- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
803 Courses in Bristol delivered Live Online
⏰️ Available from 24th October at 7pm Sign up once for either one or both sessions for £20 ONLY! ST1 on 29th Oct: 7 - 8pm ST4 on 30th Oct: 7 - 8pm Both sessions will be held on the same link which will be sent on payment. Price: £20 (non-refundable) for Q&A only! OR…… Watch our pre-recorded webinar of ST4 and ST1 Applications and Interviews & attend the Q&A for £25 BELOW !! : https://london-school-of-cardiothoracics.cademy.co.uk/st1-st4-applications-in-cardiothoracic-surgery-webinar-2024-536c1b8c 📝 Sign up to listen to a breakdown of the scoring matrix, how best to boost your portfolio to get a national training number and all the interview tips we can give you! Hear from National trainees who have been through the process, their advice, hints and tips. 🚨 Sign up and get access to the Live Q&A where we will talk about any updates and changes to the 2025 scoring matrix - delivered by current and recently appointed ST4 and ST1 trainees. This session will give you the best opportunity to discuss in real time any changes that come out! Please ensure you check all mail folders, including spam/junk folders, and add 'notifications@system.cademy.co.uk' Cademy to the list of 'safe senders', to ensure you receive all future emails.

EC-Council Certified Ethical Hacker (CEH) v12
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for The Certified Ethical Hacking v12 course will significantly benefit security officers, auditors, security professionals, site administrators, and anyone who is concerned about the integrity of the network infrastructure. Overview Information security controls, laws, and standards. Various types of footprinting, footprinting tools, and countermeasures. Network scanning techniques and scanning countermeasures Enumeration techniques and enumeration countermeasures Vulnerability analysis to identify security loopholes in the target organization?s network, communication infrastructure, and end systems. System hacking methodology, steganography, steganalysis attacks, and covering tracks to discover system and network vulnerabilities. Different types of malware (Trojan, Virus, worms, etc.), system auditing for malware attacks, malware analysis, and countermeasures. Packet sniffing techniques to discover network vulnerabilities and countermeasures to defend against sniffing. Social engineering techniques and how to identify theft attacks to audit human-level vulnerabilities and social engineering countermeasures. DoS/DDoS attack techniques and tools to audit a target and DoS/DDoS countermeasures. Session hijacking techniques to discover network-level session management, authentication/authorization, and cryptographic weaknesses and countermeasures. Webserver attacks and a comprehensive attack methodology to audit vulnerabilities in webserver infrastructure, and countermeasures. Web application attacks, comprehensive web application hacking methodology to audit vulnerabilities in web applications, and countermeasures. SQL injection attack techniques, injection detection tools to detect SQL injection attempts, and countermeasures. Wireless encryption, wireless hacking methodology, wireless hacking tools, and Wi-Fi security tools. Mobile platform attack vector, android vulnerability exploitations, and mobile security guidelines and tools. Firewall, IDS and honeypot evasion techniques, evasion tools and techniques to audit a network perimeter for weaknesses, and countermeasures. Cloud computing concepts (Container technology, serverless computing), the working of various threats and attacks, and security techniques and tools. Penetration testing, security audit, vulnerability assessment, and penetration testing roadmap. Threats to IoT and OT platforms and defending IoT and OT devices. Cryptography ciphers, Public Key Infrastructure (PKI), cryptography attacks, and cryptanalysis tools. CEH provides an in-depth understanding of ethical hacking phases, various attack vectors, and preventative countermeasures. It will teach you how hackers think and act maliciously so you will be better positioned to setup your security infrastructure and defend against future attacks. An understanding of system weaknesses and vulnerabilities helps organizations strengthen their system security controls to minimize the risk of an incident. CEH was built to incorporate a hands-on environment and systematic process across each ethical hacking domain and methodology, giving you the opportunity to work towards proving the required knowledge and skills needed to achieve the CEH credential. You will be exposed to an entirely different posture toward the responsibilities and measures required to be secure. Now in its 12th version, CEH continues to evolve with the latest operating systems, tools, tactics, exploits, and technologies. 