- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
295 Courses delivered Live Online
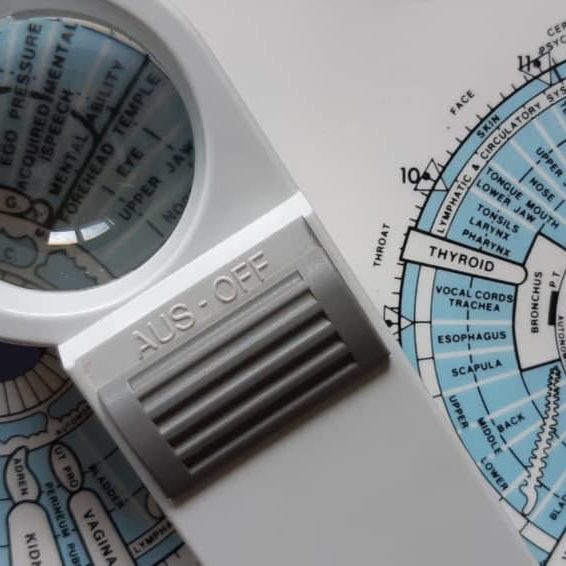
Iridology Diploma
By Plaskett International
LEARN HOW IRIDOLOGY CAN MAKE A HUGE CONTRIBUTION TO ANY COMPLEMENTARY PRACTICE A MESSAGE FROM THE AUTHOR I want to welcome you most warmly to the study of Iridology. Students of our course have taken their knowledge out into the world of practice and they have been able to see more penetratingly into the health of their patients. They have seen many truths about causes and effects in health and disease - that is what allows you to understand those extra things that make you into an even better healer. I think you are going to find this the most intriguing and absorbing study and, certainly, that is my sincere hope. As you precede, much of what you learn will amaze you and inspire wonder at the ways of the human body and mind. As you tread this very special road, I pass on to you the words that Bernard Jensen gave me years ago when I was his student, inscribed upon the inside cover of his book: “Seek the Higher Values in Life”. DR. LAWRENCE PLASKETT WHAT IS IRIDOLOGY? Iridology is the art of iris analysis. The iris is connected to the brain via the hypothalamus and can give naturopathic read outs on tissue conditions in various parts of the body. With training and practice it is possible to read signs indicative of biochemical, emotional and environmental influences that are hard to determine by other means. We can thus interpret health (and even aspects of personality) by close examination of the eyes, using suitable illumination and a magnifying glass. The close relationship between naturopathic iridology as an assessment tool and nutritional therapy and other naturopathic disciplines continues and grows closer. Now Iridology can make a huge contribution to complementary therapeutic practice and enhanced by our wonderful digital collection of eye photographs, the learning process with the Plaskett International College is a profound and exciting one. We teach Iridology quite separately from other topics and anyone who possesses, or expects to possess, a practitioner's qualification in any therapeutic discipline, may join the course. Course Duration 12 months Study Hours 200 hours Course Content 9 sections Course Fee £495 How Can Iridology Help Practitioners? Examples of how iridology can help practitioners Did you know that some iris features are so very plain that you can see them with the naked eye in ordinary social contact? You can see from two or three feet away in many cases that the person has a toxic digestive system (a strong wide dark ring around the pupil margin). You can often tell that the person has an overactive stomach (a narrow bright white ring very close to the pupil). You can tell when the skin is overlaid with toxins so that the skin's function in excreting toxins from the body is jeopardised (very narrow dark ring around the iris margin). You can tell in some people (rather advanced cases) that they suffer badly from sodium and potassium imbalance and have placed themselves at potential risk from cholesterol accumulation (the so-called corneal arcus, a white or off-white cloudy deposit, usually fairly thick, around the iris margin). Another example is the ring of spots or 'tophi' represented by the lymphatic rosary. Its mere presence tells one that there is sluggishness in the lymphatic system. When these tophi are darkly pigmented, the situation gives rise to concern for the possible generation of lymphatic illness. Using the precise positioning of iris reflex areas contained on the iris chart, one may distinguish many key points of analysis. Areas of stress and tension can be pinpointed by identifying 'contraction furrows’. Past injuries and adhesions show themselves as contortions of the normally regular and even iris fibres. You can answer questions like:- Is it the pancreas or the liver that is responsible for the trouble? Is the patient's hypertension caused by a defect of or toxic deposits in the particular brain area that is geared to control blood pressure? One of Jensen's rather dramatic