- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
26475 Courses delivered Online
Data Protection & Cyber Security Course: Remaining Compliant Against Today's Risks
By DG Legal
The professional working world has changed more rapidly than could have been envisaged at the time of the introduction of GDPR and the Data Protection Act 2018. With more people working from home post-Covid and the ever increasing risk of cyber-attacks, this short course is aimed at taking stock of current practice and risk, as well as considering ICO enforcement action and the implications of hybrid working. It is also a great recap on the rules as they stand and what you need to know to comply. The course will cover: UK GDPR - A timely reminder of the rules ICO enforcement action and what we can learn Data Protection Impact Assessments - when and how to do them Hybrid working and UK GDPR Managing cyber attacks from a UK GDPR perspective Target Audience The online course is suitable for staff of all levels, from support staff to senior partners. Resources Course notes will be provided to all delegates which may be useful for ongoing reference or cascade training. Please note a recording of the course will not be made available. Speaker Matthew Howgate, Consultant, DG Legal Matt is a non-practising solicitor who has considerable experience in regulatory issues and advising on complex issues of compliance and ethics. He is also an expert in data protection, UK GDPR and on the civil legal aid scheme. Matthew is a lead trainer on and co-developed the LAPG Certificate in Practice Management (a training programme for legal managers and law firm owners) as well as regularly providing training on legal aid Supervision, costs maximisation, data protection and security and on general SRA compliance.

ONE SPACE LEFT! 15th September Lil Chase #Agent121. Looking for: PICTURE BOOKS, CHAPTER BOOKS, MG, YA
5.0(3)By I Am In Print
LOOKING FOR: PICTURE BOOKS, CHAPTER BOOKS, MG, YA Lil is a Senior Editor at Hachette Children's. She has well over 15 years experience in the publishing industry, working for major publishers and literary agents too. For twelve years, Lil was a Senior Commissioning Editor at Working Partners Ltd – the creatives behind massive commercial hits such as Beast Quest, Warriors and the Daisy Meadows series. There she created globally successful concepts for every age group and developed storylines so the books were unputdownable. Lil is also an author in her own right: she has written 6 books under her own name, and ghost written many others under various pseudonyms. In every age level, Lil would like to see originality - particularly in voice. A strong character with depth, venturing on a quest that's never been undertaken before will get her excited. The 'quest' doesn't have to be epic in scale, it could be as small as petting the next-door neighbour's dog, or getting the good looking new kid to notice you, it just has to be something a reader will want to invest in. She also loves humour and is happy to see anything quirky (perhaps even downright silly!). For picture books, Lil would like you to submit a covering letter, and 1 complete manuscript, double-spaced, with spreads marked out, in a single word or PDF doc. For chapter books, MG and YA, please send a covering letter, the first three chapters and a synopsis, double spaced, in a single Word or PDF doc. Please send EITHER picture books OR another genre, not both in one submission. By booking this session you agree to email your material to reach I Am In Print by the stated submission deadline to agent121@iaminprint.co.uk. Please note that I Am In Print take no responsibility for the advice given in your Agent121. The submission deadline is: Monday 8th September 2025

