- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
41962 Courses
Just Enough Scala
By Nexus Human
Duration 1 Days 6 CPD hours This course is intended for Developers Overview The basics of and motivation for using the functional programming paradigmFeatures of the Scala languageWorking with variables in ScalaUsing Scala collectionsControlling code flow in ScalaImporting and using Scala code libraries Scala training course will teach students the key language concepts and programming techniques, essential for students to focus on the covered subjects without having to also learn a complex programming language at the same time. Scala Basics Scala Background Information Key Scala Concepts Programming in Scala Variables Scala Variables Numerical Boolean String Collections Tuples The Collections Hierarchy Sets Lists Arrays Maps Common Conversions Flow Control Looping Iterators Functions Passing Functions Collection Iteration Methods Pattern Matching Libraries Classes and Objects Packages Import Additional course details: Nexus Humans Just Enough Scala training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Just Enough Scala course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Cisco Implementing Secure Solutions with Virtual Private Networks v1.0 (SVPN)
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for This course is designed for professionals in the following job roles: Network security engineer CCNP Security candidate Channel Partner Overview After taking this course, you should be able to: Introduce site-to-site VPN options available on Cisco router and firewalls Introduce remote access VPN options available on Cisco router and firewalls Review site-to-site and remote access VPN design options Review troubleshooting processes for various VPN options available on Cisco router and firewalls The Implementing Secure Solutions with Virtual Private Networks (SVPN) v1.0 course teaches you how to implement, configure, monitor, and support enterprise Virtual Private Network (VPN) solutions. Through a combination of lessons and hands-on experiences you will acquire the knowledge and skills to deploy and troubleshoot traditional Internet Protocol Security (IPsec), Dynamic Multipoint Virtual Private Network (DMVPN), FlexVPN, and remote access VPN to create secure and encrypted data, remote accessibility, and increased privacy. Course Outline Introducing VPN Technology Fundamentals Implementing Site-to-Site VPN Solutions Implementing Cisco Internetwork Operating System (Cisco IOS©) Site-to-Site FlexVPN Solutions Implement Cisco IOS Group Encrypted Transport (GET) VPN Solutions Implementing Cisco AnyConnect VPNs Implementing Clientless VPNs Lab Outline Explore IPsec Technologies Implement and Verify Cisco IOS Point-to-Point VPN Implement and Verify Cisco Adaptive Security Appliance (ASA) Point-to-Point VPN Implement and Verify Cisco IOS Virtual Tunnel Interface (VTI) VPN Implement and Verify Dynamic Multipoint VPN (DMVPN) Troubleshoot DMVPN Implement and Verify FlexVPN with Smart Defaults Implement and Verify Point-to-Point FlexVPN Implement and Verify Hub and Spoke FlexVPN Implement and Verify Spoke-to-Spoke FlexVPN Troubleshoot Cisco IOS FlexVPN Implement and Verify AnyConnect Transport Layer Security (TLS) VPN on ASA Implement and Verify Advanced Authentication, Authorization, and Accounting (AAA) on Cisco AnyConnect VPN Implement and Verify Clientless VPN on ASA

AS28 IBM BRMS for IBM i
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for This is an intermediate course for POWER i administrators, IBM Business Partners, and anyone else who would like practical knowledge of the features and functions supported by BRMS. Overview Describe the major features and functions of BRMS List the steps to install BRMS on a single system or in a BRMS Network environment Implement a previously defined backup and recovery strategy using BRMS Implement a previously defined archival and retrieval plan, including dynamic retrieval, using BRMS Explain how to utilize a tape drive, tape library system, virtual tape, and optical drive with BRMS Implement and use BRMS using the green screen, System i Navigator, and IBM Navigator for i This course covers the features & functions supported by Backup Recovery & Media Services (BRMS). Learn how to perform the supported functions when using a 5250 emulation session, when using System i Navigator, & when using IBM Navigator for i. Overview of BRMS . Installing BRMS . BRMS policies overview . Media devices and encryption using software and hardware . Overview and implementation of virtual tape, DVD, and optical device support . Creating a simple backup control group . BRMS log . Saving IFS data . Working with backup lists . Parallel save, user exits, and save-while-active . Performing a backup and full system backup . Other backup topics i . Storage locations . Containers . Move management . Media class . Media policies . Media topics . BRMS networking . Scheduling BRMS jobs . Daily maintenance . BRMS reports . Recovery . Tape duplication and label print . Functional usage . Archive . Retrievaltion . TSM Client and BRMS on IBM i . BRMS Enterprise . Summary .

