- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
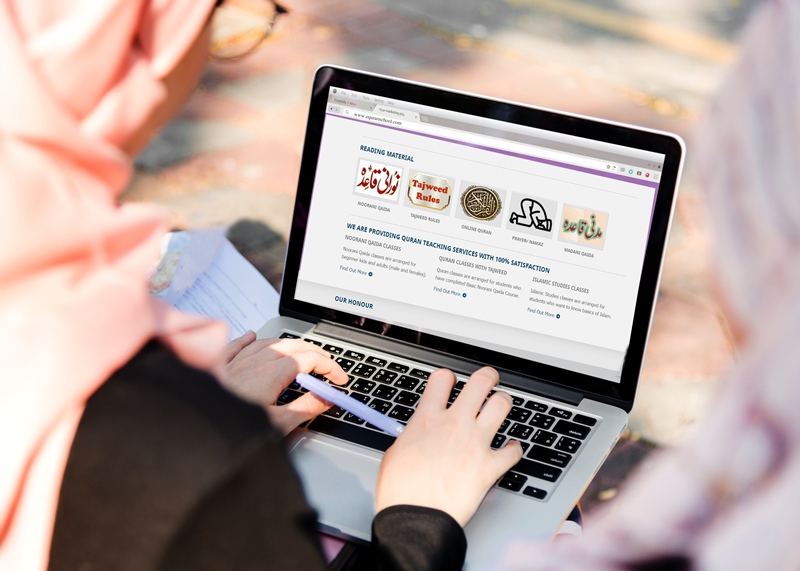
Online Quran Classes For Kids and Adults
By Quran Assistant
Learn Quran Online at your convince time
Embark on a transformative journey with our course, 'Applied Behaviour Analysis (ABA) for Autism Spectrum Disorders.' This program is your gateway to understanding and applying the potent principles of ABA to empower individuals with Autism Spectrum Disorder (ASD). Dive into a world where compassion meets science, and learn how to make a profound impact on the lives of those affected by ASD. Our immersive curriculum guides you through every facet of ABA, equipping you with the skills and knowledge to bring about positive change. In this course, you'll start with an in-depth exploration of ASD, gaining insight into its nuances and challenges. As you progress, you'll master the foundational elements of ABA, learning to assess, evaluate, and develop effective behavioural strategies. Discover how to nurture skill acquisition while addressing challenging behaviours, and witness the remarkable transformations that result. Whether you aspire to be a practitioner, educator, or advocate, this course is your conduit to making a real difference in the world of ASD. Learning Outcomes Comprehend the intricacies of Autism Spectrum Disorder (ASD) and its impact on individuals and their families. Proficiently apply the foundational principles of Applied Behaviour Analysis (ABA) to design effective interventions. Conduct comprehensive assessments and evaluations to tailor ABA strategies to individual needs. Implement behavioural techniques to facilitate skill acquisition, fostering independence and development. Employ ABA interventions to address and reduce challenging behaviours, improving the quality of life for individuals with ASD. Why buy this Applied Behaviour Analysis (ABA) for Autism Spectrum Disorders? Unlimited access to the course for a lifetime. Opportunity to earn a certificate accredited by the CPD Quality Standards and CIQ after completing this course. Structured lesson planning in line with industry standards. Immerse yourself in innovative and captivating course materials and activities. Assessments designed to evaluate advanced cognitive abilities and skill proficiency. Flexibility to complete the Course at your own pace, on your own schedule. Receive full tutor support throughout the week, from Monday to Friday, to enhance your learning experience. Unlock career resources for CV improvement, interview readiness, and job success Who is this Applied Behaviour Analysis (ABA) for Autism Spectrum Disorders for? Aspiring Behaviour Analysts and Therapists Educators and Special Education Professionals Parents and Caregivers of Individuals with ASD Healthcare and Mental Health Practitioners Advocates and Anyone Passionate About Making a Difference. Career path Behaviour Analyst: £30,000 - £60,000 Special Education Teacher: £25,000 - £45,000 Speech and Language Therapist: £30,000 - £50,000 Clinical Psychologist: £35,000 - £70,000 Autism Support Specialist: £25,000 - £45,000 School Counselor: £30,000 - £50,000 Prerequisites This Applied Behaviour Analysis (ABA) for Autism Spectrum Disorders does not require you to have any prior qualifications or experience. You can just enrol and start learning. This course was made by professionals and it is compatible with all PC's, Mac's, tablets and smartphones. You will be able to access the course from anywhere at any time as long as you have a good enough internet connection. Certification After studying the course materials, there will be a written assignment test which you can take at the end of the course. After successfully passing the test you will be able to claim the pdf certificate for £4.99 Original Hard Copy certificates need to be ordered at an additional cost of £8. Course Curriculum Module 1: Introduction to Autism Spectrum Disorder (ASD) Introduction to Autism Spectrum Disorder (ASD) 00:19:00 Module 2: Foundations of Applied Behavior Analysis (ABA) Foundations of Applied Behavior Analysis (ABA) 00:19:00 Module 3: Assessment and Evaluation in ABA Assessment and Evaluation in ABA 00:20:00 Module 4: Behavioural Strategies for Skill Acquisition Behavioural Strategies for Skill Acquisition 00:20:00 Module 5: Behavioural Strategies for Reducing Challenging Behaviours Behavioural Strategies for Reducing Challenging Behaviours 00:15:00 Module 6: ABA Interventions for Communication and Social Skills ABA Interventions for Communication and Social Skills 00:15:00 Module 7: ABA Interventions for Daily Living and Self-Help Skills ABA Interventions for Daily Living and Self-Help Skills 00:16:00 Module 8: Transitioning and Maintenance of ABA Interventions Transitioning and Maintenance of ABA Interventions 00:19:00

