- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
1680 Architecture courses in Syston delivered Online
Python Programming for Beginners - Learn in 100 Easy Steps
By Packt
Learn Python Programming using a Step By Step Approach with 200+ code examples.

Did you know CAD designers in UK, on average make over £50,000 annually? This online CAD training bundle teaches students how to use computer-aided design software to create 2D and 3D models. The course covers drafting and design principles and how to create and edit technical drawings. Students will also learn how to use CAD tools for visualisation and simulation and how to apply their skills in various industries. By completing the program, students will have a strong foundation in using CAD software and be able to design and communicate their ideas effectively. If you want to learn CAD, then stop looking and start learning. Enrol on the course now and start designing your future. Along with this CAD Training course, you will get 14 premium courses, 14 PDF certificates (Main Course + Additional Courses) Student ID card as gifts. This CAD Training Bundle Consists of the following Premium courses: Course 01: CAD Design Training: Assemblies, Modelling And Civil Drawings Course 02: Learn AutoCAD Programming using VB.NET - Hands On! Course 03: AutoCAD VBA Programming Course 04: AutoCAD Electrical Design Course 05: Professional Interior Design & Construction Course 06: WELL Building Standard Course 07: Solid Works Foundation Training Course 08: Architectural Studies Course 09: Interior Design Professional Diploma Course 10: LEED V4: Building Design and Construction Course 11: Construction Cost Estimation Diploma Course 12: Stress Management Training Course 13: Time Management Course 14: Decision Making and Critical Thinking By the end of the course, you'll: Understand the basics of computer-aided design (CAD) software and its various functions and features. Develop skills in creating and editing 2D and 3D designs using CAD software. Learn how to use tools such as dimensioning, text, and symbols to create professional-grade drawings. Understand the different file formats used in CAD and how to export and import designs. Gain experience in working with layers and creating technical drawings for engineering, architecture, or manufacturing projects. Develop the ability to work with custom templates and macros to streamline design workflows. Improve your problem-solving and critical thinking skills through the use of CAD software to solve real-world design challenges. Enrol now in CAD Training to advance your career, and use the premium study materials from Apex Learning. The bundle incorporates basic to advanced level skills to shed some light on your way and boost your career. Hence, you can strengthen your CAD Training expertise and essential knowledge, which will assist you in reaching your goal. Moreover, you can learn from any place in your own time without travelling for classes. Course 01: Learn AutoCAD Programming using VB.NET - Hands On! Introduction Exploring AutoCAD .NET API Components VB.NET Creating AutoCAD Objects using VB.NET Manipulating Objects using VB.NET Exploring Dictionaries using VB.NET User Interactions in VB.NET Selection Sets and Filters Developing Projects - Hands On Conclusion Certificate: PDF Certificate: Free (Previously it was £6*11 = £66) Hard Copy Certificate: Free (For The Title Course: Previously it was £10) CPD 120 CPD hours/ points Accredited by CPD Quality Standards Who is this course for? Anyone from any background can enrol in this CAD Training bundle. Requirements This CAD Training course has been designed to be fully compatible with tablets and smartphones. Career path CAD is a spontaneously growing field with increasing job opportunities in a wide range of sectors. Our bindle training course will assist the learners in pursuing jobs like - CAD Technician - £17,000 to £35,000 Building Technician - £19,000 to £35,000 Mechanical Engineering Technician - £24,000 to £40,000 Architectural technician - £18,000 to £40,000 Certificates Certificate of completion Digital certificate - Included You will get the PDF Certificate for the title course (Level 5 CAD Designer Training) absolutely Free! Certificate of completion Hard copy certificate - Included You will get the Hard Copy certificate for the title course (Level 5 CAD Designer Training) absolutely Free! Other Hard Copy certificates are available for £10 each. Please Note: The delivery charge inside the UK is £3.99, and the international students must pay a £9.99 shipping cost.

Go Full Stack with Spring Boot and React
By Packt
Build your first full stack application with React and Spring Boot. Become a full-stack web developer now!

