- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
272 Courses delivered Online
Child care and Development Mega Bundle (12 Courses)
By Training Tale
Healthy and well-prepared children perform better, so the early years of a child's life are vital to their future success. This Child care and Development Mega Bundle (12 Courses) course provides learners with a thorough understanding of the various areas of child care and development. This course includes theoretical training and guidance, making it ideal for teachers, childminders and social care workers. Anyone who works with children must understand their legal responsibilities when it comes to promoting their well-being, and this course covers the key duties involved in child care provision, from safeguarding to child protection. Through this course, you will learn how to identify signs of child abuse and neglect, plan educational play activities, and support children with physical disabilities, special educational, social, and emotional needs. This Child care and Development Mega Bundle (12 Courses) course also includes important information on health and nutrition, child services, and the factors that influence child growth and development, preparing you to build positive relationships with children and provide a nurturing environment in which children feel comfortable. With this course, you will get 15 courses! It means you will get 15 different certificates of achievement once you complete all the courses successfully. This course is fully online and self-paced, so you don't need to worry about timing. You can set your own schedule to continue the courses. Enrol on our Child care and Development Mega Bundle (12 Courses) course and take the first steps toward a successful long-term career. This Child care and Development Mega Bundle (12 Courses) course will enhance your CV, impress potential employers, and stand out from the crowd. At Training Tale, we provide more than just courses, we also provide a rich learning experience. When you purchase a course from Training Tale, you get unlimited access to the course with tutor support. Our expert instructors are always available to answer any questions you may have and make your learning experience enjoyable and memorable. This Child care and Development Mega Bundle (12 Courses)course is ideal for all aspiring Child Care professionals as it is packed with up-to-date Child Care and development knowledge. Let's see what are those 12 courses included in this Child care and Development Mega Bundle (12 Courses)course- Level 4 Child Care and Development Course Diploma in Special Education Needs (SEN) Level 3 Award in Childcare and Education Course Care and support for Vulnerable Children Level 2 Diploma for the Early Years Practitioner Level 2 Certificate in Behaviour that Challenges in Children Nursery Nurse Course Level 2 Safeguarding Children Training Course Level 4 Diploma in Child Psychology Course Level 3 Designated Safeguarding Lead Training Course Primary Teaching Diploma Level 2 Certificate in Understanding Common Childhood Illnesses Affecting Children Learning Outcomes By the end of this Child care and Development Mega Bundle (12 Courses), you will be able to - Gain in-depth knowledge of parenting styles and how they affect a child's development Gain a thorough understanding of developmental theories and psychology of children Understand how children form relationships with others Understand language, emotions, and cognitive development of children Understand whether the career path of 'child psychology' is for you! Understand the main theories in Developmental Psychology Understand children's intentions and behaviour at different ages of life Know why 'unconditional love' is important to the growing baby Gain in-depth about 'The Stages' of a child's development Know how language and linguistic skills develop in children Understand Cognitive Development (mind, subconscious mind, ego) Know how to do parenting for the better development of a child. Knowhow to build self-esteem and confidence in a child. Know how to identify bullying and child abuse and manage it. Know how to identify stress, grief and depression in a child and manage it. Know how to identify separation in a child and manage it. Why Choose Child Care and Development Bundle from Us Self-paced course, access available from anywhere. Easy to understand, high-quality study materials. Course developed by industry experts. MCQ quiz after each module to assess your learning. Automated and instant assessment results. 24/7 support via live chat, phone call or email. Free PDF certificate as soon as completing the course. Others Benefits of Child care and Development Mega Bundle (12 Courses) 12 PDF Certificate Free Expert Tutor Support Lifetime Access Unlimited Retake Exam FREE [ COURSE 01 ] - Level 4 Child Care and Development Module 01: Few Basic Things to Keep in Mind Module 02: Caring for newborn Babies Module 03: Feeding Module 04: Nutrition and Health Module 05: Health Concerns Module 06: First Aid and Emergency Module 07: Raising Mentally Healthy Children Module 08: Sex Education Module 09: Common Developmental and Behavioral Challenges [ COURSE 02 ] - Diploma in Special Education Needs (SEN) Module 01: Introduction Module 02: A Quick Overview of the New SEND Code of Practice Module 03: Legislation Related to SEN Module 04: SEN Assessments and Descriptors Module 05: Education for Children with Disabilities Module 06: Common SEN Conditions Found Within Mainstream Schools Module 07: Assessment and Planning for Children with Special Educational Needs Module 08: The Wider Children's Workforce Associated with Special Education Needs Provisions Module 09: Working with other Professionals and other Sources of Support and Information [ COURSE 03 ] - Level 3 Award in Childcare and Education Module 1: Child Development from Conception to Seven Years Module 2: Children's Health and Wellbeing [ COURSE 04 ] - Care and support for Vulnerable Children Module 01: Introduction Module 02: The Rights of Children Module 03: Understanding the Distinction Between Vulnerability and Risk Module 04: Child in Crisis Module 05: Controlling The Issues Module 06: Available Services Module 07: History and Future Developments [ COURSE 05 ] - Level 2 Diploma for the Early Years Practitioner Module 01: Roles and Responsibilities of the Early Years Practitioner Module 02: Health and Safety of Babies and Young Children in the Early Years Module 03: Equality, Diversity and Inclusive Practice in Early Years Settings Module 04: Safeguarding, Protection and Welfare of Babies and Young Children in Early Years Settings Module 05: Understand How to Support Children's Development Module 06: Support Care Routines for Babies and Young Children Module 07: Support the Planning and Delivery of Activities, Purposeful Play Opportunities and Educational Programmes Module 08: Promote Play in an Early Years Setting Module 09: Support Well-being of Babies and Young Children for Healthy Lifestyles Module 10: Support Babies and Young Children to be Physically Active Module 11: Support the Needs of Babies and Young Children with Special Educational Needs and Disability Module 12: Promote Positive Behaviour in Early Years Settings Module 13: Partnership Working in the Early Years Module 14: Support Children's Transition to School [ COURSE 06 ] - Level 2 Certificate in Behaviour that Challenges in Children Module 1: Understand Behaviour That Challenges Module 2: Understand How to Support Positive Behaviour Module 3: Understand the Importance of Effective Communication and the Management of Behaviour That Challenges Module 4: Understand the Role of Reflection and Support for Those Involved in Incidents of Behaviour That Challenges [ COURSE 07 ] - Nursery Nurse Course Module 01: An Overview of Nursery Nurse Module 02: Recognizing Children's Growth and Development Module 03: Observation and Assessment of Children in Early Childhood Settings Module 04: How to Promote Equality, Diversity and Inclusive Practice in Early Years of Learning Module 05: Safeguarding and Protecting Young