- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
3898 Courses in Cardiff delivered Live Online
Total SPB training course description A comprehensive look at Service Provider Bridging (SPB) as standardised in 802.1aq. This SPB course starts with the problems in traditional switched networks then moves onto to how SPB solves these problems. As IS-IS is key to loop free topologies in SPB networks, this protocols is also studied. What will you learn Explain the benefits of SPB. Explain how SPB works. Explain the role of IS-IS in SPB. Integrate SPB into existing networks. Total SPB training course details Who will benefit: Technical staff working with Ethernet. Prerequisites: Definitive Ethernet switching for engineers Duration 1 day Total SPB training course contents What is SPB? Layer 2 versus Layer 3, STP problems: One path, convergence, MAC explosion. Virtualisation issues: VRF. Service Provider Bridging (SPB), 802.1aq. Virtual Services Network. SPB variants 802.1Q, 802.1ad, Q-in-Q, VLAN IDs, 802.1ah, M-in-M, I-SID. SPBV, SPBM. SPBM frame format. How SPB works Node ID, Backbone Edge Bridges, Backbone MAC address, Customer MACs, I-SID. IS-IS. Forwarding database. VSN. IS-IS Link layer IS-IS, SPF trees, traffic management. IS-IS extensions for SPB. ISIS TLV. SPB services Data centre bridging, server virtualisation, multitenant applications. Integration of SPB into existing networks. VLAN to ISID mappings. Inter ISID routing, IP/SPB Layer 3 VRF extensions. Miscellaneous Multicast in SPB environments. Source specific multicast trees. SPB configuration. SPB deployment considerations.

CompTIA Cybersecurity Analyst (CySA+)
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for This course is designed primarily for cybersecurity practitioners who perform job functions related to protecting information systems by ensuring their availability, integrity, authentication, confidentiality, and non-repudiation. This course focuses on the knowledge, ability, and skills necessary to provide for the defense of those information systems in a cybersecurity context, including protection, detection, analysis, investigation, and response processes. In addition, the course ensures that all members of an IT team?everyone from help desk staff to the Chief Information Officer?understand their role in these security processes. Overview In this course, you will assess and respond to security threats and operate a systems and network security analysis platform. You will: - Assess information security risk in computing and network environments. - Analyze reconnaissance threats to computing and network environments. - Analyze attacks on computing and network environments. - Analyze post-attack techniques on computing and network environments. - Implement a vulnerability management program. - Collect cybersecurity intelligence. - Analyze data collected from security and event logs. - Perform active analysis on assets and networks. - Respond to cybersecurity incidents. - Investigate cybersecurity incidents. - Address security issues with the organization's technology architecture. The course introduces tools and tactics to manage cybersecurity risks, identify various types of common threats, evaluate the organization's security, collect and analyze cybersecurity intelligence, and handle incidents as they occur. 1 - ASSESSING INFORMATION SECURITY RISK Identify the Importance of Risk Management Assess Risk Mitigate Risk Integrate Documentation into Risk Management 2 - ANALYZING RECONNAISSANCE THREATS TO COMPUTING AND NETWORK ENVIRONMENTS Assess the Impact of Reconnaissance Incidents Assess the Impact of Social Engineering 3 - ANALYZING ATTACKS ON COMPUTING AND NETWORK ENVIRONMENTS Assess the Impact of System Hacking Attacks Assess the Impact of Web-Based Attacks Assess the Impact of Malware Assess the Impact of Hijacking and Impersonation Attacks Assess the Impact of DoS Incidents Assess the Impact of Threats to Mobile Security Assess the Impact of Threats to Cloud Security 4 - ANALYZING POST-ATTACK TECHNIQUES Assess Command and Control Techniques Assess Persistence Techniques Assess Lateral Movement and Pivoting Techniques