- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
5672 Computing & IT courses in Greenock delivered Online
FULL STACK JAVA
By London School of Emerging Technology
Full Stack Development encompasses the complete creation of end-to-end development of both the front-end and back-end of an application. LSET Bridges The Gap Between Education And Employment

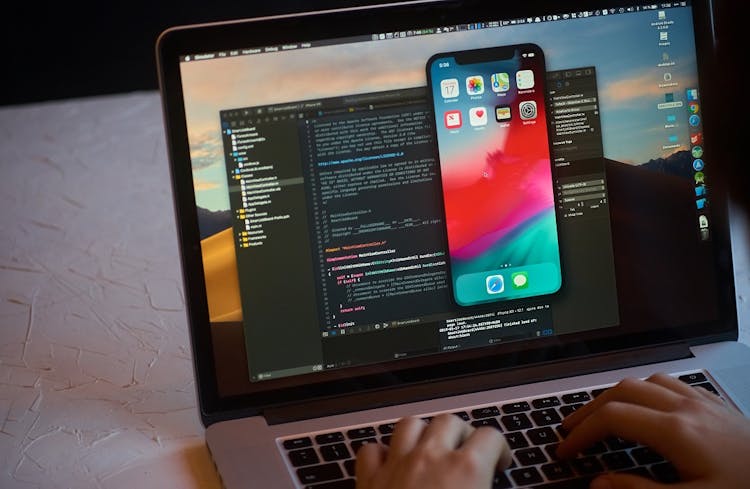
Overview This comprehensive course on Complete iOS 11 and Swift 4 will deepen your understanding on this topic. After successful completion of this course you can acquire the required skills in this sector. This Complete iOS 11 and Swift 4 comes with accredited certification from CPD, which will enhance your CV and make you worthy in the job market. So enrol in this course today to fast track your career ladder. How will I get my certificate? You may have to take a quiz or a written test online during or after the course. After successfully completing the course, you will be eligible for the certificate. Who is This course for? There is no experience or previous qualifications required for enrolment on this Complete iOS 11 and Swift 4. It is available to all students, of all academic backgrounds. Requirements Our Complete iOS 11 and Swift 4 is fully compatible with PC's, Mac's, Laptop, Tablet and Smartphone devices. This course has been designed to be fully compatible with tablets and smartphones so you can access your course on Wi-Fi, 3G or 4G. There is no time limit for completing this course, it can be studied in your own time at your own pace. Career Path Learning this new skill will help you to advance in your career. It will diversify your job options and help you develop new techniques to keep up with the fast-changing world. This skillset will help you to- Open doors of opportunities Increase your adaptability Keep you relevant Boost confidence And much more! Course Curriculum 13 sections • 177 lectures • 19:08:00 total length •iOS 11 Course Overview: 00:11:00 •Install Xcode 9: 00:07:00 •Xcode 9 Beta 4 Update: 00:09:00 •App: Hustle - Your first iOS 11 App: 00:22:00 •Variables, operators, and how computers work: 00:17:00 •Strings in Swift: 00:15:00 •Working with numbers in Swift: 00:20:00 •Swift Functions: 00:23:00 •Booleans: 00:21:00 •Constants: 00:10:00 •Array Data Structure in Swift: 00:13:00 •Swift Loops: 00:19:00 •Dictionary Data Structure in Swift: 00:19:00 •Object Oriented Programming in Swift: 00:12:00 •Inheritance: 00:08:00 •Polymorphism: 00:08:00 •Optionals: 00:21:00 •Enumerations: 00:20:00 •Extensions: Part 1: 00:15:00 •Extensions: Part 2: 00:21:00 •Intro to Protocols, Delegates - Numbers Example: 00:13:00 •Intro to Protocols, Delegates Part 2 - Question Generator: 00:18:00 •Protocols, Delegates - Building Color Magic App UI: 00:17:00 •Protocols, Delegates - Using the Delegate Method in Color Magic App: 00:16:00 •Protocols, Delegates - Using Mutating Functions in Types: 00:18:00 •Git and Version Control - The Fun Way!: 00:12:00 •Terminal Basics - Changing Directories: 00:06:00 •Terminal Basics - Creating Directories and Files: 00:05:00 •Terminal Basics - Copying and Renaming Files: 00:09:00 •Terminal Basics - Deleting Files and Directories: 00:06:00 •Git Basics: 00:17:00 •Setting up Github: 00:05:00 •Working with Local and Remote Repositories: 00:11:00 •Handling Git Merge Conflicts: 00:17:00 •App: Swoosh 01 - Creating the Welcome Screen: 00:25:00 •App: Swoosh 02 - Working with Frames: 00:16:00 •App: Swoosh 03 - Intro to Auto Layout: 00:27:00 •App: Swoosh 04 - Working with Stack Views: 00:27:00 •App: Swoosh 05 - Intro to Segues (Changing Screens): 00:10:00 •App: Swoosh 06 - Refactoring in Xcode 9: 00:10:00 •App: Swoosh 07 - Debugging: setValue forUndefinedKey: 00:04:00 •App: Swoosh 08 - Programmatic Segues: 00:09:00 •App: Swoosh 09 - IBActions (Handling Events) and Data Models: 00:16:00 •App: Swoosh 10 - Passing Data Between View Controllers: 00:12:00 •App: Dev Profile 01 - Auto layout for iPhones: 00:22:00 •App: Dev Profile 02 - Auto layout for iPads (Size Classes): 00:20:00 •App: Window Shopper 01 - Custom Text Fields: 00:18:00 •App: Window Shopper 02 - Input Accessory Views: 00:15:00 •App: Window Shopper 03 - Unit Testing our Data: 00:17:00 •App: Window Shopper 04 - Calculation Algorithm: 00:13:00 •App: Window Shopper 05 - Custom Drawing with drawRect: 00:12:00 •App: Coder Swag 01 - Project creation: 00:23:00 •App: Coder