- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
1638 Courses in London
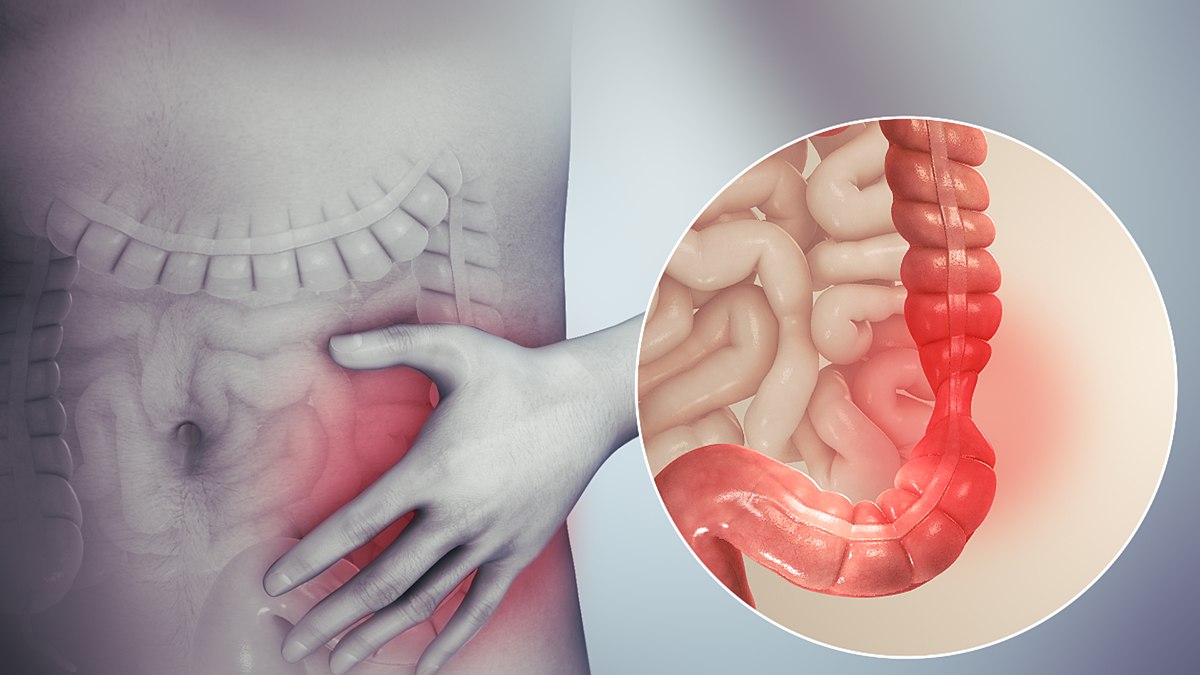
An Understanding of Bowel Care
By Guardian Angels Training
Gain comprehensive knowledge and practical skills for safe and effective bowel care management with our "An Understanding of Bowel Care Techniques" course. Ideal for healthcare professionals seeking to promote patient comfort and prevent complications.
Windows certificates training course description A hands-on training course concentrating solely on PKI using Windows certificates. What will you learn Explain how PKI works. Install windows certificates. Configure windows certificates. Troubleshoot windows certificates. Windows certificates training course details Who will benefit: Technical security staff. Prerequisites: Windows server. Duration 3 days Windows certificates training course contents PKI Symmetric encryption, asymmetric encryption, authentication, digital signing, hashing, certificates, Certification Authorities, Root CA, Intermediate CA, policy CA, Issuing CA, Certificate Revocation Lists. Hands on Inspecting a certificate. Policies and PKI Security policy, certification policy. CA hierarchy Impact of CAs on Active Directory, CA architecture, number of tiers, issuing CA organisation, CA configuration files. CA security. Hands on CA installation PKI health tool, monitoring. Certificate revocation When to revoke, OCSP. Hands on Revoking certificates. Certificate validation Discovery, validation, checks, revocation checking, certificate chains, certification publication. Hands on Event viewer. Certificate templates Version 1, version 1, default, modifying templates. Hands on Template management. Roles Criteria roles, CA administrator, Certificate manager, Backup operator, Auditor. Other PKI management roles. Disaster recovery Backups, recovery. Hands on certutil. Issuing certificates The certificate enrolment process, enrolment methods, manual enrolment, automatic enrolment. Trust between organisations Creating Trust, CTLs, common root CA, cross certification, bridge CA. Web servers and certificates SSL encryption, certificate authentication. Hands on Web servers. VPN Hands on Certificate deployment for VPN. WiFi Hands on 802.1X

