- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
7057 Courses near Ewen delivered Live Online
Restorative Justice
By Inclusive Solutions
Restorative Interventions in Schools A “Restorative Solution” is a non-adversarial approach to conflict resolution where the person who has done something wrong in a given situation becomes accountable to those s/he has harmed. This person is then given the opportunity to “make up” for their inappropriate behaviour through agreement and reparation. An intervention can involve a formal conference, or it can be a simple conversation on a corridor or playground. Restorative Interventions work with all ages of young people, and the techniques can be used in parental meetings, can prevent exclusions and challenge poor behaviour. Our feedback tells us that when problems between young people are addressed in this way, those problems rarely reoccur. Course Category Behaviour and Relationships Teaching and Learning Description Restorative Interventions in Schools A “Restorative Solution” is a non-adversarial approach to conflict resolution where the person who has done something wrong in a given situation becomes accountable to those s/he has harmed. This person is then given the opportunity to “make up” for their inappropriate behaviour through agreement and reparation. An intervention can involve a formal conference, or it can be a simple conversation on a corridor or playground. Restorative Interventions work with all ages of young people, and the techniques can be used in parental meetings, can prevent exclusions and challenge poor behaviour. Our feedback tells us that when problems between young people are addressed in this way, those problems rarely reoccur. Also Available on line– self paced learning… give it a try! Testimonials ‘Interesting. A different approach. Another ‘weapon’ in the armoury. Will try to use.’ ‘Made me think how I can approach confrontations differently. Useful, reminded me where my focus should be and that things will be difficult at times, but that’s no excuse to stay in the comfort zone!’ ‘Excellent day. Lots of ideas to take away and use on a daily basis. Thanks.’ ‘Nice to do some work on behaviour without sanctions and restraints in mind’ Learning Objectives To introduce participants to Restorative Interventions To develop understanding of value and role in developing inclusive practice of Restorative Interventions To develop and practise Restorative Intervention skills processes Opportunity to reflect on professional practice Mutual support established with other ‘front line’ practitioners Who Is It For ? Multi Agency Teams Social workers CAMHS teams Year Managers Primary and secondary staff Early Years and School based Practitioners Heads and Deputies SENCOs Advanced Skills Teachers Primary and secondary teachers Local Authority Support Services Course Content This can be introduced in one day or as a workshop but is better offered over a series of sessions. The course answers the questions: What should we do if rewards and punishments do not work? Can we find an alternative process to recommending permanent exclusion or special unit or school placement? Struggling with a child for whom praise and sanctions seem ineffective? Want to develop a more restorative school or team? I need a process which works with relationships not just behaviour. What will work for our relationships policy? This day’s training will enable participants to facilitate Short Restorative Conferences, and will suggest ways of working with young people and others that will help to repair broken relationships, and challenge some difficult behaviour. Including all those affected by an incident in its resolution is a powerful way of producing significant improvements in behaviour. We will cover: What are restorative solutions? Background and detailed teaching of processes Inclusion values underpinning this work Processes modelled and opportunities to try process out Practical setting up of restorative conferences Stories and outcomes

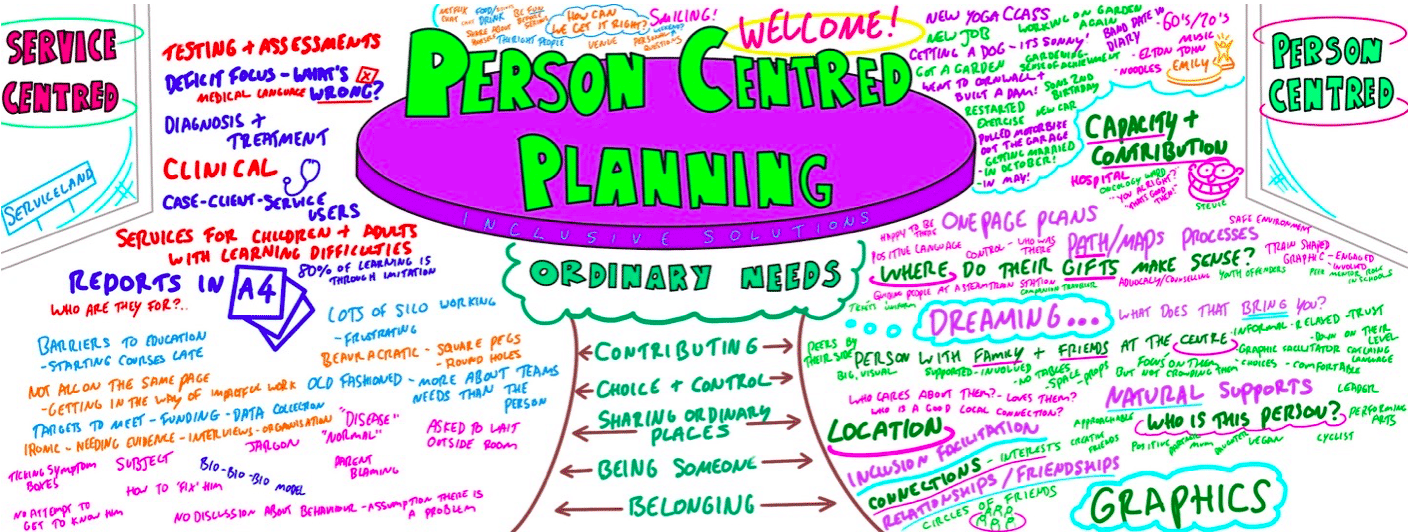
Person Centred Planning using PATH and MAPs
By Inclusive Solutions
