- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
1174 Courses delivered Live Online
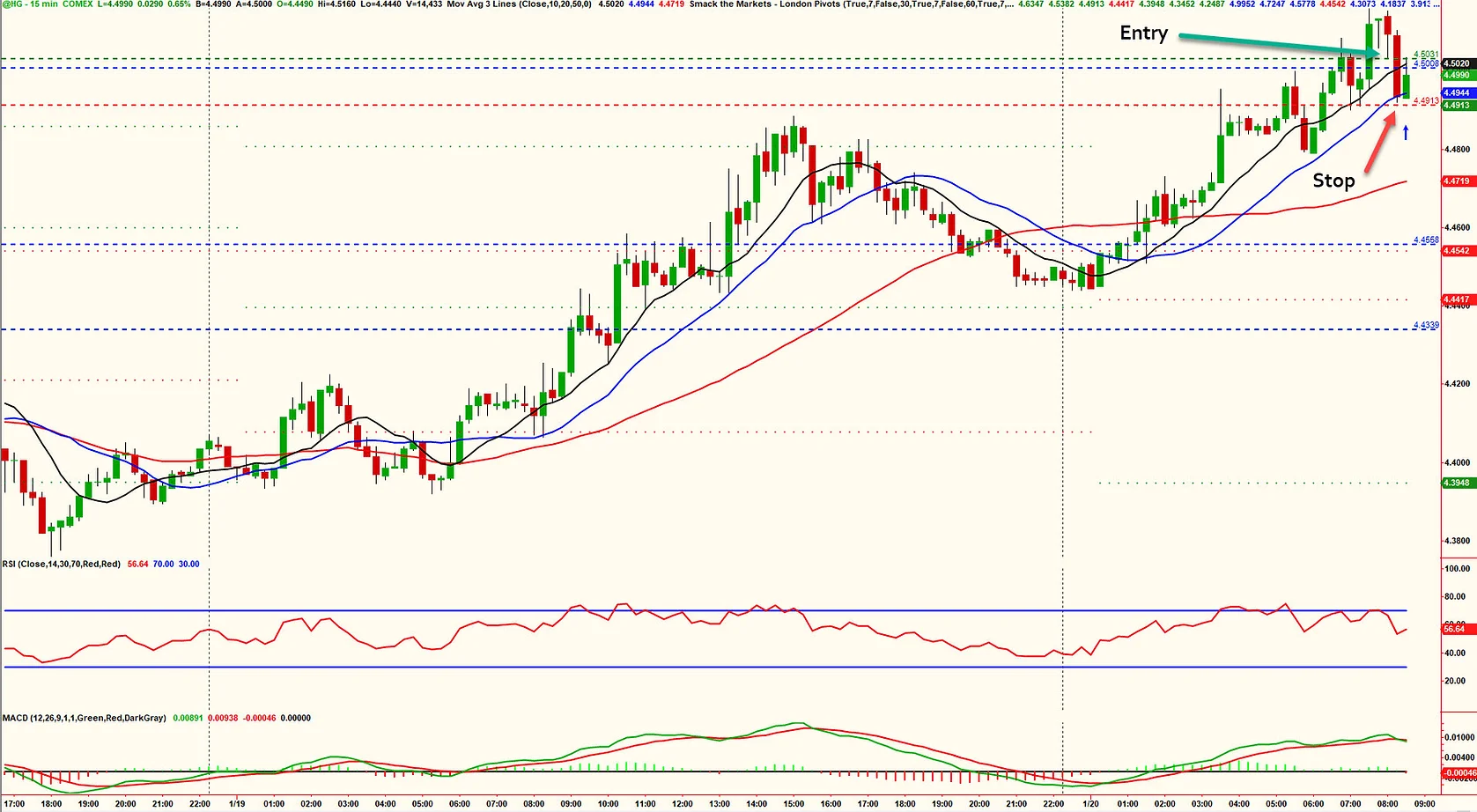
ONE-TO-ONE BESPOKE TRADER TRAINING
By Smack The Markets
At Smack the Markets we offer a different way for serious traders who want a bespoke and personal approach to learning to trade. We work with a small number of new traders on a one-to-one basis at a time. This enables us to develop a program completely around you, whether you’re brand new to this business and need to start from scratch, or you have some experience but need to unlearn what’s not working and relearn new skills that do work. Because your requirements may be unique, our bespoke programs are flexible too. We aim to work with new traders over the long term (typically as long as a year) to ensure you’ve mastered the skills and techniques we’ve taught, and also to ensure you can apply them effectively in different market conditions. Our typical one-to-one programs will consist of weekly live online workshops covering the trading skills and techniques you need, moving gradually to monthly coaching and mentoring sessions as you become more proficient in trading on your own. Our style of trading incorporates a combination of fundamental and technical analysis to read the markets, using one of four technical trading strategies to execute trade positions. Our strategies are suitable for all liquid markets including Indices, Forex, Commodities and Stocks. All our bespoke programs include some access to our online trading room, so you can observe how we are using the same techniques to trade the markets ourselves. Once you have gained suitable experience in our trading methods and have a good understanding of risk management, you will be offered full membership, which will give you permanent access to the trading room and other membership services should you wish. As a guild our bespoke one-to-one programs can range from 5 to 15+ individual sessions with prices ranging in the region of £1,500.00 to £3,000.00 depending on your requirements and current trading experience. If you would like to discuss our bespoke one-to-one programs further, please get in touch to arrange a no obligation consultation with our head trader.
