- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
1154 Courses in Bristol delivered Live Online
MESOTHERAPY, FACE, BODY, HAIR COURSE
By Harley Elite Academy (HeLa)
MASTERCLASS 8 CPD POINTS 1 DAY INTENSIVE COURSE ONLINE or IN-CLINIC NOTE! After booking we will contact you for scheduling the exact course date! Courses dates are subject to change due to mentors availability. We will inform you via email if a date becomes available! Nose Job Masterclass You will perform this procedure on live models under the supervision and guidance of highly experienced aesthetic practitioners. You will be trained under ENT specialist. We will give you all the knowledge you need for a safe technique in your practice. A certification of training will be provided upon completion of the course. Practice will enable you to learn in 1-day ONE-TO-ONE Training You will also have the opportunity to view a mesotherapy treatment demonstration at the conclusion of the training. Upon successful completion of the course, you will receive a certificate and title of Mesotherapy Certified Practitioner. You need to be medically qualified as a doctor, dentist, nurse, pharmacist or paramedic with full governing body registration and have completed a Foundation Filler Course and to have administered a number of cases. Additional information ATTENDANCE ONLINE (Theory), IN CLINIC (Practice) COURSE LEVEL EXPERT | Masterclass Course

Agile Scrum as a Delivery Method - Certification Assessment - Essentials (C-ASDM) for Government and Public Sector
By UK Scrum Academy
Delegates with existing Agile project delivery experience can choose to take the Certification Assessment without enrolling on the course. Get your Continuing Professional Development recognised with a UK CPD Certification Service accredited C-ASDM certificate. Frequently Asked Questions I will receive my certificate as soon as I have completed the course You will initially receive an Assessment Completion report after completing the assessment. The report details the certification status: 'Pass' or 'Fail', and also includes information on which questions were answered incorrectly. The certificate is issued by the CPD Certification Service approximately four to six weeks after completing the certification assessment. A CPD certification is recognised by employers Yes! CPD certification is recognised by private and public sector employers, and in central government departments as a valuable way to evaluate the skills of an individual. Listing your CPD certification as well as the number of CPD Points you have achieved on your CV is essentially showcasing your achievements in continuing your professional development. One CPD Point is equivalent to an hour of training CPD points are units that quantify time, and the quality of learning and development activities. Delegates will earn 3 CPD Points upon successful completion of the CPD-ASE Certification Assessment, but will 13 CPD Points after completing the two-day course. My CPD certificate will expire after three years Your certificate will not expire however, best practice suggests a renewal after three years. You can do this by enroling in the C-ASDM course to ensure your knowledge of Agile as a Delivery Method is up to date. I will receive my certificate as soon as I have completed the course You will initially receive an Assessment Completion report after completing the assessment. The report details the certification status: 'Pass' or 'Fail', and also includes information on which questions were answered incorrectly. Your certificate is issued by the CPD Certification Service approximately four to six weeks after successfully completing and passing the C-ASDM Certification Assessment. A CPD certification is recognised by employers Yes! CPD certification is recognised by private and public sector employers, and in central government departments as a valuable way to evaluate the skills of an individual, and the quality of the learning activities. Listing your CPD certification as well as the number of CPD Points you have achieved on your CV is essentially showcasing your achievements in continuing your professional development. One CPD Point is equivalent to an hour of training CPD points are units that quantify time, and the quality of learning and development activities. Delegates will earn 3 CPD Points upon successful completion of the C-ASDM Certification Assessment, but will 13 CPD Points after completing the two-day course. My CPD certificate will expire after three years Your certificate will not expire however, best practice suggests a renewal after three years. You can do this by enrolling on the C-ASDM course to ensure your knowledge as Agile as a Delivery Method is up to date. Service Features Certification Agile Scrum as a Delivery Method - Essentials (C-ASDM) On-going support Email support No Telephone support No Webchat support No Online support No Community Support Delegates who achieve the pass mark for CPD certification are additionally offered access to our private 'Certified Scrum Practitioners’ Guild', a private Slack community of like-minded Agile professionals.

At this Oracle SQL Fundamentals course, we cover SQL queries, group by's , aggregates, joins, date-functions, String Functions, Random Functions, Math Functions, Insert, update and delete, Creating and changing tables, sub-queries in detail, views, stored procedures, custom functions, and table variables. Course level is beginners to intermediate.

