- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
57528 Courses
VMware Telco Cloud Infrastructure: Install, Configure, Manage [V2.0]
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for Telco cloud system administrators and telco network operations engineers Professionals who work with telco or enterprise and data center networks Designers and operations engineers who manage telco workloads Overview By the end of the course, you should be able to meet the following objectives: Describe the VMware Telco Cloud Infrastructure⢠architecture Describe the VMware Cloud Director architecture List the infrastructure requirements of ETSI NFV Describe the VMware Cloud Director architecture as Virtualized Infrastructure Manager (VIM) Describe the options associated with VMware cloud providers Explain how organizations are supported in VMware Cloud Director Describe the security model in VMware Cloud Director Configure key networking elements of VMware Cloud Director Manage and monitor resources in VMware Cloud Director Enumerate troubleshooting concepts and Day 2 operations using VMware Cloud Director This five-day, hands-on training course provides you with the advanced knowledge, skills, and tools to achieve competency in operating and troubleshooting the VMware Telco Cloud Infrastructure environment. In this course, you are introduced to VMware Cloud Director? as a virtualized infrastructure manager. You will examine ETSI NFV requirements, deployment options, and procedures. You will also deploy virtualized network functions and understand their detailed configuration settings. You will learn how to support organizations as well as set up networking and security using hands-on lab exercises.In addition, you are presented with various types of technical problems in VMware Cloud Director, which you will identify, analyze, and solve through a systematic troubleshooting process. Course Introduction Introductions and course logistics Course objectives Day 0 Operations: VMware Telco Cloud Infrastructure Installation Describe the challenges of the telco cloud Describe the key functions of the telco cloud List the benefits of the VMware Cloud Director based VMware Telco Cloud Infrastructure Describe the VMware Telco Cloud Infrastructure architecture Describe the role of VMware Cloud Director in the VMware Telco Cloud Infrastructure architecture List the VMware Telco Cloud Infrastructure deployment options Describe the VMware Cloud Director architecture List the key VMware components that are part of VMware Cloud Director Describe the key use cases for the VMware Cloud Director based VMware Telco Cloud Infrastructure Day 0 Operations: ETSI NFV Requirements for Cloud Platforms Compare physical and virtual infrastructures List the benefits and challenges of physical infrastructure Describe the types of virtual infrastructure Describe the advantages and components of the NFV infrastructure (NFVI) Explain the role of network virtualization in the NFVI List the requirements of NFVI for VMware Cloud Director Describe the networking options of VMware Cloud Director Describe the key networking use cases Describe requirements of VMware Telco Cloud Automation? for networking Describe the storage options of VMware Cloud Director Describe the key storage use cases Day 1 Operations: Virtualized Infrastructure Manager (VIM) Configuration Explain basic concepts related to VMware Cloud Director Describe the components of the VMware Cloud Director architecture Describe the basic configuration of the VMware Cloud Director architecture Describe virtual data centers or VDCs Explain the role of organization VDCs Describe the relationship between provider VDCs and organization VDCs Describe resources in VMware Cloud Director List the key resource organization Create resource pools Describe how vSAN integrates with VMware Cloud Director Day 1 Operations: Configuring VMware Cloud Director Providers Describe how compute resources are provided to VMware Cloud Director Describe how storage resources are provided to VMware Cloud Director Describe provider VDC requirements and best practices List the requirements of creating VDCs Describe the VNF on-boarding process Create provider VDCs Day 1 Operations: Configuring VMware Cloud Director Organizations Describe VMware Cloud Director organizations Create VMware Cloud Director organizations Navigate through the VMware Cloud Director HTML5 provider portal Describe the VMware Cloud Director organization VDC Navigate through the tenant portal List use cases for a VMware Cloud Director organization VDC List the organization VDC allocation models Describe the types of resources that can be allocated