1 - Introduction to Ethical Hacking Information Security Overview Cyber Kill Chain Concepts Hacking Concepts Ethical Hacking Concepts Information Security Controls Information Security Laws and Standards 2 - 2 - Foot-printing and Reconnaissance Footprinting Concepts Footprinting through Search Engines Footprinting through Web Services Footprinting through Social Networking Sites Website Footprinting Email Footprinting Who is Footprinting DNS Footprinting Network Footprinting Footprinting through Social Engineering Footprinting Tools Footprinting Countermeasures 3 - Scanning Networks Network Scanning Concepts Scanning Tools Host Discovery Port and Service Discovery OS Discovery (Banner Grabbing/OS Fingerprinting) Scanning Beyond IDS and Firewall Draw Network Diagrams 4 - Enumeration Enumeration Concepts NetBIOS Enumeration SNMP Enumeration LDAP Enumeration NTP and NFS Enumeration SMTP and DNS Enumeration Other Enumeration Techniques Enumeration Countermeasures 5 - Vulnerability Analysis Vulnerability Assessment Concepts Vulnerability Classification and Assessment Types Vulnerability Assessment Solutions and Tools Vulnerability Assessment Reports 6 - System Hacking System Hacking Concepts Gaining Access Escalating Privileges Maintaining Access Clearing Logs 7 - Malware Threats Malware Concepts APT Concepts Trojan Concepts Virus and Worm Concepts Fileless Malware Concepts Malware Analysis Countermeasures Anti-Malware Software 8 - Sniffing Sniffing Concepts Sniffing Technique: MAC Attacks Sniffing Technique: DHCP Attacks Sniffing Technique: ARP Poisoning Sniffing Technique: Spoofing Attacks Sniffing Technique: DNS Poisoning Sniffing Tools Countermeasures Sniffing Detection Techniques 9 - Social Engineering Social Engineering Concepts Social Engineering Techniques Insider Threats Impersonation on Social Networking Sites Identity Theft Countermeasures 10 - Denial-of-Service DoS/DDoS Concepts DoS/DDoS Attack Techniques BotnetsDDoS Case Study DoS/DDoS Attack Tools Countermeasures DoS/DDoS Protection Tools 11 - Session Hijacking Session Hijacking Concepts Application Level Session Hijacking Network Level Session Hijacking Session Hijacking Tools Countermeasures 12 - Evading IDS, Firewalls, and Honeypots IDS, IPS, Firewall, and Honeypot Concepts IDS, IPS, Firewall, and Honeypot Solutions Evading IDS Evading Firewalls IDS/Firewall Evading Tools Detecting Honeypots IDS/Firewall Evasion Countermeasures 13 - Hacking Web Servers Web Server Concepts Web Server Attacks Web Server Attack Methodology Web Server Attack Tools Countermeasures Patch Management Web Server Security Tools 14 - Hacking Web Applications Web Application Concepts Web Application Threats Web Application Hacking Methodology Web API, Webhooks, and Web Shell Web Application Security 15 - SQL Injection SQL Injection Concepts Types of SQL Injection SQL Injection Methodology SQL Injection Tools Evasion Techniques Countermeasures 16 - Hacking Wireless Networks Wireless Concepts Wireless Encryption Wireless Threats Wireless Hacking Methodology Wireless Hacking Tools Bluetooth Hacking Countermeasures Wireless Security Tools 17 - Hacking Mobile Platforms Mobile Platform Attack Vectors Hacking Android OS Hacking iOS Mobile Device Management Mobile Security Guidelines and Tools 18 - IoT and OT Hacking IoT Hacking IoT Concepts IoT Attacks IoT Hacking Methodology IoT Hacking Tools Countermeasures OT Hacking OT Concepts OT Attacks OT Hacking Methodology OT Hacking Tools Countermeasures 19 - Cloud Computing Cloud Computing Concepts Container Technology Serverless Computing Cloud Computing Threats Cloud Hacking Cloud Security 20 - Cryptography Cryptography Concepts Encryption Algorithms Cryptography Tools Public Key Infrastructure (PKI) Email Encryption Disk Encryption Cryptanalysis Countermeasures Additional course details: Nexus Humans EC-Council Certified Ethical Hacker (CEH) v.12 training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the EC-Council Certified Ethical Hacker (CEH) v.12 course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Microsoft Project Advanced - In-company (now with trainer led live online classes)
By Microsoft Office Training
