- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
VMware Workspace ONE: Deploy and Manage [V22.x]
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for Workspace ONE UEM and Workspace ONE Access operators and administrators, account managers, solutions architects, solutions engineers, sales engineers, and consultants Overview By the end of the course, you should be able to meet the following objectives: Explain and apply the fundamental techniques for launching and maintaining an intelligence-driven, multiplatform endpoint management solution with Workspace ONE UEM Outline the components of Workspace ONE UEM Explain the general features and functionality enabled with Workspace ONE UEM Summarize the basic Workspace ONE administrative functions Explain and deploy common Workspace ONE integrations Securely deploy configurations to Workspace ONE UEM managed devices Onboard device endpoints into Workspace ONE UEM Summarize the alternative management methodologies for rugged devices Discuss strategies to maintain environment and device fleet health Configure and deploy applications to Workspace ONE UEM managed devices Analyze a Workspace ONE UEM deployment Enable email access on devices Integrate Workspace ONE UEM with content repositories and corporate file shares Explain the general features and functionalities that Workspace ONE Access enables Demonstrate how to integrate Workspace ONE UEM with Workspace ONE Access Summarize and implement Workspace ONE productivity services into the digital workspace environment Explain the methods of enabling mobile single sign-on for mobile endpoints managed in the digital workspace Configure Workspace ONE Access to support SAML 2.0 for federated authentication across the workforce In this five-day course, you learn how to apply the fundamental techniques for launching and maintaining an intelligence-driven, multiplatform, endpoint management solution with VMware Workspace ONE© UEM. Through a combination of hands-on labs, simulations, and interactive lectures, you will configure and manage the endpoint life cycle. After the course, you will have the foundational knowledge for effectively implementing Workspace ONE UEM.Also, you learn how to apply the fundamental techniques for integrating VMware Workspace ONE© Access? with Workspace ONE UEM to securely distribute business-critical applications from any device and to configure access management controls. Through a combination of hands-on labs, simulations, and interactive lectures, you configure Workspace ONE Access and Workspace ONE UEM system and productivity integrations.You will leave with a foundational understanding of how Workspace ONE uses various authentication methods and protocols to determine user access permissions and enable single sign-on. Overall, the course lays out the foundational principles of identity and access management.Please note - This course is a combination of the VMware Workspace ONE: Skills for UEM and the VMware Workspace ONE: Integrations course. Course Introduction Introductions and course logistics Course objectives Platform Architecture Summarize the features and functionality of Workspace ONE UEM Outline the benefits of leveraging Workspace ONE UEM Recognize the core and productivity components that make up the Workspace ONE UEM platform Summarize high availability and disaster recovery for the Workspace ONE solution Administration Navigate and customize the Workspace ONE UEM console Summarize the hierarchical management structure Explain the features and functions of Workspace ONE Hub Services Outline account options and permissions Enterprise Integrations Outline the process of integrating with directory services Explain certificate authentication and practical implementation with Workspace ONE Explain the benefits of integrating an email SMTP service into the Workspace ONE UEM console Describe VMware Dynamic Environment Manager and its architecture Onboarding Outline the prerequisite configurations in the Workspace ONE UEM environment for onboarding devices for management Outline the steps for setting up autodiscovery in the Workspace ONE UEM console Enroll an endpoint through the VMware Workspace ONE© Intelligent Hub app Summarize the platform onboarding options Managing Endpoints Explain the differences between device and user profiles Describe policy management options for Windows and macOS Describe the functions and benefits of using compliance policies Explain the use case for Freestyle Orchestrator Describe the capabilities that sensors and scripts enable. Alternative Management Methods Describe the function and benefits of device staging Configure product provisioning in the Workspace ONE UEM console Understand the benefits of deploying a VMware Workspace ONE© Launcher? configuration to Android devices List the system and device requirements for Linux device management in Workspace ONE UEM Applications Describe the features, benefits, and capabilities of application management in Workspace ONE UEM Understand and configure deployment settings for public, internal, and paid applications in the Workspace ONE UEM console Describe the benefits of using Apple Business Manager content integration Describe the benefits of using server-to-client software distribution List the functions and benefits of VMware Workspace ONE© SDK Device Email List the email clients supported by Workspace ONE UEM Configure an Exchange Active Sync profile in the Workspace ONE UEM console Configure VMware Workspace ONE© Boxer settings Summarize the available email infrastructure integration models and describe their workflows Configure email compliance policies and notifications services Content Sharing Describe the benefits of using Content Gateway Describe the Content Gateway workflows Describe the benefits of integrating content repositories with Workspace ONE UEM Configure a repository in the Workspace ONE UEM console Maintenance Manage endpoints from the Device List view and the Details view. Analyze endpoint deployment and compliance data from the Workspace ONE UEM Monitor page. Workspace ONE Access Summarize the benefits of Workspace ONE Access Outline the core features and functions enabled by Workspace ONE Access Navigate the Workspace ONE Access console Explain the functions of directory integration with Workspace ONE Access Explain the various types of authentication protocols enabled by Workspace ONE Access Integrating Workspace ONE UEM and Workspace ONE Access Explain the rationale for integrating Workspace ONE UEM and Workspace ONE Access Outline the process of connecting Workspace ONE UEM and Workspace ONE Access Examine the workflow of integrations Summarize the key features of an integrated solution Productivity Integrations Identify the functions enabled by VMware Unified Access Gateway? Outline the purpose of the VMware AirWatch© Secure Email Gateway? edge service Explain the features enabled by the VMware Workspace ONE© Tunnel? edge service Summarize the capabilities enabled by the Content Gateway edge service SAML 2.0 Authentication Outline the authentication methods supported by Workspace ONE Access Summarize the main properties of the SAML protocol Summarize the SAML authentication workflow Explain the application SSO authentication workflow with SAML Mobile Single Sign-On Describe the concept of mobile SSO Outline the mobile SSO workflows Intelligence and Automation Summarize the features of Workspace ONE© Intelligence? Outline the benefits of using Workspace ONE Intelligence Additional course details:Notes Delivery by TDSynex, Exit Certified and New Horizons an VMware Authorised Training Centre (VATC) Nexus Humans VMware Workspace ONE: Deploy and Manage [V22.x] training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the VMware Workspace ONE: Deploy and Manage [V22.x] course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.