Assess Data Exfiltration Techniques Assess Anti-Forensics Techniques 5 - MANAGING VULNERABILITIES IN THE ORGANIZATION Implement a Vulnerability Management Plan Assess Common Vulnerabilities Conduct Vulnerability Scans Conduct Penetration Tests on Network Assets 6 - COLLECTING CYBERSECURITY INTELLIGENCE Deploy a Security Intelligence Collection and Analysis Platform Collect Data from Network-Based Intelligence Sources Collect Data from Host-Based Intelligence Sources 7 - ANALYZING LOG DATA Use Common Tools to Analyze Logs Use SIEM Tools for Analysis 8 - PERFORMING ACTIVE ASSET AND NETWORK ANALYSIS Analyze Incidents with Windows-Based Tools Analyze Incidents with Linux-Based Tools Analyze Malware Analyze Indicators of Compromise 9 - RESPONDING TO CYBERSECURITY INCIDENTS Deploy an Incident Handling and Response Architecture Mitigate Incidents Prepare for Forensic Investigation as a CSIRT 10 - INVESTIGATING CYBERSECURITY INCIDENTS Apply a Forensic Investigation Plan Securely Collect and Analyze Electronic Evidence Follow Up on the Results of an Investigation 11 - ADDRESSING SECURITY ARCHITECTURE ISSUES Remediate Identity and Access Management Issues Implement Security During the SDLC Additional course details: Nexus Humans CompTIA Cybersecurity Analyst Certification (CySA Plus) (Exam CS0-003) training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the CompTIA Cybersecurity Analyst Certification (CySA Plus) (Exam CS0-003) course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

BOHS P402 Online - Surveying and sampling strategies for Asbestos in buildings
By Airborne Environmental Consultants Ltd
The main subject areas of the course are: Building construction and the uses of asbestos Survey types Bulk sampling and material assessments Survey reports Quality control

INSIGHTS AND SOLUTIONS CIRCLE
By Inclusive Solutions
This can be introduced in one day but is better offered over a series of twilight or half day workshops with individualised coaching. We will provide background context for this approach and will directly model the process with real live issues facing participants. So bring your most challenging concerns to this training. Course Category Behaviour and Relationships Visioning and Problem Solving Team Building and Leadership Description ‘Insights and Solutions Circle’ a new expanded version of Solution Circle that uses some of the best of the Circle of Adults process. Its a 50 minute process and works really well with families and professionals! Contact us today for a live demo or training… Steps Problem presented Questions asked Theories Shared Strategies listed Dialogue regarding selected strategies Next steps Testimonials Excellent! It was great how we all cam up with ideas and theories including us parents I wish all meeting about my child’s behaviour were like this The whole world is going to be interested in this… The empowerment is great The buzz after the meeting says it all. Learning Objectives Deeper understanding of what is actually happening underneath the presenting behaviour Increased confidence in managing and building relationships with challenging pupils in mainstream schools Learn process for locating richer and wider range of practical strategies to impact on behaviour problems Deeper understanding of yourself and the psychodynamic processes happening between pupils, staff and pupils and families Opportunity to reflect on professional practice Mutual support established with other front line practitioners Who Is It For ? Team Around the Child agencies Parents and Professional working together Families Multi Agency Teams Social workers CAMHS teams Year Managers Primary and secondary staff teams Early Years and School based Practitioners Heads and Deputies SENCOs Advanced Skills Teachers Primary and secondary teachers Local Authority Support Services Course Content This can be introduced in one day but is better offered over a series of twilight or half day workshops with individualised coaching. We will provide background context for this approach and will directly model the process with real live issues facing participants. So bring your most challenging