Group Coaching Programme
By British School of Coaching
An intensive group coaching programme for qualified and certified coaches who want to add group coaching as an offer in their practice.

AZ-500T00 Microsoft Azure Security Technologies
By Nexus Human
Duration 4 Days 24 CPD hours This course is intended for This course is for Azure Security Engineers who are planning to take the associated certification exam, or who are performing security tasks in their day-to-day job. This course would also be helpful to an engineer that wants to specialize in providing security for Azure-based digital platforms and play an integral role in protecting an organization's data. This course provides IT Security Professionals with the knowledge and skills needed to implement security controls, maintain an organization?s security posture, and identify and remediate security vulnerabilities. This course includes security for identity and access, platform protection, data and applications, and security operations. Prerequisites AZ-104T00 - Microsoft Azure Administrator Security best practices and industry security requirements such as defense in depth, least privileged access, role-based access control, multi-factor authentication, shared responsibility, and zero trust model. Be familiar with security protocols such as Virtual Private Networks (VPN), Internet Security Protocol (IPSec), Secure Socket Layer (SSL), disk and data encryption methods. Have some experience deploying Azure workloads. This course does not cover the basics of Azure administration, instead the course content builds on that knowledge by adding security specific information. Have experience with Windows and Linux operating systems and scripting languages. Course labs may use PowerShell and the CLI. 1 - Manage identities in Microsoft Entra ID Secure users in Microsoft Entra ID Secure groups in Microsoft Entra ID Recommend when to use external identities Secure external identities Implement Microsoft Entra Identity protection 2 - Manage authentication by using Microsoft Entra ID Configure Microsoft Entra Verified ID Implement multifactor authentication (MFA) Implement passwordless authentication Implement password protection Implement single sign-on (SSO) Integrate single sign-on (SSO) and identity providers Recommend and enforce modern authentication protocols 3 - Manage authorization by using Microsoft Entra ID Configure Azure role permissions for management groups, subscriptions, resource groups, and resources Assign built-in roles in Microsoft Entra ID Assign built-in roles in Azure Create and assign a custom role in Microsoft Entra ID Implement and manage Microsoft Entra Permissions Management Configure Microsoft Entra Privileged Identity Management Configure role management and access reviews by using Microsoft Entra Identity Governance Implement Conditional Access policies 4 - Manage application access in Microsoft Entra ID Manage access to enterprise applications in Microsoft Entra ID, including OAuth permission grants Manage app registrations in Microsoft Entra ID Configure app registration permission scopes Manage app registration permission consent Manage and use service principals Manage managed identities for Azure resources Recommend when to use and configure a Microsoft Entra Application Proxy, including authentication 5 - Plan and implement security for virtual networks Plan and implement Network Security Groups (NSGs) and Application Security Groups (ASGs) Plan and implement User-Defined Routes (UDRs) Plan and implement Virtual Network peering or gateway Plan and implement Virtual Wide Area Network, including secured virtual hub Secure VPN connectivity, including point-to-site and site-to-site Implement encryption over ExpressRoute Configure firewall settings on PaaS resources Monitor network security by using Network Watcher, including NSG flow logging 6 - Plan and implement security for private access to Azure resources Plan and implement virtual network Service Endpoints Plan and implement Private Endpoints Plan and implement Private Link services Plan and implement network integration for Azure App Service and Azure Functions Plan and implement network security configurations for an App Service Environment (ASE) Plan and implement network security configurations for an Azure SQL Managed Instance 7 - Plan and implement security for public access to Azure resources Plan and implement Transport Layer Security (TLS) to applications, including Azure App Service and API Management Plan, implement, and manage an Azure Firewall, Azure Firewall Manager and firewall policies Plan and implement an Azure Application Gateway Plan and implement an Azure Front Door, including Content Delivery Network (CDN) Plan and implement a Web Application Firewall (WAF) Recommend when to use Azure DDoS Protection Standard 8 - Plan and implement advanced security for compute Plan and implement remote access to public endpoints, Azure Bastion and just-in-time (JIT) virtual machine (VM) access Configure network isolation for Azure Kubernetes Service (AKS) Secure and monitor AKS Configure authentication for AKS Configure