- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
3095 Associate courses in Derry/Londonderry delivered Online
World of Computer Networking: Your CCNA start
By Packt
This course will help you to prepare for the Cisco Certified Network Associate (CCNA) certification exam. The course covers all the major topics of computer networking and network devices, such as Internet Protocol (IP) addressing, routing, switching, Transmission Control Protocol/Internet Protocol (TCP/IP), Network Address Translation (NAT), Dynamic Host Configuration Protocol (DHCP), and Domain Name System (DNS).

Database fundamentals training course description This three-day training course helps you prepare for Microsoft Technology Associate Exam 98-364, and build an understanding of these topics: Core Database Concepts, Creating Database Objects, Manipulating Data, Data Storage, and Administering a Database. What will you learn Describe core database concepts. Create database objects. Manipulate data. Describe data storage. Administer a database. Create a relational database consisting of 3 related tables. Database fundamentals training course details Who will benefit: Those working with databases. Prerequisites: None. Duration 3 days Database fundamentals training course contents Understanding core database concepts Flat-type databases, hierarchical databases, relational databases, database fundamentals, relational database concepts, using the SQL Server Management Studio Interface. Data Manipulation Language (DML), Data Definition Language (DDL), using DDL statements. Creating database objects Defining data types, using built-in data types, using exact numeric data types, using approximate numeric data types. Creating and using tables. Creating views. Creating stored procedures, SQL injections. Manipulating data Using Queries to select data, combining conditions, using the BETWEEN clause, using the NOT clause, using the UNION clause, using the EXCEPT and INTERSECT clauses, using the JOIN clause. Using Queries to insert data, Inserting data. Updating data and databases, Using the UPDATE statement. Deleting data, Using the DELETE statement, truncating a table with TRUNCATE TABLE, deleting a table with DROP TABLE, using referential integrity. Understanding data storage Normalising a database, normalization, first normal form, second normal form, third normal form, fourth normal form, fifth normal form. Primary, foreign and composite keys, clustered and non-clustered indexes, creating a non-clustered table. Administering a Database Securing Databases, server-level security, database-level security, Windows security, SQL authentication, database server roles, granting access to a database, fixed database roles, object permissions, managing roles, ownership chains, reviewing a sample security model. Backing up and restoring databases, recovery models, backup devices.

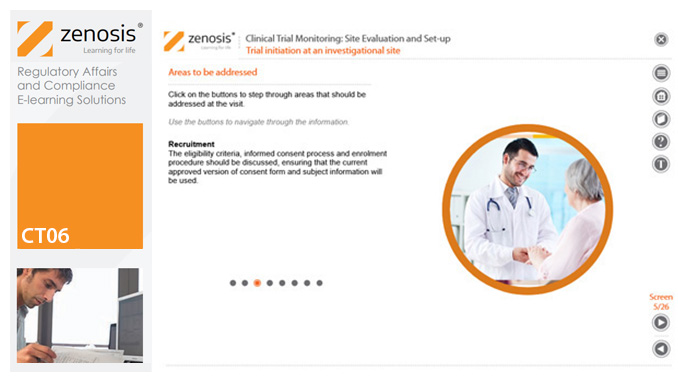
CT06: Clinical Trial Monitoring: Site Evaluation and Setup
By Zenosis
The sponsor of a clinical trial needs to reach agreement with clinical investigators to conduct the trial. The suitability of investigators and their institutional sites, typically hospitals, has to be evaluated, and the trial has to be set up at each site. This module describes the processes involved, focusing particularly on the role of a Clinical Research Associate (CRA) employed or contracted by the sponsor to monitor the trial.