Course Objectives At the end of this course you will be able to: Manage project costs Consolidate and reuse project plan information Exchange project plan data with other applications Update a project plan Customise Project to meet specific requirements ' 1 year email support service Take a look at the consistent excellent feedback from our corporate clients visiting our site ms-officetraining co uk Customer Feedback Really useful and engaging course. Learnt a lot that will be very beneficial in my job. Trainer was great. Kelly Moreley - TACT Very happy with the course. Worked as a good refresher from what I knew already and enhanced my knowledge further Jenny Price - Acer ' With more than 20 years experience, we deliver courses on all levels of the Desktop version of Microsoft Office and Office 365; ranging from Beginner, Intermediate, Advanced to the VBA level. Our trainers are Microsoft certified professionals with a proven track record with several years experience in delivering public, one to one, tailored and bespoke courses. Our competitive rates start from £550.00 per day of training Tailored training courses: You can choose to run the course exactly as they are outlined by us or we can customise it so that it meets your specific needs. A tailored or bespoke course will follow the standard outline but may be adapted to your specific organisational needs. Exchanging Project Plan Data with Other Applications Import a list of tasks from Outlook Import a Task List from an Excel File Create a Custom Import Map Export Project Plan Cost Data into Excel Save Project Plan Information as a Web Page Updating a Project Plan Enter Task Progress Information View Task Progress Split a Task Reschedule a Task Creating Custom Fields Text fields Lookup fields Calculated fields with the use of formulas and functions Inserting Graphical Indicators Customizing how you look at data Filter Tasks in a Project Plan Create a Custom Table Create a Custom View Copy custom Views and Tables between projects Earned value analysis Understanding Earned Value Fields View Multiple Baselines in a Single Project Tracking progress between interim plans Creating Custom Reports Create a Custom Report Modify a Custom Report's Header and Footer Add a Picture to a Report Modify a Custom Report's Margins Print a Custom Report Re-using Project Plan Information Create a Project Plan Template Create a Custom Combination View Make Custom Views Available to Other Project Plans Share Resources between Projects, Create a Master Project Plan with sub projects Who is this course for? Who is this course for? This course is designed for those that who already have the skills to create and modify project plans and would like to acquire a more in depth and thorough knowledge of more advanced functionalities in project planning and tracking. Requirements Requirements Preferably, delegates would have attended the MS Project Introduction course. Career path Career path Microsoft Office know-how can instantly increase your job prospects as well as your salary. 80 percent of job openings require spreadsheet and word-processing software skills

Docker for engineers training course description Docker is the container platform of choice. This course covers how to use Docker to package your applications with all of their dependencies and then test, deploy, scale and support your containers. Hands on sessions follow all the major sessions. What will you learn Work with Docker images, containers and command line tools. Deploy and test Docker containers. Debug Docker containers. Describe Docker networking, deployment tools, orchestration and security. Docker for engineers training course details Who will benefit: Anyone working with Docker. Prerequisites: Introduction to virtualization. Duration 2 days Docker for engineers training course contents Introduction The birth of Docker, the promise of Docker, what Docker isn't. Docker at a glance Process simplification, broad support and adoption, architecture, getting the most from Docker, the Docker workflow. Installing Docker Important terminology, Docker client, Docker server, test the setup. Working with Docker images Anatomy of a Dockerfile, building an image, running your image, custom base images, storing images. Working with Docker containers What are containers? creating a container, starting a container, auto-restarting a container, stopping a container, killing a container, pausing and unpausing a container, cleaning up containers and images, next steps. Exploring Docker Printing the Docker version, server information, downloading image updates, inspecting a container, getting inside a running container, exploring the shell, returning a result, docker logs, monitoring Docker, exploration. The path to production containers Deploying, testing containers. Debugging containers Process output, process inspection, controlling processes, network inspection, image history, inspecting a container, filesystem inspection, moving along. Docker at scale Docker swarm, centurion, amazon EC2 container service. Advanced topics Pluggable backends, containers in detail, security, networking. Designing your production container platform The twelve-factor app, the reactive manifesto. Conclusion The challenges, the Docker workflow, minimizing deployment artifacts, optimizing storage and retrieval, the payoff, the final word.