Take Control Of The Digital Transformation
By Nexus Human
Duration 1.75 Days 10.5 CPD hours This course is intended for The course is aimed at experienced project managers, business management and specialists in both private and public companies. A good understanding of the basic mechanisms in organisations and markets is required. Overview Knowledge of the 4 dimensions needed for efficient business transformation and digital transformation: Platform, Planning, People and Processes Be able to look at your own organisation in an outside-in perspective Insight into the journey from a precise project scope to the project's components of work packages and to the following organisational implementation Ability to define precise digital service processes Understanding of business and organisational dynamics Tools to break down a defined business algorithm to specific specifications for an IT project Transformation Framework integrates well known management theory with common project management methods. Provides access to a unique and coherent toolbox and IT workbench, which includes the ability to transform digital strategies. The Structure Of 4Dimensions Framework The Digital Ecosystem Organisational setup Structure of the Business Platform Understanding of the course goal The 4D Framework Platform Dimension Plan Dimension People Dimension Working with the framework Views Approaches Wrap up of the day How To Work With 4Dimensions Framework Wrap up of day 1 Toolbox Change sheets Agile Transformation Plan Case work How to use the transformation tool 4dimensions.info How to succeed with the transformation Transformation roles How to get started

Oral Health Care
By NextGen Learning
Course Overview: The "Oral Health Care" course is designed to provide a comprehensive understanding of the essential concepts and practices in maintaining optimal oral health. Learners will explore a wide range of topics, from the basics of oral hygiene to the management of common oral health issues and preventive strategies. The course equips learners with the knowledge necessary to support dental care practices effectively. By the end of the course, participants will have developed a solid understanding of oral health, preventive care, and the importance of ongoing maintenance. This course offers valuable insights for those looking to advance their knowledge in dental care or enhance their qualifications in the health sector. Course Description: This course covers a range of topics designed to enhance learners' understanding of oral health care. Modules will guide participants through the fundamentals of oral health, common issues like tooth decay and gum disease, and preventive dentistry techniques. Emphasis is placed on promoting oral health, particularly in children and special populations. Learners will gain insights into the relationship between diet and oral health, as well as the importance of ongoing maintenance to prevent future complications. By completing this course, learners will be prepared to contribute to effective oral health care strategies and will acquire valuable knowledge to apply in various healthcare and dental settings. Course Modules: Module 01: Introduction to Oral Health Care Module 02: Fundamentals of Oral Health Module 03: Common Oral Health Issues Module 04: Preventive Dentistry Module 05: Oral Health Promotion in Children Module 06: Oral Health Care for Special Populations Module 07: Dental Care Procedures Module 08: Oral Health and Nutrition Module 09: Oral Health Maintenance and Beyond (See full curriculum) Who is this course for? Individuals seeking to improve their knowledge of oral health care. Professionals aiming to enhance their understanding of dental health. Beginners with an interest in pursuing a career in health and dental care. Anyone looking to gain a deeper understanding of oral health issues and prevention. Career Path Dental Care Assistant Oral Health Educator Community Health Worker Public Health Specialist Dental Practice Manager

Store Assistant
By NextGen Learning
Course Overview The "Store Assistant" course offers learners an in-depth understanding of the retail sector, covering essential aspects such as customer service, store management, and retail operations. By completing this course, learners will gain the skills necessary to effectively contribute to the day-to-day operations of a retail environment. The course will also equip them with knowledge of retail management practices, customer interaction strategies, and industry regulations. Learners will come away with a comprehensive understanding of the role and the ability to enhance their professional practice in a retail setting, making them well-prepared for a variety of store assistant positions. Course Description This course is designed to provide learners with essential knowledge and skills for a career as a store assistant. Topics include