What is Person Centred Planning? How is it different to any other kind of meeting or planning? On this day all will become clear… Give your team the opportunity to pause and reflect on what matters most to them about the work they do. The act of listening to each other creates relationship and strengthens trust and inclusion within the team – in creating a shared vision, groups of people build a sense of commitment together. They develop images of ‘the future we want to create together’, along with the values that will be important in getting there and the goals they want to see achieved along the way. Unfortunately, many people still think ’vision’ is the top leader’s job. In schools, the ‘vision task’ usually falls to the Headteacher and/or the governors or it comes in a glossy document from the local authority or the DfES. But visions based on authority are not sustainable. Making inclusive action plans using full participation and graphic facilitation Drawing on the planning tools MAPS and PATH (Pearpoint, Forest and O’Brien 1997) and other facilitation sources we use both process and graphic facilitation to enable the group to build their picture of what they would love to see happening within their organisation/community in the future and we encourage this to be a positive naming, not just a list of the things they want to avoid. Jack Pearpoint, Marsha Forest and John O’Brien developed these innovative approaches in North America and they are being used successfully in many parts of the UK. The planning can focus on an individual, group or organisation and provides a powerful problem solving opportunity, which is flexible and robust enough for many occasions. Tell the story, find the dream, touch the nightmare, and explore who you are, what are the gifts and strengths of the person or group, what are the needs of those present and what is the action plan for the future? Learning objectives Participants understand Person Centred Planning and its values and applications Participants have skills and confidence to facilitate PATH/MAP processes Participants learn graphic as well as process facilitation skills Strengthens practitioners inclusive practice Provides additional tools for those involved in inclusive work in schools and the community Further develop problem solving and planning skills Course Content The course answers the questions: Need to find new ways to bring Pathway Planning alive? Bored with annual reviews, transition plans and review meetings? Want to find a way of making meetings and planning feel more real and engaging? Need an approach, which engages a young person respectfully together with his or her family and friends? Want the ultimate visual record of the process of a meeting, which will help everyone, keep track? Want to problem solve and plan for the future of a small or large group, service or organisation up to the size of an LA? Inclusive Solutions offer an introductory day to person centred planning or a 3 – 10 session course which is practical as well as values based. Participants will receive direct individualised coaching and training. We will cover: The person being at the centre Family members and friends being full partners Planning reflecting the person’s capacities, what is important to the person and specifying the support they require to make a full contribution to their community Planning building a shared commitment to action that will uphold the person’s rights Planning leading to continual listening, learning and action and helping the person get what they want out of life. Essential Lifestyle Planning, PATH MAPS Personal Futures Planning.
Feedback Mastery Unleashed
By Mindset Leadership
Feedback Mastery Unleashed: 28 day online mini-programme to ignite high performance leadership for high achieving teams

Advanced Body Shape Package
By Harley Elite Academy (HeLa)
Expert Body Shape Fillers Package includes: Fat-Dissolving injections – Fillers BBL (Brazilian Buttocks Lift ) with Filler – Non Surgical Threads lift injectables for body Entry requirements Registered Medical professional Level – Beauty Therapist Dental Nurse Physiotherapist Holds at least 6 months experience with needles (micro-needling, microblading, tattooing, vaccinations, phlebotomy and more) NOTE! After booking we will contact you for scheduling the exact course date! Courses dates are subject to change due to mentors availability. We will inform you via email if a date becomes available! Additional information ATTENDANCE ONLINE (Theory), IN CLINIC (Practice) EXPERT LEVEL Fat-Dissolving injections – Fillers BBL (Brazilian Buttocks Lift ) with Filler – Non Surgical PDO Threads lift injectables for body PRP/ Mesotherapy Training Course Choose Online Theory or In-Clinic with practice 4 Days Intensive Courses (1 Week)

Winter Series 2025 - Organisation & Relationship Systems Coaching Training
By CRR UK
CRRUK equips professionals with the concepts, skills and tools to build conscious, intentional relationships, and to coach relationship systems of any size.