concerns to this training. The course answers the questions: Can we find an alternative to permanent exclusion or special unit or school placement? Cannot understand why a child is behaving as they do? Struggling with a child for whom praise is ineffective? Feeling isolated in your responses to a child’s needs? Worried about where your instinctive reactions are leading you? Cannot seem to get any consensus view of a young person’s behaviour/needs amongst all the family and professionals involved – is everyone pulling in different directions? We will cover: Setting the tone Background and detailed teaching of process Inclusion values underpinning this work Graphic and process facilitation skills Processes modelled and opportunities to try process out with coaching Practical setting up of insights and solutions circles Lessons learned If you liked this you may like: CIRCLES OF ADULTS…

NETCONF and YANG training course description An introduction to NETCONF and YANG. The course progresses from what they are, why they are needed, and how to configure them onto a more detailed analysis of how NETCONF works and how to read YANG models. What will you learn Recognise the limits and problems of SNMP and the CLI. Describe the relationship between NETCONF and YANG. Configure NETCONF on network devices. Use NETCONF to configure devices. Read YANG models. NETCONF and YANG training course details Who will benefit: Network engineers. Prerequisites: Network management technologies Duration 1 day NETCONF and YANG training course content What are NETCONF and YANG? Network management and configuration issues. What is NETCONF? What is YANG? Protocols, data models, architecture. Hands on Configuring NETCONF on network devices, using NETCONF. NETCONF NETCONF layers, Secure transport: SSH, Messages: rpc, Operations, Content. Base operations: <get>, <get-config>, <edit-config>, <copy-config>, <delete-config>, <lock>,<unlock>, <close-session>, <kill-session> NETCONF datastores: :candidate, :startup, running. Hands on Retrieving a configuration with NETCONF, Editing a configuration with NETCONF. NETCONF more details NETCONF traffic flows, NETCONF capabilities, hello, capabilities exchange., Filtering data, atomic transactions, validating configurations. Hands on Using NETCONF. YANG YANG models, IETF standard YANG models, tree diagrams, an example: YANG interface management, Module header, Imports and includes, Containers, Lists, leaves, Data types, typedef, Instance data, XML. Hands on Reading YANG data models, creating a configuration instance.

SMPTE 2022 training course description SMPTE 2022 is the standard for IP video transport in the broadcast industry. This course covers the seven section of the standard in detail. Particular attention is given to FEC and seamless protection switching areas of the standard. What will you learn Use Wireshark to analyse. SMPTE 2022 streams. Explain the role of FEC in SMPTE 2022. Explain how SMPTE 2022 provides resilience. SMPTE 2022 training course details Who will benefit: Anyone working with TV distribution. Prerequisites: TCP/IP foundation for engineers Duration 1 day SMPTE 2022 training course contents Introduction What is SMPTE 2022, SMPTE 2022 parts. SDI over IP. Contribution and distribution versus delivery. The SMPTE 2022 protocol stack SMPTE 2022-2 (mapping of MPEG TS into IP) and SMPTE 2022-6 mapping uncompressed video into IP. IP: Best effort, connectionless, DF flag, routers, Diffserv, RSVP. IPv6. UDP: Unreliable, connectionless, broadcasts, multicasts and unicasts. RTP RTP, ports, payloads types, sequence numbers, timestamps. RTP header extensions. RTCP. MPEG2-TS: Elementary streams, transport over IP. FEC Forward Error Correction. SMPTE 2022-1, SMPTE 2022-5. Logical rows and columns. 1D and 2D parity. FEC header format. FEC configuration and choosing dimensions. FEC traffic shaping. Overheads and delays. Seamless protection switching IP failover. SMPTE 2022-7: Sending two matching streams over different paths. Stream synchronization. The HBRMT header. Calculating the packet to switch over. Summary Summary of the 7 sections of the SMPTE 2022 standard. Clock recovery.