Swag 02 - Tableviews, Delegate, and Data Source: 00:33:00 •App: Coder Swag 03 - Collection Views (Grid Layouts): 00:13:00 •App: Coder Swag 04 - Working with Data Models: 00:14:00 •App: Coder Swag 05 - Displaying Data in Collection View Cells: 00:20:00 •Intro to Chat App: 00:04:00 •App: Smack - Project Setup: 00:26:00 •App: Smack - SWReveal: 00:20:00 •App: Smack - ChannelVC UI: 00:25:00 •App: Smack - LoginVC UI: 00:22:00 •App: Smack - CreateAccountVC UI: 00:19:00 •App: Smack - Web request and API: 00:09:00 •App: Smack - Hosting API: 00:20:00 •App: Smack - Locally Hosting API: 00:18:00 •App: Smack - Creating a web request in Xcode: 00:28:00 •App: Smack - Registering a User: 00:16:00 •App: Smack - Logging in a user: 00:20:00 •App: Smack - Creating a user: 00:26:00 •App: Smack - Avatar Picker Part 1: 00:19:00 •App: Smack - Avatar Picker Part 2: 00:20:00 •App: Smack - Generate a Avatar BG Color: 00:26:00 •App: Smack - LoggedIn Interface: 00:23:00 •App: Smack - Profile View: 00:25:00 •App: Smack - Logging in users: 00:23:00 •App: Smack - Getting channels: 00:19:00 •App: Smack - Channels TableView: 00:14:00 •App: Smack - Add Channel VC: 00:19:00 •App: Smack - Sockets and Channels: 00:26:00 •App: Smack - Refining Login Flow: 00:19:00 •App: Smack - Fetching Messages: 00:20:00 •App: Smack - Sending First Message: 00:17:00 •App: Smack - Displaying Chat Messages: 00:18:00 •App: Smack - Sockets and Messages: 00:19:00 •App: Smack - Typing Users: 00:22:00 •App: Smack - Unread Channels: 00:18:00 •Where to go from here: 00:08:00 •I'm Back: 00:08:00 •Intro to App: Pixel City: 00:02:00 •Creating Xcode Project: Pixel City: 00:04:00 •Installing Alamofire / AlamofireImage Cocoapods: 00:07:00 •Building MapVC UI /Conforming to MKMapViewDelegate /Setting Delegate of mapView: 00:15:00 •Requesting Location Services in iOS 11 / Centering Map On User Location: 00:18:00 •Adding UITapGestureRecognizer to Drop Custom Pins on MapView: 00:15:00 •Setting a Custom Map Annotation Color: 00:05:00 •Animating Photos View / Programmatically adding spinner and label subviews: 00:20:00 •Adding UILabel for Pull Up View / Adding UICollectionView Programmatically: 00:17:00 •Getting API Key from Flickr / Using Flickr API URL Format: 00:14:00 •Using Alamofire to Download URLS: 00:21:00 •Using Alamofire to Download Images / Cancelling All Sessions: 00:16:00 •Setting Up UICollectionView / Adding Images / Reloading UICollectionView: 00:10:00 •Building PopVC / Presentation PopVC When UICollectionViewCell is Tapped: 00:16:00 •Adding 3D Touch Peek: 00:15:00 •Challenge 1: 00:02:00 •Setting up developer: 00:10:00 •Implementing Google AdMob: 00:19:00 •Fetching a list of Products: 00:15:00 •Starting an in-app Purchase: 00:09:00 •Testing in-app Purchases: 00:18:00 •Restoring in-app Purchases after App Deletion: 00:09:00 •Intro to App: GoalPost: 00:03:00 •Creating Xcode Project / Project Folders: 00:04:00 •Building GoalsVC: 00:14:00 •Building GoalCell: 00:14:00 •What is Core Data?: 00:06:00 •Creating Goal Core Data Entity and Attributes: 00:08:00 •Displaying Static GoalCells in UITableView / Creating GoalType Enum: 00:10:00 •Building CreateGoalVC: 00:15:00 •Creating a UIViewController Extension: 00:11:00 •Creating a UIView / UIButton Extension: 00:19:00 •Building FinishGoalVC / Passing Data from CreateGoalVC: 00:19:00 •Saving Goal Data to Persistent Store: 00:13:00 •Fixing Dismissal of FinishGoalVC: 00:07:00 •Fetching Data from Persistent Store / Filling UITableView with Fetched Data: 00:16:00 •Removing Objects from Persistent Store using UITableView Delete Action: 00:11:00 •Setting Goal Progress for UITableViewCell: 00:15:00 •Challenge 2: 00:01:00 •Intro to App: Breakpoint: 00:03:00 •Creating Xcode Project / Setting Up Project Folders: 00:05:00 •Creating Firebase Project: 00:11:00 •Setting Up DataService / Creating Firebase Database Users: 00:11:00 •Building AuthVC and LoginVC in Interface Builder: 00:18:00 •Creating InsetTextField and ShadowView Subclasses: 00:18:00 •Setting up AuthService: 00:13:00 •Building FeedVC and GroupsVC in Interface Builder: 00:16:00 •Presenting LoginVC from AppDelegate / Allowing Login with Email: 00:22:00 •Building MeVC and Adding to UITabBarController: 00:10:00 •Creating CreatePostVC and Uploading Posts to Firebase: 00:20:00 •Creating UIView Extension for Binding Views to Keyboard: 00:15:00 •Building FeedCell: 00:10:00 •Writing the Message Model and Getting All Feed