CWSP training course description A hands-on training course concentrating solely on WiFi security with an emphasis on the delegates learning the necessary knowledge and skills to pass the CWSP exam. The course progresses from simple authentication, encryption and key management onto in depth coverage of 802.X and EAP along with many other security solutions such as access control, intrusion prevention and secure roaming. What will you learn Demonstrate the threats to WiFi networks. Secure WiFi networks. Configure: WPA2 RADIUS 802.1x EAP Pass the CWSP exam. CWSP training course details Who will benefit: Technical network staff. Technical security staff. Prerequisites: Certified Wireless Network Associate. Duration 5 days CWSP training course contents WLAN Security overview Standards, security basics, AAA, 802.11 security history. Hands on WLAN connectivity. Legacy 802.11 security Authentication: Open system, shared key. WEP. VPNs. MAC filters. SSID segmentation, SSID cloaking. Hands on Analysing 802.11 frame exchanges, viewing hidden SSIDs. Encryption Basics, AES, TKIP, CCMP, WPA, WPA2. Hands on Decrypting 802.11 data frames. 802.11 layer 2 authentication 802.1X: Supplicant, Authenticator, Authentication server. Credentials. Legacy authentication. EAP, Weak EAP protocols, Strong EAP protocols: EAP -PEAP, EAP-TTLS, EAP-TLS, EAP-FAST. Hands on Analysing 802.1X/EAP frames. 802.11 layer 2 dynamic key generation Robust Security Network. Hands on Authentication and key management. SOHO 802.11 security WPA/WPA2 personal, Preshared Keys, WiFi Protected Setup (WPS). Hands on PSK mapping. WLAN security infrastructure DS, Autonomous APs, WLAN controllers, split MAC, mesh, bridging, location based access control. Resilience. Wireless network management system. RADIUS/LDAP servers, PKI, RBAC. Hands on 802.1X/EAP configuration. RADIUS configuration. 802.11 Fast secure roaming History, RSNA, OKC, Fast BSS transition, 802.11k. Hands on Roaming. Wireless security risks Rogue devices, rogue prevention. Eavesdropping, DOS attacks. Public access and hotspots. Hands on Backtrack. WiFi security auditing Layer 1 audit, layer 2 audit, pen testing. WLAN security auditing tools. WiFi security monitoring Wireless Intrusion Detection and Prevention Systems. Device classification, WIDS/WIPS analysis. Monitoring. 802.11w. Hands on Laptop spectrum analysers. VPNs, remote access, guest access Role of VPNs in 802.11, remote access, hotspots, captive portal. Wireless security policies General policy, functional policy, recommendations.

Retail Management: Retail Buying and Merchandising - CPD Certified
4.7(47)By Academy for Health and Fitness
24-Hour Knowledge Knockdown! Prices Reduced Like Never Before Tired of the same old retail routine? Do you crave a career filled with challenge, creativity where you can directly influence customer choices and trends? The UK retail industry is booming, with over 3 million people employed in varying roles, and this power-packed bundle is your golden ticket to success! Our jam-packed bundle equips you with the skills to rule the retail roost! Learn the secrets of buying, merchandising, and operations like a pro. Master the art of data-driven decision making, craft winning sales strategies, and design show-stopping store displays that turn browsers into buyers! We'll also cover essential topics like consumer rights and supply chain management, making you a retail rockstar with a complete skillset. Courses are Included in This Bundle: Course 01: Retail Management Course 02: Retail Data Analytics Course 03: Retail Associate Certificate Course 04: Understanding Retail Operations Course 05: Business Management Course 06: Supply Chain Management Course 07: Warehouse Operative Course 08: Inventory Management Training Course 09: Sales and Marketing Skills Course 10: Visual Merchandising Course 11: Consumer Rights Awareness Don't just survive in retail, thrive! Enrol today and unlock your full potential. Learning Outcomes of Retail Management Gain a comprehensive understanding of retail operations and management principles. Analyze retail data to identify customer trends and inform buying decisions. Develop effective strategies for sourcing, managing, and selling merchandise. Master the art of visual merchandising to create attractive and engaging store displays. Understand consumer rights and how to implement best practices in customer service. Enhance your sales and marketing skills to boost revenue and customer satisfaction. Why Choose Us? Get a Free CPD Accredited Certificate upon completion of Retail Management Get a free student ID card with Retail Management Training program (£10 postal charge will be applicable for international delivery) The Retail Management is affordable and simple to understand This course is entirely online, interactive lesson with voiceover audio Get Lifetime access to the Retail Management course materials The Retail Management comes with 24/7 tutor support Start your learning journey straightaway! *** Course Curriculum *** Course 01: Retail Management Module 01: Introduction To Retail Management Module 02: Retail Strategy Module 03: Retail Buying And Merchandising Module 04: Retail Pricing Module 05: Supply Chain Management In Retailing