illustrations is of the iris of a man who has just been shot. It shows the precise areas of tissue damage within the body and the response is very fast. The number of potential examples is almost without limit. The above may suffice to show the types of things that iridology can do for practitioners. We hope it will help you decide to study Iridology with the Plaskett International College. Course Overview The course covers the nature of iris observation, the nutritive zone, the iris chart, the chronic and acute, the intestinal and stomach zones and nerve collarette, the constitution type, respiratory system, lacunae, open lacuna, inherent weaknesses, the organs of elimination, other organs, special signs, complete diagnosis of a subject. The treatment of the topic follows the principles of Bernard Jensen in the USA. Once the basics have been learnt, the course teachings then extend considerably by bringing in the work of Dorothy Hall and of Dr Josef Deck, both of which are the subject of a special presentation during the course. The published insights of Farida Sharan and Harri Wolf, while not separately presented, also influence the presentation of the course material. Both the Australian School, (Dorothy Hall) and the German School, (Dr Deck/Harri Wolf), offer an added dimension to the study and interpretation of the constitution. PERSONALITY ASPECTS & CONSTITUTIONAL TYPES The study focuses upon the different personality aspects, which show up in different constitutional types. Dorothy Hall gives insights into what contributes to various different types of personality and their emotional and mental responses and their pre-dispositions to health or disease. Different sorts of people can have different priorities, preferences and imperatives built into their very nature from or before birth, sometimes determining the course of their entire lives and their attitudes to the world and to other people. AN EMPATHY BETWEEN PATIENT & PRACTITIONER The course teaches an understanding of these types and facilitates an empathy between patient and practitioner. It shows how people of the differing constitutional types are likely to go out of balance either mentally or emotionally and how their vulnerability to various physical ailments varies. The German School offers a very exciting and precise approach to the constitutional types, which is really quite different, but no less helpful. It highlights variations in the susceptibility to diseases of different organs and systems. THE 3 SCHOOLS OF THOUGHT It is a prime purpose of this course, not only to teach these differing positions, but also to demonstrate how it is that all three of these major schools of Iridology embody different aspects of the truth, how each is individually valuable and how a full and deep understanding of the meaning of 'constitution' can be gained through a sympathetic synthesis of the contributions from all three of these schools. BREAKDOWN OF THE COURSE SECTIONS In total there are 9 sections comprising of text, videos and iris images to study: SECTION 1 GENERAL PRACTICE AND AN ACCOUNT OF THE NUTRITIVE ZONE Areas Covered Iris colour Information that iridology can give us The structure of the eye and the iris Using the iris as an assessment tool The principle of reflex areas The Nutritive Zone Abnormality in the colon The Collarette (autonomic nerve wreath or anw) Diagnosis of the constitution based upon fibre structure Studies on images of real eyes SECTION 2 FEATURES OF THE FIBRES OUTSIDE THE COLLARETTE Areas Covered The general layout of fibres outside the collarette Inherent weaknesses First stage in further deterioration of an inherent weakness The meaning of darkness in the iris The development of discrete – open lacunae Lacunae Further notes about lightness and darkness amongst the fibres Healing lines Crypts Round the iris chart – the left iris Round the iris chart – the right iris Checking which structures and inside and which outside the collarette The organ systems The neural arc reflex SECTION 3 SPECIAL SIGNS Areas covered The corneal arcus (sodium ring, cholesterol ring, lipemic ring) The tophi (also lymphatic tophi or lymphatic