Children Module 06: Ensuring Health and Safety of Children in the Early Years Module 07: The Essence of Nutrition and Healthy Food for Children Module 08: Importance of Play and Learning in Children's Education Module 09: Ways of Working with Children Having Special Needs Module 10: Working in Partnership with Parents and Carers [ COURSE 08 ] - Level 2 Safeguarding Children Training Course Module 1: Basic Knowledge of Children Safeguarding Module 2: Children and the Law Module 3: Legislation and Policies That Surround Safeguarding Children Module 4: Child Abuse & Its Types Module 5: Responding to Disclosure Module 6: The Role of Health and Other Professionals [ COURSE 09 ] - Level 4 Diploma in Child Psychology Course Module 01: An Introduction to Child Psychology Module 02: Attachment and the Childhood (I) Module 03: Attachment and the Childhood (II) Module 04: Consequences of Separation and Loss on Children's Development Module 05: Aspects that Impact Development Module 06: Social and Emotional Development Module 07: Personality Development of Children: The Process Module 08: Stages of Language Development Module 09: The Process of Moral Development [ COURSE 10 ] - Level 3 Designated Safeguarding Lead Training Course Module 01: Introduction Module 02: Safeguarding Structure and Guidance Module 03: Recognising and Responding to Abuse Module 04: Responses Under the Safeguarding Structure Module 05: Working Together and Sharing Information Module 06: Recording Information [ COURSE 11 ] - Primary Teaching Diploma Module 01: Primary Education in the UK Module 02: Responsibilities, Qualifications and Skills Module 03: Initial Teacher Training Module 04: Types of Schools in the UK Module 05: Importance of Early Years in Development Module 06: EYFS Teaching Techniques Module 07: Teaching Primary English Module 08: Teaching Primary Mathematics Module 09: Teaching Primary Science, Design and Technology Module 10: Teaching Other Primary Subjects Module 11: Children Having Special Education Needs or Disabilities Module 12: EYFS Framework in 2021 Module 13: Self-Management and Dealing with Stress [ COURSE 12 ] - Level 2 Certificate in Understanding Common Childhood Illnesses Affecting Children Module 1: Understand How to Provide a Safe and Healthy Environment for Babies and Young Children Module 2: Understand Common Childhood Illnesses Module 3: Understand Health Emergencies and Specific Health Conditions in an Early Years Setting Assessment Method After completing each module of the Child care and Development Mega Bundle (12 Courses), you will find automated MCQ quizzes. To unlock the next module, you need to complete the quiz task and get at least 60% marks. Once you complete all the modules in this manner, you will be qualified to request your certification. Certification After completing the MCQ/Assignment assessment for this course, you will be entitled to a Certificate of Completion from Training Tale. It will act as proof of your extensive professional development. The certificate is in PDF format, which is completely free to download. A printed version is also available upon request. It will also be sent to you through a courier for £13.99. Who is this course for? This Child care and Development Mega Bundle (12 Courses) is ideal for those who are aspiring professionals or who want to get a head start in the field of child care and development. Requirements There is no specific requirement to enrol for this Child care and Development Mega Bundle (12 Courses). However, you need to be over 16. Career path After completing this Child care and Development Mega Bundle (12 Courses) course, you may be able to pursue a variety of career opportunities. Such as - Residential Child Care Worker: £10.09 - £13.00 per hour Child Care Solicitor: £35,000 - £60,000 per annum Nanny: £13.00 - £15.00 per hour Paediatric Nurses: £20.00 - £26.00 per hour Certificates Certificate of completion Digital certificate - Included

Fundamentals of Secure Software
By Packt
This course is complete training for someone who wants to join the security world and get familiar with most of the practices/risks and different areas, where they can invest to become experts. It covers both the 'admin' side of how to develop the processes and program around it as well as an insight into the technical aspects.

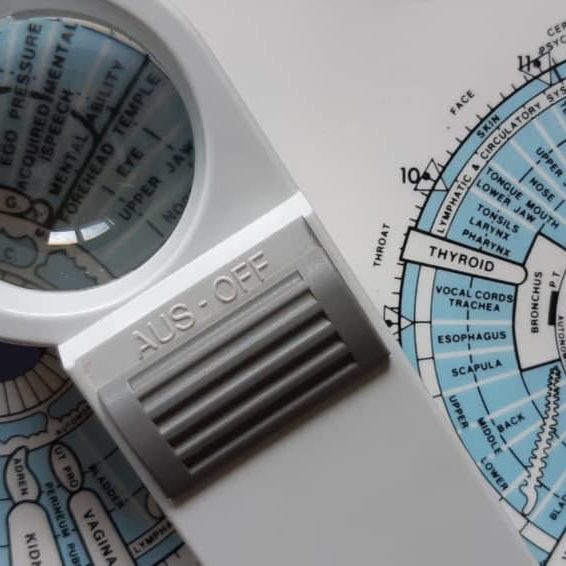
Iridology Diploma
By Plaskett International
LEARN HOW IRIDOLOGY CAN MAKE A HUGE CONTRIBUTION TO ANY COMPLEMENTARY PRACTICE A MESSAGE FROM THE AUTHOR I want to welcome you most warmly to the study of Iridology. Students of our course have taken their knowledge out into the world of practice and they have been able to see more penetratingly into the health of their patients. They have seen many truths about causes and effects in health and disease - that is what allows you to understand those extra things that make you into an even better healer. I think you are going to find this the most intriguing and absorbing study and, certainly, that is my sincere hope. As you precede, much of what you learn will amaze you and inspire wonder at the ways of the human body and mind. As you tread this very special road, I pass on to you the words that Bernard Jensen gave me years ago when I was his student, inscribed upon the inside cover of his book: “Seek the Higher Values in Life”. DR. LAWRENCE PLASKETT WHAT IS IRIDOLOGY? Iridology is the art of iris analysis. The iris is connected to the brain via the hypothalamus and can give naturopathic read outs on tissue conditions in various parts of the body. With training and practice it is possible to read signs indicative of biochemical, emotional and environmental influences that are hard to determine by other means. We can thus interpret health (and even aspects of personality) by close examination of the eyes, using suitable illumination and a magnifying glass. The close relationship between naturopathic iridology as an assessment tool and nutritional therapy and other naturopathic disciplines continues and grows closer. Now Iridology can make a huge contribution to complementary therapeutic practice and enhanced by our wonderful digital collection of eye photographs, the learning process with the Plaskett International College is a profound and exciting one. We teach Iridology quite separately from other topics and anyone who possesses, or expects to possess, a practitioner's qualification in any therapeutic discipline, may join the course. Course Duration 12 months Study Hours 200 hours Course Content 9 sections Course Fee £495 How Can Iridology Help Practitioners? Examples of how iridology can help practitioners Did you know that some iris features are so very plain that you can see them with the naked eye in ordinary social contact? You can see from two or three feet away in many cases that the person has a toxic digestive system (a strong wide dark ring around the pupil margin). You can often tell that the person has an overactive stomach (a narrow bright white ring very close to the pupil). You can tell when the skin is overlaid with toxins so that the skin's function in excreting toxins from the body is jeopardised (very narrow dark ring around the iris margin). You can tell in some people (rather advanced cases) that they suffer badly from sodium and potassium imbalance and have placed themselves at potential risk from cholesterol accumulation (the so-called corneal arcus, a white or off-white cloudy deposit, usually fairly thick, around the iris margin). Another example is the ring of spots or 'tophi' represented by the lymphatic rosary. Its mere presence tells one that there is sluggishness in the lymphatic system. When these tophi are darkly pigmented, the situation gives rise to concern for the possible generation of lymphatic illness. Using the precise positioning of iris reflex areas contained on the iris chart, one may distinguish many key points of analysis. Areas of stress and tension can be pinpointed by identifying 'contraction furrows’. Past injuries and adhesions show themselves as contortions of the normally regular and even iris fibres. You