Messages from Firebase: 00:21:00 •Converting UIDs into Emails and Reversing the Order of a TableView: 00:20:00 •Creating CreateGroupVC and Connecting @IBOutlets/Actions: 00:15:00 •Creating UserCell: 00:16:00 •Searching for Email Accounts to Add to Group: 00:19:00 •Adding Users to Group with didSelectRowAt indexPath: 00:21:00 •Creating Groups and pushing them to Firebase: 00:16:00 •Creating GroupCell: 00:15:00 •Creating Group Model and Getting All Groups from Firebase: 00:19:00 •Building GroupFeedVC: 00:18:00 •Initializing Group Data for a Group and Presenting on GroupFeedVC: 00:16:00 •Downloading All Message for a Group and Animating Upon New Message: 00:24:00 •Creating a UIViewController Extension for Presenting GroupFeedVC: 00:07:00 •Challenge 3: 00:02:00 •Intro to app: 00:02:00 •Intro to CoreML: 00:05:00 •What is machine learning?: 00:08:00 •Creating Xcode 9 project: 00:03:00 •Building UI: 00:18:00 •AVFoundation: 00:18:00 •Tap gestures to take snapshot on item: 00:11:00 •Core ML Xcode 9 Beta 4 Update / Fix Preview Photo Crash: 00:03:00 •Downloading CoreML models: 00:21:00 •Adding UI controls for flash control: 00:07:00 •Training your app to speak what it sees: 00:18:00 •App: RampUp - Intro to ARKit App: 00:02:00 •App: RampUp - Resources: 00:04:00 •App: RampUp - Project creation: 00:11:00 •App: RampUp - SceneKit, 3D models: 00:11:00 •App: RampUp - Ramp picker popover: 00:14:00 •App: RampUp - 3D models in SceneKit for popover: 00:18:00 •App: RampUp - 3D models in SceneKit for popover part 2: 00:12:00 •App: RampUp - Detecting taps on 3D objects: 00:17:00 •App: RampUp - Placing ramps in ARKit: 00:24:00 •App: RampUp - Moving objects in 3D space in augmented reality: 00:20:00 •ARKit - where to go next: 00:04:00 •Assignment - Complete iOS 11 and Swift 4: 00:00:00
Overview This comprehensive course on Advanced Photoshop CC will deepen your understanding on this topic. After successful completion of this course you can acquire the required skills in this sector. This Advanced Photoshop CC comes with accredited certification from CPD, which will enhance your CV and make you worthy in the job market. So enrol in this course today to fast-track your career ladder. How will I get my certificate? You may have to take a quiz or a written test online during or after the course. After successfully completing the course, you will be eligible for the certificate. Who is This course for? There is no experience or previous qualifications required for enrolment on this Advanced Photoshop CC. It is available to all students, of all academic backgrounds. Requirements Our Advanced Photoshop CC is fully compatible with PC's, Mac's, Laptop, Tablet and Smartphone devices. This course has been designed to be fully compatible with tablets and smartphones so you can access your course on Wi-Fi, 3G or 4G. There is no time limit for completing this course, it can be studied in your own time at your own pace. Career Path Learning this new skill will help you to advance in your career. It will diversify your job options and help you develop new techniques to keep up with the fast-changing world. This skillset will help you to- Open doors of opportunities Increase your adaptability Keep you relevant Boost confidence And much more! Course Curriculum 2 sections • 21 lectures • 00:55:00 total length •Module 01: Overview: 00:01:00 •Module 02: Having Graphic Designs Created: 00:02:00 •Module 03: Making PSD Thumbnails Visible on Your PC: 00:03:00 •Module 04: Creating a Simple Design - Part 1: 00:05:00 •Module 05: Creating a Simple Design - Part 2: 00:04:00 •Module 06: Changing the Background Image: 00:03:00 •Module 07: Changing the Font or Text: 00:02:00 •Module 08: Working with Photoshop Actions: 00:02:00 •Module 09: Sources for Photoshop Actions: 00:01:00 •Module 10: Selecting Photoshop Actions: 00:02:00 •Module 11: Producing Photoshop Actions - Part 1: 00:05:00 •Module 12: Show Transform Controls: 00:02:00 •Module 13: Producing Photoshop Actions - Part 2: 00:07:00 •Module 14: Creating a Multiple 3D Image Shot: 00:04:00 •Module 15: Sizing of File Formats: 00:01:00 •Module 16: Saving For Certain File Formats: 00:02:00 •Module 17: Live Application - Part 1: 00:03:00 •Module 18: Live Application - Part 2: 00:02:00 •Module 19: Multiple Short Live Application: 00:03:00 •Module 20: Conclusion: 00:01:00 •Assignment - Advanced Photoshop CC: 00:00:00

