- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
2176 Courses in Nottingham delivered Live Online
HP ProCurve training course description A hands on course covering the product specifics of HP switches. Installation, configuration, maintenance and troubleshooting are all covered in a practical oriented way. VLANs often take up a large part of the course. The course covers all interfaces but concentrates on using the command line interface. Delegates are, however, free to use the web based interface in all exercises. What will you learn Install HP ProCurve switches. Use the command line interface and the web based interface to manage HP ProCurve switches. Configure and troubleshoot HP ProCurve switches. Perform software upgrades and maintain configurations using TFTP. HP ProCurve training course details Who will benefit: Anyone working with HP switches. Particularly aimed at engineers and technicians supporting HP switches. Prerequisites: None. Duration 2 days HP ProCurve training course content Introduction Traditional Ethernet, Hubs, Frames, MAC addresses. Hands on Building a network with a hub What is a switch? Switches versus hubs, the MAC address table, handling unknown addresses. Hands on Building a network with HP switches. Configuration methods How to configure a HP switch using: Console port access menus, CLI, telnet, web based access. Hands on Console access, show commands, using the menus, IP address configuration, telnet. Command Line Interface Operator mode, Manager mode, configuration mode, passwords, online help, CLI commands, basic troubleshooting. Hands on More show commands, basic troubleshooting, setting a password, displaying status and counters. Web based interface Web access, basic format, Getting started. SSL. Hands on Web based configuration. Port configuration Common port configuration tasks, port security, port aggregation. Hands on Configuring ports. Trunking and failover. STP configuration Broadcast storms. What is STP? RSTP. Configuring STP. Hands on Enabling and disabling STP, investigation failover. VLAN configuration What are VLANS? 802.1Q, tagged/untagged, creating VLANS, applying VLANS. Addressing and VLANs, Layer 3 switches and VLANs. Hands on Setting up VLANS, setting up tagged ports, Inter VLAN traffic. Housekeeping TFTP, software upgrades, downloading configurations. Hands on Software upgrade, downloading a configuration. SNMP SNMP configuration, HP OpenView. Hands on Using SNMP to manage a HP ProCurve switch. Basic troubleshooting Putting it all together. Layer 1 troubleshooting, Layer 2 troubleshooting. Miscellaneous exercises CDP. Logging

HP switches training course description A hands on course covering the product specifics of HP switches. Installation, configuration, maintenance and troubleshooting are all covered in a practical oriented way. VLANs often take up a large part of the course. The course covers all interfaces but concentrates on using the command line interface. Delegates are, however, free to use the web based interface in all exercises. What will you learn Install HP switches. Use the command line interface and the web based interface to manage HP switches. Configure and troubleshoot HP switches. Perform software upgrades and maintain configurations using TFTP. HP switches training course details Who will benefit: Anyone working with HP switches. Particularly aimed at engineers and technicians supporting HP switches. Prerequisites: None. Duration 2 days HP switches training course content Introduction Traditional Ethernet, Hubs, Frames, MAC addresses. Hands on Building a network with a hub. What is a switch? Switches versus hubs, the MAC address table, handling unknown addresses. Hands on Building a network with HP switches. Configuration methods How to configure a HP switch using: Console port access menus, CLI, telnet, web based access. Hands on Console access, show commands, using the menus, IP address configuration, telnet. Command Line Interface Operator mode, Manager mode, configuration mode, passwords, online help, CLI commands, basic troubleshooting. Hands on More show commands, basic troubleshooting, setting a password, displaying status and counters. Web based interface Web access, basic format, Getting started. SSL. Hands on Web based configuration. Port configuration Common port configuration tasks, port security, port aggregation, Hands on Configuring ports. Trunking and failover. STP configuration Broadcast storms. What is STP? RSTP. Configuring STP. Hands on Enabling and disabling STP, investigation failover. VLANs What are VLANS? 802.1Q, tagged/untagged, creating VLANS, applying VLANS. Addressing and VLANs, Layer 3 switches and VLANs. Hands on Setting up VLANS, setting up tagged ports, Inter VLAN traffic. Housekeeping TFTP, software upgrades, downloading configurations. Hands on Software upgrade, downloading a configuration. SNMP SNMP configuration, HP OpenView NNM. Hands on Using SNMP to manage a HP switch. Basic troubleshooting Putting it all together. Layer 1 troubleshooting, Layer 2 troubleshooting. Miscellaneous exercises CDP. Logging