Advanced TP-CT - Implementing and Configuring Cisco TelePresence Video Suite
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for The primary audience for this course is as follows: Network Video Engineer Voice/UC/Collaboration/Communications Engineer Collaboration Tools Engineer Collaboration Sales/Systems Engineer Overview Implement and Configure Cisco Endpoints Implement and Configure Cisco Unified Communications Manager for Video Endpoints Implement and Configure Cisco IMP for Jabber Implement and Configure Cisco Expressway Implement and Configure Cisco Video Communications Server (VCS) Control Implement and Configure Cisco Video Communications Server (VCS) Expressway Implement and Configure connectivity between a Cisco VCS and Cisco UCM Implement and Configure a Cisco Conductor Implement, Configure, and Operate Cisco TelePresence Management Suite (TMS) and provision devices using Cisco TMS Provisioning Extension (TMSPE) Implement and Configure Cisco Meeting Server This one of kind Cisco Collaboration in-depth course takes student from initial endpoint configuration to a full solution deployment using all of the Cisco Collaboration Components. Students will have extensive labs in which they will configure and troubleshoot a full Cisco Telepresence Deployment. Participants will gain in-depth practical knowledge with exercises on installing, configuring, maintaining and troubleshooting of all Cisco Telepresence Components.The software applications that are covered in this course include:Cisco Unified Communications Manager (CUCM)Cisco Unified Communications Manager IM and PresenceCisco ExpresswayCisco Video Communication Server (VCS)Cisco ConductorCisco Telepresence Server (TS)Cisco Meeting Server (CMS)Cisco Telepresence Management Suite (TMS)Cisco TMS Extensions Understanding Cisco TelePresence Endpoints Cisco TelePresence Endpoint Solutions Overview Cisco DX Series Endpoint Characteristics Cisco TelePresence TC Software-Based Endpoint Characteristics Cisco TelePresence EX60 and EX90 Cisco TelePresence MX Series Cisco TelePresence SX Series Endpoints Cisco TelePresence Room Kits Cisco Intelligent Proximity Cisco TelePresence TC Software-Based Endpoint Peripherals Cisco TelePresence TC Software-Based Endpoint Deployments Cisco TelePresence Integrator C Series-Based Endpoints Cisco Jabber Video for TelePresence Characteristics Cisco Jabber Understanding the Cisco Video Network Network Overview H323 Overview SIP Overview VCS vs Unified Communications Manager Internetworking QOS Overview Implementing and Configuring Unified Communication Manager Unified Communications Manager Initial Settings Service Activation Enterprise and Service Parameters SIP Domains Configure IMP for Jabber Configure Jabber Settings Registering Endpoints Verifying Network Registration Cisco VCS / Expressway Overview and Configuration Configuring Initial VCS Setting Configuring Authentication Registration Conflict Policy Registration Restriction Policy Local Zone Components Membership Rules Transforms Purpose of Zones Search Priority Neighbor Zones Creating Neighbor Zones Need for Traversal Zones H.460 and Assent Protocols Traversal Zone Configuration Domain Name System Dialing E.164 Number Mapping Bandwidth Management Pipes Subzones and Zones Subzone Call Failure Call Processing Order Certificates Certificate Installation Clustering and the Cisco VCS Clustering Configuration Collecting Information Log Files Search History Connecting VCS-C to CUCM Connect VCS-C to VCS-E Connecting CUCM to VCS-C Understanding the Cisco TelePresence Conductor What is Conductor? Conductor ? How it works Installing Cisco Conductor Configuring Conductor Network Settings Configuring Conductor for a CUCM Configuration MCU Configuration Telepresence Server Telepresence Conductor Server Configuration Configuring TelePresence Conductor for ad hoc conferences Configuring TelePresence Conductor for rendezvous conferences Configuring Unified CM Configuring general settings on Unified CM Locations in Unified CM Unified CM trusts TelePresence Conductor's server certificate SIP trunk security profile Configuring Unified CM for rendezvous conferences Sip Trunk Configuration Conference Bridge Configuration MRG and MRGL Configuration Unified CM normalization scripts Configuring Unified CM for ad hoc conferences Sip Trunk Configuration Route pattern to match the SIP Trunk Configuration Unified CM normalization scripts Configuring the Cisco VCS with TelePresence Conductor Designing a Dial Plan MCU Configuration Telepresence Server Configuring the Cisco VCS Telepresence Conductor Server Configuration Backing Up Conductor Troubleshooting Conductor Overview of Cisco Telepresence Management Server (TMS) Windows Server Installation SQL Server Installation Server Pre-requisites and configuration Installing TMS Installing TMS Provisioning Extensions Initial Configuration Endpoint Configuration Adding Systems to TMS Configuration Templates Setting Configuration VCS Configuration for TMS Direct Endpoint Management VCS/TMS CUCM Configuration for TMS Direct Endpoint Management?CUCM Phonebooks & Phonebook Sources Conference Creation Advanced Conference Settings Booking & Scheduling Participant Types Methods Conference Monitoring Dial Plans, Configuration Templates Scheduler/Smart Scheduler Managing and Troubleshooting Cisco TMS Using the Logs Cisco TMS Ticketing System Troubleshooting VCS Registrations Troubleshooting CUCM Registrations System Maintenance Configuring Cisco Meeting Server (formerly Acano) Setting up CMS Installing Certificates Configuring CUCM with CMS Provision the RTC Client Configuring Meeting Spaces Additional course details: Nexus Humans Advanced TP-CT - Implementing and Configuring Cisco TelePresence Video Suite training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Advanced TP-CT - Implementing and Configuring Cisco TelePresence Video Suite course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Cisco Implementing and Configuring Cisco Identity Services Engine v3.0 (SISE)