Overview This comprehensive course on Amazon Web Services (AWS) will deepen your understanding on this topic. After successful completion of this course you can acquire the required skills in this sector. This Amazon Web Services (AWS) comes with accredited certification from CPD, which will enhance your CV and make you worthy in the job market. So enrol in this course today to fast-track your career ladder. How will I get my certificate? You may have to take a quiz or a written test online during or after the course. After successfully completing the course, you will be eligible for the certificate. Who is This course for? There is no experience or previous qualifications required for enrolment on this Amazon Web Services (AWS). It is available to all students, of all academic backgrounds. Requirements Our Amazon Web Services (AWS) is fully compatible with PC's, Mac's, Laptop, Tablet and Smartphone devices. This course has been designed to be fully compatible with tablets and smartphones so you can access your course on Wi-Fi, 3G or 4G. There is no time limit for completing this course, it can be studied in your own time at your own pace. Career Path Learning this new skill will help you to advance in your career. It will diversify your job options and help you develop new techniques to keep up with the fast-changing world. This skillset will help you to- Open doors of opportunities Increase your adaptability Keep you relevant Boost confidence And much more! Course Curriculum 9 sections • 66 lectures • 08:58:00 total length •Introduction to AWS - Cloud Computing: 00:11:00 •Introduction to AWS - Cloud Computing Continue: 00:10:00 •Launching a Server: 00:10:00 •Launching a Server Continues: 00:08:00 •Adding Tags: 00:09:00 •Launching a Windows Instance: 00:08:00 •Data storage Using S3: 00:07:00 •Data storage Using S3 Continues: 00:07:00 •AWS - EBS Part A: 00:07:00 •AWS - EBS Part B: 00:08:00 •AWS - EBS Part C: 00:06:00 •Running Instance: 00:08:00 •Terminate Instances: 00:02:00 •RDS and Dynamo DB Overview: 00:08:00 •Delete DB Instance: 00:06:00 •AWS - EFS Demo: 00:08:00 •More on AWS - EFS Demo: 00:10:00 •S3 Java API: 00:12:00 •More on S3 Java API: 00:11:00 •Dynamo DB Java API: 00:08:00 •Dynamo DB Java API Continues: 00:05:00 •Connecting to RDS - MySql: 00:11:00 •My SQL Driver: 00:09:00 •S3 using CLI: 00:10:00 •S3 using CLI Continues: 00:08:00 •AWS - Syn Command: 00:08:00 •Amazon DynamoDB Using: 00:09:00 •Amazon DynamoDB Using Continue: 00:10:00 •Amazon RDS Using CL: 00:12:00 •Amazon RDS Using CL Continue: 00:06:00 •More on Amazon RDS Using CL: 00:07:00 •Static website Using S3: 00:06:00 •AWS - Set Permission: 00:06:00 •Point your Domain to S3 Static Website: 00:07:00 •Point your Domain to S3 Static Website Continues: 00:09:00 •Name Servers: 00:07:00 •Create Record Set: 00:08:00 •Security Pre Work: 00:09:00 •IAM in AWS: 00:07:00 •IAM in AWS Continues: 00:06:00 •Creating New User: 00:07:00 •Storage C3: 00:10:00 •AWS - MFA in AWS: 00:07:00 •AWS - MFA in AWS Continues: 00:06:00 •Source Vs Destination: 00:07:00 •Infrastructure as Code: 00:08:00 •Infrastructure as Code Continues: 00:07:00 •Resources Name - AWSCF Bucket: 00:07:00 •Deployment Cloud Formation: 00:09:00 •Changing Access Control: 00:11:00 •Key Name - Key Val: 00:06:00 •Deployment Elastic Beanstalk: 00:06:00 •Creating Sample ENV: 00:06:00 •Deployment Ops Works Demo: 00:08:00 •Cloud Front Demo: 00:08:00 •Cloud Front Demo Continues: 00:10:00 •Security Groups: 00:08:00 •More on Security Groups: 00:08:00 •Creating a VPC: 00:09:00 •Virtual Private Cloud: 00:09:00 •Elastic IP: 00:07:00 •Allocate New Address: 00:08:00 •ELB Demo: 00:10:00 •ELB Demo Continues: 00:10:00 •Elastic Map Reduce: 00:11:00 •Amazon Cluster Running: 00:11:00

Overview This comprehensive course on Basic Photoshop CC will deepen your understanding on this topic. After successful completion of this course you can acquire the required skills in this sector. This Basic Photoshop CC comes with accredited certification from CPD, which will enhance your CV and make you worthy in the job market. So enrol in this course today to fast-track your career ladder. How will I get my certificate? You may have to take a quiz or a written test online during or after the course. After successfully completing the course, you will be eligible for the certificate. Who is This course for? There is no experience or previous qualifications required for enrolment on this