Describe how resources are allocated for an organization Examine the function and requirements of network pools Describe the network types available in VMware Cloud Director (external, organization, and vApp) Create and manage organization VDC networks Describe catalogs Manage an organization?s catalog Populate, share, and publish catalogs Describe vApps Manage access to vApps and catalogs Modify the configuration of vApps and their virtual machines (VMs) Manage organization VDC networking Create affinity and anti-affinity rules Day 1 Operations: Configuring VMware Cloud Director Security Describe role-based access Create custom security roles Describe the directory services in VMware Cloud Director Describe the role of LDAP, SAML, SSL, Kerberos, and OAuth2 with VMware Cloud Director Explain the use of VMware Cloud Director with SSO Day 1 Operations: Configuring VMware Cloud Director Networking List networking options in VMware Cloud Director Describe key networking use cases in VMware Cloud Director Describe the use and placement of VMware NSX© Edge? services gateways in relation to VMware Cloud Director Review routing with the distributed logical router and edge services gateways in combination with VMware Cloud Director Describe firewall management in VMware Cloud Director with edge services gateways and the distributed firewall Describe an overview of VMware NSX-T? Data Center Explain the architecture of NSX-T Data Center Describe VMware Cloud Director supported features of NSX-T Data Center Describe the benefits and challenges of multisite networking List the requirements for multisite networking Describe the benefits and challenges of networking between VDCs List the requirements for networking between VDCs Configure cross-VDC networking Day 2 Operations: VMware Cloud Director Resource Management and Monitoring Identify the key resources that need to be managed with VMware Cloud Director List monitoring options with VMware Cloud Director Explain the resource management and monitoring architecture in VMware Cloud Director Monitor objects from the VMware Cloud Director portal Identify features of VMware vRealize© Operations Manager? Integrate VMware Cloud Director with vRealize Operations Manager Configure VMware vRealize© Operations Management Pack for VMware Cloud Director? Outline the monitoring features of vRealize Operations Manager in VMware Cloud Director Describe the purpose of the vRealize Operations Tenant App for VMware Cloud Director Integrate VMware Cloud Director with the Tenant App Configure the Tenant App for VMware Cloud Director Monitor objects with the Tenant App List the steps to monitor VMware Cloud Director environments with vRealize Operations Manager List the steps to monitor VMware Cloud Director environments with VMware vRealize© Log Insight? List the steps to review historical virtual machine metrics in VMware Cloud Director Examine VMware Cloud Director logs Day 2 Operations: VMware Cloud Director Troubleshooting Identify the features of the VMware Telco Cloud Automation dashboards List the components of the VMware Telco Cloud Automation dashboards Explain the features of fault management in VMware Telco Cloud Director Describe the use of fault management in VMware Cloud Director Describe the use of performance management in VMware Cloud Director Describe the use of logs in VMware Cloud Director Troubleshoot using VMware Cloud Director
![VMware Telco Cloud Infrastructure: Install, Configure, Manage [V2.0]](https://cademy-images-io.b-cdn.net/9dd9d42b-e7b9-4598-8d01-a30d0144ae51/4c81f130-71bf-4635-b7c6-375aff235529/original.png?width=3840)
40550 Microsoft Cloud Workshop - Windows Server and SQL Server 2008 EOS planning
By Nexus Human
Duration 1 Days 6 CPD hours This course is intended for This workshop is intended for Cloud Architects and IT professionals who have architectural expertise of infrastructure and solutions design in cloud technologies and want to learn more about Azure and Azure services Overview At the end of this whiteboard design session, you will leave with the information needed to develop a solid migration plan to keep mission-critical apps and data protected as they are transitioned and modernized. Topics covered will include how to get an inventory of a 2008 server environment, how to categorize 2008 workloads and evaluate the best option for each category, migration and upgrade tools available, TCO analysis tools, offers available from Microsoft to leverage existing licenses and innovations of recent product updates, licensing and technologies. This course will look at the process of migrating workloads to Azure. You will leave with the information needed to develop a solid migration plan to keep mission-critical apps and data protected as your customers transition and modernize their application, data, and infrastructure environment. Whiteboard Design Session - Windows Server 2008 and SQL Server 2008 end of support planning Review the customer case study Design a proof of concept solution Present the solution