Tired of browsing and searching for the course you are looking for? Can't find the complete package that fulfils all your needs? Then don't worry as you have just found the solution. Take a minute and look through this 14-in-1 extensive bundle that has everything you need to succeed in Structural Engineering and other relevant fields! After surveying thousands of learners just like you and considering their valuable feedback, this all in one Structural Engineering bundle has been designed by industry experts. We prioritised what learners were looking for in a complete package and developed this in-demand Structural Engineering course that will enhance your skills and prepare you for the competitive job market. Furthermore, to help you showcase your expertise in Structural Engineering, we have prepared a special gift of 1 hardcopy certificate and 1 PDF certificate for the title course completely free of cost. These certificates will enhance your credibility and encourage possible employers to pick you over the rest. This Structural Engineering Bundle Consists of the following Premium courses: Course 01: Diploma in Construction Management Course 02: Architectural Studies Course 03: Quantity Surveyor Diploma Course 04: Building Surveyor Course 05: Land Surveying Course 06: Bricklaying Course 07: Construction Cost Estimation Diploma Course 08: Construction Estimation using RSMeans Course 09: AutoCAD VBA Programming - Beginner course Course 10: Property Law and Legislation Course 11: Construction Industry Scheme (CIS) Course 12: WELL Building Standard Course 13: LEED V4: Building Design and Construction Course 14: Construction Safety Benefits you'll get from choosing Apex Learning: Pay once and get lifetime access to 14 CPD courses Certificates, student ID for the Course included in a one-time fee Free up your time - don't waste time and money travelling for classes Accessible, informative modules of Course courses designed by expert instructors Learn about Course at your ease - anytime, from anywhere Study Course from your computer, tablet or mobile device CPD accredited Course - improve the chance of gaining professional skills How will I get my Certificate? After successfully completing the course, you will be able to order your CPD Accredited Certificates (PDF + Hard Copy) as proof of your achievement. PDF Certificate: Free (For The Title Course) Hard Copy Certificate: Free (For The Title Course) PS: The delivery charge inside the UK is £3.99, and the international students have to pay £9.99. Curriculum of Bundle Course 01: Diploma in Construction Management Introduction to Construction Management Project Life Cycle and Success Cost Management Preliminary Site Investigation and Site Organisation Site Management Planning and Management of Equipment Construction Materials Management Vendor Analysis in Construction Management Construction Procurement Stock Control Supply Chain Management The Main Participators Quality Assurance and Customer Care Course 02: Architectural Studies Introduction to Architectural Studies Ancient Architecture Architectural Ideas and Movements Architectural Styles Art Deco Architectural Style Scandinavian Architectural Style Victorian Architectural Style Classical and Early Christian Architectural Style Gothic Architectural Style Baroque and Rococo Architectural Style Course 03: Quantity Surveyor Diploma Quantity Survey An Introduction Development of the Quantity Surveyor Quantity Surveying Measurement Cost Management Pricing and Operational Estimation Contract Management and Tendering Procurement and Bill Preparation Course 04: Building Surveyor Building Survey: An Introduction Building Law Principles Building Procurement and Contract Administration Building Information Modelling Building Technology The Procedure of Building Survey and Surveys of Historic Buildings Beginning of the Survey: Foundation and In-depth Survey in Walls Ground Level Investigation: Floors and Investigation Above the Ground: Roofs and Chimneys And Many More... Course 05: Land Surveying Introduction to Land Surveying Land Surveying Basics Land Surveying Instrumentation Land Surveying Methods and Techniques Course 06: Bricklaying Introduction to Bricklaying Tools of Bricklaying Bonding of Bricklaying And Many More... Course 07: Construction Cost Estimation Diploma Introduction to Construction