24 Hour Flash Deal **25-in-1 Diploma in User Experience Design Mega Bundle** Diploma in User Experience Design Enrolment Gifts **FREE PDF Certificate**FREE PDF Transcript ** FREE Exam** FREE Student ID ** Lifetime Access **FREE Enrolment Letter ** Take the initial steps toward a successful long-term career by studying the Diploma in User Experience Design package online with Studyhub through our online learning platform. The Diploma in User Experience Design bundle can help you improve your CV, wow potential employers, and differentiate yourself from the mass. This Diploma in User Experience Design course provides complete 360-degree training on Diploma in User Experience Design. You'll get not one, not two, not three, but twenty-five Diploma in User Experience Design courses included in this course. Plus Studyhub's signature Forever Access is given as always, meaning these Diploma in User Experience Design courses are yours for as long as you want them once you enrol in this course This Diploma in User Experience Design Bundle consists the following career oriented courses: Course 01: Advanced Diploma in User Experience UI/UX Design Course 02: Web Design for Beginners: Build Websites in HTML & CSS Course 03: JavaScript Foundations Course 04: Responsive Web Design Course 05: Information Architecture (IA) Fundamentals for Website Design Course 06: Digital Art - Sketching In Photoshop Course 07: ASP.Net MVC and Entity Framework Course 08: Info Graphics Web Design - Affinity Designer Training Course 09: Web Design with Adobe XD Course 10: Diploma in Adobe Illustrator Course 11: jQuery Masterclass Course: JavaScript and AJAX Coding Bible Course 12: Animation Designer (Drawings, Timing, Overlapping, Coloring) Course 13: Adobe After Effects CC: Learn To Create Gradient Animations Course 14: Basics of WordPress Course 15: Shopify: A step by Step Guide to Creating an Online Store Course 16: Learn MySQL from Scratch Course 17: PHP Web Development with MySQL Course 18: Learn Spring & Angular Material with a Full Web Application Course 19: Node JS: API Development with Swagger Interface Description Language Course 20: Python Basic Programming for Absolute Beginners Course 21: Data Analysis, Automating and Visualisation in Excel Course 22: Digital Painting Course Course 23: Digital Media & Interaction Design Diploma Course 24: Customer Relationship Management (CRM) Course 25: Professional Digital Marketing Diploma The Diploma in User Experience Design course has been prepared by focusing largely on Diploma in User Experience Design career readiness. It has been designed by our Diploma in User Experience Design specialists in a manner that you will be likely to find yourself head and shoulders above the others. For better learning, one to one assistance will also be provided if it's required by any learners. The Diploma in User Experience Design Bundle is one of the most prestigious training offered at StudyHub and is highly valued by employers for good reason. This Diploma in User Experience Design bundle course has been created with twenty-five premium courses to provide our learners with the best learning experience possible to increase their understanding of their chosen field. This Diploma in User Experience Design Course, like every one of Study Hub's courses, is meticulously developed and well researched. Every one of the topics is divided into Diploma in User Experience Design Elementary modules, allowing our students to grasp each lesson quickly. The Diploma in User Experience Design course is self-paced and can be taken from the comfort of your home, office, or on the go! With our Student ID card you will get discounts on things like music, food, travel and clothes etc. In this exclusive Diploma in User Experience Design bundle, you really hit the jackpot. Here's what you get: Step by step Diploma in User Experience Design lessons One to one assistance from Diploma in User Experience Designprofessionals if you need it Innovative exams to test your knowledge after the Diploma in User Experience Designcourse 24/7 customer support should you encounter any hiccups Top-class learning portal Unlimited lifetime access to all twenty-five Diploma in User Experience Design courses Digital Certificate, Transcript and student ID are all included in the price PDF certificate immediately after passing Original copies of your Diploma in User Experience Design certificate and transcript on the next working day Easily learn the Diploma in User Experience Design skills and knowledge you want from the comfort of your home CPD 250 CPD hours / points Accredited by CPD Quality Standards Who is this course for? This Diploma in User Experience Design training is suitable for - Students Recent graduates Job Seekers Individuals who are already employed in the relevant sectors and wish to enhance their knowledge and expertise in Diploma in User Experience Design Level 8 Diploma User Experience Design Professional Certification in User Research Please Note: Studyhub is a Compliance Central approved resale partner for Quality Licence Scheme Endorsed courses. Requirements To participate in this Diploma in User Experience Design course, all you need is - A smart device A secure internet connection And a keen interest in Diploma in User Experience Design Career path You will be able to kickstart your Diploma in User Experience Design career because this course includes various courses as a bonus. This Diploma in User Experience Design is an excellent opportunity for you to learn multiple skills from the convenience of your own home and explore Diploma in User Experience Design career opportunities. Certificates CPD Accredited Certificate Digital certificate - Included CPD Accredited e-Certificate - Free CPD Accredited Hardcopy Certificate - Free Enrolment Letter - Free Student ID Card - Free

LOOKING FOR: ADULT FICTION Clare set up the Liverpool Literary Agency in 2020 to help address inequality and underrepresentation in the publishing industry. With more than 15 years’ experience of writing and editing professionally, including the publication of two novels, Definitions (2015) and We Are of Dust (2018 - which has received development funding from the Liverpool Film Office for a TV adaptation), she has developed an in-depth knowledge of what commissioning editors and publishers expect to see from a submitted manuscript. With a background in PR and marketing, alongside teaching on creative writing programmes, Clare also has extensive experience in pitching and promoting writers and has been nominated for the Romantic Novelist Association Agent of the Year Award! Clare would love to see historical fiction, crime fiction, psychological thrillers and women’s fiction, but she is open to all great writing with a strong hook in any area (excluding non-fiction, children’s and YA). She actively encourages submissions from writers who have been traditionally under-represented. Clare would like you to submit a covering letter, 1 page synopsis and the first 5,000 words of your manuscript in a single word document. (In addition to the paid sessions, Clare is kindly offering one free session for low income/under-represented writers. Please email agent121@iaminprint.co.uk to apply, outlining your case for this option which is offered at the discretion of I Am In Print). By booking you understand you need to conduct an internet connection test with I Am In Print prior to the event. You also agree to email your material in one document to reach I Am In Print by the stated submission deadline and note that I Am In Print take no responsibility for the advice received during your agent meeting. The submission deadline is: Wednesday 10th September 2025

Beginner Celtic Knot Workshop
By Panda Scribes
Introduction to Celtic Knots – Live Zoom Session Join me for a relaxing and creative hour-long Zoom session where you'll learn the basics of how to create beautiful Celtic knots. Perfect for beginners, this introduction will guide you through simple techniques to start drawing your own intricate designs. No prior experience needed—just bring a pencil, paper, and your curiosity!