![VMware Workspace ONE: Deploy and Manage [V22.x]](https://cademy-images-io.b-cdn.net/9dd9d42b-e7b9-4598-8d01-a30d0144ae51/4c81f130-71bf-4635-b7c6-375aff235529/original.png?width=3840)
VMware vSphere: Fast Track [v7.0]
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for System administrators System engineers Overview By the end of the course, you should be able to meet the following objectives: Describe the software-defined data center (SDDC) Explain the vSphere components and their function in the infrastructure Install and configure VMware ESXi⢠hosts Deploy and configure VMware vCenter Server Appliance⢠Use VMware vSphere Client⢠to manage the vCenter Server inventory and the vCenter Server configuration Manage, monitor, back up, and protect vCenter Server Appliance Create virtual networks with vSphere standard switches Describe the storage technologies supported by vSphere Configure virtual storage using iSCSI and NFS storage Create and manage VMware vSphere VMFS datastores Use the vSphere Client to create virtual machines, templates, clones, and snapshots Create a content library and deploy virtual machines from templates in the library Manage virtual machine resource use and manage resource pools Migrate virtual machines with VMware vSphere vMotion and VMware vSphere Storage vMotion Create and manage a vSphere cluster that is enabled with VMware vSphere High Availability and VMware vSphere Distributed Resource Scheduler⢠Create virtual networks with VMware vSphere Distributed Switch⢠and enable distributed switch features Discuss solutions for managing the vSphere life cycle Use VMware vSphere Lifecycle Manager⢠to apply patches and perform upgrades to ESXi hosts and virtual machines Use host profiles to manage ESXi configuration compliance Describe how vSphere storage APIs help storage systems integrate with vSphere Configure and use virtual machine storage policies Discuss the purpose and capabilities of VMware vSphere with Kubernetes and how it fits into the VMware Tanzu⢠portfolio This five-day, intensive course takes you from introductory to advanced VMware vSphere© 7 management skills. Building on the installation and configuration content from our best-selling course, you will also develop advanced skills needed to manage and maintain a highly available and scalable virtual infrastructure. Through a mix of lecture and hands-on labs, you will install, configure and manage vSphere 7. You will explore the features that build a foundation for a truly scalable infrastructure and discuss when and where these features have the greatest effect. This course prepares you to administer a vSphere infrastructure for an organization of any size using vSphere 7, which includes VMware ESXi? 7 and VMware vCenter Server© 7. Course Introduction Introductions and course logistics Course objectives Introduction to vSphere and the Software-Defined Data Center Explain basic virtualization concepts Describe how vSphere fits into the software-defined data center and the cloud infrastructure Explain how vSphere interacts with CPUs, memory, networks, and storage Recognize the user interfaces for accessing the vCenter Server system and ESXi hosts Use VMware Host Client? to access and manage ESXi host Virtual Machines Create and remove a virtual machine Provision a virtual machine with virtual devices Identify the files that make up a virtual machine Explain the importance of VMware Tools vCenter Server Describe the vCenter Server architecture Discuss how ESXi hosts communicate with vCenter Server Deploy and configure vCenter Server Appliance Use the vSphere Client to manage the vCenter Server inventory Add data center, organizational objects, and hosts to vCenter Server Use roles and permissions to enable users to access objects in the vCenter Server inventory Back up vCenter Server Appliance Monitor vCenter Server tasks, events, and appliance health Use vCenter Server High Availability to protect a vCenter Server Appliance Configuring and Managing Virtual Networks Create and manage standard switches Describe the virtual switch connection types Configure virtual switch security, traffic-shaping and load-balancing policies Compare vSphere distributed switches and standard switches Configuring and Managing Virtual Storage Identify storage protocols and storage device types Discuss ESXi hosts using iSCSI, NFS, and Fibre Channel storage Create and manage VMFS and NFS datastores Explain how multipathing works with iSCSI, NFS, and Fibre Channel storage Deploy virtual machines on a VMware vSAN? datastore Virtual Machine Management Use templates and cloning to deploy new virtual machines Modify and manage virtual machines Create a content library and deploy virtual machines from templates in the library Dynamically increase the size of a virtual disk Use customization specification files to customize a new virtual machine Perform vSphere vMotion and vSphere Storage vMotion migrations Create and manage virtual machine snapshots Examine the features and functions of VMware vSphere© Replication? Resource Management and Monitoring Discuss CPU and memory concepts in a virtualized environment Describe what over commitment of a resource means Describe methods for optimizing CPU and memory usage Use various tools to monitor resource use Create and use alarms to report certain conditions or events vSphere Clusters Describe options for making a vSphere environment highly available Explain the vSphere HA architecture Configure and manage a vSphere HA cluster Examine the features and functions of VMware vSphere© Fault Tolerance Configure a vSphere cluster using ESXi Cluster Quickstart Describe the functions of a vSphere DRS cluster Create a vSphere DRS cluster Network Scalability Configure and manage vSphere distributed switches Describe how VMware vSphere© Network I/O Control enhances performance Explain distributed switch features such as port mirroring and NetFlow vSphere Lifecycle Management Describe how VMware vSphere© Lifecycle Manager? works Use vSphere Lifecycle Manager to update ESXi hosts in a cluster Host and Management Scalability Use host profiles to manage ESXi configuration compliance Create and manage resource pools in a cluster Storage Scalability Explain why VMware vSphere© VMFS is a highperformance, scalable file system Explain VMware vSphere© Storage APIs - Array Integration, VMware vSphere© API for Storage Awareness?, and vSphere APIs for I/O Filtering Configure and assign virtual machine storage policies Create VMware vSAN? storage policies Configure VMware vSphere© Storage DRS? and VMware vSphere© Storage I/O Control Discuss vSphere support for NVMe and iSER Introduction to vSphere with Kubernetes Differentiate between containers and virtual machines Identify the parts of a container system Recognize the basic architecture of Kubernetes Describe a basic Kubernetes workflow Describe the purpose of vSphere with Kubernetes and how it fits into the VMware Tanzu portfolio Explain the vSphere with Kubernetes supervisor cluster Describe the Tanzu Kubernetes Grid service Additional course details:Notes Delivery by TDSynex, Exit Certified and New Horizons an VMware Authorised Training Centre (VATC) Nexus Humans VMware vSphere: Fast Track [v7.0] training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the VMware vSphere: Fast Track [v7.0] course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.