Management Cost Estimation Role of Cost Estimator and New Aspects of Cost Estimation Elements and Factors influencing Cost Estimation Cost Estimation in Construction Industry Cost Management Management of Materials for construction Course 08: Construction Estimation using RSMeans Introduction Quantity Take Off Cost Estimation using RSMeans Course 09: AutoCAD VBA Programming - Beginner course Introduction VBA Integrated Development Environment (IDE) Understanding AutoCAD Object Model in VBA Using Variables in VBA User Forms and Controls Conditionals and Decisions in VBA Course 10: Property Law and Legislation Introduction to Property Law Land Law Principles- Rights and Interests Registered and Unregistered Land Ownership and Possession of the Property Co-Ownership in Property Course 11: Construction Industry Scheme (CIS) Construction Industry Scheme (CIS) Coverage of the Scheme Contractors and Registration for the Scheme Verification Process The CIS Returns Course 12: WELL Building Standard Introduction Air Water Nourishment Light Fitness Comfort Mind Course 13: LEED V4: Building Design and Construction Introduction Integrative Process Location & Transportation Sustainable Sites Water Efficiency Course 14: Construction Safety Managing Health and Safety Risk Assessment and Common Risks Health and Safety Guidelines and Legislations Reporting Accidents at Work And Many More... CPD 140 CPD hours / points Accredited by CPD Quality Standards Who is this course for? Anyone from any background can enrol in this Structural Engineering bundle. Disclaimer: Our comprehensive course will enhance your theoretical knowledge to help you explore your opportunities in relevant sectors. But please note that this course is not a professional qualification and will not allow you to work professionally. Requirements Our Structural Engineering course is fully compatible with PCs, Macs, laptops, tablets and Smartphone devices. Career path Having this Structural Engineering expertise will increase the value of your CV and open you up to multiple job sectors. Certificates Certificate of completion Digital certificate - Included

Spring Framework Interview Guide - 200+ Questions and Answers
By Packt
This course comes bundled with basic to advanced level knowledge on Spring and Spring Boot with 200+ questions and answers. With REST API, JPA, Hibernate, and Spring Data JPA, you have the upper hand in your interviews for sure.

SketchUp Basic Level Training Course
By ATL Autocad Training London
Who is this course for? SketchUp Basic Level Training Course. Click here for more info: Website Ideal for newcomers to 3D modeling, it suits students, hobbyists, and professionals. Gain a strong foundation in SketchUp, perfect for careers in architecture and interior design. Our flexible 1-on-1 sessions let you tailor your learning schedule. Schedule sessions Monday to Saturday, 9 am to 7 pm. The 5-hour course adapts to your timeline, ensuring a personalized, supportive, and adaptable learning experience. Course Title: SketchUp Basic Course. Course Duration: 5 hours Understanding the Basics of SketchUp Introduction to SketchUp Navigating the SketchUp Environment Exploring Zoom, Pan, and Rotate Functions Familiarizing Yourself with the XYZ Axis Mastering SketchUp Tools Efficient Toolbar Selections Utilizing Templates for Projects Drawing with Precision Using the Pencil Tool Working with Fundamental Geometric Shapes Taking Accurate Measurements Advanced SketchUp Techniques Creating Circles and Arcs Harnessing Sticky Geometry Solutions Unveiling the Power of Tags (Formerly Layers) Streamlining Workflow with Keyboard Shortcuts Accurate Object Measurement within SketchUp Information Management and Database Usage Moving and Copying Objects Simple Array Techniques Mastering Rotational Manipulations Effortless Rotational Copying Fractional and Relative Scaling Component and Group Creation Constructing Components for Reusability Creating Efficient Groups Comparing the Advantages of Components and Groups Saving and Reusing Components Importing Components from Digital Repositories Advanced Modeling and Geometry Leveraging Push-Pull Operations Creating Complex Shapes with the Follow Me Tool Exploring Geometry Intersections Duplicating and Offsetting Faces, Edges, and Polygons Incorporating 2D Polygons into Your Drawings Skillful Use of the Paint