- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
QLS Endorsed Criminology, Forensic Science and Criminal Psychology - 3 QLS Course
4.7(47)By Academy for Health and Fitness
Feed your curiosity and navigate the captivating world of crime investigation with our eight-course bundle. Break away from the shackles of ordinary knowledge and equip yourself with expertise that goes beyond the conventional! Unearth the fascinating realms of Endorsed Criminology, Forensic Science, and Criminal Psychology with our QLS-endorsed 3-course bundle. Dive into the complex world of crime, not just as an observer, but as a knowledgeable participant. This meticulously crafted curriculum explores the profound depths of criminal minds, revealing patterns, deciphering motives, and learning to navigate the winding roads of criminal law. Specially curated, our bundle includes three prime QLS-endorsed courses - Criminology, Forensic Science Level 3, and Criminal Psychology - Interrogation Techniques. Upon completion, you will be awarded hardcopy certificates, tangible tokens of your mastered knowledge. Key Features of the QLS Endorsed Criminology, Forensic Science and Criminal Psychology - 3 QLS Course Bundle: 3 QLS-Endorsed Courses: We proudly offer 3 QLS-endorsed courses within our QLS Endorsed Criminology, Forensic Science and Criminal Psychology - 3 QLS Course bundle, providing you with industry-recognized qualifications. Plus, you'll receive a free hardcopy certificate for each of these courses. QLS Course 01: Criminology QLS Course 02: Forensic Science Level 3 Course QLS Course 03: Criminal psychology - Interrogation Techniques 5 CPD QS Accredited Courses: Additionally, our bundle includes 5 relevant CPD QS accredited courses, ensuring that you stay up-to-date with the latest industry standards and practices. Course 01: Criminal Law Course 02: Criminal Investigation Course 03: Crime Scene Investigator Course 04: Accident investigation Course 05: Security Management Diploma In Addition, you'll get Five Career Boosting Courses absolutely FREE with this Bundle. Course 01: Professional CV Writing Course 02: Job Search Skills Course 03: Self Esteem & Confidence Building Course 04: Professional Diploma in Stress Management Course 05: Complete Communication Skills Master Class Convenient Online Learning: Our QLS Endorsed Criminology, Forensic Science and Criminal Psychology - 3 QLS Course courses are accessible online, allowing you to learn at your own pace and from the comfort of your own home. Learning Outcomes: Comprehensive understanding of the principles of Criminology, Forensic Science, and Criminal Psychology. Mastery of the latest techniques used in crime scene investigations. Detailed knowledge of criminal law and the skills needed for criminal investigations. Proficiency in accident investigation techniques and security management principles. Adeptness at interpreting and understanding the psychology behind criminal behaviors. Competence in using forensic science in practical criminal investigation scenarios. Proficiency in applying interrogation techniques derived from criminal psychology. Embark on a journey through the labyrinth of criminal minds with our eight-course bundle. Our QLS-endorsed courses in Criminology, Forensic Science, and Criminal Psychology guide you through the theoretical framework of crime investigation. Gain in-depth knowledge of forensic science and criminal law while simultaneously mastering the interrogation techniques used by professionals. Additionally, our CPD QS accredited courses supplement your learning, providing a comprehensive view of the crime investigation field. CPD 250 CPD hours / points Accredited by CPD Quality Standards Who is this course for? Individuals interested in exploring the theoretical depths of criminology, forensic science, and criminal psychology. Law enforcement officers looking to enhance their knowledge base. Professionals in the field of security management seeking advanced training. Students studying criminal law or psychology who wish to specialize in criminal investigation. Career path Criminologist - Average salary in the UK: £35,000 - £39,000 per year. Forensic Scientist - Average salary in the UK: £35,000 - £40,000 per year. Criminal Psychologist - Average salary in the UK: £31,700 - £44,500 per year. Crime Scene Investigator - Average salary in the UK: £20,000 - £30,000 per year. Accident Investigator - Average salary in the UK: £25,000 - £35,000 per year. Certificates Digital certificate Digital certificate - Included Hard copy certificate Hard copy certificate - Included