Certified Data Centre Risk Professional (CDRP)
By Nexus Human
Duration 2 Days 12 CPD hours This course is intended for There is no specific prerequisite for the CDRP© course. However, participants who have at least three years' experience in a data centre and/or IT infrastructures will be best suited. Overview After completion of the course, the participant will be able to: 1. Understand the different standards and methodologies for risk management and assessment 2. Establish the required project team for risk management 3. Perform the risk assessment, identifying current threats, vulnerabilities and the potential impact based on customised threat catalogues 4. Report on the current risk level of the data centre both quantitative and qualitative 5. Anticipate and minimise potential financial impacts 6. Understand the options for handling risk 7. Continuously monitor and review the status of risk present in the data centre 8. Reduce the frequency and magnitude of incidents 9. Detect and respond to events when they occur 10. Meet regulatory and compliance requirements 11. Support certification processes such as ISO/IEC 27001 12. Support overall corporate and IT governance Introduction to Risk Management Risk management concepts Senior management and risk Enterprise Risk Management (ERM) Benefits of risk management Data Centre Risk and Impact Risk in facility, power, cooling, fire suppression, infrastructure and IT services Impact of data centre downtime Main causes of downtime Cost factors in downtime Standards, Guidelines and Methodologies ISO/IEC 27001:2013, ISO/IEC 27005:2011, ISO/IEC 27002:2013 NIST SP 800-30 ISO/IEC 31000:2009 SS507:2008 ANSI/TIA-942 Other methodologies (CRAMM, EBIOS, OCTAVE, etc.) Risk Management Definitions Asset Availability/Confidentiality/Integrity Control Information processing facility Information security Policy Risk Risk analysis/Risk assessment/Risk evaluation/ Risk treatment Threat/Vulnerability Types of risk Risk Assessment Software The need for software Automation Considerations Risk Management Process The risk management process Establishing the context Identification Analysis Evaluation Treatment Communication and consultation Monitoring and review Project Approach Project management principles Project management methods Scope Time Cost Cost estimate methods Context Establishment General considerations Risk evaluation, impact and acceptance criteria Severity rating of impact Occurrence rating of probability Scope and boundaries Scope constraints Roles & responsibilities Training, awareness and competence Risk Assessment - Identification The risk assessment process Identification of assets Identification of threats Identification of existing controls Identification of vulnerabilities Identification of consequences Hands-on exercise: Identification of assets, threats, existing controls, vulnerabilities and consequences Risk Assessment - Analysis and Evaluation Risk estimation Risk estimation methodologies Assessment of consequences Assessment of incident likelihood Level of risk estimation Risk evaluation Hands-on exercise: Assessment of consequences, probability and estimating level of risk Risk Treatment The risk treatment process steps Risk Treatment Plan (RTP) Risk modification Risk retention Risk avoidance Risk sharing Constraints in risk modification Control categories Control examples Cost-benefit analysis Control implementation Residual risk Communication Effective communication of risk management activities Benefits and concerns of communication Risk Monitoring and Review Ongoing monitoring and review Criteria for review Risk scenarios Risk assessment approach Data centre site selection Data centre facility Cloud computing UPS scenarios Force majeure Organisational shortcomings Human failure Technical failure Deliberate acts Exam: Certified Data Centre Risk Professional Actual course outline may vary depending on offering center. Contact your sales representative for more information.

Oracle Database 19c: New Features for Administrators
By Nexus Human