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for Network security engineers ISE administrators Wireless network security engineers Cisco integrators and partners Overview After taking this course, you should be able to: Describe Cisco ISE deployments, including core deployment components and how they interact to create a cohesive security architecture. Describe the advantages of such a deployment and how each Cisco ISE capability contributes to these advantages. Describe concepts and configure components related to 802.1X and MAC Authentication Bypass (MAB) authentication, identity management, and certificate services. Describe how Cisco ISE policy sets are used to implement authentication and authorization, and how to leverage this capability to meet the needs of your organization. Describe third-party Network Access Devices (NADs), Cisco TrustSec, and Easy Connect. Describe and configure web authentication, processes, operation, and guest services, including guest access components and various guest access scenarios. Describe and configure Cisco ISE profiling services, and understand how to monitor these services to enhance your situational awareness about network-connected endpoints. Describe best practices for deploying this profiler service in your specific environment. Describe BYOD challenges, solutions, processes, and portals. Configure a BYOD solution, and describe the relationship between BYOD processes and their related configuration components. Describe and configure various certificates related to a BYOD solution. Describe the value of the My Devices portal and how to configure this portal. Describe endpoint compliance, compliance components, posture agents, posture deployment and licensing, and the posture service in Cisco ISE. Describe and configure TACACS+ device administration using Cisco ISE, including command sets, profiles, and policy sets. Understand the role of TACACS+ within the Authentication, Authentication, and Accounting (AAA) framework and the differences between the RADIUS and TACACS+ protocols. Migrate TACACS+ functionality from Cisco Secure Access Control System (ACS) to Cisco ISE, using a migration tool. The Implementing and Configuring Cisco Identity Services Engine (SISE) v3.0 course shows you how to deploy and use Cisco© Identity Services Engine (ISE) v2.4, an identity and access control policy platform that simplifies the delivery of consistent, highly secure access control across wired, wireless, and VPN connections. This hands-on course provides you with the knowledge and skills to implement and use Cisco ISE, including policy enforcement, profiling services, web authentication and guest access services, BYOD, endpoint compliance services, and TACACS+ device administration. Through expert instruction and hands-on practice, you will learn how to use Cisco ISE to gain visibility into what is happening in your network, streamline security policy management, and contribute to operational efficiency. This course helps you prepare to take the exam, Implementing and Configuring Cisco Identity Services Engine (300-715 SISE), which leads to CCNP© Security and the Cisco Certified Specialist - Security Identity Management Implementation certifications. Introducing Cisco ISE Architecture and Deployment Using Cisco ISE as a Network Access Policy Engine Cisco ISE Use Cases Describing Cisco ISE Functions Cisco ISE Deployment Models Context Visibility Cisco ISE Policy Enforcement Using 802.1X for Wired and Wireless Access Using MAC Authentication Bypass for Wired and Wireless Access Introducing Identity Management Configuring Certificate Services Introducing Cisco ISE Policy Implementing Third-Party Network Access Device Support Introducing Cisco TrustSec Cisco TrustSec Configuration Easy Connect Web Authentication and Guest Services Introducing Web Access with Cisco ISE Introducing Guest Access Components Configuring Guest Access Settings Configuring Sponsor and Guest Portals Cisco ISE Profiler Introducing Cisco ISE Profiler Profiling Deployment and Best Practices Cisco ISE BYOD Introducing the Cisco ISE BYOD Process Describing BYOD Flow Configuring the My Devices Portal Configuring Certificates in BYOD Scenarios Cisco ISE Endpoint Compliance Services Introducing Endpoint Compliance Services Configuring Client Posture Services and Provisioning in Cisco ISE Working with Network Access Devices Review TACACS+ Cisco ISE TACACS+ Device Administration Configure TACACS+ Device Administration TACACS+ Device Administration Guidelines and Best Practices Migrating from Cisco ACS to Cisco ISE Lab outline Access the SISE Lab and Install ISE 2.4 Configure Initial Cisco ISE Setup, GUI Familiarization, and System Certificate Usage Integrate Cisco ISE with Active Directory Configure Basic Policy on Cisco ISE Configure Policy Sets Configure Access Policy for Easy Connect Configure Guest Access Configure Guest Access Operations Create Guest Reports Configure Profiling Customize the Cisco ISE Profiling Configuration Create Cisco ISE Profiling Reports Configure BYOD Blacklisting a Device Configure Cisco ISE Compliance Services Configure Client Provisioning Configure Posture Policies Test and Monitor Compliance-Based Access Test Compliance Policy Configure Cisco ISE for Basic Device Administration Configure TACACS+ Command Authorization Additional course details: Nexus Humans Cisco Implementing and Configuring Cisco Identity Services Engine v3.0 (SISE) training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Cisco Implementing and Configuring Cisco Identity Services Engine v3.0 (SISE) course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Systems Operations on AWS
