5- Induction Motor Simulation Using Simulink in MATLAB Module 1-Construction and Theory of Operation of Induction Machines 00:27:00 Module 2-Equivalent Circuit and Power Flow in Induction Motor 00:23:00 Module 3-Torque-Speed Characteristics of Induction Motor 00:20:00 Module 4- Simulation of Induction Motor or Asynchronous Motor Using Simulink 00:33:00 Unit 6- Synchronous Generator Simulation in Simulink of MATLAB Module 1- Importing Data from PSCAD Program for Fault Location Detection to MATLAB Program 00:37:00 Unit 7- Power System Simulations Module 1-How to Implement PID Controller in Simulink of MATLAB 00:14:00 Module 2-Tuning a PID Controller In MATLAB Simulink 00:17:00 Assignment Assignment - MATLAB Simulink for Electrical Power Engineering 00:00:00

The Bash Scripting, Linux and Shell Programming Masterclass course is a comprehensive guide to mastering Bash scripting, Linux, and shell programming. It's designed to address a common challenge: the complexity of navigating and controlling Linux-based systems. By simplifying these concepts, the course empowers learners to manage and operate within a Linux environment efficiently. The ability to script and program in the shell opens doors to streamlined processes, automation, and enhanced productivity, benefits that are crucial in today's tech-driven world. Through this masterclass, you will learn the essentials of Linux navigation, file management, and shell programming. Each section is crafted to build your skills progressively, ensuring a deep understanding of each aspect. Whether managing users, handling text files, or exploring advanced Bash features, the course is structured to provide practical, real-world applications. This approach not only enhances your technical skills but also boosts your problem-solving abilities within a Linux context. By the end of this course, you will be proficient in the technical aspects of Linux and Bash scripting and gain a strategic edge in applying these skills. The course is designed for accessibility, allowing learners to study at their own pace, from any device. This flexibility ensures that you can integrate learning seamlessly into your schedule, making it ideal for both beginners and those looking to refresh their skills Learning Outcomes Gain proficiency in basic Bash scripting and shell programming. Learn to navigate efficiently within the Linux environment. Develop skills to access and use help resources in Linux. Acquire expertise in managing files and folders in Linux. Understand how to manipulate and process text files. Learn to manage user accounts and permissions in Linux. Master techniques for terminating programs and safe logouts. Discover efficient shortcuts for faster Linux operations. Deepen understanding of Bash specifics and advanced features. Access a wealth of resources for ongoing Linux learning. Why choose this Bash Scripting, Linux and Shell Programming Masterclass? Unlimited access to the course for a lifetime. Opportunity to earn a certificate accredited by the CPD Quality Standards and CIQ after completing this course. Structured lesson planning in line with industry standards. Immerse yourself in innovative and captivating course materials and activities. Assessments designed to evaluate advanced cognitive abilities and skill proficiency. Flexibility to complete the Course at your own pace, on your own schedule. Receive full tutor support throughout the week, from Monday to Friday, to enhance your learning experience. Unlock career resources for CV improvement, interview readiness, and job success. Who is this Bash Scripting, Linux and Shell Programming Masterclass for? Beginners eager to learn about Linux and shell programming. IT professionals seeking to enhance their scripting skills. System administrators aiming to improve their Linux proficiency. Developers interested in automating tasks with Bash scripting. Anyone curious about mastering Linux-based systems. Career path Linux System Administrator: £25,000 - £50,000. DevOps Engineer: £30,000 - £70,000. IT Support Specialist: £20,000 - £40,000. Software Developer (with Linux skills): £25,000 - £55,000. Network Engineer: £25,000 - £50,000 Prerequisites This Bash Scripting, Linux and Shell Programming Masterclass does not require you to have any prior qualifications or experience. You can just enrol and start learning.This Bash Scripting, Linux and Shell Programming Masterclass was made by professionals and it is compatible with all PC's, Mac's, tablets and smartphones. You will be able to access the course from anywhere at any time as long as you have a good enough internet connection. Certification After studying the course materials, there will be a written assignment test which you can take at the end of the course. After successfully passing the test you will be able to claim the pdf certificate for £4.99 Original Hard Copy certificates need to be ordered at an additional cost of £8. Course Curriculum Section 01: Introduction Introduction 00:02:00 Bash vs Shell vs Command Line vs Terminal 00:06:00 Section 02: Navigation Listing Folder Contents (ls) 00:05:00 Print Current Folder (pwd) 00:01:00 Change Folder (cd) 00:03:00 Using A Stack To Push Folders (pushd/popd) 00:03:00 Check File Type (file) 00:01:00 Find File By Name (locate) & Update Locate Database (updatedb) 00:02:00 Find A Command (which) 00:02:00 Show Command History (history) 00:02:00 Section 03: Getting Help Show Manual Descriptions (whatis) 00:01:00 Search Manual (apropos) 00:02:00 Reference Manuals (man) 00:02:00 Section 04: Working With Files/Folders Creating A Folder (mkdir) 00:02:00 Creating A File (touch) 00:02:00 Copy Files/Folders (cp) 00:02:00 Move & Rename Files/Folders (mv) 00:02:00 Delete Files/Folders (rm) 00:02:00 Delete Empty Folder (rmdir) 00:02:00 Change File Permissions (chmod) 00:06:00 Section 05: Text Files File Concatenation (cat) 00:03:00 File Perusal Filter (more/less) 00:02:00 Terminal Based Text Editor (nano) 00:03:00 Section 06: Users Run Commands As A Superuser (sudo) 00:03:00 Change User (su) 00:03:00 Show Effecter User and Group IDs (id) 