Basic Photoshop CC. It is available to all students, of all academic backgrounds. Requirements Our Basic Photoshop CC is fully compatible with PC's, Mac's, Laptop, Tablet and Smartphone devices. This course has been designed to be fully compatible with tablets and smartphones so you can access your course on Wi-Fi, 3G or 4G. There is no time limit for completing this course, it can be studied in your own time at your own pace. Career Path Learning this new skill will help you to advance in your career. It will diversify your job options and help you develop new techniques to keep up with the fast-changing world. This skillset will help you to- Open doors of opportunities Increase your adaptability Keep you relevant Boost confidence And much more! Course Curriculum 1 sections • 20 lectures • 00:54:00 total length •Module 01: Overview: 00:02:00 •Module 02: Pricing and Licensing Options: 00:02:00 •Module 03: Basic File Types and Options: 00:02:00 •Module 04: Working with the Interface: 00:02:00 •Module 05: Working with a Basic Canvas: 00:03:00 •Module 06: Working with Layers: 00:03:00 •Module 07: Working with the Move Tool: 00:03:00 •Module 08: Working with Shapes: 00:04:00 •Module 09: Working with the Marquee Tool: 00:03:00 •Module 10: Working with Colors: 00:02:00 •Module 11: Working with the Paintbucket: 00:03:00 •Module 12: Working with the Eraser Tool: 00:03:00 •Module 13: Working with the Text Tool: 00:04:00 •Module 14: Working with Images: 00:03:00 •Module 15: Working with Sizing: 00:03:00 •Module 16: Working with Transparent Layers: 00:03:00 •Module 17: Using the Crop Tool: 00:03:00 •Module 18: Working with Layer Styles: 00:02:00 •Module 19: Working with Rotation of Image and Layers: 00:03:00 •Module 20: Conclusion: 00:01:00

SonicWALL Network Security Administrator For Sonic OS 7 - SNSA v7 - NA
By Nexus Human
Duration 2 Days 12 CPD hours This course is intended for Security professionals, System engineers, channel partners, service partners, and end users with at least one year of experience in implementing IT security technologies (Network, Applications, and Systems). Overview This course will enable students to configure, monitor, manage, and optimize the SonicWall Network Security firewall appliances running the new SonicOS 7 to effectively defend against limitless network and cyberthreats and implement SonicWall Boundless Cybersecurity safeguards for seamless protection. Upon completion of the course, students will be able to configure the SonicWall firewall for Secure and Remote Connectivity, Network Optimization, and Advanced Threat Protection. The SonicWall Network Security Administrator (SNSA) for SonicOS 7.0curriculum provides students the required background, knowledge, and hands-on experience to begin designing, implementing, and troubleshooting SonicWall Network Security products. SonicOS 7 is SonicWall?s brand new and most advanced security operating system and is at the core of its latest physical and virtual firewalls, including models from the TZ, NSv, NSa and NSsp Series. SonicOS 7.0 features advanced security, simplified policy management, and critical networking and management capabilities for distributed enterprises and small- to medium-sized businesses with SD-branch support. Course Outline Setting up Basic Firewall Components Unified Threat Management Secure Access Deep Packet Inspection for SSL (DPI-SSL) Content Filtering Services Application Control Scalability and Reliability SD-WAN High Availability Troubleshooting Tools

NetApp ONTAP 9 Cluster Administration and Data Protection Bundle
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for Network Engineers Channel Partners System Engineers Overview By the end of this course, you will be able to: Describe how ONTAP 9 fits into NetApp?s Cloud and Data Fabric strategy Identify supported ONTAP platforms Define ONTAP cluster components Create a cluster Manage ONTAP administrators Configure and manage storage resources Configure and manage networking resources Describe a Storage Virtual Machine?s (SVM?s) role in NetApp?s storage architecture Create and configure an SVM Create and manage FlexVols Implement storage efficiency features Create protocol servers within an SVM Upgrade and revert ONTAP patches and releases Describe the levels on which ONTAP protects data Describe the ONTAP 9 data protection features Understand the various data mirroring relationships