can answer questions like:- Is it the pancreas or the liver that is responsible for the trouble? Is the patient's hypertension caused by a defect of or toxic deposits in the particular brain area that is geared to control blood pressure? One of Jensen's rather dramatic illustrations is of the iris of a man who has just been shot. It shows the precise areas of tissue damage within the body and the response is very fast. The number of potential examples is almost without limit. The above may suffice to show the types of things that iridology can do for practitioners. We hope it will help you decide to study Iridology with the Plaskett International College. Course Overview The course covers the nature of iris observation, the nutritive zone, the iris chart, the chronic and acute, the intestinal and stomach zones and nerve collarette, the constitution type, respiratory system, lacunae, open lacuna, inherent weaknesses, the organs of elimination, other organs, special signs, complete diagnosis of a subject. The treatment of the topic follows the principles of Bernard Jensen in the USA. Once the basics have been learnt, the course teachings then extend considerably by bringing in the work of Dorothy Hall and of Dr Josef Deck, both of which are the subject of a special presentation during the course. The published insights of Farida Sharan and Harri Wolf, while not separately presented, also influence the presentation of the course material. Both the Australian School, (Dorothy Hall) and the German School, (Dr Deck/Harri Wolf), offer an added dimension to the study and interpretation of the constitution. PERSONALITY ASPECTS & CONSTITUTIONAL TYPES The study focuses upon the different personality aspects, which show up in different constitutional types. Dorothy Hall gives insights into what contributes to various different types of personality and their emotional and mental responses and their pre-dispositions to health or disease. Different sorts of people can have different priorities, preferences and imperatives built into their very nature from or before birth, sometimes determining the course of their entire lives and their attitudes to the world and to other people. AN EMPATHY BETWEEN PATIENT & PRACTITIONER The course teaches an understanding of these types and facilitates an empathy between patient and practitioner. It shows how people of the differing constitutional types are likely to go out of balance either mentally or emotionally and how their vulnerability to various physical ailments varies. The German School offers a very exciting and precise approach to the constitutional types, which is really quite different, but no less helpful. It highlights variations in the susceptibility to diseases of different organs and systems. THE 3 SCHOOLS OF THOUGHT It is a prime purpose of this course, not only to teach these differing positions, but also to demonstrate how it is that all three of these major schools of Iridology embody different aspects of the truth, how each is individually valuable and how a full and deep understanding of the meaning of 'constitution' can be gained through a sympathetic synthesis of the contributions from all three of these schools. BREAKDOWN OF THE COURSE SECTIONS In total there are 9 sections comprising of text, videos and iris images to study: SECTION 1 GENERAL PRACTICE AND AN ACCOUNT OF THE NUTRITIVE ZONE Areas Covered Iris colour Information that iridology can give us The structure of the eye and the iris Using the iris as an assessment tool The principle of reflex areas The Nutritive Zone Abnormality in the colon The Collarette (autonomic nerve wreath or anw) Diagnosis of the constitution based upon fibre structure Studies on images of real eyes SECTION 2 FEATURES OF THE FIBRES OUTSIDE THE COLLARETTE Areas Covered The general layout of fibres outside the collarette Inherent weaknesses First stage in further deterioration of an inherent weakness The meaning of darkness in the iris The development of discrete – open lacunae Lacunae Further notes about lightness and darkness amongst the fibres Healing lines Crypts Round the iris chart – the left iris Round the iris chart – the right iris Checking which structures and inside and which outside the collarette The organ systems The neural arc reflex SECTION 3 SPECIAL SIGNS Areas covered The corneal arcus (sodium ring, cholesterol ring, lipemic ring) The tophi (also lymphatic tophi or lymphatic rosary) Corneal Arcus The anaemia sign The catarrhal sign Acidity Grey background Scurf rim Circulatory ring Sphincter muscle (also called pupillary sphincter) Pigments (topastible or topolabile) Psoric spots Contrcation furrows Radial furrows SECTION 4 THE CONSTITUTIONS IN RELATION TO PERSONALITY TYPE AND DISEASE DISPOSITION Areas covered Very resilient Resilient average Moderately resilient Mildly resilient SECTION 5 MORE ABOUT WHITE SIGNS Areas covered Revision of distinctions between the different white signs Pictures of irises with white signs, with commentaries Further interpretation of the corneal arcus Further interpretation of the lytophi More general interpretation of the colour white SECTION 6 COLOURS IN THE IRIS AND OTHER SPECIAL SIGNS Areas Covered Yellow pigment in the iris Orange pigment Brown pigment Contraction furrows Radial furrows Psoric spots Pupillary border The “friendly fibrils” sign Summary of remedies SECTION 7 THE CONSTITUTION AND SIGNS ACCORDING TO THE GERMAN SCHOOL Areas Covered The German school of iridology Our approach to teaching the German school Introduction to the German constitutional types The lymphatic constitutions Mixed biliary constitution or biliary constitution Haematogenic (or haematogenous) constitution The way to use information on the German constitutions New signs that are specific to the German school Treatment recommendations for constitutional types SECTION 8 ADVANCED STUDIES OF THE IRIS Areas Covered Further details of the iris chart – its layout and its implications Neural arc reflex Deformation of pupil shape and position Advanced study of fibre separations, sinuosity, injuries & adhesions Lacunae of different shape and appearance The b3 bulge and the pterygium Working with genetically brown eyes SECTION 9 THE CONSULTATION & THE PRACTICALITIES Areas Covered Diagnosing pathology of individual critical organs Personality interpretations based upon the German school Conducting an iridology consultation Practical aspects of iris examination Making drawings of the iris and recording the data The uses, advantages and limitations of iris photography and its place in iridology practice Equipments and techniques of iris photography Using the computer to store and process digital images The interaction of signs Interpreting the whole iris in conjunction with the case study Pointers to treatment Carrying out case histories TESTIMONIALS Here's what students have to say about the course Emma Rubio, Health Coach Spain "As a Health Coach I decided to pursue my studies with the Plaskett College to become a Nutritional Therapist. For that, I am also studying Iridology. I am happy to have a tutor to answer my doubts and I like the flexibility that the College offers me. I love the subject of Iridology and the way it is explained, I also like having some videos of Dr Plaskett teaching Iridology as I admire him." Dr Ezequiel Lafontaine, Iridologist Puerto Rico "I LOVE IRIDOLOGY. I have over 30 iridology books, Italian, French, German, Spanish and English, plus over 4,000 photos from my own practice. I took this course for a refresher course and found the material was second to none." Mrs D. Moothy, Nutritional Therapist Mauritius “The distance learning courses have given me the opportunity to pursue my dreams through a program that was not only flexible and convenient for my schedule, but was also challenging and rewarding. I thoroughly enjoyed the readings and the assignments but most importantly, I enjoyed being able to do things at my pace. I must say that the most exciting and challenging course was the Iridology Diploma, and I am happy that I was able to do well in all the courses."
