- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
684 Courses in Nottingham delivered Live Online
The New Sustainability Disclosure Reporting Standards - IFRS S1 and S2
By Ideas Into Action
An overview of new disclosure reporting standards IFRS S1 and IFRS S2

Recruitment Resourcer Level 2
By Rachel Hood
Identifying, attracting and shortlisting candidates for the recruitment process to fulfil the requirements of the business brief.

VMware vSAN: Plan and Deploy [v7]
By Nexus Human
Duration 2 Days 12 CPD hours This course is intended for Experienced VMware vSphere administrators Overview By the end of the course, you should be able to meet the following objectives: Explain the key features and use cases for vSAN Detail the underlying vSAN architecture and components Describe the different vSAN deployment options Detail vSAN cluster requirements and considerations Apply recommended vSAN design considerations and capacity sizing practices Determine and plan for storage consumption by data growth and failure tolerance Design vSAN hosts for operational needs Explain Maintenance Mode use and its impacts on vSAN Apply best practices for vSAN network configurations Manually configure a vSAN cluster using VMware vSphere Client⢠Explain and configure vSAN fault domains Understand and apply vSAN storage policies Define encryption in the vSAN cluster Describe the architecture and use cases for stretched clusters Describe the architecture and use cases for two-node clusters Understand the steps involved in creating the vSAN iSCSI target services This two-day, hands-on training course provides you with the knowledge, skills, and tools to plan and deploy a VMware vSAN? cluster. In this course, you are taught the many considerations that the end vSAN configuration has on the initial planning of the vSAN datastore. You also perform a fully manual configuration of a vSAN cluster. Course Introduction Introductions and course logistics Course objectives Introduction to vSAN Describe vSAN architecture Identify vSAN objects and components Describe the advantages of object-based storage Describe the difference between All-Flash and Hybrid vSAN architecture Explain the key features and use cases for vSAN Discuss the vSAN integration and compatibility with other VMware technologies Planning a vSAN Cluster Identify requirements and planning considerations for vSAN clusters Apply vSAN cluster planning and deployment best practices Determine and plan for storage consumption by data growth and failure tolerance Design vSAN hosts for operational needs Identify vSAN networking features and requirements Describe ways of controlling traffic in a vSAN environment Recognize best practices for vSAN network configurations Deploying a vSAN Cluster Deploy and configure a vSAN cluster using the Cluster Quickstart wizard Manually configure a vSAN cluster using vSphere Client Explain and configure vSAN fault domains Using VMware vSphere© High Availability with vSAN Understand vSAN cluster maintenance capabilities Describe the difference between implicit and explicit fault domains Create explicit fault domains vSAN Storage Policies Describe a vSAN object Describe how objects are split into components Explain the purpose of witness components Explain how vSAN stores large objects View object and component placement on the vSAN datastore Explain how storage policies work with vSAN Define and create a virtual machine storage policy Apply and modify virtual machine storage policies Change virtual machine storage policies dynamically Identify virtual machine storage policy compliance status Introduction to Advanced vSAN Configurations Define and configure compression and deduplication in the vSAN cluster Define and configure encryption in the vSAN cluster Understand the remote vSAN datastore topology Identify the operations involved in managing the remote vSAN datastore Understand the steps involved in creating the vSAN iSCSI target service vSAN Stretched and Two-Node Clusters Describe the architecture and use cases for stretched clusters Detail the deployment and replacement of a vSAN witness node Describe the architecture and uses case for two-node clusters Explain the benefits of vSphere HA and vSphere Site Recovery Manager in a vSAN stretched cluster Explain storage policies for vSAN stretched cluster Additional course details:Notes Delivery by TDSynex, Exit Certified and New Horizons an VMware Authorised Training Centre (VATC) Nexus Humans VMware vSAN: Plan and Deploy [v7] training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the VMware vSAN: Plan and Deploy [v7] course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.
