- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
2945 Courses in London delivered Live Online
CWSP training course description A hands-on training course concentrating solely on WiFi security with an emphasis on the delegates learning the necessary knowledge and skills to pass the CWSP exam. The course progresses from simple authentication, encryption and key management onto in depth coverage of 802.X and EAP along with many other security solutions such as access control, intrusion prevention and secure roaming. What will you learn Demonstrate the threats to WiFi networks. Secure WiFi networks. Configure: WPA2 RADIUS 802.1x EAP Pass the CWSP exam. CWSP training course details Who will benefit: Technical network staff. Technical security staff. Prerequisites: Certified Wireless Network Associate. Duration 5 days CWSP training course contents WLAN Security overview Standards, security basics, AAA, 802.11 security history. Hands on WLAN connectivity. Legacy 802.11 security Authentication: Open system, shared key. WEP. VPNs. MAC filters. SSID segmentation, SSID cloaking. Hands on Analysing 802.11 frame exchanges, viewing hidden SSIDs. Encryption Basics, AES, TKIP, CCMP, WPA, WPA2. Hands on Decrypting 802.11 data frames. 802.11 layer 2 authentication 802.1X: Supplicant, Authenticator, Authentication server. Credentials. Legacy authentication. EAP, Weak EAP protocols, Strong EAP protocols: EAP -PEAP, EAP-TTLS, EAP-TLS, EAP-FAST. Hands on Analysing 802.1X/EAP frames. 802.11 layer 2 dynamic key generation Robust Security Network. Hands on Authentication and key management. SOHO 802.11 security WPA/WPA2 personal, Preshared Keys, WiFi Protected Setup (WPS). Hands on PSK mapping. WLAN security infrastructure DS, Autonomous APs, WLAN controllers, split MAC, mesh, bridging, location based access control. Resilience. Wireless network management system. RADIUS/LDAP servers, PKI, RBAC. Hands on 802.1X/EAP configuration. RADIUS configuration. 802.11 Fast secure roaming History, RSNA, OKC, Fast BSS transition, 802.11k. Hands on Roaming. Wireless security risks Rogue devices, rogue prevention. Eavesdropping, DOS attacks. Public access and hotspots. Hands on Backtrack. WiFi security auditing Layer 1 audit, layer 2 audit, pen testing. WLAN security auditing tools. WiFi security monitoring Wireless Intrusion Detection and Prevention Systems. Device classification, WIDS/WIPS analysis. Monitoring. 802.11w. Hands on Laptop spectrum analysers. VPNs, remote access, guest access Role of VPNs in 802.11, remote access, hotspots, captive portal. Wireless security policies General policy, functional policy, recommendations.

AZ-400T00 Designing and Implementing Microsoft DevOps Solutions
By Nexus Human
Duration 4 Days 24 CPD hours This course is intended for Students in this course are interested in designing and implementing DevOps processes or in passing the Microsoft Azure DevOps Solutions certification exam. This course provides the knowledge and skills to design and implement DevOps processes and practices. Students will learn how to plan for DevOps, use source control, scale Git for an enterprise, consolidate artifacts, design a dependency management strategy, manage secrets, implement continuous integration, implement a container build strategy, design a release strategy, set up a release management workflow, implement a deployment pattern, and optimize feedback mechanisms Prerequisites Successful learners will have prior knowledge and understanding of: Cloud computing concepts, including an understanding of PaaS, SaaS, and IaaS implementations. Both Azure administration and Azure development with proven expertise in at least one of these areas. Version control, Agile software development, and core software development principles. It would be helpful to have experience in an organization that delivers software. AZ-104T00 - Microsoft Azure Administrator AZ-204T00: Developing Solutions for Microsoft Azure 1 - Introduction to DevOps What is DevOps? Explore the DevOps journey Identify transformation teams Explore shared goals and define timelines 2 - Choose the right project Explore greenfield and brownfield projects Decide when to use greenfield and brownfield projects Decide when to use systems of