Module 06: The Sales Process And Dealing With Customers At The Checkout Module 07: Importance Of Consumer Behaviour Module 08: Taking Trends And Targeting Customers Effectively Module 09: The Importance Of Communicating With Customers Module 10: Choosing A Retail Location Module 11: Retail Psychology Module 12: Negotiate The Right Deal With Suppliers Module 13: Develop Store Security Procedures Module 14: Management Skills For Leading Your Team Module 15: Selling In Multiple Channels Module 16: Retail Brand Management Module 17: Health & Safety For Retail Stores Module 18: Consumer Rights Act Course 02: Retail Data Analytics Module 1: Introduction To Retail Analytics Module 2: Retail Psychology Module 3: Retail And Data Analytics Module 4: Benefits Of Retail Analytics Module 5: Retail Strategy Module 6: Retail Buying And Merchandising Module 7: Forecasting Module 8: Retail Pricing Module 9: Analytics Software Module 10: Supply Chain Management In Retailing Module 11: The Sales Process And Dealing With Customers At The Checkout Module 12: Selling In Multiple Channels Module 13: Taking Trends And Targeting Customers Effectively Course 03: Retail Associate Certificate Module 01: Introduction to Retail Associate Module 02: Qualities of a Retail Associate Module 03: Retail Psychology Module 04: Importance of Consumer Behaviour Module 05: The Importance of Communicating with Customers Module 06: Taking Trends and Targeting Customers Effectively Module 07: The Sales Process and Dealing with Customers at the Checkout Module 08: Consumer Rights Act Module 09: Introduction to Visual Merchandising Module 10: In-Store Design Module 11: Exterior Design Module 12: Health & Safety for Retail Stores Module 13: Management Skills for Leading Your Team =========>>>>> And 9 More Courses <<<<<========= How will I get my Certificate? After successfully completing the course, you will be able to order your Certificates as proof of your achievement. PDF Certificate: Free (Previously it was £12.99*11 = £143) CPD Hard Copy Certificate: £29.99 CPD 110 CPD hours / points Accredited by CPD Quality Standards Who is this course for? Anyone interested in learning more about the topic is advised to take this bundle. This bundle is ideal for: Aspiring Buyers Merchandisers Sales Associates Store Managers Retail Entrepreneurs Career Changers Requirements You will not need any prior background or expertise to enrol in this bundle. Career path After completing this bundle, you are to start your career or begin the next phase of your career. Buyer Merchandiser Sales Manager Store Manager Retail Operations Manager Retail Business Owner Certificates CPD Accredited Digital Certificate Digital certificate - Included Upon passing the Course, you need to order a Digital Certificate for each of the courses inside this bundle as proof of your new skills that are accredited by CPD QS for Free. CPD Accredited Hard Copy Certificate Hard copy certificate - £29.99 Please note that International students have to pay an additional £10 as a shipment fee.

Complete Cisco Bundle with 6 Exams
By Hudson
This course bundle is ideal for anyone looking to establish their Cisco networking career. It consists of one Cisco Certified Network Associate (CCNA) certification, one Cisco Certified DevNet Associate (CCDA) certification, and four Cisco Certified Networking Professional (CCNP) certifications. Although there are no formal prerequisites to enrol on the CCNA, CCDA, or CCNP certification courses and sit the exams, learners should have a good foundation knowledge in networking. The newly retooled CCNA covers a breadth of topics, including: Network fundamentals Network access IP connectivity IP services Security fundamentals Automation and programmability Achieving CCNA certification is the first step in preparing for a career in networking technologies. To earn your CCNA certification, you only need to pass one exam – which covers a broad range of fundamentals for IT careers, based on the latest networking technologies. The Cisco Certified DevNet Associate certification validates your skills and knowledge in understanding and using APIs, Cisco platforms and development, application development and security, and infrastructure and automation. Ideally, DevNet Associates candidates also have one or more years of experience with software development including Python programming. The CCNP is the next level from the CCNA and CCDA. As with the CCNA, there are no formal prerequisites to enrol on the CCNP certification course and sit for the exams. Learners taking a CCNP course generally have an in-depth knowledge of networking, as well as a good understanding of Cisco technologies. The typical certification path for most learners would begin with either the CCDA or CCNA, then progress onto the CCNP. Learners need to pass two exams (one core exam and one concentration exam) in order to gain one CCNP certification. This course bundle includes the core exam and three concentration exams. Once a learner has passed the core exam, they can choose to specialise in one or all three of the CCNP concentration areas listed in this course. The core exam’s focus is based around implementing and operating Cisco enterprise network core technologies.

