- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
Tips and Tricks for Teaching Listening and Reading Skills (25 Hours)
5.0(5)By TEFL Wonderland - Brilliant Minds
Tips and Tricks for Teaching Listening and Reading Skills (25 Hours)

CertNexus Certified Cyber Secure Coder (CSC-210)
By Nexus Human
Duration 3 Days 18 CPD hours This course is intended for This course is designed for software developers, testers, and architects who design and develop software in various programming languages and platforms, including desktop, web, cloud, and mobile, and who want to improve their ability to deliver software that is of high quality, particularly regarding security and privacy. This course is also designed for students who are seeking the CertNexus Cyber Secure Coder (CSC) Exam CSC-210 certification Overview In this course, you will employ best practices in software development to develop secure software.You will: Identify the need for security in your software projects. Eliminate vulnerabilities within software. Use a Security by Design approach to design a secure architecture for your software. Implement common protections to protect users and data. Apply various testing methods to find and correct security defects in your software. Maintain deployed software to ensure ongoing security... The stakes for software security are very high, and yet many development teams deal with software security only after the code has been developed and the software is being prepared for delivery. As with any aspect of software quality, to ensure successful implementation, security and privacy issues should be managed throughout the entire software development lifecycle. This course presents an approach for dealing with security and privacy throughout the entire software development lifecycle. You will learn about vulnerabilities that undermine security, and how to identify and remediate them in your own projects. You will learn general strategies for dealing with security defects and misconfiguration, how to design software to deal with the human element in security, and how to incorporate security into all phases of development. Identifying the Need for Security in Your Software Projects Identify Security Requirements and Expectations Identify Factors That Undermine Software Security Find Vulnerabilities in Your Software Gather Intelligence on Vulnerabilities and Exploits Handling Vulnerabilities Handle Vulnerabilities Due to Software Defects and Misconfiguration Handle Vulnerabilities Due to Human Factors Handle Vulnerabilities Due to Process Shortcomings Designing for Security Apply General Principles for Secure Design Design Software to Counter Specific Threats Developing Secure Code Follow Best Practices for Secure Coding Prevent Platform Vulnerabilities Prevent Privacy Vulnerabilities Implementing Common Protections Limit Access Using Login and User Roles Protect Data in Transit and At Rest Implement Error Handling and Logging Protect Sensitive Data and Functions Protect Database Access Testing Software Security Perform Security Testing Analyze Code to find Security Problems Use Automated Testing Tools to Find Security Problems Maintaining Security in Deployed Software Monitor and Log Applications to Support Security Maintain Security after Deployment

Certified Information Privacy Technologist (CIPT)
By Training Centre
The CIPT is the first and only certification of its kind worldwide. It was launched by the IAPP in 2014 and updated in early 2023 to meet the growing need that only tech pros can fill-securing data privacy at all stages of IT product and service lifecycles. Whether you work in the public or private sector, data privacy skills are quickly becoming a must-have-and that's a great opportunity for you. The CIPT certification also holds accreditation under ISO 17024: 2012 About This Course What will you learn? Critical data protection concepts and practices that impact IT Consumer data protection expectations and responsibility How to bake privacy into early stages of IT products and services for cost control, accuracy and speed-to-market How to establish data protection practices for data collection and transfer How to pre-empt data protection issues in the Internet of Things How to factor data protection into data classification and emerging tech such as cloud computing, facial recognition and surveillance How to communicate data protection issues with partners such as management, development, marketing and legal. This course has two programmatic modules, the first four areas focus on the fundamentals of data protection. The second module takes the fundamentals and puts it into practice. MODULE 1: Fundamentals of Information Privacy Unit 1: Common Principles and Approaches to Privacy This unit includes a brief discussion of the modern history of privacy, an introduction to types of information, an overview of information risk management and a summary of modern privacy principles. Unit 2: Jurisdiction and Industries This unit introduces the major