rosary) Corneal Arcus The anaemia sign The catarrhal sign Acidity Grey background Scurf rim Circulatory ring Sphincter muscle (also called pupillary sphincter) Pigments (topastible or topolabile) Psoric spots Contrcation furrows Radial furrows SECTION 4 THE CONSTITUTIONS IN RELATION TO PERSONALITY TYPE AND DISEASE DISPOSITION Areas covered Very resilient Resilient average Moderately resilient Mildly resilient SECTION 5 MORE ABOUT WHITE SIGNS Areas covered Revision of distinctions between the different white signs Pictures of irises with white signs, with commentaries Further interpretation of the corneal arcus Further interpretation of the lytophi More general interpretation of the colour white SECTION 6 COLOURS IN THE IRIS AND OTHER SPECIAL SIGNS Areas Covered Yellow pigment in the iris Orange pigment Brown pigment Contraction furrows Radial furrows Psoric spots Pupillary border The “friendly fibrils” sign Summary of remedies SECTION 7 THE CONSTITUTION AND SIGNS ACCORDING TO THE GERMAN SCHOOL Areas Covered The German school of iridology Our approach to teaching the German school Introduction to the German constitutional types The lymphatic constitutions Mixed biliary constitution or biliary constitution Haematogenic (or haematogenous) constitution The way to use information on the German constitutions New signs that are specific to the German school Treatment recommendations for constitutional types SECTION 8 ADVANCED STUDIES OF THE IRIS Areas Covered Further details of the iris chart – its layout and its implications Neural arc reflex Deformation of pupil shape and position Advanced study of fibre separations, sinuosity, injuries & adhesions Lacunae of different shape and appearance The b3 bulge and the pterygium Working with genetically brown eyes SECTION 9 THE CONSULTATION & THE PRACTICALITIES Areas Covered Diagnosing pathology of individual critical organs Personality interpretations based upon the German school Conducting an iridology consultation Practical aspects of iris examination Making drawings of the iris and recording the data The uses, advantages and limitations of iris photography and its place in iridology practice Equipments and techniques of iris photography Using the computer to store and process digital images The interaction of signs Interpreting the whole iris in conjunction with the case study Pointers to treatment Carrying out case histories TESTIMONIALS Here's what students have to say about the course Emma Rubio, Health Coach Spain "As a Health Coach I decided to pursue my studies with the Plaskett College to become a Nutritional Therapist. For that, I am also studying Iridology. I am happy to have a tutor to answer my doubts and I like the flexibility that the College offers me. I love the subject of Iridology and the way it is explained, I also like having some videos of Dr Plaskett teaching Iridology as I admire him." Dr Ezequiel Lafontaine, Iridologist Puerto Rico "I LOVE IRIDOLOGY. I have over 30 iridology books, Italian, French, German, Spanish and English, plus over 4,000 photos from my own practice. I took this course for a refresher course and found the material was second to none." Mrs D. Moothy, Nutritional Therapist Mauritius “The distance learning courses have given me the opportunity to pursue my dreams through a program that was not only flexible and convenient for my schedule, but was also challenging and rewarding. I thoroughly enjoyed the readings and the assignments but most importantly, I enjoyed being able to do things at my pace. I must say that the most exciting and challenging course was the Iridology Diploma, and I am happy that I was able to do well in all the courses."
Certified Professional for Usability and User Experience – Foundation Certification (CPUX-F)
By Bunnyfoot
Bunnyfoot were the pioneers and are now one of the leading providers of the Certified Professional for Usability and User Experience – Foundation Level (CPUX-F) in the United Kingdom. Created in association with the international UXQB, this professional 3-day UX certification programme covers user experience methods and theories – and is independently assessed/certified.