security for Azure Container Instances (ACIs) Configure security for Azure Container Apps (ACAs) Manage access to Azure Container Registry (ACR) Configure disk encryption, Azure Disk Encryption (ADE), encryption as host, and confidential disk encryption Recommend security configurations for Azure API Management 9 - Plan and implement security for storage Configure access control for storage accounts Manage life cycle for storage account access keys Select and configure an appropriate method for access to Azure Files Select and configure an appropriate method for access to Azure Blob Storage Select and configure an appropriate method for access to Azure Tables Select and configure an appropriate method for access to Azure Queues Select and configure appropriate methods for protecting against data security threats, including soft delete, backups, versioning, and immutable storage Configure Bring your own key (BYOK) Enable double encryption at the Azure Storage infrastructure level 10 - Plan and implement security for Azure SQL Database and Azure SQL Managed Instance Enable database authentication by using Microsoft Entra ID Enable and monitor database audit Identify use cases for the Microsoft Purview governance portal Implement data classification of sensitive information by using the Microsoft Purview governance portal Plan and implement dynamic mask Implement transparent data encryption? Recommend when to use Azure SQL Database Always Encrypted 11 - Plan, implement, and manage governance for security Create, assign, and interpret security policies and initiatives in Azure Policy Configure security settings by using Azure Blueprint Deploy secure infrastructures by using a landing zone Create and configure an Azure Key Vault Recommend when to use a dedicated Hardware Security Module (HSM) Configure access to Key Vault, including vault access policies and Azure Role Based Access Control Manage certificates, secrets, and keys Configure key rotation Configure backup and recovery of certificates, secrets, and keys 12 - Manage security posture by using Microsoft Defender for Cloud Implement Microsoft Defender for Cloud Identify and remediate security risks by using the Microsoft Defender for Cloud Secure Score and Inventory Assess compliance against security frameworks and Microsoft Defender for Cloud Add industry and regulatory standards to Microsoft Defender for Cloud Add custom initiatives to Microsoft Defender for Cloud Connect hybrid cloud and multicloud environments to Microsoft Defender for Cloud Identify and monitor external assets by using Microsoft Defender External Attack Surface Management 13 - Configure and manage threat protection by using Microsoft Defender for Cloud Enable workload protection services in Microsoft Defender for Cloud, including Microsoft Defender for Storage, Databases, Containers, App Service, Key Vault, Resource Manager, and DNS Configure Microsoft Defender for Servers Configure Microsoft Defender for Azure SQL Database Manage and respond to security alerts in Microsoft Defender for Cloud Configure workflow automation by using Microsoft Defender for Cloud Evaluate vulnerability scans from Microsoft Defender for Server 14 - Configure and manage security monitoring and automation solutions Monitor security events by using Azure Monitor Configure data connectors in Microsoft Sentinel Create and customize analytics rules in Microsoft Sentinel Configure automation in Microsoft Sentinel Additional course details: Nexus Humans AZ-500T00 Microsoft Azure Security Technologies training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the AZ-500T00 Microsoft Azure Security Technologies course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

3D Printing Training Course for Product Designers
By ATL Autocad Training London
Who is this course for? The 3D Printing Bespoke 1-on-1 Training Course is designed for individuals seeking personalized instruction and hands-on experience in the field of 3D printing. Click here for more info: Website Training: 40 hrs, split as per your availability. When: 9 a.m. to 7 p.m., Mon-Sat. Call 02077202581 to reserve. Live online, or in-person. Option A: AutoCAD 10 hrs, Rhino 16 hrs, Vray 4 hrs, Photoshop 4 hrs, 3D Printing 6 hrs Option B: AutoCAD 12 hrs, 3ds Max 16 hrs, Vray 4 hrs, Photoshop 4 hrs, 3D Printing 4 hrs. Option A: AutoCAD, Rhino, Vray, Photoshop, 3D Printing (Total: 40 hours) AutoCAD (10 hours): Module 1: Introduction to AutoCAD (2 hours) Familiarization with AutoCAD interface and tools Creating, opening, and saving drawings Basic drawing and editing commands Module 2: Drawing and Editing (3 hours) Lines, circles, and arcs Polylines and polygons Modifying objects: Move, Copy, Rotate, and Scale Module 3: Precision Drawing (3 hours) Using coordinate systems Dimensioning and text Hatching and gradients Module 4: Advanced Tools (2 hours) Blocks and attributes Layers and object properties Creating layouts and plotting Rhino (16 hours): Module 1: Introduction to Rhino (2 hours) Navigating the Rhino interface Basic 2D and 3D modeling concepts Creating and manipulating objects Module 2: Advanced Modeling (6 