IT Course
By KEMP CENTER
Develop and improve your IT knowledge and skills and advance your career A comprehensive IT course with both theoretical explanation and practical exercises to teach you, improve your IT skills, and advance your career. The course is delivered by an IT expert trainer with many years of experience in the field of information technology. Successfully complete the practical tasks and tests through the course and the final exam to consolidate your knowledge and skills. We created a professionally designed, advanced IT course to answer all your needs. We created an IT guide for all newcomers in the field and suitable for those already involved in IT service at the same time. It will make you proficient in the most important aspects of IT so you can enjoy limitless career prospects worldwide. The course will be delivered through a multimedia platform Kemp Center and will eventually bring you a valuable certificate of completion. It gives you the opportunity to study at any time in the comfort of your own home and at your own pace from any device that has an internet connection. It is designed for everyone interested in the IT field. The course begins with an introduction to information technology; and then explores computer hardware and software; operating systems, how they interact with computer hardware, and how to start up, install and uninstall the most widely used operating systems today – Windows and Linux. You will also learn about the Internet and networking, database systems and data analytics, the importance of troubleshooting and customer support, information assurance, and security. This course will enrich you with both, theoretical knowledge and practical skills that will help you start your IT career from 0, or to improve further your career getting more advanced IT roles. Join the communication course and get the benefits: Learning from a professional instructor24/7 access from any devicePractical exercisesTests, quizzes and recapsCertificate of completionExtra materials and downloadable bonuses100% satisfaction guarantee Your Singing Instructor: Toni Matthijs IT Expert The Information technology course will be delivered by Toni Matthijs -an IT expert, the best one in the field with many years of experience and an active role in information technology. Our IT expert will introduce you to the world of Information technology very carefully and detailed and will teach you how to properly organize and store data using various telecommunication systems. You will learn about computer hardware and software, about today’s most widely used operating systems: Windows and Linux, about Internet and networking, database systems and data analytics, troubleshooting and customer service, information assurance, and security. Your expert trainer will assist you and guide you through several knowledge repetitions, practical tasks, and tests to make sure you remember all the important information and consolidate your gained knowledge even better. In the end, you will be capable to use everything you learned in practice like an IT master. Overview of the course: Detailed video presentation Practical knowledge about business administration Practical knowledge of information technology, from installing software to managing databases. The course touches on selected topics in IT fundamentals among others: computer hardware and software, operating systems, installing, updating and uninstalling computer software, networking, databases and data analytics, troubleshooting and customer support, information assurance and security. Real examples of IT environment Assembling a computer from scratch, installing operating system on computer, installing, updating and uninstalling software on Windows and Linux, networking, creating database, stages of analytics process, using troubleshooting skills to solve a problem, developing an effective strategy for information assurance and security. Training videos In the course, you will find many training videos and video tutorials that will provide you with deeper knowledge about IT field and with practical IT skills that you can implement in your everyday IT tasks. 