Bucket Tool Materials and Textures Proficiency with the Materials Editor Applying High-Quality Textures Sourcing and Positioning Textures Graphics and Bitmap Considerations Crafting Scenes and Styles Generating and Customizing Scenes Managing Scenes and Styles Introduction to Animation and Presentation Animation Concepts Adding Dimensions to Your SketchUp Models Annotating Designs for Clarity Preparing Models for Printing Exporting Images and PDFs in 2D Formats This comprehensive SketchUp Fundamentals course will equip you with essential skills to create, modify, and present 3D models effectively. After completing our 5-hour SketchUp training, you'll achieve the following learning outcomes: Basic SketchUp Proficiency: Gain essential skills to navigate the SketchUp interface and utilize its core features effectively. Geometry Creation: Learn to create 2D and 3D geometric shapes, lines, and curves with precision. Rendering Concepts: Understand the fundamentals of rendering and how to apply basic rendering techniques to enhance your designs. Model Organization: Discover techniques for organizing and structuring your SketchUp models efficiently. Visualization Skills: Develop the ability to visualize and plan architectural and interior design concepts in 3D. Efficient Workflows: Acquire time-saving tips and tricks for streamlining your design workflow. Personal Projects: Apply your newfound skills to your personal design projects or professional endeavors. By the end of this short training, you'll have a solid foundation in SketchUp, allowing you to create and present basic 3D models and designs effectively. After SketchUp Training, You'll Acquire: Advanced 3D Modeling: Master the art of creating intricate 3D models, architectural designs, and detailed structures using SketchUp. Texture Mapping and Material Application: Learn to apply realistic textures and materials, enhancing the visual appeal of your 3D creations. Rendering Techniques: Explore rendering plugins like V-Ray or Twilight Render to create lifelike visualizations of your designs. Collaboration and Presentation: Develop skills to effectively collaborate with teams and present your ideas in professional and compelling ways. Project Visualization: Enhance your ability to transform conceptual ideas into visually stunning and detailed 3D representations. Job Opportunities: Architectural Designer: Create detailed architectural models for residential and commercial projects. Interior Designer: Design interior spaces, visualizing furniture placements, colors, and decor elements. Landscape Architect: Develop 3D landscape designs, showcasing outdoor spaces and environmental elements. 3D Modeler: Work in various industries, creating 3D models for animations, games, or simulations. Visualization Specialist: Provide visualization services to real estate agencies, design firms, or marketing companies, transforming ideas into compelling visuals. Why Choose Us? Tailored One-on-One Training: Exclusive coaching from skilled architects and designers, in-person or live online, Monday to Saturday. Customized Tutorials: Enhance your skills with tailored video tutorials to take home. Comprehensive Learning: Receive digital resources for thorough understanding and revision. Free Ongoing Support: Enjoy continuous assistance via phone or email, ensuring your success beyond the course. Flexible Syllabus: Adapted to your needs for focused learning. Official Certificate: Validate your expertise with our prestigious certification.

Cisco Engineering Cisco Meraki Solutions Part 1 (ECMS1) v2.1
By Nexus Human
Duration 1 Days 6 CPD hours This course is intended for After taking this course, you should be able to: Describe cloud architecture, administration, and licensing Understand hardware and features of all product families Implement best practices for troubleshooting and when to contact support Overview After taking this course, you should be able to: Implement core configurations for a full stack solution in the Meraki Dashboard Deploy foundational Meraki product features to meet basic IT requirements Understand and leverage essential Meraki Dashboard tools for troubleshooting The Engineering Cisco Meraki Solutions Part 1 (ECMS1) v2.1 is an introductory course that equips you with the technical knowledge and skills to confidently operate Cisco Meraki solutions