Adults Safeguarding
By IOMH - Institute of Mental Health
Overview of Adults Safeguarding Unlocking a Safe and Empowered Future for Vulnerable Adults! Assume a world where everyone lives with dignity and respect, regardless of age or vulnerability, free from harm and neglect. This vision drives the growing field of adult safeguarding, a sector with opportunities to make a tangible difference in lives. Consider these statistics: in the UK alone, an estimated 1.5 million adults experience some form of abuse or neglect annually. This translates to a staggering one person every minute. The Adults Safeguarding course equips you with the knowledge and skills to participate in the solution. Through its comprehensive curriculum, you'll delve into the intricacies of safeguarding legislation, explore diverse forms of abuse and neglect, and understand your crucial role in reporting concerns and advocating for vulnerable individuals. Join us on this empowering journey and become a champion of safety, respect, and autonomy. Whether you're a seasoned professional seeking to sharpen your expertise or a newcomer eager to break into this meaningful field, this course holds the key to unlocking a rewarding career path and, most importantly, shaping a brighter future for those who need it most. This Adults Safeguarding Course will help you to learn: Recognise signs and types of abuse against vulnerable adults. Understand legislation and policies for safeguarding vulnerable adults. Know how to respond and report concerns about abuse. Be able to communicate effectively in care situations. Understand information-sharing principles in safeguarding cases. Know the roles and responsibilities for safeguarding vulnerable adults. This course covers the topic you must know to stand against the tough competition. The future is truly yours to seize with this Adults Safeguarding. Enrol today and complete the course to achieve a certificate that can change your career forever. Details Perks of Learning with IOMH One-To-One Support from a Dedicated Tutor Throughout Your Course. Study Online - Whenever and Wherever You Want. Instant Digital/ PDF Certificate. 100% Money Back Guarantee. 12 Months Access. Process of Evaluation After studying the course, an MCQ exam or assignment will test your skills and knowledge. You have to get a score of 60% to pass the test and get your certificate. Certificate of Achievement Certificate of Completion - Digital / PDF Certificate After completing the Adults Safeguarding course, you can order your CPD Accredited Digital / PDF Certificate for £5.99. Certificate of Completion - Hard copy Certificate You can get the CPD Accredited Hard Copy Certificate for £12.99. Shipping Charges: Inside the UK: £3.99 International: £10.99 Who Is This Course for? Care Workers and Support Staff: Deepen your understanding of safeguarding procedures and confidently navigate potential risks in your daily practice. Social Workers and Community Support Workers: Equip yourself with the specialised knowledge and skills to identify and respond to abuse in vulnerable communities effectively. Healthcare Professionals: Learn to recognise and report signs of abuse in your patients, safeguarding their well-being within healthcare settings. Police Officers and Law Enforcement Personnel: Gain valuable insights into safeguarding protocols and enhance your ability to investigate and protect vulnerable individuals. Anyone with a Passion for Protecting Vulnerable Adults: Whether you're a volunteer, family member, or a concerned citizen, this course empowers you to play a vital role in building a safer society. Requirements There is no prerequisite to enrol in this course. You don't need any educational qualification or experience to enrol in the Adults Safeguarding course. Do note: you must be at least 16 years old to enrol. Any internet-connected device, such as a computer, tablet, or smartphone, can access this online course. Career Path Social Worker: £27K to £50K/year. Mental Health Nurse: £24K to £40K/year. Safeguarding Lead/Officer: £28K to £48K/year. Police Officer: £31K to £60K/year. Independent Safeguarding Consultant: £35K to £65K/year. Course Curriculum Adults Safeguarding Module 01: An Introduction to Safeguarding of Vulnerable Adults 00:15:00 Module 02: Safeguarding Legislations 00:25:00 Module 03: Understanding Abuse and Neglect 00:25:00 Module 04: Safeguarding Vulnerable AdultsPolicy, Roles and Responsibilities 00:23:00 Module 05: Understanding the Importance of Communication in Care 00:20:00 Module 06: Sharing Information and Responding To a Disclosure 00:20:00 Module 07: Reporting Your Concern 00:17:00 Assignment Assignment - Adults Safeguarding 00:00:00

AZ-400 Designing and Implementing Microsoft DevOps Solutions
By Nexus Human
Duration 4 Days 24 CPD hours This course is intended for Students in this course are interested in implementing DevOps processes or in passing the Microsoft Azure DevOps Solutions certification exam. Overview After completing this course, students will be able to: Plan for the transformation with shared goals and timelines Select a project and identify project metrics and Key Performance Indicators (KPI's) Create a team and agile organizational structure Design a tool integration strategy Design a license management strategy (e.g., Azure DevOps and GitHub users) Design a strategy for end-to-end traceability from work items to working software Design an authentication and access strategy Design a strategy for integrating on-premises and cloud resources Describe the benefits of using Source Control Describe Azure Repos and GitHub Migrate from TFVC to Git Manage code quality including technical debt SonarCloud, and other tooling solutions Build organizational knowledge on code quality Explain how to structure Git repos Describe Git branching workflows Leverage pull requests for collaboration and code reviews Leverage Git hooks for automation Use Git to foster inner source across the organization Explain the role of Azure Pipelines and its components Configure Agents for use in Azure Pipelines Explain why continuous integration matters Implement continuous integration using Azure Pipelines Define Site Reliability Engineering Design processes to measure end-user satisfaction and analyze user feedback Design processes to automate application analytics Manage alerts and reduce meaningless and non-actionable alerts Carry out blameless retrospectives and create a just culture Define an infrastructure and configuration strategy and appropriate toolset for a release pipeline and application infrastructure Implement compliance and security in your application infrastructure Describe the potential challenges with integrating open-source software Inspect open-source software packages for security and license compliance Manage organizational security and compliance policies Integrate license and vulnerability scans into build and deployment pipelines Configure build pipelines to access package security and license ratings This course provides the knowledge and skills to design and implement DevOps processes and practices. Students will learn how to plan for DevOps, use source control, scale Git for an enterprise, consolidate artifacts, design a dependency management strategy, manage secrets, implement continuous integration, implement a container build strategy, design a release strategy, set up a release management workflow, implement a deployment pattern, and optimize feedback mechanisms. Module 1: Get started on a DevOps transformation journey Introduction to DevOps Choose the right project Describe team structures Choose the DevOps tools Plan Agile with GitHub Projects and Azure Boards Introduction to source control Describe types of source control systems Work with Azure Repos and GitHub Module 2: Development for enterprise DevOps Structure your Git Repo Manage Git branches and workflows Collaborate with pull requests in Azure Repos Explore Git hooks Plan foster inner source Manage Git repositories Identify technical debt Module 3: Implement CI with Azure Pipelines and GitHub Actions Explore Azure Pipelines Manage Azure Pipeline agents and pools Describe pipelines and concurrency Explore Continuous integration Implement a pipeline strategy Integrate with Azure Pipelines Introduction to GitHub Actions Learn continuous integration with GitHub Actions Design a container build strategy Module 4: Design and implement a release strategy Introduction to continuous delivery Explore release strategy recommendations Build a high-quality release pipeline Introduction to deployment patterns Implement blue-green deployment and feature toggles Implement canary releases and