- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
CertNexus Certified Ethical Emerging Technologist (CEET) v1.0
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for This course is designed for technology leaders, solution developers, project managers, organizational decision makers, and other individuals seeking to demonstrate a vendor-neutral, cross-industry understanding of ethics in emerging data-driven technologies, such as AI, robotics, IoT, and data science. This course is also designed for professionals who want to pursue the CertNexus Certification Exam CET-110: Certified Ethical Emerging Technologies. Overview In this course, you will incorporate ethics into data-driven technologies such as AI, IoT, and data science. You will: Describe general concepts, theories, and challenges related to ethics and emerging technologies. Identify ethical risks. Practice ethical reasoning. Identify and mitigate safety and security risks. Identify and mitigate privacy risks. Identify and mitigate fairness and bias risks. Identify and mitigate transparency and explainability risks. Identify and mitigate accountability risks. Build an ethical organization. Develop ethical systems in technology-focused organizations. Mutually reinforcing innovations in computing and engineering are catapulting advances in technological production. From blockchain and artificial intelligence (AI) to gene editing and the Internet of Things (IoT), these advances come with tremendous opportunities for improvement in productivity, efficiency, and human well-being. But as scandals increasingly demonstrate, these advances also introduce new and serious risks of conflict and harm.Technology professionals now face growing demands to identify and mitigate ethical risks to human rights and the environment, as well as to navigate ethical tradeoffs between qualities such as privacy and accuracy, fairness and utility, and safety and accountability. This course provides the tools to identify and manage common ethical risks in the development of emerging data-driven technologies. It distills ethical theory, public regulations, and industry best practices into concrete skills and guidelines needed for the responsible development of digital products and services. By following the course's practical, problems-based approach, learners will become adept at applying theories, principles, frameworks, and techniques in their own roles and organizations. Introduction to Ethics of Emerging Technologies Topic A: What?s at Stake Topic B: Ethics and Why It Matters Topic C: Ethical Decision-Making in Practice Topic D: Causes of Ethical Failures Identifying Ethical Risks Topic A: Ethical Reasons Topic B: Stumbling Blocks for Ethical Reasoning Topic C: Identify Ethical Risks in Product Development Topic D: Tools for Identifying Ethical Risks Topic E: Use Regulations, Standards, and Human Rights to Identify Ethical Risks Ethical Reasoning in Practice Topic A: Ethical Theories Topic B: Use Ethical Decision-Making Frameworks Topic C: Select Options for Action Topic D: Avoid Problems in Ethical Decision-Making Identifying and Mitigating Security Risks Topic A: What Is Security? Topic B: Identify Security Risks Topic C: Security Tradeoffs Topic D: Mitigate Security Risks Identifying and Mitigating Privacy Risks Topic A: What Is Privacy? Topic B: Identify Privacy Risks Topic C: Privacy Tradeoffs Topic D: Mitigate Privacy Risks Identifying and Mitigating Fairness and Bias Risks Topic A: What Are Fairness and Bias? Topic B: Identify Bias Risks Topic C: Fairness Tradeoffs Topic D: Mitigate Bias Risks Identifying and Mitigating Transparency and Explainability Risks Topic A: What Are Transparency and Explainability? Topic