record versus systems of engagement Identify groups to minimize initial resistance Identify project metrics and key performance indicators (KPIs) 3 - Describe team structures Explore agile development practices Explore principles of agile development Define organization structure for agile practices Explore ideal DevOps team members Enable in-team and cross-team collaboration Select tools and processes for agile practices 4 - Choose the DevOps tools What is Azure DevOps? What is GitHub? Explore an authorization and access strategy Migrate or integrate existing work management tools Migrate or integrate existing test management tools Design a license management strategy 5 - Plan Agile with GitHub Projects and Azure Boards Link GitHub to Azure Boards Configure GitHub Projects Manage work with GitHub Project boards Customize Project views Collaborate using team discussions Agile Plan and Portfolio Management with Azure Boards 6 - Introduction to source control Explore DevOps foundational practices What is source control? Explore benefits of source control Explore best practices for source control 7 - Describe types of source control systems Understand centralized source control Understand distributed source control Explore Git and Team Foundation Version Control Examine and choose Git Understand objections to using Git Describe working with Git locally 8 - Work with Azure Repos and GitHub Migrate from TFVC to Git Use GIT-TFS Develop online with GitHub Codespaces 9 - Structure your Git Repo Explore monorepo versus multiple repos Implement a change log 10 - Manage Git branches and workflows Explore branch workflow types Explore feature branch workflow Explore Git branch model for continuous delivery Explore GitHub flow Explore fork workflow Version Control with Git in Azure Repos 11 - Collaborate with pull requests in Azure Repos Collaborate with pull requests Examine GitHub mobile for pull request approvals 12 - Identify technical debt Examine code quality Examine complexity and quality metrics Measure and manage technical debt Integrate other code quality tools Plan effective code reviews 13 - Explore Git hooks Implement Git hooks 14 - Plan foster inner source Explore foster inner source Implement the fork workflow Describe inner source with forks 15 - Manage Git repositories Work with large repositories Purge repository data Manage releases with GitHub Repos Automate release notes with GitHub 16 - Explore Azure Pipelines Explore the concept of pipelines in DevOps Describe Azure Pipelines Understand Azure Pipelines key terms 17 - Manage Azure Pipeline agents and pools Choose between Microsoft-hosted versus self-hosted agents Explore job types Explore predefined agent pool Understand typical situations for agent pools Communicate with Azure Pipelines Communicate to deploy to target servers Examine other considerations Describe security of agent pools Configure agent pools and understanding pipeline styles 18 - Describe pipelines and concurrency Understand parallel jobs Estimate parallel jobs Describe Azure Pipelines and open-source projects Explore Azure Pipelines and Visual Designer Describe Azure Pipelines and YAML 19 - Explore continuous integration Learn the four pillars of continuous integration Explore benefits of continuous integration Describe build properties Enable Continuous Integration with Azure Pipelines 20 - Implement a pipeline strategy Configure agent demands Implement multi-agent builds Explore source control types supported by Azure Pipelines 21 - Integrate with Azure Pipelines Describe the anatomy of a pipeline Understand the pipeline structure Detail templates Explore YAML resources Use multiple repositories in your pipeline 22 - Introduction to GitHub Actions What are Actions? Explore Actions flow Understand workflows Describe standard workflow syntax elements Explore events Explore jobs Explore runners Examine release and test an action 23 - Learn continuous integration with GitHub Actions Describe continuous integration with actions Examine environment variables Share artifacts between jobs Examine Workflow badges Describe best practices for creating actions Mark releases with Git tags Create encrypted secrets Use secrets in a workflow Implement GitHub Actions