as a unified management system of an entire network from a centralized dashboard. Through a full day of instruction including live demos and guided lab practice, you will learn how to implement core configurations for a full stack solution in the Meraki Dashboard and leverage essential Meraki Dashboard tools to enforce device security policies, deploy software and apps, and perform remote, live troubleshooting on managed devices. This is the first of two courses that prepare you for the Cisco Meraki Solutions Specialist certification exam. Describing the Cloud and the Cisco Meraki Dashboard Single Pane of Glass Management Cisco Meraki Full Stack Capabilities Describing Cisco Meraki Products and Administration Cisco Meraki MX Security and SD-WAN Appliance Cisco Meraki MS Switches Describing Cisco Meraki Troubleshooting Cisco Meraki Dashboard Sync and Real-Time Tools Integration of Cisco Meraki Monitoring and Troubleshooting Tools in Existing Systems

F2900 IBM Case Manager Essentials (V5.3.2)
By Nexus Human
Duration 1 Days 6 CPD hours This course is intended for This course is for solution architects, solution designers, administrators, product managers, or anyone who needs to learn the essentials of IBM Case Manager. Overview Describe the users of IBM Case Manager Identify components of IBM Case Manager Create and process a case Search for a case Review a case Add annotations and comments to a case Split a case Explore and identify the structure of a solution Add a custom task Add a quick task Identify IBM Case Manager integration options This course is an introduction to IBM Case Manager, concepts, functions, and architecture. Participants use an IBM Case Manager system to practice the skills that are required by case workers to process cases and create runtime tasks. Introduction to IBM Case Manager Describe the uses of IBM Case Manager Identify components of IBM Case Manager Create and process a case Identify a case List the components of a case type Describe the IBM Case Manager Client Add a case and process a work item Review a case Search for a case Review a case Add annotations and comments to a case Split a case Structure of a solution Describe IBM Case Manager solutions and their assets Identify IBM Case Manager environments Explore the IBM Case Manager Builder Step Designer Add runtime tasks Add a custom task Add a quick task IBM Case Manager integration options Identify IBM Case Manager integration options

CCCS Check Point Certified Cloud Specialist-Administrator
By Nexus Human
Duration 2 Days 12 CPD hours This course is intended for Technical professionals who support, install, deploy, or administer Check Point products in Cloud Environments. Overview Explain the nature of the cloud environment. Describe the five pillars of cloud architecture. Explain the Basics of Cloud Infrastructure. Explain the Basics of Cloud Automation. Explain Check Point Security Management and How it Applies to CloudGuard. Describe CloudGuard Security Gateway offerings. Describe Cloud Load Balancers. Explain CloudGuard Licensing. Explain the different Deployment options and architectures for CloudGuard. Explain how and why CloudGuard is automated. Describe the functions of CloudGuard that can be automated. Describe the tools used to automate CloudGuard. Explain CloudGuard Automation Requirements. Explain basic troubleshooting techniques specific to Check Point Security Management Servers and Security Gateways. Describe the steps for Troubleshooting CloudGuard Network Installation. Explain the tools and techniques used to troubleshoot CloudGuard Network Automation. Explain the need for Cloud Security Posture Management. Describe the posture management tools available in CloudGuard. Explain methods for correcting Cloud Security Posture Management issues. Learn basic concepts and develop skills necessary to administer Check Point CloudGuard security solutions Course Outline Deploy a Security Management Server in the Cloud. Install a Security Gateway Image. Create Virtual Networks. Deploy Internal and External Load Balancers Deploy a Security Gateway Using Templates. Assign Public IP Addresses to Cloud Devices Create Web Servers in the Cloud. Configure North-South Traffic Policy. Configure East-West Traffic Policy and Routes. Troubleshoot North-South Traffic Issues. Troubleshoot East-West Traffic Issues.

