- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
Overview This is a 2 day course on understanding credit markets converting credit derivatives, from plain vanilla credit default swaps through to structured credit derivatives involving correlation products such as nth to default baskets, index tranches, synthetic collateralized debt obligations and more. Gain insights into the corporate credit market dynamics, including the role of ratings agencies and the ratings process. Delve into the credit triangle, relating credit spreads to default probability (PD), exposure (EAD), and expected recovery (LGD). Learn about CDS indices (iTRAXX and CDX), their mechanics, sub-indices, tranching, correlation, and the motivation for tranched products. The course also includes counterparty risk in derivatives market where you learn how to managed and price Counterparty Credit Risk using real-world, practical examples Understand key definitions of exposure, including Mark-to-Market (MTM), Expected Exposure (EE), Expected Positive Exposure (EPE), Potential Future Exposure (PFE), Exposure at Default (EAD), and Expected Loss (EL) Explore the role of collateral and netting in managing counterparty risk, including the key features and mechanics of the Credit Support Annex (CSA) Briefly touch upon other XVA adjustments, including Margin Valuation Adjustment (MVA), Capital Valuation Adjustment (KVA), and Collateral Valuation Adjustment (CollVA). Who the course is for Credit traders and salespeople Structurers Asset managers ALM and treasury (Banks and Insurance Companies) Loan portfolio managers Product control, finance and internal audit Risk managers Risk controllers xVA desk IT Regulatory capital and reporting Course Content To learn more about the day by day course content please request a brochure To learn more about schedule, pricing & delivery options, book a meeting with a course specialist now

Learn the 1st secret of self defence
By Streetwise Defence (Self Defence Training)
Interested in learning about personal safety and self defence? Enrol now on our FREE mini course and learn the 1st secret of self defence!

Bespoke and One-off Courses and Workshops
By Beyond Theory: business training & coaching
leadership management training course

Tableau Desktop Training - Foundation
By Tableau Training Uk
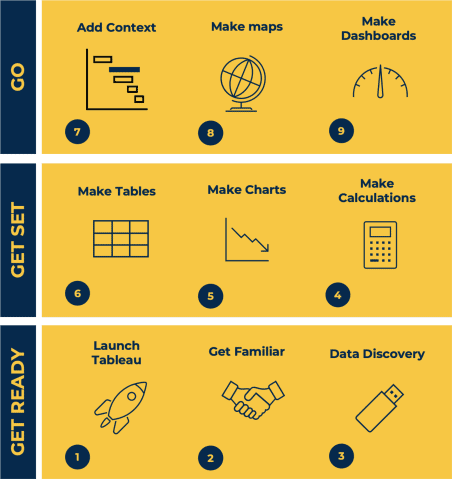
This Tableau Desktop Training course is a jumpstart to getting report writers and analysts with little or no previous knowledge to being productive. It covers everything from connecting to data, through to creating interactive dashboards with a range of visualisations in two days of your time. For Private options, online or in-person, please send us details of your requirements: This Tableau Desktop Training course is a jumpstart to getting report writers and analysts with little or no previous knowledge to being productive. It covers everything from connecting to data, through to creating interactive dashboards with a range of visualisations in two days of your time. Having a quick turnaround from starting to use Tableau, to getting real, actionable insights means that you get a swift return on your investment of time and money. This accelerated approach is key to getting engagement from within your organisation so everyone can immediately see and feel the impact of the data and insights you create. This course is aimed at someone who has not used Tableau in earnest and may be in a functional role, eg. in sales, marketing, finance, operations, business intelligence etc. The course is split into 3 phases and 9 modules: PHASE 1: GET READY MODULE 1: LAUNCH TABLEAU Check Install & Setup Why is Visual Analytics Important MODULE 2: GET FAMILIAR What is possible How does Tableau deal with data Know your way around How do we format charts Dashboard Basics – My First Dashboard MODULE 3: DATA DISCOVERY Connecting to and setting up data in Tableau How Do I Explore my Data – Filters & Sorting How Do I Structure my Data – Groups & Hierarchies, Visual Groups How Tableau Deals with Dates – Using Discrete and Continuous Dates, Custom Dates Phase 2: GET SET MODULE 4: MAKE CALCULATIONS How Do I Create Calculated Fields & Why MODULE 5: MAKE CHARTS Charts that Compare