![VMware vSphere: Fast Track [v7.0]](https://cademy-images-io.b-cdn.net/9dd9d42b-e7b9-4598-8d01-a30d0144ae51/4c81f130-71bf-4635-b7c6-375aff235529/original.png?width=3840)
Oracle 12c SQL Fundamentals
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for The target audience for this textbook is all Oracle professionals, both business and systems professionals. Among the specific groups for whom this textbook will be helpful are: ? Business and non-IT professionals ? Application designers and database developers ? Business Intelligence (BI) analysts and consumers ? Database administrators ? Web server administrators Overview The first portion of this textbook considers the logical models upon which a relational database is based and the various configurations and environments in which you may work with the Oracle database. The next segment focuses on the actual SQL syntax for writing database queries. You will begin with the simplest of queries and then proceed onto moderately complex query scenarios. Finally, this textbook covers the DDL, DML and transaction control portions of the SQL language that allow one to create, maintain and manipulate application database objects and application data. This textbook takes a unique approach to SQL training in that it incorporates data modeling theory, relational database theory, graphical depictions of theoretical concepts and numerous examples of actual SQL syntax into one learning vehicle. Relational Databases & Data Models About Data Models About the Relational Model The Electronics Data Model About the Relational DBMS Selection & Setup of the Database Interface Considering Available Tools Selecting the Appropriate Tool Oracle Net Database Connections Oracle PAAS Database Connections Setup SQL Developer Setup SQL*Plus Setup Jdeveloper Using the Database Interface About Bind & Substitution Variables Using SQL Developer Using SQL*Plus Introduction to the SQL Language About the SQL Language Characteristics of SQL Introducing SQL Using Select SQL Rules The Select Statement The Select Statement Distinct/Unique Keyword Using Alias Names Restricting Results with the Where Clause About Logical Operators Equality Operator Boolean Operators REGEXP_LIKE() In Operator Sorting Data with the Order By Clause About the Order by Clause Multiple Column Sorts Specify the Sort Sequence About Null Values within Sorts Using Column Aliases Pseudo Columns, Functions & Top-N Queries Rowid Pseudo Column ORA_ROWSCN PSEUDO Column ROWNUM Pseudo Column About the Built-In Functions SYSDATE User & UID SESSIONTIMEZONE Function Using the Dual Table Row Limiting & Top-N Queries FETCH First x Rows Only Clause OFFSET x Rows Clause FETCH?PERCENT Clause The WITH TIES Option Joining Tables About Joins Inner Joins Reflexive Join Non-Key Join Outer Join Using the Set Operators About the Set Operators SQL Set Operator Examples UNION Example INTERECT Example MINUS Example UNION All Summary Functions Using Sub-Queries Finding Data with Sub-Queries Standard Sub-Queries Correlated Sub-Queries The EXISTS Operator Aggregating Data within Groups About Summary Groups Find Groups within the Tables Select Data From the Base Tables Select Groups from the Results Use DDL to Create & Manage Tables Create Table Statement Column Data Types Not Null Default Describe Alter Table Statement Drop Table Statement Table DDL Using SQL Developer Alter User Statement Alter Session Statement NLS_Language NLS_Date Use DML to Manipulate Data The Insert Statement The Delete Statement The Update Statement About Transactions Transaction Rollback Transaction Commit Transaction Savepoint The Set Transaction Statement Set Transaction Read Only Statement Rules Understanding the Data Models The Company Data Model The Electronics Data Model About the SQL-99 Standard SQL-92 & SQL-99 Cross Joins Natural Joins Inner Joins Implicit Inner Join Outer Joins Anti Joins Named Sub-Queries Enhancing Groups with Rollup & Cube Using Rollup The Grouping() Function Using Cube SQL Functions: Character Handling What are the SQL Functions? String Formatting Functions UPPER(), LOWER() Example INITCAP() Example Character Codes Functions CHR((), ASCII() Examples PAD & TRIM Functions RPAD() Example RTRIM() Example TRIM() Example String Manipulation Functions DECODE () Example SUBSTR() Example INSTR() Example TRANSLATE() Example REPLACE() Example String Comparison Functions LEAST() Example Phonetic Search Function SOUNDEX() Example SQL Functions: Numeric Handling About the Numeric Data Functions GREATEST() Example ABS() Example ROUND() Example TRUNC() Example SIGN() Example TO_NUMBER() Example & Data ype Conversions NULL VALUES FUNCTIONS NVL() & NVL2() Function NVL() Example (Character) NVL() Example (Numeric Loss of Data) NVL() Example (Numeric Output) NVL2() Example COALESCE() Function NULLIF() Function SQL Functions: Date Handling Date Formatting Functions TO_CHAR() & TO_DATE() Format Patterns TO_CHAR() Examples TO_DATE() Examples EXTRACT() Example Date Arithmetic Functions MONTHS_BETWEEN() Example ADD_MONTHS() Example LAST_DAY() Example NEXT_DAY() Example TRUNC(), ROUND() Dates Example NEW_ TIME() Example About V$TIMEZONE_NAMES CAST() FUNCTION & TIME ZONES Database Objects: About Database Objects About Database Objects About Schemas Making Object References Database Objects: Relational Views About Relations Views The Create View Statement Why Use Views? Accessing Views with DML Maintaining View Definitions Alter View Drop View DDL Using SQL Developer Database Objects: Indexes About Indexes Create & Drop Index Statements Indexes & Performance Data Dictionary Storage Database Objects: Creating Other Objects About Sequences Referencing NEXTVAL Referencing CURRVAL Within the DEFAULT Clause Alter Sequence & Drop Sequence ALTER SEQUENCE DROP SEQUENCE About Identity Columns CREATE TABLE?GENERATED AS IDENTITY ALTER TABLE?GENERATED AS IDENTITY Start With Limit Value ALTER TABLE...DROP IDENTITY About Synonyms CREATE & DROP SYNONYM Statements CREATE SYNONYM DROP SYNONYM Public Vs Private Synonyms CREATE SCHEMA AUTHORIZATION Database Objects: Object Management Using DDL The RENAME Statement TABLESPACE Placement CREATE TABLE?TABLESPACE The Comment Statement The TRUNCATE TABLE Statement Database Objects: Security About Object Security Grant Object Privileges Revoke Object Privileges Object Privileges & SQL Developer Data Integrity Using Constraints About Constraints NOT NULL Constraint NOT NULL Example CHECK Constraint UNIQUE Constraint PRIMARY KEY Constraint REFERENCES Constraint ON DELETE CASCADE Example ON DELETE SET NULL Example Constraints on Existing Tables Constraints & SQL Developer Managing Constraint Definitions RENAMING & DROPPING Constraints ENABLING & DISABLING Constraints DEFERRED Constraint Enforcement SET CONSTRAINTS Handling Constraint Exceptions Constraints with Views DATA Dictionary Storage The Data Dictionary Structure More About the Data Dictionary OBJECT-SPECIFIC Dictionary Views USER_UPDATABLE_COLUMNS The Dictionary Structure METADATA & SQL Developer Additional course details: Nexus Humans Oracle 12c SQL Fundamentals training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Oracle 12c SQL Fundamentals course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

VMware Horizon Cloud Service Next Gen on Microsoft Azure: Deploy and Manage