the roles and responsibilities of store assistants, the basics of retail management, and how to effectively manage customer relationships. Learners will explore visual merchandising, consumer behaviour, and the psychological aspects of retail, along with understanding how to interact with suppliers. Additionally, the course covers relevant retail legislation to ensure compliance in day-to-day operations. Through a structured curriculum, learners will gain insights into managing a retail store, enhancing customer experiences, and applying effective store strategies to improve business outcomes. The course is ideal for those seeking to develop a strong foundation in retail roles and prepare for a successful career in the industry. Course Modules Module 01: Introduction to Store Assistant Module 02: Roles and Responsibilities of a Store Assistant Module 03: Introduction to Retail Management Module 04: Managing a Retail Store Module 05: Visual Merchandising Module 06: Consumer Behaviour Module 07: Dealing with Customers Module 08: Dealing with Suppliers Module 09: Store Psychology Module 10: Legislations Related to Retail (See full curriculum) Who is this course for? Individuals seeking to start a career in retail. Professionals aiming to enhance their retail management skills. Beginners with an interest in customer service and retail operations. Anyone looking to understand retail environments and store dynamics. Career Path Store Assistant Retail Associate Retail Manager Visual Merchandiser Customer Service Representative Retail Supervisor Supply Chain Assistant

DeepSeek Masterclass: A Complete DeepSeek Zero to Hero!
By NextGen Learning
Course Overview The DeepSeek Masterclass: A Complete DeepSeek Zero to Hero! is designed to provide learners with a comprehensive understanding of DeepSeek AI from the ground up. Whether you are new to artificial intelligence or seeking to deepen your expertise, this course offers a structured journey through DeepSeek's functionalities and real-world applications. Learners will discover how to navigate DeepSeek for software development, business innovation, and educational advancement. Through this masterclass, individuals will build a strong theoretical foundation, explore diverse use cases, and emerge with the confidence to implement DeepSeek-driven strategies in a range of professional environments. By the end of the programme, learners will have developed the knowledge and insights necessary to use DeepSeek as a transformative tool across multiple disciplines. Course Description This in-depth course covers a wide range of essential topics, including the foundations of artificial intelligence, DeepSeek system setup, and its applications across various sectors such as business, education, and software development. Learners will explore how DeepSeek can be leveraged to create smart solutions for students, empower business professionals, and support teaching practices. The masterclass delivers an immersive learning experience that blends conceptual knowledge with strategic application insights. Participants will build expertise in utilising DeepSeek to enhance efficiency, support innovation, and foster professional growth. Whether learners are looking to enter the AI space or to future-proof their careers, this course equips them with the essential skills and understanding to confidently engage with DeepSeek technologies in a competitive landscape. Course Modules Module 01: Getting Started Module 02: Foundations of Artificial Intelligence (AI) Module 03: Setting up DeepSeek AI for Beginners Module 04: DeepSeek for Software Developers Module 05: DeepSeek for Business Professionals Module 06: DeepSeek Smart Solutions for Students Module 07: The Power of DeepSeek Module 08: DeepSeek for Teaching Professionals (See full curriculum) Who is this course for? Individuals seeking to master DeepSeek AI from basic to advanced levels. Professionals aiming to integrate DeepSeek solutions into their organisations. Beginners with an interest in artificial intelligence, software development, or educational technology. Educators and trainers wishing to incorporate AI-based strategies into teaching. Career Path AI Solutions Specialist Software Developer (AI Focus) Business Innovation Consultant Educational Technology Specialist Data Analysis Support Roles AI Application Support Officer Digital Transformation Assistant

Supply Chain Management, Purchasing & Procurement
By NextGen Learning