Course Introduction Covers B12 deficiency, pernicious anaemia, diagnosis, treatment and management. It also covers signs and symptoms. This course does cover how to set up your own service. Please note: this course is for health care professionals or those working in Primary Care. It is not open to Beauticians unless you are a registered healthcare professional. If in doubt- please email annie at training@anniebarr.com or phone +44 7500048222 About this event Course Introduction This course concentrates on B12 deficiency, symptoms, treatments and management. The course covers B12 deficiency, pernicious anaemia, diagnosis, treatment and management. It also covers signs and symptoms of pernicious anaemia. This course is interactive and we include case studies and discuss issues regarding diagnostic testing. We review inclusion and exclusion criteria and identification of appropriate clients. Delegates will get the opportunity to review practice with hands on practical demonstrations of how to give injections correctly. We will cover administration techniques, where to give the injections and record keeping / documentation. We will discuss role and responsibilities and contraindications and precautions. The delegates will leave this course with an example of an individual protocol of Patient Specific Direction (PSD) and a competence based framework document to be used in practice. This course is very interactive. AIMS AND OBJECTIVES Understand the need for accountability and responsibility in relation to role development Demonstrate an understanding of safe practice Describe the signs and symptoms of pernicious anaemia Describe pernicious anaemia and its impact on patients Fully understand the principles, and practice B12 deficiency and B12 injections Understand the importance of safety issues related to giving injections Understand the law relating to role and function of the HCA and prescribing. Describe why patients require B12 injectionsBe able to correctly identify anatomical sites for injectionsDemonstrate correct administration techniquesDemonstrate how to correctly dispose of wasteDemonstrate correct infection control procedures and use of PPEDescribe when patients require referral and understand the importance of referral using correct clinical pathwaysDemonstrate an understanding of anaphylaxis and emergency proceduresUnderstand the need for correct prescribing proceduresBe able to document consultations following your organisations procedures COURSE CONTENTS Role and responsibilities Accountability guidelines and requirements Pernicious anaemia Blood- function B12 Deficiency Risk factors/groups Causes of B12 deficiency Diagnosis and reference ranges, testing Protocols and guidelines Factors affecting B12 diagnosis and treatment Factors affecting absorption B12 injections and common side effects Could it be B12 Deficiency Supplements Side effects and management including ADR’s Contraindications and Precautions Correct Administration and techniques including practical session Injection sites Legal Issues including consent Prescribing and Patient Specific Directions What to record Storage Disposal of injections/waste Infection control Needle stick injuries Competence and supervised practice Policies and procedures Facts and Figures Setting up and running a clinic Insurance/indemnity Research/evidence base and resources Please note Anaphylaxis is not covered on this course, however we do run a separate Anaphylaxis 1hr training course, which takes place at the end of this B12 webinar. If you wish to do the 1 hr Anaphylaxis also, you should book onto BOTH courses. WHO SHOULD ATTEND? HCAs Nurses Doctors Pharmacists Anyone interested in Vitamin B12 deficiency and pernicious anaemia and those working with clients with B12 deficiency AB Health Group awards CPD points / certificate of attendance for each course. If you would prefer an accredited certificate by our accrediting body Aim Qualifications we can organise this. The charge for the certificate including postage is £30.