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for Horizon Cloud Service on Microsoft Azure administrators, system integrators, account managers, solutions architects, solutions engineers, sales engineers, and consultants. Overview By the end of the course, you should be able to meet the following objectives: Describe the architecture of Horizon Cloud Service on Microsoft Azure Discuss the initial Microsoft Azure configurations required for the Horizon Cloud Service on Microsoft Azure deployment Discuss Horizon Cloud Service on Microsoft Azure networking concepts Discuss Horizon Cloud Service on Microsoft Azure AD requirements and integration best practices Discuss the integration of Workspace ONE Access with Horizon Cloud Service on Microsoft Azure Discuss the requirements for deploying Horizon Cloud Service on Microsoft Azure Demonstrate how to deploy or upgrade Horizon Cloud Service on Microsoft Azure Identify the Horizon Cloud Service console controls that are available to administrators Identify Horizon Cloud upgrade features and benefits List the steps and considerations to take when setting up a primary VM to be used as an assignable image List the steps to install the user software on the primary VM Describe pools and pool groups Explain the creation process and configuration options for single-session and multisession pools and pool groups Create single-session and multisession assignments and entitlements Explain power management options in the multisession pool groups Manage assignable images on Horizon Cloud Service on Microsoft Azure Identify how to access desktops and application from Horizon Cloud Service on Microsoft Azure Describe the integration of VMware Dynamic Environment Manager with Horizon Cloud Service on Microsoft Azure Manage user personalization and application configurations using the VMware Dynamic Environment Manager management console and application profiler Discuss the usage of App Volumes for Horizon Cloud Service on Microsoft Azure Interpret scalability considerations for Horizon Cloud Service on Microsoft Azure Apply troubleshooting techniques relevant to Horizon Cloud Service and Microsoft Azure Summarize the analytics and monitoring capabilities in Horizon Cloud Service on Microsoft Azure This five-day, hands-on training provides you with the knowledge, skills, and abilities to successfully deploy and manage VMware Horizon© Cloud Service? on Microsoft Azure. This training also teaches you how to use the VMware Horizon Cloud administration console and Microsoft Azure portal. Through a combination of hands-on labs and interactive lectures, you learn how to import and manage images for single and multisession assignments. You also learn how to configure and use the Universal Broker function, VMware App Volumes?, VMware Workspace ONE© Access?, and VMware Dynamic Environment Manager? in the Horizon Cloud Service on Microsoft Azure deployment. Course Introduction Introduction and course logistics Course objectives Introduction to Horizon Cloud Service on Microsoft Azure Discuss the features and benefits of Horizon Cloud Service on Microsoft Azure Identify the available Horizon Cloud and Microsoft licensing options Identify the system architecture components of Horizon Cloud Service on Microsoft Azure Explain how VMware Dynamic Environment Manager is used in Horizon Cloud profile management Describe Horizon Cloud application management using App Volumes Identify the Microsoft Azure configuration prerequisites for a Horizon Cloud integration Identify the main Microsoft Azure components required for a Horizon Cloud deployment Review the virtual machines supported in Horizon Cloud Service on Microsoft Azure Microsoft Azure Networking Requirements Discuss Horizon Cloud connectivity considerations and tasks Explain the networking concepts for Horizon Cloud Service on Microsoft Azure Identify the ports required for local connections, remote connections, and endpoint OS firewall rules Identity Management Explain computer identity type and user identity type Discuss the best practices for Horizon Cloud Service on Microsoft Azure AD integrations Determine the requirements for Horizon Cloud Service on Microsoft Azure AD Describe the benefits of integrating Horizon Cloud with Workspace ONE Access Explain how a user obtains access to an entitled virtual desktop or application from the VMware Workspace ONE© Intelligent Hub catalog Discuss the importance of binding directory with Workspace ONE Access and setting up custom user attribute synchronization Discuss the importance of configuring the Remote App Access client in Workspace ONE Access Demonstrate how to access an entitled Horizon virtual desktop or application in the Workspace ONE Intelligent Hub catalog Deployment and Upgrades Explain the steps and requirements for deploying Horizon Cloud Service on Microsoft Azure Describe the features and benefits of Horizon Edge Describe the differences between internal and external gateways Outline the Horizon Universal Console controls available for administrators Identify the features and benefits of the Horizon Cloud upgrades Creating Images Outline the process and configuration choices for setting up primary VMs Identify the configuration choices for importing primary VMs List the steps to install the user software on the primary VM Explain how to convert a configured primary VM to an assignable image Describe pools and pool groups List the steps for configuring an image to a pool List the steps for configuring an image to a pool group Pool Groups Compare dedicated assignments to floating assignments Outline the steps for creating single-session and multisession assignment Explain the entitlement of pool groups Outline the creation process and configuration options for multisession pools and pool groups Explain the power management selections in the multisession pool groups Compare the rolling maintenance and loadbalancing options Identify the actions related to the multisession groups page Identify the actions to add and assign applications to a user or group Outline the prerequisites for entitling a multisession assignment Access Desktops and Applications Identify the different versions of Horizon Client Describe how to access desktops and remote applications with Horizon Client Describe how to access desktops and remote applications with a browser Compare the remote display protocols that are available for Horizon Cloud Describe the Blast Extreme display protocol codecs List the ideal applications for each Blast Extreme codec Describe the Blast Extreme policy configurations Managing Images Describe images Explain how to manage images VMware Dynamic Environment Manager on Horizon Cloud Service on Microsoft Azure Identify the functional areas of VMware Dynamic Environment Manager and their benefits Explain how to use the VMware Dynamic Environment Manager console and application profiler to manage user personalization and application configurations App Volumes for Horizon Cloud Service on Microsoft Azure Explain how App Volumes works with Horizon Cloud Service on Microsoft Azure Identify the features and benefits of App Volumes in Horizon Cloud Service on Microsoft Azure Identify the interface elements of App Volumes in Horizon Cloud Service on Microsoft Azure Demonstrate how to configure App Volumes in Horizon Cloud Service on Microsoft Azure Scalability Considerations Recognize the scalability settings for Horizon Cloud Service on Microsoft Azure Troubleshooting Horizon Cloud Service on Microsoft Azure Explain the troubleshooting basics for Horizon Cloud Service on Microsoft Azure Identify the analytics and monitoring capabilities of Horizon Cloud Service on Microsoft Azure Explain the troubleshooting basics for Horizon Cloud Additional course details:Notes Delivery by TDSynex, Exit Certified and New Horizons an VMware Authorised Training Centre (VATC) Nexus Humans VMware Horizon Cloud Service Next Gen on Microsoft Azure: Deploy and Manage training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the VMware Horizon Cloud Service Next Gen on Microsoft Azure: Deploy and Manage course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

VMware Workspace ONE: Deploy and Manage plus UEM Troubleshooting Fast Track [V22.x]
