- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
Computing & IT courses delivered Online
We couldn't find any listings for your search. Explore our online options and related educators below to see if they help you.
Know someone teaching this? Help them become an Educator on Cademy.
Online Options
Show all 5604Certified Cloud Computing & IT Security Training
By iStudy UK
Cloud Computing and everything you need to know about security in the online world Do you have too much data to store and not enough space to manage all of them? Do you want to protect your valuable information online? Then this course might just be what you are looking for. Cloud computing is the delivery of computing services - servers, storage, databases, networking, software, analytics and more - over the Internet ('the cloud'). Companies offering these computing services are called cloud providers and typically charge for cloud computing services based on usage, similar to how you're billed for gas or electricity at home. Training in Security is a crucial enabler to instill a culture of awareness and to protect your business from internal and external Cyber Threats. This Course is designed to give you all the information regarding Cyber Security and how to protect yourself online. It will teach you about the benefits of cloud computing and the typpes of cloud services. So what are you waiting for! Take the course. Course Highlights Certified Cloud Computing & IT Security Training is an award winning and the best selling course that has been given the CPD Certification & IAO accreditation. It is the most suitable course anyone looking to work in this or relevant sector. It is considered one of the perfect courses in the UK that can help students/learners to get familiar with the topic and gain necessary skills to perform well in this field. We have packed Certified Cloud Computing & IT Security Training into 30 modules for teaching you everything you need to become successful in this profession. To provide you ease of access, this course is designed for both part-time and full-time students. You can become accredited in just 20 hours, 30 minutes and it is also possible to study at your own pace. We have experienced tutors who will help you throughout the comprehensive syllabus of this course and answer all your queries through email. For further clarification, you will be able to recognize your qualification by checking the validity from our dedicated website. Why You Should Choose Certified Cloud Computing & IT Security Training Lifetime access to the course No hidden fees or exam charges CPD Accredited certification on successful completion Full Tutor support on weekdays (Monday - Friday) Efficient exam system, assessment and instant results Download Printable PDF certificate immediately after completion Obtain the original print copy of your certificate, dispatch the next working day for as little as £9. Improve your chance of gaining professional skills and better earning potential. Who is this Course for? Certified Cloud Computing & IT Security Training is CPD certified and IAO accredited. This makes it perfect for anyone trying to learn potential professional skills. As there is no experience and qualification required for this course, it is available for all students from any academic backgrounds. Requirements Our Certified Cloud Computing & IT Security Training is fully compatible with any kind of device. Whether you are using Windows computer, Mac, smartphones or tablets, you will get the same experience while learning. Besides that, you will be able to access the course with any kind of internet connection from anywhere at any time without any kind of limitation. Career Path You will be ready to enter the relevant job market after completing this course. You will be able to gain necessary knowledge and skills required to succeed in this sector. All our Diplomas' are CPD and IAO accredited so you will be able to stand out in the crowd by adding our qualifications to your CV and Resume. Cloud Computing What Is Cloud Computing? FREE 00:15:00 Benefits Of Cloud Computing FREE 01:00:00 Is Cloud Computing Really Secure? 