- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
300 Courses in Cardiff delivered Live Online
BSc (Hons) Health and Social Care Top-Up- Inclusive of Level 4 and 5 Pathway Diploma
By School of Business and Technology London
Getting Started The BSc in Health and Social Care is a comprehensive undergraduate program designed to equip students with the knowledge and skills necessary for success in the healthcare and social services sectors. This programme covers essential health, well-being, and social support topics, ensuring that graduates are well-prepared for fulfilling careers in these vital fields. Anglia Ruskin University offers the BSc (Hons) Health and Social Care program, a highly regarded undergraduate degree providing students with a deep understanding of the dynamic and crucial health and social care sectors. This program is tailored to equip students with the knowledge and skills essential for excelling in various roles within these sectors. The curriculum strongly emphasises integrating theory and practice, enabling students to develop the essential competencies required for effective healthcare and social work delivery. A standout feature of this program is its strong emphasis on real-world experience through placements and practical training, ensuring that graduates are well-prepared to tackle the challenges within the healthcare and social care sectors. Additionally, Anglia Ruskin University's distinguished reputation in healthcare education and research enhances the value of this program, making it an excellent choice for individuals aspiring to make a meaningful impact in these critical fields. The programme comprises two phases; the first is the Qualifi Level 4 and 5 Diploma in Health and Social Care, awarded by Qualifi and delivered by the School of Business and Technology London. The second phase is the BSc (Hons) Health and Social Care Top Up, awarded and delivered 100% online by Anglia Ruskin University. At Anglia Ruskin University, you will study through Canvas, a world-class online Learning Management System (LMS), accessed from your phone, pc or tablet at home or on the move. Canvas provides instant access to study materials, forums, and support from tutors and classmates, as well as enabling easy submission of your assignments. After successfully completing your studies, you'll be invited to attend a graduation ceremony on campus at Anglia Ruskin University. If attending the ceremony in person is not possible, we'll arrange to send your certificate to you. School of Business and Technology London partners with Chestnut Education Group to promote this programme. About Awarding Body Anglia Ruskin University began in 1858 as the Cambridge School of Art founded by William Beaumont. It was then merged with the Cambridge shire College of Arts and Technology and the Essex Institute of Higher Education and was renamed Anglia Polytechnic. It was then given university status in 1992 and renamed Anglia Ruskin University in 2005. The university has campuses in the UK (Cambridge, Chelmsford, London and Peterborough), as well as they are partnered with institutions around the world including Berlin, Budapest, Trinidad, Singapore and Kuala Lumpur. Assessment Assignments and Project No examinations Entry Requirements A Level or Equivalent Minimum 1 Year of Health and Social care work experience Further, candidates are also required to demonstrate their English language proficiency. Learners must request before enrolment to interchange unit(s) other than the preselected units shown in the SBTL website because we need to make sure the availability of learning materials for the requested unit(s). SBTL will reject an application if the learning materials for the requested interchange unit(s) are unavailable. Learners are not allowed to make any request to interchange unit(s) once enrolment is complete. Structure Phase 1 - Qualifi Level 4 and 5 Diploma in Health and Social Care Programme Structure Level 4 - Modules The QUALIFI Level 4 Diploma in Health and Social Care comprises 120 credits, equating to 1200 hours of TQT and 600 hours of GLH. The diploma requires six mandatory units at Level 4. Academic Study skills Reference No: T/505/9498 Credit: |20| TQT: 200 The primary objective of this unit is to equip individuals with the essential skills and knowledge required for effective higher education study, fostering the development of reflective and critical thinking abilities necessary for reaching their maximum learning potential and potentially advancing to the Level 5 Diploma in Health and Social Care. Communicating in Health and Social Care Reference No: H/505/9495 Credit: |20| TQT: 200 This unit aims to cultivate the learner's understanding of the various modes of communication utilised in health and social care settings and underscore their importance in ensuring efficient service delivery. An Introduction to Healthcare Policy Reference No : F/505/9505 Credit: |20| TQT: 200 This unit seeks to enhance the learner's awareness of the diverse factors influencing healthcare and their impact on policy development. Evaluating healthcare policies will enable learners to scrutinise the crucial contemporary concerns facing policy-makers, service providers, and support recipients. Reflective Practice Reference No : F/505/9519 Credit: |20| TQT: 200 Introducing learners to reflective practice in all its forms is the focus of this unit. Reflecting on and in practice holds significance in health and social care, promoting self-development and linking theoretical concepts to practical application. Managing people in Health and Social Care Reference No : L/505/9507 Credit: |20| TQT: 200 The primary objective of this unit is to provide learners with an understanding of the processes involved in the recruitment, management, and development of personnel in the health and social care workplace. Learners will investigate the procedures governing the management of individuals in this sector and explore how to instigate organisational change. Sociology: Concepts in Health and Social Care Reference No : M/505/9502 Credit: |20| TQT: 200 This unit aims to impart to learners an understanding of sociological concepts related to health and illness and their practical application in health and social care. It will enable learners to comprehend the nature of contemporary society and its influence on the perception of health and illness. Learners will delve into the structural aspects of culture, such as age, gender, ethnicity, social class, family, and households, and their impact on health and well-being. Level 5 - Modules The Level 5 Diploma is made up of 120 credits, which equates to 1200 hours of TQT and includes 500 hours of GLH. The Diploma requires five mandatory units at Level 5. Principles Underpinning Health and Social Care Reference No : K/505/9496 Credit: |20| TQT: 200 Health and social care professionals must adhere to specific ethical and professional standards. This course module is designed to foster comprehension of the principles, theories, and regulations that form the foundation of health and social care practice. It also explores the various tools and systems in place to uphold high standards of practice within the industry. The Management of Quality in Health and Social Care Reference No : A/505/9521 Credit: |20| TQT: 200 Quality plays a significant role in the realm of health and social care. In this unit, students will acquire insight into diverse viewpoints concerning the quality of health and social care services and the methods used to evaluate them. This knowledge aims to empower and involve service users in the process. Research Project Reference No : H/505/9500 Credit: |40| TQT: 400 The primary objective of this unit is to enhance students' research abilities, encouraging them to conduct a concise pilot study that directly pertains to their higher education program or career advancement. This endeavour aims to cultivate independent inquiry and critical analysis skills. Partnership working in Health and Social Care Reference No : A/505/9499 Credit: |20| TQT: 200 In this unit, students will grasp the significance of establishing favourable professional relationships in health and social care. The module will delve into the concept of partnership on three distinct levels: Collaboration with service users. Cooperation among health and social care practitioners. Engagement with organisations. Understanding these aspects will empower individuals to make informed choices and advocate for autonomy. Working with Service users with Complex Needs Reference No : T/505/9520 Credit: |20| TQT: 200 This course module aims to equip learners with insights into matters concerning health, disability, and illness. It further enables them to recognise effective strategies for assisting individuals with intricate physical and mental health requirements in their roles as healthcare professionals. Phase 2 - BSc (Hons) Health and Social Care Programme Structure Leadership Practice in Health and Social Care Evaluating Research for Evidence-Based Practice Strategic Management in Health and Social Care Undergraduate Major Project Delivery Methods The programme comprises two phases; the first is the Qualifi Level 4 and 5 Diploma in Health and Social Care, awarded by Qualifi and delivered by the School of Business and Technology London. The School of Business and Technology London offers flexible learning methods, including online and blended learning, allowing students to choose the mode of study that suits their preferences and schedules. The program is self-paced and facilitated through an advanced Learning Management System. Students can easily interact with tutors through the SBTL Support Desk Portal System for course material discussions, guidance, assistance, and assessment feedback on assignments. School of Business and Technology London provides exceptional support and infrastructure for online and blended learning. Students benefit from dedicated tutors who guide and support them throughout their learning journey, ensuring a high level of assistance. The second phase is the BSc (Hons) Health and Social Care Top Up, awarded and delivered 100% online by Anglia Ruskin University. At Anglia Ruskin University, you will study through Canvas, a world-class online Learning Management System (LMS), accessed from your phone, pc or tablet at home or on the move. Canvas provides instant access to study materials, forums, and support from tutors and classmates, as well as enabling easy submission of your assignments. After successfully completing your studies, you'll be invited to attend a graduation ceremony on campus at Anglia Ruskin University. If attending the ceremony in person is not possible, we'll arrange to send your certificate to you. School of Business and Technology London partners with Chestnut Education Group to promote this programme. Resources and Support School of Business & Technology London is dedicated to offering excellent support on every step of your learning journey. School of Business & Technology London occupies a centralised tutor support desk portal. Our support team liaises with both tutors and learners to provide guidance, assessment feedback, and any other study support adequately and promptly. Once a learner raises a support request through the support desk portal (Be it for guidance, assessment feedback or any additional assistance), one of the support team members assign the relevant to request to an allocated tutor. As soon as the support receives a response from the allocated tutor, it will be made available to the learner in the portal. The support desk system is in place to assist the learners adequately and streamline all the support processes efficiently. Quality learning materials made by industry experts is a significant competitive edge of the School of Business & Technology London. Quality learning materials comprised of structured lecture notes, study guides, practical applications which includes real-world examples, and case studies that will enable you to apply your knowledge. Learning materials are provided in one of the three formats, such as PDF, PowerPoint, or Interactive Text Content on the learning portal. How does the Online Learning work at SBTL? We at SBTL follow a unique approach which differentiates us from other institutions. Indeed, we have taken distance education to a new phase where the support level is incredibly high.Now a days, convenience, flexibility and user-friendliness outweigh demands. Today, the transition from traditional classroom-based learning to online platforms is a significant result of these specifications. In this context, a crucial role played by online learning by leveraging the opportunities for convenience and easier access. It benefits the people who want to enhance their career, life and education in parallel streams. SBTL's simplified online learning facilitates an individual to progress towards the accomplishment of higher career growth without stress and dilemmas. How will you study online? With the School of Business & Technology London, you can study wherever you are. You finish your program with the utmost flexibility. You will be provided with comprehensive tutor support online through SBTL Support Desk portal. How will I get tutor support online? School of Business & Technology London occupies a centralised tutor support desk portal, through which our support team liaise with both tutors and learners to provide guidance, assessment feedback, and any other study support adequately and promptly. Once a learner raises a support request through the support desk portal (Be it for guidance, assessment feedback or any additional assistance), one of the support team members assign the relevant to request to an allocated tutor. As soon as the support receive a response from the allocated tutor, it will be made available to the learner in the portal. The support desk system is in place to assist the learners adequately and to streamline all the support process efficiently. Learners should expect to receive a response on queries like guidance and assistance within 1 - 2 working days. However, if the support request is for assessment feedback, learners will receive the reply with feedback as per the time frame outlined in the Assessment Feedback Policy.

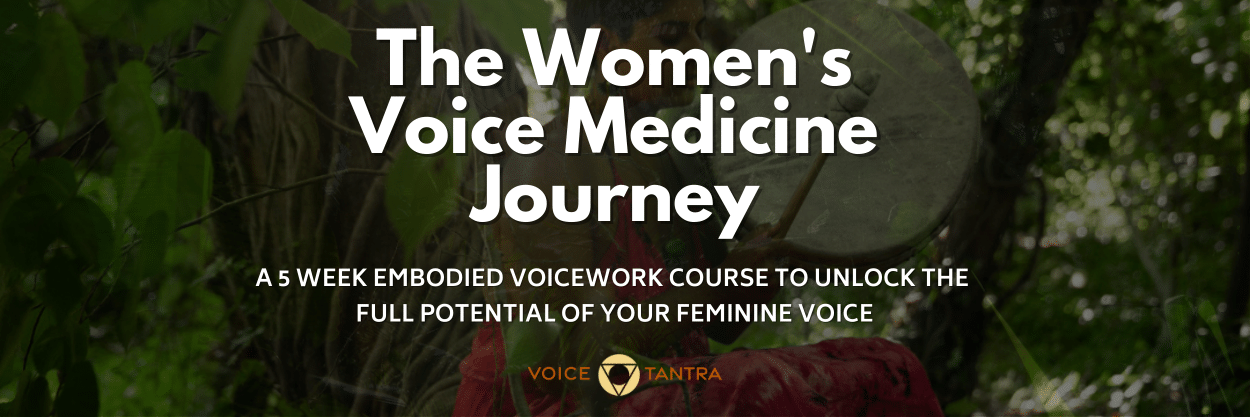
Welcome to the Women's Voice Medicine Journey. This is a female-designed, step-by-step programe, to teach you how you can truly activate and integrate some of the most essential Embodied Voicework tools to Free Your Voice and unleash your Creative Feminine Power.