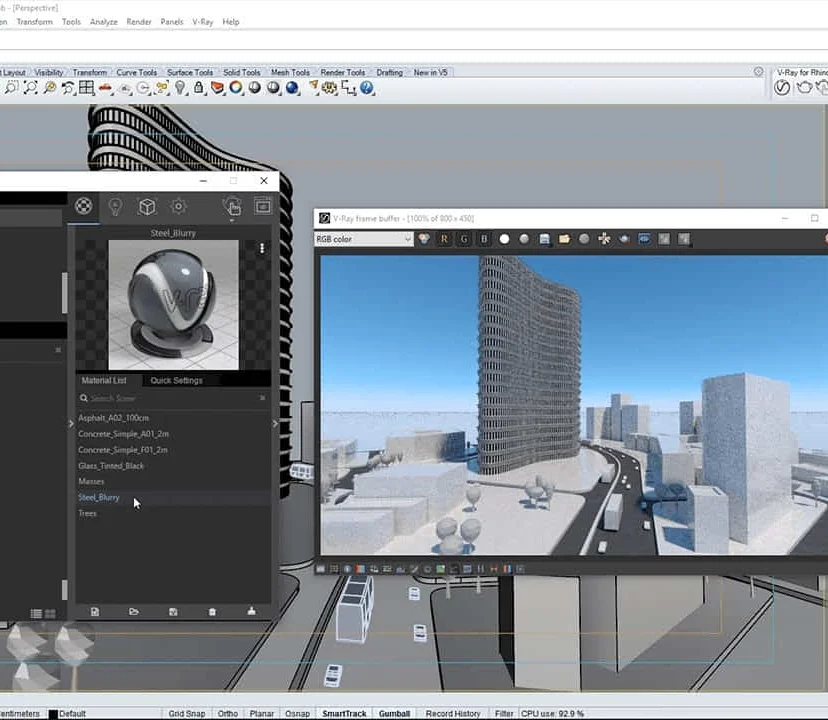
Complete Rhino 3D and V-Ray Training Program: Basic to Intermediate
By ATL Autocad Training London
Why Choose Complete Rhino 3D and V-Ray Training Program: Basic to Intermediate? Learn Rhino 3D and V-Ray for Rhino Basic to Intermediate Training Course. Suitable for beginners and experienced users alike, this program equips you with vital modeling and rendering skills. Opt for in-person or live online sessions. Click here for more info: Website Duration: 16 hours. Approach: 1-on-1 Sessions, Customized Content and Flexible Learning. Scheduling Flexibility: Tailor your sessions from Mon to Sat between 9 am and 7 pm. Course Title: Complete Rhino 3D and V-Ray Training Program: Basic to Intermediate - 16 Hours Session 1-2: Introduction to Rhino 3D Basics (2 hours) Understanding Rhino Interface: Navigating toolbars, command line, and properties panel. Basic Geometric Shapes: Creating lines, circles, and polygons with precision. Editing Tools: Mastering move, rotate, scale, and mirror commands. Session 3-4: Advanced Rhino 3D Modeling Techniques (2 hours) Curves and Surfaces: Delving into NURBS curves, creating complex surfaces, and blending techniques. Modeling Aids: Utilizing grids, snaps, and construction planes for accuracy. Organizing with Layers: Managing complex projects efficiently. Session 5-6: Introduction to V-Ray for Rhino (2 hours) V-Ray Interface: Understanding V-Ray toolbar and settings. Basic Lighting: Exploring different light types and their effects on scenes. Materials: Creating realistic materials, understanding diffuse, reflection, and transparency. Session 7-8: Intermediate V-Ray Concepts (2 hours) Advanced Lighting: Mastering HDRI lighting, creating natural outdoor lighting scenarios. Texture Mapping: Understanding UV mapping, applying textures seamlessly. Rendering Optimization: Reducing noise, optimizing settings for quicker, high-quality renders. Session 9-10: Rhino-V-Ray Integration (2 hours) Model Preparation: Optimizing Rhino models for V-Ray rendering. Advanced Material Manipulation: Creating complex materials, incorporating textures. Interactive Rendering: Real-time adjustments for immediate feedback. Session 11-12: Advanced Modeling Techniques in Rhino (2 hours) Advanced Surface Modeling: Creating organic shapes, advanced surfacing techniques. Precision Modeling: Advanced curve editing, filleting, and trimming. Working with 3D Text: Creating custom 3D text for design projects. Session 13-14: Scene Composition and Presentation (2 hours) Camera Settings: Understanding focal length, depth of field, and perspective. Scene Composition: Design principles, rule of thirds, focal points, and balance. Post-Processing: Enhancing renders in Photoshop, adding atmosphere and context. Session 15-16: Final Project and Portfolio Review (2 hours) Final Project Work: Participants apply learned skills to create a complex 3D scene. Instructor-led Critique: Feedback session for final projects. Portfolio Guidance: Tips for selecting the best works for a professional portfolio. By the end of this 16-hour course, participants will have a deep understanding of both Rhino 3D and V-Ray, allowing them to create intricate 3D models and produce high-quality, realistic renders for various applications. Upon completing the Rhino 3D and V-Ray Basic to Intermediate Training Course, participants can expect to achieve the following learning outcomes: Proficiency in Rhino 3D and V-Ray: Develop a comprehensive understanding of Rhino 3D and V-Ray interfaces, tools, and functionalities, enabling participants to navigate and utilize the software effectively. 