PMI-PBA Exam Prep: In-House Training
By IIL Europe Ltd
PMI-PBA® Exam Prep: In-House Training The course provides targeted exam preparation support for PMI®'s Professional in Business Analysis exam candidates, including a content review of The PMI Guide to Business Analysis, a review of the PMI-PBA® reference books, and an exam preparation tutorial. You will be given a Study Guide that you can re-use to assess your knowledge gaps as part of your Personal Action Plan. Your score on this for each Knowledge Area can be compared to your results on the quiz at the end of each course module to guide your study efforts. What you will Learn Upon completion, participants will be able to: Demonstrate familiarity with the structure, content and framework of The PMI Guide to Business Analysis Explain the six Knowledge Areas of The PMI Guide to Business Analysis, as well as, their inter-relationships with each other and the six Process Groups Differentiate among the five business analysis domains in the project life cycle Create a personal action plan to study and prepare for the PMI-PBA® Exam Getting Started PMI-PBA Examination Certification Process The Credential Examination Foundation Concepts for PMI-PBA® Prep Business analysis terminology and definitions Business analysis project, program, and portfolio management Product and project life cycles Skills and qualities of a business analyst Introduction to Business Analysis in Projects Business analysis overview How organizations implement business analysis Business analyst and project manager relationships Requirements definitions and types Practice quiz On-Demand Segment A: Define the Business Problem (Pre-work for Needs Assessment) Needs Assessment Review Needs Assessment knowledge area Identify problem or opportunity Assess current and future state Determine options and provide recommendations Facilitate product roadmap development Assemble business case Practice quiz Stakeholder Engagement Review Stakeholder Engagement knowledge area Identify Stakeholders and conduct analysis Determine Stakeholder engagement and communication approach Conduct business analysis planning Practice quiz On-Demand Segment B: The Elicitation Plan (Pre-work for Elicitation) Elicitation Review Elicitation knowledge area Determine Elicitation approach Preparing for Elicitation Conducting Elicitation Confirming Elicitation results Practice quiz On-Demand Segment C: Overview of Requirements Analysis (Pre-work for Analysis) Analysis Review Analysis knowledge area Determine Analysis approach Create and analyze models Define requirements and acceptance criteria Verify, validate, and prioritize requirements Identify and analyze product risks Assess product design options Practice quiz Traceability and Monitoring Review Traceability and Monitoring knowledge area Determine Traceability and Monitoring approach Establish relationships and dependencies Select and approve requirements Make changes to requirements and other product information Practice quiz Solution Evaluation Review Solution Evaluation knowledge area Evaluate solution performance Determine solution evaluation approach Evaluate acceptance results and address defects Obtain solution acceptance for release Practice quiz Exam Application and Preparation Process Applying for the Exam Studying for the Exam Sitting for the Exam Reviewing your Knowledge Gap Practice Exam Study Guide - a reliable learning aid Summary and Next Steps Crystallizing the Business Analysis Domains Developing a Personal Action Plan for Exam Study

EC-Council Certified Ethical Hacker (CEH) v12
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for The Certified Ethical Hacking v12 course will significantly benefit security officers, auditors, security professionals, site administrators, and anyone who is concerned about the integrity of the network infrastructure. Overview Information security controls, laws, and standards. Various types of footprinting, footprinting tools, and countermeasures. Network scanning techniques and scanning countermeasures Enumeration techniques and enumeration countermeasures Vulnerability analysis to identify security loopholes in the target organization?s network, communication infrastructure, and end systems. System hacking methodology, steganography, steganalysis attacks, and covering tracks to discover system and network vulnerabilities. Different types of malware (Trojan, Virus, worms, etc.), system auditing for malware attacks, malware