Dive into the dynamic realm of property with the Real Estate Certificate. This comprehensive course unveils the intricacies of this sector, starting with a foundational introduction, swiftly moving into the core roles and responsibilities of estate agents. Discover the distinctions among various agent types, master the art of property listing, and grasp the pivotal valuation processes. The curriculum culminates with advanced modules dedicated to negotiation techniques, selling and letting properties, and embracing the latest technology tailored for estate agents. Learning Outcomes Understand the foundational concepts and terminologies related to real estate. Differentiate between diverse types of estate agents and their roles. Master the steps involved in property listing and the valuation procedure. Develop effective negotiation strategies specific to this industry. Gain insights into selling, letting properties and utilising technology optimally in the estate sector. Why buy this Real Estate Certificate? Unlimited access to the course for a lifetime. Opportunity to earn a certificate accredited by the CPD Quality Standards and CIQ after completing this course. Structured lesson planning in line with industry standards. Immerse yourself in innovative and captivating course materials and activities. Assessments designed to evaluate advanced cognitive abilities and skill proficiency. Flexibility to complete the course at your own pace, on your own schedule. Receive full tutor support throughout the week, from Monday to Friday, to enhance your learning experience. Unlock career resources for CV improvement, interview readiness, and job success. Who is this Real Estate Certificate for? Individuals aspiring to embark on a real estate career. Current estate agents aiming to upskill and stay abreast of industry changes. Property enthusiasts wanting an in-depth understanding of estate agency operations. Those interested in mastering property negotiation techniques. Tech-savvy individuals keen to integrate technology into real-estate practices. Career path Real Estate Agent: £20,000 - £60,000 Property Valuer: £25,000 - £50,000 Property Negotiator: £22,000 - £45,000 Property Listing Specialist: £20,000 - £55,000 Letting Agent: £18,000 - £45,000 Prerequisites This Real Estate Certificate does not require you to have any prior qualifications or experience. You can just enrol and start learning. This course was made by professionals and it is compatible with all PC's, Mac's, tablets and smartphones. You will be able to access the course from anywhere at any time as long as you have a good enough internet connection. Certification After studying the course materials, there will be a written assignment test which you can take at the end of the course. After successfully passing the test you will be able to claim the pdf certificate for £4.99 Original Hard Copy certificates need to be ordered at an additional cost of £8. Course Curriculum Module 01: Introduction to Real Estate Introduction to Real Estate 00:07:00 Module 02: Basics of Estate Agent Basics of Estate Agent 00:09:00 Module 03: Different Types of Estate Agents Different Types of Estate Agents 00:09:00 Module 04: Getting Started on the Job Getting Started on the Job 00:08:00 Module 05: Listing Property Listing Property 00:15:00 Module 06: Valuation Process Valuation Process 00:11:00 Module 07: Negotiating as an Estate Agent Negotiating as an Estate Agent 00:08:00 Module 08: Selling Property: Finding the Buyers Selling Property: Finding the Buyers 00:14:00 Module 09: Letting Property Letting Property 00:17:00 Module 10: Technology for Estate Agents Technology for Estate Agents 00:13:00