By Nexus Human
Duration 3 Days 18 CPD hours This course is intended for This course is intended for: System administrators and operators who are operating in the AWS Cloud Informational technology workers who want to increase the system operations knowledge. Overview In this course, you will learn to: Recognize the AWS services that support the different phases of Operational Excellence, a WellArchitected Framework pillar. Manage access to AWS resources using AWS Accounts and Organizations and AWS Identity and Access Management (IAM). Maintain an inventory of in-use AWS resources using AWS services such as AWS Systems Manager, AWS CloudTrail, and AWS Config. Develop a resource deployment strategy utilizing metadata tags, Amazon Machine Images, and Control tower to deploy and maintain an AWS cloud environment. Automate resource deployment using AWS services such as AWS CloudFormation and AWS Service Catalog. Use AWS services to manage AWS resources through SysOps lifecycle processes such as deployments and patches. Configure a highly available cloud environment that leverages AWS services such as Amazon Route 53 and Elastic Load Balancing to route traffic for optimal latency and performance. Configure AWS Auto Scaling and Amazon Elastic Compute Cloud auto scaling to scale your cloud environment based on demand. Use Amazon CloudWatch and associated features such as alarms, dashboards, and widgets to monitor your cloud environment. Manage permissions and track activity in your cloud environment using AWS services such as AWS CloudTrail and AWS Config. Deploy your resources to an Amazon Virtual Private Cloud (Amazon VPC), establish necessary connectivity to your Amazon VPC, and protect your resources from disruptions of service. State the purpose, benefits, and appropriate use cases for mountable storage in your AWS cloud environment. Explain the operational characteristics of object storage in the AWS cloud, including Amazon Simple Storage Service (Amazon S3) and Amazon S3 Glacier. Build a comprehensive costing model to help gather, optimize, and predict your cloud costs using services such as AWS Cost Explorer and the AWS Cost & Usage Report. This course teaches systems operators and anyone performing system operations functions how to install, configure, automate, monitor, secure, maintain and troubleshoot the services, networks, and systems on AWS necessary to support business applications. The course also covers specific AWS features, tools, andbest practices related to these functions. Module 1: Introduction to System Operations on AWS Systems operations AWS Well-Architected Framework AWS Well-Architected Tool Module 2a: Access Management Access management Resources, accounts, and AWS Organizations Module 2b: System Discovery Methods to interact with AWS services Introduction to monitoring services Tools for automating resource discovery Inventory with AWS Systems Manager and AWS Config Troubleshooting scenario Hands-On Lab: Auditing AWS Resources with AWS Systems Manager and AWS Config Module 3: Deploying and Updating Resources Systems operations in deployments Tagging strategies Deployment using Amazon Machine Images (AMIs) Deployment using AWS Control Tower Troubleshooting scenario Module 4: Automating Resource Deployment Deployment using AWS CloudFormation Deployment using AWS Service Catalog Troubleshooting scenario Hands-On Lab: Infrastructure as Code Module 5: Manage Resources AWS Systems Manager Troubleshooting scenario Hands-On Lab: Operations as Code Module 6a: Configure Highly Available Systems Distributing traffic with Elastic Load Balancing Amazon Route 53 Module 6b: Automate Scaling Scaling with AWS Auto Scaling Scaling with Spot Instances Managing licenses with AWS License Manager Troubleshooting scenario Module 7: Monitor and Maintaining System Health Monitoring and maintaining healthy workloads Monitoring distributed applications Monitoring AWS infrastructure Monitoring your AWS account Troubleshooting scenario Hands-On Lab: Monitoring Applications and Infrastructure Module 8: Data Security and System Auditing Maintain a strong identity and access foundation Implement detection mechanisms Automate incident remediation Troubleshooting scenario Hands-On Lab: Securing the Environment Module 9: Operate Secure and Resilient Networks Building a secure Amazon Virtual Private Cloud (Amazon VPC) Networking beyond the VPC Troubleshooting scenario Module 10a : Mountable Storage Configuring Amazon Elastic Block Storage (Amazon EBS) Sizing Amazon EBS volumes for performance Using Amazon EBS snapshots Using Amazon Data Lifecycle Manager to manage your AWS resources Creating backup and data recovery plans Configuring shared file system storage Module 10b: Object Storage Deploying Amazon Simple Storage Service (Amazon S3) with Access Logs, Cross-Region Replication, and S3 Intelligent-Tiering Hands-On Lab: Automating with AWS Backup for Archiving and Recovery Module 11: Cost Reporting, Alerts, and Optimization Gain AWS expenditure awareness Use control mechanisms for cost management Optimize your AWS spend and usage Hands-On Lab: Capstone lab for SysOps Additional course details: Nexus Humans Systems Operations on AWS training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Systems Operations on AWS course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