for CI/CD 24 - Design a container build strategy Examine structure of containers Work with Docker containers Understand Dockerfile core concepts Examine multi-stage dockerfiles Examine considerations for multiple stage builds Explore Azure container-related services Deploy Docker containers to Azure App Service web apps 25 - Introduction to continuous delivery Explore traditional IT development cycle What is continuous delivery? Move to continuous delivery Understand releases and deployments Understand release process versus release 26 - Create a release pipeline Describe Azure DevOps release pipeline capabilities Explore release pipelines Explore artifact sources Choose the appropriate artifact source Examine considerations for deployment to stages Explore build and release tasks Explore custom build and release tasks Explore release jobs Configure Pipelines as Code with YAML 27 - Explore release recommendations Understand the delivery cadence and three types of triggers Explore release approvals Explore release gates Use release gates to protect quality Control Deployments using Release Gates 28 - Provision and test environments Provision and configure target environments Configure automated integration and functional test automation Understand Shift-left Set up and run availability tests Explore Azure Load Testing Set up and run functional tests 29 - Manage and modularize tasks and templates Examine task groups Explore variables in release pipelines Understand variable groups 30 - Automate inspection of health Automate inspection of health Explore events and notifications Explore service hooks Configure Azure DevOps notifications Configure GitHub notifications Explore how to measure quality of your release process Examine release notes and documentation Examine considerations for choosing release management tools Explore common release management tools 31 - Introduction to deployment patterns Explore microservices architecture Examine classical deployment patterns Understand modern deployment patterns 32 - Implement blue-green deployment and feature toggles What is blue-green deployment? Explore deployment slots Describe feature toggle maintenance 33 - Implement canary releases and dark launching Explore canary releases Examine Traffic Manager Understand dark launching 34 - Implement A/B testing and progressive exposure deployment What is A/B testing? Explore CI-CD with deployment rings 35 - Integrate with identity management systems Integrate GitHub with single sign-on (SSO) Explore service principals Explore Managed Identity 36 - Manage application configuration data Rethink application configuration data Explore separation of concerns Understand external configuration store patterns Examine Key-value pairs Examine App configuration feature management Integrate Azure Key Vault with Azure Pipelines Manage secrets, tokens and certificates Examine DevOps inner and outer loop Integrate Azure Key Vault with Azure DevOps Enable Dynamic Configuration and Feature Flags 37 - Explore infrastructure as code and configuration management Explore environment deployment Examine environment configuration Understand imperative versus declarative configuration Understand idempotent configuration 38 - Create Azure resources using Azure Resource Manager templates Why use Azure Resource Manager templates? Explore template components Manage dependencies Modularize templates Manage secrets in templates Deployments using Azure Bicep templates 39 - Create Azure resources by using Azure CLI What is Azure CLI? Work with Azure CLI 40 - Explore Azure Automation with DevOps Create automation accounts What is a runbook? Understand automation shared resources Explore runbook gallery Examine webhooks Explore source control integration Explore PowerShell workflows Create a workflow Examine checkpoint and parallel processing 41 - Implement Desired State Configuration (DSC) Understand configuration drift Explore Desired State Configuration (DSC) Explore Azure Automation State configuration (DSC) Examine DSC configuration file Explore hybrid management Implement DSC and Linux Automation on Azure 42 - Implement Bicep What is Bicep? Install Bicep Understand Bicep file structure and syntax 43 - Introduction to