hours) Modeling with curves and surfaces Editing and transforming geometry Building complex 3D structures Module 3: Visualization with Vray (4 hours) Understanding the Vray rendering engine Applying materials and textures Setting up lighting and cameras for realistic rendering Module 4: Presentation and Editing (2 hours) Exporting and sharing Rhino models Post-processing and enhancing designs Photoshop (4 hours): Module 1: Introduction to Photoshop (2 hours) Navigating Photoshop interface Image resolution and size Basic image editing tools Module 2: Image Editing and Enhancement (2 hours) Adjusting colors and tones Using layers and masks Retouching and image manipulation 3D Printing (6 hours): Module 1: Introduction to 3D Printing (2 hours) Basics of 3D printing technology Understanding file formats and requirements Module 2: Preparing 3D Models (2 hours) Model optimization for 3D printing Creating supports and rafts Ensuring successful prints Option B: AutoCAD, 3ds Max, Vray, Photoshop, 3D Printing (Total: 38 hours) AutoCAD (12 hours): Module 1: Introduction to AutoCAD (2 hours) Overview of AutoCAD interface and tools Creating, opening, and saving drawings Basic drawing and editing commands Module 2: Drawing and Editing (3 hours) Lines, circles, and arcs Polylines and polygons Modifying objects: Move, Copy, Rotate, and Scale Module 3: Precision Drawing (3 hours) Using coordinate systems Dimensioning and text Hatching and gradients Module 4: Advanced Tools (4 hours) Blocks and attributes Layers and object properties Creating layouts and plotting 3ds Max (16 hours): Module 1: Introduction to 3ds Max (2 hours) Exploring the 3ds Max interface Navigating viewports and objects Basic modeling techniques Module 2: 3D Modeling (6 hours) Creating and editing 3D objects Modifiers and deformations Working with shapes and splines Module 3: Visualization with Vray (4 hours) Setting up lights and cameras Rendering settings and options Post-production and compositing Photoshop (4 hours): Module 1: Introduction to Photoshop (2 hours) Navigating Photoshop interface Image resolution and size Basic image editing tools Module 2: Image Editing and Enhancement (2 hours) Adjusting colors and tones Using layers and masks Retouching and image manipulation 3D Printing (4 hours): Module 1: Introduction to 3D Printing (2 hours) Basics of 3D printing technology Understanding file formats and requirements Module 2: Preparing 3D Models (2 hours) Model optimization for 3D printing Creating supports and rafts Ensuring successful prints Training Duration: 40 hours Flexible Timings: Students can choose their preferred time slots based on our availability, operating from 9:00 am to 7:00 pm (Monday to Saturday). Pricing Details: Company Rate: £1200 (Plus 20% VAT) = £1440 inc VAT. Student, Self-Financed, and Live Online Rate: £1000 (Plus 20% VAT) = £1200 inc VAT. Who Should Enroll: This course caters to a wide range of individuals, including: Novices: Perfect for beginners unfamiliar with AutoCAD, 3ds Max, Adobe Photoshop, Rhino, Vray, and 3D printing, providing a solid foundational understanding. Architects and Interior Designers: Tailored insights for professionals seeking precision in enhancing their design skills, valuable for design firms. Industry Professionals: Establishes industry benchmarks, offering adaptable education applicable across sectors like interior design, architecture, and civil engineering. Learning Approach: Hands-On Practicality: Emphasizes practical, real-world skills through personalized one-on-one training, available in face-to-face or live online sessions. Step-by-Step Instruction: Experienced instructors guide you systematically through techniques using AutoDesk AutoCAD, Autodesk 3ds Max, Adobe Photoshop, and Trimble Sketchup. What You'll Receive: Certificate of Achievement: Upon completion, receive a certificate validating your expertise. Comprehensive Training Guide: Access an extensive PDF guide compatible with both Windows and MAC. Live Feedback: Connect with your tutor for real-time feedback during sessions and the option to record each session for future reference. Our Benefits: Price Assurance: Guaranteeing exceptional value for your career investment. Personalized Training: Tailored one-on-one sessions, adjusting to your learning pace and style. Flexible Scheduling: Choose your preferred training time and day, available Monday to Sunday, from 9 am to 8 pm. Lifetime Support: Ongoing email and phone support beyond the course completion. Computer Setup Assistance: We assist in configuring your computer for seamless software installation. Referral Benefits: Recommend a friend and enjoy discounts, including significant savings on group training courses. Advantages of Option A: Diverse Skill Enhancement: Acquire proficiency in AutoCAD, Rhino, Vray, Photoshop, and 3D Printing, expanding your skill repertoire. Career Opportunities: Access a wide range of career paths in design, architecture, and 3D printing fields, enhancing your professional prospects. Compelling Visualizations: Craft realistic and visually appealing 3D renderings using Vray, elevating the quality of your