- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
1735 Courses delivered Live Online
SC-300T00 Microsoft Identity and Access Administrator
By Nexus Human
Duration 4 Days 24 CPD hours This course is intended for This course is for the Identity and Access Administrators who are planning to take the associated certification exam, or who are performing identity and access administration tasks in their day-to-day job. This course would also be helpful to an administrator or engineer that wants to specialize in providing identity solutions and access management systems for Azure-based solutions; playing an integral role in protecting an organization. The Microsoft Identity and Access Administrator course explores how to design, implement, and operate an organization?s identity and access management systems by using Microsoft Entra ID. Learn to manage tasks such as providing secure authentication and authorization access to enterprise applications. You will also learn to provide seamless experiences and self-service management capabilities for all users. Finally, learn to create adaptive access and governance of your identity and access management solutions ensuring you can troubleshoot, monitor, and report on your environment. The Identity and Access Administrator may be a single individual or a member of a larger team. Learn how this role collaborates with many other roles in the organization to drive strategic identity projects. The end goal is to provide you knowledge to modernize identity solutions, to implement hybrid identity solutions, and to implement identity governance. Prerequisites SC-900T00: Microsoft Security, Compliance, and Identity Fundamentals AZ-104T00 - Microsoft Azure Administrator 1 - Explore identity in Microsoft Entra ID Explain the identity landscape Explore zero trust with identity Discuss identity as a control plane Explore why we have identity Define identity administration Contrast decentralized identity with central identity systems Discuss identity management solutions Explain Microsoft Entra Business to Business Compare Microsoft identity providers Define identity licensing Explore authentication Discuss authorization Explain auditing in identity 2 - Implement initial configuration of Microsoft Entra ID Configure company brand Configure and manage Microsoft Entra roles Configure delegation by using administrative units Analyze Microsoft Entra role permissions Configure and manage custom domains Configure tenant-wide setting 3 - Create, configure, and manage identities Create, configure, and manage users Create, configure, and manage groups Configure and manage device registration Manage licenses Create custom security attributes Explore automatic user creation 4 - Implement and manage external identities Describe guest access and Business to Business accounts Manage external collaboration Invite external users - individually and in bulk Demo - manage guest users in Microsoft Entra ID Manage external user accounts in Microsoft Entra ID Manage external users in Microsoft 365 workloads Implement and manage Microsoft Entra Verified ID Configure identity providers Implement cross-tenant access controls 5 - Implement and manage hybrid identity Plan, design, and implement Microsoft Entra Connect Implement manage password hash synchronization (PHS) Implement manage pass-through authentication (PTA) Demo - Manage pass-through authentication and seamless single sign-on (SSO) Implement and manage federation Trouble-shoot synchronization errors Implement Microsoft Entra Connect Health Manage Microsoft Entra Health 6 - Secure Microsoft Entra users with multifactor authentication What is Microsoft Entra multifactor authentication? Plan your multifactor authentication deployment Configure multi-factor authentication methods 7 - Manage user authentication Administer FIDO2 and passwordless authentication methods Explore Authenticator app and OATH tokens Implement an authentication solution based on Windows Hello for Business Deploy and manage password protection Configure smart lockout thresholds Implement Kerberos and certificate-based authentication in Microsoft Entra ID Configure Microsoft Entra user authentication for virtual machines 8 - Plan, implement, and administer Conditional Access Plan security defaults Plan Conditional Access policies Implement Conditional Access policy controls and assignments Test and troubleshoot Conditional Access policies Implement application controls Implement session management Implement continuous access evaluation 9 - Manage Microsoft Entra Identity Protection Review identity protection basics Implement and manage user risk policy Monitor, investigate, and remediate elevated risky users Implement security for workload identities Explore Microsoft Defender for Identity 10 - Implement access management for Azure resources