VMware NSX for Intrinsic Security [V4.x]
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for Experienced security administrators Overview By the end of the course, you should be able to meet the following objectives: Define the concepts related to information security Explain the different types of firewalls and their use cases Describe the operation of intrusion detection and intrusion prevention systems Differentiate between Malware Prevention approaches Describe the VMware intrinsic security portfolio Use NSX segmentation to implement Zero-Trust Security Configure user and role management Configure and troubleshoot Distributed Firewall, Identity Firewall, and time-based policies Configure and troubleshoot Gateway Security Use VMware Aria Operations⢠for Logs and VMware Aria Operations⢠for Networks to operate NSX firewalls Explain the security best practices related to grouping, tagging, and rule configuration Describe north-south and east-west service insertion Describe endpoint protection Configure and troubleshoot IDS/IPS Deploy NSX Application Platform Configure and troubleshoot NSX Malware Prevention Describe the capabilities of NSX Intelligence and NSX NDR This five-day, hands-on training course provides you with the knowledge, skills, and tools to achieve competency in configuring, operating, and troubleshooting VMware NSX© for intrinsic security. This course introduces all the security features in NSX, including Distributed Firewall and Gateway Firewall, Intrusion Detection and Prevention (IDS/IPS), NSX Application Platform, NSX Malware Prevention, VMware NSX© Intelligence?, and VMware NSX© NDR?. In addition, this course presents common configuration issues and gives a methodology to resolve them. Course Introduction Introduction and course logistics Course objectives Security Basics Define the concepts related to information security Explain the different types of firewalls and their use cases Describe the operation of IDS/IPS Differentiate between Malware Prevention approaches VMware Intrinsic Security Define the VMware intrinsic security strategy Describe the VMware intrinsic security portfolio Explain how NSX aligns with the intrinsic security strategy Implementing Zero-Trust Security Define Zero-Trust Security Describe the five pillars of a Zero-Trust architecture Define NSX segmentation and its use cases Describe the steps needed to enforce Zero-Trust with NSX segmentation User and Role Management Integrate NSX and VMware Identity Manager? Integrate NSX and LDAP Describe the native users and roles in NSX Create and assign custom user roles Explain object-based RBAC in a multitenancy environment Distributed Firewall Configure Distributed Firewall rules and policies Describe the NSX Distributed Firewall architecture Troubleshoot common problems related to NSX Distributed Firewall Configure time-based policies Configure Identity Firewall rules Configure the distributed firewall to block malicious IPs Gateway Security Configure Gateway Firewall rules and policies Describe the architecture of the Gateway Firewall Identify and troubleshoot common Gateway Firewall issues Configure TLS Inspection to decrypt traffic for both internal and external services Configure URL filtering and identify common configuration issues Operating Internal Firewalls Use VMware Aria Operations for Logs and VMware Aria Operations for Networks to operate NSX firewalls Explain security best practices related to grouping, tagging, and rule configuration Network Introspection Explain network introspection Describe the architecture and workflows of north-south and east-west service insertion Troubleshoot north-south and east-west service insertion Endpoint Protection Explain endpoint protection Describe the architecture and workflows of endpoint protection Troubleshoot endpoint protection Intrusion Detection and Prevention Describe the MITRE ATT&CK framework Explain the different phases of a cyber attack Describe how NSX security solutions can be used to protect against cyber attacks Configure and troubleshoot Distributed IDS/IPS Configure and troubleshoot North-South IDS/IPS NSX Application Platform Describe NSX Application Platform and its use cases Identify the topologies supported for the deployment of NSX Application Platform Deploy NSX Application Platform Explain the NSX Application Platform architecture and services Validate the NSX Application Platform deployment and troubleshoot common issues NSX Malware Prevention Identify use cases for NSX Malware Prevention Identify the components in the NSX Malware Prevention architecture Describe the NSX Malware Prevention packet flows for known and unknown files Configure NSX Malware Prevention for east-west and north-south traffic NSX Intelligence and NSX NDR Describe NSX Intelligence and its use cases Explain NSX Intelligence visualization, recommendation, and network traffic analysis capabilities Describe NSX NDR and its use cases Explain the architecture of NSX NDR in NSX Describe the visualization capabilities of NSX NDR Additional course details:Notes Delivery by TDSynex, Exit Certified and New Horizons an VMware Authorised Training Centre (VATC) Nexus Humans VMware NSX for Intrinsic Security [V4.x] training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the VMware NSX for Intrinsic Security [V4.x] course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.