Managing Stress and Building Resilience
By IIL Europe Ltd
Managing Stress and Building Resilience Stress has an impact on all of us at some point in our professional lives. Learning how to manage stress and build resilience will result in higher professional productivity, better health, and more sustainable living habits. It will also help us create a physical - and emotional - work-life balance. In this one-day workshop, you will learn practical solutions to sustain behavior change that can positively impact your life on both a professional and personal level. When you are able to reduce the level of negative stress that affects you, your performance improves, along with your health and happiness. The objective of this course is therefore not only to create awareness around emotional well-being in a work context, but also to help participants create a better overall balance between the investment they make in their personal and professional lives. This course covers how our perceptions affect our beliefs and how our beliefs affect our actions. You will learn a host of stress-reduction techniques, while exploring your own stress triggers and responses. Highly interactive, the sessions cover a blend of theory, discussions, and exercises. You will explore concepts with fellow participants within a safe environment where skills and habits can be developed, sharpened, and improved. What You Will Learn At the end of this program, you will be able to: Identify what stress feels like and what the typical symptoms and reactions are to stress Analyze your own responses to stressful events and the consequences of those reactions Organize your work structure to reduce stress and build resilience Recognize activities that drain you and those that give you energy Generate relief from stressful events Cultivate a mindset of resilience Better manage your time, work commitments, and personal boundaries in order to be most effective at your job Getting Started What is stress? Beliefs and thinking errors Work-life balance Drainers and energizers Stress reduction techniques Time management Summary and Next Steps

Security+ training course description A hands on course aimed at getting delegates successfully through the CompTia Security+ examination. What will you learn Explain general security concepts. Describe the security concepts in communications. Describe how to secure an infrastructure. Recognise the role of cryptography. Describe operational/organisational security. Security+ training course details Who will benefit: Those wishing to pass the Security+ exam. Prerequisites: TCP/IP foundation for engineers Duration 5 days Security+ training course contents General security concepts Non-essential services and protocols. Access control: MAC, DAC, RBAC. Security attacks: DOS, DDOS, back doors, spoofing, man in the middle, replay, hijacking, weak keys, social engineering, mathematical, password guessing, brute force, dictionary, software exploitation. Authentication: Kerberos, CHAP, certificates, usernames/ passwords, tokens, biometrics. Malicious code: Viruses, trojan horses, logic bombs, worms. Auditing, logging, scanning. Communication security Remote access: 802.1x, VPNs, L2TP, PPTP, IPsec, RADIUS, TACACS, SSH. Email: S/MIME, PGP, spam, hoaxes. Internet: SSL, TLS, HTTPS, IM, packet sniffing, privacy, Javascript, ActiveX, buffer overflows, cookies, signed applets, CGI, SMTP relay. LDAP. sftp, anon ftp, file sharing, sniffing, 8.3 names. Wireless: WTLS, 802.11, 802.11x, WEP/WAP. Infrastructure security Firewalls, routers, switches, wireless, modems, RAS, PBX, VPN, IDS, networking monitoring, workstations, servers, mobile devices. Media security: Coax, UTP, STP, fibre. Removable media. Topologies: Security zones, DMZ, Intranet, Extranet, VLANs, NAT, Tunnelling. IDS: Active/ passive, network/host based, honey pots, incident response. Security baselines: Hardening OS/NOS, networks and applications. Cryptography basics Integrity, confidentiality, access control, authentication, non-repudiation. Standards and protocols. Hashing, symmetric, asymmetric. PKI: Certificates, policies, practice statements, revocation, trust models. Key management and certificate lifecycles. Storage: h/w, s/w, private key protection. Escrow, expiration, revocation, suspension, recovery, destruction, key usage. Operational/Organisation security Physical security: Access control, social engineering, environment. Disaster recovery: Backups, secure disaster recovery plans. Business continuity: Utilities, high availability, backups. Security policies: AU, due care, privacy, separation of duties, need to know, password management, SLAs, disposal, destruction, HR policies. Incident response policy. Privilege management: Users, groups, roles, single sign on, centralised/decentralised. Auditing. Forensics: Chain of custody, preserving and collecting evidence. Identifying risks: Assets, risks, threats, vulnerabilities. Role of education/training. Security documentation.