Assign Azure roles Configure custom Azure roles Create and configure managed identities Access Azure resources with managed identities Analyze Azure role permissions Configure Azure Key Vault RBAC policies Retrieve objects from Azure Key Vault Explore Microsoft Entra Permissions Management 11 - Plan and design the integration of enterprise apps for SSO Discover apps by using Microsoft Defender for Cloud Apps and Active Directory Federation Services app report Configure connectors to apps Design and implement app management roles Configure preintegrated gallery SaaS apps Implement and manage policies for OAuth apps 12 - Implement and monitor the integration of enterprise apps for SSO Implement token customizations Implement and configure consent settings Integrate on-premises apps with Microsoft Entra application proxy Integrate custom SaaS apps for single sign-on Implement application-based user provisioning Monitor and audit access to Microsoft Entra integrated enterprise applications Create and manage application collections 13 - Implement app registration Plan your line of business application registration strategy Implement application registration Register an application Configure permission for an application Grant tenant-wide admin consent to applications Implement application authorization Manage and monitor application by using app governance 14 - Plan and implement entitlement management Define access packages Configure entitlement management Configure and manage connected organizations Review per-user entitlements 15 - Plan, implement, and manage access review Plan for access reviews Create access reviews for groups and apps Create and configure access review programs Monitor access review findings Automate access review management tasks Configure recurring access reviews 16 - Plan and implement privileged access Define a privileged access strategy for administrative users Configure Privileged Identity Management for Azure resources Plan and configure Privileged Access Groups Analyze Privileged Identity Management audit history and reports Create and manage emergency access accounts 17 - Monitor and maintain Microsoft Entra ID Analyze and investigate sign-in logs to troubleshoot access issues Review and monitor Microsoft Entra audit logs Export logs to third-party security information and event management system Analyze Microsoft Entra workbooks and reporting Monitor security posture with Identity Secure Score

ONE SPACE LEFT! 24th September Lucy Brownridge #Agent121. Looking for: PICTURE BOOKS
5.0(3)By I Am In Print
LOOKING FOR: CHILDREN'S: PICTURE BOOK TEXTS, NON-FICTION, POETRY Lucy Brownridge is Editorial Director at Wide Eyed Editions and Frances Lincoln Children’s Books, and formerly Thames & Hudson where she helped to establish the Children’s list. She specialises in highly illustrated picture books and non-fiction (including poetry) for children. She has commissioned and edited books which have gone on to win the Carnegie Awards, The British Book Awards, the Klaus Flugge Prize, the Blue Peter Prize and have been translated into over 30 languages. She has been editor to Alan Ahlberg, Quentin Blake, Mariajo Ilustrajo, Yuval Zommer and Children’s Laureate Joseph Coelho among many others. She is the author of The Fantastical Safari and The Cat Family series, and many other books for children. She is interested in the history of illustrated children’s books and is always looking for innovative ways to use the book format. ABOUT YOU Include a covering letter, in a Word document, telling Lucy about yourself and your sources of inspiration. If you have one, include a link to your website. She is keen to read stories she hasn't seen before or see artwork with a distinctive style rather than something that fits with trends. She has particular experience with picture books and illustrated narrative non-fiction. PICTURE BOOKS Please send one or two (max) full manuscripts, in a Word document, starting with a short summary/blurb. Make the summary punchy and engaging. Remember that the best picture book stories are simple and every word should count. Do you see this book as part of a series? NON-FICTION PROPOSALS Please send a paragraph explaining your idea, a contents list, if appropriate, and a sample piece of text. (In addition to the paid sessions, Lucy is kindly offering one free session for low income/under-represented writers. Please email agent121@iaminprint.co.uk to apply, outlining your case for this option which is offered at the discretion of I Am In Print). By booking you understand you need to conduct an internet connection test with I Am In Print prior to the event. You also agree to email your material in one document to reach I Am In Print by the stated submission deadline and note that I Am In Print take no responsibility for the advice received during your agent meeting. The submission deadline is: Monday 15th September 2025 at 10:00am UK BST