COBOL training course description A hands on training course providing an introduction to COBOL. What will you learn Write COBOL programs Debug COBOL programs Examine existing code and determine its function. COBOL training course details Who will benefit: Programmers working with COBOL. Prerequisites: None although experience in another high level language would be useful. A 10 day version of this course would be more applicable for those new to programming. Duration 5 days COBOL training course contents Introduction to COBOL Compilation, linkage editor. Compile errors, compiler options. Divisions, syntax and format, COBOL character set, program structure. COBOL statement structure COBOL words, format of statements. Divisions Identification entries, Environment entries, Data division: FD, record descriptions, hierarchy and level numbers, description-string entry. File and Working-Storage Sections Literals, figurative constants, redefines clause, data representation, Usage clause, synchronization, sign clause. Procedure Division File status codes; Open, Read, Write, Close, Stop, Goback; Accept, display; Move, Justified, data name qualification, reference modification. Perform statement Out-of-line, With test ... Until, ... Times, in-line statement; Go to statement. Program design Design techniques, design considerations, procedure names, program structure. Printing Printed output, Write, advancing option, editing characters; Initialize. Condition testing Conditional statements: IF, class, sign and relation conditions, condition-name conditionals, Set, compound conditions, logical operators. Evaluate, Continue. Arithmetic Rounded option, On Size Error option, Add, Subtract, Multiply, Divide, Compute. Non-sequential files File access modes, Select. Indexed and relative files. Open, Close, creating / reading sequential access files, Write, Read, Invalid key clause, reading, writing / updating Random access files, Rewrite, Delete, Start. Declarative routines Clauses. Subroutines Call, Using clause - calling program/called program, Linkage Section, returning control. Table handling Subscripted tables: One/two/three dimensional tables, Perform, variable length tables. Indexed tables: Set, using an index; Search. Copy code: Copy, Suppress, Replacing. Data Manipulation Inspect, String, Unstring. COBOL/370 LE/370 and Intrinsic Functions.

Microsoft Lync training course description This course teaches IT staff how to plan, design, deploy, configure, and administer a Microsoft Lync Server solution. The course emphasizes Lync Server Enterprise Unified Communications features focussing particularly on coexisting with and migrating from legacy communication services. The labs in this course create a solution that includes IM and Presence, Conferencing, and Persistent Chat. This course helps prepare for Exam 70-336. What will you learn Describe the Lync Server architecture. Install and deploy Lync Server. Use Lync Server management interfaces. Deploy and manage clients. Manage and administer dial-in conferencing. Design audio and video for web conferencing. Plan for instant message and presence Federation. Deploy and configure persistent chat in Lync. Configure archiving and monitoring services. Troubleshoot Lync Server. Describe the required daily, weekly, and monthly maintenance tasks. Use SIP commands and analyze SIP logs. Configure high availability features in Lync. Design load balancing in Lync Server. Backup and restore Lync Server data. Microsoft Lync training course details Who will benefit: Technical staff working with Microsoft Lync. Prerequisites: Supporting Windows 2008 or 2012. Duration 5 days Microsoft Lync training course contents Microsoft Lync Server architecture Lync Server architecture, Lync core capabilities, Lync design process, assessing infrastructure requirements and updating the design, planning for all Microsoft solutions framework phases. Designing a Lync Server topology Infrastructure requirements for Lync Server, using the planning tool, using topology builder, server infrastructure, documentation. Hands on Environment preparation and Lync Server pools. Users and rights in Microsoft Lync Server Managing Lync Server, role based access control. Hands on Using the management shell, configuring role-based access control. Client/device