Permanent Makeup Laser Removal | N-Light-10 Laser Only
By ID Liner | Permanent Makeup Training & Supplies
HIGHLY SOUGHT-AFTER AND ALREADY AN EXTREMELY LUCRATIVE INDUSTRY, LASER TATTOO REMOVAL IS SET TO BE THE BIGGEST BEAUTY TREND OF 2023!

Permanent Makeup Laser Removal - Small Group Training - N-Light-10 Laser
By ID Liner | Permanent Makeup Training & Supplies
HIGHLY SOUGHT-AFTER AND ALREADY AN EXTREMELY LUCRATIVE INDUSTRY, LASER TATTOO REMOVAL IS SET TO BE THE BIGGEST BEAUTY TREND OF 2023!

Petroleum Geology for Non-Geologists
By EnergyEdge - Training for a Sustainable Energy Future
About this Training Course To the non-geologist, working with Petroleum Geologists can be confusing. Petroleum geology has specific terminology and many concepts and data sources unfamiliar to the uninitiated. This course has been designed to introduce these terms and provide an insight into how oil and gas are formed, how they are found and how they are extracted. Using a holistic combination of lectures, experiments, case study and practical exercises, the course involves an introduction to fundamental geological concepts, to exploration techniques, prospecting, drilling, well logs and recovery methods. The course will also demystify the terminology surrounding petroleum geology, demonstrate the use of geological information to show the value and weakness of different datasets, and lead to better communication and decision-making between the geologists and non-geologists. It will feature world-class virtual reality field trips that incorporate activities and features unavailable in the physical field, and provide for a more integrated and flexible learning resource (also see the trainer's article on page 4 which was first published in GEO ExPro Magazine, the upstream oil and gas industry's favourite magazine). Course Highlights: Course facilitator has delivered petroleum geology training to many companies over the years Facilitator is also a professionally trained teacher and former university lecturer who is experienced in communicating with people at all levels of technical knowledge Practical exercises, experiments, examination of real rocks, a virtual reality field trip and case study are used to clarify and reinforce important concepts Training Objectives By attending this training, you will be able to acquire the following: Understand the geological methods and principles used in hydrocarbon exploration, development and production. Understand the key elements of a petroleum system, from hydrocarbon source to reservoir and seal Appreciate basin analysis, regional geology and play based exploration techniques Be aware of the different sorts of hydrocarbon trap from structural to stratigraphic Understand the technical terminology, tools and methods used in exploration geology Learn about unconventional Understand and evaluate the sources and reliability of various types of geological information Understand acquisition, processing and interpretation of seismic data Learn the technical processes and terminology involved in exploration Understand how a prospect is defined and risked Understand how seismic, existing well information and outcrop geology can be used for exploration Gain an understanding of the methods used for petroleum geology to allow a discovery to be appraised and then developed Target Audience The course is suitable to all personnel, but those that benefit most include: This course will benefit Petroleum Engineers (reservoir, drilling, production) who work with geological data, Geophysicists with little or no geological background, Project managers whose teams include petroleum geologists, Finance, Procurement, Marketing and Communications staff, and government Data Managers who handle petroleum geological data and need to understand the sources of different types of data. Trainer Your expert course leader is the Geosciences Technical Director for PetroEdge. She was previously, the manager of Robertson Petroleum Training Centre and a Senior Project Scientist at Robertson CGG. She has over 20 years of experience in teaching geology and leading field trips. Prior to her 8 years at Robertson, she was in academia as a lecturer for 6 years and a Research Fellow for 3 years. She has conducted fieldwork and led field trips in the US and many areas in the UK. In addition, she has led university regional geology day schools and has comprehensive experience in course and study programme writing. She has extensive experience in delivering courses and in Clastic and Carbonate Reservoir Geology, Deepwater Turbidites, Sandstone Reservoirs, Wireline Log Interpretation, Integrated Sequence Stratigraphy, Basin Analysis and Exploration & Appraisal workshops globally. In delivering the Exploration Team Management Workshop, she has project managed and taught key principles and modules on project planning, data collection/collation, geophysical assessment, stratigraphy and facies mapping, source rock facies and hydrocarbon generation, play fairway mapping, risking and prospect evaluation. Her knowledge and enthusiasm for instructing is reflected in consistently being rated as excellent by trainees, and clients specifically requesting her participation in courses. POST TRAINING COACHING SUPPORT (OPTIONAL) To further optimise your learning experience from our courses, we also offer individualized 'One to One' coaching support for 2 hours post training. We can help improve your competence in your chosen area of interest, based on your learning needs and available hours. This is a great opportunity to improve your capability and confidence in a particular area of expertise. It will be delivered over a secure video conference call by one of our senior trainers. They will work with you to create a tailor-made coaching program that will help you achieve your goals faster. Request for further information post training support and fees applicable Accreditions And Affliations