analysis, and countermeasures. Packet sniffing techniques to discover network vulnerabilities and countermeasures to defend against sniffing. Social engineering techniques and how to identify theft attacks to audit human-level vulnerabilities and social engineering countermeasures. DoS/DDoS attack techniques and tools to audit a target and DoS/DDoS countermeasures. Session hijacking techniques to discover network-level session management, authentication/authorization, and cryptographic weaknesses and countermeasures. Webserver attacks and a comprehensive attack methodology to audit vulnerabilities in webserver infrastructure, and countermeasures. Web application attacks, comprehensive web application hacking methodology to audit vulnerabilities in web applications, and countermeasures. SQL injection attack techniques, injection detection tools to detect SQL injection attempts, and countermeasures. Wireless encryption, wireless hacking methodology, wireless hacking tools, and Wi-Fi security tools. Mobile platform attack vector, android vulnerability exploitations, and mobile security guidelines and tools. Firewall, IDS and honeypot evasion techniques, evasion tools and techniques to audit a network perimeter for weaknesses, and countermeasures. Cloud computing concepts (Container technology, serverless computing), the working of various threats and attacks, and security techniques and tools. Penetration testing, security audit, vulnerability assessment, and penetration testing roadmap. Threats to IoT and OT platforms and defending IoT and OT devices. Cryptography ciphers, Public Key Infrastructure (PKI), cryptography attacks, and cryptanalysis tools. CEH provides an in-depth understanding of ethical hacking phases, various attack vectors, and preventative countermeasures. It will teach you how hackers think and act maliciously so you will be better positioned to setup your security infrastructure and defend against future attacks. An understanding of system weaknesses and vulnerabilities helps organizations strengthen their system security controls to minimize the risk of an incident. CEH was built to incorporate a hands-on environment and systematic process across each ethical hacking domain and methodology, giving you the opportunity to work towards proving the required knowledge and skills needed to achieve the CEH credential. You will be exposed to an entirely different posture toward the responsibilities and measures required to be secure. Now in its 12th version, CEH continues to evolve with the latest operating systems, tools, tactics, exploits, and technologies. 1 - Introduction to Ethical Hacking Information Security Overview Cyber Kill Chain Concepts Hacking Concepts Ethical Hacking Concepts Information Security Controls Information Security Laws and Standards 2 - 2 - Foot-printing and Reconnaissance Footprinting Concepts Footprinting through Search Engines Footprinting through Web Services Footprinting through Social Networking Sites Website Footprinting Email Footprinting Who is Footprinting DNS Footprinting Network Footprinting Footprinting through Social Engineering Footprinting Tools Footprinting Countermeasures 3 - Scanning Networks Network Scanning Concepts Scanning Tools Host Discovery Port and Service Discovery OS Discovery (Banner Grabbing/OS Fingerprinting) Scanning Beyond IDS and Firewall Draw Network Diagrams 4 - Enumeration Enumeration Concepts NetBIOS Enumeration SNMP Enumeration LDAP Enumeration NTP and NFS Enumeration SMTP and DNS Enumeration Other Enumeration Techniques Enumeration Countermeasures 5 - Vulnerability Analysis Vulnerability Assessment Concepts Vulnerability Classification and Assessment Types Vulnerability Assessment Solutions and Tools Vulnerability Assessment Reports 6 - System Hacking System Hacking Concepts Gaining Access Escalating Privileges Maintaining Access Clearing Logs 7 - Malware Threats Malware Concepts APT Concepts Trojan Concepts Virus and Worm Concepts Fileless Malware Concepts Malware Analysis Countermeasures Anti-Malware Software 8 - Sniffing Sniffing Concepts Sniffing Technique: MAC Attacks Sniffing Technique: DHCP Attacks Sniffing Technique: ARP Poisoning Sniffing Technique: Spoofing Attacks Sniffing Technique: DNS Poisoning Sniffing Tools Countermeasures Sniffing Detection Techniques 9 - Social Engineering Social Engineering Concepts Social Engineering Techniques Insider Threats Impersonation on Social Networking Sites Identity Theft Countermeasures 10 - Denial-of-Service DoS/DDoS Concepts DoS/DDoS Attack Techniques BotnetsDDoS Case Study DoS/DDoS Attack Tools Countermeasures DoS/DDoS Protection Tools 11 - Session Hijacking Session Hijacking Concepts Application Level Session Hijacking Network Level Session Hijacking Session Hijacking Tools Countermeasures 12 - Evading IDS, Firewalls, and Honeypots IDS, IPS, Firewall, and Honeypot Concepts IDS, IPS, Firewall, and Honeypot Solutions Evading IDS Evading Firewalls IDS/Firewall Evading Tools Detecting Honeypots IDS/Firewall Evasion Countermeasures 13 - Hacking Web Servers Web Server Concepts Web Server Attacks Web Server Attack Methodology Web Server Attack Tools Countermeasures Patch Management Web Server Security Tools 14 - Hacking Web Applications Web Application Concepts Web Application Threats Web Application Hacking Methodology Web API, Webhooks, and Web Shell Web Application Security 15 - SQL Injection SQL Injection Concepts Types of SQL Injection SQL Injection Methodology SQL Injection Tools Evasion Techniques Countermeasures 16 - Hacking Wireless Networks Wireless Concepts Wireless Encryption Wireless Threats Wireless Hacking Methodology Wireless Hacking Tools Bluetooth Hacking Countermeasures Wireless Security Tools 17 - Hacking Mobile Platforms Mobile Platform Attack Vectors Hacking Android OS Hacking iOS Mobile Device Management Mobile Security Guidelines and Tools 18 - IoT and OT Hacking IoT Hacking IoT Concepts IoT Attacks IoT Hacking Methodology IoT Hacking Tools Countermeasures OT Hacking OT Concepts OT Attacks OT Hacking Methodology OT Hacking Tools Countermeasures 19 - Cloud Computing Cloud Computing Concepts Container Technology Serverless Computing Cloud Computing Threats Cloud Hacking Cloud Security 20 - Cryptography Cryptography Concepts Encryption Algorithms Cryptography Tools Public Key Infrastructure (PKI) Email Encryption Disk Encryption Cryptanalysis Countermeasures Additional course details: Nexus Humans EC-Council Certified Ethical Hacker (CEH) v.12 training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the EC-Council Certified Ethical Hacker (CEH) v.12 course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Revit V-Ray 3ds Max Visualization Training Course
By ATL Autocad Training London
Why Learn Revit V-Ray 3ds Max Visualization Training Course? Revit is perfect for architecture, and 3ds Max, with V-Ray rendering, offers super results. Autodesk Revit Interoperability integrates Revit and 3ds Max seamlessly, combining metadata, materials, and lighting. Architects and designers using 3ds Max tools for architectural designs. Check our Website Booking: 1-on-1 Duration: You can split these 40 hours over as many days, Mon to Sat between 9 am to 7 pm, or call 02077202581 to book In-person or Live Online Module 1: Revit Fundamentals (16 hours) Introduction to Revit: Acquaint yourself with Revit's essential concepts and tools. Interface and Workspace: Navigate Revit's interface and workspace seamlessly. Building Information Modeling (BIM) Workflow: Grasp the fundamental BIM workflow principles for effective modeling. Basic Building Model Creation: Learn to craft a foundational building model using Revit. Basic Modeling Techniques: Master elements like walls, doors, windows, floors, roofs, stairs, and railings. Advanced Revit Modeling: Dive into advanced topics, including family creation and working with intricate geometries. Annotation and Documentation: Enhance your projects with text, dimensions, schedules, and efficient printing/exporting methods. Module 2: 3ds Max Mastery (16 hours) Introduction to 3ds Max: Familiarize yourself with the core aspects and interface of 3ds Max. 3D Modeling Workflow: Understand the intricacies of creating basic 3D models in 3ds Max. Basic 3D Modeling Techniques: Work with primitive shapes, splines, and create complex 3D models. Materials and Textures: Explore the material editor, apply materials, and craft realistic textures. Lighting and Cameras: Learn to illuminate scenes, utilize the daylight system, and optimize camera angles. Module 3: V-Ray Rendering Proficiency (8 hours) Introduction to V-Ray: Grasp the fundamentals of V-Ray, including its interface and workflow. V-Ray Materials and Textures: Understand the intricacies of V-Ray materials and textures for lifelike renderings. Basic Rendering Techniques: Dive into essential rendering techniques, including lighting adjustments and global illumination. Advanced Rendering Methods: Explore advanced techniques to