- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
3699 Courses in Belfast delivered Live Online
IATP - Asbestos Awareness Online
By Airborne Environmental Consultants Ltd
If you have no intention of removing asbestos but work on buildings built or refurbished before the year 2000, asbestos could be present. You will need awareness training so you know how to avoid the risks. Asbestos awareness training should be given to employees whose work could foreseeably disturb the fabric of a building and expose them to asbestos or who supervise or influence the work. In particular, it should be given to those workers in the refurbishment, maintenance and allied trades where it is foreseeable that ACMs may become exposed during their work.

Essential Adobe InDesign Training Course
By ATL Autocad Training London
Who is this for? Essential Adobe InDesign Training Course. Acquire Adobe InDesign basics from certified instructors. Master layout design, typography, and core design concepts. Opt for in-person or live online sessions. Receive a Certificate of Completion and lifelong email assistance. Lean desktop publishing skills and quality layouts. Click here for more info: Website Duration: 5 hours Approach: Individualized 1-on-1 training with customized content. Schedule: Flexible sessions, available Monday to Saturday from 9 am to 7 pm. Course Outline: Module 1: Introduction to Adobe InDesign (1 hour) Familiarize with workspace and tools Create new documents with appropriate page size and margins Effectively format text and images Customize the interface for efficient workflow Module 2: Text Formatting and Styles (1 hour) Apply consistent character and paragraph styles Manage text flow using frames Organize lists with bullets and numbering Master special characters for precise typography Module 3: Working with Images (1 hour) Import and position images in documents Adjust image size and alignment within frames Create professional layouts with text wrapping around images Enhance visuals with image frames and effects Module 4: Layout Design (1 hour) Create precise grids and guides for alignment Arrange objects for balanced layouts Streamline work with layers Maintain consistency using master pages and templates Module 5: Printing and Exporting (1 hour) Understand color modes and print principles Export to PDF and other formats for diverse outputs Ensure print readiness through preflighting Efficiently archive and manage InDesign files Through practical exercises, solidify your grasp of each module, enabling you to design visually appealing layouts, craft documents for various purposes, and manage InDesign projects adeptly. Adobe InDesign's potential is vast, and this fundamentals course opens doors for you to explore diverse design projects. Seize this opportunity to unleash your creative prowess with InDesign! Upon completing the Adobe InDesign Fundamentals course, participants will be able to: Master InDesign Tools: Demonstrate proficiency in utilizing InDesign's essential tools, workspace, and interface for effective design workflows. Layout Design Skills: Create visually appealing layouts using grids, guides, and balanced object arrangements, ensuring professional-quality design. Text Formatting Mastery: Apply consistent character and paragraph styles, manage text flow, and enhance typography with special characters. Image Manipulation Expertise: Import, position, and enhance images within frames, integrating them seamlessly into layouts. Printing and Exporting Proficiency: Understand color modes, print principles, and export documents to various