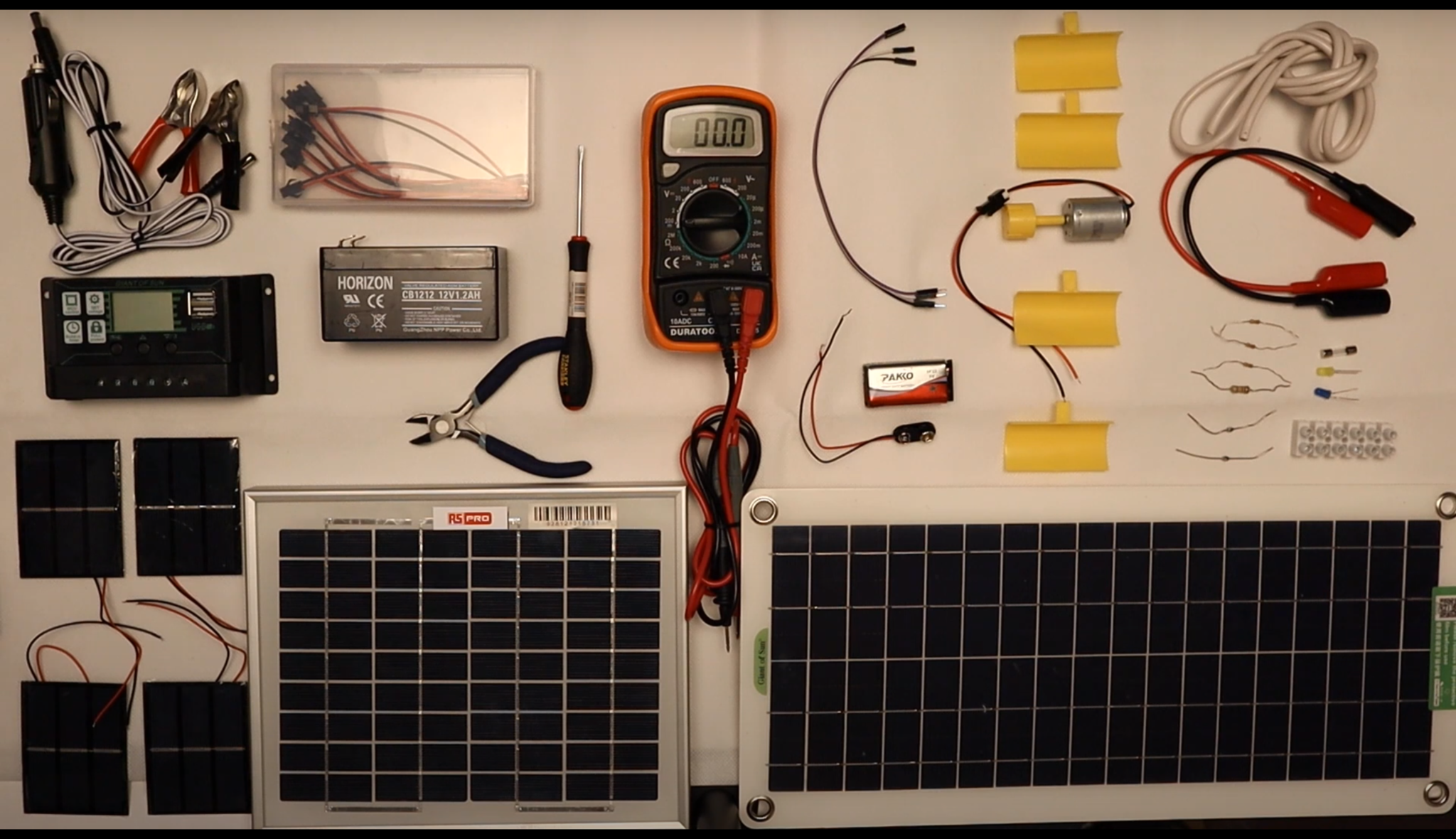
Alternative Energy Technology Course
By Hi-Tech Training
The Alternative Energy Technology Course is a practically based alternative energy course designed to give participants an understanding of alternative energy options and provide them with that practical knowledge and skills to build solar to electric and wind to electric systems at a foundation level. The course is designed to be of benefit to people either working or intending to work as:- Alternative Energy Installers or anyone just wishing to gain practical knowledge of Practical Alternative Energy Systems
European Data Protection & Privacy Programme Management - DPO Ready
By Training Centre
European Data Protection Principles of Data Protection in Europe covers the essential pan-European and national data protection laws, as well as industry-standard best practices for corporate compliance with these laws. Those taking this course will gain an understanding of the European model for privacy enforcement, key privacy terminology and practical concepts concerning the protection of personal data and trans-border data flows. The training is based on the body of knowledge for the IAPP's ANSI-accredited Certified Information Privacy Professional/Europe (CIPP/E) certification program. Privacy Programme Management Principles of Privacy Management is the how-to training on implementing a privacy program framework, managing the privacy program operational lifecycle and structuring a knowledgeable, high-performing privacy team. Those taking this course will learn the skills to manage privacy in an organisation through process and technology-regardless of jurisdiction or industry. The Principles of Privacy Program Management training is based on the body of knowledge for the IAPP's ANSI-accredited Certified Information Privacy Manager (CIPM) certification programme. Make a difference in your organization and in your career. The CIPM designation says that you're a leader in privacy program administration and that you've got the goods to establish, maintain and manage a privacy program across all stages of its lifecycle. About This Course Delivered in a modular format, this four day course covers Days 1 & 2 Module 1: Data Protection Laws Introduces key European data protection laws and regulatory bodies, describing the evolution toward a Harmonised European Legislative Framework. Module 2: Personal Data Defines and differentiates between types of data-including personal, anonymous, pseudo-anonymous and special categories. Module 3: Controllers and Processors Describes the roles and relationships of controllers and processors. Module 4: Processing Personal Data Defines data processing and GDPR processing principles, Explains the application of the GDPR and outlines the legitimate bases for processing personal data. Module 5: Information provision Explains controller obligations for providing information about data processing activities to data subjects and Supervisory Authorities. Module 6: Data Subjects 'Rights Describes data subjects' rights, applications of rights and obligations controller and processor. Module 7: Security or Processing Discusses considerations and duties of controllers and processors for Ensuring security of personal data and providing notification of data breaches. Module 8: Accountability Investigates accountability requirements, data protection management systems, data protection impact assessments, privacy policies and the role of the data protection officer. Module 9: International Data Transfers Outlines options and obligations for transferring data outside the European Economic Area, Decisions adequacy and appropriateness safeguards and