Course Overview This comprehensive course in Supply Chain Management, Purchasing & Procurement provides learners with the strategic knowledge and operational understanding needed to navigate today’s dynamic supply environments. It explores the core components of supply chain systems, procurement cycles, and purchasing strategies, offering insight into effective logistics planning, supplier relations, and risk mitigation. Learners will gain the tools to streamline processes, optimise procurement decisions, and align purchasing objectives with broader business goals. Designed to support both career development and organisational efficiency, the course equips participants with a strong foundation in modern supply chain functions—contributing to smarter decision-making and improved supply performance. Course Description This course delves into the critical areas of supply chain operations, from foundational concepts to advanced procurement practices. Participants will study logistic management frameworks, category and inventory management, transport coordination, and supplier relationship strategies. Special focus is given to procurement tools, bid management, and cost reduction techniques that can enhance purchasing functions. Through each module, learners are introduced to effective methods for improving supply accuracy, managing quality, and applying risk assessment across sourcing channels. The course supports learners in understanding the interconnected nature of global supply networks, helping them contribute more effectively to procurement, planning, and supplier engagement in diverse business settings. Course Modules Module 01: Supply Chain Basics Module 02: Supply Chain Drivers Module 03: Introduction to Logistic Management Module 04: Planning Framework for Logistics Module 05: Transport Management Module 06: Role of Procurement in an Organisation Module 07: The Purchasing Cycle Module 08: Purchasing Toolkits Module 09: Managing Competitive Bids Module 10: Quality Management Module 11: Supplier Relationship Management Module 12: Analysing and Reducing Risk in the Supply Chain Module 13: Improving Efficiency and Accuracy Module 14: Category Management Module 15: Inventory Management Module 16: E-Procurement (See full curriculum) Who is this course for? Individuals seeking to build a career in procurement or logistics. Professionals aiming to upskill in supply chain operations. Beginners with an interest in purchasing and supply management. Business owners or team leaders looking to optimise procurement processes. Career Path Supply Chain Analyst Procurement Officer Purchasing Manager Inventory Control Specialist Logistics Coordinator Category Manager Supplier Relationship Manager Operations Executive in manufacturing, retail, or distribution sectors

Criminal Psychology and Profiling
By NextGen Learning
Course Overview The Criminal Psychology and Profiling course offers an insightful exploration into the psychological underpinnings of criminal behaviour and the art of criminal profiling. Learners will develop a strong foundation in understanding the minds of offenders, the impact of mental health disorders, and the various methods used to classify and investigate crime. Through studying forensic science, behavioural analysis, and victimology, participants will be equipped with the theoretical knowledge and analytical techniques needed to interpret criminal behaviour. Upon completion, learners will possess a deeper appreciation of how criminal psychology informs investigative strategies, legal processes, and crime prevention efforts, positioning them for further study or professional growth in this fascinating field. Course Description This course delves into the intricate relationship between psychology and criminal behaviour, offering a comprehensive study of mental disorders, forensic science applications, and profiling methodologies. Learners will examine the classification of crime, the phases of offender profiling, and the importance of victimology within investigations. The course also provides an overview of the criminal justice system in England and Wales, ensuring a contextual understanding of the legal framework surrounding criminal cases. Designed to strengthen analytical and critical thinking abilities, this programme encourages learners to apply logical reasoning and metacognitive strategies to criminal profiling. By the end of the course, participants will have cultivated a well-rounded skill set valuable for careers in criminal psychology, forensic science, and investigative fields. Course Modules Module 01: Understanding Criminal Psychology Module 02: Influence of Mental Disorders Module 03: Classification of Crime Module 04: Forensic Science Module 05: Criminal Profiling: Science, Logic and Metacognition Module 06: Phases of Profiling Module 07: Offender Profiling: Pragmatic Solution and Behavioural Investigative Advice Module 08: Victimology Module 09: The Criminal Justice System in England and Wales (See full curriculum) Who is this course for? Individuals seeking to understand criminal behaviour and profiling methods. Professionals aiming to enhance their expertise in psychology, criminology, or investigative roles. Beginners with an interest in forensic psychology, crime analysis, or criminal justice. Anyone aspiring to explore a career pathway in criminal psychology, forensic science, or legal support services. Career Path Criminal Psychologist Forensic Psychologist Behavioural Analyst Crime Analyst Offender Profiler Criminal Investigator Legal Assistant within criminal law practices Victim Support Worker