Duration 2 Days 12 CPD hours This course is intended for Oacle Database Administrators System Administrators Developers Overview Understand the concept, benefits, configuration, and usage of the new features and enhancements in database overall area Understand the concept, benefits, configuration, and usage of the new features and enhancements in the security area Understand the concept, benefits, configuration, and usage of the new features and enhancements in the availability area Understand the concept, benefits, configuration, and usage of the new features and enhancements in the performance area Understand the concept, benefits, configuration, and usage of the new features and enhancements in big data and data warehousing area Understand the concept, benefits, configuration, and usage of the new features and enhancements in diagnosability area Understand the concept, benefits, configuration, and usage of the new features and enhancements in sharding area The course provides the Oracle Database 19c new features and enhancements related to database overall, security, availability, performance, data warehousing, and diagnosability. In the lessons, you learn the new and enhanced features of Oracle Database 19c amongst different areas such as database overall, security, availability, performance, big data and warehousing, and diagnosability. Using General Database Overall EnhancementsUsing Security EnhancementsUsing Availability EnhancementsUsing Performance EnhancementsUsing Big Data and Data Warehousing EnhancementsUsing Diagnosability EnhancementsSharding Enhancements

Salesforce Discover Salesforce Fundamentals to Support Your Business (BSX101)
By Nexus Human
Duration 3 Days 18 CPD hours This course is intended for This class is ideal for business users - the people who need to learn what's possible with Salesforce functionality across the suite of products, but aren't necessarily responsible for managing the application. If you're a customer service manager, business executive, business operations manager, sales operations manager, or any other operations, management, or process analysis 'super user,' this class is just what you need to better understand the business value of the Salesforce Platform. Overview Describe the primary business value of each major Salesforce Cloud. Manage users and data. Manage basic org configuration. Create email templates. Create reports and dashboards. Apply and champion Chatter. Understand the Salesforce implementation and maintenance lifecycle. Extend Salesforce functionality beyond basic configuration. Explore what?s possible with Salesforce. In this 3-day class, our Salesforce experts will walk you through the Salesforce Platform, its specific applications, and their business values and benefits. Familiarize yourself with Salesforce Cloud, and learn about platform features and processes to more effectively support day-to-day Salesforce operations within your organization. Through interactive lectures, discussions, and hands-on exercises, you?ll recognize the core elements of the implementation lifecycle, the key considerations to drive user adoption, and the important components of ongoing management of your Salesforce environment. Introduction Understand How Salesforce Works Explore Salesforce Applications Review Salesforce Organization Data Access and Security Control Org Access Manage Who Views and Modifies Objects Unlock Access to Records Share Access to Records Lock Down Individual Fields User Management and Troubleshooting Create New Users Troubleshoot Login, Record Access, and Field Visibility Issues Salesforce Customizations Think About Your Implementation Explore Custom Fields, Picklists, Page Layouts, and Record Types Create Email Templates Business Processes Automation Review Validation Rules Review Assignment and Escalation Rules Review Web-to-Lead and Entitlements Review Lightning Process Builder and Workflow Review Approval Processes and Visual Workflow Reports Explore the Reports Tab, Folders, and Formats Explore the Report Builder Summarize Your Data Dashboards and Data Insights Get More Insight from Your Data Visualize Your Data with Dashboards Create Your Analytics Strategy Everyday Salesforce Collaborate with Chatter, Groups, and Communities Share Feedback with Chatter Answers and Ideas Go Mobile with Salesforce1 Make Salesforce Part of Your Day Data Management Create a Data Migration Strategy Ensure Data Quality Extending Salesforce Drive a Salesforce Implementation Customize Salesforce Using Custom Objects, Apps, and the Salesforce AppExchange Build It Yourself Wrap-up and Certification Review the Certification Process and Resources

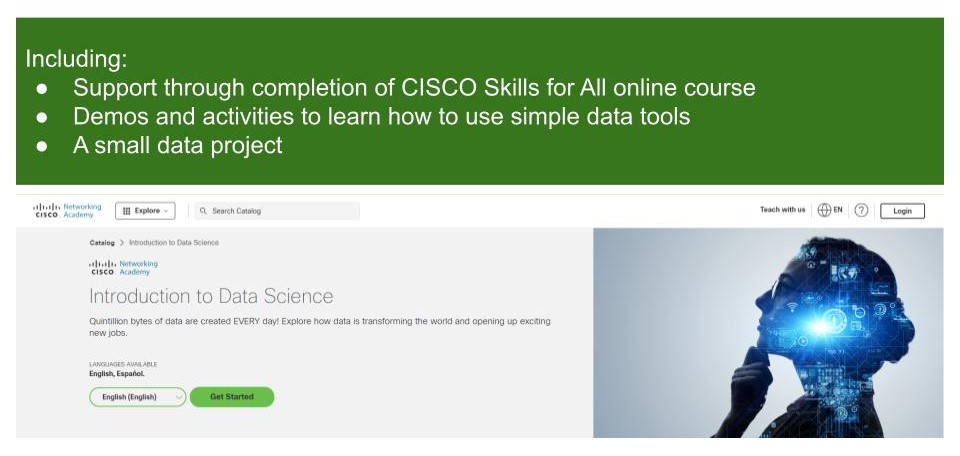
Introduction to Data Science - free for Medway residents
By futureCoders SE
Learn the basics of Data Science, combining a supported #CISCO Skills for All online course with practical learning and a project to help consolidate the learning.