formats, ensuring print readiness and diverse output options. Efficient Project Management: Utilize layers, master pages, and templates for streamlined project organization and management in InDesign. Book Recommendations: "InDesign CC Classroom in a Book" by Kelly Kordes Anton and John Cruise: This official Adobe guide provides hands-on lessons and practical techniques for mastering InDesign's core features. "InDesign Type: Professional Typography with Adobe InDesign" by Nigel French: Explore advanced typography techniques, layout principles, and typographic finesse specific to Adobe InDesign. "Real World Adobe InDesign CC" by Olav Martin Kvern, David Blatner, and Bob Bringhurst: A comprehensive guide offering practical insights, tips, and real-world techniques for InDesign users of all levels. "The Adobe InDesign CS6 Book for Digital Photographers" by Scott Kelby: Focused on integrating photography with InDesign, this book provides valuable insights into creating visually stunning layouts with images. "InDesign Secrets" by David Blatner and Anne-Marie Concepción: This book is packed with expert tips, tricks, and techniques that can significantly enhance your efficiency and creativity in InDesign. 1-on-1 InDesign Courses: Personalized Learning: Tailored 1-on-1 courses designed to meet your specific learning needs and goals. Expert Instructors: Learn from industry professionals with extensive experience in animation and design. Flexible Scheduling: Schedule sessions at your convenience, allowing you to balance learning with your busy lifestyle. Comprehensive Curriculum: Dive deep into animation techniques, software mastery, and creative skills through our comprehensive courses. Hands-On Training: Get practical, hands-on experience with real-world animation projects, enhancing your skills effectively. Individual Attention: Benefit from personalized attention and detailed feedback from instructors, ensuring your progress and understanding. Professional Development: Acquire skills relevant to the industry, empowering you for career advancement in animation and related fields. Portfolio Enhancement: Develop a strong portfolio with the guidance of experts, showcasing your newfound skills and creativity. Post-Course Support: Enjoy continued support even after the course completion, ensuring you have resources for ongoing learning and growth. Certification: Receive a certificate upon course completion, validating your expertise and enhancing your professional credentials. Course Highlights: Master Adobe InDesign's key features for layout, text, images, and graphics. Learn design principles and typography techniques for visually appealing documents. Efficiently handle multi-page projects like magazines and brochures. Utilize styles, templates, and libraries for streamlined design and consistency. Explore advanced techniques for interactive PDFs and digital publishing. Earn a Certificate of Completion for your Adobe InDesign proficiency. Flexible learning options: in-person or live online sessions. Lifetime email support for ongoing assistance after the course. Adobe InDesign Learn & Support https://helpx.adobe.com ⺠support ⺠indesign Get started with Adobe InDesign. Find tutorials, the user guide, answers to common questions, and help from the community forum.

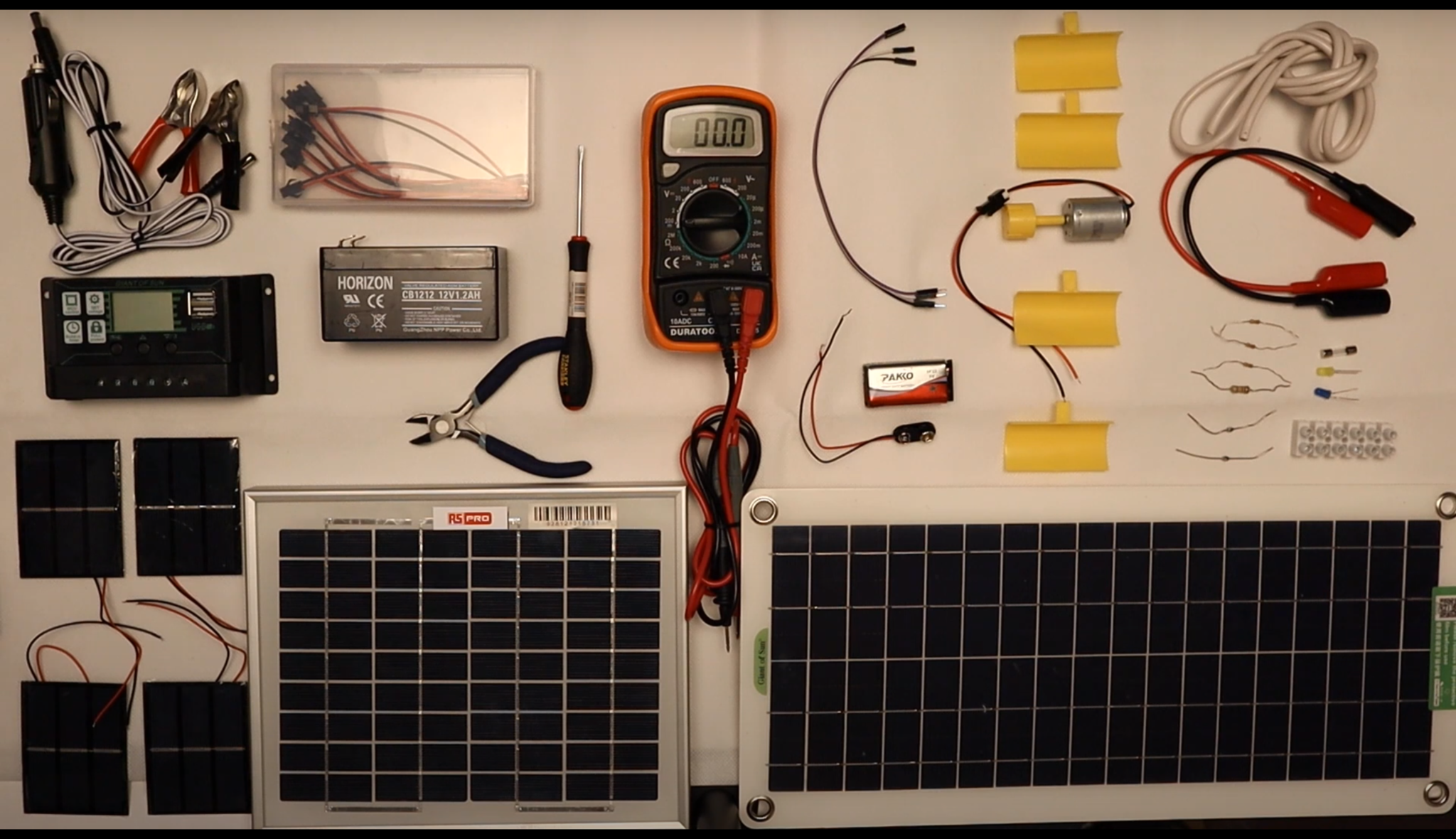
Alternative Energy Technology Course
By Hi-Tech Training