Interpersonal Skills
By OnlineCoursesLearning.com
Relational Skills Relational abilities are social abilities that permit you to connect and speak with individuals around you. They shape what our identity is and how others see us in our day by day lives. These capacities are gained from the encounters you have had all through life. While this range of abilities can come effectively to numerous individuals, a few group think that its more troublesome associating in the working environment, home and somewhere else. As we are each of the a result of our current circumstance, everybody is distinctive by they way they figured out how to associate with others. Discovering manners by which to better ourselves is and consistently has been achievable. In this course, we will talk about the significance that these abilities play in driving an effective and satisfying life. You will find that there are manners by which to prepare yourself to utilize your learned practices, to advance and improve any circumstance where you may get yourself. The outcome is a more sure form of yourself that can survey and beat issues and issues. It requires some investment, however the excellence of relational abilities is that they can generally be educated and relearned when required. Dealing with these practices every day can prompt a seriously compensating life and profession. What You Will Learn: How crucial relational abilities are in the work environment, home, and different conditions How you can improve your range of abilities through training and different techniques That you don't need to continue to utilize the very practices that you have done previously How a solid range of abilities gives you certainty and harmony in any circumstance The Benefits of Taking This Course: You can grow better abilities to use at work and at home You can improve how you associate with others You can distinguish what you need to fix with regards to your learned practices You will actually want to enter any friendly circumstance with certainty

Affiliate Marketing
By OnlineCoursesLearning.com
Affiliate Marketing Certification Member advertising is getting progressively famous as an intriguing method to acquire income. Offshoot showcasing alludes to exchanging different items on your site, blog or video, and so on and getting paid a commission for it. There are numerous approaches to procure income through associate showcasing, and, despite the fact that you can acquire a great many pounds, you should be aware of a few elements. The seminar on offshoot advertising clarifies how you can advance without any preparation in the field of associate showcasing and ultimately become effective. What's Covered in the Course? Some significant points canvassed in the seminar on partner advertising include: Instructions to pick the right specialty for offshoot showcasing, and the variables that you ought to consider; The most effective method to advance your subsidiary items on your site or off your site, utilizing aggregator locales; The most effective method to compose articles and item audits, and so on that help increment positioning; The various sorts of offshoot showcasing offers, including pay per call/click, membership, ordinary buy and repeating commissions; Instructions to utilize the AIDA guideline, to compose fascinating 'How to' articles and surveys, etc'; How aggregator locales use treats, to follow buyer conduct; The most ideal approaches to move toward organizations straightforwardly, in case you're keen on their offshoot items; The advantages and burdens of Amazon as an offshoot accomplice; An outline and examination of other partner sites, including CjDotCom, Sharecare, Clickbank, etc, and how to utilize their highlights for your potential benefit; Instructions to amplify traffic and deals, by utilizing uncommon techniques. This video course offers the accompanying advantages Advantages of examining the seminar on offshoot showcasing include: You will see how to pick a partner specialty that turns out best for you; You will actually want to explore different avenues regarding diverse advertising procedures, while, simultaneously, arranging a decent subsidiary offer; You acquire a decent comprehension of the relative multitude of components that effect offshoot promoting. The tips, stunts and techniques clarified in this course will assist you with keeping away from traps and stay on target.