![VMware vSAN: Plan and Deploy [v7]](https://cademy-images-io.b-cdn.net/9dd9d42b-e7b9-4598-8d01-a30d0144ae51/4c81f130-71bf-4635-b7c6-375aff235529/original.png?width=3840)
Hybrid Management & Leadership Training for Hospitals and Ministries of Health
5.0(1)By Generation Leader
Award-winning, highly cost effective, certified leadership & management training for your organisation Online and face to face learning for cohorts of between 50- 100,000 users. Available Globally. World-leading content mapped to your vision, organisational objective and your competency framework. Full reporting transparency and engagement tracking. Capability uplift at scale, in the most cost effective, impactful way possible Beneficial for GMC or JCI compliance Give your workforce access to world-leading MIT Sloan Management Review content. Stunning, award-winning learning platform available on all devices. Overview Attract, retain and inspire the best national and global talent with training that will make your hospital thrive It’s essential your investment is ulitised and has the desired impact. Our content is relatable and relevant so encourages active usage and engagement. We are invested in making sure you get a great return on your investment each day. Our programmes are: Focused on your organisation’s strategic objectives and competency framework. We help you tackle pressing issues Made for you. Our platform can intigrate with your learning management system (LMS) Cost-effective. Develop teams, departments and organisation wide with our innovative platform Prestigious. Give your workforce access to world-leading MIT Sloan Management Review and Mayo Clinic content Recognised by the Chartered Management Institute (CMI) & fully CPD certified Flexible. On-demand learning via our platform and app. Keep the workforce learning on the go. No study leave required Global. Made by NHS doctors and used by healthcare professionals worldwide Hybrid. Face to face group sessions delivered by clinical and leadership experts, supported by our technology Organised. Upload your own specific training material to our platform to save time and resourses Trusted and Accredited. We have the only management and leadership courses in the world accredited by: World leading content supported by cutting edge technology. Made for healthcare professionals. Course Content Content to inspire your workforce What is the role of leader? Building and Leading Successful teams CPDwatch Building and Leading Successful teams Building and Leading Successful teams Leading with Values and Ethics CPDwatch Leading with Values and Ethics Leading with Values and Ethics watch Leadership Insights on Leading with Executive Presence Leadership Insights on Leading with Executive Presence watch Leadership Insights on Building & Leading Teams Leadership Insights on Building & Leading Teams watch Leadership Toolkit: Facilitating a Workshop Leadership Toolkit: Facilitating a Workshop watch Leadership Toolkit: Facilitating a Brainstorming Session Leadership Toolkit: Facilitating a Brainstorming Session watch Leadership Toolkit: Running a Team Debrief Leadership Toolkit: Running a Team Debrief watch The Characteristics of an Accountable Leader The Characteristics of an Accountable Leader Leading through Shared Vision CPDwatch Leading through Shared Vision Leading through Shared Vision watch Evaluating Your Management Style Evaluating Your Management Style watch The Adaptive Leader: Be an Iceberg The Adaptive Leader: Be an Iceberg The Collaborative Leader CPDwatch The Collaborative Leader The Collaborative Leader Leading through Problem Solving and Decision Making CPDwatch Leading through Problem Solving and Decision Making Leading through Problem Solving and Decision Making watch Leadership Insights on Leading Diversity Leadership Insights on Leading Diversity watch Leadership Insights on Judgment and Decisiveness Leadership Insights on Judgment and Decisiveness Leading with Judgment and Decisiveness CPDwatch Leading with Judgment and Decisiveness Leading with Judgment and Decisiveness Accountable Leadership CPDwatch Accountable Leadership Accountable Leadership watch Leadership Insights on Being Accountable Leadership Insights on Being Accountable watch Expert Insights on Networking & Building Relationships Expert Insights on Networking & Building Relationships watch Building Your Professional Network Building Your Professional Network watch Leadership Insights on Networking with your Peers Leadership Insights on Networking with your Peers watch Networking to Improve Leadership Effectiveness Networking to Improve Leadership Effectiveness watch Empowering Employees Empowering Employees read MIT Sloan Management Review on New Leader Transitions MIT Sloan Management Review on New Leader Transitions read All the Leader You Can Be: The Science of Achieving Extraordinary Executive Presence All the Leader You Can Be: The Science of Achieving Extraordinary Executive Presence read MIT Sloan Management Review on The Adaptive Leader MIT Sloan Management Review on The Adaptive Leader read MIT Sloan Management Review Article on Looking for Opportunity in the Midst of Crisis MIT Sloan Management Review Article on Looking for Opportunity in the Midst of Crisis read Executive Presence: The Art of Commanding Respect like a CEO, Second Edition Executive Presence: The Art of Commanding Respect like a CEO, Second Edition read MIT Sloan Management Review on Leader as Motivator MIT Sloan Management Review on Leader as Motivator listen The Accountable Leader: Developing Effective Leadership Through Managerial Accountability The Accountable Leader: Developing Effective Leadership Through Managerial Accountability listen From Bud to Boss: Secrets to a Successful Transition to Remarkable Leadership From Bud to Boss: Secrets to a Successful Transition to Remarkable Leadership listen Strategic Connections: The New Face of Networking in a Collaborative World Strategic Connections: The New Face of Networking in a Collaborative World listen The Courage Way: Leading and Living with Integrity The Courage Way: Leading and Living with