![VMware NSX for Intrinsic Security [V4.x]](https://cademy-images-io.b-cdn.net/9dd9d42b-e7b9-4598-8d01-a30d0144ae51/4c81f130-71bf-4635-b7c6-375aff235529/original.png?width=3840)
VMware Telco Cloud: Day 2 Operate and Scale [V2.x]
By Nexus Human
Duration 5 Days 30 CPD hours Overview By the end of the course, you should be able to meet the following objectives: List the operational challenges for rolling out and operating telco services including 5G. Identify the role of VMware Telco Cloud products in supporting telco services. Discuss the role of VMware technologies such as vSphere, NSX, and Tanzu etc. in implementing telco services. Outline the role of native tools and other VMware monitoring tools such as vRealize Operations and vRealize Log Insight in maintaining network services. Choose the VMware Telco Cloud products that meet your application requirements. Deploy a solution architecture that meet VMware best practices for delivering services using VMware Telco Cloud products. Implement and maintain VMware Telco Cloud products in a secure manner. Identify the tools and remediation pathways for maintaining the availability and performance of your applications and infrastructure using VMware Telco Cloud and vRealize Suite products. Follow specific steps to resolve application performance and availability problems Scale your VMware Telco Cloud products to meet operational requirements in line with VMware best practices. Optimize the operation of VMware Telco Cloud products to ensure SLAs are met. This five-day, hands-on training course provides the knowledge to operate and scale VMware Telco Cloud version 2.x products in a Telco cloud provider environment. In this course, you are exposed to the entire VMware Telco Cloud portfolio, and the tools and methodologies available to ensure they operate effectively. In addition, you are presented with various scenarios where you will be guided through the process of identifying, analyzing, and formulating solutions to performance and other problems. Course Introduction Introductions and course logistics Course objectives Overview of Network Transformation Reviews the technologies that enable modern networks Lists the components of modern service provider networks Outlines characteristics of modern service provider networks in meeting customer application needs Service Delivery with VMware Telco Cloud Outlines the components of the VMware Telco Cloud portfolio Reviews the role each VMware Telco Cloud product plays in delivering telco services Specifies the dependencies each product has on underlying technologies Supporting VMware Telco Cloud Service Delivery Reviews the products that implements the virtualization, management, platform, and orchestration layers Outlines the role played by other VMware products such as NSX in delivering cloud services Outline opensource integration options with VMware Telco Cloud products Securing VMware Telco Cloud Reviews security threats that affect telco services Identifies the critical telco assets that are prone to attack Outlines best practice for securing VMware Telco Cloud products and underlying technology Provides overview of appropriate security controls for VMware Telco Cloud products Assessing Service Provision Reviews tools and methodologies used to gather requirements Outlines how to assess cloud-native capabilities Documenting findings Identifying security vulnerabilities with Helm. Reviews VMware?s Customer Engagement process Capturing infrastructure requirements from TCA Designing a VMware Telco Cloud Solution Selecting appropriate deployment topology Pros and cons of design choices How a design choice might be affected by other factors such as NSX and TKG deployment, or data center architecture Outlines typical scenarios where specific products align with identified requirements Documenting a design Designing for availability Ensuring a design aligns with best practice Specifying monitoring options Implementing VMware Telco Cloud Products Review deployment options for VMware products Integrating new products with existing ones Outline post-installation tasks Adding the new products as data sources in monitoring tools such as vRealize Operations and vRealize Operations Network Insight Ensuring products meet security requirements Configuring monitoring software Outlines the xNF onboarding process in TCA Maintaining Telco Services Outlines typical administrative tasks in ensuring services are maintained Use of native and other VMware performance monitoring tools Reviewing performance data Role of SLAs in service maintenance Reviews scenarios where known behaviors indicate problems Troubleshooting Deployed Telco Services Reviews the troubleshooting tools available Using tools to gather useful data Outlines how event correlation can be used to isolate problems Using a methodology to determine the root cause of a problem Steps to identify and resolve a problem Reviews scenarios where known problems are isolated and resolution steps identified Scaling VMware Telco Cloud Products Assessing if operations are impacted by lack of resources now or will be in the future Reviews performance optimization options Identifies implications for other products if you scale VMware Telco Cloud products Reviews VMware sizing guidelines Additional course details:Notes Delivery by TDSynex, Exit Certified and New Horizons an VMware Authorised Training Centre (VATC) Nexus Humans VMware Telco Cloud: Day 2 Operate and Scale [V2.x] training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the VMware Telco Cloud: Day 2 Operate and Scale [V2.x] course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.