SC-100T00 Microsoft Cybersecurity Architect
By Nexus Human
Duration 4 Days 24 CPD hours This course is intended for This course is for experienced cloud security engineers who have taken a previous certification in the security, compliance and identity portfolio. Specifically, students should have advanced experience and knowledge in a wide range of security engineering areas, including identity and access, platform protection, security operations, securing data, and securing applications. They should also have experience with hybrid and cloud implementations. Beginning students should instead take the course SC-900: Microsoft Security, Compliance, and Identity Fundamentals. This is an advanced, expert-level course. Although not required to attend, students are strongly encouraged to have taken and passed another associate level certification in the security, compliance and identity portfolio (such as AZ-500, SC-200 or SC-300) before attending this class. This course prepares students with the expertise to design and evaluate cybersecurity strategies in the following areas: Zero Trust, Governance Risk Compliance (GRC), security operations (SecOps), and data and applications. Students will also learn how to design and architect solutions using zero trust principles and specify security requirements for cloud infrastructure in different service models (SaaS, PaaS, IaaS). Prerequisites Highly recommended to have attended and passed one of the associate level certifications in the security, compliance and identity portfolio (such as AZ-500T00 Microsoft Azure Security Technologies, SC-200T00: Microsoft Security Operations Analyst, or SC-300T00: Microsoft Identity and Access Administrator.) Advanced experience and knowledge in identity and access, platform protection, security operations, securing data and securing applications. Experience with hybrid and cloud implementations. 1 - Introduction to Zero Trust and best practice frameworks Zero Trust initiatives Zero Trust technology pillars part 1 Zero Trust technology pillars part 2 2 - Design solutions that align with the Cloud Adoption Framework (CAF) and Well-Architected Framework (WAF) Define a security strategy Cloud Adoption Framework secure methodology Design security with Azure Landing Zones The Well-Architected Framework security pillar 3 - Design solutions that align with the Microsoft Cybersecurity Reference Architecture (MCRA) and Microsoft cloud security benchmark (MCSB) Design solutions with best practices for capabilities and controls Design solutions with best practices for attack protection 4 - Design a resiliency strategy for common cyberthreats like ransomware Common cyberthreats and attack patterns Support business resiliency Ransomware protection Configurations for secure backup and restore Security updates 5 - Case study: Design solutions that align with security best practices and priorities Case study description Case study answers Conceptual walkthrough Technical walkthrough 6 - Design solutions for regulatory compliance Translate compliance requirements into a security solution Address compliance requirements with Microsoft Purview Address privacy requirements with Microsoft Priva Address security and compliance requirements with Azure policy Evaluate infrastructure compliance with Defender for Cloud 7 - Design solutions for identity and access management Design cloud, hybrid and multicloud access strategies (including Azure AD) Design a solution for external identities Design modern authentication and authorization strategies Align conditional access and Zero Trust Specify requirements to secure Active Directory Domain Services (AD DS) Design a solution to manage secrets, keys, and certificates 8 - Design solutions for securing privileged access The enterprise access model Design identity governance solutions Design a solution to secure tenant administration Design a solution for cloud infrastructure entitlement management (CIEM) Design a solution for privileged access workstations and bastion services 9 - Design solutions for security operations Design security operations capabilities in hybrid and multicloud environments Design centralized logging and auditing Design security information and event management (SIEM) solutions Design solutions for detection and response Design a solution for security orchestration, automation, and response (SOAR) Design security workflows Design threat detection coverage 10 - Case study: Design security operations, identity and compliance capabilities Case study description Case study answers Conceptual walkthrough Technical walkthrough 11 - Design solutions for securing Microsoft 365 Evaluate security posture for collaboration and productivity workloads Design a Microsoft 365 Defender solution Design configurations and operational practices for Microsoft 365 12 - Design solutions for securing applications Design and implement standards to secure application development Evaluate security posture of existing application portfolios Evaluate application threats with threat modeling Design security lifecycle strategy for applications Secure access for workload identities Design a solution for API management and security Design a solution for secure access to applications 13 - Design solutions for securing an organization's data Design a solution for data discovery and classification using Microsoft Purview Design a solution for data protection Design data security for Azure workloads Design security for Azure Storage Design a security solution with