available with ONTAP 9 Configure and operate SnapMirror and SnapVault data replication Demonstrate Storage Virtual Machine data protection Explain the components and configuration involved with SyncMirror and MetroCluster Describe NDMP protocol operation, configuration and management Pre/Post Assessment The ONTAP 9.0 Cluster Administration and Data Protection combo course uses lecture and hands-on exercises to teach basic administration and configuration of a cluster as well as the core backup and restore technologies found in ONTAP 9. The hands-on labs allow you to practice working with ONTAP features and manage your storage and network resources using the cluster shell and OnCommand System Manager. You will learn how to implement and manage SnapMirror, SnapVault, and SnapLock technology which are used to replicate and restore mission-critical data in the enterprise. The course also surveys real-world scenarios and use cases to teach you when to use each of the NetApp protection solutions. Backup and restore operations are taught using the command line and OnCommand System Manager.Includes: ONTAP commands for software versions 8.3.x to 9.0 The ONTAP 9.0 Cluster Administration and Data Protection combo course uses lecture and hands-on exercises to teach basic administration and configuration of a cluster as well as the core backup and restore technologies found in ONTAP 9. The hands-on labs allow you to practice working with ONTAP features and manage your storage and network resources using the cluster shell and OnCommand System Manager. You will learn how to implement and manage SnapMirror, SnapVault, and SnapLock technology which are used to replicate and restore mission-critical data in the enterprise. The course also surveys real-world scenarios and use cases to teach you when to use each of the NetApp protection solutions. Backup and restore operations are taught using the command line and OnCommand System Manager. Includes: ONTAP commands for software versions 8.3.x to 9.0

Symantec Endpoint Protection 14.X - Configure And Protect
By Nexus Human
Duration 3 Days 18 CPD hours This course is intended for This course is for Network, IT security, and systems administration professionals in a Security Operations position who are tasked with configuring optimum security settings for endpoints protected by Symantec Endpoint Protection 14. Overview At the completion of the course, you will be able to: Protect against Network Attacks and Enforcing Corporate Policies using the Firewall Policy. Blocking Threats with Intrusion Prevention. Introducing File-Based Threats. Preventing Attacks with SEP. Layered Security. Securing Windows Clients. Secure Mac Clients. Secure Linux Clients. Controlling Application and File Access. Restricting Device Access for Windows and Mac Clients. Hardening Clients with System Lockdown. Customizing Policies based on Location. Managing Security Exceptions. This course is designed for the network, IT security, and systems administration professionals in a Security Operations position who are tasked with configuring optimum security settings for endpoints protected by Symantec Endpoint Protection 14. Introduction Course environment Lab environment Introducing Network Threats Describing how Symantec Endpoint Protection protects each layer of the network stack Discovering the tools and methods used by attackers Describing the stages of an attack Protecting against Network Attacks and Enforcing Corporate Policies using the Firewall Policy Preventing network attacks Examining Firewall Policy elements Evaluating built-in rules Creating custom firewall rules Enforcing corporate security policy with firewall rules Blocking network attacks using protection and stealth settings Configuring advanced firewall feature Blocking Threats with Intrusion Prevention Introducing Intrusion Prevention technologies Configuring the Intrusion Prevention policy Managing custom signatures Monitoring Intrusion Prevention events Introducing File-Based Threats Describing threat types Discovering how attackers disguise their malicious applications Describing threat vectors Describing Advanced Persistent Threats and a typical attack scenario Following security best practices to reduce risks Preventing Attacks with SEP Layered Security Virus and Spyware protection needs and solutions Describing how Symantec Endpoint Protection protects each layer