00:02:00 Section 07: Killing Programs & Logging Out Kill A Running Command (ctrl + c) 00:02:00 Kill All Processes By A Name (killall) 00:02:00 Logging Out Of Bash (exit) 00:01:00 Section 08: Shortcuts Tell Bash That There Is No More Input (ctrl + d) 00:02:00 Clear The Screen (ctr + l) 00:02:00 Zoom In (ctrl + +) 00:02:00 Zoom Out (ctrl + -) 00:02:00 Moving The Cursor 00:02:00 Deleting Text 00:04:00 Fixing Typos 00:03:00 Cutting and Pasting 00:03:00 Character Capitalisation 00:03:00 Section 09: Bash Bash File Structure 00:03:00 Echo Command 00:04:00 Comments 00:04:00 Variables 00:06:00 Strings 00:06:00 While Loop 00:04:00 For Loop 00:04:00 Until Loop 00:03:00 Break & Continue 00:03:00 Get User Input 00:02:00 If Statement 00:09:00 Case Statements 00:06:00 Get Arguments From The Command Line 00:04:00 Functions 00:05:00 Global vs Local Variables 00:03:00 Arrays 00:06:00 Shell & Environment Variables 00:06:00 Scheduled Automation 00:03:00 Aliases 00:03:00 Wildcards 00:03:00 Multiple Commands 00:02:00 Section 10: Resource Resource 00:00:00 Assignment Assignment - Bash Scripting; Linux and Shell Programming Masterclass 00:00:00

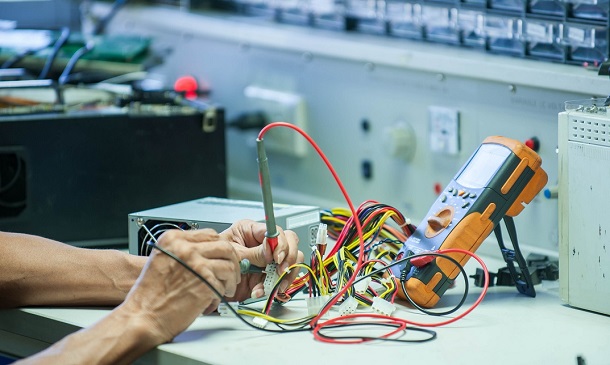
Delve into the world of electronics with our 'Electronic Device Maintenance and Troubleshooting Course.' This programme is meticulously crafted to transform beginners into proficient troubleshooters and maintenance experts of electronic devices. Starting with an introductory section, the course familiarises learners with the basics, setting a strong foundation for more complex topics. As you progress, the curriculum delves deeper into the intricate world of electronic and electrical maintenance, equipping you with the knowledge to handle a wide array of electronic devices. The course is segmented into comprehensive sections, each focusing on a critical aspect of electronic maintenance. You will learn about essential tools, dive into the complexities of electronic components, and master the skills of testing and troubleshooting. The highlight of the programme is a detailed guide on electronic components, presented in an easy-to-follow, step-by-step format. This course is not just about theoretical knowledge; it's an invitation to a hands-on journey where each module builds your confidence and skills, preparing you for real-world applications. Learning Outcomes Gain foundational knowledge in electronic device maintenance. Understand the various tools required for electronic repairs. Learn about different electronic components and their functions. Develop skills in testing electronic devices and components. Master the techniques of troubleshooting electronic malfunctions. Why choose this Electronic Device Maintenance and Troubleshooting Course? Unlimited access to the course for a lifetime. Opportunity to earn a certificate accredited by the CPD Quality Standards and CIQ after completing this course. Structured lesson planning in line with industry standards. Immerse yourself in innovative and captivating course materials and activities. Assessments designed to evaluate advanced cognitive abilities and skill proficiency. Flexibility to complete the Course at your own pace, on your own schedule. Receive full tutor support throughout the week, from Monday to Friday, to enhance your learning experience. Unlock career resources for CV improvement, interview readiness, and job success. Who is this Electronic Device Maintenance and Troubleshooting Course for? Enthusiasts eager to delve into the field of electronic maintenance. Individuals aspiring to build a career in electronic device repair. Hobbyists looking to enhance their skills in electronics troubleshooting. Professionals seeking to update and expand their electronic repair knowledge. Students and apprentices aiming to gain practical insights into electronic maintenance. Career path Electronic Repair Technician: £20,000 - £30,000 Maintenance Engineer: £25,000 - £35,000 Technical Support Specialist: £22,000 - £32,000 Field Service Technician: £23,000 - £33,000 Electronics Engineer: £28,000 - £38,000 Instrumentation Technician: £24,000 - £34,000 Prerequisites This Electronic Device Maintenance and Troubleshooting Course does not require you to have any prior qualifications or experience. You can just enrol and start learning.This Electronic Device Maintenance and Troubleshooting Course was made by professionals and it is compatible with all PC's, Mac's, tablets and smartphones. You will be able to access the course from anywhere at any time as long as you have a good enough internet connection. Certification After studying the course materials, there will be a written assignment test which you can take at the end of the course. After successfully passing the test you will be able to claim the pdf certificate for £4.99 Original Hard Copy certificates need to be ordered at an additional cost of £8. Course Curriculum Section 1: Introduction & Getting Started Unit 1: Introduction 00:02:00 Unit 2: Instructor's Introduction 00:05:00 Section 2: Electronic and Electrical maintenance Repair Unit 1: Becoming a Troubleshooter 00:02:00 Section 3: Tools Needed Unit 1: Tools Needed 00:01:00 Unit 2: Multimeters 00:07:00 Unit 3: Wire Cutter and Stripper 00:03:00 Unit 4: Wiring Tools Soldering Iron 00:02:00 Unit 5: Screw Drivers 00:03:00 Unit 6: Pliers 00:02:00 Unit 7: Wrench 00:02:00 Unit 8: Oscilloscope and Function Generator 00:03:00 Section 4: Electronic Components Unit 1: Passive Electronic Components 00:03:00 Unit 2: Active Electronic Component Diode 00:03:00 Unit 3: Active Electronic Component Transistor 00:03:00 Unit 4: Common Electronic and Electrical Components 00:05:00 Section 5: Testing Unit 1: Testing a Fuse 00:03:00 Unit 2: Testing a Bulb or Lamp 00:02:00 Unit 3: Testing a Switch 00:01:00 Unit 4: Testing a Transformer 00:04:00 Unit 5: Testing a Resistance 00:08:00 Section 6: Troubleshooting Unit 1: Safety Concerns 00:05:00 Unit 2: Main Concerns - Maintenance 00:02:00 Unit 3: Main Concerns - Servicing 00:02:00 Unit 4: Troubleshooting Part - 1 00:03:00 Unit 5: Troubleshooting Part - 2 00:04:00 Section 7: Introduction to Electronic Components: A Step by Step Guide Unit 1: Introduction 00:05:00 Unit 2: Voltage Current and Resistance 00:06:00 Unit 3: Types of Current 00:03:00 Unit 4: Types of Circuits 00:02:00 Unit 5: Practical: Introduction to Digital Multimeter DMM 00:07:00 Unit 6: Volt Ohm Meter Basics 00:05:00 Unit 7: Measuring Voltage 00:13:00 Unit 8: Practical: How to Measure DC Voltage 00:03:00 Unit 9: Measuring Current 00:05:00 Unit 10: Measuring Currents - Lab Experiment Explained 00:11:00 Unit 11: Practical 1: How to Measure Current 00:04:00 Unit 12: Practical 2: How to Measure Current 00:01:00 Unit 13: Measuring Resistance 00:08:00 Unit 14: Practical: How to Test Resistors 00:05:00 Unit 15: Circuit Diagram Basics and Basic Symbols 00:12:00 Unit 16: Introduction to Resistor and Color Band Coding 00:09:00 Unit 17: Power Dissipation + Parallel and Series Resistors 00:12:00 Unit 18: Ohm's Law 00:14:00 Unit 19: Introduction to Capacitors 00:11:00 Unit 20: Capacitors Behavior + Capacitors in Series and Parallel 00:07:00 Unit 21: Practical 1: How to Test a Capacitor 00:03:00 Unit 22: Practical 2: How to Test A Capacitor 00:02:00 Unit 23: Introduction to Inductors 00:07:00 Unit 24: Practical: How to Test and Measure Coils 00:06:00 Unit 25: Introduction to Diode + Zener Diode and LED 00:08:00 Unit 26: Practical 1: How to Test a Diode 00:02:00 Unit 27: Practical 2: How to Test a Diode 00:02:00 Unit 28: Introduction to Transistors 00:10:00 Unit 29: Practical 1: How to Test a Transistor 00:04:00 Unit 30: Practical 2: How to Test a Transistor 00:04:00 Unit 31: Practical 3: How to Test a Transistor 00:03:00 Assignment Assignment - Electronic Device Maintenance and Troubleshooting Course 00:00:00
Starting the journey on the 'Functional Skills IT/ICT Level 2' course unlocks a world of digital prowess, essential in today's tech-driven era. Learners will explore the essentials of system hardware, understand the nuances of operating systems, and gain crucial insights into data storage and sharing. Moreover, the curriculum extends to practical skills in setting up and configuring both PCs and mobile devices, ensuring a well-rounded understanding of modern technology. As the course progresses, students will delve into the complexities of network and internet connectivity, IT security, and efficient computer maintenance. The final stages of the course focus on specialised areas like troubleshooting, database understanding, and software development, equipping learners with the knowledge to excel in the evolving tech landscape. Learning Outcomes: Acquire comprehensive knowledge of computer usage, system hardware, and peripherals. Master skills in configuring and managing PCs and mobile devices. Develop proficiency in data storage, file management, and application software usage. Gain expertise in network connectivity, IT security, and computer maintenance. Understand database systems and acquire skills in software development and implementation. Why buy this Functional Skills IT course? Unlimited access to the course for forever Digital Certificate, Transcript, student ID all included in the price Absolutely no hidden fees Directly receive CPD accredited qualifications after course completion Receive one to one assistance on every weekday from professionals Immediately receive the PDF certificate after passing Receive the original copies of your certificate and transcript on the next working day Easily learn the skills and knowledge from the comfort of your home Certification After studying the course materials of the Functional Skills IT/ ICT Level 2 there will be a written assignment test which you can take either during or at the end of the course. After successfully passing the test you will be able to claim the pdf certificate for £5.99. Original Hard Copy certificates need to be ordered at an additional cost of £9.60. Who is this Functional Skills IT course for? Individuals seeking foundational and advanced Functional IT skills. Aspiring IT professionals aiming to broaden their technical knowledge. Students pursuing a career in the information technology sector. Employees looking to enhance their IT competencies in the workplace. Entrepreneurs need technical skills for business management. Prerequisites This Functional Skills IT/ ICT Level 2 does not require you to have any prior qualifications or experience. You can just enrol and start learning.This Functional Skills IT/ ICT Level 2 was made by professionals and it is compatible with all PC's, Mac's, tablets and smartphones. You will be able to access the course from anywhere at any time as long as you have a good enough internet connection. Career path IT Support Specialist: £20,000 - £30,000 per annum Network Administrator: £25,000 - £35,000 per annum Database Manager: £30,000 - £45,000 per annum Software Developer: £25,000 - £50,000 per annum Systems Analyst: £35,000 - £55,000 per annum Cybersecurity Analyst: £30,000 - £60,000 per annum Course Curriculum Section 01: How People Use Computers The Case for Computer Literacy 00:03:00 Features Common to Every Computing Device 00:02:00 Common General-Purpose Computing Devices 00:02:00 Networks of Computing Devices 00:04:00 Remotely-Accessed Computer Systems 00:04:00 Specialized Computer Systems 00:02:00 Specialty I/O Devices 00:01:00 Section 02: System Hardware CPUs 00:03:00 Passive and Active Cooling 00:03:00 RAM and Active Memory 00:05:00 Motherboards 00:03:00 Power Supplies 00:03:00 AMA - Ask Me Anything about System Hardware 00:07:00 Section 03: Device Ports and Peripherals Ports and Connectors 00:03:00 General Use I/O Devices 00:03:00 AMA - Ask Me Anything about I/O, Ports and Peripherals 00:07:00 Section 04: Data Storage and Sharing Basics of Binary 00:04:00 Storage Technologies 00:04:00 Mass Storage Variation 00:03:00 AMA - Ask Me Anything about Data Storage and Sharing 00:07:00 Section 05: Understanding Operating Systems Operating System Functions 00:04:00 Operating System Interfaces 00:05:00 AMA - Ask Me Anything about Understanding OS's 00:05:00 Section 06: Setting Up and Configuring a PC Preparing the Work Area 