1. Hardware This section will introduce you the computer inside. Actually, you will learn all the components or different pieces inside a computer that together present the computer hardware. You will discover the function of each component and how all hardware components work together to make a computer function. By the end of this module, you will be able to build a computer from scratch! 2. Operating system In this section you will become familiar with operating systems, particularly those that are most widely used today and learn how an operating system interacts with computer hardware. 3. Networking This unit will introduce you to computer networking in practical and theoretical way. 4. Software This section focuses on computer software. By the end of this module, you will be able to install, update and remove software on both Windows and Linux operating systems. 5. Data analysis This section gives an overview of the concepts related to data analysis. 6. Troubleshooting and customer support In this section of the course, you’ll learn about the importance of troubleshooting and customer support. By the end of this module, you will utilize soft skills and write documentation to communicate with others. 7. Security and information assurance The last section of the course is a survey of the fundamental elements of computer security and information assurance. Knowledge repetitions and tests Repetitions of acquired knowledge and tests This course begins with a comprehensive introduction to the world of information technology. Through the course, you will have 9 repetitions and 9 tests that will allow you to check the acquired knowledge and better remember the topics discussed in the course. Final test Passing the final test means that you have enough knowledge and skills in the field of information technology and that you became a certified IT, expert. Practical tasks Practical tasks about: Counting in binary Assemble a computer from scratch Choose and install an operating system on a computer IP addressing and sub-netting Installing software on Windows Creating database, importing and exporting information for use in another application Using data to drive successful outcomes Troubleshooting Developing an effective information assurance strategy Bonus materials for the course: Advice on how to develop an effective strategy for information assurance and security A practical guide on how to install, update and uninstall operation systems, software, and other applications on the computer List of practical advice on how to improve your IT skill Practical guide on how to assemble a computer from scratch and how to work with computers successfully A letter from your expert instructor: The world of IT management is growing at a rapid pace and having the right skills and experience can help you develop and further improve your qualifications that will lead you to a lucrative career. We are pleased to present you and invite you to most popular and advanced study program for information technology – IT that aims to prepare you for a role of IT Specialist.In the course, you will be introduced to the world of IT through carefully, detailed developed lessons. The material shared covers plenty of IT topics and is designed to give you deeper knowledge of the IT field. The course will instruct you and teach you how to accomplish common IT tasks with the best tools and resources.This certificate course will equip you with the skills and working practices you need to apply to any IT job and that you need to succeed at all stages of your IT career. It will help you to develop and further improve your knowledge at a range of a master of IT.Investing in yourself is not wasting money and time, but a key for a better future ahead. Enroll our self-paced IT course now and start learning today, so you can benefit tomorrow!Toni Matthijs- IT Expert

Level 7 Diploma in Criminal Intelligence Researcher - QLS Endorsed
By Kingston Open College
QLS Endorsed + CPD QS Accredited - Dual Certification | Instant Access | 24/7 Tutor Support | All-Inclusive Cost