Disciplined Agile Scrum Master (DASM): Virtual In-House Training
By IIL Europe Ltd
Disciplined Agile Scrum Master (DASM): Virtual In-House Training Is your team treading water using waterfall? Do you feel trapped in an agile framework? Would you like to find solutions to the problems you've been wrestling with? Are you looking for ways to enhance your team's agility? Break free from your old ways by choosing a way of working that fits your team's context. Find strategies to improve your processes and strengthen your team with the Disciplined Agile® tool kit. Disciplined Agile Scrum Master is a nine-lesson, instructor-led course that shows you how to use Disciplined Agile (DA™) to improve your team's way of working. In just two days, you will become familiar with foundational agile and lean practices that DA supports, practice using the tool kit to solve problems, and learn how to build high-performance teams. Filled with activities, animations, supplemental reading, and more, this course will prepare you to take the Disciplined Agile Scrum Master (DASM) exam and, equally important, start using Disciplined Agile immediately. #BBD0E0 » What You Will Learn After the completion of this course, you will be able to: Apply foundational agile and lean practices in your own team setting Describe what business agility is and how it is core to value proposition of Disciplined Agile® Describe the significance of the Disciplined Agile mindset Define the DA™ principles, promises, and guidelines and how they set Disciplined Agile apart from other frameworks Explain how people are organized into DA teams Define the primary DA roles and how they each are key to the success of a self-organizing agile team Explain how to help your team work well together using the Lean principle of 'respect people' Analyze your team's context to make better process-related decisions Select the best-fit DA life cycles for your teams Apply the five DA steps of choosing your team's way of working (WoW) Apply the relevant agile and lean techniques to successfully initiate your team Apply the relevant agile and lean techniques to support your team producing business value Apply the relevant agile and lean techniques to support your team releasing their work into production Apply the relevant agile and lean techniques to support your team on an ongoing basis Recognize when to be resilient List and define the principles of Lean Significance of the Disciplined Agile® Mindset Business agility and how it is core to value proposition of Disciplined Agile Eight DA principles and how they are core to what sets Disciplined Agile apart from other agile frameworks Which situations each of the DA™ life cycles is best applied DA Practice of choosing a team's way of working (WoW) Foundations of Agile How people are organized into DA teams Primary DA roles and how they each are key to the success of a self-organizing agile team Help your team work well together (Lean principle 'Respect people') Inception phase and why it is important DA tool kit to tailor your way of working within a select phase according to context Agile techniques and ceremonies relevant to Inception Construction phase and why it is important Agile techniques and ceremonies that take place during Construction Eliminate Waste and Build Quality (Lean principles) Deliver Value Quickly (Lean principle) Transition phase and why it is important Ongoing phase and why it is important Learn Pragmatically (Lean principle) Elements of the process blade (onion) diagram Principles of Lean When to be resilient Benefits of explicit workflow Kaizen loops and PDSA techniques for continuous improvement Options for cross-team learning: "community of practice" and "center of excellence"

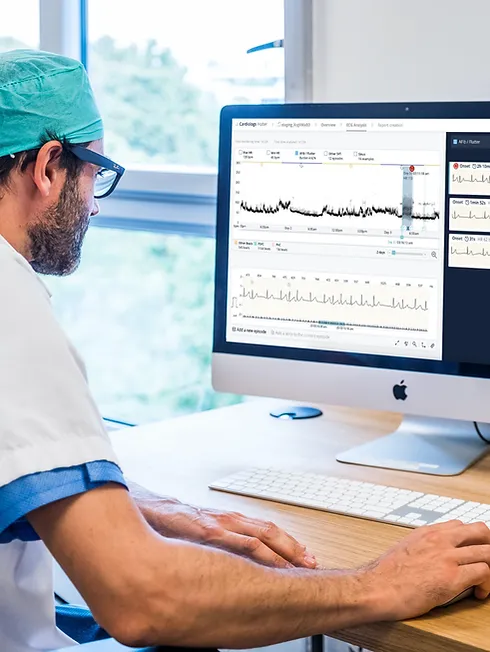
Learn how to perform and read an ECG ... Nationally Recognised Qualification OCN Accredited - Level 3 (advanced level) CPD Accredited - The CPD Certification Service Introduces you to the fundamentals of setting up and operating an ECG machine Includes patient preparation Produce a valid (error free) ECG Learn and understand ECG traces Recognise recordings that require urgent attention Basic understanding of English language required OPEN TO ALL APPLICANTS VIRTUAL CLASSROOM OPTION INCLUDES COMPREHENSIVE PRACTISE@HOME ECG TRAINING KIT Final interpretation of all ECG recordings is the responsibility of a medical professional.
SUSTAINABILITY IN SUPPLY CHAIN
By Export Unlocked Limited
This module aims to develop knowledge and understanding of the impact of Import/Export freight movement on the environment and the opportunities available to organisations to use sustainable options. we will cover CBAM , Deforestation, GSPR and many challenges facing Exporters and Importers.