![VMware Telco Cloud: Day 2 Operate and Scale [V2.x]](https://cademy-images-io.b-cdn.net/9dd9d42b-e7b9-4598-8d01-a30d0144ae51/4c81f130-71bf-4635-b7c6-375aff235529/original.png?width=3840)
Tableau Desktop Training - Analyst
By Tableau Training Uk
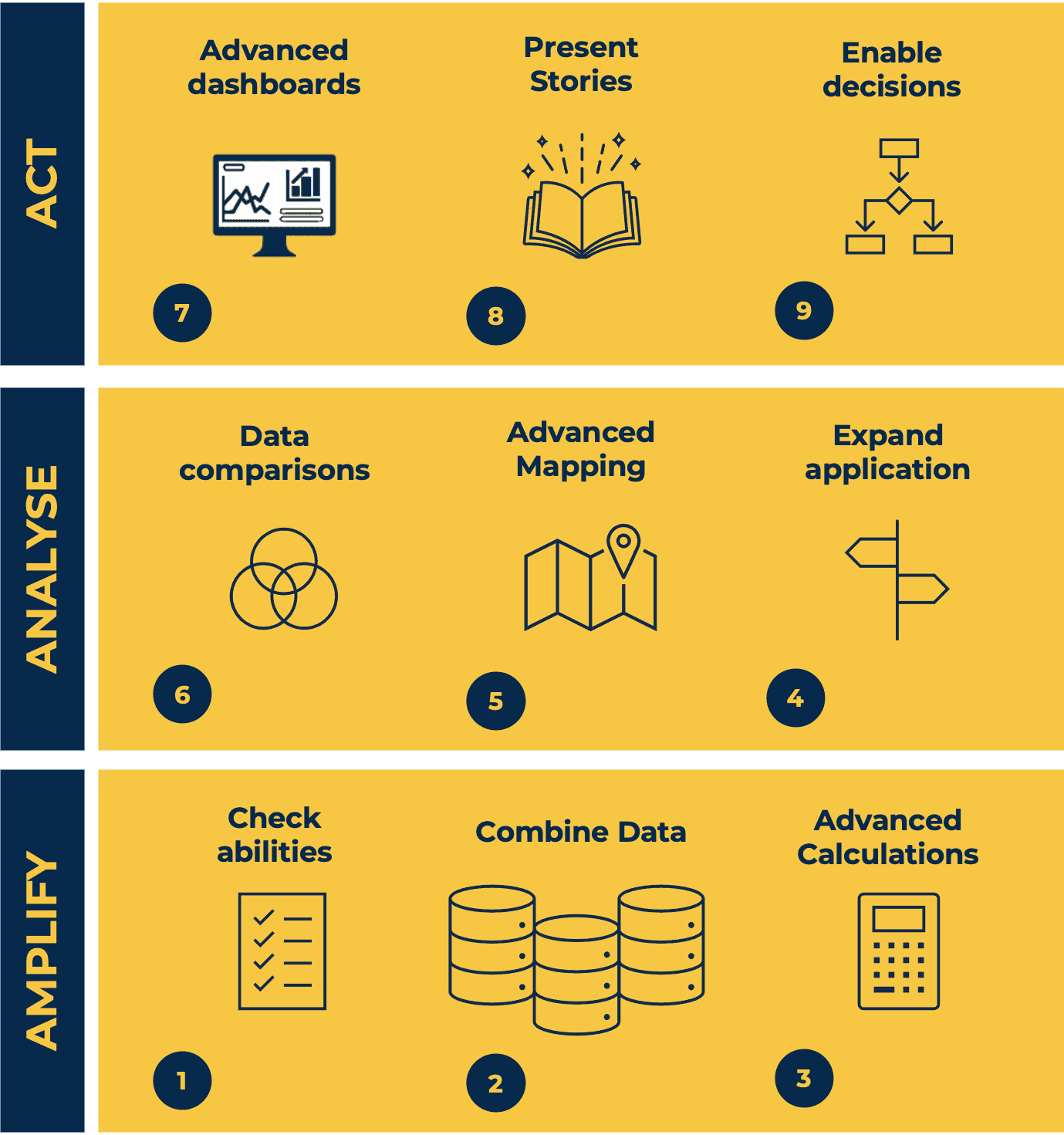
This Tableau Desktop Training intermediate course is designed for the professional who has a solid foundation with Tableau and is looking to take it to the next level. For Private options, online or in-person, please send us details of your requirements: This Tableau Desktop training intermediate course is designed for the professional who has a solid foundation with Tableau and is looking to take it to the next level. Attendees should have a good understanding of the fundamental concepts of building Tableau worksheets and dashboards typically achieved from having attended our Tableau Desktop Foundation Course. At the end of this course you will be able to communicate insights more effectively, enabling your organisation to make better decisions, quickly. The Tableau Desktop Analyst training course is aimed at people who are used to working with MS Excel or other Business Intelligence tools and who have preferably been using Tableau already for basic reporting. The course is split into 3 phases and 9 modules: Phase 1: AMPLIFY MODULE 1: CHECK ABILITIES Revision – What I Should Know What is possibleHow does Tableau deal with dataKnow your way aroundHow do we format chartsHow Tableau deals with datesCharts that compare multiple measuresCreating Tables MODULE 2: COMBINE DATA Relationships Joining Tables – Join Types, Joining tables within the same database, cross database joins, join calculations Blending – How to create a blend with common fields, Custom defined Field relationships and mismatched element names, Calculated fields in blended data sources Unions – Manual Unions and mismatched columns, Wildcard unions Data Extracts – Creating & Editing Data extracts MODULE 3: ADVANCED CALCULATIONS Row Level v Aggregations Aggregating dimensions in calculations Changing the Level of Detail (LOD) of calculations – What, Why, How Adding Table Calculations Phase 2: ANALYSE MODULE 4: EXPAND APPLICATION Making things dynamic with parameters Sets Trend Lines How do we format charts Forecasting MODULE 5: ADVANCED MAPPING Using your own images for spatial analysis Mapping with Spatial files MODULE 6: DATA COMPARISONS Advanced Charts Bar in Bar charts Bullet graphs Creating Bins and Histograms Creating a Box & Whisker plot Phase 3: ACT MODULE 7: ADVANCED DASHBOARDS Using the dashboard interface and Device layout Dashboard Actions and Viz In tooltips Horizontal & Vertical containers Navigate between dashboards MODULE 8: PRESENT STORIES Telling data driven stories MODULE 9: ENABLE DECISIONS What is Tableau Server Publishing & Permissions How can your users engage with content This training course includes over 25 hands-on exercises and quizzes to help participants “learn by doing” and to assist group discussions around real-life use cases. Each attendee receives a login to our extensive training portal which covers the theory, practical applications and use cases, exercises, solutions and quizzes in both written and video format. Students must bring their own laptop with an active version of Tableau Desktop 2018.2 (or later) pre-installed. What People Are Saying About This Course “Course was fantastic, and completely relevant to the work I am doing with Tableau. I particularly liked Steve’s method of teaching and how he applied the course material to ‘real-life’ use-cases.”Richard W., Dashboard Consulting Ltd “This course was extremely useful and excellent value. It helped me formalise my learning and I have taken a lot of useful tips away which will help me in everyday work.” Lauren M., Baillie Gifford “I would definitely recommend taking this course if you have a working knowledge of Tableau. Even the little tips Steve explains will make using Tableau a lot easier. Looking forward to putting what I’ve learned into practice.”Aron F., Grove & Dean “Steve is an excellent teacher and has a vast knowledge of Tableau. I learned a huge amount over the two days that I can immediately apply at work.”John B., Mporium “Steve not only provided a comprehensive explanation of the content of the course, but also allowed time for discussing particular business issues that participants may be facing. That was really useful as part of my learning process.”Juan C., Financial Conduct Authority “Course was fantastic, and completely relevant to the work I am doing with Tableau. I particularly liked Steve’s method of teaching and how he applied the course material to ‘real-life’ use-cases.”Richard W., Dashboard Consulting Ltd “This course was extremely useful and excellent value. It helped me formalise my learning and I have taken a lot of useful tips away which will help me in everyday work.” Lauren M., Baillie Gifford “I would definitely recommend taking this course if you have a working knowledge of Tableau. Even the little tips Steve explains will make using Tableau a lot easier. Looking forward to putting what I’ve learned into practice.”Aron F., Grove & Dean “Steve is an excellent teacher and has a vast knowledge of Tableau. I learned a huge amount over the two days that I can immediately apply at work.”John B., Mporium