CO2 Transportation From Capture to Storage and Usage
By EnergyEdge - Training for a Sustainable Energy Future
About this training course This 5-days comprehensive training course provides not only an introduction into the issues associated with the development of the pipeline transportation of CO2 from its Capture, it's transportation, storage and usage but also provides an in depth understanding of the issues to be considered in the development, design and operations of these pipelines. The theme throughout this training course is CO2 Flow Assurance and Innovative Technologies. Each training day will consist of lectures in the morning and a hands-on workshop in the afternoon. The workshop allows the participants to appreciate the design process associated with CO2 transport and its operations. Various software will be available during the workshop to predict thermo hydraulics and associated phase flows through CO2 pipelines and the attached infrastructure. Further software to assess surge and environmental safety will also be available. The CO2 pipeline design approach will consider an integrated solution through modelling the CO2 capture system as well as the host storage facility. The participants will have a total appreciation of the methodology required to develop a CO2 transportation system and have an understanding of all of the Flow Assurance, risks, and operating issues and technology requirements. Training Objectives After the completion of this training course, participants will be able to: Understand the process required and identify data to analyse Flow Assurance for CO2 pipeline transport Review and Identify the Flow Assurance issues required to be evaluated for CO2 pipeline transport design and operations methodology. These include; Hydrates, Slugging, Corrosion, Scaling, Fluid Phase Behaviour and transient conditions Establish the studies to be undertaken for each area of CO2 transport including 'Rules of Thumb' and software to be used Comprehend the need for innovative methods and the technologies to mitigate Flow Assurance issues and the need for economics considerations Appreciate the need for an integrated analysis of the CO2 transport system from the CO2 capture to the host storage facility Gain an appreciation of the emerging and enabling technologies for CO2 transport and storage application Dive deeper into the operational strategies requirements to mitigate Flow Assurance issues Target Audience This training course is suitable and will greatly benefit the following specific groups: Reservoir Engineers Flow Assurance Engineers Thermodynamics Engineers Process and Chemical Engineers Pipeline Engineers Facilities Engineers Control and Subsea Engineers working in the Oil and Gas industries Engineers in other disciplines may attend that require an appreciation of CO2 pipeline transport Control and Subsea Engineers working in the Oil and Gas industries Engineers in other disciplines may attend that require an appreciation of CO2 pipeline transport Course Level Intermediate Training Methods The training instructor relies on a highly interactive training method to enhance the learning process. This method ensures that all participants gain a complete understanding of all the topics covered. The training environment is highly stimulating, challenging, and effective because the participants will learn by case studies which will allow them to apply the material taught in their own organization. Course Duration: 5 days in total (35 hours). Training Schedule 0830 - Registration 0900 - Start of training 1030 - Morning Break 1045 - Training recommences 1230 - Lunch Break 1330 - Training recommences 1515 - Evening break 1530 - Training recommences 1700 - End of Training Course delivery: The maximum number of participants allowed for this training course is 20. A basic understanding of thermo-hydraulics would be advantageous. Morning Lectures and afternoon hands-on practical workshop. Special features: PC-based simulation software demonstration Workshop for hands-on training Course References & Additional resources: 'CO2 Transport from Capture to Storage and Usage', 1st Edition Handouts Pre & Post Assessment Trainer Your expert course leader is a renowned specialist in flow assurance management for the oil & gas field developments. His expertise enables him to support the operating and contracting companies as well as financial institutions regarding due diligence on offshore development investment decisions and associated operational system risks. Technical assessment of fields for acquisition and production enhancement opportunity. He possesses specialist expertise in evaluating difficult pipeline fluids transport such as Ethylene, Carbon Dioxide and Hydrogen through feasibility studies and technical reviews for clients. He has an exceptional academic background and natural leadership abilities are supported by practical experience of diverse projects worldwide, along with numerous publications at key conferences and publication of four books. Particular interests in developing novel and innovative technologies for subsea applications to solve difficult flow assurance problem areas and improve field development economics. He has worked on major industry projects including; Concorde aircraft fuelling system, the Channel Tunnel aerodynamics and the first deep water oil field development (Foinaven) in the West of Shetland. He is also currently developing a renewable energy solar farm and carbon neutral energy crop (Miscanthus) for domestic and commercial power generation application. He has developed in-house resources including specialist oil & gas field development evaluation software for subsea and onshore field infrastructure development options including; costing and financial analysis, reservoir viability, flow assurance assessment, subsea processing and boosting technologies, flow induced vibrations, surge analysis, heat transfer and chemical injection systems. Patents: · Subsea Seabed Power Generation for Depleting Gas fields Using Renewable Energy · Gas to Liquids Absorption Technology (GTLA) for subsea and onshore Flow Assurance applications · Subsea Gas Compressor System using pigs and liquid pumps · Pressure Boosting using water injection pumps · B&W Mentor subsea multi-phase meter · Surge suppression using a contained gas method for pipeline systems POST TRAINING COACHING SUPPORT (OPTIONAL) To further optimise your learning experience from our courses, we also offer individualized 'One to One' coaching support for 2 hours post training. We can help improve your competence in your chosen area of interest, based on your learning needs and available hours. This is a great opportunity to improve your capability and confidence in a particular area of expertise. It will be delivered over a secure video conference call by one of our senior trainers. They will work with you to create a tailor-made coaching program that will help you achieve your goals faster. Request for further information post training support and fees applicable Accreditions And Affliations

Certified Professional for Usability and User Experience – Usability Testing and Evaluation (CPUX-UT)
By Bunnyfoot
This one-day course introduces the field of user experience and provides an excellent entry point to our other specialised training courses. UX processes and practices have become a central component of product design, service design and web design.