01:00:00 The Concept of Public Cloud 00:30:00 The Concept of Private Cloud 00:30:00 Hybrid Cloud and It's Advantages 00:30:00 Types of Cloud for Your Business 00:30:00 Key Features of Cloud Computing 01:00:00 How Cloud Computing Can Revolutionize Your Business? 00:30:00 Wrapping Up 00:15:00 Data Protection Why Internet Marketers Need More Protection FREE 01:00:00 You Can't Be Anonymous FREE 00:15:00 Start With Basic Security Measures 01:00:00 Using Disclaimers 01:00:00 Proper Use Of Email 01:00:00 Protecting Product Rights 01:00:00 Protecting Your Website 01:00:00 Terms Of Use Or Service 00:30:00 Privacy Policy 01:00:00 IT Security Spyware Can Destroy 00:30:00 How Does Spyware Spread? 00:30:00 How To Remove Spyware 00:30:00 Anti Spyware Program 01:00:00 The Anti Anti-Spyware Programs 00:15:00 Research And Learn More 00:15:00 Choosing The Best Anti Spyware Tool 01:00:00 Computer Security And Spyware 01:00:00 The Programs To Avoid 00:15:00 Is It Legal? 00:15:00 Checklist Of Protection 00:15:00 Mock Exam Mock Exam- Certified Cloud Computing & IT Security Training 00:30:00 Final Exam Final Exam- Certified Cloud Computing & IT Security Training 00:30:00

**Unlock the Power of AI: Introduction to AI for Business Workshop**
By Panda Education and Training Ltd
Introduction to AI for Business

Data Protection & Cyber Security: Remaining Compliant Against Today's Risks
By DG Legal
The professional working world has changed more rapidly than could have been envisaged at the time of the introduction of GDPR and the Data Protection Act 2018. With more people working from home post-Covid and the ever increasing risk of cyber-attacks, this short course is aimed at taking stock of current practice and risk, as well as considering ICO enforcement action and the implications of hybrid working. It is also a great recap on the rules as they stand and what you need to know to comply. The course will cover: UK GDPR - A timely reminder of the rules ICO enforcement action and what we can learn Data Protection Impact Assessments - when and how to do them Hybrid working and UK GDPR Managing cyber attacks from a UK GDPR perspective Target Audience The online course is suitable for staff of all levels, from support staff to senior partners. Resources Course notes will be provided to all delegates which may be useful for ongoing reference or cascade training. Please note a recording of the course will not be made available. Speaker Matthew Howgate, Consultant, DG Legal Matt is a non-practising solicitor who has considerable experience in regulatory issues and advising on complex issues of compliance and ethics. He is also an expert in data protection, UK GDPR and on the civil legal aid scheme. Matthew is a lead trainer on and co-developed the LAPG Certificate in Practice Management (a training programme for legal managers and law firm owners) as well as regularly providing training on legal aid Supervision, costs maximisation, data protection and security and on general SRA compliance.