privacy models employed around the globe and provides an overview of privacy and data protection regulation by jurisdictions and industry sectors. Unit 3: Information Security: Safeguarding Personal Information This unit presents introductions to information security, including definitions, elements, standards and threats/vulnerabilities, as well as introductions to information security management and governance, including frameworks, controls, cryptography and identity and access management (IAM). Unit 4: Online Privacy: Using Personal Information on Websites and with Other Internet-related Technologies This unit examines the web as a platform, as well as privacy considerations for sensitive online information, including policies and notices, access, security, authentication and data collection. Additional topics include children's online privacy, email, searches, online marketing and advertising, social media, online assurance, cloud computing and mobile devices. MODULE 2: Privacy in Technology Unit 1: Understanding the Need for Privacy in the IT Environment This unit highlights the impact that regulatory activities, security threats, advances in technology and the increasing proliferation of social networks have on IT departments. Unit 2: Core Privacy Concepts This unit reveals how privacy compliance becomes more attainable through developing information lifecycle plans, data identification and classification systems and data flow diagrams. Unit 3: Regulations and Standards Impacting Privacy in IT This unit introduces privacy laws, regulations and standards that can help IT professionals design better privacy programmes and systems to handle personal information throughout the data lifecycle. Unit 4: Privacy in Systems and Applications This unit develops an understanding of the risks inherent in the IT environment and how to address them. Unit 5: Online Privacy Issues This unit presents information about online threats, threat prevention and the role of IT professionals in ensuring proper handling of user data. Unit 6: De-identifying and Anonymizing Personally Identifiable Information This unit reveals the importance of personally identifiable information and methods for ensuring its protection. Unit 7: Cloud Computing This unit evaluates privacy and security concerns associated with cloud services, and standards that exist to advise on their use. Prerequisites There are no prerequisites for this course but attendees would benefit from a review of the materials on the IAPP site. What's Included? 1 years membership of the IAPP Refreshments & Lunch (Classroom courses only) Participant Guide Official Study Guides Official Practice Exam Official Q&A The Exam Fees Who Should Attend? The CIPT credential shows you've got the knowledge to build your organisation's data protection structures from the ground up. With regulators worldwide calling for tech professionals to factor data protection into their products and services, the job market for privacy-trained IT pros has never been stronger. As a result, the CIPT is targeted towards; Data Protection Officers IT Managers and Administrators Records Managers System Developers IT Security specialists Accreditation Our Guarantee We are an approved IAPP Training Partner. You can learn wherever and whenever you want with our robust classroom and interactive online training courses. Our courses are taught by qualified practitioners with a minimum of 25 years commercial experience. We strive to give our delegates the hands-on experience. Our courses are all-inclusive with no hidden extras. The one-off cost covers the training, all course materials, and exam voucher. Our aim: To achieve a 100% first time pass rate on all our instructor-led courses. Our Promise: Pass first time or 'train' again for FREE. *FREE training offered for retakes - come back within a year and only pay for the exam.

Competition Law in the telecoms sector
By Cullen International SA
Competition in the communications sector is complex and fast-changing. This presents both risks and opportunities to providers, as well as challenges for public authorities. Would you like to gain expert insights on the practical applications of competition law in the regulated telecoms industry? Then, this training is for you! Presented by experts through practical case examples, this online training will guide you through the latest competition law developments affecting the telecoms industry and give you a full overview of the role played by competiton law in shaping the telecoms market. Topics covered include: Relationship between competition law and sector-specific telecoms regulation Market definition Telecoms mergers Antitrust aspects of network co-operation Typical abuses of dominance in the telecoms sector Broadband state aid When: 17-19 September 2024 - 9 hours of interactive sessions spread over 3 days Where: Online, using Microsoft Teams Cannot make it to one of the sessions? All sessions will be recorded and made available to registered participants.