B: Identify Transparency and Explainability Risks Topic C: Transparency and Explainability Tradeoffs Topic D: Mitigate Transparency and Explainability Risks Identifying and Mitigating Accountability Risks Topic A: What Is Accountability? Topic B: Identify Accountability Risks Topic C: Accountability Tradeoffs Topic D: Mitigate Accountability Risks Building an Ethical Organization Topic A: What Are Ethical Organizations? Topic B: Organizational Purpose Topic C: Ethics Awareness Topic D: Develop Professional Ethics within Organizations Developing Ethical Systems in Technology-Focused Organizations Topic A: Policy and Compliance Topic B: Metrics and Monitoring Topic C: Communication and Stakeholder Engagement Topic D: Ethical Leadership

Symantec ProxySG 6.6 Advanced Administration (BCCPP)
By Nexus Human
Duration 2 Days 12 CPD hours This course is intended for This course is for IT network or security professionals who have practical experience with the ProxySG in the field and wish to master the advanced network security of the ProxySG. Overview Solve common authentication and SSL issuesUnderstand the underlying architecture of SGOSMonitor and analyze ProxySG performanceUse policy tracing as a troubleshooting tool The ProxySG 6.6 Advanced Administration course is intended for IT professionals who wish to learn to master the advanced features of the ProxySG. Using Authentication Realms Describe the benefits of enabling authentication on the ProxySG Describe, at a high level, the ProxySG authentication architecture Understand the use of IWA realms, with both IWA Direct and IWA BCAAA connection methods Understanding Authentication Credentials Describe how NTLM and Kerberos authentication work in both IWA direct and IWA BCAAA deployments Configure the ProxySG to use Kerberos authentication Understanding Authentication Modes Describe authentication surrogates and authentication modes Describe ProxySG authentication in both explicit and transparent deployment mode Understanding HTTPS Describe key components of SSL encryption Describe how the SSL handshake works Describe some of the legal and security considerations related to use of the SSL proxy Managing SSL Traffic on the ProxySG Describe how the SSL proxy service handles SSL traffic Describe the standard keyrings that are installed by default on the ProxySG Identify the types of security certificates that the ProxySG uses Optimizing SSL Interception Performance Configure the ProxySG to process SSL traffic according to best practices for performance SGOS Architecture Identify key components of SGOS Explain the interaction among client workers and software workers in processing client requests Explain the significance of policy checkpoints Describe key characteristics of the SGOS storage subsystem Explain the caching behavior of the ProxySG Caching Architecture Describe the benefits of object caching on the ProxySG Explain the caching-related steps in a ProxySG transaction Identify and describe the HTTP request and response headers related to caching Describe, in general terms, how the ProxySG validates cached objects to ensure freshness Explain how the ProxySG uses cost-based deletion, popularity contests, and pipelining to improve object caching System Diagnostics Describe the use of the health monitor and health checks Explain the use of the event and access logs Describe the information available in advanced URLs and sysinfo files Describe the function of policy tracing and packet captures Introduction to Content Policy Language (CPL) Describe the fundamental concepts and purposes of ProxySG policy transactions Understand the relationship of layers, rules, conditions, properties, and triggers Describe the two types of actions in CPL Describe how to write, edit, and upload CPL code Using Policy Tracing for Troubleshooting Identify the two main types of ProxySG policy traces Describe the various sections of a policy trace result Configure a global and policy-driven trace Access and interpret policy trace results ProxySG Integration Identify other Symantec products that can be used as part of a complete security solution