***24 Hour Limited Time Flash Sale*** Network Security Engineer Diploma Admission Gifts FREE PDF & Hard Copy Certificate| PDF Transcripts| FREE Student ID| Assessment| Lifetime Access| Enrolment Letter Cyber threats pose a major risk to organisations, with an attack every 39 seconds in the UK. In 2023, UK businesses reported 750,000 cybersecurity breaches, a 46% increase from the previous year. This calls for skilled network security engineers to safeguard systems and data. This Network Security Engineer Diploma bundle provides extensive training in network defense, ethical hacking, penetration testing, and risk analysis to advance cybersecurity careers. This bundle focuses on network security, ethical hacking, penetration testing, risk management, CompTIA certifications (Network+, Security+, CySA+, PenTest+), cloud computing, IT fundamentals, and web app security. Learners will gain in-demand skills to protect organisations. But that's not all. When you enrol in this Bundle Course Online Training, you'll receive 25 CPD-Accredited PDF Certificates, Hard Copy Certificates, and our exclusive student ID card, all absolutely free. Courses Are Included In this Network Security Engineer Diploma Course Career Bundle: Course 01: Network Security Engineer Course 02: Computer Networks Security from Scratch to Advanced Course 03: Network Security and Risk Management Course 04: Diploma in CompTIA Network Training at QLS Level 7 Course 05: CompTIA Network+ (N10-008) Course 06: CompTIA Network+ Certification (N10-007) Course 07: Cloud Computing / CompTIA Cloud+ (CV0-002) Course 08: CompTIA CySA+ Cybersecurity Analyst (CS0-002) Course 09: CompTIA Security+ (SY0-601) Course 10: CompTIA A+ (220-1001) Course 11: CompTIA IT Fundamentals ITF+ (FCO-U61) Course 12: CompTIA PenTest+ (Ethical Hacking) Course 13: Learn Ethical Hacking From A-Z: Beginner To Expert Course 14: IT: Ethical Hacking & IT Security Course 15: Web Application Penetration Testing Course Course 16: Penetration Testing with OWASP ZAP: Mastery course Course 17: Understanding Data Protection and Data Security Course 18: GENERAL DATA PROTECTION REGULATION (GDPR) & CYBER SECURITY MANAGEMENT Course 19: Data Center Training Essentials: Mechanical & Cooling Course 20: Cyber Security Incident Handling and Incident Response Course 21: IT Administration and Networking Course 22: IT Support Technician Course 23: Level 5 Diploma in Cyber Security Course 24: Cyber Security Law Course 25: Information Management Enrol in the Network Security Engineer Diploma Course today and take the first step towards achieving your goals and dreams. Why buy this Bundle Course? Free CPD Accredited Certificate upon completion of this Bundle Course Get a free student ID card with this Bundle Course Lifetime access to this Bundle of Course materials Get instant access to this Bundle Course Learn from anywhere in the world 24/7 tutor support with tthis Bundle Course. Start your learning journey straightaway! This Bundle Course premium bundle consists of 25 precisely chosen courses on a wide range of topics essential for anyone looking to excel in this field. Each segment of the Network Security Engineer Diploma Course is meticulously designed to maximise learning and engagement, blending interactive content and audio-visual modules for a truly immersive experience. Certification You have to complete the assignment given at the end of this Bundle Course. After passing this Bundle Course exam You will be entitled to claim a PDF & Hardcopy certificate accredited by CPD Quality standards completely free. CPD 350 CPD hours / points Accredited by CPD Quality Standards Who is this course for? This bundle is ideal for: Students seeking mastery in this field Professionals seeking to enhance their skills Anyone who is passionate about this topic Requirements You will not need any prior background or expertise to enrol in this bundle. Career path This Network Security Engineer Diploma Course bundle will allow you to kickstart or take your career in the related sector to the next stage. Network Security Engineer Security Analyst Penetration Tester Security Consultant Cybersecurity Specialist IT Security Manager Certificates CPD Accredited Digital certificate Digital certificate - Included CPD Accredited Hard copy certificate Hard copy certificate - Included If you are an international student, then you have to pay an additional 10 GBP for each certificate as an international delivery charge.

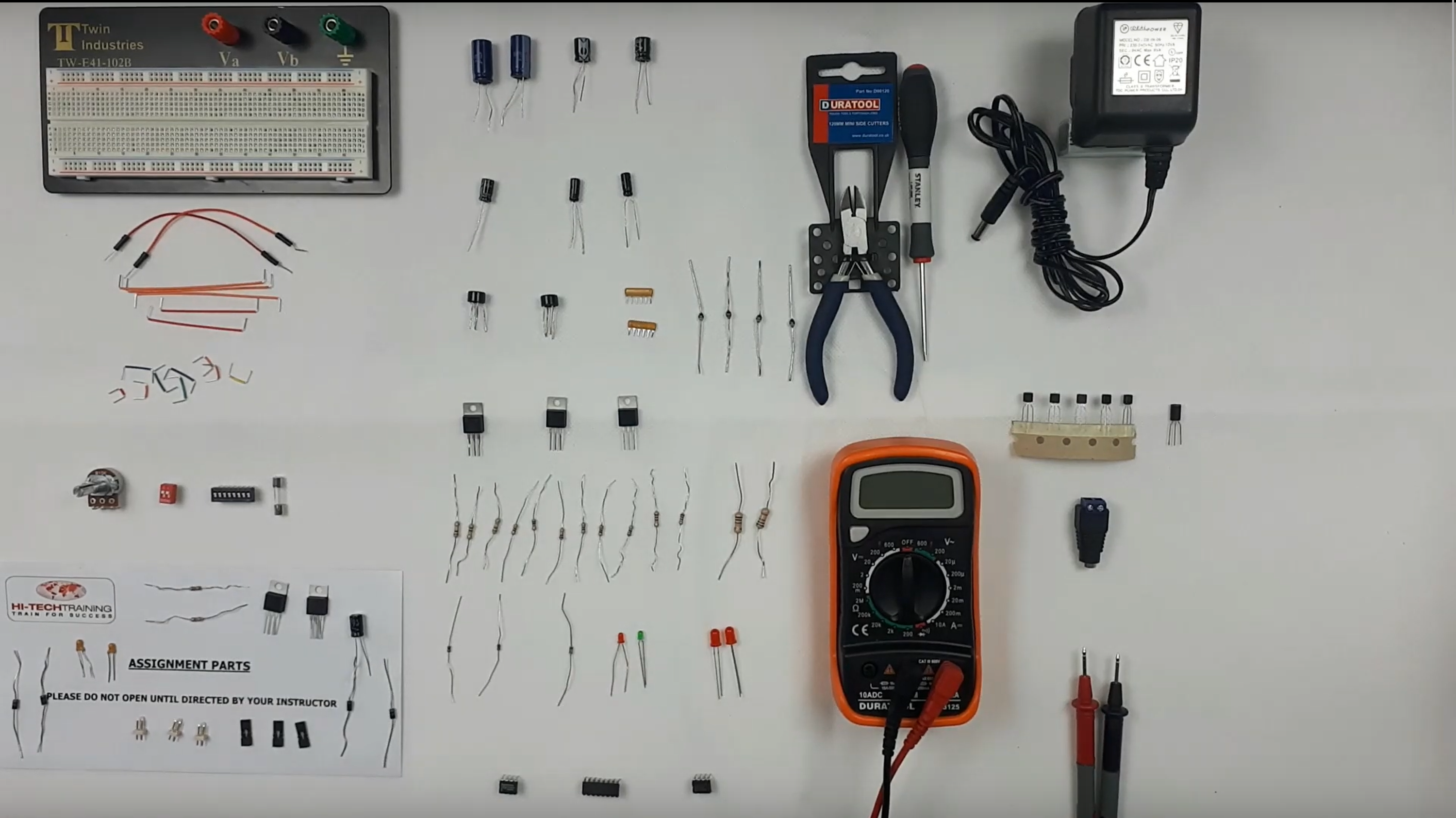