derogations. Module 10: Supervision and Enforcement Describes the role, powers and procedures or Supervisory Authorities; the composition and tasks of the European Data Protection Board; the role of the European Data Protection Supervisor; and remedies, liabilities and penalties for non-compliance. Module 11: Compliance Discusses the applications of European data protection law, legal bases and compliance requirements for processing personal data in practice, employers-including processing employee data, surveillance, direct marketing, Internet technology and communications and outsourcing. Days 3 & 4 Module 1: Introduction to privacy program management Identifies privacy program management responsibilities, and describes the role of accountability in privacy program management. Module 2: Privacy governance Examines considerations for developing and implementing a privacy program, including the position of the privacy function within the organization, role of the DPO, program scope and charter, privacy strategy, support and ongoing involvement of key functions and privacy frameworks. Module 3: Applicable laws and regulations Discusses the regulatory environment, common elements across jurisdictions and strategies for aligning compliance with organizational strategy. Module 4: Data assessments Relates practical processes for creating and using data inventories/maps, gap analyses, privacy assessments, privacy impact assessments/data protection impact assessments and vendor assessments. Module 5: Policies Describes common types of privacy-related policies, outlines components and offers strategies for implementation. Module 6: Data subject rights Discusses operational considerations for communicating and ensuring data subject rights, including privacy notice, choice and consent, access and rectification, data portability, and erasure and the right to be forgotten. Module 7: Training and awareness Outlines strategies for developing and implementing privacy training and awareness programs. Module 8: Protecting personal information Examines a holistic approach to protecting personal information through privacy by design. Module 9: Data breach incident plans Provides guidance on planning for and responding to a data security incident or breach. Module 10: Measuring, monitoring and auditing program performance Relates common practices for monitoring, measuring, analyzing and auditing privacy program performance Prerequisites There are no prerequisites for this course but attendees would benefit from a review of the materials on the IAPP SITE What's Included? 1 years membership of the IAPP Breakfast, Lunch, mid-morning and afternoon snacks, teas, coffees Official Study Guides* Official Participant Guides* Official Exam Q&A's* Both exam fees * In electronic format for Live Online and hard copy for Classroom delegates Who Should Attend? This course is suitable for aspiring Data Protection Officers, as well as Information Security Managers, Lawyers, Data Managers, Analysts and Risk Teams. Provided by Our Guarantee We are an approved IAPP Training Partner. You can learn wherever and whenever you want with our robust classroom and interactive online training courses. Our courses are taught by qualified practitioners with a minimum of 25 years commercial experience. We strive to give our delegates the hands-on experience. Our courses are all-inclusive with no hidden extras. The one-off cost covers the training, all course materials, and exam voucher. Our aim: To achieve a 100% first time pass rate on all our instructor-led courses. Our Promise: Pass first time or 'train' again for FREE. *FREE training offered for retakes - come back within a year and only pay for the exam.