Microsoft security training course description A hands on training course focusing on security in the Microsoft environment. The course progresses from patch management onto the use of Microsoft security tools. Then server, desktop and network security are studied in the Microsoft environment. What will you learn Use Microsoft security tools. Secure Microsoft servers. Secure Microsoft desktops. Secure Microsoft networks. Microsoft security training course details Who will benefit: Technical server support staff. Technical desktop support staff. Technical network staff. Technical security staff. Prerequisites: Supporting Windows server 2016 Networking Microsoft systems. Duration 3 days Microsoft security training course contents Introduction Security threats, Microsoft defaults, admin accounts, security patches, patch management, patch tools. Hands on: Studying Microsoft defaults, applying security patches. Microsoft security tools Microsoft updates, WSUS, Inventory tool, baseline security analyser, URLscan, EventCombMT, Cipher security tool, Port reporter, PortQry. Tools hackers use. Hands on: Using Microsoft security tools. Server security Checklists, core server security, AD, Member server security, Domain controller security, Specific roles. Hands on Hardening Microsoft servers, security templates. Active Directory Admin authority in AD, group policy, trust and authentication. Desktop security Checklists, core client security, anti virus software, anti spyware software, firewalls, securing clients with AD, securing clients with group policy, software restriction policies. Hands on Securing Microsoft desktops. Network security Checklist, IP security, VPNs, PKI, certificate authorities, RAS, RRAS, IAS. Hands on: VPN configuration, IAS configuration. Monitoring Auditing, authorisation and logons, tracking, system monitoring, detecting attacks. Hands on: Monitoring Microsoft systems. Summary Microsoft security response centre, security advisories.

Mediation 4 Managers - 2-Day Training Course (£1450 total for this 2-day course for a group of 5-10 Managers)
By Buon Consultancy
Mediation for Managers Training

The “ISO 22301:2019 Lead Implementer ” course provides comprehensive training in the ISO 22301:2019 standard and all its requirements from the Implementer ’s point of view, as well as basic skills necessary to execute the requirements. It’s a practical-oriented training that should be considered “a must” for every ISO 22301:2019 Implementer. This intensive course is specifically designed to participants to serve as ISO 22301:2019 Lead Implementers. The interactive training program, complete with quizzes, will provide the necessary technical knowledge and understanding of all ISO 22301:2019 requirements to implement the requirement of the standard.

Search By Location
- Management Courses in London
- Management Courses in Birmingham
- Management Courses in Glasgow
- Management Courses in Liverpool
- Management Courses in Bristol
- Management Courses in Manchester
- Management Courses in Sheffield
- Management Courses in Leeds
- Management Courses in Edinburgh
- Management Courses in Leicester
- Management Courses in Coventry
- Management Courses in Bradford
- Management Courses in Cardiff
- Management Courses in Belfast
- Management Courses in Nottingham