The Alternative Energy Technology Course is a practically based alternative energy course designed to give participants an understanding of alternative energy options and provide them with that practical knowledge and skills to build solar to electric and wind to electric systems at a foundation level. The course is designed to be of benefit to people either working or intending to work as:- Alternative Energy Installers or anyone just wishing to gain practical knowledge of Practical Alternative Energy Systems
Overview Overview The purpose of this course is to enable participants to understand and apply the principles of emergency response planning and crisis management. It considers the need for emergency and crisis response planning and an integrated approach to emergency management. Training typically covers: Crisis management structure and staffing an emergency response team Incident reporting and notification Operational processes Guidance of facility response policies and procedures Annual testing and evaluation of the crisis management plan Upcoming Events Online (USD 1950) Online Streaming Live (Flexible Dates) At Venue (USD 4500) Dubai 13 March - 17 March Istanbul 20 March - 24 March London 20 March - 24 March For more dates and Venue, Please email sales@gbacorporate.co.uk

Writing for the Business Professional
By Nexus Human
Duration 2 Days 12 CPD hours This course is intended for Professionals desiring to be able to communicate clearly and concisely in their writing will benefit from this course. Overview Awareness of common spelling and grammar issues in business writing. Basic concepts in sentence and paragraph construction. Basic structure of agendas, email messages, business letters, business proposals, and business reports. Collaborative writing techniques, tools and best practices Tips and techniques to use when deciding the most appropriate format to use for agendas, email messages, business letters, business proposals, and business reports In this course, you will learn the essential skills needed to organize your thoughts and select the best words and phrases to clearly convey them in writing. Private classes on this topic are available. We can address your organization?s issues, time constraints, and save you money, too. Contact us to find out how. 1. Working With Words Monitoring Spelling, Grammar, and Verb Tense Creating a Reference Sheet 2. Constructing Sentences Recognizing Sentence Parts Classifying Sentence Type Increasing Readability with Punctuation 3. Creating Paragraphs The Three Basic Components Organization Methods 4. Finding Facts Identifying and Using Key Resources Fact-Finding and Information Gathering 5. Collaborative Writing Clarifying the Objective Collaborative Writing Strategies and Patterns 6. Types of Collaborative Business Writing Applying Different Construction Techniques Cut & Paste, Puzzle, Sequential Summative Integrating Construction 7. Collaborative Tools and Processes Planning and Revision Creating Outlines and Storyboards Building Team Cohesion 8. Writing Meeting Agendas Choosing an Agenda Format Structuring and Writing the Agenda 9. Writing E-Mails, Reports and Proposals Addressing Your Message Using Proper Grammar and Defining Acronyms Structuring, Formatting, and Writing Your Report Additional course details: Nexus Humans Writing for the Business Professional training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Writing for the Business Professional course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Rapid Prototyping with Axure
By Bunnyfoot
This one-day course introduces the field of user experience and provides an excellent entry point to our other specialised training courses. UX processes and practices have become a central component of product design, service design and web design.