Integrity listen Executive Presence: The Art of Commanding Respect Like a CEO Executive Presence: The Art of Commanding Respect Like a CEO The importance of skillful communication Leading across Cultures CPDwatch Leading across Cultures Leading across Cultures watch Leadership Insights on Setting and Managing Priorities Leadership Insights on Setting and Managing Priorities watch Expert Insights on Collaboration Expert Insights on Collaboration Becoming a Successful Collaborator CPDwatch Becoming a Successful Collaborator Becoming a Successful Collaborator Leading with Judgment and Decisiveness CPDwatch Leading with Judgment and Decisiveness Leading with Judgment and Decisiveness watch Managing Conflict across Cultures Managing Conflict across Cultures watch Managing Conflict in High Performance Teams Managing Conflict in High Performance Teams watch Leadership Insights on Conflict Management Leadership Insights on Conflict Management The Collaborative Leader CPDwatch The Collaborative Leader The Collaborative Leader watch Leadership Insights on Leading Across Cultures Leadership Insights on Leading Across Cultures Leading Diversity CPDwatch Leading Diversity Leading Diversity Encouraging Team Communication and Collaboration CPDwatch Encouraging Team Communication and Collaboration Encouraging Team Communication and Collaboration Navigating Challenging Situations with Diplomacy and Tact CPDwatch Navigating Challenging Situations with Diplomacy and Tact Navigating Challenging Situations with Diplomacy and Tact Facing Virtual Team Challenges CPDwatch Facing Virtual Team Challenges Facing Virtual Team Challenges watch Leadership Insights on Problem Solving & Decision Making Leadership Insights on Problem Solving & Decision Making watch Leadership Insights on Leading through Disruption Leadership Insights on Leading through Disruption watch Leadership Insights on Leading through Motivation Leadership Insights on Leading through Motivation Leading Others through Conflict CPDwatch Leading Others through Conflict Leading Others through Conflict Cultivating Cross-functional Team Collaboration CPDwatch Cultivating Cross-functional Team Collaboration Cultivating Cross-functional Team Collaboration watch Running a Team Debrief Running a Team Debrief watch Leaders Have to Be Human Leaders Have to Be Human watch Collaborating Beyond the Team Collaborating Beyond the Team watch How the Power of Listening Can Reveal Your Team's Motivating Tensions How the Power of Listening Can Reveal Your Team's Motivating Tensions read Successful Time Management: How to be Organized, Productive and Get Things Done Successful Time Management: How to be Organized, Productive and Get Things Done read Managing Conflict at Work: Understanding and Resolving Conflict for Productive Working Relationships Managing Conflict at Work: Understanding and Resolving Conflict for Productive Working Relationships read Conflict Management Conflict Management read Committed Teams: Three Steps to Inspiring Passion and Performance Committed Teams: Three Steps to Inspiring Passion and Performance read Building the Team Organisation: How to Open Minds, Resolve Conflict, and Ensure Cooperation Building the Team Organisation: How to Open Minds, Resolve Conflict, and Ensure Cooperation read MIT Sloan Management Review on Problem Solving and Decision Making MIT Sloan Management Review on Problem Solving and Decision Making read Communicate Like a Leader: Connecting Strategically to Coach, Inspire, and Get Things Done Communicate Like a Leader: Connecting Strategically to Coach, Inspire, and Get Things Done read MIT Sloan Management Review on Negotiation MIT Sloan Management Review on Negotiation read 5 Critical Conversations to Talent Development: Tips, Tools & Intelligence for Developing Talent 5 Critical Conversations to Talent Development: Tips, Tools & Intelligence for Developing Talent read MIT Sloan Management Review on Developing People MIT Sloan Management Review on Developing People read MIT Sloan Management Review on Cross-Functional Collaboration MIT Sloan Management Review on Cross-Functional Collaboration listen Opening Doors to Teamwork and Collaboration: 4 Keys That Change Everything Opening Doors to Teamwork and Collaboration: 4 Keys That Change Everything How to create and lead change Contributing as a Virtual Team Member CPDwatch Contributing as a Virtual Team Member Contributing as a Virtual Team Member Leading Innovation CPDwatch Leading Innovation Leading Innovation Leading with Strategic Thinking CPDwatch Leading with Strategic Thinking Leading with Strategic Thinking watch Leadership Insights on Strategic Thinking Leadership Insights on Strategic Thinking Building and Leading Successful Teams CPDwatch Building and Leading Successful Teams Building and Leading Successful Teams watch Leadership Insights on Building & Leading Teams Leadership Insights on Building & Leading Teams Creating a Successful Business Execution Culture CPDwatch Creating a Successful Business Execution Culture Creating a Successful Business Execution Culture watch How to Build Trust in a Team How to Build Trust in a Team watch Leadership Insights on Leading Innovation Leadership Insights on Leading Innovation watch Leadership Insights on Leading a Culture of Execution Leadership Insights on Leading a Culture of Execution watch Leadership Insights on Leading through Change Leadership Insights on Leading through Change Leading through the Challenge of Change CPDwatch Leading through the Challenge of Change Leading through the Challenge of Change watch Leadership Insights on Leading Collaboratively Leadership Insights on Leading Collaboratively Facilitating Sustainable Change CPDwatch Facilitating Sustainable Change Facilitating Sustainable Change watch Disruptive Leadership Disruptive Leadership read Learning to Think Strategically Learning to Think Strategically read Leading with Strategic Thinking: Four Ways Effective Leaders Gain Insight, Drive Change, and Get Results Leading with Strategic Thinking: Four Ways Effective Leaders Gain Insight, Drive Change, and Get Results read Demystifying