- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
CSCS is the leading Construction Skills Certification Scheme within the UK construction industry to ensure safety standards are high and maintained within the construction industry in the UK. CSCS cards provide proof that individuals working on construction sites have the required training in Construction Health and Safety awareness for the type of work they carry out.

Create Your Own Beautiful Pearl Necklace in One Day!
By Ark Jewellery by Kristina Smith
Have you ever admired the elegant drape of a classic pearl necklace? Now you can learn the secret! This one-day introductory workshop teaches you the refined skill of pearl and gemstone bead knotting. This technique not only adds exquisite decorative spacing but also protects your delicate beads and keeps them secure should a string ever break. In just a few focused hours, you'll master the key techniques to confidently design and create your own knotted necklaces. We'll guide you through planning your design, perfecting your knots, and securely adding a clasp. You'll also discover the best threads and tools for professional results. You'll leave the class with a gorgeous, self-made knotted pearl necklace, ready to wear or gift! What's Included: Your investment covers a productive day of tuition (10 am - 2:30 pm), full access to all necessary tools, and a beautiful selection of gemstones and pearls to create your piece. All other materials and consumables are included, as are tea, coffee, and refreshments. Lunch can be provided at an additional cost. Cancellation Policy: Life happens! You can cancel and receive a full refund up to two weeks before the course begins.

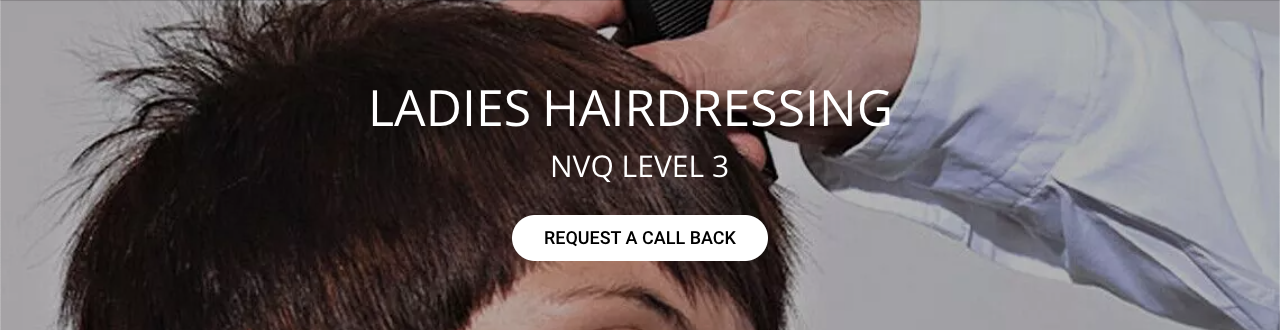
Level 3 NVQ Diploma in Hairdressing
By Alan d Hairdressing Education
This Advanced Hairdressing Course is aimed at qualified stylists looking to develop more advanced skills whilst working towards an internationally recognised qualification. You’ll receive training on creative cutting, advanced colour techniques, colour correction, creative long hair styling and some creative barbering techniques.
Refresher training IV sedation for Dentists and Nurses
By UKSedation
Work in Dentistry and provide sedation for your patients? This one day face to face course gives 7 hour vCPD and will refresh you on techniques and scenarios. Includes Practical training with blood pressure, pulse oximetry, cannulation and monitoring, along with emergency scenarios. THIS ONE DAY FACE TO FACE COURSE IS DESIGNED FOR DENTISTS AND NURSES ALREADY IN THE FIELD OF DENTAL SEDATION, WITH UPDATES ON REGULATIONS ALONG WITH PRACTICAL STATIONS ON CANNULATION, PROBLEM SOLVING, ASSESSMENTS AND MONITORING. PART OF THE DAY WILL INVOLVE SOME AIRWAY MANAGEMENT TRAINING AS WELL. Course Includes 24 Lessons 14 Quizzes Course Certificate About Instructor Rob Endicott Roy Bennett Dr Roy Bennett is the director of Mellow Dental Training, IACSD accredited trainer and mentor and former director of Portmans Dental Care. Dr Rob Endicott is an IACSD accredited trainer and mentor and is the ViceChair of the ADAS (Association of Dental Anaesthetists and Sedationists)

Personal Tax Return and Self Assessment training Course
By Osborne Training
Personal Tax Return and Self Assessment training Course Most self-employed people and directors of companies have to do submit a Tax Return every year. If you are a self-employed person you may learn how to do tax return yourself. As a result, you can save money by not having to pay an external agent. Don't forget You can also save more money as you will know more about how to apply for a tax rebate. According to statistics, more than 60% of taxpayers not sure how to do tax return correctly and lose money for not knowing how to apply for a tax rebate correctly. If you want to offer tax services to the general public, then skills in this sector can dramatically improve your job prospect or business prospect. How to do a tax return Firstly, you need to be registered with HMRC to process your tax return. You should get a UTR (Unique Tax Reference) no, which is your personal identification no for tax purpose. Once you have details for all incomes and expenditure, you can submit them electronically to HMRC. The deadline for submitting a personal tax return is 31 January for the previous tax year. Apply for a Tax Rebate It is possible that you could be eligible for a tax rebate. The most possible scenarios are When you pay more tax than required Submitting an incorrect tax return Claiming special Tax relief There could be many more reasons why should you get a tax refund. It is vital to know the scenarios under which you should apply for a tax rebate. Identify the type(s) of returns that may be completed Understand the duties and responsibilities of a bookkeeper / tax agent when completing self-assessment tax returns Calculating the taxes on profits for Self Employed & on income for Employed individuals Understanding differences between Drawings & Dividends Introduction to UTR and NI Classes Understanding Tax Return submission procedures to HMRC (using 2 individual Scenarios) Analysing Class 2 & Class 4 NIC Analysing Personal Allowance Analysing Income from Self Employments Employment benefits Analysis Analysis of Car & Fuel benefits Analysis on savings and investment income and tax implications on them. Introduction to Capital Gains Tax analysis Introduction to Inheritance Tax Analysis Understanding the procedure for payment and administration of both tax and National Insurance Contributions

The NVQ Level 3 is designed to provide both new entrants and those seeking progression in their career, with the opportunity to develop the necessary skills to carry out job roles and responsibilities associated with the installation and maintenance of Electrotechnical systems. There are two options to complete the NVQ Level 3 in Electrical Installations, these are the C&G 2346 and C&G 2357. Successful completion of the NVQ and AM2 assessment will satisfy the entry criteria for JIB accredited electricians

Foundation Ladies Cutting & Styling
By Alan d Hairdressing Education
Take your first step into the world of hairdressing with this Beginners Hairdressing Course. You will learn the 9 Alan d Foundation haircuts along with classes on shampooing, blow-drying, cutting, styling, client care and salon protocol.

DROP-IN chocolate workshops with: CHRISTMAS MONTH: Every Sunday you can choose to make a chocolate bar and its wrapper illustrating Christmas.
4.7(60)By The Chocolate Museum
The Drop-in workshop is a DIY creative chocolate making session running on Sundays; You can book 1h slot anytime between 11.30am and 5.30pm for table of 6 maximum.

Search By Location
- class Courses in London
- class Courses in Birmingham
- class Courses in Glasgow
- class Courses in Liverpool
- class Courses in Bristol
- class Courses in Manchester
- class Courses in Sheffield
- class Courses in Leeds
- class Courses in Edinburgh
- class Courses in Leicester
- class Courses in Coventry
- class Courses in Bradford
- class Courses in Cardiff
- class Courses in Belfast
- class Courses in Nottingham