design presentations. Image Editing Expertise: Master the art of enhancing design projects with Photoshop, adding finesse to your creative work. Prototyping Prowess: Develop essential skills in 3D Printing, enabling you to create physical design prototypes for various applications. Advantages of Option B: Versatile Skill Mastery: Excel in AutoCAD, 3ds Max, Vray, Photoshop, and 3D Printing, gaining expertise in diverse areas of design and visualization. Career Advancement: Unlock opportunities in architecture, animation, and visualization fields, broadening your career horizons. High-Quality Renderings: Showcase your designs impressively with high-quality renderings generated through Vray, leaving a lasting impact on viewers. Image Editing Mastery: Polish your design concepts and presentations using advanced Photoshop techniques, ensuring your visuals are refined and professional. 3D Printing Expertise: Bring your digital designs to life across various industries, mastering the intricate art of 3D printing. Our training courses cater to both Mac and Windows operating systems and provide: Price Assurance: Ensuring the best value for your investment. Personalized Attention: Benefit from one-on-one training sessions tailored to your learning pace and style. Flexible Scheduling: Choose your preferred time and day for training sessions, available seven days a week from 9 am to 8 pm. Ongoing Support: Enjoy lifetime email and phone support, ensuring you're never alone on your learning journey. Technical Assistance: Receive guidance in configuring your computer for software installation, ensuring a seamless learning experience. Special Benefits: Avail special discounts when you refer a friend and significant savings on group training courses, maximizing the value of your training investment.

SC-100T00 Microsoft Cybersecurity Architect
By Nexus Human
Duration 4 Days 24 CPD hours This course is intended for This course is for experienced cloud security engineers who have taken a previous certification in the security, compliance and identity portfolio. Specifically, students should have advanced experience and knowledge in a wide range of security engineering areas, including identity and access, platform protection, security operations, securing data, and securing applications. They should also have experience with hybrid and cloud implementations. Beginning students should instead take the course SC-900: Microsoft Security, Compliance, and Identity Fundamentals. This is an advanced, expert-level course. Although not required to attend, students are strongly encouraged to have taken and passed another associate level certification in the security, compliance and identity portfolio (such as AZ-500, SC-200 or SC-300) before attending this class. This course prepares students with the expertise to design and evaluate cybersecurity strategies in the following areas: Zero Trust, Governance Risk Compliance (GRC), security operations (SecOps), and data and applications. Students will also learn how to design and architect solutions using zero trust principles and specify security requirements for cloud infrastructure in different service models (SaaS, PaaS, IaaS). Prerequisites Highly recommended to have attended and passed one of the associate level certifications in the security, compliance and identity portfolio (such as AZ-500T00 Microsoft Azure Security Technologies, SC-200T00: Microsoft Security Operations Analyst, or SC-300T00: Microsoft Identity and Access Administrator.) Advanced experience and knowledge in identity and access, platform protection, security operations, securing data and securing applications. Experience with hybrid and cloud implementations. 1 - Introduction to Zero Trust and best practice frameworks Zero Trust initiatives Zero Trust technology pillars part 1 Zero Trust technology pillars part 2 2 - Design solutions that align with the Cloud Adoption Framework (CAF) and Well-Architected Framework (WAF) Define a security strategy Cloud Adoption Framework secure methodology Design security with Azure Landing Zones The Well-Architected Framework security pillar 3 - Design solutions that align with the Microsoft Cybersecurity Reference Architecture (MCRA) and Microsoft cloud security benchmark (MCSB) Design solutions with best practices for capabilities and controls Design solutions with best practices for attack protection 4 - Design a resiliency strategy for common cyberthreats like ransomware Common cyberthreats and attack patterns Support business resiliency Ransomware protection Configurations for secure backup and restore Security updates 5 - Case study: Design solutions that align with security best practices and priorities Case study description Case study answers Conceptual walkthrough Technical walkthrough 6 - Design solutions for regulatory compliance Translate compliance requirements into a security solution Address compliance requirements with Microsoft Purview Address privacy requirements with Microsoft Priva Address security and compliance requirements with Azure policy Evaluate infrastructure compliance with Defender for Cloud 7 - Design solutions