Strategic Thinking: Lessons from Leading CEOs Demystifying Strategic Thinking: Lessons from Leading CEOs read MIT Sloan Management Review on Building and Leading Teams MIT Sloan Management Review on Building and Leading Teams read Virtual Leadership: Practical Strategies for Getting the Best Out of Virtual Work and Virtual Teams Virtual Leadership: Practical Strategies for Getting the Best Out of Virtual Work and Virtual Teams read Managing and Leading People through Organizational Change: The Theory and Practice of Sustaining Change through People Managing and Leading People through Organizational Change: The Theory and Practice of Sustaining Change through People read The Effective Change Manager's Handbook: Essential Guidance to the Change Management Body of Knowledge The Effective Change Manager's Handbook: Essential Guidance to the Change Management Body of Knowledge read Choosing to Change: An Alternative Understanding of Change Management Choosing to Change: An Alternative Understanding of Change Management Why leaders should possess emotional intelligence Leading by Developing People CPDwatch Leading by Developing People Leading by Developing People watch Leadership Insights on Critical Thinking Leadership Insights on Critical Thinking watch Knowing When to Think Critically Knowing When to Think Critically Developing Your Critical Thinking and Cognitive Flexibility CPDwatch Developing Your Critical Thinking and Cognitive Flexibility Developing Your Critical Thinking and Cognitive Flexibility Leading through Setting and Managing Priorities CPDwatch Leading through Setting and Managing Priorities Leading through Setting and Managing Priorities watch Managing Priorities Managing Priorities watch Leadership Insights on Leading with Values & Ethics Leadership Insights on Leading with Values & Ethics The Collaborative Leader CPDwatch The Collaborative Leader The Collaborative Leader The Agile Leader CPDwatch The Agile Leader The Agile Leader watch Disruptive Leadership Disruptive Leadership Make The Time You Need: Get Organised CPDwatch Make The Time You Need: Get Organised Make The Time You Need: Get Organised watch Leadership Insights on Emotional Intelligence Leadership Insights on Emotional Intelligence Becoming an Emotionally Intelligent Leader CPDwatch Becoming an Emotionally Intelligent Leader Becoming an Emotionally Intelligent Leader Managing in a Crisis CPDwatch Managing in a Crisis Managing in a Crisis watch Planning Crisis Communications Planning Crisis Communications watch Crisis Management for Leaders Crisis Management for Leaders watch Take a Deep Breath and Manage Your Stress Take a Deep Breath and Manage Your Stress watch Being a Mindful Leader Being a Mindful Leader watch Overcome Emotional Feelings Overcome Emotional Feelings Managing Pressure and Stress to Optimise Your Performance CPDwatch Managing Pressure and Stress to Optimise Your Performance Managing Pressure and Stress to Optimise Your Performance watch Expert Insights on Managing Stress Expert Insights on Managing Stress watch Emotional Intelligence and Effective Leadership Emotional Intelligence and Effective Leadership watch Helping Your Team Work Helping Your Team Work watch Fair and Just Decision Making Fair and Just Decision Making read MIT Sloan Management Review on Setting and Managing Priorities MIT Sloan Management Review on Setting and Managing Priorities read Advances in Authentic and Ethical Leadership Advances in Authentic and Ethical Leadership read Resilient Organisations: How to Survive, Thrive and Create Opportunities Through Crisis and Change Resilient Organisations: How to Survive, Thrive and Create Opportunities Through Crisis and Change read 50 Activities For Managing Stress 50 Activities For Managing Stress read Emotional Intelligence Pocketbook: Little Exercises for an Intuitive Life Emotional Intelligence Pocketbook: Little Exercises for an Intuitive Life read Mindful Leadership: The 9 Ways to Self-Awareness, Transforming Yourself, and Inspiring Others Mindful Leadership: The 9 Ways to Self-Awareness, Transforming Yourself, and Inspiring Others The significance of coaching in your career Developing Successful Coaching Relationships CPDwatch Developing Successful Coaching Relationships Developing Successful Coaching Relationships watch Working on Shared Goals through Teaming Working on Shared Goals through Teaming watch Initiating a Coaching Relationship Initiating a Coaching Relationship watch Coaches Build Self-Confidence Coaches Build Self-Confidence watch Be a Better Coach Be a Better Coach watch Coaching Team Members Coaching Team Members Leading by Developing People CPDwatch Leading by Developing People Leading by Developing People watch Delivering Results While Developing People Delivering Results While Developing People watch How to Increase Engagement How to Increase Engagement watch Leadership Insights on Coaching Leadership Insights on Coaching watch Leadership Insights on Developing Women Leaders Leadership Insights on Developing Women Leaders watch Leadership Insights on Leading Collaboratively Leadership Insights on Leading Collaboratively watch Creating a Vision Creating a Vision watch Becoming A More Effective Delegator Becoming A More Effective Delegator read MIT Sloan Management Review on Leader as Coach Special Collection MIT Sloan Management Review on Leader as Coach Special Collection read Anytime Coaching: Unleashing Employee Performance, Second Edition Anytime Coaching: Unleashing Employee Performance, Second Edition read Coaching and Mentoring: Practical Techniques for Developing Learning and Performance, Third Edition Coaching and Mentoring: Practical Techniques for Developing Learning and Performance, Third Edition read The Extraordinary Coach: How the Best Leaders Help Others Grow The Extraordinary Coach: How the Best Leaders Help Others Grow read Leading the Unleadable: How to Manage Mavericks, Cynics, Divas, and Other Difficult People Leading the Unleadable: How to Manage Mavericks, Cynics, Divas, and Other Difficult People read 100 Ways to Motivate Others: How Great Leaders Can Produce Insane Results without Driving People Crazy, Third Edition 100 Ways to Motivate Others: How Great Leaders Can Produce Insane Results without Driving People Crazy, Third Edition read Communicate Like a Leader: Connecting Strategically to Coach, Inspire, and Get Things Done Communicate Like a Leader: Connecting Strategically to Coach, Inspire, and Get Things Done listen 50 Top Tools for Coaching: A Complete Toolkit for Developing and Empowering People, Third Edition 50 Top Tools for Coaching: A Complete Toolkit for Developing and Empowering People, Third Edition