Course Summary: This workshop aims to increase awareness of Safeguarding and Protecting Children, helping coaches to recognise signs of abuse and poor practice, and deal sensitively and effectively with issues that arise. It also prompts a review of coaching practice to ensure that sport provides a positive and enriching experience for children. The 3 hour workshop covers the following and learners will be able to: Identify and recognise good coaching practice and the implications for them. Explore their values and feelings in relation to child abuse, and recognise how these may potentially impact on their response. Recognise and respond to the signs and symptoms of child abuse and poor practice. Take appropriate action if concerns about a child arise. If you require a group booking for your staff/volunteers, please select group booking to request a private group session. This option will require a minimum of 8 delegates. If we do not have 8 delegates the course will be rearranged for a later date.

Certificate in UX Design Fundamentals
By UX Design Institute
A comprehensive introduction to UX design. Learn the key principles and concepts behind the UX process. Take your first steps into UX Whether you want to explore UX as a career or expand your professional skillset, this UX design fundamentals course is the perfect starting point. Follow 65 expert lessons that will immerse you in the theory and principles of UX Design Learn about the techniques that underpin the UX process, like user research, affinity diagrams, and prototyping Earn a globally recognised and university credit-rated professional qualification Who is it for? Anybody who needs to understand UX Format Online, self-paced Duration 6 weeks (recommended) Commitment 3 hours per week How you’ll benefit If you want to really understand UX, this UX design fundamentals course for you. Speak confidently about UX design Develop a mindset for problem-solving Learn to advocate for the user - and make better business decisions as a result Become a more rounded, valuable professional Showcase your knowledge with a university credit-rated certificate Learn the key UX design fundamentals concepts in just six weeks. Everything you need to truly grasp UX, over five engaging modules. Module 1 Introduction to UX design Gain a comprehensive overview of the UX design process. Module 2 User research methods Learn how to gain deep insights into customer needs and behaviours. Module 3 Analysis techniques Discover how research gets translated into actionable insights. Module 4 Defining the experience Explore problem-solving techniques and design principles. Module 5 Prototyping techniques Understand the different forms of prototyping and when to use them. Exam 40-minute final exam Get assessed on your knowledge through a final exam.

At Noble, we deliver the SLII programme as either an in person or virtual programme. Option 1 - a two-day session, in person at North Scare - 9th & 23rd October, 9am to 4.30pm. Option 2 - 5 x two & a half hour virtual sessions via Zoom. We blend self-directed learning, online discussions, interactive exercises, reflection, and offline assignments with a comprehensive personal leadership assessment/360 feedback tool. Programme Overview Create individual success with a situational approach to leadership. With business moving at a blistering pace, there’s more pressure than ever for leaders to be effective at managing successful teams. But often, they don’t have the skills to be the agile, adaptive leaders they need to be, and they struggle to build meaningful connections and achieve results. It’s not for lack of effort or interest. Research has shown that most leaders are limited to a single leadership style—so they don’t know how to unleash the potential of their people as their needs shift. Leaders need to learn how to lead situationally. Blanchard’s SLII® empowers leaders to become adaptive—a requirement for our uncertain times. Backed by 40 years of research and an unmatched track record of results, The SLII Experience™ teaches your leaders how to lead situationally by giving their people the right support and direction at the right time. SLII enables leaders to build deeper relationships with their people, making every day more inspiring, motivating, and meaningful.