ONLINE CLASS: FOCUSES ON HARASSMENT IN THE WORKPLACE AND HOW TO ADDRESS THE PROBLEM. Harassment doesn’t have to be of a sexual nature – it can include offensive remarks about a person’s gender. For example, anyone could be guilty of harassing another if offensive comments are made about certain group in general. Simple teasing or offhand comments might not be illegal, but harassment is illegal when it creates a hostile or offensive work environment. This workshop teaches how to recognize, understand, and respond to harassment so that you can help to maintain a happy work environment, free from hostility and discomfort. Topics: Harassment Laws: The definition of sexual harassment and quid pro quo. Types of Harassment: Verbal, Non-Verbal, Physical, Psychological (teasing and offhand comments). Creating a happy work environment free from hostility and discomfort. Reporting: What to do when employees witness or experience harassment. Responding: How managers can identify and respond to prohibited conduct. Attendees will be able to: Identify the signs of Harassment and take steps to prevent it, Follow a legal and ethical protocol in responding and reporting it when it is perceived to occur, Involve the correct individuals in being made aware of the occurrence, and Respond appropriately to the situation after it occurs. This workshop is offered in two versions – management-only and staff-only. Online Format—Workplace Professionalism is a 4-hour interactive virtual class. Register for this class and you will be sent ONLINE login instructions prior to the class date. It was an extreme pleasure to have you as part of the Communication Enhancement Training Program. Your presentation was excellent and well received by the staff. Courtney C. Crouch, Jr., PresidentSelected Funeral and Life Insurance Company

LOOKING FOR: ADULT FICTION Jade Kavanagh is a Literary Agent at Darley Anderson Literary Agency. She has a degree in English Literature from the University of Westminster then went on to achieve her Masters in Modern and Contemporary Fictions. Alongside assisting Camilla Bolton on her list of clients Jade is building her own list of suspense, thriller and horror with distinct voices and setting. Across these genres Jade looks for powerful female narratives and dynamic characterisation. She wants female characters like Shiv Roy (Succession), Emily Gilmore (Gilmore Girls), Annalise Keating (How to Get Away with Murder), Buffy Summers (Buffy), Ellen Ripley (Alien), Dana Scully (The X Files), Detective Kima Greggs (The Wire). Jade would love something with a big book club hook that readers devour in one sitting. Setting and atmosphere are of huge appeal. She wants stories with a vivid sense of place and to be immersed in the world of the characters. Jade wants detail down to what shade of lipstick or colour of the lamp on their bedside table and the nature and landscape around them. She loves luxury settings she can get excited about reading and descriptions to lose herself in. Jade also loves dark twists on glamorous concepts and settings. Think The Devil Wears Prada meets Killing Eve, or Real Housewives or Succession meets How to Kill My Family or something akin to White Lotus. Across the spectrum of horror and speculative fiction, Jade is looking for haunting stories filled with slow build darkness and characters with heart. Think 28 Days Later and The Last of Us. She really wants a dark witchy story… or on the cozier side a fresh take on something like Practical Magic or Charmed. Jade wants heroes to root for, and villains that terrify and enrage her in equal measure. One of Jade's favourite TV shows is Orphan Black; she'd love to see a book series like this. As a proud member of the Twilight generation, (Team Edward forever!) she’d also love to read a modern vampire novel. Show her American Psycho meets Dracula. Give her 2023 Carlisle Cullen in a thriller or a new take on Buffy. Whilst not actively looking for sci-fi