***24 Hour Limited Time Flash Sale*** Coding (C++, Python & JavaScript) Admission Gifts FREE PDF & Hard Copy Certificate| PDF Transcripts| FREE Student ID| Assessment| Lifetime Access| Enrolment Letter Do you dream of building websites, creating games, or analysing data? In the UK, the digital sector is booming, with over 2 million tech jobs and a projected growth of 3% per year. If you're ready to join the wave, this Coding Bundle is your launchpad! Whether you're a complete beginner or have some experience, this comprehensive coding programme equips you with the in-demand skills to thrive in the digital world. This Coding (C++, Python & JavaScript) bundle offers a structured learning journey across three powerhouse languages: JavaScript, C++, and Python. Learn the fundamentals with beginner-friendly coding courses, then focus on advanced concepts like web application security, game development, data visualisation, and machine learning. But that's not all. When you enrol in Coding (C++, Python & JavaScript) Online Training, you'll receive 25 CPD-Accredited PDF Certificates, Hard Copy Certificates, and our exclusive student ID card, all absolutely free. Courses Are Included In this Coding (C++, Python & JavaScript) Career Bundle: Course 01: Coding Essentials - Javascript, ASP. Net, C# - Bonus HTML Course 02: C++ Programming for Absolute Beginners Course 03: C++ Development: The Complete Coding Guide Course 04: Game Development using Cocos2d-x v3 C++ Course 05: Tic-Tac-Toe Clone - The Complete Cocos2d-x C++ Game Course Course 06: Flappy Bird Clone: SFML C++ Game Course 07: Secure Programming of Web Applications Course 08: Python Basic Programming for Absolute Beginners Course 09: Python Programming Bible Course 10: Python Masterclass: Advanced Diploma Course 11: Machine Learning with Python Course Course 12: Python Programming from Scratch with My SQL Database Course 13: JavaScript Foundations for Everyone Course 14: JavaScript Advanced Training Course 15: Master JavaScript with Data Visualization Course 16: JavaScript Project Development - Creating Web Apps Course 17: Understanding Data Protection and Data Security Course 18: Computer Networks Security from Scratch to Advanced Course 19: Essential IT Skills Level 2 Course 20: IT Support Technician Course 21: Functional Skills IT Course 22: Basics of Network Security Course 23: IT: Ethical Hacking & IT Security Course 24: Learning Computers and Internet Course 25: Internet of Things With Coding (C++, Python & JavaScript), you'll embark on an immersive learning experience that combines interactive lessons with voice-over audio, ensuring that you can learn from anywhere in the world, at your own pace. And with 24/7 tutor support, you'll never feel alone in your journey, whether you're a seasoned professional or a beginner. Learning Outcomes of this Bundle Grasp core coding principles in JavaScript, Python, and C++. Build functional web applications using ASP.Net and JavaScript. Develop engaging games with Cocos2d-x and SFML. Leverage Python for data analysis and machine learning. Implement secure coding practices for web applications. Confidently navigate the vast world of coding with expert guidance. Don't let coding skills hold you back from your dream career. Enrol in Coding (C++, Python & JavaScript) today and take the first step towards achieving your goals and dreams. Why buy this Coding (C++, Python & JavaScript)? Free CPD Accredited Certificate upon completion of this Bundle Get a free student ID card with this Bundle Lifetime access to the course materials Get instant access to this Bundle course Learn from anywhere in the world 24/7 tutor support with this Bundle course. Start your learning journey straightaway with our Coding (C++, Python & JavaScript) Training! Coding (C++, Python & JavaScript) premium bundle consists of 25 precisely chosen courses on a wide range of topics essential for anyone looking to excel in this field. Each segment of Coding (C++, Python & JavaScript) is meticulously designed to maximise learning and engagement, blending interactive content and audio-visual modules for a truly immersive experience. Certification of Coding (C++, Python & JavaScript) You have to complete the assignment given at the end of the Coding (C++, Python & JavaScript) course. After passing the Coding (C++, Python & JavaScript) exam You will be entitled to claim a PDF & Hardcopy certificate accredited by CPD Quality standards completely free. CPD 250 CPD hours / points Accredited by CPD Quality Standards Who is this course for? This Coding (C++, Python & JavaScript) course is ideal for: Students seeking mastery in Coding (C++, Python & JavaScript) Professionals seeking to enhance Coding (C++, Python & JavaScript) skills Individuals looking for a Coding (C++, Python & JavaScript)-related career. Anyone passionate about Coding (C++, Python & JavaScript) Requirements This Coding (C++, Python & JavaScript) doesn't require prior experience and is suitable for diverse learners. Career path This Coding (C++, Python & JavaScript) bundle will allow you to kickstart or take your career in the related sector to the next stage. Web Developer Data Analyst Software Engineer Game Developer Machine Learning Engineer Full-Stack Developer Certificates CPD Accredited Digital Certificate Digital certificate - Included CPD Accredited Hard copy certificate Hard copy certificate - Included If you are an international student, then you have to pay an additional 10 GBP for each certificate as an international delivery charge.

Airport Management - QLS Level 5 Diploma
By Imperial Academy
Level 5 QLS Diploma | QLS Certificate Included | 10 CPD Courses & PDF Certificates | 145 CPD Points | Lifetime Access

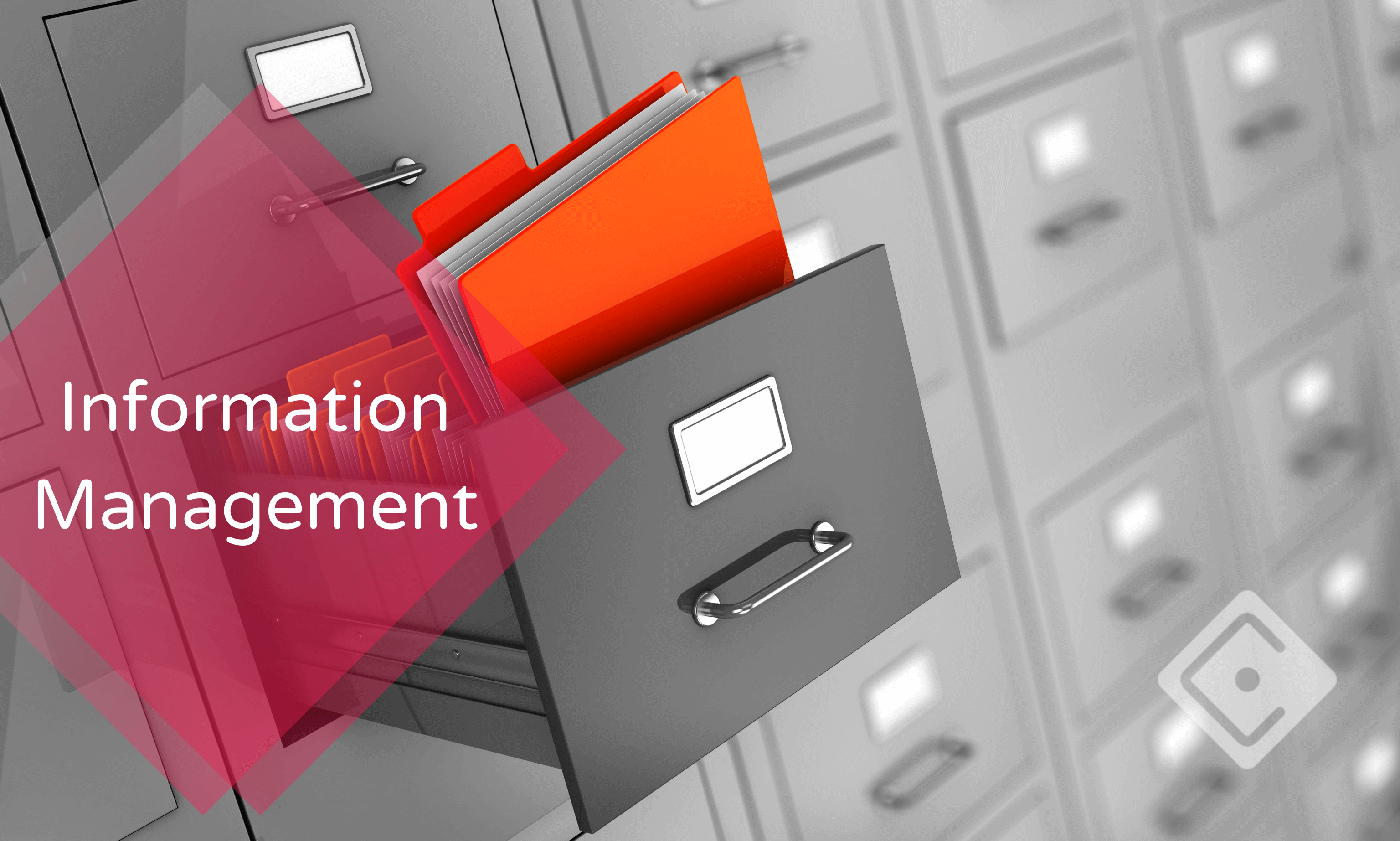
Imagine yourself being an expert in information management when the entire world is drowning in data. Indeed, it will give you an edge in multiple industries if you can gain concrete skills in this field. This information management course has been designed to equip you with all the basic knowledge to start your pathway to becoming an industry leader in the data sector. Picture the first module as your grand entry into the world of data. Here, you will be introduced to the fundamentals terminology. Plus, you will also get insights into how data is critical to business growth. The second module 2 of this course will teach you about the strategies for managing information. Understanding this module will help you sync information and manage goals with the organisation's primary mission. Plus, you will learn strategic planning, creating a roadmap of data to action, and data governance. In module 3, you will explore database systems, design, and data storage. Here, you will also have an idea about the NoSQL databases. Module 5 sheds light on auditing information systems. It will help you determine the tools and techniques to evaluate data reliability. Here, you will learn audit principles, planning, risk assessment, and procedures. The final module of this course focuses on ethical considerations related to data management. The key concepts you will learn here are ethical framework, data privacy laws, data ethics, and data protection strategies. At the end of this module, you can ensure responsible data handling and robust data protection management. Enrol in this top-notch information systems management course to secure yourself in a job market with an average salary of £39,000 per year in the UK. Learning Outcome Gain proficiency in analysing and interpreting data for decision-making Build a strategic mindset to prepare an excellent information strategy Acquire skills to ensure efficient data storage plus retrieval Ability to use MIS to assist managerial decision-making Develop auditing skills to ensure compliance, security, data integrity Have a clear understanding of ethical awareness related to data Career path Data Analyst Information Security Specialist Database Administrator IT Project Manager Chief Information Officer Business intelligence analyst Course Curriculum Module 01: Introduction to Information Management Introduction to Information Management 00:32:00 Module 02: Information Management Strategy Information Management Strategy 00:17:00 Module 03: Databases and Information Management Databases and Information Management 00:29:00 Module 04: Management Information Systems (MIS) Management Information Systems (MIS) 00:16:00 Module 05: Auditing Information Systems Auditing Information Systems 00:16:00 Module 06: Ethical and Social Issues and Data Protection Ethical and Social Issues and Data Protection 00:27:00 Certificate and Transcript Order Your Certificates or Transcripts 00:00:00