DIPLOMA IN GAME DESIGN AND DEVELOPMENT One to One Online or Face to Face
By Real Animation Works
Face to face training customised and bespoke. Professional tutors. One to One Online or Face to Face

Welcome to the Women's Voice Medicine Journey. This is a female-designed, new, step-by-step guide, to teach you how you can truly activate and integrate some of the most essential Voicework tools to Free Your Voice and unleash your Creative Feminine Power.

MS-102T00 Microsoft 365 Administrator Essentials
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for This course is designed for persons aspiring to the Microsoft 365 Administrator role and have completed at least one of the Microsoft 365 role-based administrator certification paths. This course covers the following key elements of Microsoft 365 administration: Microsoft 365 tenant management, Microsoft 365 identity synchronization, and Microsoft 365 security and compliance. In Microsoft 365 tenant management, you learn how to configure your Microsoft 365 tenant, including your organizational profile, tenant subscription options, component services, user accounts and licenses, security groups, and administrative roles. You then transition to configuring Microsoft 365, with a primary focus on configuring Office client connectivity. Finally, you explore how to manage user-driven client installations of Microsoft 365 Apps for enterprise deployments. The course then transitions to an in-depth examination of Microsoft 365 identity synchronization, with a focus on Microsoft Entra Connect and Connect Cloud Sync. You learn how to plan for and implement each of these directory synchronization options, how to manage synchronized identities, and how to implement password management in Microsoft 365 using multifactor authentication and self-service password management. In Microsoft 365 security management, you begin examining the common types of threat vectors and data breaches facing organizations today. You then learn how Microsoft 365?s security solutions address each of these threats. You are introduced to the Microsoft Secure Score, as well as to Microsoft Entra ID Protection. You then learn how to manage the Microsoft 365 security services, including Exchange Online Protection, Safe Attachments, and Safe Links. Finally, you are introduced to the various reports that monitor an organization?s security health. You then transition from security services to threat intelligence; specifically, using Microsoft 365 Defender, Microsoft Defender for Cloud Apps, and Microsoft Defender for Endpoint. Once you have this understanding of Microsoft 365?s security suite, you then examine the key components of Microsoft 365 compliance management. This begins with an overview of all key aspects of data governance, including data archiving and retention, Microsoft Purview message encryption, and data loss prevention (DLP). You then delve deeper into archiving and retention, paying particular attention to Microsoft Purview insider risk management, information barriers, and DLP policies. You then examine how to implement these compliance features by using data classification and sensitivity labels. Prerequisites Completed a role-based administrator course such as Messaging, Teamwork, Security, Compliance, or Collaboration. A proficient understanding of DNS and basic functional experience with Microsoft 365 services. A proficient understanding of general IT practices. A working knowledge of PowerShell. 1 - Configure your Microsoft 365 experience Explore your Microsoft 365 cloud environment Configure your Microsoft 365 organizational profile Manage your tenant subscriptions in Microsoft 365 Integrate Microsoft 365 with customer engagement apps Complete your tenant configuration in Microsoft 365 2 - Manage users, licenses, and mail contacts in Microsoft 365 Determine the user identity model for your organization Create user accounts in Microsoft 365 Manage user account settings in Microsoft 365 Manage user licenses in Microsoft 365 Recover deleted user accounts in Microsoft 365 Perform bulk user maintenance in Microsoft Entra ID Create and manage guest users Create and manage mail contacts 3 - Manage groups in Microsoft 365 Examine groups in Microsoft 365 Create and manage groups in Microsoft 365 Create dynamic groups using Azure rule builder Create a Microsoft 365 group naming policy Create groups in Exchange Online and SharePoint Online 4 - Add a custom domain in Microsoft 365 Plan a custom domain for your Microsoft 365 deployment Plan the DNS zones for a custom domain Plan the DNS record requirements for a custom domain Create a custom domain in Microsoft 365 5 - Configure client connectivity to Microsoft 365 Examine how automatic client configuration works Explore the DNS records required for client configuration Configure Outlook clients Troubleshoot client connectivity 6 - Configure administrative roles in Microsoft 365 Explore the Microsoft 365 permission model Explore the Microsoft 365 admin roles Assign admin roles to users in Microsoft 365 Delegate admin roles to partners Manage permissions using administrative units in Microsoft Entra ID Elevate privileges using Microsoft Entra Privileged Identity Management Examine best practices when configuring administrative roles 7 - Manage tenant health and services in Microsoft 365 Monitor the health of your Microsoft 365 services Monitor tenant health using Microsoft 365 Adoption Score Monitor tenant health using Microsoft 365 usage analytics Develop an incident response plan Request assistance from Microsoft 8 - Deploy Microsoft 365 Apps for enterprise Explore Microsoft 365 Apps for enterprise functionality Explore your app compatibility by using the Readiness Toolkit Complete a self-service installation of Microsoft 365 Apps for enterprise Deploy Microsoft 365 Apps for enterprise with Microsoft Configuration Manager Deploy Microsoft 365 Apps for enterprise from the cloud Deploy Microsoft 365 Apps for enterprise from a local source Manage updates to Microsoft 365 Apps for enterprise Explore the update channels for Microsoft 365 Apps for enterprise Manage your cloud apps using the Microsoft 365 Apps admin center 9 - Analyze your Microsoft 365 workplace data using Microsoft Viva Insights Examine the analytical features of Microsoft Viva Insights Explore Personal insights Explore Team insights Explore Organization insights Explore Advanced insights 10 - Explore identity synchronization Examine identity models for Microsoft 365 Examine authentication options for the hybrid identity model Explore directory synchronization 11 - Prepare for identity synchronization to Microsoft 365 Plan your Microsoft Entra deployment Prepare for directory synchronization Choose your directory synchronization tool Plan for directory synchronization using Microsoft Entra Connect Plan for directory synchronization using Microsoft Entra Connect cloud sync 12 - Implement directory synchronization tools Configure Microsoft Entra Connect prerequisites Configure Microsoft Entra Connect Monitor synchronization services using Microsoft Entra Connect Health Configure Microsoft Entra Connect cloud sync prerequisites Configure Microsoft Entra Connect cloud sync 13 - Manage synchronized identities Manage users with directory synchronization Manage groups with directory synchronization Use Microsoft Entra Connect Sync Security Groups to help maintain directory synchronization Configure object filters for directory synchronization Explore Microsoft Identity Manager Troubleshoot directory synchronization 14 - Manage secure user access in Microsoft 365 Manage user passwords Enable pass-through authentication Enable multifactor authentication Enable passwordless sign-in with Microsoft Authenticator Explore self-service password management Explore Windows Hello for Business Implement Microsoft Entra Smart Lockout Implement conditional access policies Explore Security Defaults in Microsoft Entra ID Investigate authentication issues using sign-in logs 15 - Examine threat vectors and data breaches Explore today's work and threat landscape Examine how phishing retrieves sensitive information Examine how spoofing deceives users and compromises data security Compare spam and malware Examine account breaches Examine elevation of privilege attacks Examine how data exfiltration moves data out of your tenant Examine how attackers delete data from your