Value Stream Management Foundation (DevOps Institute)
By Nexus Human
Duration 2 Days 12 CPD hours This course is intended for People working in an organization aiming to improve performance, especially in response to digital transformation or disruption. Any roles involved in the creation and delivery of products or services: Leadership and CXO, especially CIO, CTO, CPO, and CVO Transformation and evolution leads and change agents Value stream architects, managers, engineers Scrum Masters, agile and DevOps coaches and facilitators Portfolio, product and project managers, and owners Business analysts Architects, developers, and engineers Release and environment managers IT Ops, service and support desk workers Customer experience and success professionals Overview After completing this course, students will be able to: Describe the origins of value stream management and key concepts such as flow, value, and delivery Describe what value stream management is, why it's needed and the business benefits of its practice Describe how lean, agile, DevOps, and ITSM principles contribute to value stream management Identify and describe value streams, where they start and end, and how they interconnect Identify value stream roles and responsibilities Express value streams visually using mapping techniques, define current and target states and hypothesis backlog Write value stream flow and realization optimization hypotheses and experiments Apply metrics such as touch/processing time, wait/idle time, and cycle time to value streams Understand flow metrics and how to access the data to support data-driven conversations and decisions Examine value realization metrics and aligning to business outcomes, and how to sense and respond to them (outcomes versus outputs) Architect a DevOps toolchain alongside a value stream and data connection points Design a continuous inspection and adaptation approach for organizational evolution The Value Stream Management Foundation course from Value Stream Management Consortium, and offered in partnership with DevOps Institute, is an introductory course taking learners through a value stream management implementation journey. It considers the human, process, and technology aspects of this way of working and explores how optimizing value streams for flow and realization positively impacts organizational performance. History and Evolution of Value Stream Management and its Application Value stream management?s origins Definitions of value stream management Flow Lean and systems thinking and practices Agile, DevOps and other frameworks Research and analysis Identifying Value Streams What is a value stream? Identifying value streams Choosing a value stream Digital value streams Value stream thinking Mapping Value Streams Types of maps Value stream mapping The fuzzy front end Artifacts 10 steps to value stream mapping Mapping and management VSM investment case Limitations of value stream mapping Connecting DevOps Toolchains CICD and the DevOps toolchain Value stream management processes Value stream management platforms DevOps tool categories Building an end-to-end DevOps toolchain Common data model and tools integrations Value Stream Metrics The duality of VSM Downtime in technology Lean, DORA and Flow metrics Definition of Done Value metrics Benefits hypotheses Value streams as profit centers KPIs and OKRs Inspecting the Value Stream 3 Pillars of Empiricism Organizational performance Visibility When to inspect Data and discovery Insights and trends Organizing as Value Streams Value stream alignment Team types and topologies Project to product Hierarchy to autonomy Target Operating Model Value stream people Value stream roles Value stream funding Evolving Value Streams Why now? Transitions VSM capability matrix VSM culture iceberg Learning Making local discoveries global improvements Managing value stream interdependencies

Cisco Securing the Web with Cisco Web Security Applicance v3.0 (SWSA)
By Nexus Human
Duration 2 Days 12 CPD hours This course is intended for Security architects System designers Network administrators Operations engineers Network managers, network or security technicians, and security engineers and managers responsible for web security Cisco integrators and partners Overview After taking this course, you should be able to: Describe Cisco WSA Deploy proxy services Utilize authentication Describe decryption policies to control HTTPS traffic Understand differentiated traffic access policies and identification profiles Enforce acceptable use control settings Defend against malware Describe data security and data loss prevention Perform administration and troubleshooting This course shows you how to implement, use, and maintain Cisco© Web Security Appliance (WSA), powered by Cisco Talos, to provide advanced protection for business email and control against web security threats. Through a combination of expert instruction and hands-on practice, you?ll learn how to deploy proxy services, use authentication, implement policies to control HTTPS traffic and access, implement use control settings and policies, use the solution?s anti-malware features, implement