Application delivery training course description A concise hands on course covering section 1 of the F5 networks AD fundamentals exam. The course focuses on the technology and not any one manufacturers product. This will enable delegates to work with devices from any manufacturer. Practical hands on with Cisco and Microsoft systems follow the major sessions to reinforce the theory. What will you learn Explain, compare and contrast the OSI layers. Explain protocols and technologies specific to the data link layer. Explain protocols and apply technologies specific to the network layer. Explain the features and functionality of protocols and technologies specific to the Transport layer. Explain the features and functionality of protocols and technologies specific to the Application layer Application delivery training course details Who will benefit: Anyone taking the F5 networks AD fundamentals exam. Technical staff working in Application delivery. Prerequisites: None. Duration 3 days Application delivery training course contents What is TCP/IP? Protocols, services. The Internet, RFCs, The OSI 7 layer model. Layer 1 cables. Ping and addressing Host configuration of IP addresses, subnet masks, default gateways, ipconfig, ping. Hands on Configuring TCP/IP, ping. Ethernet and the data link layer 802.3, evolution, choosing cables, topologies, CSMA/CD, hubs, NICs, MAC addresses. Hands on Analysing MAC addresses. IP and Ethernet Relationship. Hands on ARP. What is a switch? Switches connect multiple devices, switches versus hubs, simultaneous conversations, switches work at layer 2, the forwarding database, how the forwarding database is built, broadcast and collision domains. Hands on Difference between hubs and switches. Link aggregation Loops, broadcast storms, STP, Architectures, modes, link aggregation, load sharing, resilience. Hands on fail over times. VLANs Virtual versus physical LANs, Why have VLANs? Broadcast domains. Hands on VLANs effect on traffic. IP IP datagram format, ICMP datagram format. Hands on Analysing IP and ICMP packets. IP addressing Format of addresses, registering, dotted decimal notation, choosing addresses, DHCP. Hands on impact of addressing errors. Routing What is a router? Reason for routing, network addressing, default gateways, how routing works, routing and addresses, routing tables, traceroute. Hands on Using a routed network. Routing protocols IGPs, EGPs, RIP & OSPF. Hands on Configuring routers for RIP and OSPF. Subnetting When to subnet, subnet masks, working with subnetting, CIDR notation. Hands on Changing the routed network to use subnetting. The transport layer UDP, Ports, TCP, acknowledgements, sliding windows. Hands on Analysing packets. Applications Clients, servers, web, Email SMTP, resource sharing, IM, VoIP, Video over IP, terminal emulation, FTP. Hands on FTP, SIP. Web pages URLs, DNS, names to IP addresses. HTTP, versions and status codes. Keepalives, cookies. Hands on Analysing HTTP headers.