COBIT 2019 Foundation
By Nexus Human
Duration 2 Days 12 CPD hours This course is intended for The COBIT 2019 Foundation course would suit candidates working in the following IT professions or areas: IT Auditors IT Managers IT Quality professionals IT Leadership IT Developers Process practitioners Managers in IT service providing firms The above list is a suggestion only; individuals may wish to attend based on their own career aspirations, personal goals or objectives. Delegates may take as few or as many Intermediate qualifications as they require, and to suit their needs. Overview This COBIT 2019 Foundation course is designed as an introduction to COBIT 2019 and enables you to understand how an integrated business framework for the governance and management of enterprise IT can be utilized to achieve IT business integration, cost reductions and increased productivity. The syllabus areas that this course is designed to cover are: New framework introduction Key concepts and terminology Governance and Framework Principles Governance system and components Governance and management objectives Performance management Designing a tailored governance system COBIT 2019 builds on and integrates more than 25 years of development in this field, not only incorporating new insights from science, but also operationalizing these insights as practice. The heart of the COBIT framework updates COBIT principles while laying out the structure of the overall framework including: New concepts are introduced and terminology is explained?the COBIT Core Model and its 40 governance and management objectives provide the platform for establishing your governance program. The performance management system is updated and allows the flexibility to use maturity measurements as well as capability measurements. Introductions to design factors and focus areas offer additional practical guidance on flexible adoption of COBIT 2019, whether for specific projects or full implementation. From its foundation in the IT audit community, COBIT has developed into a broader and more comprehensive information and technology (I&T) governance and management framework and continues to establish itself as a generally accepted framework for I&T governance. 1 - COBIT 5 OVERVIEW AND INTRODUCTION Course Administration Course Objectives Exam Overview Certification Scheme History of COBIT COBIT 2019 Improvements Major differences with 2019 Misconceptions about COBIT COBIT and Other Standards 2 - KEY CONCEPTS AND TERMINOLOGY Introduction to Enterprise Governance of Information and Technology Benefits of Information and Technology Governance COBIT Information and Technology Governance Framework Distinction of Governance and Management Three Principles of a Governance Framework Six Principles for a Governance System 3 - GOVERNANCE SYSTEMS AND COMPONENTS Introduction to the Components of a Governance System Processes and Capability Levels Organizational Structures and Defined Roles Information Flows and Items People, Skills and Competencies Principles, Policies and Frameworks Culture, Ethics and Behavior Services, Infrastructure and Applications 4 - GOVERNANCE MANAGEMENT OBJECTIVES Governance and Management Objectives Publication Governance and Management Objectives Governance and Management Objectives Core Model Evaluate, Direct and Monitor Align, Plan and Organize Build, Acquire and Implement Deliver, Service and Support Monitor, Evaluate and Assess 5 - GOALS CASCADE Governance and Management Objective Relationships Governance and Management Objective Descriptions High-Level Information Example Introduction to the Goals Cascade Enterprise Goals Alignment Goals Mapping Tables ? Appendix A 6 - PERFORMANCE MANAGEMENT Introduction to Performance Management COBIT Performance Management Principles COBIT Performance Management (CPM) Overview Process Capability Levels Rating Process Activities Focus Area Maturity Levels Performance Management of Organizational Structures Performance Management of Information Items Performance Management of Culture and Behavior 7 - DESIGNING A TAILORED GOVERNANCE SYSTEM The Need for Tailoring Design Factors Enterprise Strategy Enterprise Goals Risk Profile I&T Related Issues Threat Landscape Compliance Requirements Role of IT Sourcing Model for IT IT Implementation Methods Technology Adoption Strategy Enterprise Size Focus Areas Designing a Tailored Governance System Management Objective Priority and Target Capability Levels Component Variations Specific Focus Areas Stages and Steps in the Design Process 8 - IMPLEMENTING ENTERPRISE GOVERNANCE OF IT The Business Case The COBIT Implementation Guide Purpose COBIT Implementation Approach Phase 1 ? What are the Drivers Phase 2 ? Where are we Now Phase 3 ? Where do we Want to be Phase 4 ? What Needs to be Done Phase 5 ? How do we get There Phase 6 ? Did we get There Phase 7 How do we Weep the Momentum Going? EGIT Implementation Program Challenges

AZ-900T00 Microsoft Azure Fundamentals
By Nexus Human