Venture into the heart of food safety with the 'HACCP Course,' a meticulously crafted guide that sheds light on each aspect of the Hazard Analysis and Critical Control Points system. Walk with us through the thoroughfares of this globally recognized approach, where each module introduces you to critical elements, from its foundational principles to the implementation of a full-fledged HACCP system. In a world where food safety is paramount, this course promises not just knowledge, but the empowerment to set standards and maintain them with unparalleled finesse. Learning Outcomes Grasp the foundational concepts and importance of HACCP in food safety. Understand and identify food safety hazards and their implications. Develop the expertise to plan and create a comprehensive HACCP system. Dive deep into the seven principles of HACCP and their significance. Master the intricacies of implementing, verifying, and documenting the HACCP system. Why choose this HACCP Course? Unlimited access to the course for a lifetime. Opportunity to earn a certificate accredited by the CPD Quality Standards after completing this course. Structured lesson planning in line with industry standards. Immerse yourself in innovative and captivating course materials and activities. Assessments are designed to evaluate advanced cognitive abilities and skill proficiency. Flexibility to complete the HACCP Course Course at your own pace, on your own schedule. Receive full tutor support throughout the week, from Monday to Friday, to enhance your learning experience. Who is this Freestyle HACCP Course for? Individuals aspiring to be food safety professionals. Current food and beverage managers and supervisors. Quality assurance personnel in the food industry. Food business owners and entrepreneurs. Food safety auditors and consultants. Career path HACCP Coordinator: £25,000 - £35,000 Food Safety Auditor: £28,000 - £40,000 Quality Assurance Manager: £35,000 - £55,000 Food Safety Officer: £24,000 - £37,000 HACCP Trainer: £30,000 - £45,000 Quality Control Supervisor: £27,000 - £42,000 Prerequisites This HACCP Course does not require you to have any prior qualifications or experience. You can just enrol and start learning.This HACCP Course was made by professionals and it is compatible with all PC's, Mac's, tablets and smartphones. You will be able to access the course from anywhere at any time as long as you have a good enough internet connection. Certification After studying the course materials, there will be a written assignment test which you can take at the end of the course. After successfully passing the test you will be able to claim the pdf certificate for £4.99 Original Hard Copy certificates need to be ordered at an additional cost of £8. Course Curriculum HACCP Course Module 01: An Introduction to HACCP 00:15:00 Module 02: HACCP and Food Safety Legislation 00:25:00 Module 03: Food Safety Hazards 01:00:00 Module 04: Planning a HACCP System 00:40:00 Module 05: Creating the HACCP System 00:20:00 Module 06: Principle 1: Hazard Analysis 00:15:00 Module 07: Principle 2: Critical Control Points 00:12:00 Module 08: Principle 3: Critical Limits 00:20:00 Module 09: Principle 4: Monitoring Critical Control Points 00:20:00 Module 10: Principle 5: Corrective Action 00:25:00 Module 11: Principle 6: Verification of the HACCP System 00:30:00 Module 12: Principle 7: Documentation 00:16:00 Module 13: Implementing the HACCP System 00:12:00 Module 14: HACCP Alternatives 00:15:00 Mock Exam Mock Exam - HACCP Course 00:20:00 Final Exam Final Exam - HACCP Course 00:20:00

Delve deep into the transformative world of 'Schema Psychotherapy for BPD (Borderline Personality Disorder)' and uncover the intricacies of this powerful therapeutic approach. This course will illuminate the nuances of Schema Therapy, from establishing a robust therapeutic relationship to mastering diverse techniques tailored for each mode. As you journey through the curriculum, you'll not only gain insight into treatment planning but also understand the essence of both cognitive and behavioural methods, culminating in the graceful ending of therapy. Learning Outcomes Comprehend the foundational principles of Schema Therapy in treating BPD. Formulate effective treatment plans aligned with the needs of BPD patients. Develop a deep understanding of the therapeutic relationship and its significance in healing. Acquire proficiency in a range of techniques, including cognitive, experiential, and behavioural. Recognise the intricacies of specific techniques for each mode and their application in therapy. Why buy this Schema Psychotherapy for BPD (Borderline Personality Disorder) course? Unlimited access to the course for forever Digital Certificate, Transcript, student ID all included in the price Absolutely no hidden fees Directly receive CPD accredited qualifications after course completion Receive one to one assistance on every weekday from professionals Immediately receive the PDF certificate after passing Receive the original copies of your certificate