deployment and management Deploy and manage clients, prepare for device deployment, IP phones. Hands on Clients. Conferencing in Lync Server Introduction to conferencing in Lync Server, designing for audio\video and web conferencing, dial-in conferencing in Lync Server, managing and administering conferencing. Hands on Conferencing in Microsoft Lync. Designing and deploying external access Conferencing and external capabilities of Lync Server, planning for IM and presence federation, designing edge services. Hands on Deploying Edge Server and Configuring Remote Access, Validating the Edge Server. Deploying Lync Server persistent chat Overview of persistent chat architecture in Lync Server, designing persistent chat, deploying and persistent chat. Hands on persistent chat server. Monitoring and archiving The archiving service, the monitoring service, configuring archiving and monitoring. Hands on Archiving and monitoring in Lync Server. Administration and maintenance of Lync Lync Server troubleshooting tools, Lync Server operational tasks, Lync Server troubleshooting techniques. Hands on Lync administration tools, centralized logging service, analysing Lync Server logs and traces. High Availability in Lync Server High availability in Lync Server, configuring high availability in Lync Server, planning for load balancing, designing load balancing. Hands on Configuring database mirroring, experiencing a scheduled SQL Server outage, experiencing an unscheduled SQL Server outage. Disaster recovery in Lync Server Disaster recovery in Lync Server, tools for backing up and restoring Lync Server, critical Lync Server data to back up and restore, critical data to export and import, designing branch site resiliency. Hands on Configure pool pairing, experiencing a pool failure or outage. Planning a migration to Lync Server Coexistence and migration, migration steps, planning for clients and devices. Designing a client migration and device migration strategy. Hands on Creating a migration plan, documenting the migration phases.

Complete Visual BASIC training course description A hands-on introduction to programming in Visual BASIC V6. What will you learn Build Visual BASIC applications. Build simple components. Debug Visual BASIC programs. Examine existing code and determine its function. Complete Visual BASIC training course details Who will benefit: Anyone wishing to program in Visual BASIC. Prerequisites: None although experience in another high level language would be useful. Duration 5 days Complete Visual BASIC training course contents Application development using VB VB features. VB editions, VB terminology. Working in the Development Environment. Event-Driven Programming. Creating a program in VB. Project and executable files. VB reference materials. Visual Basic fundamentals Objects. Controlling objects. Introduction to forms. Introduction to controls. Basic controls. Working with code and forms Modules. Working with code. Interacting with the user. Working with code statements. Managing forms. Variables and procedures Introduction to variables and constants. Working with Procedures and Functions. Controlling program execution Common VB functions. Comparison and relational operators. Conditional structures. Looping structures. Debugging Error types. Debugging logic errors in VB. Working with controls Control types. Standard controls. Advanced standard controls. ActiveX controls. Insertable controls. Data access using the ADO data control Overview of ActiveX Data Objects. VB data access features. Relational database concepts. Using the ADO data Control to access data. SQL. Manipulating data. Using the data form wizard. Input validation Field-Level validation. The masked edit control. Form-Level validation. Form events used when validating data. Error trapping Trapping run time errors. Error handling overview. Enabling an error trap. Errors and the calling chain. In line error handling. Enhancing the User Interface Menus. Status bars. Toolbars. Drag and Drop Overview of Drag and Drop. Mouse events Drag and Drop basics. More about controls Using control arrays. Using the controls collection. Working with object variables. Collections. Finishing touches User Interface design principles. Distributing an application. Creating a default project.