Duration 1 Days 6 CPD hours This course is intended for This course is suitable for IT personnel who are just beginning to work with Azure. This audience wants to learn about our offerings and get hands-on experience with the product. This course primarily uses the Azure portal and command line interface to create resources and does not require scripting skills. Students in this course will gain confidence to take other role-based courses and certifications, such as Azure Administrator. This course combines lecture, demonstrations, and hands-on labs. This course will also help prepare someone for the AZ-900 exam. This course will provide foundational level knowledge on cloud concepts; core Azure services; and Azure management and governance features and tools. Prerequisites There are no prerequisites for taking this course. Familiarity with cloud computing is helpful, but isn't necessary. 1 - Describe cloud computing What is cloud computing Describe the shared responsibility model Define cloud models Describe the consumption-based model 2 - Describe the benefits of using cloud services Describe the benefits of high availability and scalability in the cloud Describe the benefits of reliability and predictability in the cloud Describe the benefits of security and governance in the cloud Describe the benefits of manageability in the cloud 3 - Describe cloud service types Describe Infrastructure as a Service Describe Platform as a Service Describe Software as a Service 4 - Describe the core architectural components of Azure What is Microsoft Azure Get started with Azure accounts Describe Azure physical infrastructure Describe Azure management infrastructure 5 - Describe Azure compute and networking services Describe Azure Virtual Machines Describe Azure Virtual Desktop Describe Azure Containers Describe Azure Functions Describe application hosting options Describe Azure Virtual Networking Describe Azure Virtual Private Networks Describe Azure ExpressRoute Describe Azure DNS 6 - Describe Azure storage services Describe Azure storage accounts Describe Azure storage redundancy Describe Azure storage services Identify Azure data migration options Identify Azure file movement options 7 - Describe Azure identity, access, and security Describe Azure directory services Describe Azure authentication methods Describe Azure external identities Describe Azure conditional access Describe Azure role-based access control Describe zero trust model Describe defense-in-depth Describe Microsoft Defender for Cloud 8 - Describe cost management in Azure Describe factors that can affect costs in Azure Compare the Pricing and Total Cost of Ownership calculators Describe the Microsoft Cost Management tool Describe the purpose of tags 9 - Describe features and tools in Azure for governance and compliance Describe the purpose of Microsoft Purview Describe the purpose of Azure Policy Describe the purpose of resource locks Describe the purpose of the Service Trust portal 10 - Describe features and tools for managing and deploying Azure resources Describe tools for interacting with Azure Describe the purpose of Azure Arc Describe Azure Resource Manager and Azure ARM templates 11 - Describe monitoring tools in Azure Describe the purpose of Azure Advisor Describe Azure Service Health Describe Azure Monitor Additional course details: Nexus Humans AZ-900T00 Microsoft Azure Fundamentals training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the AZ-900T00 Microsoft Azure Fundamentals course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

SC-400T00 Administering Information Protection and Compliance in Microsoft 365
By Nexus Human
Duration 4 Days 24 CPD hours This course is intended for The information protection administrator translates an organization?s risk and compliance requirements into technical implementation. They are responsible for implementing and managing solutions for content classification, data loss prevention (DLP), information protection, data lifecycle management, records management, privacy, risk, and compliance. They also work with other roles that are responsible for governance, data, and security to evaluate and develop policies to address an organization's risk reduction and compliance goals. This role assists workload administrators, business application owners, human resources departments, and legal stakeholders to implement technology solutions that support the necessary policies and controls. Learn how to protect information in your Microsoft 365 deployment. This course focuses on data lifecycle management and information protection and compliance within your organization. The course covers implementation of data loss prevention policies, sensitive information types, sensitivity labels, data retention policies, Microsoft Purview Message Encryption, audit, eDiscovery, and insider risk among other related topics. The course helps learners prepare for the Microsoft Information Protection Administrator exam (SC-400). Prerequisites Foundational knowledge of Microsoft security and compliance technologies. Basic knowledge of information protection concepts. Understanding of cloud computing concepts. Understanding of Microsoft 365 products and services. 