Cisco Implementing and Troubleshooting Networks Using Cisco ThousandEyes v1.0 (ENTEIT)
By Nexus Human
Duration 3 Days 18 CPD hours This course is intended for This course is intended for: Network administrators Network engineers Network managers System engineers Overview After taking this course, you should be able to: Describe the Cisco ThousandEyes solution and its high-level use cases Identify different types of ThousandEyes agents and supported tests Describe different Enterprise Agent deployment options, requirements, and procedures for agent deployment Describe different ThousandEyes test types Compare Thousand Eyes web layer tests Describe the role of an Endpoint Agent Deploy and Configure an Endpoint Agent Utilize ThousandEyes when performing the root cause analysis Discuss the challenges that ThousandEyes Internet Insights can address Describe the role and configuration of default and custom alerts Distinguish between usability of dashboards and reports Utilize ThousandEyes to monitor solutions end-to-end Describe how to perform system administration The Implementing and Troubleshooting Networks Using Cisco ThousandEyes (ENTEIT) v1.0 course is designed to introduce you to and familiarize you with Cisco© ThousandEyes. Through a combination of lectures and hands-on experience, you will learn to implement and configure the Cisco ThousandEyes solution. You will also learn to install and configure the Cisco ThousandEyes agents with different test types. This solution will also enable you to perform root cause analysis when troubleshooting. Course Outline Introducing Cisco ThousandEyes Introducing Cisco ThousandEyes Agents and Tests Deploying Enterprise Agents Describing ThousandEyes Routing, Network DNS, and Voice Tests Describing Cisco ThousandEyes Web Tests Introducing Endpoint Agents Deploying Endpoint Agents Troubleshooting with Cisco ThousandEyes Using Internet Insights Configuring Alerts Customizing Dashboards and Reports Monitoring Solutions Administrating the System

ICCC-CT-Installing and Configuring Cisco Cube/Gateways
By Nexus Human
Duration 3 Days 18 CPD hours This course is intended for The primary audience for this course is as follows: Network Video Engineer Voice/UC/Collaboration/Communications Engineer Collaboration Tools Engineer Collaboration Sales/Systems Engineer In this 3 Day Cisco Course, students will learn how to deploy Voice Gateways/CUBE and setup Cisco Unified Communication Manager (CUCM) to deploy SIP Trunking. The course starts out with an overview of Cisco gateways and their uses. Next, students learn about MGCP and SIP and how to implement each protocol. Students will then learn how to use Cisco CUBE to connect CUCM, Gateways and Service Providers together. This course details how to connect a Cisco environment to a Service Provider using a Cisco CUBE. Introduction to Voice Gateways Cisco UC Networks and the Role of Gateways Gateway Call Routing and Call Legs Configuring Gateway Voice Ports DSP Functionality, Codecs, and Codec Complexity Router Requirements for CUBE SIP Protocol Overview Gateway Dial Plans VoIP Call Legs Dial Plan Implementation Configuring (CUCM) Cisco Unified Communication Manager 12.5 Cisco UCM Audio Codec Preference List Cisco UCM Region Configuration Device Pool Configuration Annunciator