00:02:00 Setting up a Desktop PC 00:01:00 Completing PC Setup 00:04:00 AMA - Ask Me Anything about Setting up and Configuring a PC 00:09:00 Section 07: Setting Up and Configuring a Mobile Device Personalizing a Tablet 00:08:00 AMA - Ask Me Anything about Mobile Devices Part 1 00:07:00 AMA - Ask Me Anything about Mobile Devices Part 2 00:07:00 Section 08: Managing Files File Management Tools 00:02:00 File Manipulation 00:06:00 Backups 00:03:00 AMA - Ask Me Anything about Managing Files 00:08:00 Section 09: Using and Managing Application Software Walking Survey of Applications 00:03:00 Managing Applications 00:03:00 Applications and Extensions 00:04:00 AMA - Ask Me Anything about Working with Applications 00:07:00 Section 10: Configuring Network and Internet Connectivity Wi-Fi Setup 00:06:00 Going High Speed 00:03:00 Setting Up and Sharing Printers 00:05:00 AMA - Ask Me Anything about Networks and Internet Connectivity Part 1 00:07:00 AMA - Ask Me Anything about Networks and Internet Connectivity Part 2 00:05:00 Section 11: IT Security Threat Mitigation Physical Security 00:05:00 Password Management 00:03:00 Clickworthy 00:03:00 Perils of Public Internet 00:02:00 AMA - Ask Me Anything about IT Threat Mitigation Part 1 00:07:00 AMA - Ask Me Anything about IT Threat Mitigation Part 2 00:08:00 Section 12: Computer Maintenance and Management Power Management 00:02:00 Cleaning and Maintaining Computers 00:02:00 Trash it or Stash it? 00:02:00 AMA - Ask Me Anything about Computer Maintenance and Management 00:11:00 Section 13: IT Troubleshooting Troubleshooting 101 00:03:00 AMA - Ask Me Anything about Troubleshooting Computers Part 1 00:10:00 AMA - Ask Me Anything about Troubleshooting Computers Part 2 00:11:00 Section 14: Understanding Databases Introduction to Databases 00:06:00 Database Details 00:06:00 AMA - Ask Me Anything about Databases 00:06:00 Section 15: Developing and Implementing Software Introduction to Programming 00:04:00 Programming with a PBJ Sandwich 00:08:00 AMA - Ask Me Anything about Databases 00:06:00

Overview This comprehensive course on NodeJS made easy for MEAN or MERN Stack Level 4 will deepen your understanding on this topic. After successful completion of this course you can acquire the required skills in this sector. This NodeJS made easy for MEAN or MERN Stack Level 4 comes with accredited certification from CPD, which will enhance your CV and make you worthy in the job market. So enrol in this course today to fast track your career ladder. How will I get my certificate? You may have to take a quiz or a written test online during or after the course. After successfully completing the course, you will be eligible for the certificate. Who is This course for? There is no experience or previous qualifications required for enrolment on this NodeJS made easy for MEAN or MERN Stack Level 4. It is available to all students, of all academic backgrounds. Requirements Our NodeJS made easy for MEAN or MERN Stack Level 4 is fully compatible with PC's, Mac's, Laptop, Tablet and Smartphone devices. This course has been designed to be fully compatible with tablets and smartphones so you can access your course on Wi-Fi, 3G or 4G. There is no time limit for completing this course, it can be studied in your own time at your own pace. Career Path Learning this new skill will help you to advance in your career. It will diversify your job options and help you develop new techniques to keep up with the fast-changing world. This skillset will help you to- Open doors of opportunities Increase your adaptability Keep you relevant Boost confidence And much more! Course Curriculum 14 sections • 116 lectures • 06:46:00 total length •Module 01: Course and Instructor Introduction: 00:03:00 •Module 02: GITHub URL: 00:01:00 •Module 01: What is Node?: 00:05:00 •Module 02: Why Node?: 00:04:00 •Module 03: NodeJS package manager NPM: 00:02:00 •Module 04: Install Node and Visual Studio Code: 00:02:00 •Module 01: Create a simple node application: 00:04:00 •Module 02: Adding Dependencies: 00:04:00 •Module 03: OS Module: 00:05:00 •Module 04: Write a file sync and async: 00:07:00 •Module 05: Use Arrow Functions: 00:02:00 •Module 06: Append and Rename: 00:03:00 •Module 07: Read and Delete: 00:04:00 •Module 08: HTTP module in action: 00:03:00 •Module 09: Return JSON Response: 00:04:00 •Module 10: Use nodemon: 00:02:00 •Module 11: Scripts block: 00:04:00 •Module 01: Introduction 04: 00:04:00 •Module 02: What is REST?: 00:06:00 •Module 03: Create an Express App: 00:02:00 •Module 04: Express In Action: 00:05:00 •Module 05: Handle other HTTP Methods: 00:06:00 •Module 06: Use Router: 00:05:00 •Module 07: Create Customer Endpoint: 00:05:00 •Module 01: Introduction 05: 00:02:00 •Module 02: Mongo Command Line: 00:07:00 •Module 03: Steps: 00:03:00 •Module 04: Use Mongo Client: 00:04:00 •Module 05: Implement Find All: 00:04:00 •Module 06: GET single product: 00:04:00 •Module 07: What is body-parser?: 00:03:00 •Module 08: Configure body-parser: 00:02:00 •Module 09: Create Product: 00:04:00 •Module 10: Update Product: 00:06:00 •Module 11: Delete Product: 00:02:00 •Module 01: Introduction 06: 00:04:00 •Module 02: Steps: 00:01:00 •Module 03: Create Project: 00:06:00 •Module 04: Create Server JS: 00:02:00 •Module 05: Create and Configure Product Controller: 00:02:00 •Module 06: Create Mongoose Schema and Model: 00:02:00 •Module 07: Create: 00:04:00 •Module 08: Test and Flow: 00:03:00 •Module 09: Read: 00:03:00 •Module 10: Update: 00:04:00 •Module 11: Delete: 00:02:00 •Module 01: Introduction 07: 00:01:00 •Module 02: Steps 7: 00:01:00 •Module 03: Create the Project 7: 00:02:00 •Module 04: Get All: 00:02:00 •Module 05: Create and Update: 00:04:00 •Module 06: Get and Delete: 00:03:00 •Module 01: Mocha and Chai: 00:03:00 •Module 02: Steps 8: 00:02:00 •Module 03: Install Dependencies: 00:01:00 •Module 04: First Test: 00:06:00 •Module 05: Handle Failures: 00:02:00 •Module 06: Test Create and Get: 00:02:00 •Module 07: Before and after methods: 00:03:00 •Module 01: Introduction 09: 00:03:00 •Module 02: Steps 09: 00:03:00 •Module 03: Create DB Connection: 