of the network stack Examining file reputation scoring Describing how SEP protects against zero-day threats and threats downloaded through files and email Describing how endpoints are protected with the Intelligent Threat Cloud Service Describing how the emulator executes a file in a sandbox and the machine learning engine?s role and function Securing Windows Clients Platform and Virus and Spyware Protection policy overview Tailoring scans to meet an environment?s needs Ensuring real-time protection for clients Detecting and remediating risks in downloaded files Identifying zero-day and unknown threats Preventing email from downloading malware Configuring advanced options Monitoring virus and spyware activity Securing Mac Clients Touring the SEP for Mac client Securing Mac clients Monitoring Mac clients Securing Linux Clients Navigating the Linux client Tailoring Virus and Spyware settings for Linux clients Monitoring Linux clients Providing Granular Control with Host Integrity Ensuring client compliance with Host Integrity Configuring Host Integrity Troubleshooting Host Integrity Monitoring Host Integrity Controlling Application and File Access Describing Application Control and concepts Creating application rulesets to restrict how applications run Monitoring Application Control events Restricting Device Access for Windows and Mac Clients Describing Device Control features and concepts for Windows and Mac clients Enforcing access to hardware using Device Control Discovering hardware access policy violations with reports, logs, and notifications Hardening Clients with System Lockdown What is System Lockdown? Determining to use System Lockdown in Whitelist or Blacklist mode Creating whitelists for blacklists Protecting clients by testing and Implementing System Lockdown Customizing Policies based on Location Creating locations to ensure the appropriate level of security when logging on remotely Determining the criteria and order of assessment before assigning policies Assigning policies to locations Monitoring locations on the SEPM and SEP client Managing Security Exceptions Creating file and folder exceptions for different scan types Describing the automatic exclusion created during installation Managing Windows and Mac exclusions Monitoring security exceptions

Securing Cisco Networks with Snort Rule Writing Best Practices (SSFRULES) v2.0
By Nexus Human
Duration 3 Days 18 CPD hours This course is intended for This course is for technical professionals to gain skills in writing rules for Snort-based intrusion detection systems (IDS) and intrusion prevention systems (IPS). The primary audience includes: Security administrators Security consultants Network administrators System engineers Technical support personnel using open source IDS and IPS Channel partners and resellers Overview After taking this course, you should be able to: Describe the Snort rule development process Describe the Snort basic rule syntax and usage Describe how traffic is processed by Snort Describe several advanced rule options used by Snort Describe OpenAppID features and functionality Describe how to monitor the performance of Snort and how to tune rules The Securing Cisco Networks with Snort Rule Writing Best Practices (SSFRules) v2.0 course shows you how to write rules for Snort, an open-source intrusion detection and prevention system. Through a combination of expert-instruction and hands-on practice, this course provides you with the knowledge and skills to develop and test custom rules, standard and advanced rules-writing techniques, how to integrate OpenAppID into rules, rules filtering, rules tuning, and more. The hands-on labs give you practice in creating and testing Snort rules. Course Outline Introduction to Snort Rule Development Snort Rule Syntax and Usage Traffic Flow Through Snort Rules Advanced Rule Options OpenAppID Detection Tuning Snort Lab outline Connecting to the Lab Environment Introducing Snort Rule Development Basic Rule Syntax and Usage Advanced Rule Options OpenAppID Tuning Snort

Lean Six Sigma Green Belt Course - 8 Courses Bundle
By NextGen Learning