VBA with Microsoft Excel
By Nexus Human
Duration 1 Days 6 CPD hours This course is intended for This course is primarily designed for students who want to gain the skills necessary to use VBA to automate tasks in Excel such as collecting data from external sources, cleaning, and manipulating data. The target student may also want to learn how to create custom worksheet functions to streamline worksheet formulas and make complex worksheets easier to support, maintain, and understand. Overview Identify general components of VBA and their appropriate use in solving business solutions. Record VBA macros to automate repetitive tasks. Write VBA code to create VBA subroutines and functions. Use various programming elements to solve problems through code, including variables,objects, conditional statements, and loops. Eliminate, avoid, or handle errors in VBA code, and optimize its performance. VBA (Visual Basic for Applications) enables you to enhance and extend the capabilities of Microsoft Excel and other applications in the Microsoft 365 application suite. You can use VBA to perform tasks that would be difficult or impossible to do using only worksheet functions, and you can automate a wide range of tasks so they can be performed faster, more consistently, and with less effort than performing them manually. This course will give you a good foundation for understanding, creating, and using VBA in your own Excel workbooks. You will learn how to use the macro recorder effectively, as well as how to write your own VBA code from scratch. You will use tools built into Excel to explore and learn VBA's capabilities and to optimize and debug your code. Prerequisites To ensure your success in this course, you should be an experienced Excel user who is comfortable creating and working with Excel workbooks, including tasks such as entering worksheet formulas, using absolute and relative addressing, formatting cells, and creating pivot tables and charts. This level of skill could be acquired by taking the Microsoft Excel for Office 365 (Desktop or Online) courses, Parts 1, 2, and 3. 1. Using VBA to Solve Business Problems Use Macros to Automate Tasks in Excel Identify Components of Macro-Enabled Workbooks Configure the Excel VBA Environment 2. Recording a Macro Use the Macro Recorder to Create a VBA Macro Record a Macro with Relative Addressing Delete Macros and Modules Identify Strategies for Using the Macro Recorder 3. Writing VBA Code Directly Write VBA Code Discover Objects You Can Use Create a Custom Function 4. Solving Problems through Code Make Decisions in Code Work with Variables Perform Repetitive Tasks 5. Improving Your VBA Code Debug VBA Errors Deal with Errors Improve Macro Performance 6. Controlling How and When Macros Run Prompt the User for Information Configure Macros to Run Automatically Additional course details: Nexus Humans VBA with Microsoft Excel (v1.2) training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the VBA with Microsoft Excel (v1.2) course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Windows clustering training course description This course covers high availability and disaster recovery technologies such as live migration, storage migration and Hyper-V Replica, as well as providing indepth coverage of failover clustering including a detailed implementation of failover clustering of Hyper- V using SoFS. The course also covers System Center Virtual Machine Manager and implementing Network Load Balancing (NLB) and load balancing clusters. What will you learn Plan and implement a failover cluster. Describe managing server roles and clustering resources. Implement and manage virtual machines. Use System Center Virtual Machine Manager. Describe cloud-based storage and high availability solutions. Implement a Network Load Balancing (NLB) cluster. Windows clustering training course details Who will benefit: Technical staff working with Microsoft clusters. Prerequisites: Supporting Microsoft Windows server Duration 3 days Windows clustering training course contents High Availability in Windows Server Defining levels of availability, High Availability and disaster recovery solutions with Hyper-V Virtual Machines, High Availability with failover clustering in Windows Server. Hands on Configuring High Availability and Disaster Recovery. Implementing failover clustering Planning a failover cluster, creating a new failover cluster. Hands on Creating and Administering a Cluster. Server roles and clustering resources Configuring highly available applications and services on a failover cluster, managing and maintaining a failover cluster, troubleshooting a failover cluster, implementing site high availability with multisite failover clusters. Hands on Managing server roles and clustering resources. Failover clustering with Hyper-V Overview of integrating Hyper-V with failover clustering, implementing Hyper-V with failover clustering, managing and maintaining Hyper-V Virtual Machines on failover clusters. Hands on Implementing failover clustering by using Hyper-V Storage Infrastructure Management with Virtual Machine Manager Virtual Machine Manager, managing storage infrastructure with Virtual Machine Manager, provisioning failover clustering in Virtual Machine Manager. Hands on Managing storage infrastructure. Cloud-Based storage and High Availability Azure storage solutions and infrastructure, cloud integrated storage with StorSimple, disaster recovery with Azure Site Recovery. Hands on Managing cloud-based storage and high availability Network Load Balancing Clusters Overview of NLB, configuring an NLB cluster, planning NLB. Hands on Implementing a Network Load Balancing Cluster