3D Modeling Skills: Master the art of creating captivating 3D objects and shapes using Rhino 3D, including editing, transforming, and refining designs for diverse applications. Material Application: Acquire the ability to apply and customize materials and textures to enhance the visual appeal and realism of 3D models, elevating the quality of designs. Lighting Techniques: Gain expertise in utilizing V-Ray lighting tools, such as V-Ray lights and HDRI maps, to achieve striking lighting effects in rendered scenes. Rendering Excellence: Learn to optimize V-Ray render settings, control global illumination, and apply dynamic effects like depth of field and motion blur for high-quality and impressive renders. Advanced Modeling: Develop skills in advanced modeling techniques, including handling curves, surfaces, and solids, enabling participants to tackle complex design challenges. Lighting Mastery: Acquire the knowledge and expertise to create and adjust artificial lights, utilize the Sun and Sky system, and craft custom HDR images for realistic lighting setups. Seamless File Management: Understand various file formats for exporting and importing 3D models, facilitating efficient collaboration and preparation for 3D printing. Creative Problem-Solving: Enhance creative thinking and problem-solving abilities through hands-on practice and exploration of diverse design scenarios. Professional Presentation: Learn post-production techniques in Photoshop to enhance renders and create visually appealing design presentations for effective communication. Continuous Learning: Access valuable resources and tips to encourage continuous learning and professional growth in Rhino 3D and V-Ray. Skills You'll Gain: Master Rhino 3D basics: Curves, surfaces, modeling aids, and precision techniques. Explore intermediate V-Ray concepts: Advanced lighting, material manipulation, and texture mapping. Understand Rhino-V-Ray integration for seamless 3D modeling and rendering workflows. Optimize render settings for high-quality output and reduced rendering times. Career Opportunities: Upon completing this program, you'll be prepared for various roles in the design and visualization industry, such as: 3D Modeler: Create detailed 3D models for diverse industries, including architecture and product design. Architectural Visualizer: Produce realistic architectural visualizations for presentations and marketing materials. Product Designer: Develop visually appealing product prototypes and visualizations for marketing and manufacturing. Visualization Specialist: Work in design studios, advertising agencies, or game development companies, creating immersive visual content. Freelance Designer: Offer your skills on platforms like Upwork or Fiverr, providing 3D modeling and rendering services to clients worldwide. Solidify Rhino 3D Expertise: Master foundational modeling skills, including intricate geometries and surface manipulation, establishing a robust foundation for your 3D design journey. Unlock V-Ray for Rhino: Explore the potential of V-Ray for Rhino, learning to create mesmerizing visualizations and achieve lifelike rendering results that bring vitality to your designs. Enhance Visual Appeal: Grasp advanced lighting techniques, material application, and texture methods to elevate the visual allure of your 3D creations, making them more immersive and authentic. Explore Advanced Concepts: Delve into optimizing rendering settings, post-production tactics, and efficient workflows, advancing your design proficiency to higher levels. Hands-On Experience: Engage in practical exercises and real-world projects, applying your skills in practical contexts to enrich your portfolio and showcase your capabilities effectively. Certification of Achievement: Receive a valuable Certificate of Completion, confirming your expertise in Rhino 3D and V-Ray for Rhino, enhancing your professional credibility as a skilled designer. Flexible Learning Paths: In-Person or Live Online: Opt for in-person sessions, fostering collaborative learning, or choose live online classes for convenience and accessibility, tailoring your learning experience to your preferences. Personalized Guidance: Regardless of your chosen format, benefit from tailored instruction and guidance, ensuring optimal learning outcomes and continuous support throughout the course.