data security and data loss prevention, perform administration of Cisco WSA solution, and more.This course helps you prepare to take the exam, Securing the Web with Cisco Web Security Appliance (300-725 SWSA). Describing Cisco WSA Technology Use Case Cisco WSA Solution Cisco WSA Features Cisco WSA Architecture Proxy Service Integrated Layer 4 Traffic Monitor Data Loss Prevention Cisco Cognitive Intelligence Management Tools Cisco Advanced Web Security Reporting (AWSR) and Third-Party Integration Cisco Content Security Management Appliance (SMA) Deploying Proxy Services Explicit Forward Mode vs. Transparent Mode Transparent Mode Traffic Redirection Web Cache Control Protocol Web Cache Communication Protocol (WCCP) Upstream and Downstream Flow Proxy Bypass Proxy Caching Proxy Auto-Config (PAC) Files FTP Proxy Socket Secure (SOCKS) Proxy Proxy Access Log and HTTP Headers Customizing Error Notifications with End User Notification (EUN) Pages Utilizing Authentication Authentication Protocols Authentication Realms Tracking User Credentials Explicit (Forward) and Transparent Proxy Mode Bypassing Authentication with Problematic Agents Reporting and Authentication Re-Authentication FTP Proxy Authentication Troubleshooting Joining Domains and Test Authentication Integration with Cisco Identity Services Engine (ISE) Creating Decryption Policies to Control HTTPS Traffic Transport Layer Security (TLS)/Secure Sockets Layer (SSL) Inspection Overview Certificate Overview Overview of HTTPS Decryption Policies Activating HTTPS Proxy Function Access Control List (ACL) Tags for HTTPS Inspection Access Log Examples Understanding Differentiated Traffic Access Policies and Identification Profiles Overview of Access Policies Access Policy Groups Overview of Identification Profiles Identification Profiles and Authentication Access Policy and Identification Profiles Processing Order Other Policy Types Access Log Examples ACL Decision Tags and Policy Groups Enforcing Time-Based and Traffic Volume Acceptable Use Policies, and End User Notifications Defending Against Malware Web Reputation Filters Anti-Malware Scanning Scanning Outbound Traffic Anti-Malware and Reputation in Policies File Reputation Filtering and File Analysis Cisco Advanced Malware Protection File Reputation and Analysis Features Integration with Cisco Cognitive Intelligence Enforcing Acceptable Use Control Settings Controlling Web Usage URL Filtering URL Category Solutions Dynamic Content Analysis Engine Web Application Visibility and Control Enforcing Media Bandwidth Limits Software as a Service (SaaS) Access Control Filtering Adult Content Data Security and Data Loss Prevention Data Security Cisco Data Security Solution Data Security Policy Definitions Data Security Logs Performing Administration and Troubleshooting Monitor the Cisco Web Security Appliance Cisco WSA Reports Monitoring System Activity Through Logs System Administration Tasks Troubleshooting Command Line Interface

Oracle Database: Managing Multitenant Architecture
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for Administrator Architect Database Administrator Overview To provide an acceptable response time to users and manage resources effectively, you learn how to monitor performance and manage resources within the multitenant container database and its pluggable databases, and within each pluggable database. Another important aspect is the data movement between non-CDBs and pluggable databases, and between pluggable databases. It is also important to understand the procedures of upgrading an Oracle Database multitenant container database or an Oracle Database pluggable database. Finally, students discover the way multitenant container database and pluggable databases are created and monitored in the Cloud. This course covers all aspects of the multitenant architecture, providing detailed information on the components of an Oracle multitenant container database and its regular and application pluggable databases. You learn why and how to create and manage a multitenant container database and its regular and application pluggable databases, with storage structures appropriate for the business applications. You practice cold and hot cloning, plugging unplugged pluggable databases in multitenant container databases using various methods. CDB BasicsCDB and Regular PDBsApplication PDBs and Application InstallationPDB CreationCDB and PDB ManagementStorageSecurityBackup and DuplicateRecovery and FlashbackPerformance MonitoringResources AllocationData MovementUpgrade methods

From Data to Insights with Google Cloud Platform
By Nexus Human