If you are struggling with your computer and don't know how to maintain its usability, then your business will inevitably be affected. The reason could simply be a virus. A virus will work as a component that will constitute harm to your hard disk or will meddle with the normal operational executions of the computer. Thus, it will make the computer be not able capacity appropriately until the virus is deleted and your computer is upgraded and rebooted. Having a virus on a computer is a nuisance since it will meddle with your files, programs and everything they can in the computer. Viruses are regularly checked, and computers are updated to avoid these to happen and lessen its hindering impacts to your business. There is no sound approach to distinguish how a virus truly attacks and spreads or how it is distributed without you knowing but a considerable counter preventive measure is needed to put into how to guarantee the harm done is not as big as it is expected it is. Who is the course for? Employees of the business industry and other businessmen who want to learn how to solve the virus issues of their computers. People who have an interest in Computers and how to save themselves from viruses and how to effectively communicate with their potential clients through the web. Entry Requirement: This course is available to all learners, of all academic backgrounds. Learners should be aged 16 or over to undertake the qualification. Good understanding of technology, numeracy and ICT are required to attend this course. Assessment: At the end of the course, you will be required to sit an online multiple-choice test. Your test will be assessed automatically and immediately so that you will instantly know whether you have been successful. Before sitting for your final exam you will have the opportunity to test your proficiency with a mock exam. Certification: After you have successfully passed the test, you will be able to obtain an Accredited Certificate of Achievement. You can however also obtain a Course Completion Certificate following the course completion without sitting for the test. Certificates can be obtained either in hard copy at a cost of £39 or in PDF format at a cost of £24. PDF certificate's turnaround time is 24 hours and for the hardcopy certificate, it is 3-9 working days. Why choose us? Affordable, engaging & high-quality e-learning study materials; Tutorial videos/materials from the industry leading experts; Study in a user-friendly, advanced online learning platform; Efficient exam systems for the assessment and instant result; The UK & internationally recognized accredited qualification; Access to course content on mobile, tablet or desktop from anywhere anytime; The benefit of career advancement opportunities; 24/7 student support via email. Career Path: Understanding Computer Virus course will be very beneficial and helpful, especially to the following careers: Businessman Computer Technician Computer Engineers Marketing Managers Product Creators Programmers Sales Managers Sales and Promotions Specialists Top Executives Website Developer. Understanding Computer Virus What Is A Computer Virus? 01:00:00 How Are Viruses Spread? 01:00:00 How Bad Can A Virus Attack Be? 01:00:00 What Is A Malware? 01:00:00 Getting The Right Anti-Virus For Pc 01:00:00 Removing The Computer Virus Automatically 01:00:00 Deleting The Computer Virus Manually 01:00:00 Enhance Security With A firewall 01:00:00 Tips For Protecting Your Computer From Viruses 01:00:00 How To Identify A Dangerous Website 01:00:00 Wrapping Up 00:15:00 Mock Exam Mock Exam- Understanding Computer Virus 00:20:00 Final Exam Final Exam- Understanding Computer Virus 00:20:00 Certificate and Transcript Order Your Certificates and Transcripts 00:00:00

Amazon VPC Mastery for AWS Certifications
By Packt
Learning AWS VPC would be your stepping stone into an AWS career. A good understanding of VPC and its components is a MUST going into any AWS certification. Get started with Amazon VPC and prepare for certification with the help of this comprehensive course. There are no prerequisite requirements for this course.