for identity and access management Design cloud, hybrid and multicloud access strategies (including Azure AD) Design a solution for external identities Design modern authentication and authorization strategies Align conditional access and Zero Trust Specify requirements to secure Active Directory Domain Services (AD DS) Design a solution to manage secrets, keys, and certificates 8 - Design solutions for securing privileged access The enterprise access model Design identity governance solutions Design a solution to secure tenant administration Design a solution for cloud infrastructure entitlement management (CIEM) Design a solution for privileged access workstations and bastion services 9 - Design solutions for security operations Design security operations capabilities in hybrid and multicloud environments Design centralized logging and auditing Design security information and event management (SIEM) solutions Design solutions for detection and response Design a solution for security orchestration, automation, and response (SOAR) Design security workflows Design threat detection coverage 10 - Case study: Design security operations, identity and compliance capabilities Case study description Case study answers Conceptual walkthrough Technical walkthrough 11 - Design solutions for securing Microsoft 365 Evaluate security posture for collaboration and productivity workloads Design a Microsoft 365 Defender solution Design configurations and operational practices for Microsoft 365 12 - Design solutions for securing applications Design and implement standards to secure application development Evaluate security posture of existing application portfolios Evaluate application threats with threat modeling Design security lifecycle strategy for applications Secure access for workload identities Design a solution for API management and security Design a solution for secure access to applications 13 - Design solutions for securing an organization's data Design a solution for data discovery and classification using Microsoft Purview Design a solution for data protection Design data security for Azure workloads Design security for Azure Storage Design a security solution with Microsoft Defender for SQL and Microsoft Defender for Storage 14 - Case study: Design security solutions for applications and data Case study description Case study answers Conceptual walkthrough Technical walkthrough 15 - Specify requirements for securing SaaS, PaaS, and IaaS services Specify security baselines for SaaS, PaaS, and IaaS services Specify security requirements for web workloads Specify security requirements for containers and container orchestration 16 - Design solutions for security posture management in hybrid and multicloud environments Evaluate security posture by using Microsoft Cloud Security Benchmark Design integrated posture management and workload protection Evaluate security posture by using Microsoft Defender for Cloud Posture evaluation with Microsoft Defender for Cloud secure score Design cloud workload protection with Microsoft Defender for Cloud Integrate hybrid and multicloud environments with Azure Arc Design a solution for external attack surface management 17 - Design solutions for securing server and client endpoints Specify server security requirements Specify requirements for mobile devices and clients Specify internet of things (IoT) and embedded device security requirements Secure operational technology (OT) and industrial control systems (ICS) with Microsoft Defender for IoT Specify security baselines for server and client endpoints Design a solution for secure remote access 18 - Design solutions for network security Design solutions for network segmentation Design solutions for traffic filtering with network security groups Design solutions for network posture management Design solutions for network monitoring 19 - Case study: Design security solutions for infrastructure Case study description Case study answers Conceptual walkthrough Technical walkthrough Additional course details: Nexus Humans SC-100T00 Microsoft Cybersecurity Architect training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the SC-100T00 Microsoft Cybersecurity Architect course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

NCSP Digital Business Risk Awareness Training
By IIL Europe Ltd
Accredited through APMG International, certified in the UK by the National Cyber Security Centre (NCSC) and listed as qualified cyber training by Department of Homeland Security Cybersecurity and Infrastructure Security Agency (DHS CISA) in the USA, the NIST Cyber Security Professional (NCSP®) training program teaches individuals and organizations how to engineer, operationalize, and continually improve a NIST Cybersecurity Framework program. This introductory level, non-examinable NCSP® Digital Business Risk Awareness Certificate course takes learners on a journey to understand how the ever-changing cyber threat landscape impacts an organization's ability to secure the value of its digital business services. The course will allow participants to apply what they learn in a real-world environment.