Secure DevOps Describe SQL injection attack Understand DevSecOps Explore Secure DevOps Pipeline Explore key validation points Explore continuous security validation Understand threat modeling 44 - Implement open-source software Explore how software is built What is open-source software Explore corporate concerns with open-source software components Explore common open-source licenses Examine license implications and ratings 45 - Software Composition Analysis Inspect and validate code bases for compliance Explore software composition analysis (SCA) Integrate Mend with Azure Pipelines Implement GitHub Dependabot alerts and security updates Integrate software composition analysis checks into pipelines Examine tools for assess package security and license rate Interpret alerts from scanner tools Implement security and compliance in an Azure Pipeline 46 - Static analyzers Explore SonarCloud Explore CodeQL in GitHub Manage technical debt with SonarCloud and Azure DevOps 47 - OWASP and Dynamic Analyzers Plan Implement OWASP Secure Coding Practices Explore OWASP ZAP penetration test Explore OWASP ZAP results and bugs 48 - Security Monitoring and Governance Implement pipeline security Explore Microsoft Defender for Cloud Examine Microsoft Defender for Cloud usage scenarios Explore Azure Policy Understand policies Explore initiatives Explore resource locks Explore Azure Blueprints Understand Microsoft Defender for Identity 49 - Explore package dependencies What is dependency management? Describe elements of a dependency management strategy Identify dependencies Understand source and package componentization Decompose your system Scan your codebase for dependencies 50 - Understand package management Explore packages Understand package feeds Explore package feed managers Explore common public package sources Explore self-hosted and SaaS based package sources Consume packages Publish packages Package management with Azure Artifacts 51 - Migrate consolidating and secure artifacts Identify existing artifact repositories Migrate and integrating artifact repositories Secure access to package feeds Examine roles Examine permissions Examine authentication 52 - Implement a versioning strategy Understand versioning of artifacts Explore semantic versioning Examine release views Promote packages Explore best practices for versioning 53 - Introduction to GitHub Packages Publish packages Install a package Delete and restore a package Explore package access control and visibility 54 - Implement tools to track usage and flow Understand the inner loop Explore Azure Monitor and Log Analytics Examine Kusto Query Language (KQL) Explore Application Insights Implement Application Insights Monitor application performance with Application Insights 55 - Develop monitor and status dashboards Explore Azure Dashboards Examine view designer in Azure Monitor Explore Azure Monitor workbooks Explore Power BI Build your own custom application 56 - Share knowledge within teams Share acquired knowledge within development teams Integrate with Azure Boards Share team knowledge using Azure Project Wiki 57 - Design processes to automate application analytics Explore rapid responses and augmented search Integrate telemetry Examine monitoring tools and technologies 58 - Manage alerts, blameless retrospectives and a just culture Examine when get a notification Explore how to fix it Explore smart detection notifications Improve performance Understand server response time degradation Reduce meaningless and non-actionable alerts Examine blameless retrospective Develop a just culture

55371 Windows Server Administration