Criminology & Profiling
By NextGen Learning
Course Overview The "Criminology & Profiling" course provides an in-depth exploration of criminology, criminal behaviour, and profiling techniques. Learners will gain a comprehensive understanding of crime classification, the psychology of offenders, and the methods used in criminal investigations. This course combines theory with practical insights, preparing individuals to analyse criminal patterns and contribute to crime prevention strategies. Learners will leave with the skills to evaluate crime scenes, profile offenders, and understand the workings of the criminal justice system. The course offers an essential foundation for anyone seeking to work in criminology or forensic psychology, equipping them with the expertise to support law enforcement agencies and legal professionals. Course Description This course delves into various facets of criminology, with modules covering the classification of crime, violent crimes, criminal psychology, and the forensic science used in profiling offenders. It explores offender profiling, the phases of profiling, and investigative strategies that draw from behavioural science. Learners will examine crime scenes, develop an understanding of victimology, and explore the roles within the criminal justice system. Through this structured curriculum, learners will develop skills to identify criminal behaviour, understand criminal motivation, and apply profiling techniques to real-world cases. The course is designed to equip learners with a strong theoretical foundation, complemented by an understanding of practical approaches in criminology and profiling. Course Modules Module 01: Introduction to Criminology and Profiling Module 02: Classification of Crime Module 03: Violent Crimes Module 04: The Crime Scene Module 05: Dealing with Crime Module 06: Understanding Criminal Psychology Module 07: Forensic Science Module 08: Phases of Profiling Module 09: Criminal Profiling: Science, Logic and Metacognition Module 10: Offender Profiling: Pragmatic Solution and Behavioural Investigative Advice Module 11: Victimology Module 12: The Criminal Justice System in England and Wales (See full curriculum) Who is this course for? Individuals seeking to understand criminal behaviour and profiling techniques. Professionals aiming to advance their career in criminology or forensic psychology. Beginners with an interest in criminology, criminal justice, or psychology. Those interested in law enforcement and criminal investigation. Career Path Criminologist Criminal Profiler Forensic Psychologist Police Detective Criminal Justice Researcher Victim Support Specialist Legal Consultant Crime Analyst

Palo Alto Networks : Firewall Essentials: Configuration and Management EDU-210 (v11.0)
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for Security Engineers, Security Administrators, Security Operations Specialists, Security Analysts, and Support Staff Overview The Palo Alto Networks Firewall 10.2 Essentials: Configuration and Management (EDU-210) course is five days of instructor-led training that will help you to: Configure and manage the essential features of Palo Alto Networks next-generation firewalls Configure and manage Security and NAT policies to enable approved traffic to and from zones Configure and manage Threat Prevention strategies to block traffic from known and unknown IP addresses, domains, and URLs Monitor network traffic using the interactive web interface and firewall reports Palo Alto Networks next-generation firewalls are architected to safely enable applications and prevent modern threats. Their approach identifies all network traffic based on applications, users, content and devices, and lets you express your business policies in the form of easy-to-understand security rules. Flexible deployment options and native integration with their next-generation security platform extend the policy enforcement and cyberthreat prevention to everywhere your users and data are located: in your network, on your endpoints and in the cloud. Palo Alto Networks next-generation firewalls are architected to safely enable applications and prevent modern threats. Their approach identifies all network traffic based on applications, users, content and devices, and lets you express your business policies in the form of easy-to-understand security rules. Flexible deployment options and native integration with their next-generation security platform extend the policy enforcement and cyberthreat prevention to everywhere your users and data are located: in your network, on your endpoints and in the cloud.