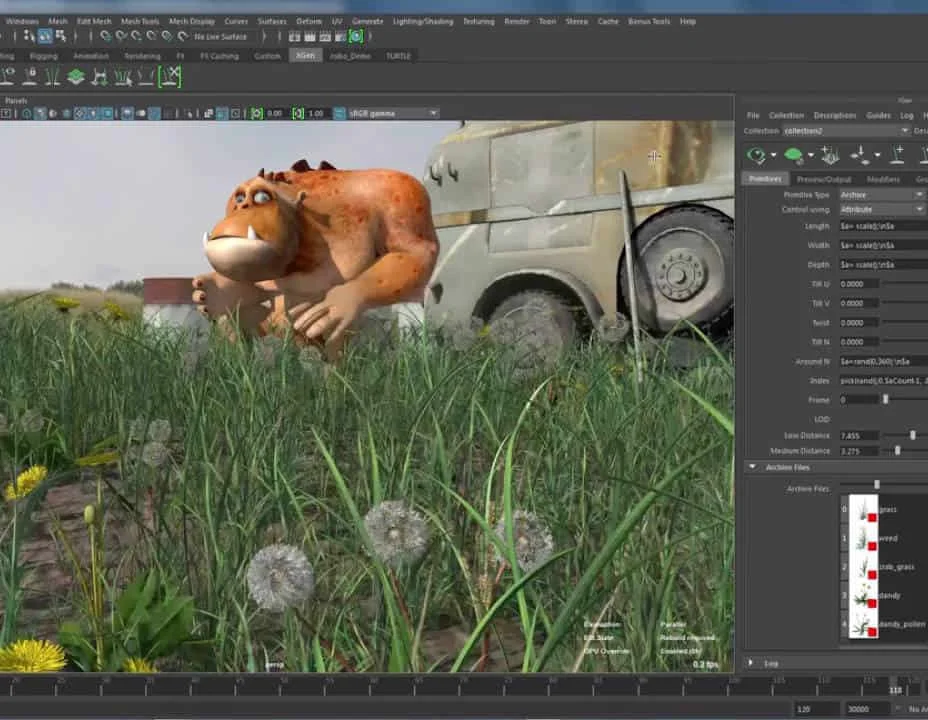
Complete Maya Beginner to Advanced Training
By ATL Autocad Training London
Why Choose Complete Maya Beginner to Advanced Training? Maya's extensive toolkit includes modeling, animation, simulation, and more, amplifying your versatility and influence in the 3D production pipeline. Click here for more info: Website Beginners or those with basic 3D knowledge. No specific digital media background is required. Duration: 40 hours Training Approach: 1-on-1 Sessions. Schedule: Customize your schedule by pre-booking a convenient hour of your choice, available Monday to Saturday between 9 am and 7 pm Course Structure: I. Introduction to Maya (3 hours) Maya Overview and Applications Interface Navigation and Basic Tools Project Creation and Management II. Basic Polygon Modeling (6 hours) Fundamentals of Polygon Modeling Creating and Editing Basic Shapes Advanced Techniques: Extrusions, Bevels, and NURBS for Organic Shapes III. Intermediate Modeling (6 hours) Advanced Polygon Modeling: Booleans, Deformers, and Surfaces Architectural Model Creation Sculpting Tools for Organic Shapes IV. Texturing and Materials (6 hours) Introduction to Texturing and Material Application Texture Mapping, UV Unwrapping, and Shaders Painting Textures with 3D Paint Tool V. Lighting and Rendering (6 hours) Basic and Advanced Lighting Techniques Realistic Lighting Environments Camera Setup, Composition, and Rendering VI. Animation (9 hours) Keyframe Animation and Animation Curves Character Rigging and Animation Complex Character Rigs, Lip Sync, Facial Animation, Dynamics, and Simulations VII. Rigging (4 hours) Skeleton Creation and Joint Binding Weight Maps and Simple to Complex Rigging Systems VIII. Special Effects (4 hours) Particle Systems, Fluid Dynamics, Fire, and Explosions Advanced Simulations with nCloth and nParticles Paint Effects and Mash Networks IX. Advanced Rendering Techniques (2 hours) Render Layers, Passes, and Global Illumination Mental Ray Rendering and Settings X. Conclusion and Next Steps (1 hour) Course Review, Tips for Further Learning Q&A Session and Feedback Please note that the course outline is flexible and can be tailored based on the learners' needs and proficiency levels. Autodesk Maya Basics to Advanced Level Course: Modeling: Surfaces, Control Vertex, Polygons, Extrusion Techniques, Subdiv Modeling, and More Deformations: Twist, Lattice, Flare, Bend Tools Shapes: Lines, Pen Tools, Surface Manipulation Techniques Animations: Keyframe Setup, Path Animations, Skeletons, IK Handles, Skinning Dynamics and Special Effects: Particle Systems, Fluid Dynamics, Lighting Effects, and Advanced Simulations Texturing and Rendering: Diffuse and Bump Mapping, Reflections, Shaders, Lights, and Camera Techniques Fluid Effects and Ncloth: 2D and 3D Containers, Collision Effects, Wind Simulations, and Gravity Control Rendering: Image and Animation Rendering, Playblast, Resolution Controls, and Output Formats. Advanced Modeling: Master intricate 3D models, including polygon, NURBS, and architectural modeling. Expert