00:04:00 •Module 04: Mongoose Static Methods: 00:03:00 •Module 05: Create the Model and DAO: 00:07:00 •Module 06: Create the Controller: 00:08:00 •Module 07: Map Routes: 00:05:00 •Module 08: Test: 00:02:00 •Module 09: Use src folder: 00:02:00 •Module 10: Use Babel and ES6 Syntax: 00:06:00 •Module 01: Usecase: 00:01:00 •Module 02: Create the Project: 00:03:00 •Module 03: Setup Configuration: 00:04:00 •Module 04: Create Model: 00:05:00 •Module 05: Implement Patient DAO: 00:03:00 •Module 06: Create Patient Controller: 00:04:00 •Module 07: Create and Configure Routes: 00:03:00 •Module 08: Create Clinical DAO and Controller: 00:07:00 •Module 09: Run and Test: 00:06:00 •Module 10: Fix Bug and Test: 00:02:00 •Module 01: Introduction 11: 00:02:00 •Module 02: Install Docker Desktop: 00:01:00 •Module 03: Steps: 00:03:00 •Module 04: Create Dockerfile: 00:07:00 •Module 05: Create docker-compose.yml: 00:05:00 •Module 06: docker compose up: 00:05:00 •Module 01: Introduction 12: 00:01:00 •Module 02: AWS EC2 Introduction: 00:03:00 •Module 03: Launch an EC2 Instance: 00:05:00 •Module 04: Windows - Use MobaXterm and connect: 00:04:00 •Module 05: Install Mongo: 00:04:00 •Module 06: Install Node and Git: 00:02:00 •Module 07: Push Project to Github: 00:04:00 •Module 08: Run the APP on EC2 and Test: 00:04:00 •Module 01: Introduction 13: 00:01:00 •Module 02: Install React CLI: 00:01:00 •Module 03: Create Project: 00:06:00 •Module 04: Create Components: 00:03:00 •Module 05: Configure Routing: 00:04:00 •Module 06: Home Component: 00:03:00 •Module 07: Use State and React Hook: 00:04:00 •Module 08: Render Rows: 00:03:00 •Module 09: Enable CORS on the Node Project: 00:04:00 •Module 10: Test Home Page: 00:03:00 •Module 11: Add Patient - Create Form: 00:05:00 •Module 12: Handle Submit: 00:04:00 •Module 13: Add Clinical's - Create Form: 00:07:00 •Module 14: Add Clinical's - Handle Submit: 00:04:00 •Module 01: Introduction 14: 00:02:00 •Module 02: Steps 14: 00:01:00 •Module 03: Setup the database: 00:03:00 •Module 04: Setup Project: 00:02:00 •Module 05: Get All: 00:05:00 •Module 06: Get One: 00:03:00 •Module 07: Create: 00:04:00 •Module 08: Return after Insert: 00:02:00 •Module 09: Update: 00:03:00

Overview This comprehensive course on Learn AutoCAD Programming using VB.NET - Hands On! will deepen your understanding on this topic. After successful completion of this course you can acquire the required skills in this sector. This Learn AutoCAD Programming using VB.NET - Hands On! comes with accredited certification from CPD, which will enhance your CV and make you worthy in the job market. So enrol in this course today to fast track your career ladder. How will I get my certificate? You may have to take a quiz or a written test online during or after the course. After successfully completing the course, you will be eligible for the certificate. Who is This course for? There is no experience or previous qualifications required for enrolment on this Learn AutoCAD Programming using VB.NET - Hands On!. It is available to all students, of all academic backgrounds. Requirements Our Learn AutoCAD Programming using VB.NET - Hands On! is fully compatible with PC's, Mac's, Laptop, Tablet and Smartphone devices. This course has been designed to be fully compatible with tablets and smartphones so you can access your course on Wi-Fi, 3G or 4G. There is no time limit for completing this course, it can be studied in your own time at your own pace. Career Path Having these various qualifications will increase the value in your CV and open you up to multiple sectors such as Business & Management, Admin, Accountancy & Finance, Secretarial & PA, Teaching & Mentoring etc. Course Curriculum 11 sections • 105 lectures • 12:09:00 total length •Module 01: Course Outline: 00:05:00 •Module 02: Introduction: 00:01:00 •Module 03: Who is this Course for?: 00:01:00 •Module 04: What will I learn from this Course?: 00:01:00 •Module 05: What is VB.NET?: 00:01:00 •Module 06: What is AutoCAD .NET API?: 00:01:00 •Module 07: What are the advantages of programming in AutoCAD .NET API?: 00:01:00 •Module 08: Hands-on Projects overview: 00:06:00 •Module 01: AutoCAD .NET API Components Overview: 00:01:00 •Module 02: AutoCAD .NET API Assemblies: 00:02:00 •Module 03: Understanding AutoCAD Object Hierarchy: 00:03:00 •Module 04: AutoCAD .NET API Application Object: 00:02:00 •Module 05: AutoCAD .NET API Document Object: 00:02:00 •Module 06: AutoCAD .NET API Database Object: 00:04:00 •Module 01: Section Overview: 00:04:00 •Module 02: Installing Visual Studio 2019: 00:05:00 •Module 03: Setting up Visual Studio 2019 Integrated Development Environment (IDE): 00:04:00 •Module 04: Creating First VB.NET Plugin (Hello AutoCAD): 00:12:00 •Module 05: Different ways to communicate with the User: 00:04:00 •Module 06: Configuring VS2019 Target Processor: 00:10:00 •Module 01: Creating AutoCAD Object using VB.NET Overview: 00:01:00 •Module 02: Creating DrawObjects Project: 00:04:00 •Module 03: Creating a Line Object using VB.NET: 00:15:00 •Module 04: Creating a MText Object using VB.NET: 00:12:00 •Module 05: Creating a Circle Object using VB.NET: 00:09:00 •Module 06: Creating an Arc Object using VB.NET: 00:07:00 •Module 07: Creating a Polyline Object using VB.NET: 00:08:00 •Module 08: Creating Multiple Circles Vertically: 00:09:00 •Module 09: Creating Multiple Circles Horizontally: 00:05:00 •Module 01: Manipulating AutoCAD Objects Overview: 00:01:00 •Module 02: Creating the Project ManipulateObjects: 00:04:00 •Module 03: Creating the SingleCopy Method: 00:13:00 •Module 04: Creating the MultipleCopy Method: 00:11:00 •Module 05: Creating the EraseObject Method: 00:12:00 •Module 06: Creating the MoveObject method: 00:07:00 •Module 07: Creating the MirrorObject method: 00:10:00 •Module 08: Creating the RotateObject method: 00:07:00 •Module 09: Creating the ScaleObject method: 00:05:00 •Module 10: Creating the OffsetObject method: 00:05:00 •Module 01: Exploring AutoCAD Dictionaries - Overview: 00:02:00 •Module 02: Creating LayersLineTypesAndStyles Project: 00:06:00 •Module 03: Creating the ListLayers