Multiple Measures – Measure Names and Measure Values, Shared Axis Charts, Dual Axis Charts, Scatter Plots Showing Relational & Proportional Data – Pie Charts, Donut Charts, Tree Maps MODULE 6: MAKE TABLES Creating Tables – Creating Tables, Highlight Tables, Heat Maps Phase 3: GO MODULE 7: ADD CONTEXT Reference Lines and Bands MODULE 8: MAKE MAPS Answering Spatial Questions – Mapping, Creating a Choropleth (Filled) Map MODULE 9: MAKE DASHBOARDS Using the Dashboard Interface Dashboard Actions This training course includes over 25 hands-on exercises and quizzes to help participants “learn by doing” and to assist group discussions around real-life use cases. Each attendee receives a login to our extensive training portal which covers the theory, practical applications and use cases, exercises, solutions and quizzes in both written and video format. Students must use their own laptop with an active version of Tableau Desktop 2018.2 (or later) pre-installed. What People Are Saying About This Course “Excellent Trainer – knows his stuff, has done it all in the real world, not just the class room.”Richard L., Intelliflo “Tableau is a complicated and powerful tool. After taking this course, I am confident in what I can do, and how it can help improve my work.”Trevor B., Morrison Utility Services “I would highly recommend this course for Tableau beginners, really easy to follow and keep up with as you are hands on during the course. Trainer really helpful too.”Chelsey H., QVC “He is a natural trainer, patient and very good at explaining in simple terms. He has an excellent knowledge base of the system and an obvious enthusiasm for Tableau, data analysis and the best way to convey results. We had been having difficulties in the business in building financial reports from a data cube and he had solutions for these which have proved to be very useful.”Matthew H., ISS Group
F5 Networks Configuring BIG-IP Advanced WAF - Web Application Firewall (formerly ASM)
By Nexus Human
Duration 4 Days 24 CPD hours This course is intended for This course is intended for security and network administrators who will be responsible for the installation, deployment, tuning, and day-to-day maintenance of the F5 Advanced Web Application Firewall. In this 4 day course, students are provided with a functional understanding of how to deploy, tune, and operate F5 Advanced Web Application Firewall to protect their web applications from HTTP-based attacks. The course includes lecture, hands-on labs, and discussion about different F5 Advanced Web Application Firewall tools for detecting and mitigating threats from multiple attack vectors such web scraping, Layer 7 Denial of Service, brute force, bots, code injection, and zero day exploits. Module 1: Setting Up the BIG-IP System Introducing the BIG-IP System Initially Setting Up the BIG-IP System Archiving the BIG-IP System Configuration Leveraging F5 Support Resources and Tools Module 2: Traffic Processing with BIG-IP Identifying BIG-IP Traffic Processing Objects Overview of Network Packet Flow Understanding Profiles Overview of Local Traffic Policies Visualizing the HTTP Request Flow Module 3: Web Application Concepts Overview of Web Application Request Processing Web Application Firewall: Layer 7 Protection F5 Advanced WAF Layer 7 Security Checks Overview of Web Communication Elements Overview of the HTTP Request Structure Examining HTTP Responses How F5 Advanced WAF Parses File Types, URLs, and Parameters Using the Fiddler HTTP Proxy Module 4: Common Web Application Vulnerabilities A Taxonomy of Attacks: The Threat Landscape What Elements of Application Delivery are Targeted? Common Exploits Against Web Applications Module 5: Security Policy Deployment Defining Learning Comparing Positive and Negative Security Models The Deployment Workflow Policy Type: How Will the Policy Be Applied Policy Template: Determines the Level of Protection Policy Templates: Automatic or Manual Policy Building Assigning Policy to Virtual Server Deployment Workflow: Using Advanced Settings Selecting the Enforcement Mode The Importance of Application Language Configure Server Technologies Verify Attack Signature Staging Viewing Requests Security Checks Offered by Rapid Deployment Defining