Electronics Repair 2 Course
By Hi-Tech Training
Electronics Equipment Repair 2 (Online Virtual Classroom) is a follow on course to Electronics Equipment Repair 1. This course builds on the skills gained and enables participants to build, test and fault-find more complex Analogue Electronic circuits
Learn everything you need to know to be fully competent with Mac iOS. This syllabus takes you around the basics and then on another deep dive into all the elements. Discover things you never knew and speed up your experience using Mac iOS. Module 1: Introduction to Mac iOS and Hardware • Understanding the Mac ecosystem • Overview of Mac hardware components • Navigating the Mac interface Module 2: Mac Operating System (macOS) • Exploring the macOS interface • Customizing system preferences • File management and organization on macOS Module 3: Essential Mac Apps • Using Safari for web browsing • Effective web searching using search engines • Email management with Apple Mail • Calendar and task management with Apple Calendar Module 4: Software Installation and Updates • Installing and updating software applications • Managing and uninstalling programs • App Store and app installations Module 5: Productivity and Collaboration • Using iCloud for cloud-based storage and collaboration • Working with Notes, Reminders, and Messages • Collaborative document editing with iWork Module 6: Multimedia and Creativity • Basic image editing with Photos and Preview • Music creation with GarageBand • Creating multimedia presentations with Keynote Module 7: Troubleshooting and Maintenance • Identifying and resolving common Mac issues • Using Activity Monitor for performance monitoring • Maintenance tasks for macOS Module 8: Mac Security and Privacy • Overview of Mac security features • Online safety and privacy best practices • Protecting personal data and devices Module 9: Advanced Mac Features • Customizing the Dock and Menu Bar • Using Siri for voice commands and search • Continuity features for seamless device integration Module 10: Using AI and Chat GPT • Introduction to AI and Chat GPT technology • Exploring AI-powered features on Mac • Using Chat GPT for productivity and assistance Module 11: Browsing and Search Engines • Effective use of web browsers on macOS • Utilizing search engines for research • Online safety and privacy while browsing Module 12: Cybersecurity • Understanding cybersecurity threats • Protecting against malware and phishing attacks • Secure online practices and password management Module 13: Software Installation and Factory Reset • Installing and updating software applications • Factory resetting a Mac device • Data backup and recovery during resets Module 14: Final Projects and Assessment • Culminating projects showcasing Mac iOS skills • Practical exams assessing Mac software knowledge and skills • Preparing for industry-recognized certifications (optional) Please note that the duration and depth of each module can vary depending on the level of expertise required and the specific needs of the learners. Additionally, it's important to adapt the curriculum to the learners' proficiency levels, whether they are A Level/GCSE students or adult learners with different experience levels.