Architecting Hybrid Cloud Infrastructure with Anthos
By Nexus Human
Duration 2 Days 12 CPD hours This course is intended for This class is primarily intended for the following participants: Technical employees using GCP, including customer companies, partners and system integrators deployment engineers, cloud architects, cloud administrators, system engineers , and SysOps/DevOps engineers. Individuals using GCP to create, integrate, or modernize solutions using secure, scalable microservices architectures in hybrid environments. Overview Connect and manage Anthos GKE clusters from GCP Console whether clusters are part of Anthos on Google Cloud or Anthos deployed on VMware. Understand how service mesh proxies are installed, configured and managed. Configure centralized logging, monitoring, tracing, and service visualizations wherever the Anthos GKE clusters are hosted. Understand and configure fine-grained traffic management. Use service mesh security features for service-service authentication, user authentication, and policy-based service authorization. Install a multi-service application spanning multiple clusters in a hybrid environment. Understand how services communicate across clusters. Migrate services between clusters. Install Anthos Config Management, use it to enforce policies, and explain how it can be used across multiple clusters. This two-day instructor-led course prepares students to modernize, manage, and observe their applications using Kubernetes whether the application is deployed on-premises or on Google Cloud Platform (GCP). Through presentations, and hands-on labs, participants explore and deploy using Kubernetes Engine (GKE), GKE Connect, Istio service mesh and Anthos Config Management capabilities that enable operators to work with modern applications even when split among multiple clusters hosted by multiple providers, or on-premises. Anthos Overview Describe challenges of hybrid cloud Discuss modern solutions Describe the Anthos Technology Stack Managing Hybrid Clusters using Kubernetes Engine Understand Anthos GKE hybrid environments, with Admin and User clusters Register and authenticate remote Anthos GKE clusters in GKE Hub View and manage registered clusters, in cloud and on-premises, using GKE Hub View workloads in all clusters from GKE Hub Lab: Managing Hybrid Clusters using Kubernetes Engine Introduction to Service Mesh Understand service mesh, and problems it solves Understand Istio architecture and components Explain Istio on GKE add on and it's lifecycle, vs OSS Istio Understand request network traffic flow in a service mesh Create a GKE cluster, with a service mesh Configure a multi-service application with service mesh Enable external access using an ingress gateway Explain the multi-service example applications: Hipster Shop, and Bookinfo Lab: Installing Open Source Istio on Kubernetes Engine Lab: Installing the Istio on GKE Add-On with Kubernetes Engine Observing Services using Service Mesh Adapters Understand service mesh flexible adapter model Understand service mesh telemetry processing Explain Stackdriver configurations for logging and monitoring Compare telemetry defaults for cloud and on-premises environments Configure and view custom metrics using service mesh View cluster and service metrics with pre-configured dashboards Trace microservice calls with timing data using service mesh adapters Visualize and discover service attributes with service mesh Lab: Telemetry and Observability with Istio Managing Traffic Routing with Service Mesh Understand the service mesh abstract model for traffic management Understand service mesh service discovery and load balancing Review and compare traffic management use cases and configurations Understand ingress configuration using service mesh Visualize traffic routing with live generated requests Configure a service mesh gateway to allow access to services from outside the mesh Apply virtual services and destination rules for version-specific routing Route traffic based on application-layer configuration Shift traffic from one service version to another, with fine-grained control, like a canary deployment Lab: Managing Traffic Routing with Istio and Envoy Managing Policies and Security with Service Mesh Understand authentication and authorization in service mesh Explain mTLS flow for service to service communication Adopt mutual TLS authentication across the service mesh incrementally Enable end-user authentication for the frontend service Use service mesh access control policies to secure access to the frontend service Lab: Managing Policies and Security with Service Mesh Managing Policies using Anthos Config Management Understand the challenge of managing resources across multiple clusters Understand how a Git repository is as a configuration source of truth Explain the Anthos Config Management components, and object lifecycle Install and configure Anthos Config Management, operators, tools, and related Git repository Verify cluster configuration compliance and drift management Update workload configuration using repo changes Lab: Managing Policies in Kubernetes Engine using Anthos Config Configuring Anthos GKE for Multi-Cluster Operation Understand how multiple clusters work together using DNS, root CA, and service discovery Explain service mesh control-plane architectures for multi-cluster Configure a multi-service application using service mesh across multiple clusters with multiple control-planes Configure a multi-service application using service mesh across multiple clusters with a shared control-plane Configure service naming/discovery between clusters Review ServiceEntries for cross-cluster service discovery Migrate workload from a remote cluster to an Anthos GKE cluster Lab: Configuring GKE for Multi-Cluster Operation with Istio Lab: Configuring GKE for Shared Control Plane Multi-Cluster Operation