1 - Introduction to information protection and data lifecycle management in Microsoft Purview Know your data Protect your data Prevent data loss Govern your data 2 - Classify data for protection and governance Data classification overview Classify data using sensitive information types Classify data using trainable classifiers Review sensitive information and label usage Explore labeled and sensitive content Understand activities related to your data 3 - Create and manage sensitive information types Compare built-in versus custom sensitive information types Create and manage custom sensitive information types Describe custom sensitive information types with exact data match Implement document fingerprinting Create keyword dictionary 4 - Understand Microsoft 365 encryption Learn how Microsoft 365 data is encrypted at rest Understand service encryption in Microsoft Purview Explore customer key management using Customer Key Learn how data is encrypted in-transit 5 - Deploy Microsoft Purview Message Encryption Implement Microsoft Purview Message Encryption Implement Microsoft Purview Advanced Message Encryption Use Microsoft Purview Message Encryption templates in mail flow rules 6 - Protect information in Microsoft Purview Information protection overview Configure sensitivity labels Configure sensitivity label policies Configure auto-labeling policies Manage, monitor, and remediate information protection 7 - Apply and manage sensitivity labels Apply sensitivity labels to Microsoft Teams, Microsoft 365 groups, and SharePoint sites Plan on-premises labeling Configure on-premises labeling for the Unified Labeling Scanner Apply protections and restrictions to email and files Monitor label performance using label analytics 8 - Prevent data loss in Microsoft Purview Data loss prevention overview Identify content to protect Define policy settings for your DLP policy Test and create your DLP policy Prepare Endpoint DLP Manage DLP alerts in the Microsoft Purview compliance portal View data loss prevention reports Implement the Microsoft Purview Extension 9 - Configure DLP policies for Microsoft Defender for Cloud Apps and Power Platform Configure data loss prevention policies for Power Platform Integrate data loss prevention in Microsoft Defender for Cloud Apps Configure policies in Microsoft Defender for Cloud Apps Manage data loss prevention violations in Microsoft Defender for Cloud Apps 10 - Manage data loss prevention policies and reports in Microsoft 365 Configure data loss prevention for policy precedence Implement data loss prevention policies in test mode Explain data loss prevention reporting capabilities Manage permissions for data loss prevention reports Manage and respond to data loss prevention policy violations 11 - Manage the data lifecycle in Microsoft Purview Data Lifecycle Management overview Configure retention policies Configure retention labels Configure manual retention label policies Configure auto-apply retention label policies Import data for Data Lifecycle Management Manage, monitor, and remediate Data Lifecycle Management 12 - Manage data retention in Microsoft 365 workloads Explain retention in Exchange Online Explain retention in SharePoint Online and OneDrive Explain retention in Microsoft Yammer Activate archive mailboxes in Microsoft Exchange Apply mailbox holds in Microsoft Exchange Recover content in Microsoft Exchange 13 - Manage records in Microsoft Purview Records management overview Import a file plan Configure retention labels Configure event driven retention Manage, monitor, and remediate records 14 - Explore compliance in Microsoft 365 Plan for security and compliance in Microsoft 365 Plan your beginning compliance tasks in Microsoft Purview Manage your compliance requirements with Compliance Manager Examine the Compliance Manager dashboard Analyze the Microsoft Compliance score 15 - Search for content in the Microsoft Purview compliance portal Explore Microsoft Purview eDiscovery solutions Create a content search View the search results and statistics Export the search results and search report Configure search permissions filtering Search for and delete email messages 16 - Manage Microsoft Purview eDiscovery (Standard) Explore Microsoft Purview eDiscovery solutions Implement Microsoft Purview eDiscovery (Standard) Create eDiscovery holds Search for content in a case Export content from a case Close, reopen, and delete a case 17 - Manage Microsoft Purview eDiscovery (Premium) Explore Microsoft Purview eDiscovery (Premium) Implement Microsoft Purview eDiscovery (Premium) Create and manage an eDiscovery (Premium) case Manage custodians and non-custodial data sources Analyze case content 18 - Manage Microsoft Purview Audit (Standard) Explore Microsoft Purview Audit solutions Implement Microsoft Purview Audit (Standard) Search the audit log Export, configure, and view audit log records Use audit log searching to investigate common support issues 19 - Prepare Microsoft Purview Communication Compliance Plan for communication compliance Identify and resolve communication compliance workflow Case study--Configure an offensive language policy Investigate and remediate communication compliance alerts 20 - Manage insider risk in Microsoft Purview Insider risk management overview Create and manage insider risk policies Investigate insider risk alerts Take action on insider risk alerts through cases Manage insider risk management forensic evidence Create insider risk management notice templates 21 - Implement Microsoft Purview Information Barriers Explore Microsoft Purview Information Barriers Configure information barriers in Microsoft Purview Examine information barriers in Microsoft Teams Examine information barriers in OneDrive Examine information barriers in SharePoint 22 - Manage regulatory and privacy requirements with Microsoft Priva Create and manage risk management policies Investigate and remediate risk management alerts Create rights requests Manage data estimate and retrieval for rights requests Review data from rights requests Get reports from rights requests 23 - Implement privileged access management Case study--Implementing privileged access management 24 - Manage Customer Lockbox Manage Customer Lockbox requests