Usability Testing
By Experience Thinkers
Gain robust techniques for obtaining feedback from end users throughout product design, and learn how to identify new opportunities for design improvement.

Securing UNIX systems training course description This course teaches you everything you need to know to build a safe Linux environment. The first section handles cryptography and authentication with certificates, openssl, mod_ssl, DNSSEC and filesystem encryption. Then Host security and hardening is covered with intrusion detection, and also user management and authentication. Filesystem Access control is then covered. Finally network security is covered with network hardening, packet filtering and VPNs. What will you learn Secure UNIX accounts. Secure UNIX file systems. Secure UNIX access through the network. Securing UNIX systems course details Who will benefit: Linux technical staff needing to secure their systems. Prerequisites: Linux system administration (LPIC-1) Duration 5 days Securing UNIX systems course contents Cryptography Certificates and Public Key Infrastructures X.509 certificates, lifecycle, fields and certificate extensions. Trust chains and PKI. openssl. Public and private keys. Certification authority. Manage server and client certificates. Revoke certificates and CAs. Encryption, signing and authentication SSL, TLS, protocol versions. Transport layer security threats, e.g. MITM. Apache HTTPD with mod_ssl for HTTPS service, including SNI and HSTS. HTTPD with mod_ssl to authenticate users using certificates. HTTPD with mod_ssl to provide OCSP stapling. Use OpenSSL for SSL/TLS client and server tests. Encrypted File Systems Block device and file system encryption. dm-crypt with LUKS to encrypt block devices. eCryptfs to encrypt file systems, including home directories and, PAM integration, plain dm-crypt and EncFS. DNS and cryptography DNSSEC and DANE. BIND as an authoritative name server serving DNSSEC secured zones. BIND as an recursive name server that performs DNSSEC validation, KSK, ZSK, Key Tag, Key generation, key storage, key management and key rollover, Maintenance and resigning of zones, Use DANE. TSIG. Host Security Host Hardening BIOS and boot loader (GRUB 2) security. Disable useless software and services, sysctl for security related kernel configuration, particularly ASLR, Exec-Shield and IP / ICMP configuration, Exec-Shield and IP / ICMP configuration, Limit resource usage. Work with chroot environments, Security advantages of virtualization. Host Intrusion Detection The Linux Audit system, chkrootkit, rkhunter, including updates, Linux Malware Detect, Automate host scans using cron, AIDE, including rule management, OpenSCAP. User Management and Authentication NSS and PAM, Enforce password policies. Lock accounts automatically after failed login attempts, SSSD, Configure NSS and PAM for use with SSSD, SSSD authentication against Active Directory, IPA, LDAP, Kerberos and local domains, Kerberos and local domains, Kerberos tickets. FreeIPA Installation and Samba Integration FreeIPA, architecture and components. Install and manage a FreeIPA server and domain, Active Directory replication and Kerberos cross-realm trusts, sudo, autofs, SSH and SELinux integration in FreeIPA. Access Control Discretionary Access Control File ownership and permissions, SUID, SGID. Access control lists, extended attributes and attribute classes. Mandatory Access Control TE, RBAC, MAC, DAC. SELinux, AppArmor and Smack. etwork File Systems NFSv4 security issues and improvements, NFSv4 server and clients, NFSv4 authentication mechanisms (LIPKEY, SPKM, Kerberos), NFSv4 pseudo file system, NFSv4 ACLs. CIFS clients, CIFS Unix Extensions, CIFS security modes (NTLM, Kerberos), mapping and handling of CIFS ACLs and SIDs in a Linux system. Network Security Network Hardening FreeRADIUS, nmap, scan methods. Wireshark, filters and statistics. Rogue router advertisements and DHCP messages. Network Intrusion Detection ntop, Cacti, bandwidth usage monitoring, Snort, rule management, OpenVAS, NASL. Packet Filtering Firewall architectures, DMZ, netfilter, iptables and ip6tables, standard modules, tests and targets. IPv4 and IPv6 packet filtering. Connection tracking, NAT. IP sets and netfilter rules, nftables and nft. ebtables. conntrackd Virtual Private Networks OpenVPN server and clients for both bridged and routed VPN networks. IPsec server and clients for routed VPN networks using IPsec-Tools / racoon. L2TP.