and transcript on the next working day Easily learn the skills and knowledge from the comfort of your home Certification After studying the course materials of the Schema Psychotherapy for BPD (Borderline Personality Disorder) there will be a written assignment test which you can take either during or at the end of the course. After successfully passing the test you will be able to claim the pdf certificate for £5.99. Original Hard Copy certificates need to be ordered at an additional cost of £9.60. Who is this Schema Psychotherapy for BPD (Borderline Personality Disorder) course for? Mental health professionals looking to expand their therapeutic toolkit. Psychology students eager to explore niche areas in psychotherapy. Counsellors aiming to deepen their expertise in BPD treatments. Therapists desiring to refine their approach to diverse modes in therapy. Individuals passionate about understanding the BPD spectrum and aiding recovery. Prerequisites This Schema Psychotherapy for BPD (Borderline Personality Disorder) does not require you to have any prior qualifications or experience. You can just enrol and start learning.This Schema Psychotherapy for BPD (Borderline Personality Disorder) was made by professionals and it is compatible with all PC's, Mac's, tablets and smartphones. You will be able to access the course from anywhere at any time as long as you have a good enough internet connection. Career path Clinical Psychologist: £40,000 - £70,000 Psychotherapist: £30,000 - £50,000 Mental Health Counsellor: £23,000 - £40,000 BPD Specialist: £35,000 - £60,000 Therapy Consultant: £45,000 - £80,000 Cognitive Behavioural Therapist: £26,000 - £47,000 Course Curriculum Course Introduction Introduction 00:05:00 Comorbidity and Prevalence 00:04:00 Development 00:04:00 Schema Therapy for BPD Disorder Treatment of personality disorders with cognitive behavioural therapy 00:02:00 Development of schema therapy 00:02:00 Comorbidity of disorders 00:01:00 The rationale for schema therapy 00:06:00 5 modes of characteristics 00:17:00 Treatment Plan Structure of Treatment 00:05:00 Phases of treatment 00:10:00 The Therapeutic Relationship Important elements of the therapeutic relationship 00:04:00 Therapist's schemas 00:14:00 Experiential Techniques Imagery 00:18:00 Roleplay 00:10:00 Two-or-more chair technique 00:06:00 Experiencing and expressing emotions 00:05:00 Cognitive Technique Introduction 00:04:00 Cognitive techniques 00:09:00 Behavioural Techniques Behavioural techniques 00:04:00 Specific Techniques for Each Mode Detached protector 00:05:00 Abandoned/abused child 00:04:00 Angry/ impulsive child 00:03:00 Punitive parent 00:04:00 Healthy adult 00:02:00 Ending of the Therapy Ending of the therapy 00:01:00 Downloadable Resources Additional Study Materials 00:00:00

Overview Imagine a journey where every brick and blueprint leads to mastery in construction management. The Level 3 Diploma in Construction offers just that - a comprehensive voyage through building and managing projects with finesse and expertise. This course, meticulously crafted to fuse theory with real-world applications, beckons learners to explore the intricate facets of construction management. From initial site investigations to intricate supply chain management, every module is a stepping stone towards becoming a veteran in this field. Delving deeper, the curriculum is tailored to nurture a profound understanding of various aspects crucial to the field. Learners will encounter modules like Cost Management and Risk and Value Management, essential for making informed decisions in construction projects. As the course progresses, students will encounter a rich tapestry of knowledge, including construction procurement, stock control, and the legal aspects of contracting. This programme isn't just about gaining information; it's an immersive experience of construction companies, construction jobs, and the latest construction news. Furthermore, the course isn't just an academic exercise; it's a beacon for those aspiring to be part of the construction enquirer community. Every lesson is a brushstroke in painting a broader picture of the industry, encompassing elements like quality assurance, customer care, and human resources management. With this diploma, learners are not just studying a subject; they are being sculpted into future leaders of the construction world, equipped to handle challenges with knowledge and confidence. Learning Outcomes Gain a comprehensive understanding of construction