SC-100T00 Microsoft Cybersecurity Architect
By Nexus Human
Duration 4 Days 24 CPD hours This course is intended for This course is for experienced cloud security engineers who have taken a previous certification in the security, compliance and identity portfolio. Specifically, students should have advanced experience and knowledge in a wide range of security engineering areas, including identity and access, platform protection, security operations, securing data, and securing applications. They should also have experience with hybrid and cloud implementations. Beginning students should instead take the course SC-900: Microsoft Security, Compliance, and Identity Fundamentals. This is an advanced, expert-level course. Although not required to attend, students are strongly encouraged to have taken and passed another associate level certification in the security, compliance and identity portfolio (such as AZ-500, SC-200 or SC-300) before attending this class. This course prepares students with the expertise to design and evaluate cybersecurity strategies in the following areas: Zero Trust, Governance Risk Compliance (GRC), security operations (SecOps), and data and applications. Students will also learn how to design and architect solutions using zero trust principles and specify security requirements for cloud infrastructure in different service models (SaaS, PaaS, IaaS). Prerequisites Highly recommended to have attended and passed one of the associate level certifications in the security, compliance and identity portfolio (such as AZ-500T00 Microsoft Azure Security Technologies, SC-200T00: Microsoft Security Operations Analyst, or SC-300T00: Microsoft Identity and Access Administrator.) Advanced experience and knowledge in identity and access, platform protection, security operations, securing data and securing applications. Experience with hybrid and cloud implementations. 1 - Introduction to Zero Trust and best practice frameworks Zero Trust initiatives Zero Trust technology pillars part 1 Zero Trust technology pillars part 2 2 - Design solutions that align with the Cloud Adoption Framework (CAF) and Well-Architected Framework (WAF) Define a security strategy Cloud Adoption Framework secure methodology Design security with Azure Landing Zones The Well-Architected Framework security pillar 3 - Design solutions that align with the Microsoft Cybersecurity Reference Architecture (MCRA) and Microsoft cloud security benchmark (MCSB) Design solutions with best practices for capabilities and controls Design solutions with best practices for attack protection 4 - Design a resiliency strategy for common cyberthreats like ransomware Common cyberthreats and attack patterns Support business resiliency Ransomware protection Configurations for secure backup and restore Security updates 5 - Case study: Design solutions that align with security best practices and priorities Case study description Case study answers Conceptual walkthrough Technical walkthrough 6 - Design solutions for regulatory compliance Translate compliance requirements into a security solution Address compliance requirements with Microsoft Purview Address privacy requirements with Microsoft Priva Address security and compliance requirements with Azure policy Evaluate infrastructure compliance with Defender for Cloud 7 - Design solutions for identity and access management Design cloud, hybrid and multicloud access strategies (including Azure AD) Design a solution for external identities Design modern authentication and authorization strategies Align conditional access and Zero Trust Specify requirements to secure Active Directory Domain Services (AD DS) Design a solution to manage secrets, keys, and certificates 8 - Design solutions for securing privileged access The enterprise access model Design identity governance solutions Design a solution to secure tenant administration Design a solution for cloud infrastructure entitlement management (CIEM) Design a solution for privileged access workstations and bastion services 9 - Design solutions for security operations Design security operations capabilities in hybrid and multicloud environments Design centralized logging and auditing Design security information and event management (SIEM) solutions Design solutions for detection and response Design a solution for security orchestration, automation, and response (SOAR) Design security workflows Design threat detection coverage 10 - Case study: Design security operations, identity and compliance capabilities Case study description Case study answers Conceptual walkthrough Technical walkthrough 11 - Design solutions for securing Microsoft 365 Evaluate security posture for collaboration and productivity workloads Design a Microsoft 365 Defender solution Design configurations and operational practices for Microsoft 365 12 - Design solutions for securing applications Design and implement standards to secure application development Evaluate security posture of existing application portfolios Evaluate application threats with threat modeling Design security lifecycle strategy for applications Secure access for workload identities Design a solution for API management and security Design a solution for secure access to applications 13 - Design solutions for securing an organization's data Design a solution for data discovery and classification using Microsoft Purview Design a solution for data protection Design data security for Azure workloads Design security for Azure Storage Design a security solution with Microsoft Defender for SQL and Microsoft Defender for Storage 14 - Case study: Design security solutions for applications and data Case study description