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for Workspace ONE UEM operators and administrators, account managers, solutions architects, solutions engineers, sales engineers, and consultants. Overview By the end of the course, you should be able to meet the following objectives: Explain and apply the fundamental techniques for launching and maintaining an intelligence-driven, multiplatform endpoint management solution with Workspace ONE UEM Outline the components of Workspace ONE UEM Explain the general features and functionality enabled with Workspace ONE UEM Summarize basic Workspace ONE administrative functions Explain and deploy common Workspace ONE integrations Securely deploy configurations to Workspace ONE UEM managed devices Onboard device endpoints into Workspace ONE UEM Summarize alternative management methodologies for rugged devices Discuss strategies to maintain environment and device fleet health Configure and deploy applications to Workspace ONE UEM managed devices Analyze Workspace ONE UEM deployments Enable email access on devices Integrate Workspace ONE UEM with content repositories and corporate file shares Explain the general features and functionality that Workspace ONE Access enables Demonstrate how to integrate Workspace ONE UEM with Workspace ONE Access Summarize and implement Workspace ONE productivity services into the digital workspace environment Explain the methods of enabling mobile single sign-on for endpoints managed in the digital workspace Configure Workspace ONE Access to support SAML 2.0 for federated authentication across the workforce Summarize basic troubleshooting methodologies Outline common troubleshooting techniques in the Workspace ONE UEM console Outline common troubleshooting techniques when integrating enterprise solutions in the Workspace ONE UEM console Summarize common troubleshooting strategies for Workspace ONE UEM managed devices Outline common application management troubleshooting techniques in the Workspace ONE UEM console Summarize common troubleshooting techniques for email management in the Workspace ONE UEM console Explain common troubleshooting approaches for the VMware Unified Access Gateway⢠platform and individual edge services Outline useful troubleshooting tools, such as the Self-Service Portal and VMware Workspace ONE Assist⢠In this extended five-day course, you learn how to apply the fundamental techniques for launching and maintaining an intelligence-driven, multiplatform endpoint management solution with VMware Workspace ONE© UEM. Through a combination of hands-on labs, simulations, and interactive lectures, you will configure and manage the endpoint life cycle. After the course, you will have the foundational knowledge necessary to implement Workspace ONE UEM effectively.In addition, you learn how to apply the fundamental techniques for integrating VMware Workspace ONE© Access? with Workspace ONE UEM to distribute business-critical applications securely from any device and configure access management controls. You will learn how Workspace ONE uses various authentication methods and protocols to determine user access permissions and enable single sign-on, and you will leave with an understanding of the fundamental principles of identity and access management.Finally, you learn to investigate, analyze, and determine issues that might occur with the different components of Workspace ONE UEM. Troubleshooting is the backbone of service maintenance and management. By understanding how to effectively troubleshoot product issues, administrators can understand how product services communicate and function, in turn optimizing service and software health management. Course Introduction Introductions and course logistics Course objectives Online resources and references Platform Architecture Summarize the features and functionality of Workspace ONE UEM Outline the benefits of leveraging Workspace ONE UEM Recognize the core and productivity components that make up the Workspace ONE UEM platform Summarize high availability and disaster recovery for Workspace ONE Solution Administration Navigate and customize the Workspace ONE UEM console Summarize the hierarchical management structure Explain the features and functions of Workspace ONE Hub Services Outline account options and permissions Enterprise Integrations Outline the process and needs to integrate with directory services Explain certificate authentication and practical implementation with Workspace ONE Explain the benefits of integrating an email SMTP service into the Workspace ONE UEM console Describe VMware Dynamic Environment Manager? and its architecture Onboarding Outline the prerequisite configurations in the Workspace ONE UEM environment for onboarding devices for management Outline the steps for setting up autodiscovery in the Workspace ONE UEM console Enroll an endpoint through the VMware Workspace ONE© Intelligent Hub app Summarize platform onboarding options Managing Endpoints Explain the differences between device and user profiles Describe policy management options for Windows and macOS Describe the functions and benefits of using compliance policies Explain the use cases for Freestyle Orchestrator Describe the capabilities that sensors and scripts enable Alternative Management Methods Describe the function and benefits of device staging Configure product provisioning in the Workspace ONE UEM console Understand the benefits of deploying a VMware Workspace ONE© Launcher? configuration to Android devices List the system and device requirements for Linux device management in Workspace ONE UEM Applications Describe the features, benefits, and capabilities of application management in Workspace ONE UEM Understand and configure deployment settings for public, internal, and paid applications in the Workspace ONE UEM console Describe the benefits of using Apple Business Manager content integration Describe the benefits of using server-to-client software distribution List the functions and benefits of VMware Workspace ONE© SDK Device Email List the email clients supported by Workspace ONE UEM Configure an Exchange Active Sync profile in the Workspace ONE UEM console Configure VMware Workspace ONE© Boxer settings Summarize the available email infrastructure integration models and describe their workflows Configure email compliance policies and notifications services Content Sharing Describe the benefits of using Content Gateway and the Content Gateway workflows Describe the benefits of integrating content repositories with Workspace ONE UEM Configure a repository in the Workspace ONE UEM console Maintenance Manage endpoints from the Device List View and the Device Details View pages Analyze endpoint deployment and compliance data from the Monitor Overview page Workspace ONE Access Summarize the benefits of Workspace ONE Access Outline the core features and functions that Workspace ONE Access enables Navigate the Workspace ONE Access console Explain the functions of directory integration with Workspace ONE Access Explain the various types of authentication protocols enabled by Workspace ONE Access Integrating Workspace ONE UEM and Workspace ONE Access Explain the rationale for integrating Workspace ONE UEM and Workspace ONE Access Outline the process of connecting Workspace ONE UEM and Workspace ONE Access Explain the integrations workflow Summarize the key features of an integrated solution Productivity Integrations Identify the functions enabled by Unified Access Gateway Outline the purpose of the VMware AirWatch© Secure Email Gateway? edge service Explain the features enabled by the VMware Workspace ONE© Tunnel? edge service Summarize the capabilities enabled by the Content Gateway edge service SAML 2.0 Authentication Outline authentication methods supported by Workspace ONE Access Summarize the main properties of the SAML protocol Summarize the SAML authentication workflow Explain the application single sign-on authentication workflow with SAML Mobile Single Sign-On Describe the concept of mobile single sign-on Outline mobile single sign-on workflows Intelligence and Automation Summarize the features of VMware Workspace ONE© Intelligence? Outline the benefits of using Workspace ONE Intelligence Fundamentals of Troubleshooting Workspace ONE UEM Outline software troubleshooting logic and support methods Summarize the main process flows for the Workspace ONE UEM components Explain the importance of Workspace ONE UEM process flows for troubleshooting Identify different Workspace ONE UEM log files Workspace ONE UEM Console Troubleshooting Outline the best practices for troubleshooting Workspace ONE UEM console issues Identify common issues related to group management and assignment Outline common issues related to Workspace ONE UEM console roles and system settings Understand how analytic events can be used to identity platform errors Summarize the steps for collecting and analyzing Workspace ONE UEM console logs Integration Troubleshooting Outline the common enterprise integrations in Workspace ONE UEM Outline common troubleshooting techniques for the VMware AirWatch© Cloud Connector? Troubleshoot issues related to Directory Services integration Identify directory user and groups synchronization issues Troubleshoot issues related to certificate authority integration Explain Workspace ONE Access integration and Workspace ONE Intelligent Hub troubleshooting techniques Endpoint Troubleshooting Compare the endpoint connection topologies in Workspace ONE UEM Outline useful tools and resources for endpoint troubleshooting Summarize the best practices for device enrollment troubleshooting Explain device connectivity troubleshooting techniques Understand how to identify and resolve profile-related issues Identify common compliance policy issues and potential root causes Application Troubleshooting Explain the different scoping questions for troubleshooting applications Review application management configurations Summarize the general tools and resources for application troubleshooting Describe the general logic of troubleshooting public applications Understand internal application issues and potential causes Explain purchased application troubleshooting techniques Unified Access Gateway And Edge Services Troubleshooting Review Unified Access Gateway architecture and edge service workflows Understand Unified Access Gateway general configurations Explain how to utilize Unified Access Gateway related troubleshooting tools and resources Identify