management, including site organization and management. Develop skills in cost estimation, and understand the elements and factors influencing these estimates. Acquire knowledge in managing materials, vendor analysis, and procurement processes. Understand the legalities in contracting and learn about quality assurance and customer care in this field. Enhance capabilities in managing risks, values, and human resources within this sector. Why buy this Level 3 Diploma in Construction? Unlimited access to the course for a lifetime. Opportunity to earn a certificate accredited by the CPD Quality Standards and CIQ after completing this course. Structured lesson planning in line with industry standards. Immerse yourself in innovative and captivating course materials and activities. Assessments designed to evaluate advanced cognitive abilities and skill proficiency. Flexibility to complete the Course at your own pace, on your own schedule. Receive full tutor support throughout the week, from Monday to Friday, to enhance your learning experience. Unlock career resources for CV improvement, interview readiness, and job success. Certification After studying the course materials of the Level 3 Diploma in Construction you will be able to take the MCQ test that will assess your knowledge. After successfully passing the test you will be able to claim the pdf certificate for £5.99. Original Hard Copy certificates need to be ordered at an additional cost of £9.60. Who is this Level 3 Diploma in Construction course for? Individuals aiming to build a career in construction management or related fields. Graduates seeking specialized knowledge in this field. Professionals in the construction industry looking to enhance their managerial skills. Entrepreneurs planning to start or manage construction companies. Personnel in procurement, supply chain, or project management within this sector. Prerequisites This Level 3 Diploma in Construction was made by professionals and it is compatible with all PC's, Mac's, tablets and smartphones. You will be able to access the course from anywhere at any time as long as you have a good enough internet connection. Career path Construction Manager: £35,000 - £50,000 annually Site Manager: £30,000 - £45,000 annually Quantity Surveyor: £25,000 - £40,000 annually Procurement Manager: £40,000 - £55,000 annually Health and Safety Manager: £35,000 - £50,000 annually Project Manager: £40,000 - £60,000 annually Course Curriculum Level 3 Diploma in Construction Module 01: Introduction to Construction Management 00:19:00 Module 02: Project Life Cycle and Success 00:28:00 Module 03: Cost Management 00:22:00 Module 04: Preliminary Site Investigation and Site Organisation 00:24:00 Module 05: Site Management 00:19:00 Module 06: Cost Estimation 00:34:00 Module 07: Elements and Factors influencing Cost Estimation 00:16:00 Module 08: Planning and Management of Equipment 00:32:00 Module 09: Construction Materials Management 00:22:00 Module 10: Vendor Analysis in Construction Management 00:24:00 Module 11: Construction Procurement 00:18:00 Module 12: Stock Control 00:22:00 Module 13: Supply Chain Management 00:21:00 Module 14: The Main Participators 00:21:00 Module 15: Quality Assurance and Customer Care 00:21:00 Module 16: Legal Aspects of Contracting 00:19:00 Module 17: Human Resources Management 00:22:00 Module 18: Risk and Value Management 00:21:00 Module 19: Communications, Information and Documentation of Construction 00:24:00 Module 20: Health and Safety in Construction Management 00:24:00

Exercise and fitness (In-House)
By The In House Training Company
Perhaps you struggle to find the time and motivation to fit exercise into your working day? Or you're not sure about what exercise is right for you or how much you should be doing. Take away a set of personal physical activity goals for yourself to improve your fitness levels and general health and wellbeing. During the session we'll discuss: Facts about physical activity and exercise. How much exercise we should be doing to stay fit and healthy vs. how much to improve our fitness levels and strength. What are the components of physical fitness, types of exercise training and benefits of each. How to get started if you're new to exercise and easy ways to incorporate more exercise into your working week (Open discussion to establish the group's current activity levels and tailor advice and ideas) How you can motivate yourself to exercise more Q&A - a chance for the group to ask questions or advice