Case study answers Conceptual walkthrough Technical walkthrough 15 - Specify requirements for securing SaaS, PaaS, and IaaS services Specify security baselines for SaaS, PaaS, and IaaS services Specify security requirements for web workloads Specify security requirements for containers and container orchestration 16 - Design solutions for security posture management in hybrid and multicloud environments Evaluate security posture by using Microsoft Cloud Security Benchmark Design integrated posture management and workload protection Evaluate security posture by using Microsoft Defender for Cloud Posture evaluation with Microsoft Defender for Cloud secure score Design cloud workload protection with Microsoft Defender for Cloud Integrate hybrid and multicloud environments with Azure Arc Design a solution for external attack surface management 17 - Design solutions for securing server and client endpoints Specify server security requirements Specify requirements for mobile devices and clients Specify internet of things (IoT) and embedded device security requirements Secure operational technology (OT) and industrial control systems (ICS) with Microsoft Defender for IoT Specify security baselines for server and client endpoints Design a solution for secure remote access 18 - Design solutions for network security Design solutions for network segmentation Design solutions for traffic filtering with network security groups Design solutions for network posture management Design solutions for network monitoring 19 - Case study: Design security solutions for infrastructure Case study description Case study answers Conceptual walkthrough Technical walkthrough Additional course details: Nexus Humans SC-100T00 Microsoft Cybersecurity Architect training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the SC-100T00 Microsoft Cybersecurity Architect course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Essential DHCP training course description Almost all businesses use DHCP. This course builds on delegates existing IP knowledge and focuses on IP Address management using DHCP. Also covered is the role of DHCP in plug and play environments. What will you learn Explain how DHCP works. Configure DHCP servers. Troubleshoot DHCP. Essential DHCP training course details Who will benefit: Anyone working with TCP/IP. Prerequisites: TCP/IP Foundation for engineers Duration 1 day Essential DHCP training course contents Introduction What is DHCP?, IP configuration: Address, mask, default gateway, DNS. History of DHCP: RARP, BOOTP. Hands on Client configuration, releasing and renewing. DHCP servers Installation. Base configuration: Scope. Lease period. DHCP options. Hands on Server setup, Impact of lease times. Server monitoring. How DHCP works Client states. Obtaining, renewing leases. DHCP messages: DISCOVER, OFFER, REQUEST, NAK, ACK, DECLINE, RELEASE, INFORM. Hands on Troubleshooting DHCP using Wireshark. DHCP architecture DHCP relay agents. Server platforms, resilience, DHCP fail over, split scopes. Dynamic DNS and DHCP. Hands on DDNS, routers, Troubleshooting.

ISO 37001 Lead Auditor
By Training Centre
Delivered in either our Live Online format (4 days) or in our Classroom (5 days), the ISO 37001 Lead Auditor training course enables you to develop the necessary expertise to perform an Anti-bribery Management System (ABMS) audit by applying widely recognized audit principles, procedures and techniques. About This Course During this training course, you will acquire the knowledge and skills to plan and carry out internal and external audits in compliance with ISO 19011 and ISO/IEC 17021-1 certification process. Based on practical exercises, you will be able to master the audit techniques and become competent to manage an audit program and audit team. After acquiring the necessary expertise to perform this audit, you can sit for the exam and gain the "Certified ISO 37001 Lead Auditor' credential. By holding this Certificate, you will demonstrate that you have the capabilities and competencies to audit organizations based on best practices. Learning objectives Understand the operation of an Anti-bribery Management System based on ISO 37001 and its principal processes Understand the correlation between ISO 37001 and other standards and regulatory frameworks Understand the auditor's role in planning, leading and following-up on a management system audit in accordance with ISO 19011 Interpret the requirements of ISO 37001 in the context of an ABMS audit Strengthen the personal skills necessary for an auditor to act with due professional care during an audit Educational approach Lecture sessions are illustrated with practical questions and examples Practical exercises include examples and discussions Practice tests are similar to the certification exam Prerequisites A foundational understanding of ISO 37001 and knowledge of audit principles. What's Included? Refreshments & Lunch (Classroom only) Course Slide Deck Official Study Guides CPD Certificate The Exam Who Should Attend? Auditors seeking to perform and lead Anti-bribery Management System (ABMS) certification audits Managers or consultants seeking to master an Anti-bribery Management System audit process Individuals responsible for maintaining conformance with ISO 37001 requirements Technical experts seeking to prepare for an Anti-bribery Management System audit Expert advisors in Anti-bribery Management Accreditation Assessment The exam is delivered in a 12 question essay format, to be completed within 150 minutes and gaining a 70% pass mark. Exam results are provided within 24 hours. Provided by This course is Accredited by NACS and Administered by the IECB.