Certified Diploma in Cloud Computing
By iStudy UK
Essentials of Cloud Computing are for anybody with an IT foundation that is keen on understanding what is Cloud Computing? It will outfit you with essential information of Cloud Technologies being used today. Cloud computing has developed from being only a trendy expression to a genuine business choice that numerous organizations are considering. Hence learning about it is important to make strategic plan to move applications and services to the Cloud. At the end of this course, you will accomplish essential comprehension of what is Cloud Computing; comprehend Cloud Segments and Cloud Deployment Models. You will also be familiarized to Key Cloud Companies and you will pick up information of Cloud Services and Cloud Security. Course Highlights Certified Diploma in Cloud Computing is an award winning and the best selling course that has been given the CPD Certification & IAO accreditation. It is the most suitable course anyone looking to work in this or relevant sector. It is considered one of the perfect courses in the UK that can help students/learners to get familiar with the topic and gain necessary skills to perform well in this field. We have packed Certified Diploma in Cloud Computing into 12 modules for teaching you everything you need to become successful in this profession. To provide you ease of access, this course is designed for both part-time and full-time students. You can become accredited in just 6 hours, 40 minutes and it is also possible to study at your own pace. We have experienced tutors who will help you throughout the comprehensive syllabus of this course and answer all your queries through email. For further clarification, you will be able to recognize your qualification by checking the validity from our dedicated website. Why You Should Choose Certified Diploma in Cloud Computing Lifetime access to the course No hidden fees or exam charges CPD Accredited certification on successful completion Full Tutor support on weekdays (Monday - Friday) Efficient exam system, assessment and instant results Download Printable PDF certificate immediately after completion Obtain the original print copy of your certificate, dispatch the next working day for as little as £9. Improve your chance of gaining professional skills and better earning potential. Who is this Course for? Certified Diploma in Cloud Computing is CPD certified and IAO accredited. This makes it perfect for anyone trying to learn potential professional skills. As there is no experience and qualification required for this course, it is available for all students from any academic backgrounds. Requirements Our Certified Diploma in Cloud Computing is fully compatible with any kind of device. Whether you are using Windows computer, Mac, smartphones or tablets, you will get the same experience while learning. Besides that, you will be able to access the course with any kind of internet connection from anywhere at any time without any kind of limitation. Career Path You will be ready to enter the relevant job market after completing this course. You will be able to gain necessary knowledge and skills required to succeed in this sector. All our Diplomas' are CPD and IAO accredited so you will be able to stand out in the crowd by adding our qualifications to your CV and Resume. Certified Diploma in Cloud Computing What Is Cloud Computing? FREE 00:15:00 Benefits Of Cloud Computing FREE 01:00:00 Is Cloud Computing Really Secure? 01:00:00 The Concept of Public Cloud 00:30:00 The Concept of Private Cloud 00:30:00 Hybrid Cloud and It's Advantages 00:30:00 Types of Cloud for Your Business 00:30:00 Key Features of Cloud Computing 01:00:00 How Cloud Computing Can Revolutionize Your Business? 00:30:00 Wrapping Up 00:15:00 Reference Books Cloud Computing Complete Guide 00:00:00 Cloud Services 00:00:00 Mock Exam Mock Exam-Certified Diploma in Cloud Computing 00:20:00 Final Exam Final Exam-Certified Diploma in Cloud Computing 00:20:00

Learn everything you need to know to be fully competent with Window OS. This syllabus takes you around the basics and then on another deep dive into all the elements. Discover things you never knew and speed up your experience using Windows OS. Module 1: Introduction to Windows OS • Understanding the Windows operating system • Navigating the Windows interface • Customizing system settings and preferences Module 2: File Management • Managing files and folders in Windows Explorer • Copying, moving, and renaming files • Using the Recycle Bin and data recovery Module 3: Windows Built-in Apps • Using Microsoft Edge for web browsing • Effective web searching using search engines • Email management with Windows Mail • Calendar and task management with Windows Calendar Module 4: Software Installation and Updates • Installing and updating software applications • Managing and uninstalling programs • Windows Store and app installations Module 5: Microsoft Office Basics • Introduction to Microsoft Office suite • Using Microsoft Word for document creation • Basic spreadsheet management with Microsoft Excel Module 6: Microsoft Office Intermediate Skills • Advanced features in Microsoft Word • Creating and formatting spreadsheets in Microsoft Excel • Creating dynamic presentations with PowerPoint Module 7: Multimedia and Graphics • Basic image editing with Paint • Using Windows Photo app for photo management • Creating graphics with Paint 3D Module 8: Productivity and Collaboration • Using OneDrive for cloud-based storage and collaboration • Working with Windows Sticky Notes and To-Do • Collaborative editing with Microsoft Office Online Module 9: Troubleshooting and Maintenance • Identifying and resolving common Windows issues • Using Task Manager for performance monitoring • Maintenance tasks for Windows OS Module 10: Windows Security and Privacy • Overview of Windows security features • Online safety and privacy best practices • Protecting personal data and devices Module 11: Advanced Windows Features • Customizing the Windows Start Menu and Taskbar • Using Cortana for voice commands and search • Virtual desktops and advanced multitasking Module 12: Using AI and Chat GPT • Introduction to AI and Chat GPT technology • Exploring AI-powered features in Windows • Using Chat GPT for productivity and assistance Module 13: Browsing and Search Engines • Effective use of web browsers • Utilizing search engines for research • Online safety and privacy while browsing Module 14: Cybersecurity • Understanding cybersecurity threats • Protecting against malware and phishing attacks • Secure online practices and password management Module 15: Software Installation and Factory Reset • Installing and updating software applications • Factory resetting a Windows device • Data backup and recovery during resets Module 16: Final Projects and Assessment • Culminating projects showcasing Windows OS skills • Practical exams assessing Windows software knowledge and skills • Preparing for industry-recognized certifications (optional) Please note that the duration and depth of each module can vary depending on the level of expertise required and the specific needs of the learners. Additionally, it's important to adapt the curriculum to the learners' proficiency levels, whether they are A Level/GCSE students or adult learners with different experience levels.