Microsoft Defender for SQL and Microsoft Defender for Storage 14 - Case study: Design security solutions for applications and data Case study description Case study answers Conceptual walkthrough Technical walkthrough 15 - Specify requirements for securing SaaS, PaaS, and IaaS services Specify security baselines for SaaS, PaaS, and IaaS services Specify security requirements for web workloads Specify security requirements for containers and container orchestration 16 - Design solutions for security posture management in hybrid and multicloud environments Evaluate security posture by using Microsoft Cloud Security Benchmark Design integrated posture management and workload protection Evaluate security posture by using Microsoft Defender for Cloud Posture evaluation with Microsoft Defender for Cloud secure score Design cloud workload protection with Microsoft Defender for Cloud Integrate hybrid and multicloud environments with Azure Arc Design a solution for external attack surface management 17 - Design solutions for securing server and client endpoints Specify server security requirements Specify requirements for mobile devices and clients Specify internet of things (IoT) and embedded device security requirements Secure operational technology (OT) and industrial control systems (ICS) with Microsoft Defender for IoT Specify security baselines for server and client endpoints Design a solution for secure remote access 18 - Design solutions for network security Design solutions for network segmentation Design solutions for traffic filtering with network security groups Design solutions for network posture management Design solutions for network monitoring 19 - Case study: Design security solutions for infrastructure Case study description Case study answers Conceptual walkthrough Technical walkthrough Additional course details: Nexus Humans SC-100T00 Microsoft Cybersecurity Architect training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the SC-100T00 Microsoft Cybersecurity Architect course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Certified Data Analyst Pathway with Career Guarantee
By NuYew Ltd
Accelerate Your Data Analyst Career: Fast-Track Program with Exams, TOTUM Card & 5-Year Support. Enrol Today! Study methodOnline Duration9 months · Self-paced Access to content5 years CertificationsCompTIA IT Fundamentals CertificationCertified Data Analysis ProfessionalMicrosoft Azure Data FundamentalsPearson IT Specialist PythonPearson IT Specialist AI (Artificial Intelligence)Pearson IT Specialist DatabasesMicrosoft Office Specialist Excel CertificationMicrosoft Power BI Data Analyst Associate (PL-300)Certificates Official CompTIA Certification - Free Additional info Exam(s) / assessment(s) is included in price Tutor is available to students TOTUM card included in price Job guarantee programme is included in this course Overview Learn the most in-demand digital skills in the world today with the Nuyew Tech Academy A Data and Business Intelligence Analyst gathers, cleans, and studies data sets to help solve problems. Gain the job-ready skills for an entry-level Data and Business Intelligence Analyst role and position yourself competitively in the thriving job market for data and business analysts, which will see a 20% growth until 2028 and beyond. Certifications CompTIA IT Fundamentals Certification Certified Data Analysis Professional Awarded by CompTIA Microsoft Azure Data Fundamentals Microsoft Office Specialist Excel Certification Microsoft Power BI Data Analyst Associate (PL-300) Awarded by Microsoft Pearson IT Specialist Python Pearson IT Specialist AI (Artificial Intelligence) Pearson IT Specialist Databases Awarded by Pearson Description With a national shortage of Data and Business Intelligence Analysts, starting salaries of up to £25,000 per annum (average UK Salary £60,000) and amazing future employed and self-employed career prospects, take the next step today with our Fast Track Data and Business Intelligence Analyst Programme. What you can expect from our Fast Track Programme: World Class Education Energetic and unlimited 24/7 Student Support Real, tangible Career Outcomes 5 Years Career Support What our programme includes: Industry Recognised Qualifications CompTIA ITF+ (IT Fundamentals) CompTIA A+ CompTIA Network+ CompTIA Security+ CompTIA Data+ Exams Includes all Exams and Unlimited Re-Sits 5 Years Career Support Guarantee As part of our unique Support Guarantee, our Career Support Team will assist you with: CV writing Expert careers advice Interview preparation Identifying and applying for the best opportunities in your area As a student in the Nuyew Tech Academy you will also be given exclusive access to our Career Skills Academy which includes advanced courses on Employability, CV Preparation, Interview Skills and Technique and everything else you need to get ready for your new Career. Who is this course for? This course is open to anyone interested in pursuing a Career in Data Analytics and Business Intelligence. Our Foundation Level provides the flexibility for us to accommodate students with any level of previous knowledge and experience. Requirements This course is open to all and has no pre-requisites All you need is a passion for technology and a strong desire to succeed. Career path Our programme is designed to enable you to achieve an Entry Level/Helpdesk role during training (£18k-£24K) ensuring that you also have the vital work experience required to enter the Tech Industry at a higher level (Av Salary £60K).