dark launching Implement A/B testing and progressive exposure deployment Module 5: Implement a secure continuous deployment using Azure Pipelines Create a release pipeline Provision and test environments Manage and modularize tasks and templates Automate inspection of health Manage application configuration data Integrate with identity management systems Implement application configuration Module 6: Manage infrastructure as code using Azure and DSC Explore infrastructure as code and configuration management Create Azure resources using Azure Resource Manager templates Create Azure resources by using Azure CLI Explore Azure Automation with DevOps Implement Desired State Configuration (DSC) Implement Bicep Module 7: Implement security and validate code bases for compliance Introduction to Secure DevOps Implement open-source software Software Composition Analysis Static analyzers OWASP and Dynamic Analyzers Security Monitoring and Governance Module 8: Design and implement a dependency management strategy Explore package dependencies Understand package management Migrate, consolidate, and secure artifacts Implement a versioning strategy Introduction to GitHub Packages Module 9: Implement continuous feedback Implement tools to track usage and flow Develop monitor and status dashboards Share knowledge within teams Design processes to automate application analytics Manage alerts, Blameless retrospectives and a just culture Additional course details: Nexus Humans AZ-400 Designing and Implementing Microsoft DevOps Solutions training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the AZ-400 Designing and Implementing Microsoft DevOps Solutions course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Intermediate Ethical Hacking Hands-on Training Online
By Lead Academy
Intermediate Ethical Hacking Hands-on Training Course Overview Are you looking to begin your ethical hacking career or want to develop more advanced skills in ethical hacking? Then this intermediate ethical hacking hands-on training course will set you up with a solid foundation to become a confident ethical hacker and help you to develop your expertise in ethical hacking. This intermediate ethical hacking hands-on training course is accredited by the CPD UK & IPHM. CPD is globally recognised by employers, professional organisations and academic intuitions, thus a certificate from CPD Certification Service creates value towards your professional goal and achievement. CPD certified certificates are accepted by thousands of professional bodies and government regulators here in the UK and around the world. Whether you are self-taught and you want to fill in the gaps for better efficiency and productivity, this intermediate ethical hacking hands-on training course will set you up with a solid foundation to become a confident ethical hacker and develop more advanced skills. Gain the essential skills and knowledge you need to propel your career forward as a ethical hacker. The intermediate ethical hacking hands-on training course will set you up with the appropriate skills and experience needed for the job and is ideal for both beginners and those currently working as a ethical hacker. This comprehensive intermediate ethical hacking hands-on training course is the perfect way to kickstart your career in the field of ethical hacking. This intermediate ethical hacking hands-on training course will give you a competitive advantage in your career, making you stand out from all other applicants and employees. If you're interested in working as a ethical hacker or want to learn more skills on ethical hacking but unsure of where to start, then this intermediate ethical hacking hands-on training course will set you up with a solid foundation to become a confident ethical hacker and develop more advanced skills. As one of the leading course providers and most renowned e-learning specialists online, we're dedicated to giving you the best educational experience possible. This intermediate ethical hacking hands-on training course is crafted by industry expert, to enable you to learn quickly and efficiently, and at your own pace and convenience. Who is this intermediate ethical hacking hands-on training online course for? This comprehensive intermediate ethical hacking hands-on training course is suitable for anyone looking to improve their job prospects or aspiring to accelerate their career in this sector and want to gain in-depth knowledge of ethical hacking. Entry Requirement There are no academic entry requirements for this intermediate ethical hacking hands-on training course, and it is open to students of all academic backgrounds. As long as you are aged seventeen or over and have a basic grasp of English, numeracy and ICT, you will be eligible to enrol. Assessment Method This intermediate ethical hacking hands-on training online course assesses learners through multiple-choice questions (MCQs). Upon successful completion of the modules, learners must answer MCQs to complete the assessment procedure. Through the MCQs, it is measured how much a learner can grasp from each section. In the assessment pass mark is 60%. Course Curriculum Course Overview Course Overview Virtual Lab Build Video - Downloading ISO and OVA Files for VirtualBox Video and Lab -Creating a Virtual install of Kali using VirtualBox Video and lab - Create a virtual install of Metasploitable2 Video and Lab - Creating Windows 7 Pro Target Machine Using VirtualBox Video - Installing the VirtualBox Extension Pack NMap Video and Lab - Installing the WebMap-Nmap Dashboard Video and Lab - Automated Recon/Enumeration Using nmapAutomator Enumerating a Windows 10 Target Video - Creating a Vulnerable Windows 10 Target Reverse Shells, Privilege Escalation and Persistent Backdoors Video and Lab - Create a Windows Reverse Shell Using the PowerShell Video and Lab - Create a Reverse Shell Using Command Injection Video and Lab - Create a Reverse Shell Using a File Upload Video and Lab - Launch an Automated Meterpreter Session Video and Lab - Upgrade a Dumb Terminal to Fully Functional BASH Shell Video and Lab - Windows 7 Privilege Escalation Using UAC Bypass Video and Lab - Creating a Persistent Backdoor Using a Persistent Service PowerShell Empire Video and Lab - Create Virtual Install of Server 2016 Full GUI Using VirtualBox Video and Lab - Installing PowerShell Empire StarKiller On Kali Linux Video and Lab - Enumerating Active Directory Video and Lab - Post-Exploitation of Windows Using PowerShell Empire Post Exploitation of Microsoft Windows Video and Lab - Advanced Password Hacking with Metasploit Video and Lab - Post-Exploitation of Microsoft Windows video and Lab - Enumerating Active Directory Using RPCClient Video and Lab - Dumping Wi-Fi Credentials Using netsh Practical Pentesting Labs Video and Lab - Heartbleed OpenSSL Exploit Vulnerability Video and Lab - Performing an RDP Brute Force Attack Video and Lab - Exploiting Active Directory using LLMNR/NBT-NS Poisoning Video and Lab - Accessing Kali Across the WAN with NGROK Video and Lab - Pentesting with Netcat Video and Lab - Enumerate DNS Records Using DNSRecon Auditing Wireless Network Video and Lab - Installing a Wireless Adapter in Kali Video and Lab - Hacking a Wireless Network Using Kali Linux Video and Lab - Wireless Deauthentication Attack Video and Lab - PMKID Client-less Wireless Attack Using Bettercap Wireshark Video - Overview of Wireshark 3.2 Video - Wireshark Capture Options Video - Wireshark Toolbar Icons Video - Capturing Wireless Traffic Using Wireshark Video and Lab - Capturing a 3-way TCP Handshake Using Wireshark Web App Penetration Testing Video and Lab - Creating a virtual install of OWASP Video and lab - Setting Up Burp Suite Video and Lab - Attack Web Apps with Burp Suite Using SQL Injection Video and Lab - OS Command Injection Using Commix 3.2x Video - Web Application Firewall Detection Using WAFW00F Video and Lab - Exploit Vulnerable Web Applications Using Command Injection Video and Lab - Using Banner Grabbing to Aid in Reconnaissance Anonymity - Remaining Anonymous While Pentesting Video and Lab - Anonymize Kali Using Whonix CTF - SQL Injection to Shell Walkthrough Video and Lab - Lab Preparation for CTF SQL Injection to Shell Video and Lab - CTF Walkthrough for SQL Injection to Shell Recognised Accreditation CPD Certification Service This course is accredited by continuing professional development (CPD). CPD UK is globally recognised by employers, professional organisations, and academic institutions, thus a certificate from CPD Certification Service creates value towards your professional goal and achievement. CPD certificates are accepted by thousands of professional