Texturing: Create realistic textures, apply shaders, and utilize the 3D paint tool. Complex Animation: Rig characters, perform lip sync, facial animation, and dynamic simulations. Special Effects Mastery: Understand particle systems, fluid dynamics, fire effects, and advanced simulations. Rendering Expertise: Grasp advanced rendering techniques, including layers, passes, and global illumination. Comprehensive Rigging: Develop joints, skeletons, and advanced rigging systems for characters and objects. Fluid Dynamics Proficiency: Manipulate 2D/3D fluid containers, create collision effects, and work with wind/gravity simulations. Advanced Lighting and Camera: Perfect lighting, shadows, and special effects. Master camera setups for diverse visual compositions. Recommended Books: "Introducing Autodesk Maya 2023" by Dariush Derakhshani and Randi L. Derakhshani "Mastering Autodesk Maya 2023" by Todd Palamar "Maya Character Creation: Modeling and Animation Controls" by Chris Maraffi "Maya Secrets of the Pros" by John Kundert-Gibbs and Dariush Derakhshani "The Art of 3D Computer Animation and Effects" by Isaac Victor Kerlow Advanced Maya Training Tailored to You: Elevate your Maya skills with specialized training covering essential areas like modeling, UV mapping, texturing, lighting, camera movement, and rigging. Your learning experience is personalized to match your unique requirements and preferences. Discuss your goals with our trainer, and we'll create a syllabus tailored just for you. Flexible Training Choices: Select between in-person sessions at our UK center or attend live online classes, offering convenience and accessibility. Certified Instructors: Benefit from expert guidance provided by Autodesk Authorized Trainers from London Design Training Course. Hands-On Learning: Our practical approach combines theory with step-by-step demonstrations, allowing ample time for hands-on practice on your computer with Maya. You'll retain all the files you create. Compatibility Across Platforms: Maya training caters to both Windows and Mac users, ensuring compatibility with various versions of Maya. Comprehensive Training Package: Participants receive an e-certificate upon successful completion, validating their Maya training. Lifetime Support: Enjoy a lifetime of email support post-training, ensuring assistance with any queries or challenges that arise. Tailored to Your Version: Training can be adapted to your preferred Maya version, ensuring you learn using the most relevant and up-to-date software features. Download Maya https://www.autodesk.co.uk Highly skilled mentors with practical experience. Cutting-edge facilities ensuring an immersive learning environment. Comprehensive courses spanning diverse design disciplines. Practical projects to enhance your portfolio. Networking avenues within the dynamic design community. Skills attuned to current industry trends. Opportunities for professional growth. Choose from flexible in-person or online classes. Internationally recognized training credentials. Engage in London's thriving art and design scene.