Configuration Conference Bridge Configuration Media Termination Point Configuration Music on Hold Server Configuration Music on Hold Service (IP Voice Media Streaming App) Parameter Settings Music on Hold Service (Duplex Streaming) Parameter Settings Media Resource Group Configuration Media Resource Group List Configuration UC Service Configuration Service Profile Configuration End User Configuration SIP Trunk Security Profile Configuration used by SIP trunk to Cisco UBE SIP Profile Configuration used by SIP trunk to Cisco UBE SIP Trunk to Cisco UBE Configuration Route Pattern Configuration Configuring Cisco Unified Border Element (CUBE) Deploying Cisco VCUBE CUCM to CUBE Integration Configuration Steps to connecting to a SIP Trunk Provider Interworking Security and Call Admission Control Media Manipulation, Enhancement & Optimization SIP UA Translation Rules VoIP Dial Peer SIP Registration SIP attributes of CUBE Transcoding services Creating and configuring Sip Trunks CUBE Configuration CUBE Call Flow CUBE Dial-Peers Call Routing CUBE Advanced Call Routing Media Manipulation External/PSTN Call Recording Call Admission Control Multiple Non-Authenticated SIP Trunks on a CUBE Multiple Authenticated/Registered SIP Trunks on a CUBE Configuring High Availability High availability on ISR G2 High availability on ISR 4k High availability on ASR Cisco Unified Border Element (CUBE) Security Five Layers of Security in CUBE SIP TLS Support with SRTP Monitoring and Troubleshooting Cisco CUBE Dialed Number Analyzer (DNA) for CUBE SIP Profile Test Tool Troubleshooting Serviceability

Cisco Unified Contact Center Enterprise Administration v11.5 (UCCE-A)
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for The primary audience for this course is as follows: • Cisco Unified Communications system channel partners and resellers who are responsible for sales, implementation or administration of a Cisco Unified Contact Center. • System and technical support engineers. • Day 1 and Day 2 support personnel. • Administrative and reporting personnel. Overview Upon completing this course, the learner will be able to meet these overall objectives: • Understand the Cisco Unified CCE solution, architecture, solution options, integrated features, and call flow options. • Understand basic principles and configuration requirements for ACD activity in Cisco Unified CM, Cisco Unified CVP, ICM, and how to access and use the Cisco Finesse Agent Desktop. • Understand requirements and configurations to implement IVR activity in Cisco Unified CVP. • Understand and use administrative features and functions of ICM and implement more complex routing to include Precision Routing, routing from Cisco Unified Communications Manager and routing in a ring-no-answer condition. • Understand basic concepts and terms to access, view, modify reports and use other reporting functions provided by Cisco Unified Intelligence Center. Helps prepare learners to administer the Cisco Unified CCE v11.5 solution. Cisco Unified Contact Center Enterprise Overview Lesson 1: Presenting Cisco Unified Contact Center Enterprise Lesson 2: Cisco Unified CCE Core Components Lesson 3: Cisco Unified CCE Options Lesson 4: Basic Call Flow Models Basic ACD Configurations Lesson 1: Configuring Cisco Unified Communications Manager Lesson 2: Configuring Cisco Unified CVP Lesson 3: Configuring Cisco Unified CCE Lesson 4: Using Cisco Finesse Lesson 5: Using Cisco Unified CCE Script Editor Configuring Cisco Unified CVP for IVR Functionality Lesson 1: Basic IVR Configurations Lesson 2: Basic IVR Scripting using CVP Micro-Applications Extended Functions Lesson 1: ICM User Accounts and Feature Control Sets Lesson 2: Using ICM Utilities Lesson 3: Understanding ICM Variables Lesson 4: Precision Routing Lesson 5: Routing Calls from Cisco Unified CM Lesson 6: Ring-No-Answer Routing Cisco Unified CCE Reporting Lesson 1: Introducing Cisco Unified Intelligence Center Lesson 2: Running and Modifying CUIC Reports Lesson 3: Creating CUIC Reports and Dashboards