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for This course is intended for Information Technology (IT) Professionals who have some experience working with Windows Server and are looking for a single five-day course that covers core administration components and technologies in Windows Server. This course also helps server administrators from previous Windows Server versions to update their knowledge and skills related to Windows Server. The course is also for individuals from a service desk role who wish to transition into server maintenance. This five-day instructor-led course is designed primarily for IT professionals who have some experience with Windows Server. It is designed for professionals who will be responsible for managing identity, networking, storage and compute by using Windows Server, and who need to understand the scenarios, requirements, and options that are available and applicable to Windows Server. The course teaches IT professionals the fundamental administration skills required to deploy and support Windows Server in most organizations. Module 1: Windows Server Administration Overview Introducing Windows Server Windows Server Core Overview Windows Server administration principles and tools overview Module 2: Identity Services in Windows Server AD DS Overview Deploying Windows Server domain controllers Azure AD overview Implementing Group Policy Active Directory Certificate Services overview Module 3: Network Infrastructure services in Windows Server Deploying and managing DHCP Deploying and managing DNS service Deploying and managing IPAM Remote Access Services in Windows Server Module 4: File Servers and Storage management in Windows Server Volumes and File Systems in Windows Server Implementing sharing in Windows Server Implementing Storage Spaces in Windows Server Implementing Data Deduplication Implementing iSCSI Deploying Distributed File System Module 5: Hyper-V virtualization and containers in Windows Server Hyper-V in Windows Server Configuring VMs Securing virtualization in Windows Server Containers in Windows Server Overview of Kubernetes Module 6: High Availability in Windows Server Planning for failover clustering implementation Creating and configuring failover cluster Overview of stretch clusters High availability and disaster recovery solutions with Hyper-V VMs Module 7: Disaster recovery in Windows Server Hyper-V Replica Backup and restore infrastructure in Windows Server Module 8: Windows Server security Credentials and privileged access protection Hardening Windows Server JEA in Windows Server Securing and analyzing SMB traffic Windows Server update management Module 9: RDS in Windows Server Overview of RDS Configuring a session-based desktop deployment Overview of personal and pooled virtual desktops Module 10: Remote access and web services in Windows Server Implementing VPNs Implementing Always On VPN Implementing NPS Implementing Web Server in Windows Server Module 11: Server and performance monitoring in Windows Server Overview of Windows Server monitoring tools Using Performance Monitor Monitoring event logs for troubleshooting Module 12: Upgrade and migration in Windows Server AD DS migration Storage Migration Service Windows Server migration tools Additional course details: Nexus Humans 55371 Windows Server Administration training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the 55371 Windows Server Administration course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

CompTIA Advanced Security Practitioner (CASP+)
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for This course is targeted toward an IT Professional that has the technical knowledge and skills required to conceptualize, design, and engineer secure solutions across complex enterprise environments. Students should have a minimum of 10 years experience including at least 5 years of hands-on technical security experience. Overview Upon successful completion of this course, students will be able to: Identify enterprise security fundamentals. Apply enterprise security technology solutions. Implement security design and solutions. Manage risk, policies and procedures within an enterprise. Integrate security solutions within an enterprise. Conduct security research and analysis. In this course, students will examine advanced security concepts, principles, and implementations that pertain to enterprise level security. Prerequisites CompTIA Cybersecurity Analyst (CySA+) Certification 1 - Enterprise Security Architecture The Basics of Enterprise Security The Enterprise Structure Enterprise Security Requirements 2 - Enterprise Security Technology Common Network Security Components and Technologies Communications and Collaboration Security Cryptographic Tools and Techniques Advanced Authentication 3 - Enterprise Resource Technology Enterprise Storage Security Issues