tenant Examine how data spillage exposes data outside your tenant Examine other types of attacks 16 - Explore the Zero Trust security model Examine the principles and components of the Zero Trust model Plan for a Zero Trust security model in your organization Examine Microsoft's strategy for Zero Trust networking Adopt a Zero Trust approach 17 - Explore security solutions in Microsoft 365 Defender Enhance your email security using Exchange Online Protection and Microsoft Defender for Office 365 Protect your organization's identities using Microsoft Defender for Identity Protect your enterprise network against advanced threats using Microsoft Defender for Endpoint Protect against cyber attacks using Microsoft 365 Threat Intelligence Provide insight into suspicious activity using Microsoft Cloud App Security Review the security reports in Microsoft 365 Defender 18 - Examine Microsoft Secure Score Explore Microsoft Secure Score Assess your security posture with Microsoft Secure Score Improve your secure score Track your Microsoft Secure Score history and meet your goals 19 - Examine Privileged Identity Management Explore Privileged Identity Management in Microsoft Entra ID Configure Privileged Identity Management Audit Privileged Identity Management Control privileged admin tasks using Privileged Access Management 20 - Examine Azure Identity Protection Explore Azure Identity Protection Enable the default protection policies in Azure Identity Protection Explore the vulnerabilities and risk events detected by Azure Identity Protection Plan your identity investigation 21 - Examine Exchange Online Protection Examine the anti-malware pipeline Detect messages with spam or malware using Zero-hour auto purge Explore anti-spoofing protection provided by Exchange Online Protection Explore other anti-spoofing protection Examine outbound spam filtering 22 - Examine Microsoft Defender for Office 365 Climb the security ladder from EOP to Microsoft Defender for Office 365 Expand EOP protections by using Safe Attachments and Safe Links Manage spoofed intelligence Configure outbound spam filtering policies Unblock users from sending email 23 - Manage Safe Attachments Protect users from malicious attachments by using Safe Attachments Create Safe Attachment policies using Microsoft Defender for Office 365 Create Safe Attachments policies using PowerShell Modify an existing Safe Attachments policy Create a transport rule to bypass a Safe Attachments policy Examine the end-user experience with Safe Attachments 24 - Manage Safe Links Protect users from malicious URLs by using Safe Links Create Safe Links policies using Microsoft 365 Defender Create Safe Links policies using PowerShell Modify an existing Safe Links policy Create a transport rule to bypass a Safe Links policy Examine the end-user experience with Safe Links 25 - Explore threat intelligence in Microsoft 365 Defender Explore Microsoft Intelligent Security Graph Explore alert policies in Microsoft 365 Run automated investigations and responses Explore threat hunting with Microsoft Threat Protection Explore advanced threat hunting in Microsoft 365 Defender Explore threat analytics in Microsoft 365 Identify threat issues using Microsoft Defender reports 26 - Implement app protection by using Microsoft Defender for Cloud Apps Explore Microsoft Defender Cloud Apps Deploy Microsoft Defender for Cloud Apps Configure file policies in Microsoft Defender for Cloud Apps Manage and respond to alerts in Microsoft Defender for Cloud Apps Configure Cloud Discovery in Microsoft Defender for Cloud Apps Troubleshoot Cloud Discovery in Microsoft Defender for Cloud Apps 27 - Implement endpoint protection by using Microsoft Defender for Endpoint Explore Microsoft Defender for Endpoint Configure Microsoft Defender for Endpoint in Microsoft Intune Onboard devices in Microsoft Defender for Endpoint Manage endpoint vulnerabilities with Microsoft Defender Vulnerability Management Manage device discovery and vulnerability assessment Reduce your threat and vulnerability exposure 28 - Implement threat protection by using Microsoft Defender for Office 365 Explore the Microsoft Defender for Office 365 protection stack Investigate security attacks by using Threat Explorer Identify cybersecurity issues by using Threat Trackers Prepare for attacks with Attack simulation training 29 - Examine data governance solutions in Microsoft Purview Explore data governance and compliance in Microsoft Purview Protect sensitive data with Microsoft Purview Information Protection Govern organizational data using Microsoft Purview Data Lifecycle Management Minimize internal risks with Microsoft Purview Insider Risk Management Explore Microsoft Purview eDiscovery solutions 30 - Explore archiving and records management in Microsoft 365 Explore archive mailboxes in Microsoft 365 Enable archive mailboxes in Microsoft 365 Explore Microsoft Purview Records Management Implement Microsoft Purview Records Management Restore deleted data in Exchange Online Restore deleted data in SharePoint Online 31 - Explore retention in Microsoft 365 Explore retention by using retention policies and retention labels Compare capabilities in retention policies and retention labels Define the scope of a retention policy Examine the principles of retention Implement retention using retention policies, retention labels, and eDiscovery holds Restrict retention changes by using Preservation Lock 32 - Explore Microsoft Purview Message Encryption Examine Microsoft Purview Message Encryption Configure Microsoft Purview Message Encryption Define mail flow rules to encrypt email messages Add organizational branding to encrypted email messages Explore Microsoft Purview Advanced Message Encryption 33 - Explore compliance in Microsoft 365 Plan for security and compliance in Microsoft 365 Plan your beginning compliance tasks in Microsoft Purview Manage your compliance requirements with Compliance Manager Examine the Compliance Manager dashboard Analyze the Microsoft Compliance score 34 - Implement Microsoft Purview Insider Risk Management Explore insider risk management Plan for insider risk management Explore insider risk management policies Create insider risk management policies Investigate insider risk management activities and alerts Explore insider risk management cases 35 - Implement Microsoft Purview Information Barriers Explore Microsoft Purview Information Barriers Configure information barriers in Microsoft Purview Examine information barriers in Microsoft Teams Examine information barriers in OneDrive Examine information barriers in SharePoint 36 - Explore Microsoft Purview Data Loss Prevention Examine Data Loss Prevention Explore Endpoint data loss prevention Examine DLP policies View DLP policy results Explore DLP reports 37 - Implement Microsoft Purview Data Loss Prevention Plan to implement Microsoft Purview Data Loss Protection Implement Microsoft Purview's default DLP policies Design a custom DLP policy Create a custom DLP policy from a template Configure email notifications for DLP policies Configure policy tips for DLP policies 38 - Implement data classification of sensitive information Explore data classification Implement data classification in Microsoft 365 Explore trainable classifiers Create and retrain a trainable classifier View sensitive data using Content explorer and Activity explorer Detect sensitive information documents using Document Fingerprinting 39 - Explore sensitivity labels Manage data protection using sensitivity labels Explore what sensitivity labels can do Determine a sensitivity label's scope Apply sensitivity labels automatically Explore sensitivity label policies 40 - Implement sensitivity labels Plan your deployment strategy for sensitivity labels Examine the requirements to create a sensitivity label Create sensitivity labels Publish sensitivity labels Remove and delete sensitivity labels Additional course details: Nexus Humans MS-102T00: Microsoft 365 Administrator training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the MS-102T00: Microsoft 365 Administrator course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Welcome to the Women's Voice Empowerment Programme. This is a female-designed, new, step-by-step guide, to teach you how you can truly activate and integrate some of the most essential Voicework tools to Free Your Voice and unleash your Creative Feminine Power.