novels, Jade would love to see A Scully and Mulder for the 2020s! Notably, Jade looks for voices from all walks of life. She is incredibly passionate about bringing working-class voices into the commercial fiction space. She would love to hear from new exciting talent, telling stories about everyday people with relatable voices, people she grew up with, people she can imagine. Jade would like you to submit a covering letter, 1 -2 page synopsis and the first 5,000 words of your completed manuscript in a single word document. (In addition to the paid sessions, Jade is kindly offering one free session for low income/under-represented writers. Please email agent121@iaminprint.co.uk to apply, outlining your case for this option which is offered at the discretion of I Am In Print). By booking you understand you need to conduct an internet connection test with I Am In Print prior to the event. You also agree to email your material in one document to reach I Am In Print by the stated submission deadline and note that I Am In Print take no responsibility for the advice received during your agent meeting. The submission deadline is: Friday 24th January 2025

21st January Alice Williams #Agent121. Looking for: PICTURE BOOKS, YOUNG FICTION, CHAPTER BOOKS, MG, YA
5.0(1)By I Am In Print
LOOKING FOR: PICTURE BOOKS, YOUNG FICTION, CHAPTER BOOKS, MG, YA Alice set up Alice Williams Literary in 2018 after representing children's books for over ten years at David Higham Associates. She is especially keen to consider playful, funny books for all ages, and is on the lookout for heartwarming, empowering stories, whether in a realistic, contemporary setting, or a wildly imaginative fantasy world - or somewhere in-between. Alice is offering 121 sessions for young fiction, middle grade, YA and picture book writers. For chapter books, MG and YA fiction, please submit a covering letter, synopsis and the first three chapters of your manuscript in a single word document. For picture books, please submit a covering letter and two texts, or for illustrators one dummy and examples from your portfolio or a link to your website. (In addition to the paid sessions, Alice is kindly offering one free session for low income/under-represented writers. Please email agent121@iaminprint.co.uk to apply, outlining your case for this option which is offered at the discretion of I Am In Print). By booking you understand you need to conduct an internet connection test with I Am In Print prior to the event. You also agree to email your material in one document to reach I Am In Print by the stated submission deadline and note that I Am In Print take no responsibility for the advice received during your agent meeting. The submission deadline is: Monday 13th January 2025

Auditing in the Exploration & Production (E&P) Industry Level 1
By EnergyEdge - Training for a Sustainable Energy Future
About this training course This 3-day introductory-level course provides a comprehensive overview of Auditing in the Exploration & Production (E&P) industry. It is suitable for anyone who wants to gain a broader understanding of Upstream Oil & Gas Auditing - including joint venture, financial and contractual audits by government and regulatory authorities in the various granting regimes (Production Sharing Contracts, Risk Service Contracts, Concessionary). Training Objectives After the completion of this training course, participants will be able to: Gain knowledge of the unique features or key phases of the E&P Business Understand the general principles and objectives of the various different types of Upstream Oil & Gas audits Add value to your organisation by improving your audit techniques and auditing skills Review the importance of following process in order to avoid costly audit related findings. Utilize industry specific examples and exercises, develop your understanding of the most common E&P industry audit issues Target Audience This training course is suitable and will greatly