Method: 00:11:00 •Module 04: Creating the CreateLayer Method: 00:10:00 •Module 05: Creating the UpdateLayer Method: 00:12:00 •Module 06: Creating the SetLayerOnOff Method: 00:08:00 •Module 07: Creating the SetLayerFrozenOrThaw Method: 00:04:00 •Module 08: Creating the DeleteLayer Method: 00:05:00 •Module 09: Creating the LockUnlockLayer Method: 00:04:00 •Module 10: Creating the SetLayerToObject Method: 00:08:00 •Module 11: Creating the ListLineTypes Method: 00:09:00 •Module 12: Creating the LoadLineType Method: 00:07:00 •Module 13: Creating the SetCurrentLineType Method: 00:05:00 •Module 14: Creating the DeleteLineType Method: 00:09:00 •Module 15: Creating the SetLineTypeToObject Method: 00:05:00 •Module 16: Exploring TextStyles - Overview: 00:01:00 •Module 17: Creating the ListStyles Method: 00:08:00 •Module 18: Creating the UpdateCurrentTextStyleFont Method: 00:12:00 •Module 19: Creating the SetCurrentTextStyle Method: 00:08:00 •Module 20: Creating the SetTextStyleToObject Method: 00:08:00 •Module 01: User Input Functions - Overview: 00:02:00 •Module 02: Creating the UserInteractions Project: 00:03:00 •Module 03: Creating the GetName Method: 00:11:00 •Module 04: Creating the SetLayer Method using the GetString function: 00:12:00 •Module 05: Creating the CreateLineUsingGetpoint Method: 00:11:00 •Module 06: Creating the CalculateDefinedArea Method: 00:17:00 •Module 07: Creating the DrawObjectsUsingGetKeywords Method: 00:14:00 •Module 08: Creating the GetDistanceBetweenTwoPoints Method: 00:05:00 •Module 09: Creating the CountObjects Method: 00:15:00 •Module 01: Selection Sets and Filters - Overview: 00:13:00 •Module 02: Creating the SelectionSets Project: 00:05:00 •Module 03: Creating the SelectAllAndChangeLayer Method: 00:12:00 •Module 04: Creating the SelectObjectOnScreen Method: 00:08:00 •Module 05: Creating the SelectWindowAndChangeColor Method: 00:06:00 •Module 06: Creating the SelectCrossingAndDelete Method: 00:05:00 •Module 07: Creating the SelectFenceAndChangeLayer Method: 00:06:00 •Module 08: Creating the CountPickFirstSelection Method: 00:07:00 •Module 09: Creating the SelectLines Method: 00:13:00 •Module 10: Creating the SelectMTexts Method: 00:05:00 •Module 11: Creating the SelectPlines Method: 00:04:00 •Module 12: Creating the SelectWalls Method: 00:07:00 •Module 13: Creating the SelectStairs Method: 00:03:00 •Module 14: Creating the SelectFrenchDoors Method: 00:04:00 •Module 15: Creating the SelectBifoldDoors Method: 00:03:00 •Module 16: Creating CountReceptacles Method: 00:04:00 •Module 17: Creating the CountLightingFixtures Method: 00:10:00 •Module 01: Developing Projects - Hands on Overview: 00:02:00 •Module 02: BlocksCounter Plugin Demo: 00:03:00 •Module 03: Creating the BlocksCounter Project: 00:04:00 •Module 04: Creating the CountBlocksToTable Method: 00:08:00 •Module 05: Creating the PromptUser Function: 00:08:00 •Module 06: Creating the GatherBlocksAndDrawTable Method: 00:12:00 •Module 07: Continuation of GatherBlocksAndDrawTable Method: 00:17:00 •Module 08: Running and Debugging the BlocksCounter Project - Part 1: 00:15:00 •Module 09: Running and Debugging the BlocksCounter Project - Part 2: 00:11:00 •Module 10: Running and Debugging the BlocksCounter Project - Part 3: 00:01:00 •Module 11: Creating the ObjectExtractor Plugin Project: 00:04:00 •Module 12: Creating the ExtractObjects Method: 00:07:00 •Module 13: Creating the ExtractLine Method: 00:16:00 •Module 14: Running and Debugging the ExtractLine Method: 00:05:00 •Module 15: Creating the ExtractCircle Method: 00:11:00 •Module 16: Creating the ExtractMText Method: 00:13:00 •Module 17: Creating the ExtractPolyline Method: 00:19:00 •Module 18: Creating the ExtractBlock Method: 00:10:00 •Module 01: Congratulations and Thank you very much!: 00:01:00 •Assignment - Learn AutoCAD Programming using VB.NET - Hands On!: 00:00:00

Payroll Accountant Mini Bundle
By Compete High
Step confidently into the world of finance with the Payroll Accountant Mini Bundle, designed to boost your hireability in accounting, payroll, and data-driven roles. This bundle highlights your capabilities in payroll, financial analysis, accounting, data analysis, and VAT — skills that every finance team values highly. If you want to stand out in a competitive job market, this bundle is your pathway to becoming an indispensable payroll accountant. With demand soaring for professionals skilled in payroll and accounting, combined with expertise in financial analysis, data analysis, and VAT, your career prospects just got brighter. Don’t miss the chance to secure your future today. Description This bundle integrates critical business functions—payroll management, financial analysis evaluation, core accounting principles, precise data analysis, and comprehensive VAT knowledge—that employers actively seek. The skills in payroll, financial analysis, accounting, data analysis, and VAT signal your readiness to manage complex payroll accounts and ensure compliance with tax regulations. Industries from corporate finance to small business accounting rely on professionals fluent in payroll operations and accounting standards, with sharp financial analysis and data analysis skills to interpret numbers accurately. Plus, VAT expertise is a must-have for smooth fiscal operations. This bundle prepares you to meet those exact demands, making you a highly hireable candidate. FAQ Q: Who benefits from this bundle? A: Aspiring payroll accountants, finance assistants, and those targeting accounting departments. Q: Are these skills in demand? A: Yes, employers constantly seek proficiency in payroll, accounting, financial analysis, data analysis, and VAT. Q: Will this help with VAT compliance roles? A: Absolutely. VAT is a vital part of modern accounting and tax functions. Q: Can I apply these skills immediately? A: Yes. This bundle equips you with practical, job-ready knowledge. Q: Is prior experience required? A: No. It’s designed for newcomers and those improving existing skills. Q: Why enroll now? A: Finance and payroll jobs grow steadily; the earlier you train, the better your prospects.