elevate the quality of your renders. Gain expertise in Revit, 3ds Max, and V-Ray through our comprehensive training, mastering the core concepts and advanced techniques necessary for stunning architectural visualizations. Upon completing the course, you will: Master Architectural Modeling: Proficiently create intricate architectural models using Revit and 3ds Max. Visualize Realistically: Utilize advanced rendering techniques in V-Ray for lifelike visualizations with realistic lighting and materials. Efficient Documentation: Learn annotation and documentation skills for clear and effective project communication. Enhance Collaboration: Understand file interoperability for seamless collaboration with diverse software platforms. Build a Professional Portfolio: Create a diverse portfolio showcasing your skills in architectural visualization. Career Opportunities: Upon completion, you can pursue roles such as: Architectural Visualizer 3D Modeler Render Artist BIM Specialist Freelancer/Consultant Architectural Technician Visualization Trainer Mastering these tools opens doors to versatile career opportunities in architectural visualization. Download Revit Download 3ds max Download Vray Revit and 3dsMax V-Ray Visualization Training: Master architectural visualization with our intensive course blending Revit, 3dsMax, and V-Ray. Dive into modeling, materials, lighting, and rendering for photorealistic results. Course Highlights: Comprehensive Learning: Cover fundamental and advanced techniques in Revit and 3dsMax, enhancing your visualization skills. V-Ray Expertise: Explore advanced V-Ray rendering techniques, from global illumination to realistic material creation. Real-World Projects: Work on industry-relevant projects, building a portfolio of professional-grade visualizations. Flexible Learning: Choose in-person or live online sessions for interactive instruction and engaging discussions. Lesson Recordings: Access session recordings to review concepts, reinforcing your learning at your own pace. Lifetime Support: Enjoy lifetime email support for ongoing guidance from experienced instructors, ensuring your success beyond the course. Enroll now to transform your architectural designs into captivating visualizations, impressing clients with your skills and creativity. Join our training for a comprehensive learning experience, enhancing your expertise in Revit, 3dsMax, and V-Ray. Revit | 3ds max | V-Ray Course Benefits: Comprehensive Skill Set: Master Revit, 3dsMax, and V-Ray for exceptional architectural visualization, from basic modeling to advanced rendering. Realistic Rendering: Harness V-Ray's capabilities for lifelike visuals, covering global illumination, materials, and textures. Practical Experience: Work on industry-relevant projects, building a professional portfolio with hands-on exercises. Flexible Learning: Choose in-person or live online sessions for interactive instruction and discussion, tailored to your preferences. Review Resources: Access recorded class sessions to reinforce your knowledge and skills at your convenience. Lifetime Support: Enjoy lifetime email support from experienced instructors, ensuring ongoing guidance for your projects.
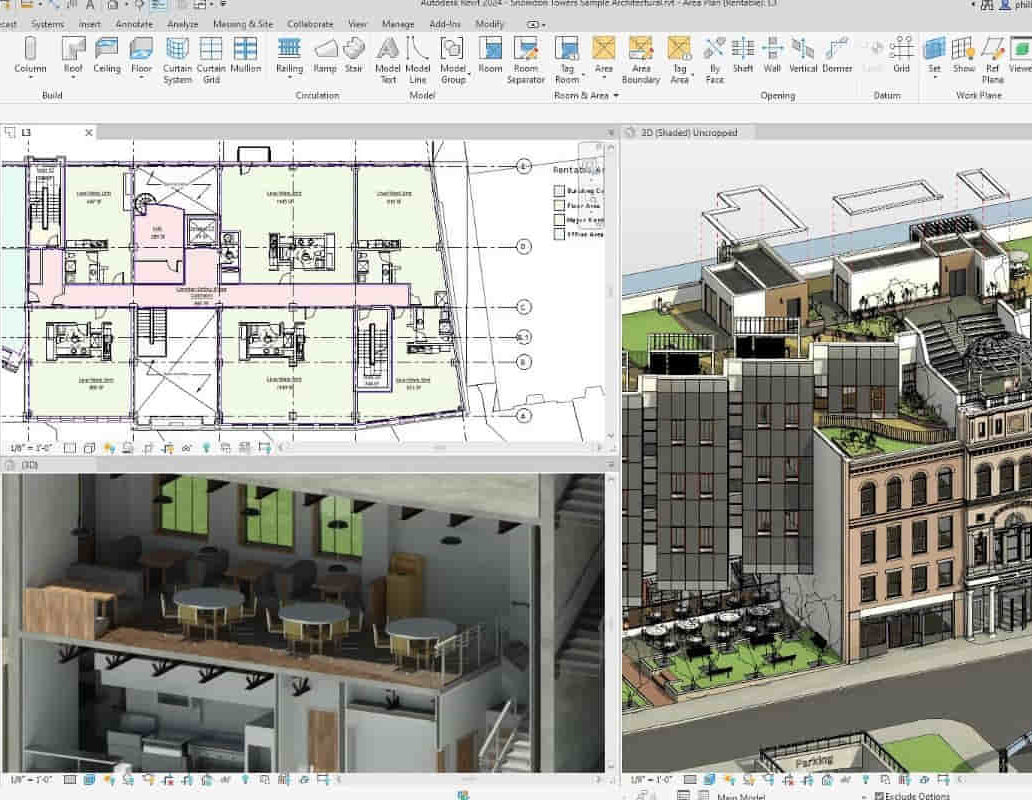
Introduction to Reactive Spring (TT3355 )
By Nexus Human
Duration 4 Days 24 CPD hours This course is intended for This in an intermediate-level Java development course geared for students experienced with Java and Spring programming essentials. This course does not cover Java or Spring development basics. Overview Working within in an engaging, hands-on learning environment, guided by our expert team, attendees will: Understand the ReactiveX specification Understand the basics of Reactive Programming Discuss the advantages and limitations of Observables Write a client application capable of handling Reactive events Apply operators to event streams to filter, modify and combine the objects emitted by event publishers Select the appropriate type of Event Source Use both Cold and Hot Observables Deal with backpressure problems in reactive programming Develop a reactive web application using Spring WebFlux Define application flows of a WebFlux application Use the WebClient API to work with both synchronous and streaming APIs Develop Unit and Integration tests to test WebFlux endpoints Creating a reactive REST endpoint Become familiar with the basics of WebSockets Create a WebSocket endpoint using Spring Create a WebSocket client Understand