Distributed, Shared, and Virtualized Computing Cloud Computing and Security 4 - Security Design and Solutions Network Security Design Conduct a Security Assessment Host Security 5 - Application Security Design Application Security Basics Web Application Security 6 - Managing Risk, Security Policies, and Security Procedures Analyze Security Risk Implement Risk Mitigation Strategies and Controls Implement Enterprise-Level Security Policies and Procedures Prepare for Incident Response and Recovery 7 - Enterprise Security Integration The Technology Life Cycle Inter-Organizational Change Integrate Enterprise Disciplines to Achieve Secure Solutions 8 - Security Research and Analysis Perform an Industry Trends and Impact Analysis Perform an Enterprise Security Analysis

Level 4 Dental Practice Management
By Cavity Dental Training
Unlock Your Potential as a Dental Practice Manager with Our Level 4 Course The Level 4 Diploma in Dental Practice Management qualification delivered by Cavity Training has been designed as a standalone qualification or as an apprenticeship qualification for anyone wishing to become a qualified practice manager. Candidates are required to be in a work placement in order to be able to commence the qualification. Learn about the Cavity Training Dental Practice Management course This qualification allows candidates to learn, develop and practice the skills required for employment and a career in Dental Practice Management. The content covers all essential areas of Management and is mapped to the GDC Learning Outcomes for Dental Nurses and relevant National Occupational Standards. This qualification is approved by the GDC. This qualification allows candidates to go on to higher level 5 management courses and expand their management career. Fees This course can be completed as an government funded apprenticeship, through Cavity Training, or as a privately funded course for £3500. You can either pay as a lump sum or alternatively, you can split into 12 instalments. Entry requirements The minimum requirements are level 2 in English and Maths. Structure To achieve the Level 4 Diploma in Dental Practice Management, candidates will need to also successfully complete a final online Knowledge Test. This is a 24 month course, with a final end point assessment. Knowledge Our course is delivered via live training webinars with specialist tutors. Skills and Behaviours You will be appointed a designated Assessor, who will coach you through your qualification and complete regular assessments with you to support you to complete your qualification. You will have weekly contact from your Assessor. How we compare with our competitors? Don't just take our word for it, here is what our staff think Bridget I did my course years ago. It was classroom based one night per week. I think I would prefer to be more ‘hands on’ like it is now. Cavity really are a great company to work for. I truly believe that there expertise will ensure the next generation are amazing! Gina I did mine over an apprenticeship but the company my employer used wasn’t great and I didn’t get much support. Although I passed I can only imagine the length that Cavity have gone to to ensure that the students feel supported. As an employee, its super! Enquire Today

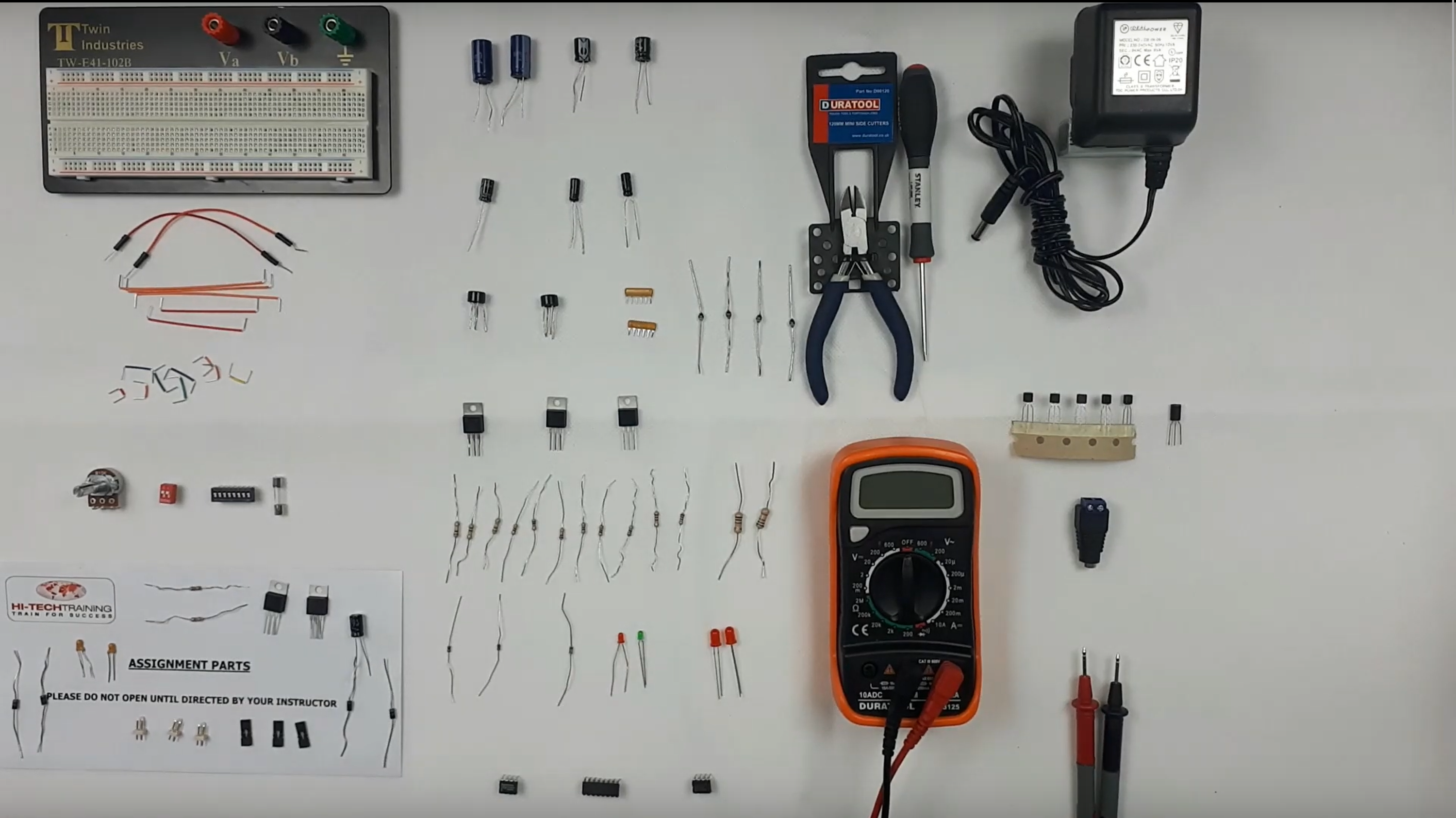
Electronics Repair 2 Course
By Hi-Tech Training
Electronics Equipment Repair 2 (Online Virtual Classroom) is a follow on course to Electronics Equipment Repair 1. This course builds on the skills gained and enables participants to build, test and fault-find more complex Analogue Electronic circuits
The Postgraduate Certificate (PG Cert.) consists of the first four modules from the MA Business of Motorsport Master’s Degree. You can then achieve a Postgraduate Diploma (PG Dip.) Business of Motorsport by studying the PG Dip. Top-Up, a further three modules from the MA.

Level 3 Certificate in Supporting Teaching and Learning
By Step Into Learning
This course is aimed at those who would like to work as a learning support assistant in a school or further education setting. Level 3 Certificate in Supporting Teaching and Learning will give you an understanding of the skills and knowledge needed to support learners in the classroom.