![VMware Workspace ONE: Deploy and Manage plus UEM Troubleshooting Fast Track [V22.x]](https://cademy-images-io.b-cdn.net/9dd9d42b-e7b9-4598-8d01-a30d0144ae51/4c81f130-71bf-4635-b7c6-375aff235529/original.png?width=3840)
VMware Horizon 8: Deploy and Manage plus App Volumes Fast Track
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for Operators, administrators, and architects for VMware Horizon should enroll in this course. These individuals are responsible for the creation, maintenance, or delivery of remote and virtual desktop services. Additional duties can include the implementation, support, and administration of an organization's end-user computing infrastructure. Overview By the end of the course, you should be able to meet the following objectives: Recognize the features and benefits of VMware Horizon Use VMware vSphere to create VMs to be used as desktops for VMware Horizon Create and optimize Windows VMs to create VMware Horizon desktops Install and configure Horizon Agent on Horizon desktop Configure and manage the VMware Horizon Client⢠systems and connect the client to a VMware Horizon desktop Configure, manage, and entitle desktop pools of full VMs Configure, manage, and entitle pools of instant-clone desktops Create and use Remote Desktop Services (RDS) desktops and application pools Monitor the VMware Horizon environment using Horizon Console Dashboard and Horizon Help Desk Tool Identify Horizon Connection Server installation, architecture, and requirements. Describe the authentication and certification options for a VMware Horizon environment Recognize the integration process and benefits of VMware Workspace ONE Access⢠and Horizon 8 Discuss performance and scalability options available in Horizon 8 Describe different security options for the Horizon environment Describe the features and functions of App Volumes and Dynamic Environment Manager Demonstrate the architectures of App Volumes and Dynamic Environment Manager Install and configure App Volumes Create and deploy Application Packages and writable volumes Install and configure Dynamic Environment Manager Manage application configurations, user environment settings, and personalization settings This five-day accelerated, hands-on training course is a blend of VMware Horizon© 8: Skills for Virtual Desktop Management, VMware Horizon 8: Infrastructure Administration, and VMware App Volumes?, and VMware Dynamic Environment Manager?. Eight days of content are taught in five-days of extending learning.This training collection gives you the hands-on skills to deliver virtual desktops and applications through a single virtual desktop infrastructure platform. You build on your skills in configuring and managing VMware Horizon 8 through a combination of lecture and hands-on labs. You learn how to configure and deploy pools of virtual machines and how to provide a customized desktop environment to end-users.You learn how to install and configure a virtual desktop infrastructure platform. You learn how to install and configure VMware Horizon© Connection Server? and VMware Unified Access Gateway?. You also learn how to configure a load balancer for use with Horizon and how to establish Cloud Pod Architecture.Additionally, you learn how to use App Volumes to deliver applications and data to desktops and users in seconds and at scale. You gain skills in managing application life cycles from installation to update and replacement. You also learn how to use Dynamic Environment Manager to provide personalization and dynamic policy configuration across virtual, physical, and cloud-based environments to simplify end-user profile management. Course Introduction Introductions and course logistics Course objectives Introduction to VMware Horizon Recognize the features and benefits of Horizon Describe the conceptual and logical architecture of VMware Horizon Introduction to Use Case Define a use case for your virtual desktop and application infrastructure Convert customer requirements to use-case attributes vSphere for Horizon 8 Explain basic virtualization concepts Use vSphere Client to access your vCenter Server system and VMware ESXi? hosts Create, provision, and remove a virtual machine VMware Horizon Desktops Create a Windows and a Linux virtual machine using vSphere Optimize and prepare Windows and Linux virtual machines to set up VMware Horizon desktop VMs VMware Horizon Agents Outline the configuration choices when installing Horizon Agent on Windows and Linux virtual machines Create a gold master for Windows Horizon desktops VMware Horizon Pools Identify the steps to set up a template for desktop pool deployment List the steps to add desktops to the Horizon Connection Server inventory Compare dedicated-assignment and floating-assignment pools Outline the steps to create an automated pool Define user entitlement Explain the hierarchy of global, pool-level, and user-level policies VMware Horizon Client Options Describe the different clients and their benefits Access the VMware Horizon desktop using various VMware Horizon clients and HTML Configure integrated printing, USB redirection, and the shared folders option Configure session collaboration and media optimization for Microsoft Teams Creating and Managing Instant-Clone Desktop Pools List the advantages of instant clones Explain the provisioning technology used for instant-clone desktop pools Set up an automated pool of instant clones Push updated images to instant-clone desktop pools Creating RDS Desktop and Application Pools Explain the difference between an RDS desktop pool and an automated pool Compare and contrast an RDS session host pool, a farm, and an application pool Create an RDS desktop pool and an application pool Access RDS desktops and application from Horizon Client Use the instant clone technology to automate the build-out of RDSH farms Configure load-balancing for RDSHs on a farm Monitoring VMware Horizon Monitor the status of the VMware Horizon components using the Horizon Administrator console dashboard Monitor desktop sessions using the HelpDesk tool Horizon Connection Server Recognize VMware Horizon reference architecture Identify the Horizon Connection Server supported features Identify the recommended system requirements for Horizon Connection Server Configure the Horizon event database Outline the steps for the initial configuration of Horizon Connection Server Discuss the ADAM database as a critical component of the Horizon Connection Server installation VMware Horizon Authentication and Certificates Compare the authentication options that Horizon Connection Server supports Describe the Smartcard authentication options that Horizon Connection Server supports Outline the steps to create a VMware Horizon administrator and custom roles Describe the roles available in a VMware Horizon environment Explain the role that certificates play for Horizon Connection Server Install and configure certificates for Horizon Connection Server Install and configure True SSO in a VMware Horizon environment Workspace ONE Access and Virtual Application Management Recognize the features and