the basics of NoSQL Become familiar with the basics of MongoDB Understand how the data in MongoDB can be retrieved using a Reactive API Define Spring Data MongoDB repositories Query the MongoDB using Spring Data Define a reactive repository using MongoDB Explore the Spring Data R2DBC API to perform reactive CRUD operations against a relational database Spring Data reative allow us to implement database operations relying on Reative Programming APIs. While the Spring R2DBC initiative aims to bring reactive programming to relational databaes, several NoSQL databases already provide this possibility. After an introduction to NoSQL and the MongoDB, this courses covers the APIs available to communicate with this NoSQL database using both blocking and reactive APIs.Introdcution to Reactive Spring is a comprehensive Java training workshop geared for experienced developers who wish to explore concurrent, asynchronous and reactive programming APIs and techniques using Spring. After an introduction to reactive programming, Reactive Streams and the Project Reactor APIs, this course will show how this APIs are integrated into Spring. Spring 5 includes Spring WebFlux, providing a reactive programming model for web applications, including support for Reactive REST APIs. Spring WebSocket assists in the creation of web applications which provide a full-duplex, two-way communication between client and server. Introduction to Reactive Programming Reactive Manifesto Introduce ReactiveX ReactiveX implementations The Observer, Iterator pattern and functional programming Discuss hot and cold publishers Reactive Streams API Introduce the Reactive Streams specification Publisher and Subscribers java.util.concurrent.Flow Transformation of Messages (Processor) Controlling messages Tutorial: Setup Eclipse for Using Maven Introduction Introduce the Reactor Building blocks Flux and Mono Creating observables Subscribing to a stream Testing Event Sources (introduction) Testing reactive implementations StepVerifier : test sequence of emitted items Defining expectations TestPublisher: produce test data to test downstream operators Reactive Operators Introduce Operators Show the use of marble diagrams Explain some commonly used operators Callback operators Schedulers (Multithreading) Thread usage of subscriber and consumer Using the subscribeOn method Introduce the Scheduler interface Using the observeOn method Backpressure Strategies for dealing with Backpressure ?reactive pull? backpressure Exception Handling Handling errors in onError Exception handling strategies Using onErrorReturn or onErrorNext operators Using the retry operators The Global Error Handler Spring Data Review Quick review of Spring Data repositories Query return types Defining Query methods Pagination and sorting R2DBC Reactive Relational Database Connectivity DatabaseClient Performing CRUD operations Reactive Query annotated methods Spring WebFlux: Introduction Annotated Controllers Functional Endpoints WebFlux configuration Creating a reactive REST endpoint Defining flows Defining the application flow Actions Defining decision Navigating flows RouterFunction View Technologies View technologies Using Thymeleaf to create the view View Configuration Spring WebClient: Introduction to WebClient Working with asynchronous and streaming APIs Making requests Handling the response Lab: WebClient WebTestClient Testing WebFlux server endpoints Testing controllers or functions Define integration tests Introduction to Spring Reactive WebSockets Be familiar with the basics of WebSockets Understand the HTTP handshake and upgrade Name some of the advantages of WebSockets Defining the WebSocket WebSocket Message Handling WebSocketSession Implementing the WebSockethandler Creating a Browser WebSocket Client WebSocket STOMP Streaming (or Simple) text-orientated messaging protocol Introduce SockJS Connecting to the STOMP endpoint Configuring the message broker STOMP destinations Reactive WebSocket Reactive WebSocket support Implement the reactive WebSocketHandler BigData Introduce Big Data Explain the need for enhanced data storage Introduction to MongoDB JavaScript Object Notation Overview Introduce Binary JSON (BSON) Starting the database Creating Collections and Documents Executing ?simple? database commands Introduce the ObjectID Searching for documents using query operators Updating and deleting documents MongoDB Compass Spring and MongoDB MongoDB Support in Spring Data MongoClient and