Introduction to SQL Programming Basics (TTSQL002)
By Nexus Human
Duration 3 Days 18 CPD hours This course is intended for This is an introductory level SQL course, appropriate for anyone needing to interface with an Oracle database or those needing a general understanding of Oracle database functionality. That would include end users, business analysts, application developers and database administrators. Overview Working in a hands on learning environment led by our expert practitioner, attendees will explore: Basic RDBMS Principles The SQL Language and Tools Using SQL Developer SQL Query Basics WHERE and ORDER BY Functions ANSI 92 Joins ANSI 99 Joins Subqueries Regular Expressions Analytics A company?s success hinges on responsible, accurate database management. Organizations rely on highly available data to complete all sorts of tasks, from creating marketing reports and invoicing customers to setting financial goals. Data professionals like analysts, developers and architects are tasked with creating, optimizing, managing and analyzing data from databases ? with little room for error. When databases aren?t built or maintained correctly, it?s easy to mishandle or lose valuable data. Our SQL Programming and Database Training Series provides students with the skills they require to develop, analyze and maintain data and in correctly structured, modern and secure databases. A full presentation of the basics of relational databases and their use are also covered. Basic RDBMS Principles Relational design principles Accessing data through a structured query language Entity relationship diagrams Data Domains Null values Indexes Views Denormalization Data Model Review The SQL Language and Tools Using SQL*Plus Why Use SQL*Plus When Other Tools Are Available? Starting SQL*Plus EZConnect SQL Commands PL/SQL Commands SQL*Plus Commands The COLUMN Command The HEADING Clause The FORMAT Clause The NOPRINT Clause The NULL Clause The CLEAR Clause Predefined define variables LOGIN.SQL Command history Copy and paste in SQL*Plus Entering SQL commands Entering PL/SQL commands Entering SQL*Plus commands Default output from SQL*Plus Entering Queries What about PL/SQL? Using SQL Developer Choosing a SQL Developer version Configuring connections Creating A Basic Connection Creating A TNS Connection Connecting Configuring preferences Using SQL Developer The Columns Tab The Data Tab The Constraints Tab The Grants Tab The Statistics Tab Other Tabs Queries In SQL Developer Query Builder Accessing Objects Owned By Other Users The Actions Pulldown Menu Differences between SQL Developer and SQL*Plus Reporting Commands Missing In SQL Developer General Commands Missing In SQL Developer Data Dictionary report User Defined reports Using scripts in SQL Developer WHERE and ORDER BY WHERE clause basics Comparison operators Literals and Constants in SQL Simple pattern matching Logical operations The DUAL table Arithmetic operations Expressions in SQL Character operators Pseudo columns Order by clause basics Ordering Nulls Accent and case sensitive sorts Sampling data WHERE and ORDER BY in SQL Developer All, Any, Some Functions The basics of Oracle functions Number functions Character functions Date functions Conversion functions Other functions Large object functions Error functions The RR format mode; Leveraging your knowledge ANSI 92 JOINS Basics of ANSI 92 Joins Using Query Builder with multiple tables Table Aliases Outer joins Outer Joins In Query Builder Set operators Self-referential joins Non-Equijoins ANSI 99 Joins Changes with ANSI99 CROSS Join NATURAL Join JOIN USING JOIN ON LEFT / RIGHT OUTER JOIN FULL OUTER JOIN Subqueries Why use subqueries? WHERE clause subqueries FROM clause subqueries HAVING clause subqueries CORRELATED subqueries SCALAR subqueries DML and subqueries EXISTS subqueries Hierarchical queries TOP N AND BOTTOM N queries Creating subqueries using Query Builder Regular Expressions Available Regular Expressions Regular Expression Operators Character Classes Pattern matching options REGEX_LIKE REGEXP_SUBSTR REGEXP_INSTR REGEXP_REPLACE REGEXP_COUNT Analytics The WITH clause Reporting aggregate functions Analytical functions User-Defined bucket histograms The MODEL clause PIVOT and UNPIVOT Temporal validity More Analytics RANKING functions RANK DENSE_RANK CUME_DIST PERCENT_RANK ROW_NUMBER Windowing aggregate functions RATIO_TO_REPORT LAG / LEAD Linear Regression functions Inverse Percentile functions Hypothetical ranking functions Pattern Matching Additional course details: Nexus Humans Introduction to SQL Programming Basics (TTSQL002) training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Introduction to SQL Programming Basics (TTSQL002) course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Search By Location
- knowledge Courses in London
- knowledge Courses in Birmingham
- knowledge Courses in Glasgow
- knowledge Courses in Liverpool
- knowledge Courses in Bristol
- knowledge Courses in Manchester
- knowledge Courses in Sheffield
- knowledge Courses in Leeds
- knowledge Courses in Edinburgh
- knowledge Courses in Leicester
- knowledge Courses in Coventry
- knowledge Courses in Bradford
- knowledge Courses in Cardiff
- knowledge Courses in Belfast
- knowledge Courses in Nottingham