COBOL training course description A hands on training course providing an introduction to COBOL. What will you learn Write COBOL programs Debug COBOL programs Examine existing code and determine its function. COBOL training course details Who will benefit: Programmers working with COBOL. Prerequisites: None although experience in another high level language would be useful. A 10 day version of this course would be more applicable for those new to programming. Duration 5 days COBOL training course contents Introduction to COBOL Compilation, linkage editor. Compile errors, compiler options. Divisions, syntax and format, COBOL character set, program structure. COBOL statement structure COBOL words, format of statements. Divisions Identification entries, Environment entries, Data division: FD, record descriptions, hierarchy and level numbers, description-string entry. File and Working-Storage Sections Literals, figurative constants, redefines clause, data representation, Usage clause, synchronization, sign clause. Procedure Division File status codes; Open, Read, Write, Close, Stop, Goback; Accept, display; Move, Justified, data name qualification, reference modification. Perform statement Out-of-line, With test ... Until, ... Times, in-line statement; Go to statement. Program design Design techniques, design considerations, procedure names, program structure. Printing Printed output, Write, advancing option, editing characters; Initialize. Condition testing Conditional statements: IF, class, sign and relation conditions, condition-name conditionals, Set, compound conditions, logical operators. Evaluate, Continue. Arithmetic Rounded option, On Size Error option, Add, Subtract, Multiply, Divide, Compute. Non-sequential files File access modes, Select. Indexed and relative files. Open, Close, creating / reading sequential access files, Write, Read, Invalid key clause, reading, writing / updating Random access files, Rewrite, Delete, Start. Declarative routines Clauses. Subroutines Call, Using clause - calling program/called program, Linkage Section, returning control. Table handling Subscripted tables: One/two/three dimensional tables, Perform, variable length tables. Indexed tables: Set, using an index; Search. Copy code: Copy, Suppress, Replacing. Data Manipulation Inspect, String, Unstring. COBOL/370 LE/370 and Intrinsic Functions.

Overview Internet is the main source of marketing today and Digital Marketing along with Social Media Marketing helps the business to stay alive in the digital world. Earlier companies use to spend a lot of money on traditional ways of marketing and still, they were not able to reach global clients. With the existence of Digital marketing, they are able to break the barriers to reaching global clients. With the use of Social Media Marketing and Digital Marketing organisations are able to reach every corner of the world and also it is very cost-effective. Digital Marketing encompasses various channels like Search Engine Optimisation, Social Media Marketing like usage of Facebook, Facebook marketing, Ad Words, and Email Campaigns and is list is longer. All these tools are used to cover global marketing. No matter where you are located in the world, your product can reach clients anywhere in the world. This course will help develop innovative social media strategies, and to boost brand awareness with rich content. With the effective analysis of campaign results, you'll be on track to exceed sales targets and advance your career with the latest social media marketing techniques.