benefits of Workspace ONE Access Recognize the Workspace ONE Access console features Explain identity management in Workspace ONE Access Explain access management in Workspace ONE Access Describe the Workspace ONE Access directory integration Describe the Workspace ONE Access directory integration Deploy virtual applications with Workspace services VMware Horizon Performance and Scalability Describe the purpose of a replica connection server Explain how multiple Horizon Connection Server instances in a pod maintain synchronization Describe the 3D rendering options available in VMware Horizon 8 List the steps to configure graphics cards for use in a VMware Horizon environment Configure a load balancer for use in a VMware Horizon environment Explain Horizon Cloud Pod Architecture LDAP replication and VIPA Explain Horizon Cloud Pod Architecture scalability options Managing VMware Horizon Security Explain concepts relevant to secure VMware Horizon connections Describe how to restrict VMware Horizon connections. Discuss the benefits of using Unified Access Gateway List the two-factor authentication options that are supported by Unified Access Gateway List Unified Access Gateway firewall rules Describe the situation in which you might deploy Unified Access Gateway instances with one, two, or three network interfaces Overview of Application and Profile Management Profile Management Application Management Overview of App Volumes App Volumes components App Volumes Installation Overview Requirements Installing and configuring App Volumes Manager Installing the App Volumes agent Working with Application Packages Packaging Applications Maintaining Applications Working with Writable Volumes Default writable volume templates Writable volume policies at creation Updating and rescanning writable volumes Working with AppStacks Enabling AppStacks Creating and provisioning AppStacks Assigning and updating AppStacks Overriding precedence in AppStacks Overview of Dynamic Environment Manager Features and benefits VMware Dynamic Environment Manager terminology User environment settings and scope User profile scenarios Install VMware Dynamic Environment Manager Infrastructure and system requirements VMware Dynamic Environment Manager Agent (FlexEngine) requirements Group Policy configuration Management Console configuration Management Console User Interface Personalize User Profile User environment configuration Application Configuration Management Predefined and user-customized application settings Using Application Profiler Using the Self-Support Tool Using the Helpdesk Support Tool VMware Horizon Smart Policies Scope of VMware Horizon Smart Policies Configure VMware Horizon Smart Policies settings Define Smart Policies conditions Additional course details:Notes Delivery by TDSynex, Exit Certified and New Horizons an VMware Authorised Training Centre (VATC) Nexus Humans VMware Horizon 8: Deploy and Manage plus App Volumes Fast Track training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the VMware Horizon 8: Deploy and Manage plus App Volumes Fast Track course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Tableau Desktop Training - Analyst
By Tableau Training Uk
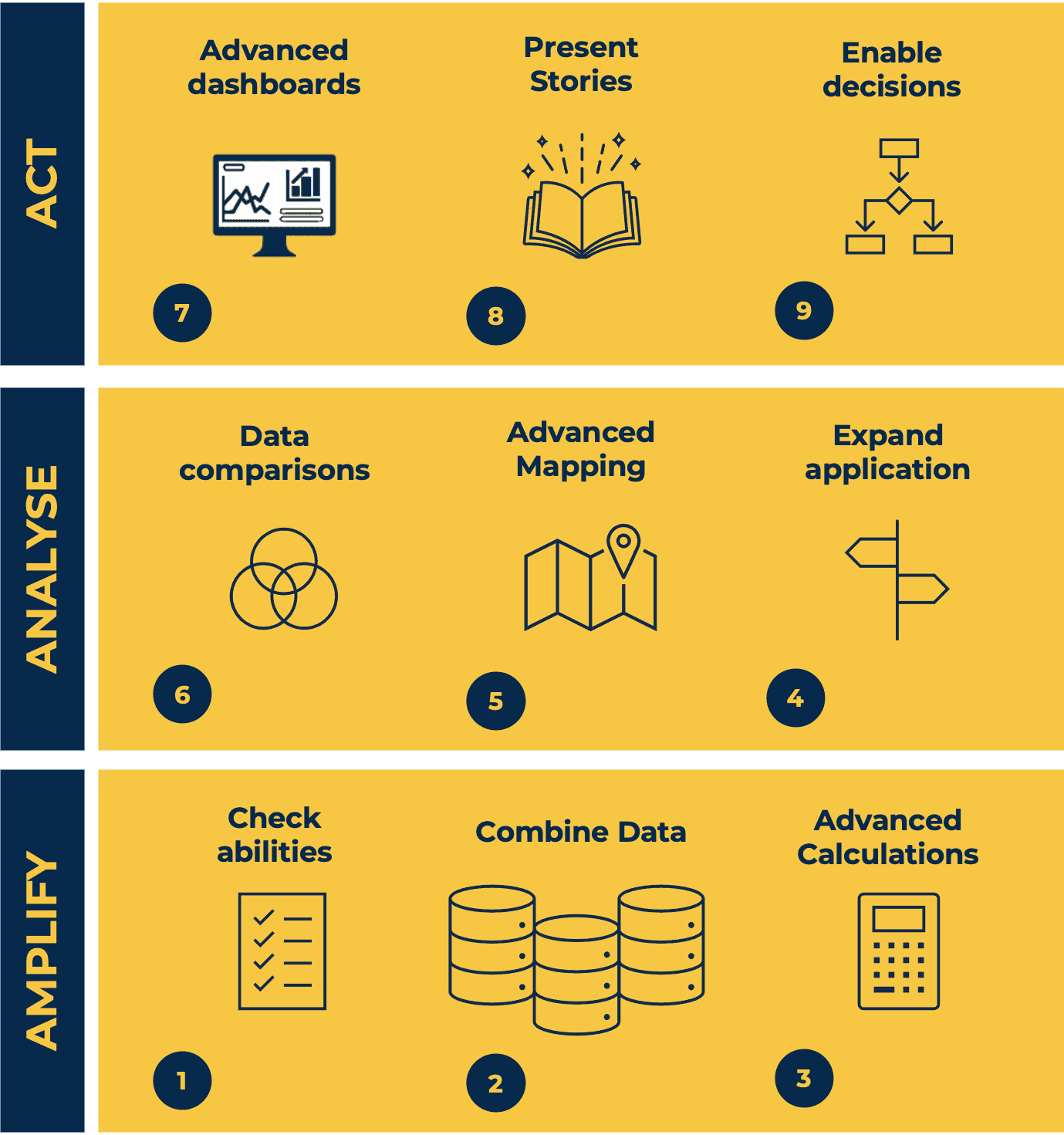
This Tableau Desktop Training intermediate course is designed for the professional who has a solid foundation with Tableau and is looking to take it to the next level. For Private options, online or in-person, please send us details of your requirements: This Tableau Desktop training intermediate course is designed for the professional who has a solid foundation with Tableau and is looking to take it to the next level. Attendees should have a good understanding of the fundamental concepts of building Tableau worksheets and dashboards typically achieved from having attended our Tableau Desktop Foundation Course. At the end of this course you will be able to communicate insights more effectively, enabling your organisation to make better decisions, quickly. The Tableau Desktop Analyst training course is aimed at people who are used to working with MS Excel or other Business Intelligence tools and who have preferably been using Tableau already for basic reporting. The course is split into 3 phases and 9 modules: Phase 1: AMPLIFY MODULE 1: CHECK ABILITIES Revision – What I Should Know What is possibleHow does Tableau deal with dataKnow your way aroundHow do we format chartsHow Tableau deals with datesCharts that compare multiple measuresCreating Tables MODULE 2: COMBINE DATA Relationships Joining Tables – Join Types, Joining tables within the same database, cross database joins, join calculations Blending – How to create a blend with common fields, Custom defined Field relationships and mismatched element names, Calculated fields in blended data sources Unions – Manual Unions and mismatched columns, Wildcard unions Data Extracts – Creating & Editing Data extracts MODULE 3: ADVANCED CALCULATIONS Row Level v Aggregations Aggregating dimensions in calculations Changing the Level of Detail (LOD) of calculations – What, Why, How Adding Table Calculations Phase 2: ANALYSE MODULE 4: EXPAND APPLICATION Making things dynamic with parameters Sets Trend Lines How do we format charts Forecasting MODULE 5: ADVANCED MAPPING Using your own images for spatial analysis Mapping with Spatial files MODULE 6: DATA COMPARISONS Advanced Charts Bar in Bar charts Bullet graphs Creating Bins and Histograms Creating a Box & Whisker plot Phase 3: ACT MODULE 7: ADVANCED DASHBOARDS Using the dashboard interface and Device layout Dashboard Actions and Viz In tooltips Horizontal & Vertical containers Navigate between dashboards MODULE 8: PRESENT STORIES Telling data driven stories MODULE 9: ENABLE DECISIONS What is Tableau Server Publishing & Permissions How can your users engage with content This training course includes over 25 hands-on exercises and quizzes to help participants “learn by doing” and to assist group discussions around real-life use cases. Each attendee receives a login to our extensive training portal which covers the theory, practical applications and use cases, exercises, solutions and quizzes in both written and video format. Students must bring their own laptop with an active version of Tableau Desktop 2018.2 (or later) pre-installed. What People Are Saying About This Course “Course was fantastic, and completely relevant to the work I am doing with Tableau. I particularly liked Steve’s method of teaching and how he applied the course material to ‘real-life’ use-cases.”Richard W., Dashboard Consulting Ltd “This course was extremely useful and excellent value. It helped me formalise my learning and I have taken a lot of useful tips away which will help me in everyday work.” Lauren M., Baillie Gifford “I would definitely recommend taking this course if you have a working knowledge of Tableau. Even the little tips Steve explains will make using Tableau a lot easier. Looking forward to putting what I’ve learned into practice.”Aron F., Grove & Dean “Steve is an excellent teacher and has a vast knowledge of Tableau. I learned a huge amount over the two days that I can immediately apply at work.”John B., Mporium “Steve not only provided a comprehensive explanation of the content of the course, but also allowed time for discussing particular business issues that participants may be facing. That was really useful as part of my learning process.”Juan C., Financial Conduct Authority “Course was fantastic, and completely relevant to the work I am doing with Tableau. I particularly liked Steve’s method of teaching and how he applied the course material to ‘real-life’ use-cases.”Richard W., Dashboard Consulting Ltd “This course was extremely useful and excellent value. It helped me formalise my learning and I have taken a lot of useful tips away which will help me in everyday work.” Lauren M., Baillie Gifford “I would definitely recommend taking this course if you have a working knowledge of Tableau. Even the little tips Steve explains will make using Tableau a lot easier. Looking forward to putting what I’ve learned into practice.”Aron F., Grove & Dean “Steve is an excellent teacher and has a vast knowledge of Tableau. I learned a huge amount over the two days that I can immediately apply at work.”John B., Mporium