MHFA Refresher (In-House)
By The In House Training Company
If you are a Mental Health First Aider or MHFA Champion you have skills for life that support you and the people around you. We believe that mental health should be treated equally to physical health - and just like physical first aid, Mental Health First Aid training should be kept up to date. The four-hour MHFA Refresher course will empower you to: Keep your awareness of mental health supports current Update your knowledge of mental health and what influences it Practice applying the Mental Health First Aid action plan Outline About mental health Stress and factors that influence mental health Mental health continuum and stigma Frame of reference and non-judgement Reintroducing ALGEE Warning signs of mental ill-health Depression and anxiety Suicide and first aid for suicidal crisis Psychosis and first aid for severe psychotic episodes Practising our MHFA sills Self-care, wellbeing and recovery

Welcome to a transformative exploration of compassionate care with our Person-centered Practice in Adult Care course. This immersive experience delves into the heart of adult care, unraveling the core principles, theories, and values that underpin person-centered practices. From understanding methodologies for optimal outcomes to ensuring personal well-being, each module is a stepping stone towards becoming an adept practitioner committed to excellence. In this course, we break the conventional to emphasize personal preferences, recognizing the uniqueness of every individual under your care. Upholding good practice isn't just a concept; it's a way of life. Dive into the intricacies of ensuring accountabilities, understanding healthcare protocols, and embracing the pivotal role of a manager in orchestrating a harmonious care environment. Join us on this enlightening journey where person-centered care isn't just a practice; it's a philosophy that transforms both caregivers and those receiving care. Learning Outcomes Grasp the foundational principles, theories, and values of person-centered care. Apply effective methodologies to achieve the best outcomes in adult care. Prioritize personal well-being, fostering holistic development. Honor and integrate personal preferences into care strategies. Uphold and champion good practice, ensuring accountability at every step. Why choose this Person-centered Practice in Adult Care course? Unlimited access to the course for a lifetime. Opportunity to earn a certificate accredited by the CPD Quality Standards and CIQ after completing this course. Structured lesson planning in line with industry standards. Immerse yourself in innovative and captivating course materials and activities. Assessments designed to evaluate advanced cognitive abilities and skill proficiency. Flexibility to complete the Course at your own pace, on your own schedule. Receive full tutor support throughout the week, from Monday to Friday, to enhance your learning experience. Unlock career resources for CV improvement, interview readiness, and job success. Who is this Person-centered Practice in Adult Care course for? Aspiring caregivers looking to enter the field of adult care with a compassionate approach. Current care practitioners seeking to enhance their person-centered care skills. Healthcare professionals expanding their expertise in adult care. Individuals transitioning to adult care management roles. Anyone passionate about fostering a culture of empathy in adult care settings. Career path Person-centered Care Coordinator: £28,000 - £40,000 Adult Care Manager: £32,000 - £48,000 Clinical Care Supervisor: £30,000 - £45,000 Quality Assurance Specialist in Adult Care: £35,000 - £50,000 Health and Well-being Advisor: £28,000 - £42,000 Adult Care Program Developer: £38,000 - £55,000 Prerequisites This Person-centered Practice in Adult Care does not require you to have any prior qualifications or experience. You can just enrol and start learning.This Person-centered Practice in Adult Care was made by professionals and it is compatible with all PC's, Mac's, tablets and smartphones. You will be able to access the course from anywhere at any time as long as you have a good enough internet connection. Certification After studying the course materials, there will be a written assignment test which you can take at the end of the course. After successfully passing the test you will be able to claim the pdf certificate for £4.99 Original Hard Copy certificates need to be ordered at an additional cost of £8. Course Curriculum Module 01: Principles, Theories, and Values Principles, Theories, and Values 00:14:00 Module 02: Methodology for Best Outcomes Methodology for Best Outcomes 00:11:00 Module 03: Personal Well-being and Outcomes Personal Well-being and Outcomes 00:12:00 Module 04: Personal Preferences Personal Preferences 00:14:00 Module 05: Uphold Good Practice Uphold Good Practice 00:13:00 Module 06: Ensuring Accountabilities Ensuring Accountabilities 00:12:00 Module 07: Ensuring Healthcare Protocol Ensuring Healthcare Protocol 00:13:00 Module 08: Role of Manager Role of Manager 00:14:00