MongoTemplate Spring Data MongoDB configuration @EnableMongoRepositories Adding documents to the database The @Document and @Field annotations Polymorphism and the _class property The Criteria object Spring Data MongoDB MongoRepository Field naming strategy Using JSON queries to find documents The @PersistenceConstructor annotation Reactive Repositories with MongoDB Using reactive repositories ReactiveMongoTemplate RxJava or Reactor Additional course details: Nexus Humans Introduction to Reactive Spring (TT3355 ) training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Introduction to Reactive Spring (TT3355 ) course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Portfolio, Programs, & Project Offices Practitioner: In-House
By IIL Europe Ltd
Portfolio, Programme, and Project Offices (P3O®) Practitioner: In-House Training P3O® is the AXELOS standard for the design of decision-making processes regarding changes in organizations. P3O provides a guideline for the design of portfolio, programme, and project offices in organizations. The P3O Practitioner Course is an interactive learning experience. The P3O Practitioner-level content provides you with sufficient knowledge and understanding of the P3O guidance to design, implement, manage or work within any component office of a P3O model. It enables participants to successfully complete the associated P30 Practitioner exam and achieve the qualification. In this course, you will be prepared to successfully attempt the P3O Practitioner exam and learn how to implement or re-energize a P3O model in their own organization. What you will Learn At the end of the P3O Practitioner course, you will be able to: Define a business case to get senior management approval for P3O Build a right P3O model to adapt to the organization's needs, taking account of the organization's size and portfolio, programme and project management maturity Identify the elements, roles, and functions deployed in a generalized P3O model Use tools and techniques in running the P3O and advising those who shape the portfolio of programmes and projects Introduction to P3O What is the purpose of P3O? Definitions What are P3Os? Portfolio, programme, and project lifecycles Governance and the P3O Designing a P3O Model Factors that affect the design Design considerations What functions and services should the P3O offer? Roles and responsibilities Sizing and tailoring of the P3O model Why have a P3O? How a P3O adds value Maximizing that value Getting investment for the P3O Overcoming common barriers Timescales Why have a P3O (Extension)? The P3O Business Case The P3O Model Blueprint Vision Statement Demonstrating the Value KPIs The Benefits of Claimed Capabilities Benefit Realisation and Strategic Objectives Benefit Profile How to Implement or Re-Energize a P3O Implementation lifecycle for a permanent P3O Identify Define Deliver Close Implementation lifecycle for a temporary programme or project office Organizational context Definition and implementation Running Closing Recycling How to operate a P3O Overview of tools and techniques Benefits of using standard tools and techniques Critical success factors P3O tools P3O techniques

Essential DHCP training course description Almost all businesses use DHCP. This course builds on delegates existing IP knowledge and focuses on IP Address management using DHCP. Also covered is the role of DHCP in plug and play environments. What will you learn Explain how DHCP works. Configure DHCP servers. Troubleshoot DHCP. Essential DHCP training course details Who will benefit: Anyone working with TCP/IP. Prerequisites: TCP/IP Foundation for engineers Duration 1 day Essential DHCP training course contents Introduction What is DHCP?, IP configuration: Address, mask, default gateway, DNS. History of DHCP: RARP, BOOTP. Hands on Client configuration, releasing and renewing. DHCP servers Installation. Base configuration: Scope. Lease period. DHCP options. Hands on Server setup, Impact of lease times. Server monitoring. How DHCP works Client states. Obtaining, renewing leases. DHCP messages: DISCOVER, OFFER, REQUEST, NAK, ACK, DECLINE, RELEASE, INFORM. Hands on Troubleshooting DHCP using Wireshark. DHCP architecture DHCP relay agents. Server platforms, resilience, DHCP fail over, split scopes. Dynamic DNS and DHCP. Hands on DDNS, routers, Troubleshooting.

Training Course for Architects & Interior Exterior Designers
By Real Animation Works
1-2-1 face to face training customised and bespoke.