Are you ready to embark on an enlightening journey of wisdom with the Lean Six Sigma Green Belt bundle, and pave your way to an enriched personal and professional future? If so, then Step into a world of knowledge with our course bundle - Lean Six Sigma Green Belt. Delve into eight immersive CPD Accredited courses, each a standalone course: Complete Lean Six Sigma Green Belt Course for Service Industry Advance Lean Six Sigma Black Belt Course Professional Lean Management: Service Industry Lean Six Sigma: Toolkit Project Management Fundamentals of Quality Management Process Improvement Process Mapping: Toolkit Traverse the vast landscapes of theory, unlocking new dimensions of understanding at every turn. Let the Lean Six Sigma Green Belt bundle illuminate your path to wisdom. The Lean Six Sigma Green Belt bundle offers a comprehensive exploration into a rich tapestry of vast knowledge across eight carefully curated courses. The journey is designed to enhance your understanding and critical thinking skills. Each course within the bundle provides a deep-dive into complex theories, principles, and frameworks, allowing you to delve into the nuances of the subject matter at your own pace. In the framework of the Lean Six Sigma Green Belt package, you are bestowed with complimentary PDF certificates for all the courses included in this bundle, all without any additional charge. Adorn yourself with the Lean Six Sigma Green Belt bundle, empowering you to traverse your career trajectory or personal growth journey with self-assurance. Register today and ignite the spark of your professional advancement! So, don't wait further and join the Lean Six Sigma Green Belt community today and let your voyage of discovery begin! Learning Outcomes: Attain a holistic understanding in the designated areas of study with the Lean Six Sigma Green Belt bundle. Establish robust bases across each course nestled within the Lean Six Sigma Green Belt bundle. Decipher intricate concepts through the articulate content of the Lean Six Sigma Green Belt bundle. Amplify your prowess in interpreting, scrutinising, and implementing theories. Procure the capacity to engage with the course material on an intellectual and profound level. Become proficient in the art of problem-solving across various disciplines. Stepping into the Lean Six Sigma Green Belt bundle is akin to entering a world overflowing with deep theoretical wisdom. Each course within this distinctive bundle is an individual journey, meticulously crafted to untangle the complex web of theories, principles, and frameworks. Learners are inspired to explore, question, and absorb, thus enhancing their understanding and honing their critical thinking skills. Each course invites a personal and profoundly enlightening interaction with knowledge. The Lean Six Sigma Green Belt bundle shines in its capacity to cater to a wide range of learning needs and lifestyles. It gives learners the freedom to learn at their own pace, forging a unique path of discovery. More than just an educational journey, the Lean Six Sigma Green Belt bundle fosters personal growth, enabling learners to skillfully navigate the complexities of the world. The Lean Six Sigma Green Belt bundle also illuminates the route to a rewarding career. The theoretical insight acquired through this bundle forms a strong foundation for various career opportunities, from academia and research to consultancy and programme management. The profound understanding fostered by the Lean Six Sigma Green Belt bundle allows learners to make meaningful contributions to their chosen fields. Embark on the Lean Six Sigma Green Belt journey and let knowledge guide you towards a brighter future. CPD 80 CPD hours / points Accredited by CPD Quality Standards Who is this course for? Individuals keen on deepening their firm understanding in the respective fields. Students pursuing higher education looking for comprehensive theory modules. Professionals seeking to refresh or enhance their knowledge. Anyone with a thirst for knowledge and a passion for continuous learning. Career path Armed with the Lean Six Sigma Green Belt bundle, your professional journey can reach new heights. The comprehensive theoretical knowledge from this bundle can unlock diverse career opportunities across several fields. Whether it's academic research, consultancy, or programme management, the Lean Six Sigma Green Belt bundle lays a solid groundwork. Certificates CPD Certificate Of Completion Digital certificate - Included 8 Digital Certificates Are Included With This Bundle CPD Quality Standard Hardcopy Certificate (FREE UK Delivery) Hard copy certificate - £9.99 Hardcopy Transcript - £9.99