Cisco Administering Cisco Contact Center Enterprise (CCEA)
By Nexus Human
Duration 4 Days 24 CPD hours This course is intended for Account and project managers Contact Center Enterprise (CCE) administrators Deployment engineers Technical sales Overview After taking this course, you should be able to: Navigate CCE configuration and scripting tools Configure a dialed number, call type, and media routing domain Build a basic Cisco Intelligent Contact Management (ICM) script Configure agents and skill groups Configure basic Interactive Voice Response (IVR) functionality Implement attributes and precision queues Configure Ring-No-Answer (RONA) using CCE configuration tools Configure and populate an agent team and primary supervisor Improve agent efficiency through finesse enhancements Build and test a basic Voice XML (VXML) application Implement roles, departments, and business hours Run Cisco Unified Intelligence Center (CUIC) reports using the Reporting tool The Administering Cisco Contact Center Enterprise (CCEA) v1.0 course teaches you the contextual information around call flow between components in the Cisco© Unified Contact Center Enterprise (UCCE) solution including intelligent contact routing, call treatment, network-to-desktop Computer Telephony Integration (CTI), and multichannel contact management over an IP infrastructure. You receive hands-on practice using administrative tools to perform routine adds, moves, and changes in an inbound contact center environment. Cisco Unified Contact Center Review Contact Center Basics Components and Architecture Deploying Basic Call Settings Associate Basic Call Settings Explore Media Routing Domains Building a Basic Cisco Unified Contact Center Enterprise Script Introduce Script Editor Use Script Editor Nodes Configuring Basic Agent Functionality Introduce Agent Functionality Configure Agent Desk Settings Configuring Basic Call Treatment and Queuing Explore Media Server and Files Introduce Microapps Implementing Precision Routing Introduce Precision Routing Basics Examine the Migration Path Configuring RONA Support Introduce RONA Functionality Identify RONA Timeout Considerations Configuring Agent Teams and Supervisors Configuring Teams and Supervisors Explore Agent Roles Administering the Cisco Finesse Desktop Administering Cisco Finesse Desktop Introduce Cisco Finesse Administration Implementing Voice XML Applications Introduce VXML Build a Basic Call Studio Project Configuring Roles, Departments, and Business Hours Examine Post-Call Survey Functionality Configure Post-Call Survey Running Unified CC Enterprise Reports with Unified Intelligence Center (IC) Configure Unified CC Enterprise Administrators Configure Departments

Cisco Unified Contact Center Enterprise Deployment v11.5 (UCCE-D)
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for The primary audience for this course is as follows: Cisco Unified Communications system channel partners and resellers. System and technical support engineers. Customers who are deploying and maintaining Cisco Unified CCE solution products. Overview Upon completing this course, the learner will be able to meet these overall objectives: Understand CCE solutions, architecture, solution options, deployment models, integrated features and call flow options. Understand underlying Cisco Unified CCE processes, messaging and fault tolerance schemes. Install, upgrade and make basic