CMI Level 7 Diploma in Strategic Management and Leadership with MBA Top Up
By School of Business and Technology London
Getting Started This course is designed for those learners who have completed or are planning to pursue their CMI Level 7 Diploma in Strategic Management and Leadership and wish to proceed with an MBA at Anglia Ruskin University. Since there is no direct pathway to Anglia Ruskin University's MBA Top Up program after the CMI Level 7 Diploma in Strategic Management and Leadership, we have introduced a Bridge module (Strategic Leadership and Organisational Transformation), which will be delivered at the School of Business and Technology London. The programme CMI Level 7 Diploma in Strategic Management and Leadership and the Bridge Module are delivered by the School of Business and Technology. The MBA Top Up is delivered and awarded online by Anglia Ruskin University. At Anglia Ruskin University, you will study through Canvas, a world-class online Learning Management System (LMS), accessed from your phone, PC or tablet at home or on the move. Canvas provides instant access to study materials, forums, and support from tutors and classmates, as well as enabling easy submission of your assignments. After successfully completing your studies, you'll be invited to attend a graduation ceremony on campus at Anglia Ruskin University. If attending the ceremony in person is not possible, we'll arrange to send your certificate to you. The duration of the whole program is 12-15 months. School of Business and Technology London partners with Chestnut Education Group to promote this programme. How it works? Once a learner successfully completes CMI Level 7 Management and Leadership and the Bridge Module - Strategic Leadership and Organisational Transformation, we will transfer the credits to Qualifi, an ofqual.gov.uk regulated awarding body for the programme Qualifi Level 7 Strategic Management and Leadership. Upon credit transfer, learners will receive a certificate and transcript from Qualifi for Level 7 Diploma in Strategic Management and Leadership with 120 credits, which will be used as a pathway for MBA Top Up. Key Benefits The qualification aims to improve your strategic management skills and techniques. The knowledge gained through the qualification will assist you in your role as a strategic manager in your workplace. You will be enabled to apply theories and models in your practical work scenarios, enhancing your problem-solving skills that can be applied to your working environment. It is a nationally accredited qualification, and the credits gained through this course can be transferred to other universities or other awarding bodies. You will be able to manage problems in your workplace more effectively, boosting the career prospectus. About Awarding Body Chartered Management Institute established over 60 years ago as the British Institute of Management back then; it has developed the UK's very first diploma in management studies. In the years that followed CMI has consistently been at the forefront of all aspects of management and leadership. Today CMI is the only chartered professional awarding body committed to offering the highest standards in management and leadership excellence. Presently over 100,000 managers use its unique services daily. CMI qualifications aim for managers and leaders at any level, and it remains the only Awarding Body which can award Chartered Manager status - the ultimate management accolade. Employers highly value the qualifications awarded by CMI, and boost your career prospects. Anglia Ruskin University began in 1858 as the Cambridge School of Art founded by William Beaumont. It was then merged with the Cambridge shire College of Arts and Technology and the Essex Institute of Higher Education and was renamed Anglia Polytechnic. It was then given university status in 1992 and renamed Anglia Ruskin University in 2005. The university has campuses in the UK (Cambridge, Chelmsford, London and Peterborough), as well as they are partnered with institutions around the world including Berlin, Budapest, Trinidad, Singapore and Kuala Lumpur. Entry Requirements Learners from age 21 and over. The learners should possess 3 Years of middle management experience or two years of senior management experience. The learner should have the ability to complete the Level 7 Qualification Learners must request before enrolment to interchange unit(s) other than the preselected units shown in the SBTL website because we need to make sure the availability of learning materials for the requested unit(s). SBTL will reject an application if the learning materials for the requested interchange unit(s) are unavailable. Learners are not allowed to make any request to interchange unit(s) once enrolment is complete. Structure Stage 1 - CMI Level 7 Diploma in Strategic Management and Leadership This is the first stage of this whole program. CMI Diploma qualification is designed for individuals wishing to develop strategic management and leadership practices who will have the knowledge, skills and behaviours to drive business activities in a senior, regional, specialist, director or CEO management and leadership role. The qualification contains a breadth of units, which reflect the tasks and activities required by managers in roles such as senior managers, regional management and specialist managers who are accountable to a senior manager or business owner. The CMI Level 7 Diploma in Strategic Management and Leadership is delivered by School of Business and Technology London and awarded by CMI. The qualifications have been designed for practising or aspiring managers in roles such as: Senior Manager Regional Manager Specialist Manager (with expertise in a specific business or technical function such as quality, finance, risk, marketing, sales IT, human resources etc.) Director CEO Module Structure UNIT1- Strategic Risk Management This unit aims for leaders to develop an in-depth understanding of strategic risk management. Leaders will critically appraise strategic risk within an organisational context. They will assess strategies for risk management and the leadership skills to lead risk initiatives successfully. Ultimately, leaders will be allowed to develop a framework to deliver a risk strategy in an organisational context. UNIT2- Strategic Leadership This unit aims to equip leaders with an in-depth understanding of strategic leadership within an organisational context. Leaders will explore the complexities of the role and the theoretical perspectives, approaches, behaviours and skills which can enhance their professional practice. The unit focuses on the leader's ability to respond creatively to complex organisational challenges and understand how to set and deliver sustainable strategic goals. UNIT3- Collaboration and Partnerships The unit aims for leaders to understand collaborative and partnership arrangements. Leaders will critically assess the scope and value of these and evaluate the impact of organisational and legal frameworks on how these arrangements are delivered. The unit culminates in the requirement for the leader to present a rationale for collaboration or partnerships to further an organisation's success. UNIT4- Developing Organisational Strategy The aim of this unit is to enable leaders to know how to develop and influence an organisation's strategic direction through the development of a meaningful strategy. To support this outcome, leaders will critique the factors driving organisational strategy development and appraise approaches to successfully develop strategy. The unit culminates in leaders developing an organisational strategy to achieve a business goal. To complement this activity, leaders will propose an approach to implement and monitor the strategy developed to ensure its sustained success. UNIT5- Entrepreneurial Practice This unit aims to enable leaders to explore the principles of entrepreneurial practice, understand the different contexts in which entrepreneurship can flourish, and the characteristics of entrepreneurial leadership. Assessment Learners are required to submit time-constrained, scenario-based assignments for each unit of the level 7 diploma. There will not