The International Law Certificate offers a comprehensive exploration of various aspects of international law, including its basics, sources, human rights, criminal law, treaties, territorial jurisdiction, and more. Participants will gain a solid understanding of the legal frameworks governing international relations and transactions. Learning Outcomes: Understand the foundational principles and basics of international law. Identify and analyze the sources of international law and their significance. Examine the relationship between international law and municipal law systems. Explore the roles and functions of international organizations in shaping global affairs. Gain insights into the international legal framework concerning human rights protection. Study the principles and applications of private international law in cross-border disputes. Familiarize with the principles and scope of international criminal law. Comprehend the legal aspects related to treaties and their significance in international relations. Analyze issues concerning territory and jurisdiction in international law. Understand the legal aspects of the law of the sea and its implications on maritime activities. Explore the legal framework governing international commercial transactions and business. Learn about the legal principles and mechanisms concerning international environmental protection. Why buy this International Law Certificate? Unlimited access to the course for forever Digital Certificate, Transcript, student ID all included in the price Absolutely no hidden fees Directly receive CPD accredited qualifications after course completion Receive one to one assistance on every weekday from professionals Immediately receive the PDF certificate after passing Receive the original copies of your certificate and transcript on the next working day Easily learn the skills and knowledge from the comfort of your home Certification After studying the course materials of the International Law Certificate there will be a written assignment test which you can take either during or at the end of the course. After successfully passing the test you will be able to claim the pdf certificate for £5.99. Original Hard Copy certificates need to be ordered at an additional cost of £9.60. Who is this course for? This International Law Certificate does not require you to have any prior qualifications or experience. You can just enrol and start learning. Prerequisites This International Law Certificate was made by professionals and it is compatible with all PC's, Mac's, tablets and smartphones. You will be able to access the course from anywhere at any time as long as you have a good enough internet connection. Career path As this course comes with multiple courses included as bonus, you will be able to pursue multiple occupations. This International Law Certificate is a great way for you to gain multiple skills from the comfort of your home. Course Curriculum Module 01: Basics of International Law Basics of International Law 00:21:00 Module 02: Sources of International Law Sources of International Law 00:26:00 Module 03: International Law and Municipal Law International Law and Municipal Law 00:14:00 Module 04: International Organisations International Organisations 00:23:00 Module 05: International Law of Human Rights International Law of Human Rights 00:21:00 Module 06: Private International Law Private International Law 00:13:00 Module 07: International Criminal Law International Criminal Law 00:15:00 Module 08: Law of Treaties Law of Treaties 00:15:00 Module 09: Territory and Jurisdiction Territory and Jurisdiction 00:18:00 Module 10: Law of the Sea Law of the Sea 00:24:00 Module 11: International Commercial Law International Commercial Law 00:13:00 Module 12: International Environmental Law International Environmental Law 00:20:00 Assignment Assignment - International Law Certificate 00:00:00