Securing Linux systems training course description This course teaches you everything you need to know to build a safe Linux environment. The first section handles cryptography and authentication with certificates, openssl, mod_ssl, DNSSEC and filesystem encryption. Then Host security and hardening is covered with intrusion detection, and also user management and authentication. Filesystem Access control is then covered. Finally network security is covered with network hardening, packet filtering and VPNs. What will you learn Secure Linux accounts. Secure Linux file systems. Secure Linux access through the network. Securing Linux systems training course details Who will benefit: Linux technical staff needing to secure their systems. Prerequisites: Linux system administration (LPIC-1) Duration 5 days Securing Linux systems training course contents Cryptography Certificates and Public Key Infrastructures X.509 certificates, lifecycle, fields and certificate extensions. Trust chains and PKI. openssl. Public and private keys. Certification authority. Manage server and client certificates. Revoke certificates and CAs. Encryption, signing and authentication SSL, TLS, protocol versions. Transport layer security threats, e.g. MITM. Apache HTTPD with mod_ssl for HTTPS service, including SNI and HSTS. HTTPD with mod_ssl to authenticate users using certificates. HTTPD with mod_ssl to provide OCSP stapling. Use OpenSSL for SSL/TLS client and server tests. Encrypted File Systems Block device and file system encryption. dm-crypt with LUKS to encrypt block devices. eCryptfs to encrypt file systems, including home directories and, PAM integration, plain dm-crypt and EncFS. DNS and cryptography DNSSEC and DANE. BIND as an authoritative name server serving DNSSEC secured zones. BIND as an recursive name server that performs DNSSEC validation, KSK, ZSK, Key Tag, Key generation, key storage, key management and key rollover, Maintenance and resigning of zones, Use DANE. TSIG. Host Security Host Hardening BIOS and boot loader (GRUB 2) security. Disable useless software and services, sysctl for security related kernel configuration, particularly ASLR, Exec-Shield and IP / ICMP configuration, Exec-Shield and IP / ICMP configuration, Limit resource usage. Work with chroot environments, Security advantages of virtualization. Host Intrusion Detection The Linux Audit system, chkrootkit, rkhunter, including updates, Linux Malware Detect, Automate host scans using cron, AIDE, including rule management, OpenSCAP. User Management and Authentication NSS and PAM, Enforce password policies. Lock accounts automatically after failed login attempts, SSSD, Configure NSS and PAM for use with SSSD, SSSD authentication against Active Directory, IPA, LDAP, Kerberos and local domains, Kerberos and local domains, Kerberos tickets. FreeIPA Installation and Samba Integration FreeIPA, architecture and components. Install and manage a FreeIPA server and domain, Active Directory replication and Kerberos cross-realm trusts, sudo, autofs, SSH and SELinux integration in FreeIPA. Access Control Discretionary Access Control File ownership and permissions, SUID, SGID. Access control lists, extended attributes and attribute classes. Mandatory Access Control TE, RBAC, MAC, DAC. SELinux, AppArmor and Smack. etwork File Systems NFSv4 security issues and improvements, NFSv4 server and clients, NFSv4 authentication mechanisms (LIPKEY, SPKM, Kerberos), NFSv4 pseudo file system, NFSv4 ACLs. CIFS clients, CIFS Unix Extensions, CIFS security modes (NTLM, Kerberos), mapping and handling of CIFS ACLs and SIDs in a Linux system. Network Security Network Hardening FreeRADIUS, nmap, scan methods. Wireshark, filters and statistics. Rogue router advertisements and DHCP messages. Network Intrusion Detection ntop, Cacti, bandwidth usage monitoring, Snort, rule management, OpenVAS, NASL. Packet Filtering Firewall architectures, DMZ, netfilter, iptables and ip6tables, standard modules, tests and targets. IPv4 and IPv6 packet filtering. Connection tracking, NAT. IP sets and netfilter rules, nftables and nft. ebtables. conntrackd Virtual Private Networks OpenVPN server and clients for both bridged and routed VPN networks. IPsec server and clients for routed VPN networks using IPsec-Tools / racoon. L2TP.