Oracle Database 12c Admin training course description This Oracle Database 12c Administration course is designed to give the Oracle database administrator practical experience in administering, monitoring, tuning and troubleshooting an Oracle 12c database. Database administrators will gain an understanding of the architecture and processes of the Oracle database server. They will be able to ensure the integrity and availability of a company's data within the Oracle environment. They will be able to monitor the performance of the database, allocate resources with the Resource Manager and Schedule jobs. What will you learn Administer an Oracle database instance. Monitor an Oracle database. Configure the Oracle network environment. Create and manage database storage structures. Manage users, profiles, privileges and roles. Manage undo data and temporary segments. Monitor and resolve lock conflicts. Maintain database security. Implement database auditing. Monitor the performance of the Database. Load and unload data. Use the job scheduler. Configure a database for backup and recovery. Oracle Database 12c Admin training course details Who will benefit: This Oracle Database 12c Administration course is for anyone who needs to administer, monitor and support an Oracle 12c database. Prerequisites: An understanding of relational database concepts and good operating system knowledge. They should have attended the Oracle SQL course or have a good working knowledge of Oracle SQL. Knowledge of the usage of PL/SQL packages is highly recommended. Duration 5 days Oracle Database 12c Admin training course contents Introduction to Oracle database 12c Overview of the Oracle database 12c, Overview of the Oracle Cloud, Relational database concepts, database administration tasks. Oracle Database 12c Architecture Overview of the Oracle database architecture, The Oracle database instance, Oracle Database memory structures, Process architecture and structures, Server and client processes, The Oracle database storage architecture, Connect to the Oracle database instance. Administer a database instance Administrative tools available to a DBA, Use SQL*Plus in Oracle to manage a database instance, Use SQL Developer to manage a database instance, Administer the database using Enterprise Manager (EM), Overview of the Enterprise Manager framework, Access Enterprise Manager Database Express, The Enterprise Manager Database Express Home Page, Enterprise Manager Cloud Control, Initialization parameter files. Configure the Oracle network environment Overview of network configuration, Oracle Net Listener configuration and management, Oracle Net naming methods, Tools for configuring and managing the Oracle network, Using the Net Configuration Assistant, Configure client connections with Net Manager, View listener configuration, Start and stop the Oracle listener, Use TNSPING to test Oracle Net connectivity, Connect to the database, Configure Net Services with Enterprise Manager. Storage Structures Overview of data storage, The database block, Overview of tablespaces and datafiles, Use Enterprise Manager to view the storage structure of the database, Create and alter tablespace commands, Temporary tablespaces, Create and manage datafiles, Use OMF, Drop tablespaces and datafiles. Manage users Predefined database administration accounts, User accounts, Create a user account, User authentication, Change a user's password, Manage a user account, Drop a user account, Monitor user information, Terminate user sessions. Manage profiles and resources Overview of user profiles, Profile resource parameters, Create profile command, Manage passwords with profiles, Control resource usage with profiles, Maintain profiles. Manage privileges Database access, Oracle supplied roles, System and object level privileges, The grant and revoke commands, Create, modify and drop roles, Use predefined roles. Database auditing Overview of database security, Overview of database auditing, Security compliance, Standard auditing, Unified audit trail, Separation of audit responsibilities with the AUDIT_ADMIN and AUDIT_VIEWER roles, Configure the audit trail, Specify audit options. Data concurrency and lock conflicts Levels of locking in Oracle, Methods used to acquire locks, Data concurrency, Possible causes of contention, DML locks, Prevent locking problems, Detect lock contention, Resolve conflicts. Undo management Undo data overview, Monitor and administer undo, Configure undo retention, Switch undo tablespaces, Specify the retention period, Guarantee undo retention, Retention period for flashback queries, View undo space information, Use the undo advisor, Size the undo tablespace, Alter an undo tablespace to a fixed size. Proactive database management Database Maintenance, View the alert log, The Automatic Workload Repository, Statistic levels, The Automatic