Disciplined Agile Scrum Master (DASM): In-House Training
By IIL Europe Ltd
Disciplined Agile Scrum Master (DASM): In-House Training Is your team treading water using waterfall? Do you feel trapped in an agile framework? Would you like to find solutions to the problems you've been wrestling with? Are you looking for ways to enhance your team's agility? Break free from your old ways by choosing a way of working that fits your team's context. Find strategies to improve your processes and strengthen your team with the Disciplined Agile® tool kit. Disciplined Agile Scrum Master is a nine-lesson, instructor-led course that shows you how to use Disciplined Agile (DA™) to improve your team's way of working. In just two days, you will become familiar with foundational agile and lean practices that DA supports, practice using the tool kit to solve problems, and learn how to build high-performance teams. Filled with activities, animations, supplemental reading, and more, this course will prepare you to take the Disciplined Agile Scrum Master (DASM) exam and, equally important, start using Disciplined Agile immediately. #BBD0E0 » What You Will Learn After the completion of this course, you will be able to: Apply foundational agile and lean practices in your own team setting Describe what business agility is and how it is core to value proposition of Disciplined Agile® Describe the significance of the Disciplined Agile mindset Define the DA™ principles, promises, and guidelines and how they set Disciplined Agile apart from other frameworks Explain how people are organized into DA teams Define the primary DA roles and how they each are key to the success of a self-organizing agile team Explain how to help your team work well together using the Lean principle of 'respect people' Analyze your team's context to make better process-related decisions Select the best-fit DA life cycles for your teams Apply the five DA steps of choosing your team's way of working (WoW) Apply the relevant agile and lean techniques to successfully initiate your team Apply the relevant agile and lean techniques to support your team producing business value Apply the relevant agile and lean techniques to support your team releasing their work into production Apply the relevant agile and lean techniques to support your team on an ongoing basis Recognize when to be resilient List and define the principles of Lean Significance of the Disciplined Agile® Mindset Business agility and how it is core to value proposition of Disciplined Agile Eight DA principles and how they are core to what sets Disciplined Agile apart from other agile frameworks Which situations each of the DA™ life cycles is best applied DA Practice of choosing a team's way of working (WoW) Foundations of Agile How people are organized into DA teams Primary DA roles and how they each are key to the success of a self-organizing agile team Help your team work well together (Lean principle 'Respect people') Inception phase and why it is important DA tool kit to tailor your way of working within a select phase according to context Agile techniques and ceremonies relevant to Inception Construction phase and why it is important Agile techniques and ceremonies that take place during Construction Eliminate Waste and Build Quality (Lean principles) Deliver Value Quickly (Lean principle) Transition phase and why it is important Ongoing phase and why it is important Learn Pragmatically (Lean principle) Elements of the process blade (onion) diagram Principles of Lean When to be resilient Benefits of explicit workflow Kaizen loops and PDSA techniques for continuous improvement Options for cross-team learning: "community of practice" and "center of excellence"

Advanced Well Engineering
By EnergyEdge - Training for a Sustainable Energy Future
About this Training Course Well engineers who are responsible for technically evaluating and authorizing programs for drilling or working over wells must have the required skills and competencies to safely design wells of varying nature. They also need to be able to confirm that well delivery and intervention programs generate intrinsic well control assurance. Such work programs must establish, verify, monitor and maintain suitable and sufficient barriers for the entire well lifecycle - from spud to abandonment. Well engineers must also be able to select a suitable drilling or workover rig, capable of safely performing the work within its operational envelope. This 3 full-day course aims to further develop and assess the knowledge required to work on and eventually, authorize a well delivery program as deemed fit for purpose. It also addresses elements of well control that must be embedded into well design, well work programming and equipment selection. This course is intended for participants who already have a sound understanding of the principles of the design and/or delivery of wells and with more than 3 years of relevant industry experience. Training Objectives By the end of this course, participants will be able to: Feel confident to design and plan drilling and workover activities while