bodies and government regulators here in the UK and around the world. Many organisations look for employees with CPD requirements, which means, that by doing this course, you would be a potential candidate in your respective field. Certificate of Achievement Certificate of Achievement from Lead Academy After successfully passing the MCQ exam you will be eligible to order your certificate of achievement as proof of your new skill. The certificate of achievement is an official credential that confirms that you successfully finished a course with Lead Academy. Certificate can be obtained in PDF version at a cost of £12, and there is an additional fee to obtain a printed copy certificate which is £35. Overview Intermediate Ethical Hacking Hands-on Training Course Overview Are you looking to begin your ethical hacking career or want to develop more advanced skills in ethical hacking? Then this intermediate ethical hacking hands-on training course will set you up with a solid foundation to become a confident ethical hacker and help you to develop your expertise in ethical hacking. This intermediate ethical hacking hands-on training course is accredited by the CPD UK & IPHM. CPD is globally recognised by employers, professional organisations and academic intuitions, thus a certificate from CPD Certification Service creates value towards your professional goal and achievement. CPD certified certificates are accepted by thousands of professional bodies and government regulators here in the UK and around the world. Whether you are self-taught and you want to fill in the gaps for better efficiency and productivity, this intermediate ethical hacking hands-on training course will set you up with a solid foundation to become a confident ethical hacker and develop more advanced skills. Gain the essential skills and knowledge you need to propel your career forward as a ethical hacker. The intermediate ethical hacking hands-on training course will set you up with the appropriate skills and experience needed for the job and is ideal for both beginners and those currently working as a ethical hacker. This comprehensive intermediate ethical hacking hands-on training course is the perfect way to kickstart your career in the field of ethical hacking. This intermediate ethical hacking hands-on training course will give you a competitive advantage in your career, making you stand out from all other applicants and employees. If you're interested in working as a ethical hacker or want to learn more skills on ethical hacking but unsure of where to start, then this intermediate ethical hacking hands-on training course will set you up with a solid foundation to become a confident ethical hacker and develop more advanced skills. As one of the leading course providers and most renowned e-learning specialists online, we're dedicated to giving you the best educational experience possible. This intermediate ethical hacking hands-on training course is crafted by industry expert, to enable you to learn quickly and efficiently, and at your own pace and convenience. Who is this intermediate ethical hacking hands-on training online course for? This comprehensive intermediate ethical hacking hands-on training course is suitable for anyone looking to improve their job prospects or aspiring to accelerate their career in this sector and want to gain in-depth knowledge of ethical hacking. Entry Requirement There are no academic entry requirements for this intermediate ethical hacking hands-on training course, and it is open to students of all academic backgrounds. As long as you are aged seventeen or over and have a basic grasp of English, numeracy and ICT, you will be eligible to enrol. Assessment Method This intermediate ethical hacking hands-on training online course assesses learners through multiple-choice questions (MCQs). Upon successful completion of the modules, learners must answer MCQs to complete the assessment procedure. Through the MCQs, it is measured how much a learner can grasp from each section. In the assessment pass mark is 60%. Course Curriculum Course Overview Course Overview Virtual Lab Build Video - Downloading ISO and OVA Files for VirtualBox Video and Lab -Creating a Virtual install of Kali using VirtualBox Video and lab - Create a virtual install of Metasploitable2 Video and Lab - Creating Windows 7 Pro Target Machine Using VirtualBox Video - Installing the VirtualBox Extension Pack NMap Video and Lab - Installing the WebMap-Nmap Dashboard Video and Lab - Automated Recon/Enumeration Using nmapAutomator Enumerating a Windows 10 Target Video - Creating a Vulnerable Windows 10 Target Reverse Shells, Privilege Escalation and Persistent Backdoors Video and Lab - Create a Windows Reverse Shell Using the PowerShell Video and Lab - Create a Reverse Shell Using Command Injection Video and Lab - Create a Reverse Shell Using a File Upload Video and Lab - Launch an Automated Meterpreter Session Video and Lab - Upgrade a Dumb Terminal to Fully Functional BASH Shell Video and Lab - Windows 7 Privilege Escalation Using UAC Bypass Video and Lab - Creating a Persistent Backdoor Using a Persistent Service PowerShell Empire Video and Lab - Create Virtual Install of Server 2016 Full GUI Using VirtualBox Video and Lab - Installing PowerShell Empire StarKiller On Kali Linux Video and Lab - Enumerating Active Directory Video and Lab - Post-Exploitation of Windows Using PowerShell Empire Post Exploitation of Microsoft Windows Video and Lab - Advanced Password Hacking with Metasploit Video and Lab - Post-Exploitation of Microsoft Windows video and Lab - Enumerating Active Directory Using RPCClient Video and Lab - Dumping Wi-Fi Credentials Using netsh Practical Pentesting Labs Video and Lab - Heartbleed OpenSSL Exploit Vulnerability Video and Lab - Performing an RDP Brute Force Attack Video and Lab - Exploiting Active Directory using LLMNR/NBT-NS Poisoning Video and Lab - Accessing Kali Across the WAN with NGROK Video and Lab - Pentesting with Netcat Video and Lab - Enumerate DNS Records Using DNSRecon Auditing Wireless Network Video and Lab - Installing a Wireless Adapter in Kali Video and Lab - Hacking a Wireless Network Using Kali Linux Video and Lab - Wireless Deauthentication Attack Video and Lab - PMKID Client-less Wireless Attack Using Bettercap Wireshark Video - Overview of Wireshark 3.2 Video - Wireshark Capture Options Video - Wireshark Toolbar Icons Video - Capturing Wireless Traffic Using Wireshark Video and Lab - Capturing a 3-way TCP Handshake Using Wireshark Web App Penetration Testing Video and Lab - Creating a virtual install of OWASP Video and lab - Setting Up Burp Suite Video and Lab - Attack Web Apps with Burp Suite Using SQL Injection Video and Lab - OS Command Injection Using Commix 3.2x Video - Web Application Firewall Detection Using WAFW00F Video and Lab - Exploit Vulnerable Web Applications Using Command Injection Video and Lab - Using Banner Grabbing to Aid in Reconnaissance Anonymity - Remaining Anonymous While Pentesting Video and Lab - Anonymize Kali Using Whonix CTF - SQL Injection to Shell Walkthrough Video and Lab - Lab Preparation for CTF SQL Injection to Shell Video and Lab - CTF Walkthrough for SQL Injection to Shell Recognised Accreditation CPD Certification Service This course is accredited by continuing professional development (CPD). CPD UK is globally recognised by employers, professional organisations, and academic institutions, thus a certificate from CPD Certification Service creates value towards your professional goal and achievement. CPD certificates are accepted by thousands of professional bodies and government regulators here in the UK and around the world. Many organisations look for employees with CPD requirements, which means, that by doing this course, you would be a potential candidate in your respective field. Certificate of Achievement Certificate of Achievement from Lead Academy After successfully passing the MCQ exam you will be eligible to order your certificate of achievement as proof of your new skill. The certificate of achievement is an official credential that confirms that you successfully finished a course with Lead Academy. Certificate can be obtained in PDF version at a cost of £12, and there is an additional fee to obtain a printed copy certificate which is £35. FAQ Is CPD a recognised qualification in the UK? CPD is globally recognised by employers, professional organisations and academic intuitions, thus a certificate from CPD Certification Service creates value towards your professional goal and achievement. CPD-certified certificates are accepted by thousands of professional bodies and government regulators here