REST and RESTCONF training course description An introduction to REST and RESTCONF using Python. The course progresses from how to use them onto how they work and then looks at using them from within Python all the time on network devices. What will you learn Explain what REST and RESTCONF are. Use the REST API on network device. Use RESTCONF. REST and RESTCONF training course details Who will benefit: Network engineers. Prerequisites: Python for network engineers. Duration 1 day REST and RESTCONF training course contents Using REST Curl, Browser plugins, Postman, RESTClient, Python. Hands on Using the REST API on network devices. What is REST? What is REST? Architecture, APIs, RESTful APIs, APIs over HTTP/HTTPS, URIs, resources, HTTP methods, GET, POST, PUT, DELETE. CRUD. Comparison with other APIs. Hands on REST analysis with Wireshark. Rest conventions Passing parameters, return values, HTTP status, JSON. XML. Hands on Configuring REST on network devices, changing format of responses, POST requests, using parameters. Configuring network devices with REST Invoking multiple RPCs. Hands on Device configuration with REST. The request library RESTFUL APIs in Python, the request library, Installation, example to retrieve the interface configuration. Hands on Using the Python requests library on network devices. RESTCONF What is RESTCONF? YANG and NETCONF, relationship with REST, RESTCONF URIs, A RESTCONF example with ietf-interfaces, RESTCONF responses. PATCH. Hands on Using RESTCONF to update a network device configuration.

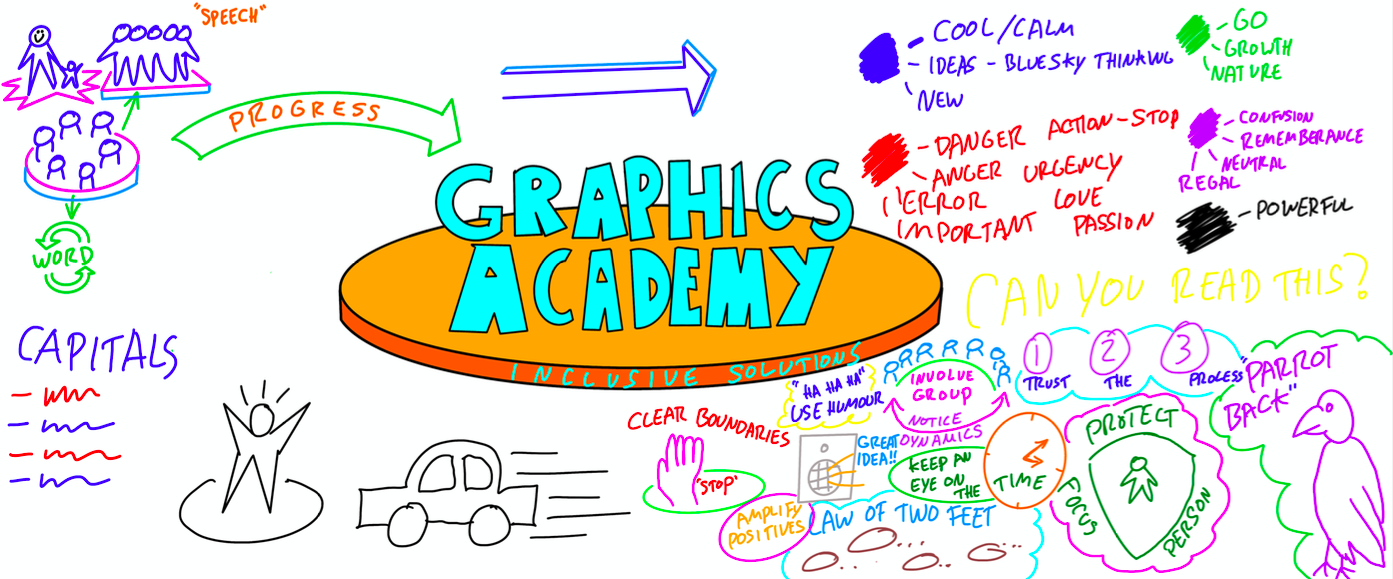
GRAPHIC FACILITATION – AN INTRODUCTION
By Inclusive Solutions
This day will introduce you to the basic techniques and skills involved in doing graphic facilitation. Learn how to use a BIG piece of paper and a handful of pens to create a memorable summary of your training day, team meeting or your work with young people and families. Learn how to harvest the essence of an event in a visual representation. This is a ‘hands on’ interactive day built around demonstrations of graphic facilitation, coaching and the chance to try things out. Ideal for teams who can then go on together to practice, practice, practice. Learning Objectives To introduce you to the basic skills of graphic facilitation – no previous experience is needed To develop your capacity to ‘listen under the words’ and draw out the deeper messages To help you suspend your self-doubt – “I can’t draw!” and rediscover your capacity to create an effective visual representation of a meeting/training day/conversation etc Course Content The day will introduce you to the fundamentals of graphic facilitation and will include the following topics: Pens, Pastels and Paper – what you will need to get started The basic ‘grammar’ of graphic facilitation; the essential shapes, using colour, images, lettering, words, creating connection How to listen for the essence of what is being said and translate this into visual language A chance to do it live – with coaching
Geothermal Project Finance Analysis and Modelling
By EnergyEdge - Training for a Sustainable Energy Future
About this Virtual Instructor Led Training (VILT) This 4 half-day Virtual Instructor Led Training (VILT) course will address a variety of contract and loan structuring issues associated with geothermal energy projects as well as comparison with solar, wind and battery storage. The course is designed to investigate how various project finance techniques and contract structures can be used to achieve a competitive power prices while maintaining a satisfactory equity return. Distinctive project finance features of power facilities that depend on geothermal, wind, hydro or solar resources will be evaluated with financial models. The course will cover economic analysis of exploration and development of geothermal facilities and how to incorporate probability of failure and success into an IRR framework. Subsequent sessions will address the theory underlying liquidated damages for delay, and performance as