Database Diagnostic Monitoring, Monitor an Oracle database, Use the Advisors, Set up notification rules/ Performance management Tuning information sources, Performance monitoring, Tuning activities, Performance planning, Instance tuning, Performance tuning methodology, Performance tuning data, Monitoring performance, Managing memory. SQL tuning SQL tuning, The Oracle Optimizer, SQL Plan directives, Adaptive execution plans, SQL Advisors, Automatic SQL Tuning results, Implement automatic tuning recommendations , SQL Tuning Advisor. Moving data Create directory objects , Data Pump architecture, Data Pump data dictionary views, Data Pump interactive mode, Data Pump API, Use Data Pump to export and import data, Overview of SQL Loader, Command line parameters, Record filtering, Control file keywords, Datafiles, SQL Loader data paths, External Tables. Automate tasks with the scheduler Introduction to the Scheduler, Access Rights, Scheduler components and workflow, Create a Job, Job Classes, Use time based, event based schedules, Create an event based schedule. Managing resources with Resource Manager Overview of the Database Resource Manage, Use the Resource Manager, Create Resource Plans, The default maintenance resource manager plan, Create Resource Plan Directives, Allocate resources for Resource Plans. Manage space Overview of space management, Block space management within segments, Segment types, Allocate extents, Allocate space, Row chaining and migration, Create tables without segments. Backup and recovery configuration Oracle backup solutions, Oracle suggested backup strategy, Overview of database backup, restore and recover, Flashback technology, Types of failure ,Instance recovery, Tune instance recovery, The MTTR Advisor, Media failure, Configure a database for recoverability Oracle support The Enterprise Manager Support Workbench, Register for security updates, Work with Oracle Support, My Oracle Support integration, Log Service Requests, Manage patches, Apply a patch

WCNA training course description Wireshark is a free network protocol analyser. This hands-on course provides a comprehensive tour of using Wireshark to troubleshoot networks. The course concentrates on the information needed in order to pass the WCNA exam. Students will gain the most from this course only if they already have a sound knowledge of the TCP/IP protocols. What will you learn Analyse packets and protocols in detail. Troubleshoot networks using Wireshark. Find performance problems using Wireshark. Perform network forensics. WCNA training course details Who will benefit: Technical staff looking after networks. Prerequisites: TCP/IP Foundation for engineers Duration 5 days WCNA training course contents What is Wireshark? Network analysis, troubleshooting, network traffic flows. Hands on Download/install Wireshark. Wireshark introduction Capturing packets, libpcap, winpcap, airpcap. Dissectors and plugins. The menus. Right click. Hands on Using Wireshark. Capturing traffic Wireshark and switches and routers. Remote traffic capture. Hands on Capturing packets. Capture filters Applying, identifiers, qualifiers, protocols, addresses, byte values. File sets, ring buffers. Hands on Capture filters. Preferences Configuration folders. Global and personal configurations. Capture preferences, name resolution, protocol settings. Colouring traffic. Profiles. Hands on Customising Wireshark. Time Packet time, timestamps, packet arrival times, delays, traffic rates, packets sizes, overall bytes. Hands on Measuring high latency. Trace file statistics Protocols and applications, conversations, packet lengths, destinations, protocol usages, strams, flows. Hands on Wireshark statistics. Display filters Applying, clearing, expressions, right click, conversations, endpoints, protocols, combining filters, specific bytes, regex filters. Hands on Display traffic. Streams Traffic reassembly, UDP and TCP conversations, SSL. Hands on Recreating streams. Saving Filtered, marked and ranges. Hands on Export. TCP/IP Analysis The expert system. DNS, ARP, IPv4, IPv6, ICMP, UDP, TCP. Hands on Analysing traffic. IO rates and trends Basic graphs, Advanced IO graphs. Round Trip Time, throughput rates. Hands on Graphs. Application analysis DHCP, HTTP, FTP, SMTP. Hands on Analysing application traffic. WiFi Signal strength and interference, monitor mode and promiscuous mode. Data, management and control frames. Hands on WLAN traffic. VoIP Call flows, Jitter, packet loss. RTP, SIP. Hands on Playing back calls. Performance problems Baselining. High latency, arrival times, delta times. Hands on Identifying poor performance. Network forensics Host vs network forensics, unusual traffic patterns, detecting scans and sweeps, suspect traffic. Hands on Signatures. Command line tools Tshark, capinfos, editcap, mergecap, text2pcap, dumpcap. Hands on Command tools.