Mastering 3ds Max: Complete Basic to Advanced Training
By ATL Autocad Training London
Who is this course for? Mastering 3ds Max: Complete Basic to Advanced Training. Looking to learn 3D modelling and animation? Look no further than our comprehensive 3ds Max beginner course! Gain a strong foundation in 3ds Max and learn essential skills for creating stunning 3D models and visualizations. Check our Website Training Duration: 40 hours Method: 1-on1 Sessions and Customized Content. Schedule: Choose your preferred time slot between 9 am and 7 pm, Mon to Sat, tailored to fit your schedule. Course Title: 3ds Max and V-Ray Comprehensive Training Program (40 Hours) Course Overview: Dive deep into the world of 3D visualization and rendering with our intensive 3ds Max and V-Ray training program. Over the course of 40 hours, you'll master the fundamental concepts, advanced techniques, and practical applications of both 3ds Max and V-Ray, empowering you to create stunning, photorealistic visualizations for various industries. Course Outline: Module 1: Introduction to 3ds Max (8 hours) Understanding the 3ds Max interface and tools Basic 3D modeling techniques and workflows Material creation and texture mapping Lights and cameras setup for scenes Module 2: Advanced 3ds Max Techniques (8 hours) Character modeling and animation Particle systems and dynamics Advanced lighting and shading techniques Scene composition and camera animation Module 3: V-Ray Fundamentals (8 hours) Introduction to V-Ray rendering engine V-Ray materials and texture mapping Lighting with V-Ray lights and HDRI maps V-Ray camera settings and depth of field Module 4: Advanced V-Ray Rendering (8 hours) Global illumination and image-based lighting V-Ray proxies and instancing Advanced V-Ray shaders and displacement maps Render elements and post-production techniques Module 5: Architectural Visualization with V-Ray (8 hours) Interior and exterior scene setup Realistic materials for architectural elements Lighting strategies for different times of the day Creating lifelike environments and atmospheric effects Course Features: Hands-On Learning: Engage in practical exercises and real-world projects to reinforce your skills and knowledge. Industry-Standard Tools: Work with the latest versions of 3ds Max and V-Ray, widely used in the professional 3D visualization industry. Expert Instruction: Learn from certified trainers and industry professionals with extensive experience in 3D modeling and rendering. Project-Based Assessments: Apply learned techniques to comprehensive projects, receiving feedback and guidance to refine your skills. Flexible Learning: Choose between in-person and online sessions, accommodating various schedules and learning preferences. Upon completing this 40-hour course, you will be equipped with the expertise to create visually stunning 3D renderings and animations, making you proficient in both 3ds Max and V-Ray for a successful career in architectural visualization, gaming, film production, and more. Upon completion, participants will: Master 3ds Max & V-Ray: Acquire advanced skills in 3ds Max and V-Ray for creating realistic 3D visualizations. Expert in Architectural Visualization: Specialize in architectural visualization techniques, ideal for interior designers and architects. Project-Based Proficiency: Apply learned skills to real projects, developing a professional portfolio. Recommended Jobs: Architectural Visualization Artist 3D Animator Product Visualization Specialist Interior Designer VR Developer Freelance 3D Artist Game Environment Artist Visualization Consultant This training opens doors to diverse roles in architecture, gaming, design, and more. Duration: 40 Hours Focus: Master 3ds Max and V-Ray for advanced 3D visualizations and architectural rendering. Learning Format: One-on-One Training for personalized attention. Availability: Book your sessions Monday to Saturday, 9 am to 7 pm, tailored to your schedule. Outcome: Expertise in 3ds Max, V-Ray, and specialized architectural visualization skills. Practical Focus: Hands-on projects and real-world applications for skill reinforcement. Certification: Upon completion, receive a certificate showcasing your advanced 3D modeling and rendering skills. This one-on-one course offers tailored training sessions from Monday to Saturday, 9 am to 7 pm, ensuring personalized attention and flexibility to suit your schedule. Download 3ds max Ongoing Email Support: We offer continuous email assistance, ensuring your queries are promptly addressed even after the course completion. Comprehensive Resources: Access extensive handouts and valuable documents designed to reinforce your learning experience. Flexible Financial Options: Explore adaptable financial support options, including installment plans and assistance through job center plus and DWP. Reach out to us for specific details. Satisfaction Guarantee: Although it's highly improbable given our exceptional quality and skilled tutors, if you find dissatisfaction after your initial session, we will promptly address your concerns. If necessary, a refund may be provided (Terms and conditions apply). Optimized Software Experience: Receive guidance on optimizing your computer for enhanced software performance in applications like Autocad, 3ds Max, and Photoshop, whether you're on MAC or PC platforms. Industry Connections: Leverage our industry ties as we actively showcase your portfolio to potential employers. Many of our students have secured jobs through our recommendations, offering valuable career opportunities.