well as design of other incentives that is inherent in different contract structures. Nuanced project finance issues associated with structuring debt for renewable projects will be discussed including under what conditions the DSCR drives debt capacity and when the debt to capital ratio is instrumental. The course will be taught with a combination of theoretical discussions, term sheet review and focused financial models. Training Objectives Evaluation of the economic risks that arise from uncertainty associated with drilling exploration wells and development wells for geothermal projects. Analyse the theoretical issues with computing LCOE for geothermal projects compared to other renewable and non-renewable resources and the importance of cost of capital for renewable projects; Understand differences in contract structures for renewable projects and dispatchable projects and how a single price structure can distort incentives for efficient construction and operation; Understand components of financing that influence the bid price required to meet a required rate of return on equity and can result in relatively low prices with reasonable returns. Understand the importance of debt sizing constraints and what strategies are relevant when the debt to capital constraint applies relative to when the debt service coverage ratio drives the debt size; Understand how to compute P50, P90 and P99 for different projects driven by resource risk; Understand the difference between mean reverting resource variation and estimation mistakes that do not correct as the basis for 1-year P90 and 10-year P90. Understand under what conditions debt sculpting can affect returns and how synthetic sculpting can be used to increase returns when the DSCR constraint applies. Understand the theory of credit spreads, variable rate debt and interest rates in different currencies and compute the implied probability of default that in inherent in credit spreads. Understand how to evaluate the costs to equity investors and the benefits to lenders for various credit enhancements including DSRA accounts, cash flow sweeps and covenants. Course Level Basic or Foundation Training Methods The VILT will be delivered online in 4 sessions comprising 4 hours per day, with 2 breaks of 10 minutes per day, including time for lectures, discussion, quizzes and short classroom exercises. Trainer Your expert course leader provides financial and economic consulting services to a variety of clients, he teaches professional development courses in an assortment of modelling topics (project finance, M&A, and energy). He is passionate about teaching in Africa, South America, Asia and Europe. Many of the unique analytical concepts and modelling techniques he has developed have arisen from discussion with participants in his courses. He has taught customized courses for MIT's Sloan Business School, Bank Paribas, Shell Oil, Society General, General Electric, HSBC, GDF Suez, Citibank, CIMB, Lind Lakers, Saudi Aramco and many other energy and industrial clients. His consulting activities include developing complex project finance, corporate and simulation models, providing expert testimony on financial and economic issues before energy regulatory agencies, and advisory services to support merger and acquisition projects. Our key course expert has written a textbook titled Corporate and Project Finance Modelling, Theory and Practice published by Wiley Finance. The book introduces unique modelling techniques that address many complex issues that are not typically used by even the most experienced financial analysts. For example, it describes how to build user-defined functions to solve circular logic without cumbersome copy and paste macros; how to write function that derives the ratio of EV/EBITDA accounting for asset life, historical growth, taxes, return on investment, and cost of capital; and how to efficiently solve many project finance issues related to debt structuring. He is in the process of writing a second book that describes a