Attack Signatures Using Data Guard to Check Responses Module 6: Policy Tuning and Violations Post-Deployment Traffic Processing Defining Violations Defining False Positives How Violations are Categorized Violation Rating: A Threat Scale Defining Staging and Enforcement Defining Enforcement Mode Defining the Enforcement Readiness Period Reviewing the Definition of Learning Defining Learning Suggestions Choosing Automatic or Manual Learning Defining the Learn, Alarm and Block Settings Interpreting the Enforcement Readiness Summary Configuring the Blocking Response Page Module 7: Attack Signatures & Threat Campaigns Defining Attack Signatures Attack Signature Basics Creating User-Defined Attack Signatures Defining Simple and Advanced Edit Modes Defining Attack Signature Sets Defining Attack Signature Pools Understanding Attack Signatures and Staging Updating Attack Signatures Defining Threat Campaigns Deploying Threat Campaigns Module 8: Positive Security Policy Building Defining and Learning Security Policy Components Defining the Wildcard Defining the Entity Lifecycle Choosing the Learning Scheme How to Learn: Never (Wildcard Only) How to Learn: Always How to Learn: Selective Reviewing the Enforcement Readiness Period: Entities Viewing Learning Suggestions and Staging Status Violations Without Learning Suggestions Defining the Learning Score Defining Trusted and Untrusted IP Addresses How to Learn: Compact Module 9: Cookies and Other Headers F5 Advanced WAF Cookies: What to Enforce Defining Allowed and Enforced Cookies Configuring Security Processing on HTTP headers Module 10: Reporting and Logging Overview: Big Picture Data Reporting: Build Your Own View Reporting: Chart based on filters Brute Force and Web Scraping Statistics Viewing F5 Advanced WAF Resource Reports PCI Compliance: PCI-DSS 3.0 The Attack Expert System Viewing Traffic Learning Graphs Local Logging Facilities and Destinations How to Enable Local Logging of Security Events Viewing Logs in the Configuration Utility Exporting Requests Logging Profiles: Build What You Need Configuring Response Logging Module 11: Lab Project 1 Lab Project 1 Module 12: Advanced Parameter Handling Defining Parameter Types Defining Static Parameters Defining Dynamic Parameters Defining Dynamic Parameter Extraction Properties Defining Parameter Levels Other Parameter Considerations Module 13: Automatic Policy Building Overview of Automatic Policy Building Defining Templates Which Automate Learning Defining Policy Loosening Defining Policy Tightening Defining Learning Speed: Traffic Sampling Defining Track Site Changes Lesson 14: Web Application Vulnerability Scanner Integration Integrating Scanner Output Importing Vulnerabilities Resolving Vulnerabilities Using the Generic XML Scanner XSD file Lesson 15: Deploying Layered Policies Defining a Parent Policy Defining Inheritance Parent Policy Deployment Use Cases Lesson 16: Login Enforcement and Brute Force Mitigation Defining Login Pages for Flow Control Configuring Automatic Detection of Login Pages Defining Session Tracking Brute Force Protection Configuration Source-Based Brute Force Mitigations Defining Credentials Stuffing Mitigating Credentials Stuffing Lesson 17: Reconnaissance with Session Tracking Defining Session Tracking Configuring Actions Upon Violation Detection Lesson 18: Layer 7 DoS Mitigation Defining Denial of Service Attacks Defining the DoS Protection Profile Overview of TPS-based DoS Protection Creating a DoS Logging Profile Applying TPS Mitigations Defining Behavioral and Stress-Based Detection Lesson 19: Advanced Bot Protection Classifying Clients with the Bot Defense Profile Defining Bot Signatures Defining Proactive Bot Defense Defining Behavioral and Stress-Based Detection Defining Behavioral DoS Mitigation Lesson 20: Form Encryption using DataSafe Targeting Elements of Application Delivery Exploiting the Document Object Model Protecting Applications Using DataSafe The Order of Operations for URL Classification Lesson 21: Review and Final Labs Review and Final Labs

Mastering Management: Navigating the UK's Top Courses for Success
By Assignment help Online
Get the best management assignment help and management course guide online by Uk management experts.