Unlocking Our-Selves 2025: "Away With the Fairies"
By Therapy Harley Street
Personal development groups for practitioners with Bárbara Godoy A playground for therapists to expand our perception to metaphor, as a way to connect directly with the experience of the other, guided by folklore and fairytales. "Supportive, thought-provoking, emancipating, grounding" Tuesday Evenings Group 6 pm to 7.15 pm (UK Time) Friday Lunchtime Group 12.30 pm to 1.45 pm (UK time) Spring Term Phase One - 2025 22 and 29 April 6, 13, 20 and 27 May 3, 10, 17 and 24 June Autumn Term Phase Two - 2025 23 and 30 September 7, 14, 21 and 28 October 4, 11, 18 and 25 November Winter Term Phase Three - 2026 20 and 27 January 3, 10, 17 and 24 February 3, 10, 17 and 24 March Winter Term Phase One - 2025 24 and 31 January 7, 14, 21, 28 February 7, 14, 21 and 28 March Spring Term Phase Two - 2025 25 April 2, 9, 16, 23 and 30 May 6, 13, 20 and 27 June Autumn Term Phase Three - 2025 26 September 3, 10, 17, 24 and 31 October 7, 14, 21 and 28 November Venue: Online (Zoom) Fee: £350 per term or £900 the whole year Bárbara Godoy M.A., Adv. Dip. Exi. Psy. Existential Psychotherapist Group Leader, Counsellour, Lecturer and Supervisor, MBACP & UKCP accredited, SEA Professional Member, Director of Therapy Harley StreetBárbara’s academic contributions in London since 2008 include lecturing and researching on the theory and practice of Phenomenological Existential Therapy on Doctorate, MA and professional courses at the School of Psychotherapy and Counselling Psychology, Regent’s University and the New School of Psychotherapy and Counselling directed by Emmy van Deurzen. Bárbara has facilitated and designed therapeutic Group Work since 1997. She brought her earliest workshop: “Experiences” to large groups in The Netherlands, Italy, France, UK and Argentina. These awareness-intensive processes are a legacy of the human potential movement (HPM) of the 1960s, with techniques such as AUM Meditation Marathons, Psychodrama, Bioenergetics and Primal Feelings work. Organized by:

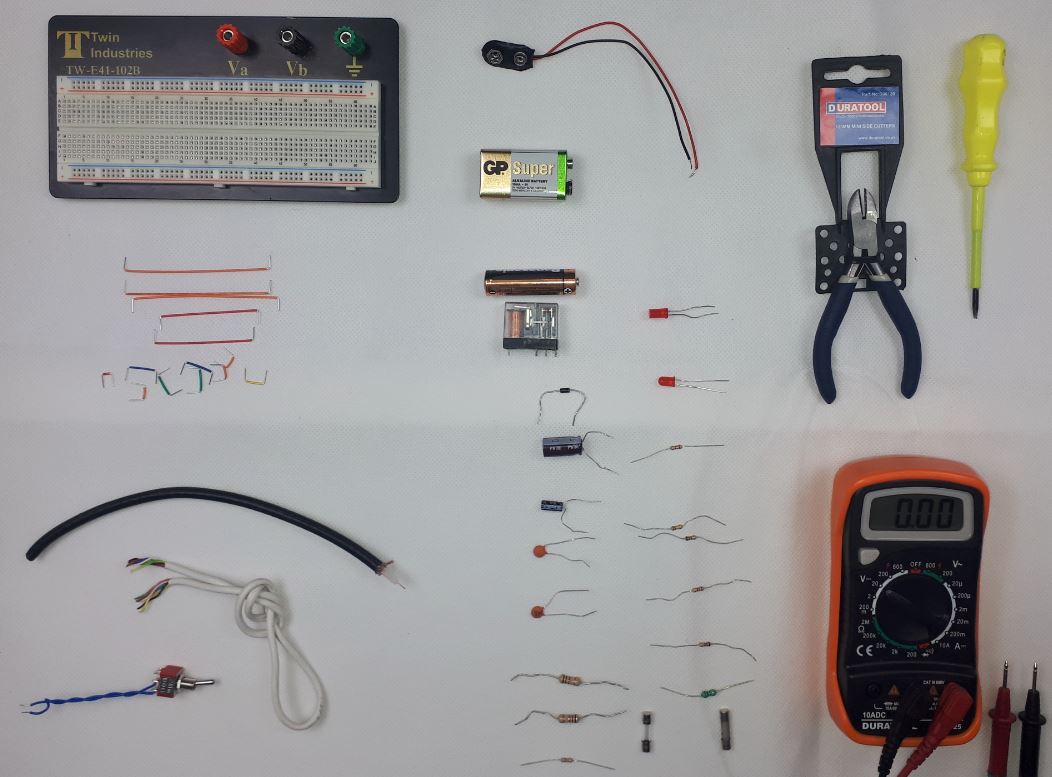
Preliminary Electronic Security Course
By Hi-Tech Training
The Preliminary Electronic Security Course is an introductory (or revision) course designed to provide participants who have no previous Electrical or Electronics experience with the background skills required to attend the CCTV Installation Course, Access Control Course or Fire Alarm Foundation Course. The course gives both an introduction to electronics and electronic security and shows how the two fields merge together. Ideal for a beginner wishing to learn more about this fascinating area. A large practical content is guaranteed. The day will be an excellent learning experience with a skilled instructor. It is a great introduction to the other courses we provide.