benefit the following specific groups: Audit staff who are new or relatively new to the industry and who require a grounding in the various aspects of E&P Audit Finance or Accounting personnel involved in supporting audits Staff from a wide range of other business functions who are connected to / impacted by audit, such as, Supply Chain, Operations, Contracts Holders, IT, Tax and Treasury Topics will be covered from both the perspective of being part of an audit team plus that of the team being audited. Therefore, the course will appeal to staff from IOC's, NOC's and those from Government and/or Regulatory Authorities. Course Level Basic or Foundation Training Methods The training instructor relies on a highly interactive training method to enhance the learning process. This method ensures that all participants gain a complete understanding of all the topics covered. The training environment is highly stimulating, challenging, and effective because the participants will learn by case studies which will allow them to apply the material taught in their own organization. Course Duration: 3 days in total (21 hours). Training Schedule 0830 - Registration 0900 - Start of training 1030 - Morning Break 1045 - Training recommences 1230 - Lunch Break 1330 - Training recommences 1515 - Evening break 1530 - Training recommences 1700 - End of Training The maximum number of participants allowed for this training course is 25. This course is also available through our Virtual Instructor Led Training (VILT) format. Trainer Your expert course leader has more than 30 years of experience in the international oil and gas industry, covering all areas of Finance and Audit, including involvement in Commercial roles. During her 19 years with ENI she worked in Italy, Netherlands, Egypt and UK and was CFO for 2 major ENI subsidiaries. She has delivered training courses in Accounting, Audit, Economics and Commercial topics in many Countries. She has a Degree in Economics & Accounting and is a Certified Chartered Accountant. She is also a Chartered Auditor and an International Petroleum Negotiator. Outside of work, she is inspired by the beauty of nature and art, helping disadvantaged people, sports (football, golf) and her cat. Courses Delivered Internationally: E&P Accounting, Auditing in the Oil & Gas Industry Cost Control & Budgeting Introduction to the Oil & Gas Industry Petroleum Project Economics Contracts Strategy International O&G Exploitation Contracts POST TRAINING COACHING SUPPORT (OPTIONAL) To further optimise your learning experience from our courses, we also offer individualized 'One to One' coaching support for 2 hours post training. We can help improve your competence in your chosen area of interest, based on your learning needs and available hours. This is a great opportunity to improve your capability and confidence in a particular area of expertise. It will be delivered over a secure video conference call by one of our senior trainers. They will work with you to create a tailor-made coaching program that will help you achieve your goals faster. Request for further information post training support and fees applicable Accreditions And Affliations

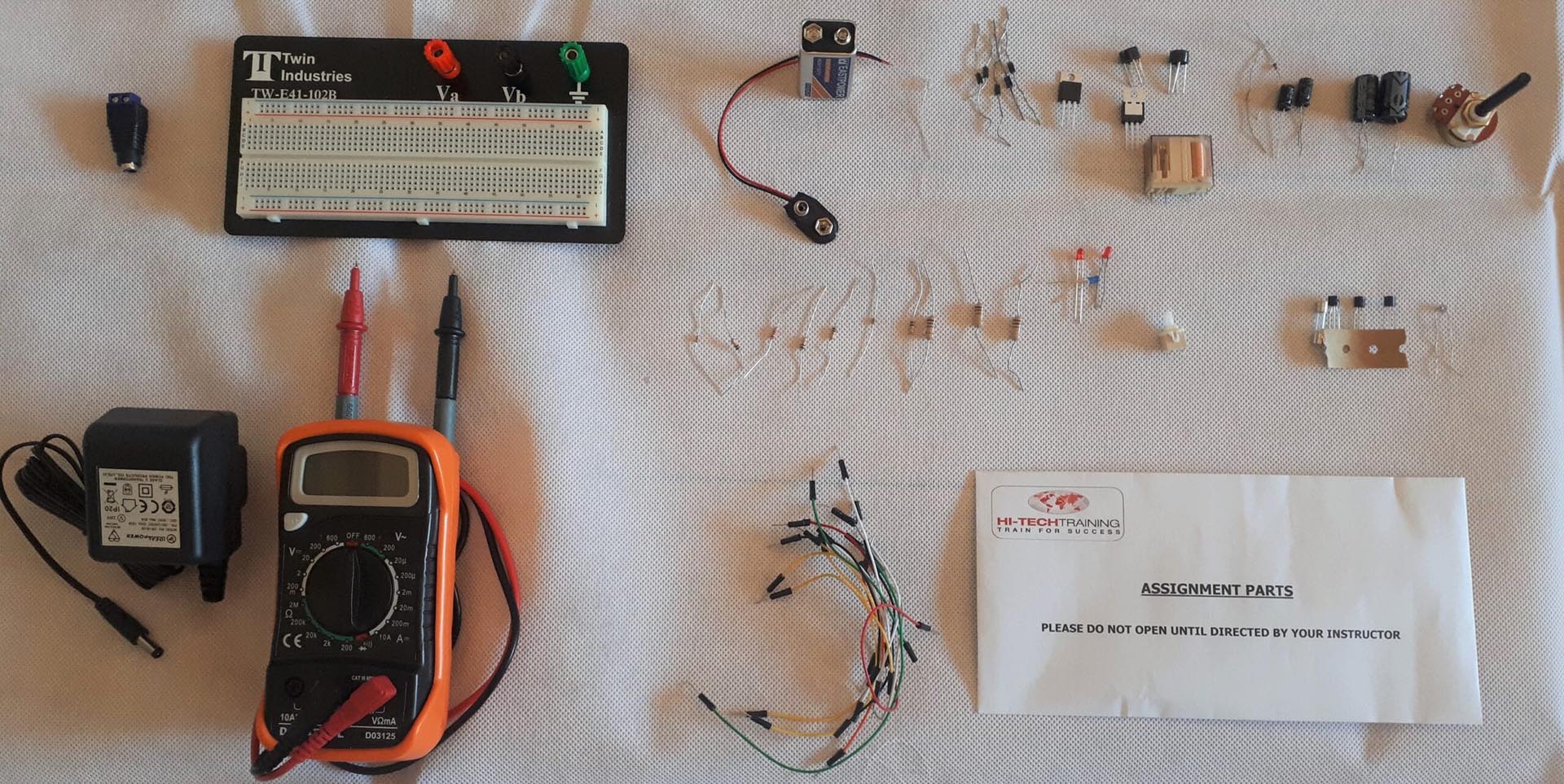
Electronics Repair 1 Course
By Hi-Tech Training
The Electronics Equipment Repair 1 equips participants with practical “Hands-On” skills relevant to the workplace and the theory required for certification. Participants on successful completion of the course will have the skills and knowledge to: Demonstrate the operation of a wide range of electronic components and circuits and their applications in modern electronic-based equipment such as amplifiers, Hi-Fi systems, stereos, and control systems Construct, test and fault-find the following popular basic circuits: Power supplies, amplifiers, timers, etc. Become competent in the correct use of electronic test and measurement equipment such as Analogue and Digital Multimeter and Oscilloscopes.