VMware vSphere Install Configure Manage (Official VMware IT Academy version)
By Nexus Human
Duration 4.875 Days 29.25 CPD hours This course is intended for VMware vSphere: Install, Configure, Manage features intensive hands-on training that focuses on installing, configuring, and managing VMware vSphere. This course prepares you to administer a vSphere infrastructure for an organization of any size and forms the foundation for most otherVMware technologies in the software-defined data center. Overview Describe the software-defined data center (SDDC) Explain the vSphere components and their function in the infrastructure Describe the benefits and capabilities of VMware Skyline Install and configure ESXi hosts Deploy and configure VMware vCenter Server Appliance⢠Use VMware vSphere Client⢠to manage the vCenter Server inventory and the vCenter Server configuration Manage, monitor, back up, and protect vCenter Server Appliance Create virtual networks with vSphere standard switches Describe the storage technologies supported by vSphere Configure virtual storage using iSCSI and NFS storage Create and manage VMware vSphere VMFS datastores Use the vSphere Client to create virtual machines, templates, clones, and snapshots Create a content library and deploy virtual machines from templates in the library Manage virtual machine resource use Migrate virtual machines with VMware vSphere vMotion and VMware vSphere Storage vMotion Create and manage a vSphere cluster that is enabled with VMware vSphere High Availability and VMware vSphere Distributed Resource Scheduler ⢠Discuss solutions for managing the vSphere life cycle Use VMware vSphere Lifecycle Manager⢠to perform upgrades to ESXi hosts and virtual machines This is an official VMware IT Academy course with official courseware and labs. Course introduction Introductions and course logistics Course objectives Introduction to vSphere and the Software-Defined Data Center Explain basic virtualization concepts Describe how vSphere fits into the software-defined data center and the cloud infrastructure Explain how vSphere interacts with CPUs, memory, networks, and storage Recognize the user interfaces for accessing the vCenter Server system and ESXi hosts Describe the ESXi host architecture Navigate the Direct Console User Interface (DCUI) to configure an ESXi host Recognize ESXi host user account best practices Install an ESXi host Use VMware Host Client? to configure ESXi host settings Describe how to proactively manage your vSphere environment using VMware Skyline Virtual Machines Create and provision a virtual machine Explain the importance of VMware Tools? Install VMware Tools Identify the files that make up a VM Recognize the components of a VM Recognize virtual devices supported by a VM Describe the benefits and use cases for containers Identify the parts of a container system vCenter Server Describe the vCenter Server architecture Discuss how ESXi hosts communicate with vCenter Server Deploy and configure vCenter Server Appliance Use vSphere Client to manage the vCenter Server inventory Add data center, organizational objects, and hosts to vCenter Server Use roles and permissions to enable users to access objects in the vCenter Server inventory Back up vCenter Server Appliance Monitor vCenter Server tasks, events, and appliance health Use VMware vCenter Server© High Availability to protect a vCenter Server Appliance Configuring and Managing Virtual Networks Create and manage standard switches Describe the virtual switch connection types Configure virtual switch security, traffic-shaping, and load-balancing policies Compare vSphere distributed switches and standard switches Configuring and Managing Virtual Storage Identify storage protocols and storage device types Discuss ESXi hosts using iSCSI, NFS, and Fibre Channel storage Create and manage VMFS and NFS datastores Explain how multipathing works with iSCSI, NFS, and Fibre Channel storage Recognize the components of a VMware vSAN? configuration Virtual Machine Management Use templates and cloning to deploy new virtual machines Modify and manage virtual machines Create a content library and deploy virtual machines from templates in the library Use customization specification files to customize a new virtual machine Perform vSphere vMotion and vSphere Storage vMotion migrations Describe the Enhanced vMotion Compatibility feature Create and manage virtual machine snapshots Examine the features and functions of VMware vSphere© Replication? Describe the benefits of VMware vSphere© Storage APIs ? Data Protection Resource Management and Monitoring Discuss CPU and memory concepts in a virtualized environment Describe what overcommitment of a resource means Describe methods for optimizing CPU and memory usage Use various tools to monitor resource use Create and use alarms to report certain conditions or events vSphere Clusters Describe the functions of a vSphere DRS cluster Create a vSphere DRS cluster Monitor a vSphere cluster configuration Describe options for making a vSphere environment highly available Explain the vSphere HA architecture Configure and manage a vSphere HA cluster Examine the features and functions of VMware vSphere© Fault Tolerance Describe the function of the vSphere© Cluster Service vSphere Lifecycle Management Recognize the importance of vCenter Server Update Planner Describe how VMware vSphere© Lifecycle Manager? works Describe how to update ESXi hosts using baselines Validate ESXi host compliance using a cluster image Describe how to upgrade VMware Tools and VM hardware Describe VMware vSphere© Lifecycle Manager? and VMware vSAN? integration

Business Administration Level 3
By Rachel Hood
Supporting and engaging with different parts of the organisation and interact with internal or external customer.