JEX - Junos Enterprise Switching using Enhanced Layer 2 Software
By Nexus Human
Duration 2 Days 12 CPD hours This course is intended for This program is designed for students who have attended successfully the IJOS and JRE courses (prior to April 1, 2017) or the IJOS course (since April 3, 2017) and are working toward JNCIA-JUNOS certification. Overview The objectives for this course follow the requirements for the current JNCIA-JUNOS. At the end of this course, the successful student will be able to: Identify the concepts and functionality of various fundamental elements of networking Identify the concepts, benefits and functionality of the core elements of the Junos OS Identify the concepts, operation and functionality of the Junos user interfaces Identify the main elements for configuring Junos devices Describe how to configure basic components of a Junos device Identify methods of monitoring and maintaining Junos devices Describe monitoring and maintenance procedures for a Junos device Identify basic routing concepts and functionality for Junos devices Describe how to configure and monitor basic routing elements for a Junos device Identify the concepts and functionality of routing policy and firewall filters on Junos devices Describe how to configure and monitor routing policies and firewall filters on a Junos device Apply knowledge of Junos operating system configuration, operations, and functionality to real-world scenarios This two-day course provides students with intermediate switching knowledge and configuration examples using Junos Enhanced Layer 2 Software. Chapter 1: Course Introduction Course Introduction Chapter 2: Layer 2 Switching Ethernet Bridging Basics Terminology and Design Considerations Overview of Enterprise Switching Platforms Enabling and Monitoring Layer 2 Switching Operations Lab 1: Implementing Layer 2 Switching Chapter 3: Virtual Networks Overview of VLANs Configuring and Monitoring VLANs Voice VLAN Native VLAN Routed VLAN Interfaces Lab 2: Implementing Virtual Networks Chapter 4: Routing Instances Routing Instances Overview Configuring and Monitoring Virtual Switches Chapter 5: Spanning Tree Spanning Tree Protocol Rapid Spanning Tree Protocol Configuring and Monitoring STP and RSTP Protection Features: BPDU Protection Protection Features: Loop Protection Protection Features: Root Protection Lab 3: Implementing Spanning Tree Chapter 6: Port Security MAC Limiting Persistent MAC Learning DHCP Snooping Dynamic ARP Inspection (DAI) IP Source Guard Lab 4: Implementing Port Security Chapter 7: Device Security and Firewall Filters Storm Control Firewall Filters Lab 5: Implementing Storm Control and Firewall Filters Chapter 8: Virtual Chassis Overview of Virtual Chassis Configuring and Monitoring a Virtual Chassis Lab 6: Implementing a Virtual Chassis System Chapter 9: High Availability Features Overview of High Availability Networks Link Aggregation Groups Redundant Trunk Groups Graceful Routing Engine Switchover (GRES) Nonstop Active Routing (NSR) Nonstop Bridging (NSB) Lab 7: Implementing High Availability Features

BOE310 SAP BusinessObjects Business Intelligence Platform - Administration and Security
By Nexus Human
Duration 2 Days 12 CPD hours This course is intended for System administrators Overview Prepare you to perform key administrative tasks in SAP BusinessObjects Business Intelligence platform to manage users, groups, and objects, and to distribute contents to users. In this course, students perform key administrative tasks in SAP BusinessObjects Business Intelligence platform to manage users, groups, and objects, and to distribute contents to users. SAP BusinessObjects Business Intelligence (BI) Platform Identifying the Components of the SAP BusinessObjects Business Intelligence BI Platform Content and Objects in the SAP BusinessObjects Business Intelligence (BI) Platform Viewing and Modifying Objects in the BI Platform Organizing Objects in the BI Platform Searching for Content in the BI Platform User and User Group Security in the SAP BusinessObjects Business Intelligence (BI) Platform Setting Up Users and Groups Administering Rights Application Security in the SAP BusinessObjects Business Intelligence (BI) Platform Managing Access to Applications Securing Applications Content Distribution Using Scheduling and Alerting Scheduling Objects Managing Instances Managing Calendars Managing Events Configuring Alerts and Alerting Publications and Publishing Designing Publications Additional course details: Nexus Humans BOE310 SAP BusinessObjects Business Intelligence Platform - Administration and Security training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the BOE310 SAP BusinessObjects Business Intelligence Platform - Administration and Security course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.