in the UK and around the world. Are QLS courses recognised? Although QLS courses are not subject to Ofqual regulation, they must adhere to an extremely high level that is set and regulated independently across the globe. A course that has been approved by the Quality Licence Scheme simply indicates that it has been examined and evaluated in terms of quality and fulfils the predetermined quality standards. When will I receive my certificate? For CPD accredited PDF certificate it will take 24 hours, however for the hardcopy CPD certificate takes 5-7 business days and for the Quality License Scheme certificate it will take 7-9 business days. Can I pay by invoice? Yes, you can pay via Invoice or Purchase Order, please contact us at info@lead-academy.org for invoice payment. Can I pay via instalment? Yes, you can pay via instalments at checkout. How to take online classes from home? Our platform provides easy and comfortable access for all learners; all you need is a stable internet connection and a device such as a laptop, desktop PC, tablet, or mobile phone. The learning site is accessible 24/7, allowing you to take the course at your own pace while relaxing in the privacy of your home or workplace. Does age matter in online learning? No, there is no age limit for online learning. Online learning is accessible to people of all ages and requires no age-specific criteria to pursue a course of interest. As opposed to degrees pursued at university, online courses are designed to break the barriers of age limitation that aim to limit the learner's ability to learn new things, diversify their skills, and expand their horizons When I will get the login details for my course? After successfully purchasing the course, you will receive an email within 24 hours with the login details of your course. Kindly check your inbox, junk or spam folder, or you can contact our client success team via info@lead-academy.org Course Fee £25 £125 80% OFF ð CPD UK Accredited PDF Certificate Included 4 interest-free payments of £6.25 Intermediate Ethical Hacking Hands-on Training Online quantity ENROL NOW Duration: * Hours Instant Access Get In Touch Today Live CHAT WITH US CALL ON - 0300 124 5585 Certificate of Achievement Certificate of Achievement from Lead Academy After successfully passing the MCQ exam you will be eligible to order your certificate of achievement as proof of your new skill. The certificate of achievement is an official credential that confirms that you successfully finished a course with Lead Academy. Certificate can be obtained in PDF version at a cost of £12, and there is an additional fee to obtain a printed copy certificate which is £35. FAQs Is CPD a recognised qualification in the UK? CPD is globally recognised by employers, professional organisations and academic intuitions, thus a certificate from CPD Certification Service creates value towards your professional goal and achievement. CPD-certified certificates are accepted by thousands of professional bodies and government regulators here in the UK and around the world. Are QLS courses recognised? Although QLS courses are not subject to Ofqual regulation, they must adhere to an extremely high level that is set and regulated independently across the globe. A course that has been approved by the Quality Licence Scheme simply indicates that it has been examined and evaluated in terms of quality and fulfils the predetermined quality standards. When will I receive my certificate? For CPD accredited PDF certificate it will take 24 hours, however for the hardcopy CPD certificate takes 5-7 business days and for the Quality License Scheme certificate it will take 7-9 business days. Can I pay by invoice? Yes, you can pay via Invoice or Purchase Order, please contact us at info@lead-academy.org for invoice payment. Can I pay via instalment? Yes, you can pay via instalments at checkout. How to take online classes from home? Our platform provides easy and comfortable access for all learners; all you need is a stable internet connection and a device such as a laptop, desktop PC, tablet, or mobile phone. The learning site is accessible 24/7, allowing you to take the course at your own pace while relaxing in the privacy of your home or workplace. Does age matter in online learning? No, there is no age limit for online learning. Online learning is accessible to people of all ages and requires no age-specific criteria to pursue a course of interest. As opposed to degrees pursued at university, online courses are designed to break the barriers of age limitation that aim to limit the learner's ability to learn new things, diversify their skills, and expand their horizons When I will get the login details for my course? After successfully purchasing the course, you will receive an email within 24 hours with the login details of your course. Kindly check your inbox, junk or spam folder, or you can contact our client success team via info@lead-academy.org

Web Hacking Secrets - How to Hack Legally and Earn Thousands of Dollars at HackerOne
By Packt
Master web application security testing and become a successful bug hunter

Bribery and corruption risk assessment
By Global Risk Alliance Ltd
Our training programme will provide those involved at any stage of the process for procuring goods and/or services within their organisations with the knowledge and skillset to identify and mitigate the threat posed by the breadth and multi-layered complexity of procurement fraud, corruption and associated financial crime and money laundering.

F5 Networks Configuring BIG-IP Advanced WAF - Web Application Firewall (formerly ASM)
By Nexus Human
Duration 4 Days 24 CPD hours This course is intended for This course is intended for security and network administrators who will be responsible for the installation, deployment, tuning, and day-to-day maintenance of the F5 Advanced Web Application Firewall. In this 4 day course, students are provided with a functional understanding of how to deploy, tune, and operate F5 Advanced Web Application Firewall to protect their web applications from HTTP-based attacks. The course includes lecture, hands-on labs, and discussion about different F5 Advanced Web Application Firewall tools for detecting and mitigating threats from multiple attack vectors such web scraping, Layer 7 Denial of Service, brute force, bots, code injection, and zero day exploits. Module 1: Setting Up the BIG-IP System Introducing the BIG-IP System Initially Setting Up the BIG-IP System Archiving the BIG-IP System Configuration Leveraging F5 Support Resources and Tools Module 2: Traffic Processing with BIG-IP Identifying BIG-IP Traffic Processing Objects Overview of Network Packet Flow Understanding Profiles Overview of Local Traffic Policies Visualizing the HTTP Request Flow Module 3: Web Application Concepts Overview of Web Application Request Processing Web Application Firewall: Layer 7 Protection F5 Advanced WAF Layer 7 Security Checks Overview of Web Communication Elements Overview of the HTTP Request Structure Examining HTTP Responses How F5 Advanced WAF Parses File Types, URLs, and Parameters Using the Fiddler HTTP Proxy Module 4: Common Web Application Vulnerabilities A Taxonomy of Attacks: The Threat Landscape What Elements of Application Delivery are Targeted? Common Exploits Against Web Applications Module 5: Security Policy Deployment Defining Learning Comparing Positive and Negative Security Models The Deployment Workflow Policy Type: How Will the Policy Be Applied Policy Template: Determines the Level of Protection Policy Templates: Automatic or Manual Policy Building Assigning Policy to Virtual Server Deployment Workflow: Using Advanced Settings Selecting the Enforcement Mode The Importance of Application Language Configure Server Technologies Verify Attack Signature Staging Viewing Requests Security Checks Offered by Rapid Deployment Defining Attack Signatures Using Data Guard to Check Responses Module 6: Policy Tuning and Violations Post-Deployment Traffic Processing Defining Violations Defining False Positives How Violations are Categorized Violation Rating: A Threat Scale Defining Staging and Enforcement Defining Enforcement Mode Defining the Enforcement Readiness Period Reviewing the Definition of Learning Defining Learning Suggestions Choosing Automatic or Manual Learning Defining the Learn, Alarm and Block Settings Interpreting the Enforcement Readiness Summary Configuring the Blocking Response Page Module 7: Attack Signatures & Threat Campaigns Defining Attack Signatures Attack Signature Basics Creating User-Defined Attack Signatures Defining Simple and Advanced Edit Modes Defining Attack Signature Sets Defining