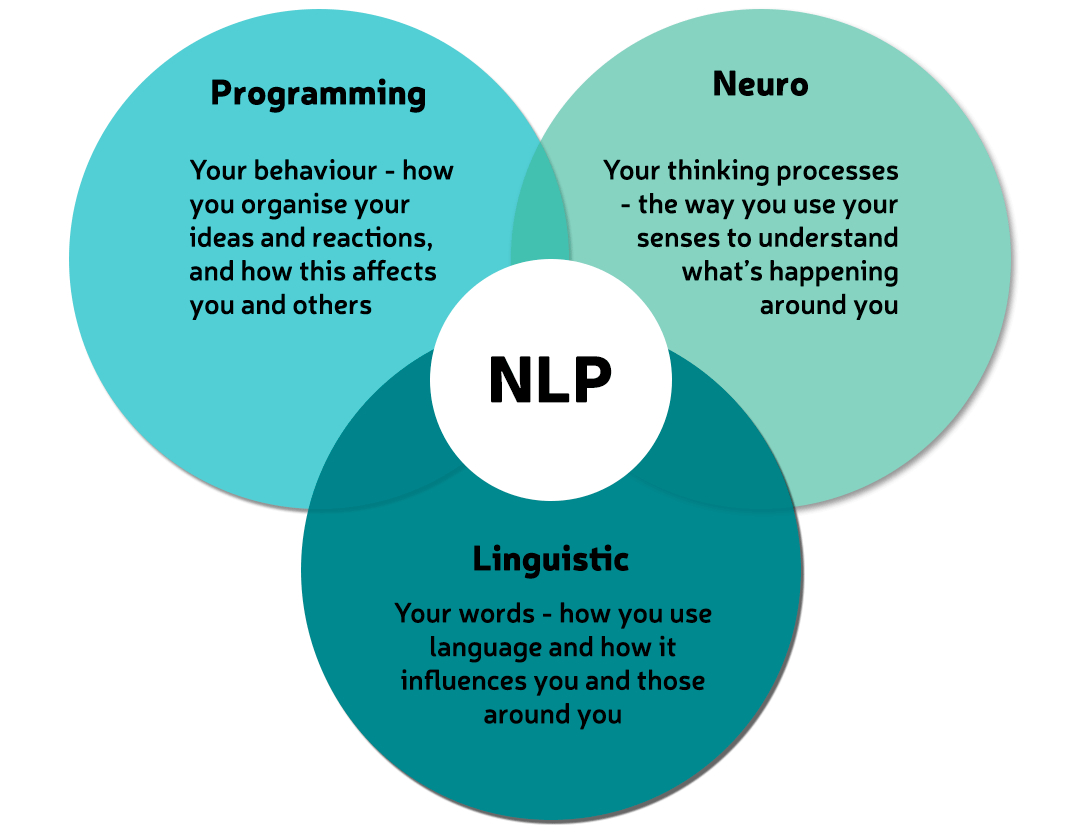
What is NLP?
By Proactive NLP Ltd
What is NLP? Join proactivenlp.com on this virtual workshop and find out how NLP can start changing your life by saying goodbye to the negatives and welcoming in all the positives you want.
Workplace First Aid & Emergency Response Training
By NextGen Learning
Gain life-saving skills with this CPD-accredited First Aid Course. Learn CPR, AED use, injury management, and emergency response for any situation.