configurations in Cisco Unified Communications Manager. Install, create databases, integrate, and upgrade all ICM components to include the ICM Router, Logger, Administration & Data Server, Peripheral Gateways, CTI Gateway and Cisco Finesse. Install, integrate, configure, and upgrade Cisco Unified CVP components to include the CVP Call Server, Voice XML Server, Media Server, Reporting Server and Cisco VVB. Install, upgrade, and make configurations for Cisco Unified Intelligence Center and Cisco Outbound Option Agent- and IVR-based campaigns. This course will provide the student with the underlying knowledge to understand deployment design solutions, requirements for deployment, and how to install and configure all major Cisco Unified CCE components. As a part of deployment activities, the student will understand how to install and integrate Intelligent Contact Manager (ICM) with Active Directory, how to install and integrate Cisco Unified CVP components using an IOS-based voice browser and Cisco Virtualized Voice Browser (Cisco VVB), how to install and integrate Cisco Finesse, how to install and integrate Cisco Unified Intelligence Center with Active Directory and associated Data Sources for reporting purposes, and how to install and configure Agent- and IVR-based Outbound Option dialing campaigns. And finally, the student will learn how to setup and use troubleshooting tools including RTMT, System CLI, Diagnostic Framework, and ICM command-line utilities to find status information and log files, and to track a call from the point of entry to the agent desktop. Cisco Unified Contact Center Enterprise Overview Lesson 1: Presenting Cisco Unified Contact Center Enterprise Lesson 2: Cisco Unified CCE Core Components Lesson 3: Cisco Unified CCE Options Lesson 4: Basic Call Flow Models Cisco Unified CCE Protocols, Processes and Services Lesson 1: Cisco Unified CM Lesson 2: Cisco Unified CCE/Intelligent Contact Manager Lesson 3: Cisco Unified CVP Installing Cisco Unified Communications Manager Lesson 1: Installation Prerequisites Lesson 2: Cisco Unified CM Installation Lesson 3: Post-installation Configurations Lesson 4: Creating Basic Infrastructure Lesson 5: Upgrading Cisco Unified CM Installing Intelligent Contact Manager Lesson 1: Installation Requirements Lesson 2: Pre-installation Tasks Lesson 3: Install the Main Installer Lesson 4: Install the Central Controller ?Lesson 5: Install the Administration and Data Server Lesson 6: Install the Peripheral Gateway Lesson 7: Install CTI Services Installing Cisco Unified CVP Lesson 1: Installation Prerequisites Lesson 2: Install the CVP Server Lesson 3: Configure Cisco Unified CVP Components Lesson 4: Upgrading Cisco Unified CVP Upgrade Path Installing and Configuring Cisco Unified CCE Options Lesson 1: Cisco Outbound Option Lesson 2: Cisco Unified Intelligence Center Supporting Cisco Unified CCE Lesson 1: Maintenance Activities Lesson 2: UCCE Troubleshooting Tools

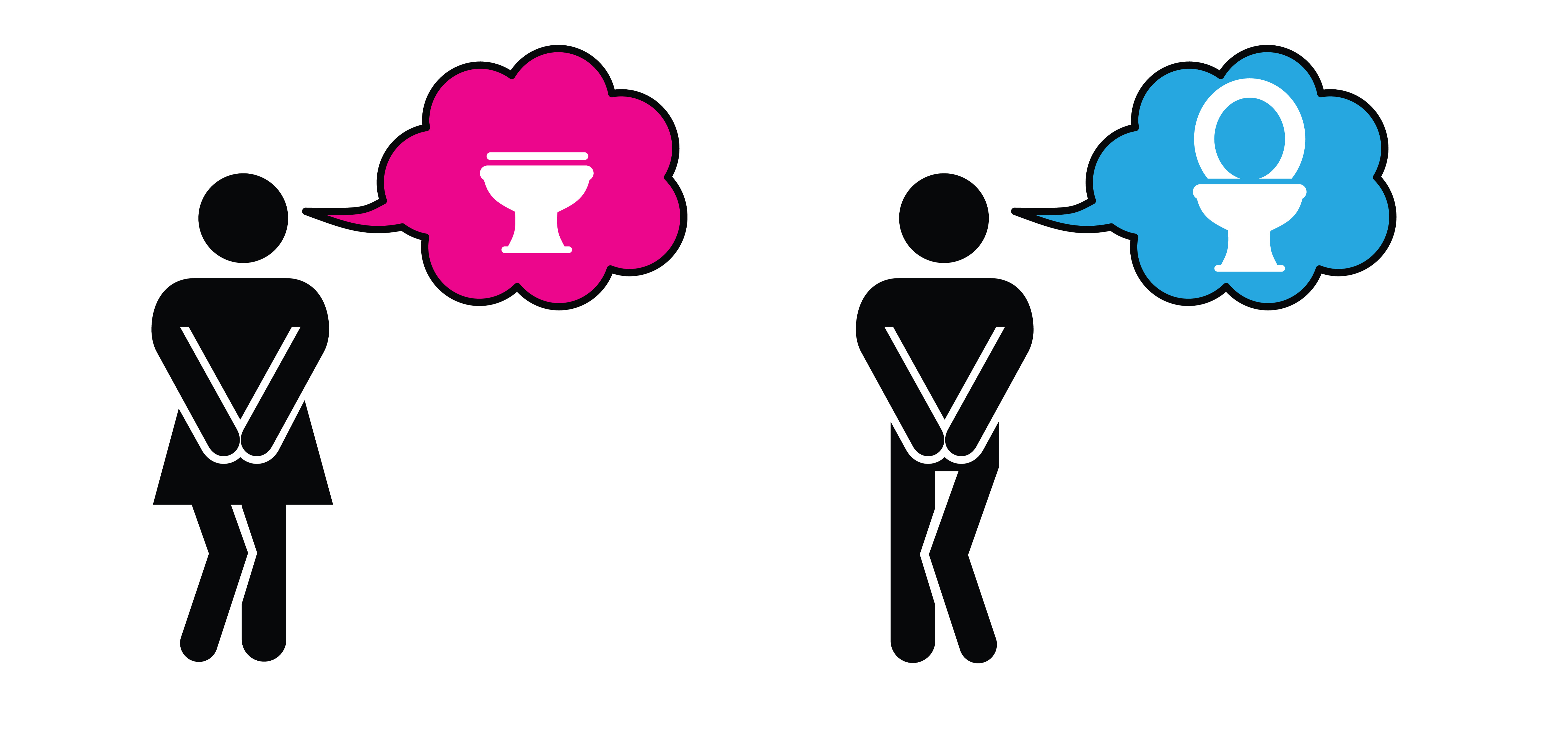
Continence Awareness & Promotion
By Prima Cura Training
This course is developed for care staff and volunteers to raise awareness of the causes of incontinence, the use of continence aids and promotion of good practice.
Mastery: How to Make It Happen? Take Charge over Life Changes.
By believe-IN. Make It Happen!®
believe-IN Webinar Series: Plan the Way Out of Life Changes Webinar 4 – Mastery: How to Make It Happen? Take Charge over Life Changes.

Equilibrium: The Chance for a Better Future. Life Changes, a wealth of opportunities.
By believe-IN. Make It Happen!®
believe-IN Webinar Series: Plan the Way Out of Life Changes Webinar 2: Equilibrium: The Chance for a Better Future. Life Changes, a wealth of opportunities.