Course Overview Clear out all your confusion about cloud computing and learn it from the primary level with the Basic Cloud Computing with Cloud Models course. This course is designed to introduce you to cloud computing fundamentals and to give you the opportunity to add a valuable certificate to your resume. This Basic Cloud Computing with Cloud Models course will provide you with a detailed definition of cloud computing. It will introduce you to the five key characteristics of cloud computing. Here, you will learn what SAAS, PAAS and IAAS are. The course will teach you the process of creating a free Azure account. You will become skilled in managing the Azure account with CL and PowerShell. In the easy to follow module, you will receive valuable information on Amazon Web Services. You will understand the techniques of getting free access to AWS and creating free AWS accounts. This Basic Cloud Computing with Cloud Models course will equip you with the essentials of cloud computing. Enroll in the course and prepare yourself to pursue a career in the relevant industry. Learning Outcomes Learn the definition and importance of cloud computing Familiarize with the five vital characters of cloud computing Understand the process of Azure free account Build the skills to manage Azure with CL and PowerShell Enrich your knowledge of Amazon Web Services Who is this course for? Anyone interested to learn about cloud computing Entry Requirement This course is available to all learners, of all academic backgrounds. Learners should be aged 16 or over to undertake the qualification. Good understanding of English language, numeracy and ICT are required to attend this course. Certification After you have successfully completed the course, you will be able to obtain an Accredited Certificate of Achievement. You can however also obtain a Course Completion Certificate following the course completion without sitting for the test. Certificates can be obtained either in hardcopy at the cost of £39 or in PDF format at the cost of £24. PDF certificate's turnaround time is 24 hours, and for the hardcopy certificate, it is 3-9 working days. Why choose us? Affordable, engaging & high-quality e-learning study materials; Tutorial videos/materials from the industry-leading experts; Study in a user-friendly, advanced online learning platform; Efficient exam systems for the assessment and instant result; The UK & internationally recognized accredited qualification; Access to course content on mobile, tablet or desktop from anywhere anytime; The benefit of career advancement opportunities; 24/7 student support via email. Career Path The Basic Cloud Computing with cloud models course is a useful qualification to possess and would be beneficial for any related profession or industry such as: Cloud Support Engineer Cloud Computing Engineer IT Support and Cloud Engineer Cloud Computing Analyst Cloud Computing Administrator Introduction Introduction 00:01:00 The Need for Cloud Computing 00:13:00 The Definition of Cloud Computing 00:05:00 Evolution of Cloud and Cloud Models 00:05:00 What is SAAS , PAAS and IAAS 00:05:00 Who is responsible for Data in cloud 00:10:00 The Five Key Characteristics of Cloud Computing 00:08:00 Benefits of Cloud Computing 00:09:00 CapEx vs OpEx 00:03:00 Cloud DataCenters : Where are they? 00:02:00 What is Gartner Say About Cloud Providers 00:02:00 Please Read This 00:01:00 Let's Talk Azure How to create Azure Free Account 00:02:00 How to Login to Azure Portal 00:10:00 Managing Azure with CLI 00:04:00 Let's Learn AWS Foot Prints of Amazon Web Services 00:14:00 AWS Console Tour 00:10:00 Free access to AWS 00:03:00 Creating a Free AWS Account 00:03:00 Certificate and Transcript Order Your Certificates and Transcripts 00:00:00

Introduction to AI for Trainers and Assessors
By Panda Education and Training Ltd
Introduction to AI for Trainers and Assessors