Penetration testing training course description An advanced technical hands on course focusing on hacking and counter hacking. The course revolves around a series of exercises based on "hacking" into a network (pen testing the network) and then defending against the hacks. What will you learn Perform penetration tests. Explain the technical workings of various penetration tests. Produce reports on results of penetration tests. Defend against hackers. Penetration testing training course details Who will benefit: Technical support staff, auditors and security professionals. Staff who are responsible for network infrastructure integrity. Prerequisites: IP Security IP VPNs Duration 5 days Penetration testing training course contents Introduction Hacking concepts, phases, types of attacks, 'White hacking', What is penetration testing? Why use pen testing, black box vs. white box testing, equipment and tools, security lifecycles, counter hacking, pen testing reports, methodologies, legal issues. Physical security and social engineering Testing access controls, perimeter reviews, location reviews, alarm response testing. Request testing, guided suggestions, trust testing. Social engineering concepts, techniques, counter measures, Identity theft, Impersonation on social media, Footprints through social engineering Reconnaissance (discovery) Footprinting methodologies, concepts, threats and countermeasures, WHOIS footprinting, Gaining contacts and addresses, DNS queries, NIC queries, ICMP ping sweeping, system and server trails from the target network, information leaks, competitive intelligence. Scanning pen testing. Gaining access Getting past passwords, password grinding, spoofed tokens, replays, remaining anonymous. Scanning (enumeration) Gaining OS info, platform info, open port info, application info. Routes used, proxies, firewalking, Port scanning, stealth port scanning, vulnerability scanning, FIN scanning, Xmas tree scanning, Null scanning, spoofed scanning, Scanning beyond IDS. Enumeration concepts, counter measures and enumeration pen testing. Hacking Hacking webservers, web applications, Wireless networks and mobile platforms. Concepts, threats, methodology, hacking tools and countermeasures. Trojan, Backdoors, Sniffers, Viruses and Worms Detection, concepts, countermeasures, Pen testing Trojans, backdoors, sniffers and viruses. MAC attacks, DHCP attacks, ARP poisoning, DNS poisoning Anti-Trojan software, Malware analysis Sniffing tools. Exploiting (testing) vulnerabilities Buffer overflows,, simple exploits, brute force methods, UNIX based, Windows based, specific application vulnerabilities. DoS/DDoS Concepts, techniques, attack tools, Botnet, countermeasures, protection tools, DoS attack pen testing. SQL Injection Types and testing, Blind SQL Injection, Injection tools, evasion and countermeasures. Securing networks 'Hurdles', firewalls, DMZ, stopping port scans, IDS, Honeypots, Router testing, firewall testing, IDS testing, Buffer Overflow. Cryptography PKI, Encryption algorithms, tools, Email and Disk Encryption. Information security Document grinding, privacy.

Advanced Junos Security training course description This course provides students with intermediate routing knowledge and configuration examples. The course includes an overview of protocol-independent routing features, load balancing and filter-based forwarding, OSPF, BGP, IP tunneling, and high availability (HA) features. Junos Intermediate Routing (JIR) is an intermediate-level course. What will you learn Demonstrate the understanding of integrated user firewall. Implement next generation Layer 2 security features. Implement virtual routing instances in a security setting. Utilize Junos tools for troubleshooting Junos security implementations. Implement IPS policy. Advanced Junos Security training course details Who will benefit: Individuals responsible for implementing, monitoring, and troubleshooting Junos security components. Prerequisites: Intro to the Junos Operating System Duration 5 days Advanced Junos Security training course contents Junos Layer 2 Packet Handling and Security Features Transparent Mode Security Secure Wire Layer 2 Next Generation Ethernet Switching MACsec Lab 2 Implementing Layer 2 Security Virtualization Virtualization Overview Routing Instances Logical Systems Lab 3 Implementing Junos Virtual Routing AppSecure Theory AppSecure Overview AppID Overview AppID Techniques Application System Cache Custom Application Signatures AppSecure Implementation AppTrack AppFW AppQoS APBR SSL Proxy Lab 4 Implementing AppSecure Working with Log Director Log Director Overview Log Director Components Installing and setting up Log Director Clustering with the Log Concentrator VM Administrating Log Director Lab 5 Deploying Log Director Sky ATP Theory Sky ATP Overview Monitoring Sky ATP Analysis and Detection of Malware Sky ATP Implementation Configuring Sky ATP Installing Sky ATP Analysis and detection of Malware Infected Host Case Study Lab 6 Instructor Led Sky ATP Demo Implementing UTM UTM Overview AntiSpam AntiVirus Content and Web Filtering Lab 7 Implementing UTM Introduction to IPS IPS Overview Network Asset Protection Intrusion Attack Methods Intrusion Prevention Systems IPS Inspection Walkthrough IPS Policy and Configuration SRX IPS Requirements IPS Operation Modes Basic IPS Policy Review IPS Rulebase Operations Lab 8 Implementing Basic IPS Policy SDSN SDSN Overview, Components & Configuration Policy Enforcer Troubleshooting SDSN Use Cases Lab 9 Implementing SDSN Enforcement, Monitoring, and Reporting User Role Firewall and Integrated User Firewall Overview User Role Firewall Implementation Monitoring User Role Firewall Integrated User Firewall Implementation Monitoring Integrated User Firewall Lab 10 Configure User Role Firewall and Integrated User Firewall Troubleshooting Junos Security Troubleshooting Methodology Troubleshooting Tools Identifying IPsec Issues Lab 11 Performing Security Troubleshooting Techniques Appendix A: SRX Series Hardware and Interfaces Branch SRX Platform Overview High End SRX Platform Overview SRX Traffic Flow and Distribution SRX Interfaces