Cisco SISE Implementing and Configuring Cisco Identity Services Engine v3.0
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for Network security engineers ISE administrators Wireless network security engineers Cisco integrators and partners Overview After taking this course, you should be able to: Describe Cisco ISE deployments, including core deployment components and how they interact to create a cohesive security architecture. Describe the advantages of such a deployment and how each Cisco ISE capability contributes to these advantages. Describe concepts and configure components related to 802.1X and MAC Authentication Bypass (MAB) authentication, identity management, and certificate services. Describe how Cisco ISE policy sets are used to implement authentication and authorization, and how to leverage this capability to meet the needs of your organization. Describe third-party Network Access Devices (NADs), Cisco TrustSec, and Easy Connect. Describe and configure web authentication, processes, operation, and guest services, including guest access components and various guest access scenarios. Describe and configure Cisco ISE profiling services, and understand how to monitor these services to enhance your situational awareness about network-connected endpoints. Describe best practices for deploying this profiler service in your specific environment. Describe BYOD challenges, solutions, processes, and portals. Configure a BYOD solution, and describe the relationship between BYOD processes and their related configuration components. Describe and configure various certificates related to a BYOD solution. Describe the value of the My Devices portal and how to configure this portal. Describe endpoint compliance, compliance components, posture agents, posture deployment and licensing, and the posture service in Cisco ISE. Describe and configure TACACS+ device administration using Cisco ISE, including command sets, profiles, and policy sets. Understand the role of TACACS+ within the Authentication, Authentication, and Accounting (AAA) framework and the differences between the RADIUS and TACACS+ protocols. Migrate TACACS+ functionality from Cisco Secure Access Control System (ACS) to Cisco ISE, using a migration tool. Implementing and Configuring Cisco Identity Services Engine (SISE) v3.0 is a Cisco ISE training program that discusses the Cisco Identity Services Engine, an identity and access control policy platform that provides a single policy plane across the entire organization, combining multiple services, including authentication, authorization, and accounting (AAA), posture, profiling, device onboarding, and guest management, into a single context-aware identity-based platform. This CCNA course provides students with the knowledge and skills to enforce security posture compliance for wired and wireless endpoints as well as enhance infrastructure security using the Cisco ISE. Introducing Cisco ISE Architecture and Deployment Using Cisco ISE as a Network Access Policy Engine Cisco ISE Use Cases Describing Cisco ISE Functions Cisco ISE Deployment Models Context Visibility Cisco ISE Policy Enforcement Using 802.1X for Wired and Wireless Access Using MAC Authentication Bypass for Wired and Wireless Access Introducing Identity Management Configuring Certificate Services Introducing Cisco ISE Policy Implementing Third-Party Network Access Device Support Introducing Cisco TrustSec Cisco TrustSec Configuration Easy Connect Web Authentication and Guest Services Introducing Web Access with Cisco ISE Introducing Guest Access Components Configuring Guest Access Settings Configuring Sponsor and Guest Portals Cisco ISE Profiler Introducing Cisco ISE Profiler Profiling Deployment and Best Practices Cisco ISE BYOD Introducing the Cisco ISE BYOD Process Describing BYOD Flow Configuring the My Devices Portal Configuring Certificates in BYOD Scenarios Cisco ISE Endpoint Compliance Services Introducing Endpoint Compliance Services Configuring Client Posture Services and Provisioning in Cisco ISE Working with Network Access Devices Review TACACS+ Cisco ISE TACACS+ Device Administration Configure TACACS+ Device Administration TACACS+ Device Administration Guidelines and Best Practices Migrating from Cisco ACS to Cisco ISE Lab outline Access the SISE Lab and Install ISE 2.4 Configure Initial Cisco ISE Setup, GUI Familiarization, and System Certificate Usage Integrate Cisco ISE with Active Directory Configure Basic Policy on Cisco ISE Configure Policy Sets Configure Access Policy for Easy Connect Configure Guest Access Configure Guest Access Operations Create Guest Reports Configure Profiling Customize the Cisco ISE Profiling Configuration Create Cisco ISE Profiling Reports Configure BYOD Blacklisting a Device Configure Cisco ISE Compliance Services Configure Client Provisioning Configure Posture Policies Test and Monitor Compliance-Based Access Test Compliance Policy Configure Cisco ISE for Basic Device Administration Configure TACACS+ Command Authorization

SCM670 SAP Global Available-to-Promise
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for The primary audience for this course are Application Consultants, Business Process Architects, Business Process Owners/Team Leads/Power Users, and Solution Architects. Overview Become familiar with detailed information about the functions of the global availability check in the SAP SCM solution in the context of sales and distribution. In this course, students learn in detail the different standard & advanced availability check capabilities of the integrated SAP APO Global-Available to Promise component, embedded in corresponding business scenarios & along with the relevant settings. Overview of Global Available-to-Promise (Global ATP) Outlining the Functionality of Global Available-to-Promise (Global ATP) Integration of Global Available-to-Promise (Global ATP) Explaining the Use of Core Interface (CIF) Integration with Global Available-to-Promise (Global ATP) Check Method Selection in Global Available-to-Promise (Global ATP) Explaining Availability Check Methods Product Availability Check in Global Available-to-Promise (Global ATP) Checking Product Availability in Global Available-to-Promise (Global ATP) Checking Scope in Global Available-to-Promise (Global ATP) Setting the Checking Horizon in Global Available-to-Promise (Global ATP) Evaluating Logic in the Available-to-Promise (ATP) Check in Global Available-to-Promise (Global ATP) Product Allocation in Global Available-to-Promise (Global ATP) Setting Up Single Level Product Allocation in Global Available- to-Promise (Global ATP) Setting Up Multilevel Product Allocation in Global Available-to- Promise (Global ATP) Check Against the Forecast in Global Available-to-Promise (Global ATP) Setting Up the Check Against Forecast in Global Available-to- Promise (Global ATP) Rules-Based Availability Check in Global Available-to-Promise (Global ATP) Setting Up Rules-Based Availability Check in Global Available-to- Promise (Global ATP) Configuring Rule Determination Based on the Condition Technique in Global Available-to-Promise (Global ATP) Setting Up a Consolidation Location in Rules-Based Available-to- Promise (ATP) Check Using the Multi-Item Single Delivery Location (MISL) Function in Global Available-to-Promise (Global ATP) Using the Exclusive Rule Strategy in Global Available-to-Promise (Global ATP) Configuring Product Interchangeability Master Data in Global Available-to-Promise (Global ATP) Production Within the ATP Check in Global Available-to-Promise (Global ATP) Configuring the Capable-to-Promise (CTP) Procedure in Global Available-to-Promise (Global ATP) Configuring the Multilevel ATP Check (MATP) Procedure in Global Available-to-Promise (Global ATP) Backorder Processing in Global Available-to-Promise (Global ATP) Executing Backorder Processing in Global Available-to-Promise (Global ATP) Using Enhanced Interactive Backorder Processing in Global Available-to-Promise (Global ATP) Configuring Event-Driven Quantity Assignment in Global Available- to-Promise (Global ATP) Setting Up Reassignment of Order Confirmations in Global Available-to-Promise (Global ATP) Transportation and Shipment Scheduling in Global Available-to- Promise (Global ATP) Scheduling Transportation and Shipment Using Master Data in Global Available-to-Promise (Global ATP) Scheduling Transportation and Shipment Using the Condition Technique in Global Available-to-Promise (Global ATP) Scheduling Transportation and Shipment Using Configuration in Global Available-to-Promise (Global ATP) Scheduling Transportation and Shipment Scheduling using Configuration and Calendars in Global Available-to-Promise (Global ATP) Additional course details: Nexus Humans SCM670 SAP Global Available-to-Promise training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the SCM670 SAP Global Available-to-Promise course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Cisco Understanding Cisco Cybersecurity Operations Fundamentals v1.0 (CBROPS)
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for This course is designed for individuals seeking a role as an associate-level cybersecurity analyst and IT professionals desiring knowledge in Cybersecurity operations or those in pursuit of the Cisco Certified CyberOps Associate certification including Students pursuing a technical degree Current IT professionals Recent college graduates with a technical degree Overview After taking this course, you should be able to Explain how a Security Operations Center (SOC) operates and describe the different types of services that are performed from a Tier 1 SOC analyst's perspective. Explain Network Security Monitoring (NSM) tools that are available to the network security analyst. Explain the data that is available to the network security analyst. Describe the basic concepts and uses of cryptography. Describe security flaws in the TCP/IP protocol and how they can be used to attack networks and hosts. Understand common endpoint security technologies. Understand the kill chain and the diamond models for incident investigations, and the use of exploit kits by threat actors. Identify resources for hunting cyber threats. Explain the need for event data normalization and event correlation. Identify the common attack vectors. Identify malicious activities. Identify patterns of suspicious behaviors. Conduct security incident investigations. Explain the use of a typical playbook in the SOC. Explain the use of SOC metrics to measure the effectiveness of the SOC. Explain the use of a workflow management system and automation to improve the effectiveness of the SOC. Describe a typical incident response plan and the functions of a typical Computer Security Incident Response Team (CSIRT). Explain the use of Vocabulary for Event Recording and Incident Sharing (VERIS) to document security incidents in a standard format. The Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) v1.0 course teaches you security concepts, common network and application operations and attacks, and the types of data needed to investigate security incidents. This course teaches you how to monitor alerts and breaches, and how to understand and follow established procedures for response to alerts converted to incidents. Through a combination of lecture, hands-on labs, and self-study, you will learn the essential skills, concepts, and technologies to be a contributing member of a cybersecurity operations center (SOC) including understanding the IT infrastructure, operations, and vulnerabilities. This course helps you prepare for the Cisco Certified CyberOps Associate certification and the role of a Junior or Entry-level cybersecurity operations analyst in a SOC. Course Outline Defining the Security Operations Center Understanding Network Infrastructure and Network Security Monitoring Tools Exploring Data Type Categories Understanding Basic Cryptography Concepts Understanding Common TCP/IP Attacks Understanding Endpoint Security Technologies Understanding Incident Analysis in a Threat-Centric SOC Identifying Resources for Hunting Cyber Threats Understanding Event Correlation and Normalization Identifying Common Attack Vectors Identifying Malicious Activity Identifying Patterns of Suspicious Behavior Conducting Security Incident Investigations Using a Playbook Model to Organize Security Monitoring Understanding SOC Metrics Understanding SOC Workflow and Automation Describing Incident Response Understanding the Use of VERIS Understanding Windows Operating System Basics Understanding Linux Operating System Basics Additional course details: Nexus Humans Cisco Understanding Cisco Cybersecurity Operations Fundamentals v1.0 (CBROPS) training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Cisco Understanding Cisco Cybersecurity Operations Fundamentals v1.0 (CBROPS) course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.