be any examinations. Stage 2 - Bridge Module - Strategic Leadership and Organisational Transformation Now the second stage is to complete the Bridge Module. This module is about leadership at strategic level and the role of transformational leaders as catalysts for change in their organisations and whole industries. The module, therefore, focuses on two but clearly intertwined elements of strategic leadership and organisational transformation. Effective strategic leadership is a facilitator for organisational success. Leaders have to be knowledgeable, creative, agile and resilient to respond to organisational need in the contemporary workplace. This unit aims to equip leaders with an in-depth understanding of strategic leadership within an organisational context. Leaders will explore the complexities of the role and the theoretical perspectives, approaches, behaviours and skills which can enhance their professional practice. The unit focuses on the leader's ability to respond creatively to complex organisational challenges and understand how to set and deliver sustainable strategic goals. By studying this module, you should better understand their own leadership, or of the leadership in places of work and the changes that could take place to create a more effective leadership. Aim of the Unit Students are expected to develop many management/leadership skills that can be transferrable for use in other modules on the course and are essential in the workplace. Students are advised to refer to some leadership theories, which enables them to undertake the tasks given throughout the module. The notes formulated in response to these tasks will lead to you gaining formative feedback for your individual development. Assessment As an individual, you will electronically submit a 5000-word assignment, which consists of a two-part report comprising of (i) a critical review of academic material (2,500 words) and (ii) a critical appraisal, evaluation and justification of change within an International organisation (2,500 words). Stage 3 - MBA - Top Up The final stage is enrolling for the Top Up programme delivered online by Anglia Ruskin University. This professional qualification improves the chances of progression in a career path. This qualification helps the learner to oversee, supervise and allocate the operations in a business firm. The program aims to make the candidate capable of understanding the functional aspects of a company and acquiring the skills for communication and decision making. This programme from the renowned UK university is well acknowledged and globally respected as it dominates critical thinking and research. MBA can also help you specialise in a new industry you want to move to or in your current sector. Assessment The course requires you to submit a final Consultancy Project Report, which is treated as an assessment and would be scrutinised and reviewed by the verifiers externally. Delivery Methods The program comprises three stages; the first is Stage 1 - CMI Level 7 Diploma in Strategic Management and Leadership awarded by CMI and delivered by School of Business and Technology London. The second stage is the Bridge Module - Strategic Leadership and Organisational Transformation delivered by School of Business and Technology London. The School of Business and Technology London offers flexible learning methods, including online and blended learning, allowing students to choose the mode of study that suits their preferences and schedules. The program is self-paced and facilitated through an advanced Learning Management System. Students can easily interact with tutors through the SBTL Support Desk Portal System for course material discussions, guidance, assistance, and assessment feedback on assignments. School of Business and Technology London provides exceptional support and infrastructure for online and blended learning. Students benefit from dedicated tutors who guide and support them throughout their learning journey, ensuring a high level of assistance. The third stage is the MBA Top Up, delivered and awarded online by Anglia Ruskin University. At Anglia Ruskin University, you will study through Canvas, a world-class online Learning Management System (LMS), accessed from your phone, PC or tablet at home or on the move. Canvas provides instant access to study materials, forums, and support from tutors and classmates, as well as enabling easy submission of your assignments. After successfully completing your studies, you'll be invited to attend a graduation ceremony on campus at Anglia Ruskin University. If attending the ceremony in person is not possible, we'll arrange to send your certificate to you. School of Business and Technology London partners with Chestnut Education Group to promote this programme. Resources and Support School of Business & Technology London is dedicated to offering excellent support on every step of your learning journey. School of Business & Technology London occupies a centralised tutor support desk portal. Our support team liaises with both tutors and learners to provide guidance, assessment feedback, and any other study support adequately and promptly. Once a learner raises a support request through the support desk portal (Be it for guidance, assessment feedback or any additional assistance), one of the support team members assign the relevant to request to an allocated tutor. As soon as the support receives a response from the allocated tutor, it will be made available to the learner in the portal. The support desk system is in place to assist the learners adequately and streamline all the support processes efficiently. Quality learning materials made by industry experts is a significant competitive edge of the School of Business & Technology London. Quality learning materials comprised of structured lecture notes, study guides, practical applications which includes real-world examples, and case studies that will enable you to apply your knowledge. Learning materials are provided in one of the three formats, such as PDF, PowerPoint, or Interactive Text Content on the learning portal. How does the Online Learning work at SBTL? We at SBTL follow a unique approach which differentiates us from other institutions. Indeed, we have taken distance education to a new phase where the support level is incredibly high.Now a days, convenience, flexibility and user-friendliness outweigh demands. Today, the transition from traditional classroom-based learning to online platforms is a significant result of these specifications. In this context, a crucial role played by online learning by leveraging the opportunities for convenience and easier access. It benefits the people who want to enhance their career, life and education in parallel streams. SBTL's simplified online learning facilitates an individual to progress towards the accomplishment of higher career growth without stress and dilemmas. How will you study online? With the School of Business & Technology London, you can study wherever you are. You finish your program with the utmost flexibility. You will be provided with comprehensive tutor support online through SBTL Support Desk portal. How will I get tutor support online? School of Business & Technology London occupies a centralised tutor support desk portal, through which our support team liaise with both tutors and learners to provide guidance, assessment feedback, and any other study support adequately and promptly. Once a learner raises a support request through the support desk portal (Be it for guidance, assessment feedback or any additional assistance), one of the support team members assign the relevant to request to an allocated tutor. As soon as the support receive a response from the allocated tutor, it will be made available to the learner in the portal. The support desk system is in place to assist the learners adequately and to streamline all the support process efficiently. Learners should expect to receive a response on queries like guidance and assistance within 1 - 2 working days. However, if the support request is for assessment feedback, learners will receive the reply with feedback as per the time frame outlined in the Assessment Feedback Policy.