F5 Networks Configuring BIG-IP Advanced WAF - Web Application Firewall (formerly ASM)
By Nexus Human
Duration 4 Days 24 CPD hours This course is intended for This course is intended for security and network administrators who will be responsible for the installation, deployment, tuning, and day-to-day maintenance of the F5 Advanced Web Application Firewall. In this 4 day course, students are provided with a functional understanding of how to deploy, tune, and operate F5 Advanced Web Application Firewall to protect their web applications from HTTP-based attacks. The course includes lecture, hands-on labs, and discussion about different F5 Advanced Web Application Firewall tools for detecting and mitigating threats from multiple attack vectors such web scraping, Layer 7 Denial of Service, brute force, bots, code injection, and zero day exploits. Module 1: Setting Up the BIG-IP System Introducing the BIG-IP System Initially Setting Up the BIG-IP System Archiving the BIG-IP System Configuration Leveraging F5 Support Resources and Tools Module 2: Traffic Processing with BIG-IP Identifying BIG-IP Traffic Processing Objects Overview of Network Packet Flow Understanding Profiles Overview of Local Traffic Policies Visualizing the HTTP Request Flow Module 3: Web Application Concepts Overview of Web Application Request Processing Web Application Firewall: Layer 7 Protection F5 Advanced WAF Layer 7 Security Checks Overview of Web Communication Elements Overview of the HTTP Request Structure Examining HTTP Responses How F5 Advanced WAF Parses File Types, URLs, and Parameters Using the Fiddler HTTP Proxy Module 4: Common Web Application Vulnerabilities A Taxonomy of Attacks: The Threat Landscape What Elements of Application Delivery are Targeted? Common Exploits Against Web Applications Module 5: Security Policy Deployment Defining Learning Comparing Positive and Negative Security Models The Deployment Workflow Policy Type: How Will the Policy Be Applied Policy Template: Determines the Level of Protection Policy Templates: Automatic or Manual Policy Building Assigning Policy to Virtual Server Deployment Workflow: Using Advanced Settings Selecting the Enforcement Mode The Importance of Application Language Configure Server Technologies Verify Attack Signature Staging Viewing Requests Security Checks Offered by Rapid Deployment Defining Attack Signatures Using Data Guard to Check Responses Module 6: Policy Tuning and Violations Post-Deployment Traffic Processing Defining Violations Defining False Positives How Violations are Categorized Violation Rating: A Threat Scale Defining Staging and Enforcement Defining Enforcement Mode Defining the Enforcement Readiness Period Reviewing the Definition of Learning Defining Learning Suggestions Choosing Automatic or Manual Learning Defining the Learn, Alarm and Block Settings Interpreting the Enforcement Readiness Summary Configuring the Blocking Response Page Module 7: Attack Signatures & Threat Campaigns Defining Attack Signatures Attack Signature Basics Creating User-Defined Attack Signatures Defining Simple and Advanced Edit Modes Defining Attack Signature Sets Defining Attack Signature Pools Understanding Attack Signatures and Staging Updating Attack Signatures Defining Threat Campaigns Deploying Threat Campaigns Module 8: Positive Security Policy Building Defining and Learning Security Policy Components Defining the Wildcard Defining the Entity Lifecycle Choosing the Learning Scheme How to Learn: Never (Wildcard Only) How to Learn: Always How to Learn: Selective Reviewing the Enforcement Readiness Period: Entities Viewing Learning Suggestions and Staging Status Violations Without Learning Suggestions Defining the Learning Score Defining Trusted and Untrusted IP Addresses How to Learn: Compact Module 9: Cookies and Other Headers F5 Advanced WAF Cookies: What to Enforce Defining Allowed and Enforced Cookies Configuring Security Processing on HTTP headers Module 10: Reporting and Logging Overview: Big Picture Data Reporting: Build Your Own View Reporting: Chart based on filters Brute Force and Web Scraping Statistics Viewing F5 Advanced WAF Resource Reports PCI Compliance: PCI-DSS 3.0 The Attack Expert System Viewing Traffic Learning Graphs Local Logging Facilities and Destinations How to Enable Local Logging of Security Events Viewing Logs in the Configuration Utility Exporting Requests Logging Profiles: Build What You Need Configuring Response Logging Module 11: Lab Project 1 Lab Project 1 Module 12: Advanced Parameter Handling Defining Parameter Types Defining Static Parameters Defining Dynamic Parameters Defining Dynamic Parameter Extraction Properties Defining Parameter Levels Other Parameter Considerations Module 13: Automatic Policy Building Overview of Automatic Policy Building Defining Templates Which Automate Learning Defining Policy Loosening Defining Policy Tightening Defining Learning Speed: Traffic Sampling Defining Track Site Changes Lesson 14: Web Application Vulnerability Scanner Integration Integrating Scanner Output Importing Vulnerabilities Resolving Vulnerabilities Using the Generic XML Scanner XSD file Lesson 15: Deploying Layered Policies Defining a Parent Policy Defining Inheritance Parent Policy Deployment Use Cases Lesson 16: Login Enforcement and Brute Force Mitigation Defining Login Pages for Flow Control Configuring Automatic Detection of Login Pages Defining Session Tracking Brute Force Protection Configuration Source-Based Brute Force Mitigations Defining Credentials Stuffing Mitigating Credentials Stuffing Lesson 17: Reconnaissance with Session Tracking Defining Session Tracking Configuring Actions Upon Violation Detection Lesson 18: Layer 7 DoS Mitigation Defining Denial of Service Attacks Defining the DoS Protection Profile Overview of TPS-based DoS Protection Creating a DoS Logging Profile Applying TPS Mitigations Defining Behavioral and Stress-Based Detection Lesson 19: Advanced Bot Protection Classifying Clients with the Bot Defense Profile Defining Bot Signatures Defining Proactive Bot Defense Defining Behavioral and Stress-Based Detection Defining Behavioral DoS Mitigation Lesson 20: Form Encryption using DataSafe Targeting Elements of Application Delivery Exploiting the Document Object Model Protecting Applications Using DataSafe The Order of Operations for URL Classification Lesson 21: Review and Final Labs Review and Final Labs