considering geological risks, formation pressures/strengths, and any integrity or well control concerns. Monitor wells operations and ensure that they can and will remain within the accepted design envelope. Assess risks and then apply mitigation or recovery methods in cases where design envelopes are threatened. Participants should be capable of assessing a drilling or workover program and then be able to answer the following key questions: Does the program delivery have a sound design and work plan that allows the well(s) to be drilled or worked over safely? Have we determined the appropriate kick tolerance for each open hole section and is it realistic for all drilling hazards that may be encountered? Have all drilling hazards been suitably assessed, and the associated risk mitigated to a level as low as reasonably practicable? Are there adequate, verifiable barriers in place throughout the operation and does everybody know their role and responsibility? And, as applicable, is the selected rig capable of implementing the work program? Target Audience This course is intended for personnel directly or indirectly involved in the preparation, review or authorization of drilling and workover programs. This includes: Well engineers and drilling supervisors who are responsible for planning and executing drilling and workover operations. Contractor well engineers, rig managers and other senior drilling staff. Senior well engineers and rig superintendents who are responsible for managing the delivery of a project or well. Technical authority holders who are responsible for licensing drilling and workover operations from a regulatory perspective. Assessment: A satisfactory command of critical knowledge and skills is assured by a 1+ hour closed book assessment. This assessment has a mix of multiple-choice questions (MCQs), calculations and answers that must be written up. The exam is taken electronically. Participants are provided with a suitable formula sheet. The pass mark for issuing a certificate is 70% and participants who are not successful will be issued with a certificate of attendance instead. Trainer Your expert course leader has over 45 years of experience in the Oil & Gas industry. During that time, he has worked exclusively in the well engineering domain. After being employed in 1974 by Shell, one of the major oil & gas producing operators, he worked as an apprentice on drilling rigs in the Netherlands. After a year, he was sent for his first international assignment to the Sultanate of Oman where he climbed up the career ladder from Assistant Driller, to Driller, to wellsite Petroleum Engineer and eventually on-site Drilling Supervisor, actively engaged in the drilling of development and exploration wells in almost every corner of this vast desert area. At that time, drilling techniques were fairly basic and safety was just a buzz word, but such a situation propels learning and the fruits of 'doing-the-basics' are still reaped today when standing in front of a class. After some seven years in the Middle East, a series of other international assignments followed in places like the United Kingdom, Indonesia, Turkey, Denmark, China, Malaysia, and Russia. Apart from on-site drilling supervisory jobs on various types of drilling rigs (such as helicopter rigs) and working environments (such as jungle and artic), he was also assigned to research, to projects and to the company's learning centre. In research, he was responsible for promoting directional drilling and surveying and advised on the first horizontal wells being drilled, in projects, he was responsible for a high pressure drilling campaign in Nigeria while in the learning centre, he looked after the development of new engineers joining the company after graduating from university. He was also involved in international well control certification and served as chairman for a period of three years. In the last years of his active career, he worked again in China as a staff development manager, a position he nurtured because he was able to pass on his knowledge to a vast number of new employees once again. After retiring in 2015, he has delivered well engineering related courses in Australia, Indonesia, Brunei, Malaysia, China, South Korea, Thailand, India, Dubai, Qatar, Kuwait, The Netherlands, and the United States. The training he provides includes well control to obtain certification in drilling and well intervention, extended reach drilling, high pressure-high temperature drilling, stuck pipe prevention and a number of other ad-hoc courses. He thoroughly enjoys training and is keen to continue taking classes as an instructor for some time to come. POST TRAINING COACHING SUPPORT (OPTIONAL) To further optimise your learning experience from our courses, we also offer individualized 'One to One' coaching support for 2 hours post training. We can help improve your competence in your chosen area of interest, based on your learning needs and available hours. This is a great opportunity to improve your capability and confidence in a particular area of expertise. It will be delivered over a secure video conference call by one of our senior trainers. They will work with you to create a tailor-made coaching program that will help you achieve your goals faster. Request for further information post training support and fees applicable Accreditions And Affliations