Linux engineer certification training course description LPIC-2 is the second certification in LPI's multi level professional certification program. This course teaches the skills necessary to pass the LPI 201 exam; the first of two LPIC-2 exams. Specifically, the course covers the administration of Linux systems in small to medium sized mixed networks. What will you learn Perform advanced administration tasks. Perform advanced file system administration. Linux engineer certification training course details Who will benefit: Linux administrators. Prerequisites: Linux system administration (LPIC-1) Duration 5 days Linux engineer certification fundamentals training course contents Part I The LPI 201 Exam Starting a System The Linux Boot Process, Firmware Startup, BIOS Startup, UEFI Startup, Linux Bootloaders, GRUB Legacy, GRUB 2, Alternative Bootloaders, Secure Bootloaders, Process Initialization, SysV Method, systemd Method, Upstart Method, System Recovery, Kernel Failures, Root Drive Failure. Maintaining the System Fluid Messaging, Static Messaging, System backups, Backup Strategies, Performing Backups, Installing Programs from Source, Obtaining and unpacking Installation Files, Compiling Programs, Resource Usage: Managing, measuring, predicting and troubleshooting. Mastering the Kernel What Is the Kernel? Kernel Features, Parts of the Kernel, Kernel Versions, Obtaining Source Code, Creating the Configuration File, Compiling and Installing the Kernel, Compiling and Installing Modules, Creating an Initial RAM Disk, Booting the New Kernel, Creating a Kernel Package, Maintaining the Kernel, Working with Module Files, Module Commands, Working with Hardware, Automatically Detecting Hardware, Troubleshooting the Kernel. Managing the Filesystem The Linux Filesystem, Filesystem Structures, Filesystem Types, Making Filesystems, Attaching Filesystems, Memory-Based Linux Filesystems, the Btrfs Filesystem, Btrfs Subvolumes, Btrfs Snapshots, Optical Filesystems, Swap Filesystems, Network-Based Filesystems, Auto-Mounting, Encrypted Filesystems, Maintaining Linux Filesystems, Adjusting a Filesystem, Checking and Repairing a Filesystem, SMART. Administering Advanced Storage Devices Configuring RAID, Implementing RAID on Linux, Managing a RAID Array, Adjusting Storage Devices, Looking at Drive Interface Concepts, Testing and Tuning Drives, Implementing iSCSI, Managing Logical Volumes, LVM, Creating Logical Volumes, Supporting Logical Volumes, Understanding the Device Mapper. Navigating Network Services Networking Basics, The Physical Layer, The Network Layer, The Transport Layer, The Application Layer, Configuring Network Features, Network Configuration Files, Graphical Tools, Command-Line Tools, Basic Network Troubleshooting, Checking the Log Files, the ARP Cache, Sending Test Packets, Testing Network Routes, Testing Client/Server Connectivity, Finding Host Information, Network Security, Advanced Network Troubleshooting, Viewing Open Network Connections, Viewing Network Statistics, Scanning the Network, Capturing Network Traffic.

SMTP training course description A hands on course focusing on the workings of email systems and the standard protocols that they use. The course is not specific to any particular implementation, but some vendor specifics are noted. Linux and Microsoft machines are used in hands on sessions to reinforce the theory of major sessions. The course concentrates on troubleshooting and interworking using network sniffing and protocol inspection rather than "which buttons to push". What will you learn Describe and explain SMTP MIME POP3 IMAP PGP, GPG, S/MIME SPF, DKIM, DMARC Configure mail routing Secure email systems SMTP training course details Who will benefit: Technical staff responsible for email systems. Prerequisites: TCP/IP foundation for engineers. Duration 3 days SMTP training course contents SMTP architecture What is SMTP, email before SMTP, SMTP history, the different protocols, clients, servers. Email composition, transmission, delivering emails, storing and reading emails. MUAs, MTAs, POP3, IMAP, SMTP, DNS, webmail. Hands on Setting up MTAs and MUAs and sending a simple email using telnet. The SMTP protocol SMTP protocol stack, SMTP headers, HELO, SMTP mail, MAIL FROM, RCPT TO, DATA, SMTPUTF8, 8BITMIME, TURN, EHLO, ETRN, 3 digit replies. Hands on Analysing SMTP packets on a network. DNS and SMTP SMTP forwarding, SMTP relays, interoperation, how SMTP uses DNS, MX records. Hands on Setting up mail relays. SMTP headers IMF data, From, to, cc, bcc, sender and recipient headers, message Ids, received trails, in-reply-to, received-SPF, mail list headers. Hands on Using clients to analyse details from mail headers, including true originators and path of emails. MIME Email attachments, MIME versions, content type headers, encoding, base 64, binary data, multi part headers, troubleshooting attachments. Hands on Analysing MIME headers and attachments. POP3 What is POP3, where to use POP3, authorisation, transactions, POP3 commands: USER, PASS, STAT, LIST, RETR, DELE. Hands on Setting up a POP3 server, analysing POP3 packets on a network. IMAP and IMAPS What is IMAP, where to use IMAP, authorisation, mailbox structure, IMAP commands: LOGIN, AUTHENTICATE, LIST, CREATE, Examine (message flags), SELECT, STORE. Hands on Setting up an IMAP server and analysing IMAP packets on a network. Interoperation Mail gateways, addressing, Exchange, sendmail. Email security Basics, Transport level: STARTTLS. Content: PGP/GPG, mail signing and encryption, S/MIME, digital certificates, secure email submission. Hands on Setting up and using a PGP key, configure MTAs to use TLS. Email authentication and spam prevention Mail relays, grey listing, block list & RBL, DNSBL (Real-time Black hole List), White list, SPF, Domain Keys Identified Mail (DKIM), Author Domain Signing Practices (ADSP), Abuse Report Format (ARF), Domain-based Message Authentication, Reporting and Conformance (DMARC). Hands on Relay spamming and the blocking spamming.