Sales closing and price negotiation skills (In-House)
By The In House Training Company
Successfully closing a sale and negotiating the best outcome for the business is a key skill for all salespeople, and often an area that is overlooked. Investing in this skill will have a positive impact on interactions with customers, both new and existing, and lead to improved sales performance. Whilst understanding how to reach a conclusion with a customer faster means increased efficiency and more time to invest in sourcing new business. We have developed this programme to be practical, fun and interactive. Participants will learn proven techniques for influencing, persuading and negotiating with clients, gain increased confidence and clarity when reviewing contract terms and prices, and understand how to structure and manage sales negotiation and contract review meetings. This course will help participants: Learn a structured and proven approach to the negotiation of contract terms Apply the key principles of negotiation, playing the person and the problem Create a contract negotiation strategy - from opening to close Recognize and put to use proven negotiation tactics and techniques Learn how to embrace conflict positively - to 'say no, then negotiate' Plan and prepare for any commercial negotiation conversations Understand the stages of negotiation and how to move through them 1 Closing and negotiating from a position of personal power The eight steps of a sales or commercial negotiation Ten ways to resist price pressure How to draw on sources of power when you have less authority The six principles of influence and persuasion and how to use them 2 Effective negotiation - planning and theory How to plan and structure your negotiation for a successful and quick conclusion Influence: knowing how to 'push or pull' to win an argument Achieving a BATNA - a range of practical skills and techniques Case study: planning for a client negotiation around contract or price issues 3 Effective closing and negotiation - practice and reality Higher-level questioning techniques to investigate and solve problems Listening to lead - active listening and structuring your conversation The most common 'unforced' negotiation mistakes and errors Case study: setting objectives, sources of value, trading concessions 4 Sales negotiation tactics and playing the game How high - how hard - how soon; why now How to identify hidden or perceived currencies and values How to use these to establish a higher base price Negotiation best-practice checklist and summary

Trade secrets - the business perspective (In-House)
By The In House Training Company
Trade barriers are going up across the globe. And cybercrime is on the increase. The link between the two? The value of trade secrets. As countries become increasingly protectionist as regards international trade, so their IP law has been changing, with the result that companies that previously would have sought protection through patents are opting to go down the trade secret route instead. But is this a high-risk strategy? Technology is changing and this is having an impact on forms of commercial co-operation. Collaborative or open forms of innovation by their very nature involve the sharing of intellectual property (IP), and in many instances this IP is in the form of valuable confidential business information (ie, trade secrets). Little surprise, then, that trade secrets disputes have increased accordingly. At the same time, the changes in technology make trade secrets more vulnerable to attack, misappropriation, theft. So just how effective are the legal protections for trade secrets? How can organisations safeguard the value in their IP (increasingly, the single biggest line in their balance sheets)? This programme is designed to help you address these issues. Note: this is an indicative agenda, to be used as a starting point for a conversation between client and consultant, depending on the organisation's specific situation and requirements. This session is designed to give you a deeper understanding of: Emerging trends in trade secrets protection and exploitation The current situation in key jurisdictions Recent case law How leading companies are responding The importance of trade secret metadata Different external stakeholders and their interests Key steps for effective protection of trade secrets Note: this is an indicative agenda, to be used as a starting point for a conversation between client and consultant, depending on the organisation's specific situation and requirements. 1 What are trade secrets? Definitions Examples Comparison with other forms of IP (patents, confidential information, know-how, copyright) 2 Current trends The various changes taking place affecting trade secrets - legal changes, trade wars, cybercrime, technology, commercial practice The current position in the UK, Europe, USA, China, Japan, Russia Corporate best practice 3 Trade secret disputes - how to avoid them Trade secret policies, processes and systems Administrative, legal and technical protection mechanisms The role of employees The sharing of trade secrets with others 4 Trade secret disputes - how to manage them Causes Anatomy of a trade secret court case 'Reasonable particularity' 5 Related issues Insurance Tax authorities and investigations Investor relations 6 Trade secret asset management roadmap Maturity ladder First steps Pilot projects

Business networking skills (In-House)
By The In House Training Company
This workshop will provide participants with the insight and skills to be more effective business networkers, face-to-face and online. The approach taken is to build on the strengths people already have and their successes. It is easier to develop what you already have than to try and develop skills that do not come easily. Being yourself is the most effective tool for business networking and building relationships. This course will help those attending: Appreciate the importance of networking, and different forms of networking Understand the dynamics of communication that are specific to networking Become more confident and assured when 'working' a room Improve their influencing skills, especially with people who are experts and in positions of authority 'Sell' themselves and promote their company Identify and manage their profiles using online social networking sites Use effective follow-up to maintain active contacts and connections Select the correct networking groups, clubs and events Create their own personal network 1 The importance, and different types, of networking Personal objectives and introductions Test networking session Examples of the importance, purpose and format of various types of networking, and benefits you can expect 2 How to work a room - preparation and strategy Three things to know before you attend any event Non-verbal communication and art of rapport Breaking the ice - worked examples with practical demonstration 3 Communication dynamics in networking - the power of the listening networker Why it is better to listen than talk Effective questioning and active listening Creating a natural and engaging conversation, 1-2-1 and in a larger group 4 Assumptions when networking How to use the 'instant judgement' of others to your advantage What assumptions are you making? How to keep an open mind 5 Business networking etiquette Meeting and greeting at a business networking event - approaching complete strangers and introducing yourself Socialising: joining and leaving groups easily Making a good first impression in 30 seconds The use of status when networking 6 Making connections Asking for cards, contact details and referrals Gaining a follow-up commitment Some tips and tricks 7 Business networking rehearsals Practice sessions 8 Personal business networking online Overview of different types of networking sites - there is a lot more out there than just Facebook! Examples of creating an effective profile Using social networking effectively - case studies and application 'Advanced' applications - blogs, articles, twitter, feeds, etc. Online demonstration and examples 9 Building relationships - follow-up and follow-through Maintaining a good database Developing a contact strategy with different types and levels of contact How to analyse your contact base