CONSULTATIVE SELLING Training Programme Framework
By Dickson Training Ltd
Key Objectives for the Training provision Effective listening to a client's needs and requirements during various stages of the sales process. Engage in meaningful communication with clients, learn to identify challenges and opportunities that relate to the prospects. Overcome the identified challenge. Build long term rapport and establish trust with the prospect throughout the sales process, Ensure continued customer satisfaction that can turn into repeat business. Be able to build rapport with customers or clients. Know the right questions to ask to fully understand the customer or client’s needs without putting on any pressure. Be able to check you have the right information from the customer or client. Be able to match products and services to the customer or client using the information you have gathered. Be able to influence effectively. Know how to stand out from your competitors. Stage 1 – Research the Company’s ‘Value Propositions’ and USP Analysis Conducting 30 min confidential interviews with a cross-section of the eligible Attendees & the Stakeholders, in order to gain an objective understanding of the various scenarios and clients that the Participants work with. the Company’s ‘Value Propositions’ Unique Selling Points The Customers’ journey(s) The Competition’s offers for analysis and comparisons. From these findings, a carefully calibrated bespoke Programme will be designed and delivered. Stage 2 - Design the Bespoke 2 x day Course nd Stage 3 - Delivery of the Course Programme This Programme can be delivered in 2 x consecutive days, or split between 2 – 3 weeks, to make it more ‘work-friendly’ – if required. It is very practical and commercially focussed in approach, with lots of interactive exercises designed to draw out the learning applications via the debriefings. The ‘Real Play’ scenarios on day 2 will be based on specific case studies drawn from the Research findings so that they are authentic to optimise the learning. Individual Action Plans will be captured at the end of each day to be debriefed by the Participants’ respective Line Managers. Template Programme Day One – Foundation – Strategic Approach Section One – The Principles of Consultative Selling Defining ‘Consultative Selling’ The Company’s ‘Unique Selling Points’ & Value Proposition The Consultative Selling model – the five stages Avoiding appearing ‘pushy’, ‘pressurising’ or ‘talking through the sale’ Section Two –Strategy & Preparation ‘Buy-Class’ Matrix Strategic plan Template – matching services/products to identified needs & opportunities. Preparing a range of objectives Constants and variables – USP’s Researching key Client/Decision Makers’ priorities, profile & background (LinkedIn etc.) Preparing for potential & likely Objections Section Three – Email etiquette & ‘influencing’ email correspondence. Email etiquette A.B.S.U.R.D model Clarity and tone – discovery of clients’ needs & motivational factors. Techniques to influence and ‘nudge’. Ensuring the data and content have a ‘gentle’ motivational & appealing message. Top Tips Day Two – Practical Application Section Four – Rapport Building & Effective Communication skills ‘Behaviour Labelling’ techniques – setting a positive tone. Asking Open Questions – gaining a full understanding of the clients’ priorities & expectations. EQ - Inviting opinions; perspectives; experiences – winning confidence. Active Listening – focus and commitment to understand. ‘Reading the room’ – adapting to responses and reactions. Maintaining focus on relevant topics that the Client cares about; carefully consider the opportunities to influence. But NO PRESSURE! Building a ‘bond of trust’ with commitments and authentic, shared values. Section Five – Explaining the Benefits – aligned to the Customers’ Priorities Understanding ‘Why do People Buy?’ Research data analysis. Open questions that lead to understanding the key issues and Clients’ priorities. Avoiding the danger of ‘pressurising’ the Client. Responding to objections effectively, with confidence and sensitivity. Explaining the benefits that are aligned to the Clients’ stated requirements. Making the Data ‘sing’ – memorable takeaways for the Client. Augmented benefits – Brand confidence; Case studies; Warranty; Service; Range; Flexibility etc. in alignment with their stated preferences/requirements Differentials compared to Competitors Section Six – Winning Commitment Inviting commitment – with confidence Consultative Selling Closing techniques (e.g. Alternative Close/Assumptive Close et al) Avoiding ‘talking through the sale’ – knowing when to ‘Shut UP!’ Confirming agreement – ensuring Clients’ motivation for repeat business Section Seven – Practical Application ‘Real Play’ From the Research findings, carefully devised scenarios can be generated to provide the most valuable learning opportunities to underpin all the skills & techniques covered in the Programme. Potential Real Play scenarios: A well-established customer has indicated that they are soon to be opening up additional new offices – this presents an opportunity to arrange for the Company to support them with their upcoming needs. After some very positive feedback and with the upcoming contract renewal imminent – how can the Company give the Customer more high-quality support in other areas of their business? A Competitor has been to see the client and they have prompted some concerns about ‘value for money’ & ‘quality of service’. How Real Play works… The group is split the group into 2 sub-groups, one with our Professional Actor (option available); the other with the Trainer or a willing Participant. Each group has a brief and has to instruct their Trainer/Actor/Participant on how to approach the scenario supplied. The Actor and Trainer (or willing Participant) perform the role play(s) as instructed by their respective teams; however, during the action they can be paused for further recommendations or direction. The outcome is the responsibility of the team(s) – not the performers. Debrief the full Programme Individual Action Plans - to be followed through. ‘Best Practices’ for application into the business Options for Exercises within the Programme Sample Exercise – Red & White There is a specific time managed agenda and itinerary, which puts the group under pressure. The key challenge is for the sub-groups to maximise the commercial value from the task, however there is always a great danger that the individuals attempt to gain financial progress at the expense of the other group! Debriefing points: Persuasive communication and influence across barriers Gaining buy-in when others are sceptical Strategic planning accounting for others’ behaviours Sample Exercise – Communication Challenge Each Participant has different pieces of information, but are not allowed to share it visually. They are only allowed to communicate to work out the solution hidden among the large amount of data. Debrief: Structured approach Maintaining focus through distractions/interference Active Listening Controlled communication Sample Exercise – Persuasive emails Sample emails are shared to be critiqued and improved upon to be debriefed: Tone & impact Making the Data ‘sing’ Influential & motivational language Customer centric message. Sample Exercise –Juggling Each Participant has to pass the ‘Customers’ (Juggling balls) carefully through the system with all the other Participants to reach a profitable conclusion Debrief: EQ to read the room and effectively communicate, when the pressure is on Customer focus and adapting to challenges Devising a plan that wins buy-in Overcoming competing ideas to get to ‘best practice’ Consistent commitment, communication and motivational drivers that influenced performance. Sample Exercise –Critical Path The group are provided with 30 x discs and some ‘post-it’ notes. (no pens or pencils are allowed) Their brief is to create a grid shape with the 30 x discs, which will act as ‘stepping stones’ for the ‘Critical Path’ But they have to follow the correct order through the grid from the start to finish, which they will have to work out through ‘trial & error’ All of the team must pass through the ‘Critical Path’ worked out on the grid, observing the constraints, within the time limit. No talking is permitted once they start using the materials Debrief: - Clear communication focussing on the ‘client’s journey’ Planning for challenges Identifying risks and mitigating them Role allocations & support Quality control and disciplines Sample Exercise –Back to Back Each Participant is positioned back-to-back with a partner. They have to work out precisely what the ‘statement’ given to the other person is without looking around. Each person has a different brief. Debrief: - Asking Open Questions Active Listening Accuracy in identifying the objective.

Customer Excellence Training
By Beyond Theory: business training & coaching
leadership management training course customer service training

If you are new to qualitative research or if you want some initial help to engage with the materials appropriately, then this webinar programme is for you. Doing Qualitative Research is a free curated resource we developed that takes researchers through the whole research cycle, not just the analysis. There is a heavy emphasis on what it is like to 'do' qualitative research in a robust, ethical and professional manner, with practical exercises and reflexive tasks suggested throughout. We are running two, one-hour webinars together with asynchronous, self-directed engagement with the course materials, to help a peer-group of researchers work through the resources on the parts of the qualitative research process they need help with. We understand that not everyone needs to cover the same materials and concepts, or at the same pace. In the first station, discussion with your peers and the facilitator, will help you choose which parts of the Doing Qualitative Research course to focus on before the second webinar. The concluding webinar uses group work and discussion for you to additionally practice one of the most important aspects of the qualitative research paradigm; reflexivity. You will identify what you have learned and how this affects what you will do next with your learning and research. The webinars are facilitated by our Qualitative Research Specialist Dr Cathy Gibbons. Cathy has almost 20 years' experience of teaching qualitative methods across a wide spectrum of disciplines within and beyond the social sciences. The session is free, and runs as two 2hr sessions, 2 weeks apart.

SDI 2.0 (Strength Deployment Inventory) : personality profiling
By Beyond Theory: business training & coaching
leadership management training course