Linux Professional Institute Certification (LPIC) 101
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for System administrator Network administrator Technician DevOps Overview The Linux Professional Institute(LPI) is the go to certification body for vendor independent Linux certifications. This course covers fundamental Linuxskills such as file management and manipulation, text processing, command line use, package management,filesystems, hardware, and many more. Students will feel confident taking the LPI LPIC-1 101 exam with in classroomassessments and practice exams. This course prepares students to take the 101 exam of the LPI level 1 certification. Work on the Command Line LPI Objectives Covered Role of Command Shell Shells Gathering System Info Identifying the Shell Changing the Shell Shell Prompts Bash: Bourne-Again Shell Navigating the Filesystem Help from Commands and Documentation Getting Help Within the Graphical Desktop Getting Help with man & info Bash: Command Line History Bash: Command Editing Bash: Command Completion Shell and Environment Variables Key Environment Variables LAB TASKS Use Streams, Pipes, and Redirects LPI Objectives Covered File Redirection Piping Commands Together Filename Matching File Globbing and Wildcard Patterns Brace Expansion General Quoting Rules Nesting Commands Gotchas: Maximum Command Length LAB TASKS Manage File Permissions and Ownership LPI Objectives Covered Filesystem Hierarchy Standard Displaying Directory Contents Filesystem Structures Determining Disk Usage With df and du File Ownership Default Group Ownership File and Directory Permissions File Creation Permissions with umask Changing File Permissions SUID and SGID on files SGID and Sticky Bit on Directories User Private Group Scheme LAB TASKS Create, Delete, Find, and Display Files LPI Objectives Covered Directory Manipulation File Manipulation Deleting and Creating Files Physical Unix File Structure Filesystem Links File Extensions and Content Which and Type Where is Searching the Filesystem Alternate Search Method Manually Installed Shared Libraries LAB TASKS Work with Archives and Compression LPI Objectives Covered Archives with tar Archives with cpio The gzip Compression Utility The bzip2 Compression Utility The XZ Compression Utility The PKZIP Archiving/Compression format LAB TASKS Process Text Streams Using Filters LPI Objectives Covered Producing File Statistics The Streaming Editor Replacing Text Characters Text Sorting Duplicate Removal Utility Extracting Columns of Text Displaying Files Prepare Text for Display Previewing Files Displaying Binary Files Combining Files and Merging Text LAB TASKS Search Text Files Using Regular Expressions LPI Objectives Covered Searching Inside Files Regular Expression Overview Regular Expressions RE Character Classes Regex Quantifiers RE Parenthesis LAB TASKS Perform Basic File Editing Operations Using VI LPI Objectives Covered Text Editing vi and Vim Learning Vim Basic vi Intermediate vi LAB TASKS Create, Monitor, and Kill Processes LPI Objectives Covered What is a Process? Process Lifecycle Process States Viewing Processes Signals Tools to Send Signals Managing Processes Tuning Process Scheduling Job Control Overview Job Control Commands Nohup and Disown Uptime & w Persistent Shell Sessions with Screen Using screen Advanced Screen LAB TASKS Use RPM, YUM, and Debian Package Management LPI Objectives Covered Managing Software RPM Architecture Working With RPMs Querying and Verifying with RPM Installing Debian Packages Querying and Verifying with dpkg The alien Package Conversion Tool Managing Software Dependencies Using the Yum command yum downloader Configuring Yum The deselect & APT Frontends to dpkg Aptitude Configuring APT LAB TASKS Work with Partitions, Filesystem, and Disk Quotas LPI Objectives Covered Partition Considerations Logical Volume Management Filesystem Planning Partitioning Disks with fdisk & gdisk Resizing a GPT Partition with gdisk Partitioning Disks with parted Non-Interactive Disk Partitioning with sfdisk Filesystem Creation Filesystem Support Unix/Linux Filesystem Features Swap Selecting a Filesystem Filesystem Maintenance Mounting Filesystems Mounting Filesystems Managing an XFS Filesystem NFS SMB Filesystem Table (/etc/fstab) Configuring Disk Quotas Setting Quotas Viewing and Monitoring Quotas LAB TASKS Linux Boot Process LPI Objectives Covered Booting Linux on PCs GRUB 2 GRUB 2 Configuration GRUB Legacy Configuration Boot Parameters Uinit Linux Runlevels Aliases Systemd local-fs.target and sysinit.target Runlevel Implementation System Boot Method Overview Systemd System and Service Manager Modifying systemd services Systemd Targets Using systemd Shutdown and Reboot System Messaging Commands Controlling System Messaging LAB TASKS Determine and Configure Hardware Settings LPI Objectives Covered Managing Linux Device Files Hardware Discovery Tools Configuring New Hardware with hwinfo PC Architecture and Bus DMA & IRQ USB Devices USB Architecture Configuring Kernel Components and Modules Kernel Modules Handling Module Dependencies Configuring the Kernel via /proc/ LAB TASKS Linux Fundamentals Unix and its Design Principles FSF and GNU GPL Æ?? General Public License The Linux Kernel Components of a Distribution Red Hat Linux Products SUSE Linux Products Debian Ubuntu Logging In got root? Switching User Contexts Gathering Login Session Info LAB TASKS Additional course details: Nexus Humans Linux Professional Institute Certification (LPIC) 101 training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Linux Professional Institute Certification (LPIC) 101 course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.