Kubernetes Bootcamp (CKAD)
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for Anyone who plans to work with Kubernetes at any level or tier of involvement Any company or individual who wants to advance their knowledge of the cloud environment Application Developers Operations Developers IT Directors/Managers Overview All topics required by the CKAD exam, including: Deploy applications to a Kubernetes cluster Pods, ReplicaSets, Deployments, DaemonSets Self-healing and observable applications Multi-container Pod Design Application configuration via Configmaps, Secrets Administrate cluster use for your team A systematic understanding of Kubernetes architecture Troubleshooting and debugging tools Kubernetes networking and services Kubernetes is a Cloud Orchestration Platform providing reliability, replication, and stability while maximizing resource utilization for applications and services. By the conclusion of this hands-on training, you will go back to work with all necessary commands and practical skills to empower your team to succeed, as well as gain knowledge of important concepts like Kubernetes architecture and container orchestration. We prioritize covering all objectives and concepts necessary for passing the Certified Kubernetes Application Developer (CKAD) exam. You will command and configure a high availability Kubernetes environment (and later, build your own!) capable of demonstrating all ?K8s'' features discussed and demonstrated in this course. Your week of intensive, hands-on training will conclude with a mock CKAD exam that matches the real thing. Kubernetes Architecture Components Understand API deprecations Containers Define, build and modify container images Pods Master Services Node Services K8s Services YAML Essentials Creating a K8s Cluster kubectl Commands Kubernetes Resources Kubernetes Namespace Kubernetes Contexts Pods What is a Pod? Create, List, Delete Pods How to Access Running Pods Kubernetes Resources Managing Cloud Resource Consumption Multi-Container Pod Design Security Contexts Init Containers Understand multi-container Pod design patterns (e.g. sidecar, init and others) Pod Wellness Tracking Networking Packet Forwarding ClusterIP and NodePort Services Provide and troubleshoot access to applications via services Ingress Controllers Use Ingress rules to expose applications NetworkPolicy resource Demonstrate basic understanding of NetworkPolicies Network Plugins Defining the Service Mesh Service mesh configuration examples ReplicaSets Services ReplicaSet Function Deploying ReplicaSets Deployments Deployment Object Updating/Rolling Back Deployments Understand Deployments and how to perform rolling updates Deployment Strategies Use Kubernetes primitives to implement common deployment strategies (e.g. blue/green or canary) Scaling ReplicaSets Autoscaling Labels and Annotations Labels Annotations Node Taints and Tolerations Jobs The K8s Job and CronJob Understand Jobs and CronJobs Immediate vs. scheduled internal use Application Configuration Understanding and defining resource requirements, limits and quotas Config Maps Create & consume Secrets Patching Custom Resource Definition Discover and use resources that extend Kubernetes (CRD) Managing ConfigMaps and Secrets as Volumes Storage Static and dynamic persistent volumes via StorageClass K8s volume configuration Utilize persistent and ephemeral volumes Adding persistent storage to containers via persistent volume claims Introduction to Helm Helm Introduction Charts Use the Helm package manager to deploy existing packages Application Security Understand authentication, authorization and admission control Understand ServiceAccounts Understand SecurityContexts Application Observability and Maintenance Use provided tools to monitor Kubernetes applications How to Troubleshoot Kubernetes Basic and Advanced Logging Techniques Utilize container logs Accessing containers with Port-Forward Debugging in Kubernetes Hands on Labs: Define, build and modify container images Deploy Kubernetes using Ansible Isolating Resources with Kubernetes Namespaces Cluster Access with Kubernetes Context Listing Resources with kubectl get Examining Resources with kubectl describe Create and Configure Basic Pods Debugging via kubectl port-forward Imperative vs. Declarative Resource Creation Performing Commands inside a Pod Understanding Labels and Selectors Insert an Annotation Create and Configure a ReplicaSet Writing a Deployment Manifest Perform rolling updates and rollbacks with Deployments Horizontal Scaling with kubectl scale Implement probes and health checks Understanding and defining resource requirements, limits and quotas Understand Jobs and CronJobs Best Practices for Container Customization Persistent Configuration with ConfigMaps Create and Consume Secrets Understand the Init container multi-container Pod design pattern Using PersistentVolumeClaims for Storage Dynamically Provision PersistentVolumes with NFS Deploy a NetworkPolicy Provide and troubleshoot access to applications via services Use Ingress rules to expose applications Understand the Sidecar multi-container Pod design pattern Setting up a single tier service mesh Tainted Nodes and Tolerations Use the Helm package manager to deploy existing packages A Completed Project Install Jenkins Using Helm and Run a Demo Job Custom Resource Definitions (CRDs) Patching Understanding Security Contexts for Cluster Access Control Utilize container logs Advanced Logging Techniques Troubleshooting Calicoctl Deploy a Kubernetes Cluster using Kubeadm Monitoring Applications in Kubernetes Resource-Based Autoscaling Create ServiceAccounts for use with the Kubernetes Dashboard Saving Your Progress With GitHub CKAD Practice Drill Alta Kubernetes Course Specific Updates Sourcing Secrets from HashiCorp Vault Example CKAD Test Questions