series of valuation and analytical mistakes made in finance. This book uses many case studies from Harvard Business School that were thought to represent effective business strategies and later turned into valuation nightmares. Over the course of his career our key course expert has been involved in formulating significant government policy related to electricity deregulation; he has prepared models and analyses for many clients around the world; he has evaluated energy purchasing decisions for many corporations; and, he has provided advice on corporate strategy. His projects include development of a biomass plant, analysis and advisory work for purchase of electricity generation, distribution and transmission assets by the City of Chicago, formulation of rate policy for major metro systems and street lighting networks, advocacy testimony on behalf of low income consumers, risk analysis for toll roads, and evaluation of solar and wind projects. He has constructed many advisory analyses for project finance and merger and acquisition transactions. Lastly, our key course expert was formerly Vice President at the First National Bank of Chicago where he directed analysis of energy loans and also created financial modelling techniques used in advisory projects. He received an MBA specializing in econometrics (with honours) from the University of Chicago and a BSc in Finance from the University of Illinois (with highest university honours). POST TRAINING COACHING SUPPORT (OPTIONAL) To further optimise your learning experience from our courses, we also offer individualized 'One to One' coaching support for 2 hours post training. We can help improve your competence in your chosen area of interest, based on your learning needs and available hours. This is a great opportunity to improve your capability and confidence in a particular area of expertise. It will be delivered over a secure video conference call by one of our senior trainers. They will work with you to create a tailor-made coaching program that will help you achieve your goals faster. Request for further information about post training coaching support and fees applicable for this. Accreditions And Affliations

QSIG training course description A concise overview of QSIG, covering the development, current use and future of this private network signalling protocol. What will you learn Describe the use of QSIG. Describe the evolution of QSIG. Describe functionality of the QSIGProtocol Stack. Describe functionality and use of the main Supplementary Services and Additional Network Functions within QSIG. QSIG training course details Who will benefit: Network/Systems Engineers Operators/Planners or anyone working within the QSIG Arena. Prerequisites: Telecommunications Introduction Duration 1 day QSIG training course contents Introduction What is QSIG? User benefits, flexible interconnection, public ISDN synergy, feature transparency-end to end intelligence, innovation specialist features - heterogeneous environment. Evolution of QSIG Evolution of QSIG, ISDN PBX Networking, Specification forum (IPNS), QSIG standardisation. The ITU-T reference model extended for corporate networks. QSIG Protocol Q Protocol stack, QSIG basic call layer 3 - SubLayer 1, QSIG Generic Functional layer 3 Sub-Layer 2 (GF), QSIG protocols for supplementary services & ANF's- Layer 3, Sub-Layer 3, Layer 3 Message Overview. Supplementary Services and ANFs QSIG supplementary services standardisation methodology. QSIG Services and additional network features: Advice of charge, Call Completion, (CCBS, CCNR), Call Forwarding and diversion (CFB, CFNR, CFU, CD), Services (CINT, CI, CO, CT, CW, DDI) Services cont. (DND, DNDO), Identification Services - (CLIP, COLP, CLIR, CNIP, CONP, CNIR), Other QSIG services and additional network features (Mobile, Multi Subscriber Number (MSN), Operator Services, Recall (RE), Sub-Addressing (SUB)), User to user signalling, compliance with services. Conclusion - QSIG1 FAQ's, European Computer Manufacturers Association. The Future.