Attack Signature Pools Understanding Attack Signatures and Staging Updating Attack Signatures Defining Threat Campaigns Deploying Threat Campaigns Module 8: Positive Security Policy Building Defining and Learning Security Policy Components Defining the Wildcard Defining the Entity Lifecycle Choosing the Learning Scheme How to Learn: Never (Wildcard Only) How to Learn: Always How to Learn: Selective Reviewing the Enforcement Readiness Period: Entities Viewing Learning Suggestions and Staging Status Violations Without Learning Suggestions Defining the Learning Score Defining Trusted and Untrusted IP Addresses How to Learn: Compact Module 9: Cookies and Other Headers F5 Advanced WAF Cookies: What to Enforce Defining Allowed and Enforced Cookies Configuring Security Processing on HTTP headers Module 10: Reporting and Logging Overview: Big Picture Data Reporting: Build Your Own View Reporting: Chart based on filters Brute Force and Web Scraping Statistics Viewing F5 Advanced WAF Resource Reports PCI Compliance: PCI-DSS 3.0 The Attack Expert System Viewing Traffic Learning Graphs Local Logging Facilities and Destinations How to Enable Local Logging of Security Events Viewing Logs in the Configuration Utility Exporting Requests Logging Profiles: Build What You Need Configuring Response Logging Module 11: Lab Project 1 Lab Project 1 Module 12: Advanced Parameter Handling Defining Parameter Types Defining Static Parameters Defining Dynamic Parameters Defining Dynamic Parameter Extraction Properties Defining Parameter Levels Other Parameter Considerations Module 13: Automatic Policy Building Overview of Automatic Policy Building Defining Templates Which Automate Learning Defining Policy Loosening Defining Policy Tightening Defining Learning Speed: Traffic Sampling Defining Track Site Changes Lesson 14: Web Application Vulnerability Scanner Integration Integrating Scanner Output Importing Vulnerabilities Resolving Vulnerabilities Using the Generic XML Scanner XSD file Lesson 15: Deploying Layered Policies Defining a Parent Policy Defining Inheritance Parent Policy Deployment Use Cases Lesson 16: Login Enforcement and Brute Force Mitigation Defining Login Pages for Flow Control Configuring Automatic Detection of Login Pages Defining Session Tracking Brute Force Protection Configuration Source-Based Brute Force Mitigations Defining Credentials Stuffing Mitigating Credentials Stuffing Lesson 17: Reconnaissance with Session Tracking Defining Session Tracking Configuring Actions Upon Violation Detection Lesson 18: Layer 7 DoS Mitigation Defining Denial of Service Attacks Defining the DoS Protection Profile Overview of TPS-based DoS Protection Creating a DoS Logging Profile Applying TPS Mitigations Defining Behavioral and Stress-Based Detection Lesson 19: Advanced Bot Protection Classifying Clients with the Bot Defense Profile Defining Bot Signatures Defining Proactive Bot Defense Defining Behavioral and Stress-Based Detection Defining Behavioral DoS Mitigation Lesson 20: Form Encryption using DataSafe Targeting Elements of Application Delivery Exploiting the Document Object Model Protecting Applications Using DataSafe The Order of Operations for URL Classification Lesson 21: Review and Final Labs Review and Final Labs

JSEC - Junos Security
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for The primary audiences for this course are the following: • Operators of Juniper Networks security solutions, including network engineers, administrators, support personnel, and resellers. Overview After successfully completing this course, you should be able to: Identify security challenges in today's networks. Identify products that are incorporated into the Juniper Connected Security solution. Explain the value of implementing security solutions. Explain how Juniper Connected Security solves the cyber security challenges of the future. Explain SRX Series session management. Explain Junos ALG functions and when to use them. Describe policy logging on the SRX series device. Explain security policy scheduling. Describe application security theory. Explain application signature usage in AppID. Describe the AppTrack service. Describe the AppFW service. Describe the AppQoS service. Configure security policies using the AppSecure suite of services. Explain unified security policies. Describe IPS signatures. Configure an IPS policy using pre-defined templates. Describe how to update the IPS attack object database. Describe IPS rules and rule bases. Configure custom attack objects. Describe Junos Space and Security Director. Configure policy management using Security Director. Describe Security Director objects. Explain the different licensing options for Sky ATP List Sky ATP's features and benefits. Configure Sky ATP profiles and enroll an SRX Series device. Configure file scanning on Sky ATP. Configure Sky ATP to scan email Configure GeoIP on Sky ATP. Describe the JATP features and benefits List the JATP device options. Explain the JATP architecture. List 3rd party support options for JATP. Explain JATP SmartCore analytics processes. Describe Policy Enforcer configuration options. Describe Policy Enforcer integration with Sky ATP. Configure Policy Enforcer to block lateral malware movement. Explain Juniper Secure Analytics features and benefits. Describe JSA log collection. Describe JSA network flow collection. Describe the JSA Offense Management workspace. Explain the JSA Risk Manager features. Configure JSA to collect network and log collection. Explain the features of JIMS. Describe JIMS integration into the current AD network. Describe the Sky Enterprise service and how it can save resources. Explain the Sky Enterprise monitoring service. Explain the vSRX Series device benefits. Describe use cases for the vSRX. Explain the cSRX Series device benefits. Describe use cases for the cSRX. Describe SSL Proxy Concepts. Explain Forward and Reverse Proxy and the limitations of each. Configure both Forward and Reverse Proxy. This five-day course uses the Junos J-Web, CLI, Junos Space, and other user interfaces to introduce students to the concept of Juniper Connected Security. Chapter 1: Course Introduction Course Introduction Chapter 2: CLI Overview User Interface Options Command-Line Interface Initial Configuration Interface Configuration Lab 1: CLI Overview Chapter 3: Advanced Security Policy Session Management Junos ALGs Policy Scheduling Policy Logging Lab 2: Advanced Security Policy Chapter 4: Application Security Theory Application ID Application Signatures App Track App Firewall App QoS App QoE Chapter 5: Application Security Implementation AppTrack Implementation AppFW Implementation AppQos Implementation APBR Implementation Lab 3: Application Security Chapter 6: Intrusion Detection and Prevention IPS Overview IPS Policy Attack Objects IPS Configuration IPS Monitoring Lab 4: Implementing IPS Chapter 7: Security Director Overview Security Director Objects Security Director Policy Management Lab 5: Security Director Chapter 8: Sky ATP Implementation Architecture and Key Components Features and Benefits Configuration Compromised Hosts Command and Control File Scanning E-mail Scanning Geo IP Security Policy Integration Troubleshooting Lab 6: Sky ATP Implementation Chapter 9: Policy Enforcer Policy Enforcer Concepts Configuration Options Policy Enforcer Installation Lab 7: Policy Enforcer Chapter 10: JATP Overview Traffic Inspection Threat Detection Threat Analysis JATP Architecture Chapter 11: JATP Implementation Data Collectors Configure SmartCore Analytics Engine Log Ingestion Incident Management SRX Threat Prevention 3rd Party support for Threat Prevention Reporting Lab 8: JATP Chapter 12: Juniper Secure Analytics (JSA) JSA Overview Data Collection Log Analytics Threat Analytics Vulnerability Management Risk Management Lab 9: JSA Chapter 13: JIMS JIMS Overview JIMS Integration Lab 10: JIMS Chapter 14: vSRX and cSRX vSRX Overview vSRX Supported Features vSRX Use Cases cSRX Overview Lab 11: vSRX Installation Chapter 15: SSL Proxy SSL Proxy Overview SSL Concepts SSL Proxy Configurations Troubleshooting Lab 12: SSL Proxy Chapter 16: Cluster Concepts Chassis Cluster Concepts Chassis Cluster Operation Chapter 17: Chassis Cluster Implementation Chassis Cluster Configuration Chassis Cluster Advanced Options Lab 13: Chassis Cluster Implementation Chapter 18: Chassis Cluster Troubleshooting Chassis Cluster Case Studies Troubleshooting Examples Lab 14: Chassis Cluster Troubleshooting Additional course details: Nexus Humans JSEC - Junos Security training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the JSEC - Junos Security course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.