Duration 3 Days 18 CPD hours This course is intended for Data Analysts, Business Analysts, Business Intelligence professionals Cloud Data Engineers who will be partnering with Data Analysts to build scalable data solutions on Google Cloud Platform Overview This course teaches students the following skills: Derive insights from data using the analysis and visualization tools on Google Cloud Platform Interactively query datasets using Google BigQuery Load, clean, and transform data at scale Visualize data using Google Data Studio and other third-party platforms Distinguish between exploratory and explanatory analytics and when to use each approach Explore new datasets and uncover hidden insights quickly and effectively Optimizing data models and queries for price and performance Want to know how to query and process petabytes of data in seconds? Curious about data analysis that scales automatically as your data grows? Welcome to the Data Insights course! This four-course accelerated online specialization teaches course participants how to derive insights through data analysis and visualization using the Google Cloud Platform. The courses feature interactive scenarios and hands-on labs where participants explore, mine, load, visualize, and extract insights from diverse Google BigQuery datasets. The courses also cover data loading, querying, schema modeling, optimizing performance, query pricing, and data visualization. This specialization is intended for the following participants: Data Analysts, Business Analysts, Business Intelligence professionals Cloud Data Engineers who will be partnering with Data Analysts to build scalable data solutions on Google Cloud Platform To get the most out of this specialization, we recommend participants have some proficiency with ANSI SQL. Introduction to Data on the Google Cloud Platform Highlight Analytics Challenges Faced by Data Analysts Compare Big Data On-Premises vs on the Cloud Learn from Real-World Use Cases of Companies Transformed through Analytics on the Cloud Navigate Google Cloud Platform Project Basics Lab: Getting started with Google Cloud Platform Big Data Tools Overview Walkthrough Data Analyst Tasks, Challenges, and Introduce Google Cloud Platform Data Tools Demo: Analyze 10 Billion Records with Google BigQuery Explore 9 Fundamental Google BigQuery Features Compare GCP Tools for Analysts, Data Scientists, and Data Engineers Lab: Exploring Datasets with Google BigQuery Exploring your Data with SQL Compare Common Data Exploration Techniques Learn How to Code High Quality Standard SQL Explore Google BigQuery Public Datasets Visualization Preview: Google Data Studio Lab: Troubleshoot Common SQL Errors Google BigQuery Pricing Walkthrough of a BigQuery Job Calculate BigQuery Pricing: Storage, Querying, and Streaming Costs Optimize Queries for Cost Lab: Calculate Google BigQuery Pricing Cleaning and Transforming your Data Examine the 5 Principles of Dataset Integrity Characterize Dataset Shape and Skew Clean and Transform Data using SQL Clean and Transform Data using a new UI: Introducing Cloud Dataprep Lab: Explore and Shape Data with Cloud Dataprep Storing and Exporting Data Compare Permanent vs Temporary Tables Save and Export Query Results Performance Preview: Query Cache Lab: Creating new Permanent Tables Ingesting New Datasets into Google BigQuery Query from External Data Sources Avoid Data Ingesting Pitfalls Ingest New Data into Permanent Tables Discuss Streaming Inserts Lab: Ingesting and Querying New Datasets Data Visualization Overview of Data Visualization Principles Exploratory vs Explanatory Analysis Approaches Demo: Google Data Studio UI Connect Google Data Studio to Google BigQuery Lab: Exploring a Dataset in Google Data Studio Joining and Merging Datasets Merge Historical Data Tables with UNION Introduce Table Wildcards for Easy Merges Review Data Schemas: Linking Data Across Multiple Tables Walkthrough JOIN Examples and Pitfalls Lab: Join and Union Data from Multiple Tables Advanced Functions and Clauses Review SQL Case Statements Introduce Analytical Window Functions Safeguard Data with One-Way Field Encryption Discuss Effective Sub-query and CTE design Compare SQL and Javascript UDFs Lab: Deriving Insights with Advanced SQL Functions Schema Design and Nested Data Structures Compare Google BigQuery vs Traditional RDBMS Data Architecture Normalization vs Denormalization: Performance Tradeoffs Schema Review: The Good, The Bad, and The Ugly Arrays and Nested Data in Google BigQuery Lab: Querying Nested and Repeated Data More Visualization with Google Data Studio Create Case Statements and Calculated Fields Avoid Performance Pitfalls with Cache considerations Share Dashboards and Discuss Data Access considerations Optimizing for Performance Avoid Google BigQuery Performance Pitfalls Prevent Hotspots in your Data Diagnose Performance Issues with the Query Explanation map Lab: Optimizing and Troubleshooting Query Performance Advanced Insights Introducing Cloud Datalab Cloud Datalab Notebooks and Cells Benefits of Cloud Datalab Data Access Compare IAM and BigQuery Dataset Roles Avoid Access Pitfalls Review Members, Roles, Organizations, Account Administration, and Service Accounts

Search By Location
- course, Courses in London
- course, Courses in Birmingham
- course, Courses in Glasgow
- course, Courses in Liverpool
- course, Courses in Bristol
- course, Courses in Manchester
- course, Courses in Sheffield
- course, Courses in Leeds
- course, Courses in Edinburgh
- course, Courses in Leicester
- course, Courses in Coventry
- course, Courses in Bradford
- course, Courses in Cardiff
- course, Courses in Belfast
- course, Courses in Nottingham